Web Service Security Emily Ren Richard Mei Agenda

Web Service Security Emily Ren Richard Mei

Agenda ¨ What is Web Service? ¨ Examples and Advantages of Web Service ¨ Common Security Threads on Web Service ¨ Web Service Security Model ¨ Confidentiality ¨ Data Integrity ¨ Authentication

What are Web Services? ¨ A Web Service is a URL-addressable software resource that performs functions (or a function). ¨ Web Services communicate using standard protocol known as SOAP (Simple Object Access Protocol). ¨ A Web Service is located by its listing in a Universal Discovery, Description and Integration (UDDI) directory.

A Component now Becomes a Service Running Outside the Consumer Boundaries Discover and/or Bind Consumer 2 3 XML SOAP invoke Policies 1 SOAP CCI CCI DB ERP CRM Service Registry XML Service register

Where are Web Services being used? ¨ Dollar Rent A Car : Created an interface to expose its existing mainframe-based reservation system for access by existing and potential business partners. ¨ Bank of America: : The Ecommerce Web service for processing online credit card payment; ¨ Kansas Department of Human Resources: Developed a Web Services based system to streamline unemployment claims processing. By using Web Services they were able to leverage and integrate ‘shrink wrapped’ software with custom screens to develop and deploy a solution very quickly.

Some Web Service Threats Threat Description Message Alteration: The message content is changed in some way. Message Snooping: An unauthorized entity “sees” the message (perhaps processing it). Impersonation: an entity pretends to be another entity, sending or receiving unauthorized messages. Message Replay: Can involve both partial and complete message replay. Man-in-the-Middle: The MITM impersonates both the sender and the recipient. Denial of Service Death by a thousand cuts

Security Challenges for Web Services ¨ SOAP allows for other Message Creator messaging patterns: – Multiple relaying brokers. – Multiple recipients. ¨ Each hop represents a Node different network connection. – May want to authenticate peers at each step. – Nodes may partially process messages. Node Message Recipient
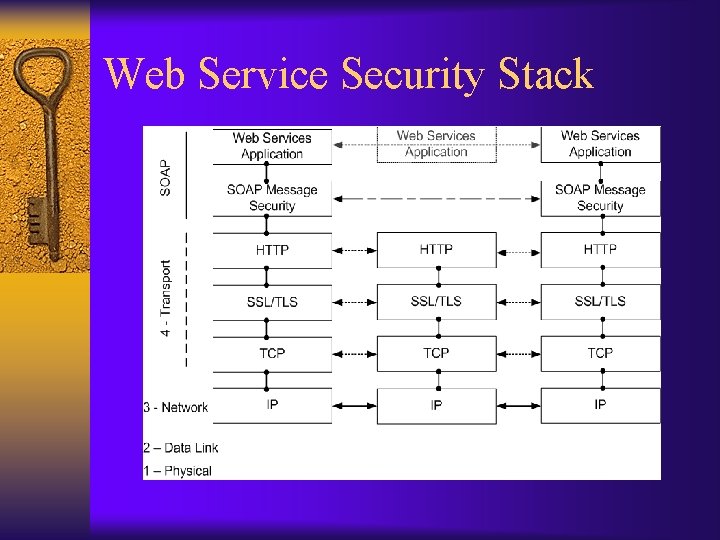
Web Service Security Stack

WS Security at Different Layers ¨ Network Level: IPSec – Secure sessions with host authentication, data integrity, data confidentiality ¨ Transport Layer: SSL/TLS Authentication, data integrity, data confidentiality – Point-to-Point secure sessions ¨ Above Transport Layer: SOAP/XML Security SOAP allows intermediaries and routing above transport – End-to-end versus point-to-point

Web Service Security Goals ¨ Confidentiality ¨ Data Integrity ¨ Authentication ¨ And More …

Manage Web Service Security ¨ Confidentiality Used to keep message transmissions private. – Typically, just encryption/description as we normally think of it.

Confidentiality ¨ Transmission Level Mechanisms – SSL, IPSec ¨ Message level: SOAP Security – Different sections may be encrypted by different keys. – Sections of XML may have layered protections Example: when transmitting credit card info, different processors may have the right to see your name, your purchase, the cost, your card number, etc.

SOAP Security and Headers ¨ SOAP headers are the extensibility point for SOAP messages. ¨ This is where we put the security metadata – Security tokens, message digests, signing algorithms, etc. ¨ SOAP security builds on XML-Encryption and XML-Digital Signatures

Sample SOAP message ¨ ¨ ¨ ¨ ¨ <? xml version="1. 0" encoding="utf-8"? > <S 11: Envelope xmlns: S 11=". . . " xmlns: wsse=". . . " xmlns: wsu=". . . " xmlns: ds=". . . "> <S 11: Header> <wsse: Security xmlns: wsse=". . . "> <ds: Signature> <ds: Signed. Info> <ds: Canonicalization. Method Algorithm= ""/> <ds: Signature. Method Algorithm=""/> </ds: Signed. Info> <ds: Signature. Value>DJbchm 5 g. K. . . </ds: Signature. Value> <ds: Key. Info> <wsse: Security. Token. Reference> <wsse: Reference URI="#My. ID"/> </wsse: Security. Token. Reference> </ds: Key. Info> </ds: Signature> </wsse: Security> </S 11: Header> <S 11: Body wsu: Id="Msg. Body“>…</S 11: Body> </S 11: Envelope>

XML Encryption ¨ Encrypted XML is still XML – The encrypted value (in base 64 encoding) of the original document is placed in another XML document. ¨ Encryption is granular – You can encrypt portions of a document – Example: child and grandchild elements become more sensitive, so apply encryptions to them in succession. ¨ XML encryption is mechanism-independent. – Specify the mechanism with a URL. The URL contains the detailed specification of the mechanism. Example: “Encryption Algorithm used”

A Simple XML Encryption Example ¨ Before <? xml version='1. 0'? > <Payment. Info> <Name>John Smith</Name> <Credit. Card Limit='5, 000' Currency='USD'> <Number>…</Number> <Issuer>…</Issuer> <Expiration>…</Expiration> </Credit. Card> </Payment. Info> After <? xml version='1. 0'? > <Payment. Info> <Name>John Smith</Name> <Encrypted. Data Type='http: //www. w 3. org/2001/04/x mlenc#Element' xmlns='http: //www. w 3. org/2001/04/x mlenc#'> <Encryption. Method Algorithm=“[http: //www. DES URI]”> <Cipher. Data> <Cipher. Value>A 23 B 45 C 56 </Cipher. Value> </Cipher. Data> </Encrypted. Data> </Payment. Info>

Manage Web Service Security ¨ Confidentiality ¨ Data Integrity – Message level, XML encryption and signatures

XML Signature ¨ The XML Signature specification represents a general way of signing XML content. ¨ Cryptographic “signing” involves the following steps: – A one-way hash of the message is created. – The hash is signed with a private key. – The signed hash and the message are transmitted. ¨ The recipient verifies the signature by hashing the received message and comparing this to the decrypted signature. – Use the sender’s public key to decrypt. – The two hashes should be bitwise identical. ¨ XML Signature tags provide both the signature and the tags necessary to verify it. – Envoloped/enveloping signatures that wrap child elements are not allowed by WS-Security. – Detached signatures apply to some other part of the document outside the tree, or even a remote document.

XML Signature (Cont. )

XML Signature Example <Signature Id="My. First. Signature" xmlns=http: //www. w 3. org/2000/09/xmldsig#> <Signed. Info> <Canonicalization. Method Algorithm=“…"/> <Signature. Method Algorithm=“…"/> <Reference URI=“…"> <Transforms> <Transform Algorithm=“…"/> </Transforms> <Digest. Method Algorithm=“…"/> <Digest. Value>j 6 lwx 3 rv. EPO 0 v. Kt. Mup 4 Nbe. Vu 8 nk=</Digest. Value> </Reference> </Signed. Info> <Signature. Value>MC 0 CFFr. VLt. Rlk=. . . </Signature. Value> <Key. Info> <Key. Value> <DSAKey. Value> </Key. Info> </Signature>

Manage Web Service Security ¨ Confidentiality – Message level and Transport level ¨ Integrity – Message level, XML encryption and digital signatures ¨ Authentication - SAML - Security Assertion Markup Language for communicating security tokens

Security Tokens ¨ Terminology – Claim: a declaration made by an entity. • Identity, group membership, privilege, etc. – Security Token: is a collection of claims ¨ Tokens may be signed or unsigned.

More on Web Service Security ¨ More security considerations: – Availability – Authorization – Federation – Etc. ¨ Far from standardized and mature

Questions? ¨ ? ? ?
![References ¨ [1] Security in a Web Services World: A Proposed Architecture and Roadmap, References ¨ [1] Security in a Web Services World: A Proposed Architecture and Roadmap,](http://slidetodoc.com/presentation_image/0fb31a33273abfc26656fdd5e196af63/image-25.jpg)
References ¨ [1] Security in a Web Services World: A Proposed Architecture and Roadmap, A joint security whitepaper from IBM Corporation and Microsoft Corporation. April 7, 2002, ¨ [2] Secure Web Services, Geoffrey Fox, Marlon Pierce, Community Grids Lab, Indiana University ¨ [3] Intro to Web Services, David M. Rubin, Softstar ¨ [4] Manage Web Service Security, Charles Burke, The OWASP foundation
- Slides: 25

















































