WELCOME TO Systems Engineering Administration Technology User Group











- Slides: 17

WELCOME TO Systems Engineering & Administration Technology User Group Holistic Security: Defining and Defending Against Multiple Attack Vectors Wednesday, 11/16/16

Introduction to SEA-TUG • Founded in 2001 by Rob Bergin and Steve Noel to help IT professionals in the seacoast collaborate and enhance their knowledge • New steering committee formed July 2016 – John Whelan, Pamela Capper, Deb Gale, PJ Soucy, Joel Wright, Derek Rolfe, Rob Maciorski, Terry Jamro, Chris Morris • Part of larger user group communities – Boston User Groups, Meetup, etc. • This is YOUR user group – help us make it better. What topics do you want covered? What resources can you contribute?

Thank you to… • Alexander Technology Group – Food/beverages • Great Bay Community College – Meeting space

Tools • Wireless (self-powered) HDMI transmitter – https: //www. iogear. com/product/GWHD 11/ • Windows Upgrade Analytics – https: //technet. microsoft. com/itpro/windows/deploy/manage-windowsupgrades-with-upgrade-analytics – https: //blogs. technet. microsoft. com/upgradeanalytics/2016/07/22/upgrad e-analytics-public-preview-is-now-available/ • Screen. Connect Free – https: //www. screenconnect. com/free/

Tools • Easy 2 Factor security for RDP – https: //duo. com/docs/rdp • Just Enough Administration: Windows Power. Shell security controls help protect enterprise data – https: //msdn. microsoft. com/en-us/library/dn 896648. aspx • Tron. Script – Automated PC clean-up – https: //www. reddit. com/r/Tron. Script/comments/5 davu 2/tron_v 984_2016 1116_bug_fixes_and_definition/ • Reddit thread re: Must-Have Sys. Admin Tools – https: //www. reddit. com/r/sysadmin/comments/5 d 327 p/what_tools_are_ on_your_must_have_list_including/

Industry News • Understanding the Windows Credential Leak Flaw and How to Prevent It – http: //www. bleepingcomputer. com/news/security/understanding-thewindows-credential-leak-flaw-and-how-to-prevent-it/ • Reset a Windows 10 password without a boot disk or other tools – https: //4 sysops. com/archives/reset-a-windows-10 -password/ • How Stolen i. OS Devices Are Unlocked – https: //isc. sans. edu/forums/diary/How+Stolen+i. OS+Devices+Are+Unlock ed/21621/

Upcoming Events – Nov 17, 2016: NH ISSA Meeting (Portsmouth) • http: //www. issanh. org/ – Oct 1 -2: World Maker Faire – NYC • http: //www. makerfaire. com

Tonight’s Presentation Holistic Security: Defining and Defending Against Multiple Attack Vectors Craig Taylor CSO, Neoscope Technology Solutions

Holistic Security: against multiple attack vectors An Interactive Discussion Setting up our Discussion: the world is flat but… Traditional threats and defenses… Attack vectors and counter-measures… The issue of cyber-fatigue… The whole enchilada…

The Internet More. Attack Flat, easier/cheaper to criss-cross Any Groupiscan from Anywhere… (1) Script Kiddies: …hacking for fun/notoriety (2) Organized Crime: …hacking for $$$ (3) Nation States: …hacking for global advantage (4) Hactivists …hacking for political agendas

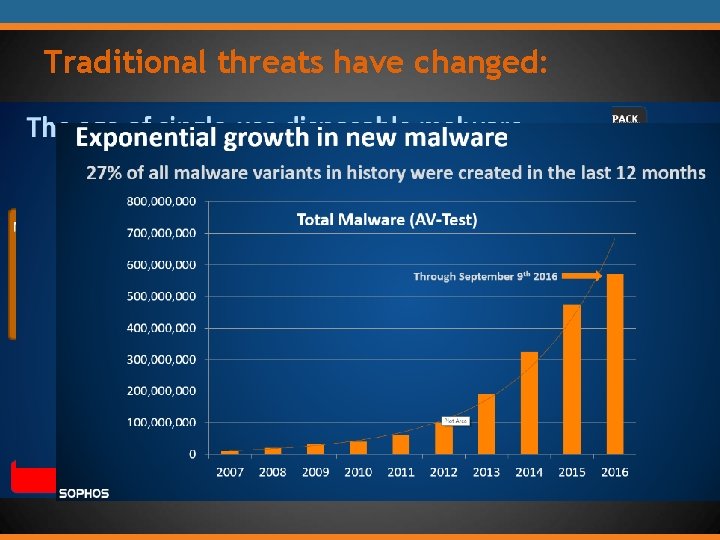
Traditional threats have changed:

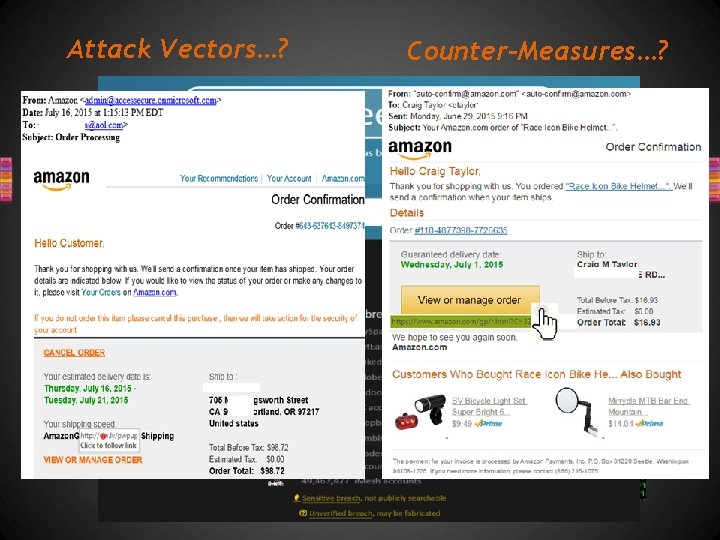
Attack Vectors…? (1) Passwords: Weakest link in organizations? (2) Phishing Attacks: Credential theft, Zero-Day Deploy (3) Ransomware: Data decryption for $$ (4) Website Attacks SQL Injection, Hosting Malware… Counter-Measures…?

Cyber Fatigue… 1. People are TIRED of too many cyber-security decisions. 2. Technical solutions for security risks must make it: easy to do the right thing, and difficult to do the wrong thing. …examples? ? ?

Security Program Components…

Addendum Slides

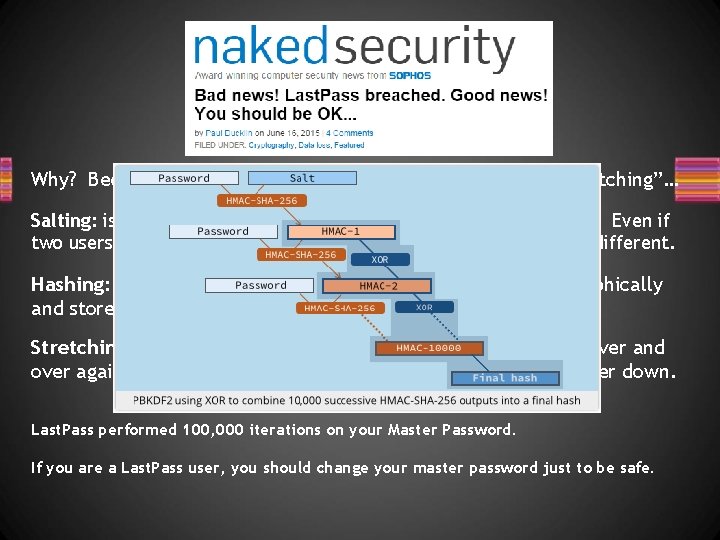
Why? Because of password “salting” then “hashing” then “stretching”… Salting: is where you add randomness to the actual password text. Even if two users pick the same password, their pwd representations are different. Hashing: is where you scramble the salted password cryptographically and store the one-way scrambled version only. Stretching: is where you deliberately re-run the hashing part over and over again before storing the representation, to slow an attacker down. Last. Pass performed 100, 000 iterations on your Master Password. If you are a Last. Pass user, you should change your master password just to be safe.

Intercept-X Attack protection techniques… Enforce Data Execution Prevention (DEP) Stack-based ROP gadget detection Mandatory Address Space Layout Randomization (ASLR) Control-Flow Integrity (CFI) assisted by hardware Bottom Up ASLR Syscall Null Page WOW 64 Anti-Heap. Spraying Load Library Dynamic Heap Spray Shellcode Import Address Table Filtering (IAF) VBScript God Mode VTable Hijacking Block Untrusted Fonts (Windows 10 only) Stack Pivot Application Lockdown Stack Exec Process Protection SEHOP Network Lockdown Prevents exploit code running from data memory Prevents predictable code locations Improves code location randomization Prevents exploits that jump via page 0 Pre-allocates common memory areas to block standard attacks Stops attacks that spray suspicious sequences on the heap Stops attackers that lookup API addresses in the IAT Helps to stop attacks that exploit virtual tables in Adobe Flash Stops abuse of the stack pointer Stops attacker code on the stack Stops abuse of the structured exception handler Stops standard Return-Oriented Programming attacks Stops advanced Return-Oriented Programming attacks Stops attackers that attempt to bypass security hooks Stops attacks that address a 64 -bit function from Wow 64 Blocks libraries that load reflectively or from UNC paths Stops code execution in the presence of exploit shellcode Prevents abuse of VBScript in IE to execute malicious code Stops elevation of privilege (EOP) attacks via untrusted fonts Stops logic-flaw attacks that bypass mitigations Stops attacks that perform process hijacking or replacement Helps to stop attacks that connect back to C&C