Welcome to all Participants Workshop on Server Hardening





















- Slides: 24

Welcome to all Participants Workshop on Server Hardening

Today Highlights • Redhat Linux 7 Installation (Dual Booting) • Server Hardening - Security overview - Vulnerability Assessment - Linux Server Hardening Security Tips - Compliance and Frameworks

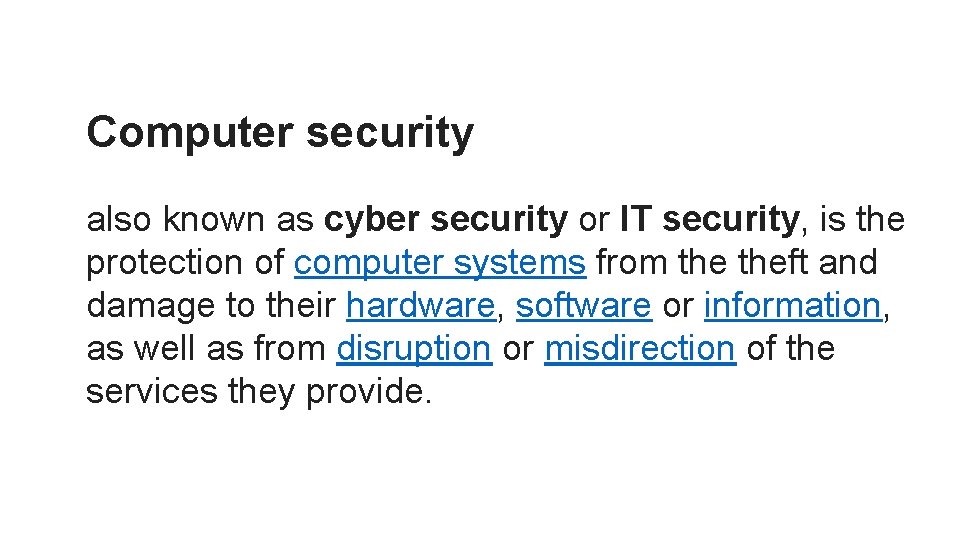
Computer security also known as cyber security or IT security, is the protection of computer systems from theft and damage to their hardware, software or information, as well as from disruption or misdirection of the services they provide.

Computer security 1. Confidentiality 2. Integrity 3. Availability

Security Controls Computer security is often divided into three distinct master categories, commonly referred to as controls: • Physical • Technical • Administrative

Physical Controls • Closed-circuit surveillance cameras • Motion or thermal alarm systems • Security guards • Picture IDs • Locked and dead-bolted steel doors • Biometrics (includes fingerprint, voice, face, iris, handwriting, etc)

Technical Controls • Encryption • Smart cards • Network authentication • Access control lists (ACLs) • Tips and Tricks

Administrative controls • Training and awareness • Disaster preparedness and recovery plans • Personnel recruitment and separation strategies • Personnel registration and accounting

Vulnerability Assessment and Testing - Outside Looking - Inside Looking

Vulnerability Assessment Tools - Nmap - Nessus - Open. VAS - Nikito - Lynis

Linux Server Hardening Security Tips § Encrypt Data Communication scp, ssh, sftp, rsync. SSL for apache etc Avoid Using FTP, Telnet

Linux Server Hardening Security Tips • Minimize Software to Minimize Vulnerability • Disable Unwanted Services • Find Listening Network Ports • Delete X Windows

Linux Server Hardening Security Tips • One Network Service Per System or VM Instance

Linux Server Hardening Security Tips • Keep Linux Kernel and Software Up to Date • Selinux • Configure Iptables and TCPWrappers • Linux Kernel /etc/sysctl. conf Hardening

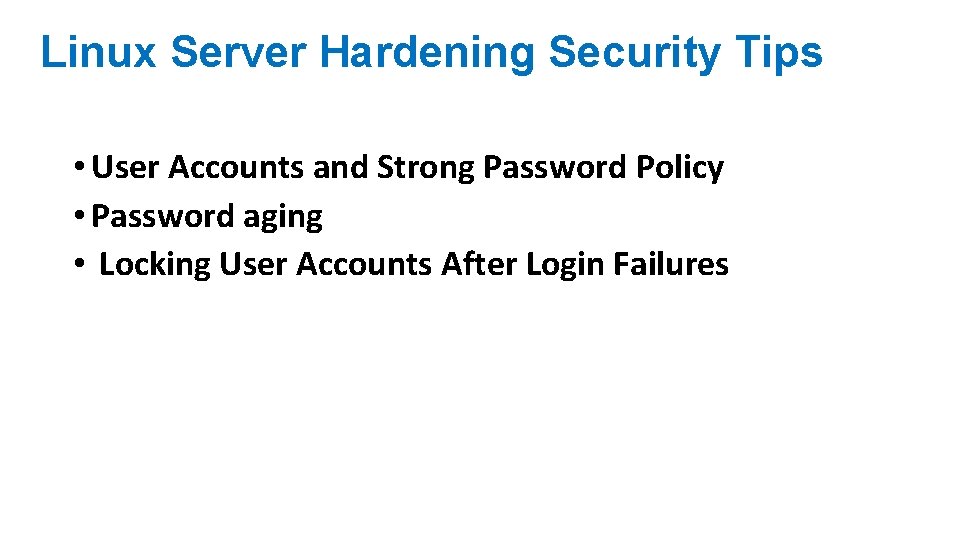
Linux Server Hardening Security Tips • User Accounts and Strong Password Policy • Password aging • Locking User Accounts After Login Failures

Linux Server Hardening Security Tips • Securing SSH Login - Disable remote root login - Use of PAM - Change default port - Port Knocking

Linux Server Hardening Security Tips • Separate Disk Partitions • Disk Quotas

Linux Server Hardening Security Tips • Use A Centralized Authentication Service • Kerberos

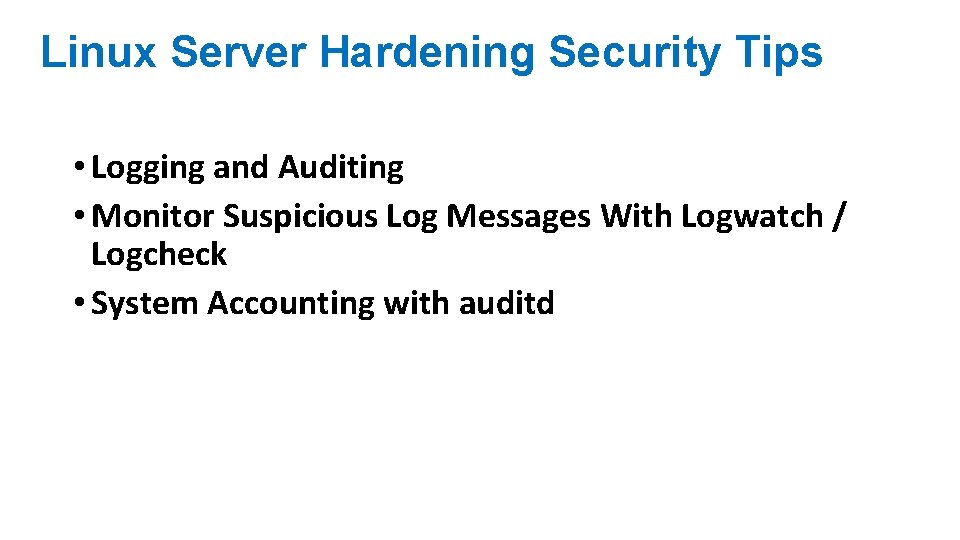
Linux Server Hardening Security Tips • Logging and Auditing • Monitor Suspicious Log Messages With Logwatch / Logcheck • System Accounting with auditd

Linux Server Hardening Security Tips • Install And Use Intrusion Detection System • Disable USB/firewire/thunderbolt devices • Use fail 2 ban/denyhost as IDS (Install an Intrusion Detection System)

Linux Server Hardening Security Tips • Use A Centralized Authentication Service • Kerberos

Linux Server Hardening Security Tips • Backup • Log Server • Physical server security

Compliance and Framework

 Welcome to all participants
Welcome to all participants Welcome to all participants
Welcome to all participants Welcome to all participants
Welcome to all participants Welcome to all participants
Welcome to all participants Introduction of participants
Introduction of participants Introduction of participants in a workshop
Introduction of participants in a workshop Welcome back participants
Welcome back participants Draw three noncollinear points j k and l
Draw three noncollinear points j k and l Wise men three clever are we
Wise men three clever are we Self-hardening sandbags
Self-hardening sandbags Hardening informatica
Hardening informatica The 4 ds
The 4 ds Macam macam hardening
Macam macam hardening Hardening openvpn
Hardening openvpn Flame hardening steel
Flame hardening steel Host hardening techniques
Host hardening techniques Firedroid
Firedroid Cisco router hardening
Cisco router hardening Ansys multilinear isotropic hardening
Ansys multilinear isotropic hardening Waney edge defect in timber
Waney edge defect in timber Difference between hardening and tempering
Difference between hardening and tempering Hardening de servidores windows
Hardening de servidores windows Cisco device hardening
Cisco device hardening Adenomalacia is the abnormal hardening of a gland.
Adenomalacia is the abnormal hardening of a gland. Work hardening definition
Work hardening definition