Web Shell Attacks Dr Bhawana Rudra National Institute

Web Shell Attacks Dr. Bhawana Rudra National Institute of Technology Karnataka

Introduction �Cyber Crime: Crime committed using a computer and the internet to steal data or information �The first recorded cyber crime took place in the year 1820 �These can be classified into �Web-based attacks � These are the attacks on a website or web application �System-based attacks � Attacks that are intended to compromise a computer or a computer network
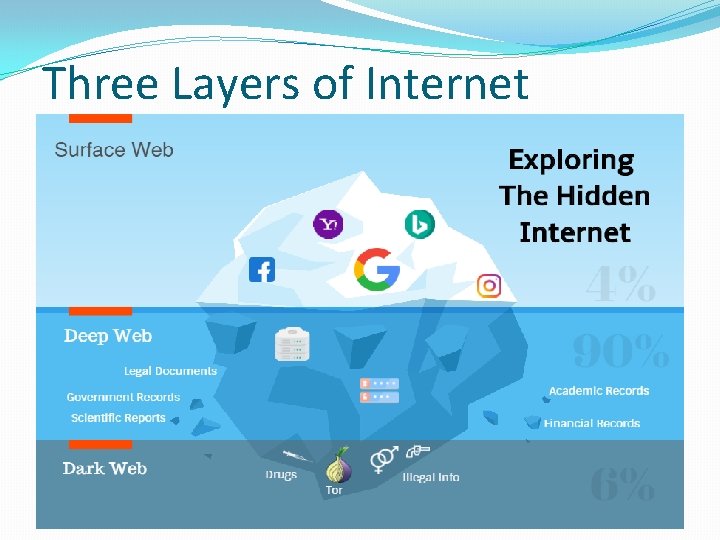
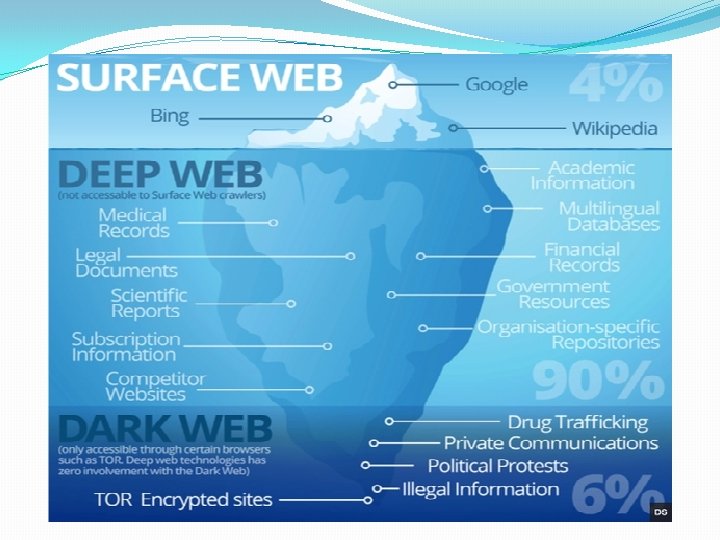
Three Layers of Internet

�Damaging or destroying data rather than stealing or misusing them is called cyber vandalism. �Transmitting virus: These are programs that attach themselves to a file and then circulate. �Terrorist attacks on the Internet is by distributed denial of service attacks, hate websites and hate emails, attacks on sensitive computer networks, etc. �Technology savvy terrorists are using 512 -bit encryption, which is impossible to decrypt.
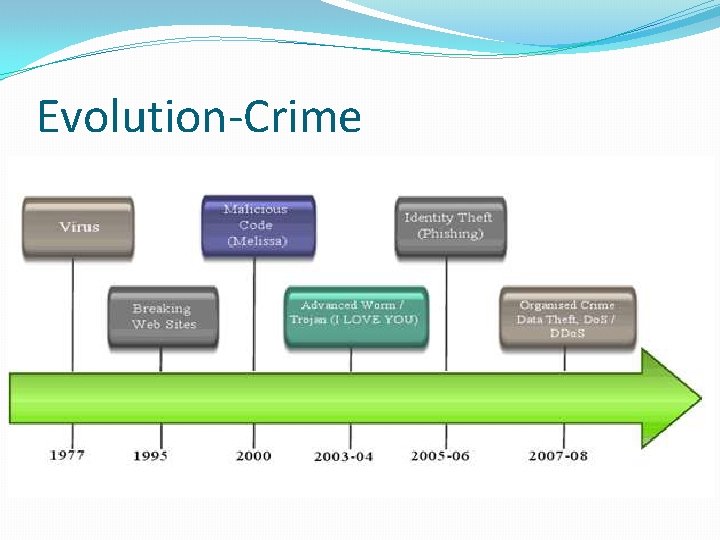
Evolution-Crime
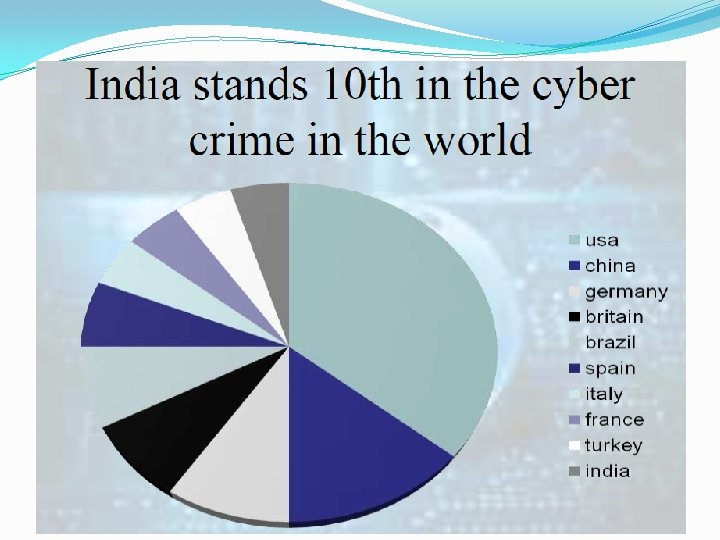
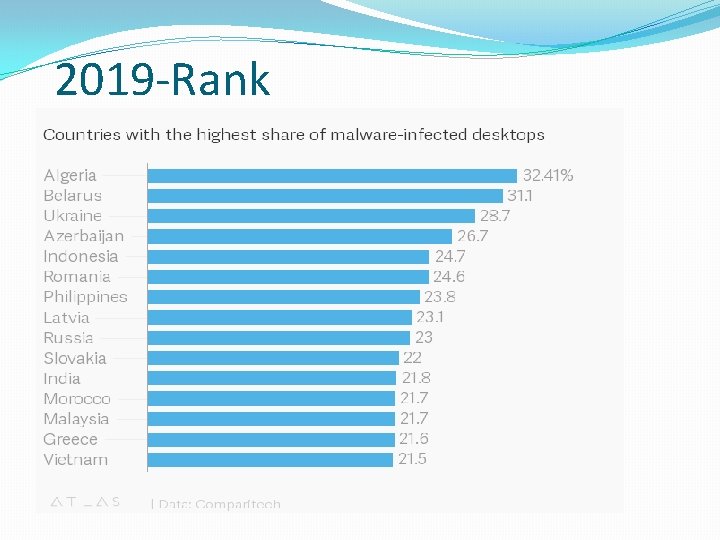
2019 -Rank

Cyber threats and concerns • • • International level Cyber crime & cyber terrorism Deliberate and anonymous use of ICTs for attacks on critical Infrastructure Unhindered growth of botnets Absence of international mechanism to facilitate information sharing & counter action Risk of attack misperception due to uncertainty of positive attack attribution • • • National level Cyber crime & terrorism Attacks on Critical Infrastructure Web defacements Website intrusion and malware propagation Malicious Code & spread of botnets Scanning and probing for Cyber espionage Denial of Service & Distributed Denial of Service attacks Supply chain integrity Technical & legal inability for positive attack attribution

Organisational level • • • Website intrusion/ defacement Domain stalking Malicious Code Scanning and probing Denial of Service & Distributed Denial of Service Targeted attacks Phishing Data theft Insider threats Financial frauds Individual level • • • Social Engineering Email hacking & misuse Identity theft & phishing Financial scams Abuse through emails Abuse through Social Networking sites • Laptop theft

Disaster Induced by Cyber Attacks • Attacks on Critical Sector Infrastructure- Nuclear, Power, Defense…in 2019 by INDIA • What will happen, if motor shaft will spin with 100 X of its normal speed? • What will happen, if control rod of nuclear reactor is controlled by attacker?
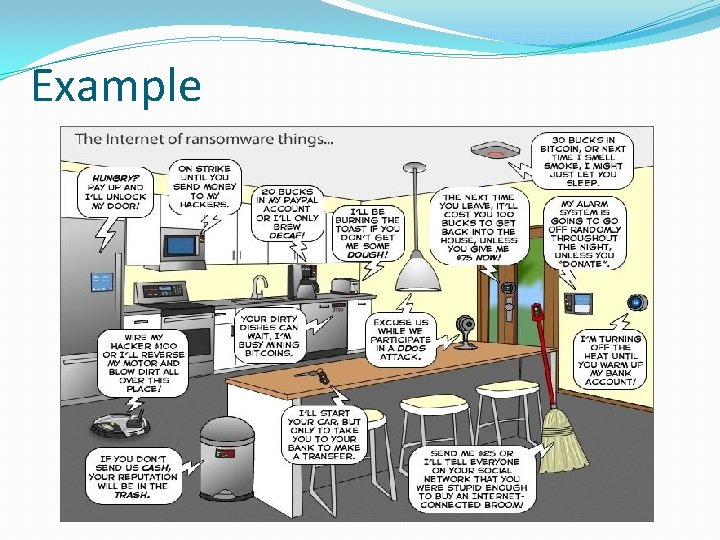
Example
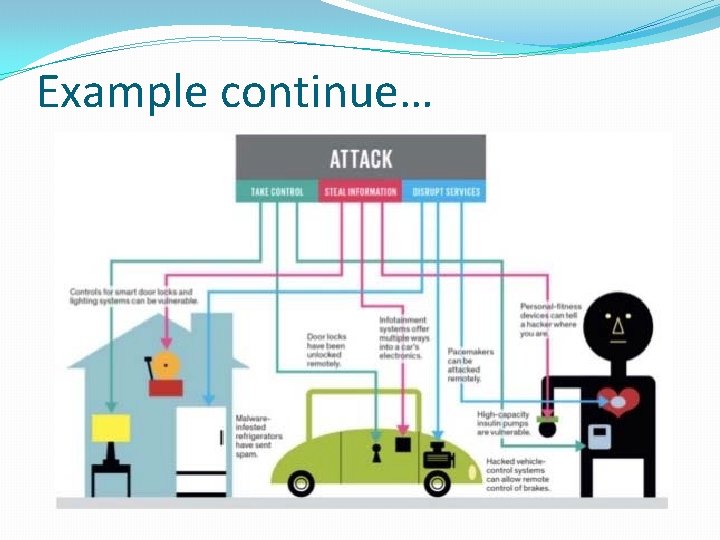
Example continue…

Main Attacks of 2017 � Ransomware Attacks � Vulnerability exploits on Windows cool down as other platforms heat up � Hardware and firmware threats an increasing target for sophisticated attackers � ‘Dronejacking’ places threats in the sky � Mobile threats to include ransomware, RATs, compromised app markets � Io. T malware opens a backdoor into the home � Io. T and DDo. S Hacks � Machine learning accelerates social engineering attacks � The explosion in fake ads and purchased “likes” erodes trust � Escalation of ad wars boosts malware delivery � Hacktivists expose privacy issues � Law enforcement takedown operations put a dent in cybercrime � Typosquatting � Threat intelligence sharing makes great strides � Cyber espionage: industry and law enforcement � Smart Medical Devices and Electronic Medical Records (EMRs) � Critical Infrastructure cyber attacks � Cloud computing providers infection � Connected Cars

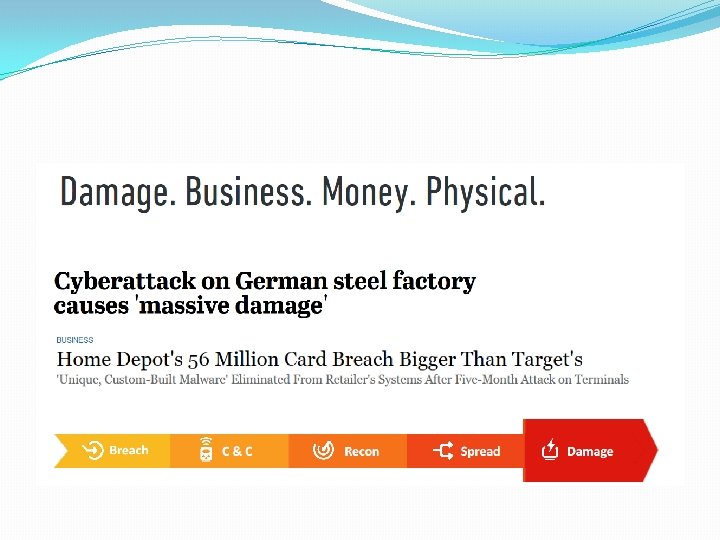
Definition � A Web. Shell is a piece of code or a script running on a server that enables remote administration. While often used for legitimate administration purposes, it is also a favorite tactic used by malicious actors in order to gain remote control of internet-facing web servers. �Once interaction with a Web. Shell is established, an attacker is free to act on any number of objectives such as service disruption, increasing foothold, and data exfiltration �Webshell is a web vulnerability and a security threat to any user or a server that can be accessed by attackers to control our system.

Attacks �Cross Site Scripting (XSS) �SQL Injection �Cross Site Request Forgery (XSRF) �Malicious File Upload �Remote File Inclusion (RFI) �Command Injection …. & more

Web-Application Attacks �Low-hanging Fruit – In-house developed- **Develop your website just Rs. 500/-**. �My Valid Email-id echo 6173686 f 6 f 2 e 6 f 6 e 6 c 696 e 6540676 d 61696 c 2 e 636 f 6 d | perl -pe 's/(. . )/chr(hex($1))/ge' �“ 75% of all attacks occurring at application layer”—Gartner �“ 8 out of 10 websites are vulnerable to attack”—White. Hat Security Team �Web apps account for 80% of internet vulnerabilities

Misleading Websites �Cybersquatters can register domain names similar to (trademarked) company, individual names �Example: http: //www. google. com vs. http: //gogle. com vs. … �Practice is illegal if done “in bad faith” �Arbitration procedures available for name reassignment (ICANN)

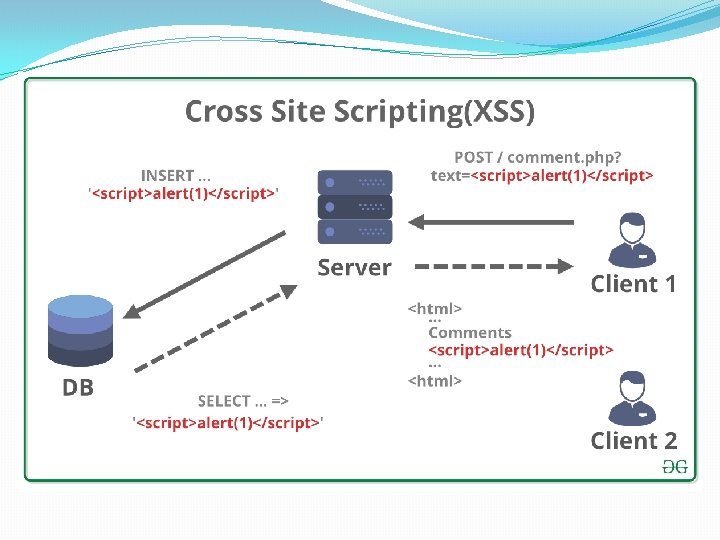
XSS and CSRF �Cross-site scripting (XSS): inject Java. Script from external source into insecure websites �Example: input <script type=“text/javascript”><!--evil code--></script> �Cross-site request forgery (CSRF): force victim browser to send request to external website → performs task on browser’s behalf �Example: force load <img src=“http: //www. bigbank. com/transfer. Funds. php? from =User&to=Attacker”/>

Malicious Shellcode �Shellcode is non-self-contained binary executable code � Distinct from malware that executes on its own � Shellcode can only execute after injection into a running process’s virtual address space �Most shellcode written in Intel IA-32 assembly language (x 86) �When injected into JS code, shellcode executes � Hijacks browser process � Can totally control target process or system �Shellcode: attack vector for malicious code execution on target systems (e. g. , Conficker worm) � Usually, browser downloads JS code containing shellcode � JS code executes, controls target process/system
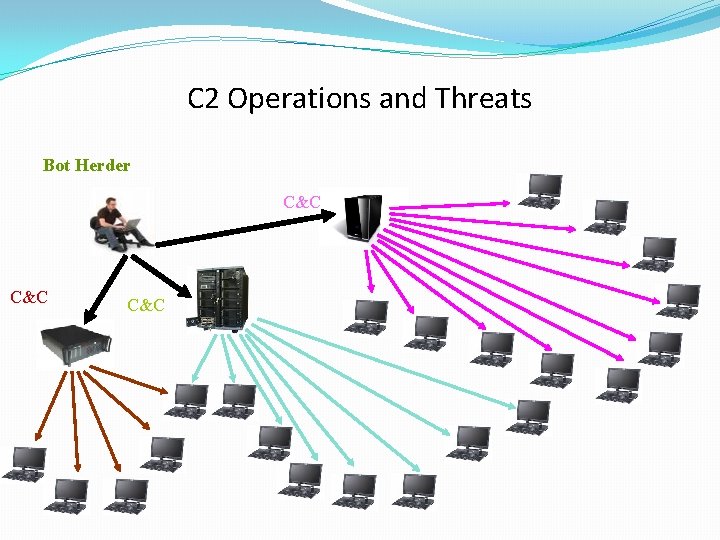
C 2 Operations and Threats Bot Herder C&C C&C

Lack of Cyber Hygiene - Attack on client side software �PDF Reader/ Flash �Microsoft office Docs �JAVA �Client side web browsers and extensions /plugins
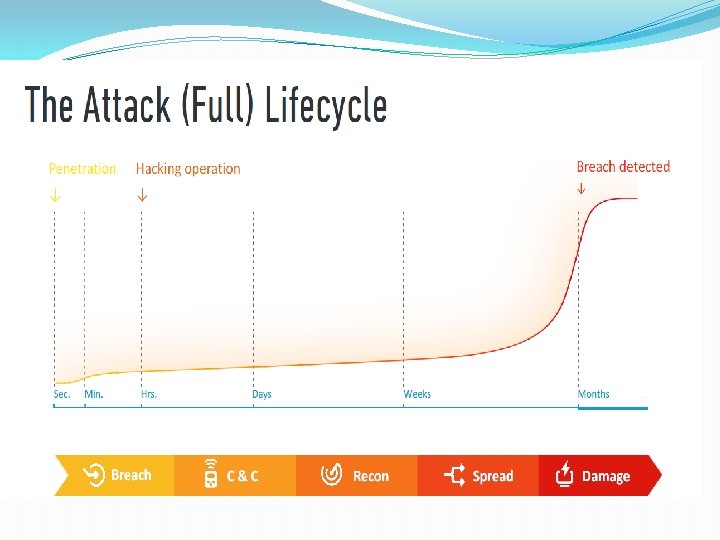
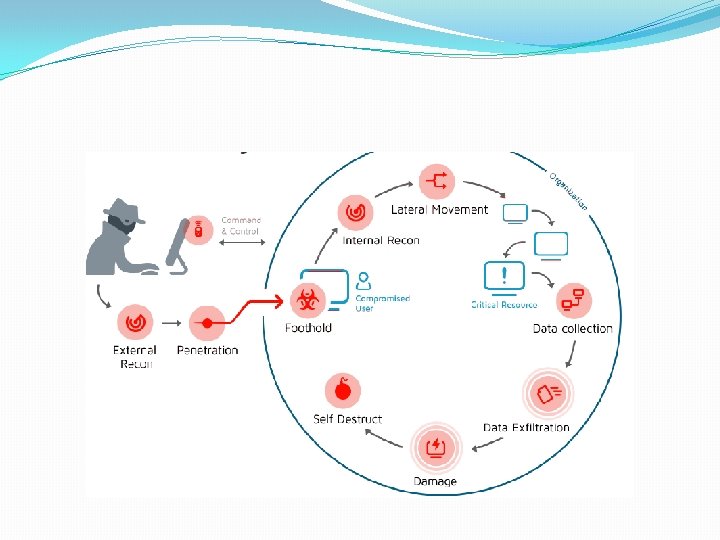



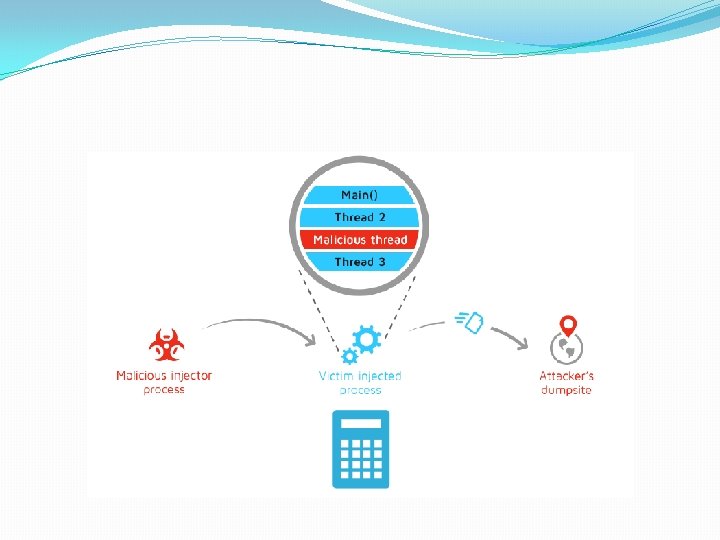



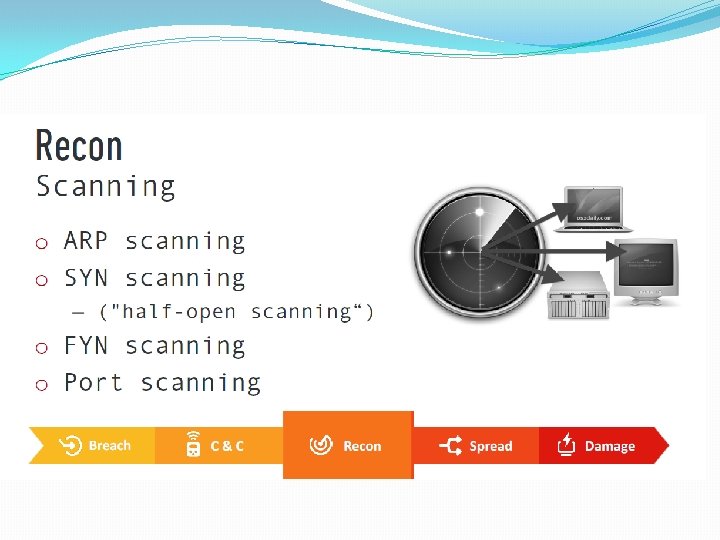

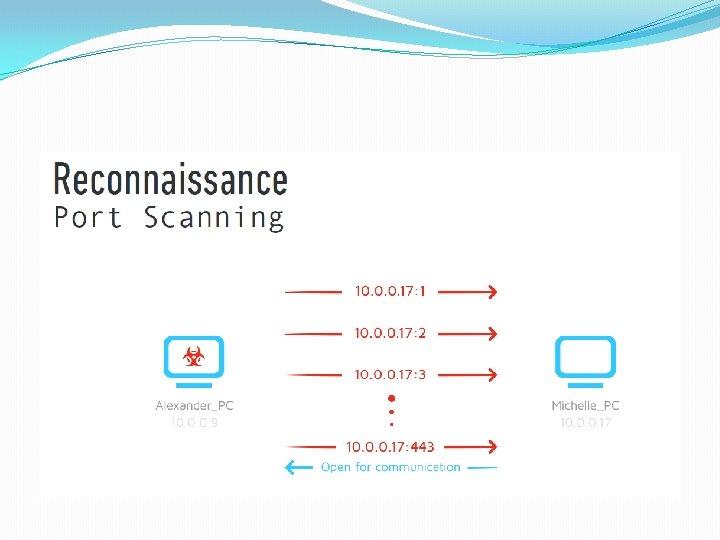
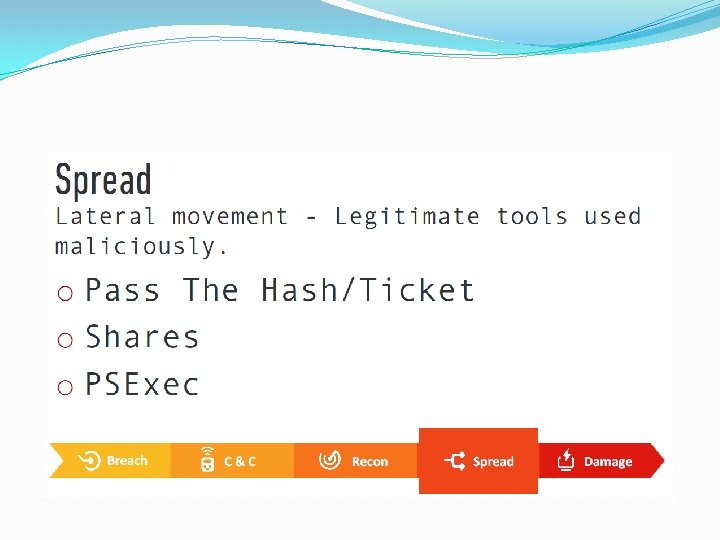

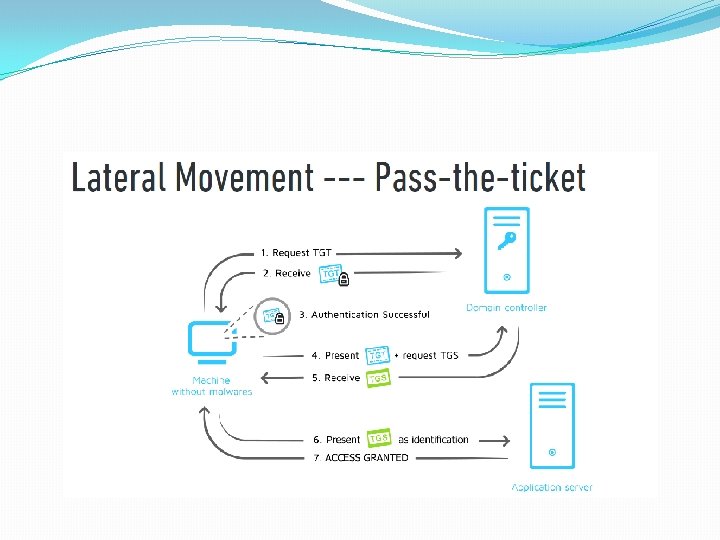
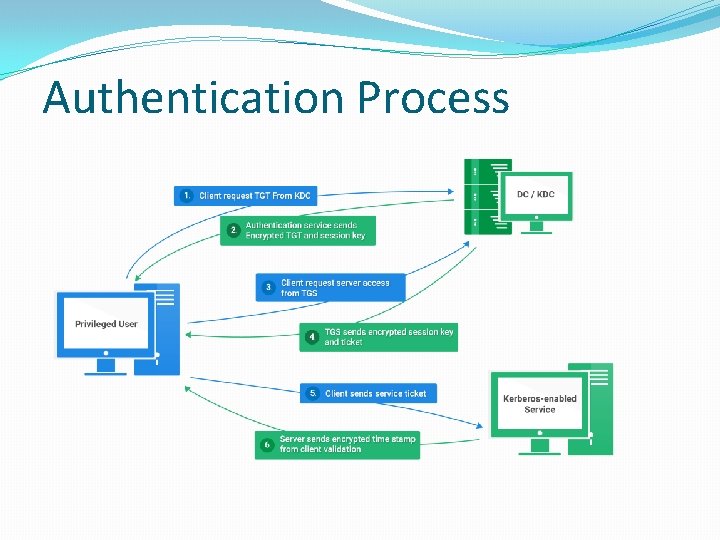
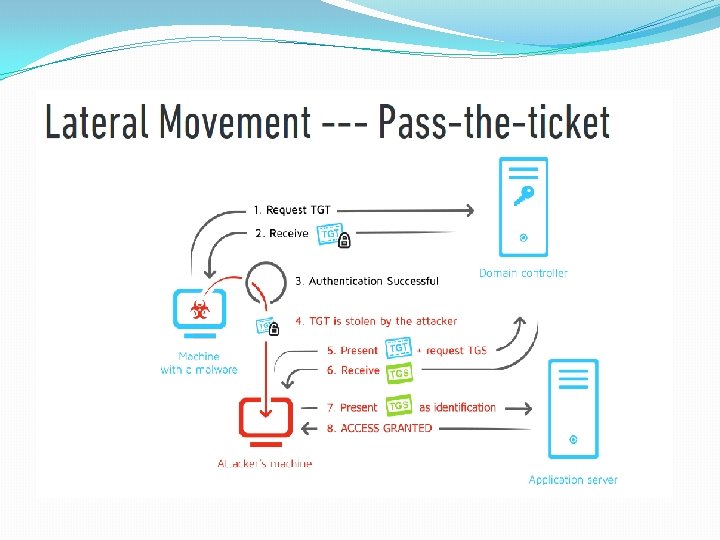
Authentication Process
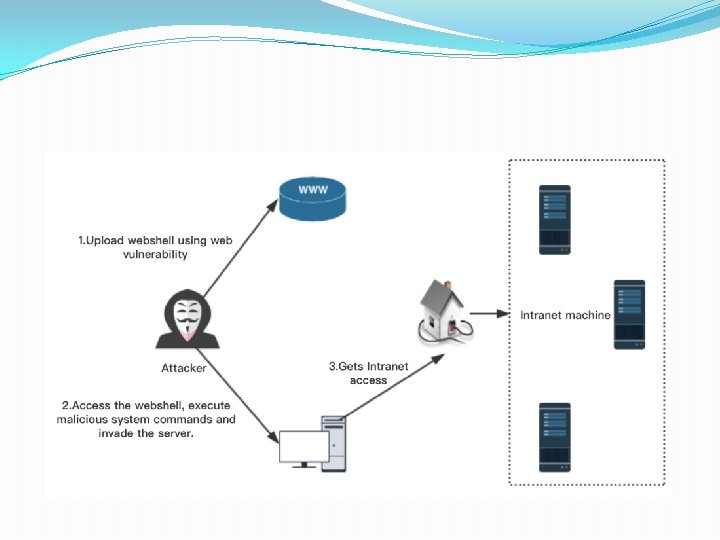
Server side Web shell Attack
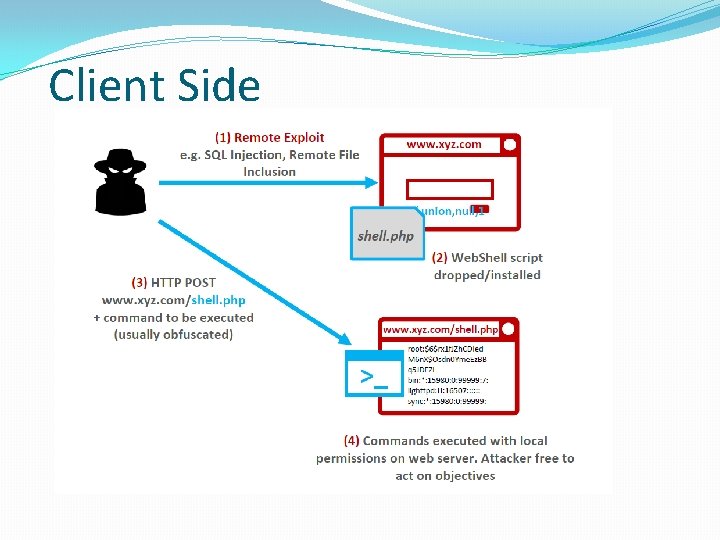
Client Side
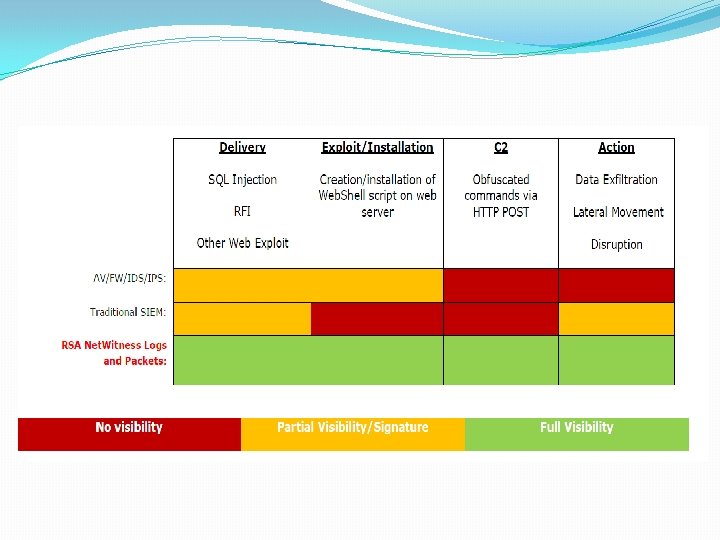
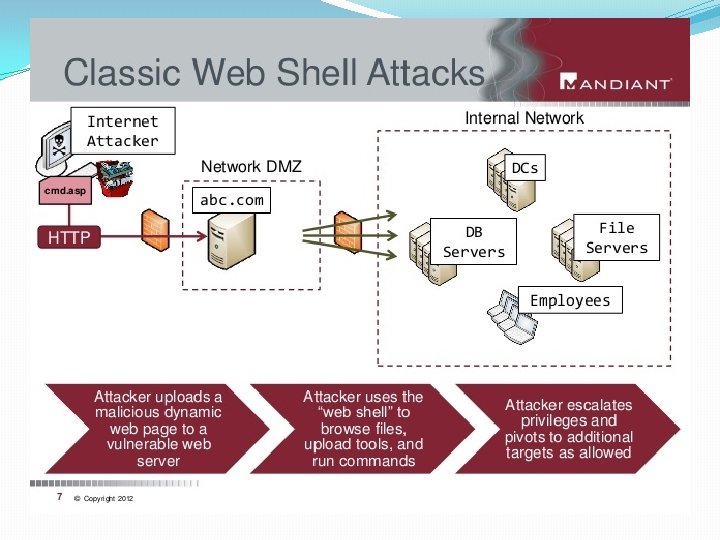

Safety Tips �Use antivirus software’s �insert firewalls �uninstall unnecessary software � maintain backup � check security settings � Stay anonymous - choose a genderless screen name �Never give your full name or address to strangers

�Learn ‘netiquette' - follow it and expect it from others �Don't respond to harassing or negative messages (flames) �Get out of uncomfortable or hostile situations quickly �Save offending messages � Learn more about Internet privacy

Thank you
- Slides: 49