Web Security Overview Web Application security OWASP ASVS


Web Security

Overview • Web Application security • OWASP ASVS • PCI-DSS • FISMA • FUM APA Lab 3
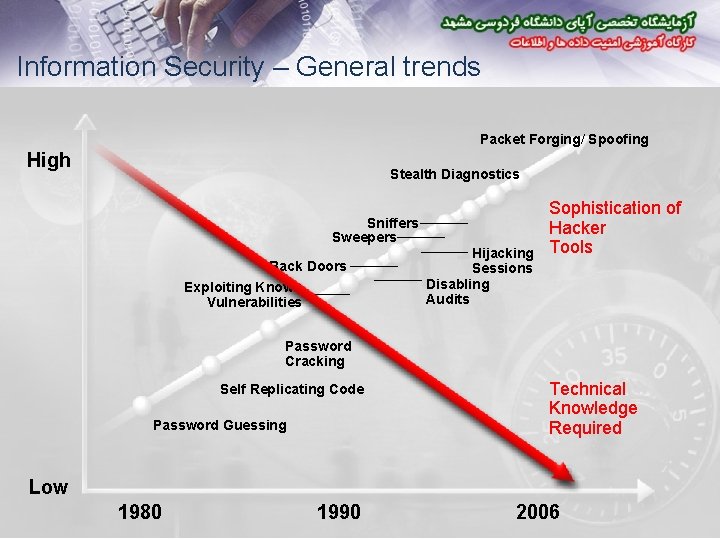
Information Security – General trends Packet Forging/ Spoofing High Stealth Diagnostics Sniffers Sweepers Back Doors Exploiting Known Vulnerabilities Hijacking Sessions Disabling Audits Sophistication of Hacker Tools Password Cracking Self Replicating Code Password Guessing Technical Knowledge Required Low 1980 1990 2006
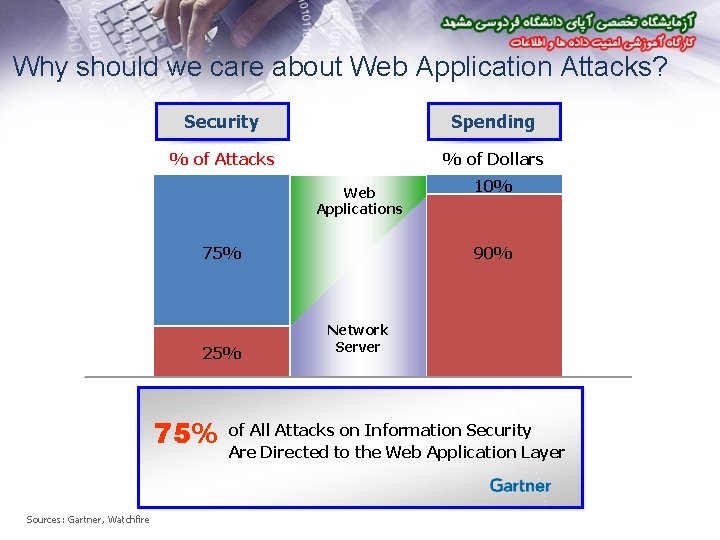
Why should we care about Web Application Attacks? Security Spending % of Attacks % of Dollars Web Applications 75% 25% 75% Sources: Gartner, Watchfire 10% 90% Network Server of All Attacks on Information Security Are Directed to the Web Application Layer
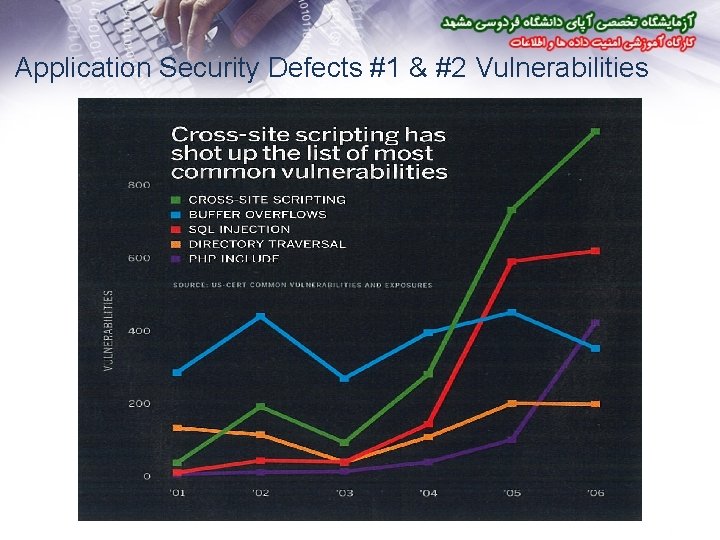
Application Security Defects #1 & #2 Vulnerabilities

Why Application Security is a High Priority • Web applications are the #1 focus of hackers: – 75% of attacks at Application layer (Gartner) – XSS and SQL Injection are #1 and #2 reported vulnerabilities (Mitre) • Most sites are vulnerable: – 90% of sites are vulnerable to application attacks (Watchfire) – 78% percent of easily exploitable vulnerabilities affected Web applications (Symantec) – 80% of organizations will experience an application security incident by 2010 (Gartner) • Web applications are high value targets for hackers: – Customer data, credit cards, ID theft, fraud, site defacement, etc • Compliance requirements: – Payment Card Industry (PCI) Standards, GLBA, HIPPA, FISMA,

Why Application Security Problems Exist Root Cause: – Developers are not trained to write or test for secure code – Network security (firewall, IDS, etc) does not protect the Web Application Layer • Current State: – Organizations test tactically at a late & costly stage in the SDLC – A communication gap exists between security and development as such vulnerabilities are not fixed – Testing coverage is incomplete Goal: – To build better and more secure Web Applications/websites

High Level Web Application Architecture Review Customer App is deployed here Sensitive data is stored here Internet Firewall Client Tier (Browser) Database SSL Protects Transport Protects Network (Presentation) App Server (Business Logic) Middle Tier Data Tier

(ASVS) July 2009
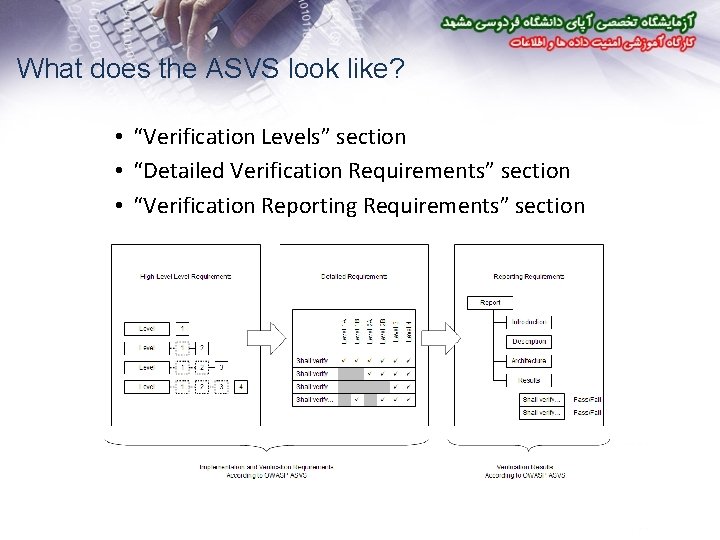
What does the ASVS look like? • “Verification Levels” section • “Detailed Verification Requirements” section • “Verification Reporting Requirements” section

What are ASVS verification levels?

Levels in more detail – Level 1 – Automated Verification – Level 1 A – Dynamic Scans (Partial Automated Verification) – Level 1 B – Source Code Scans (Partial Automated Verification) – Level 2 – Manual Verification – Level 2 A – Manual Pentesting (Partial Manual Verification) – Level 2 B – Manual Source Code Review (Partial Manual Verification) – Level 3 – Design Verification – Level 4 – Internal Verification
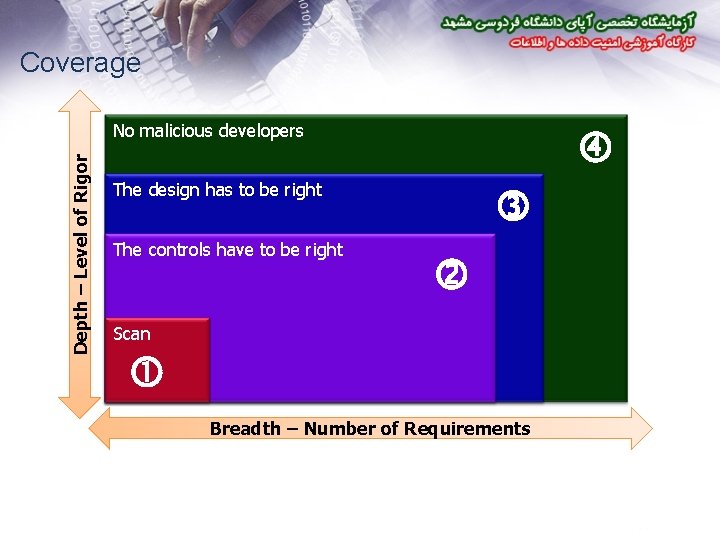
Coverage Depth – Level of Rigor No malicious developers The design has to be right The controls have to be right Scan Breadth – Number of Requirements
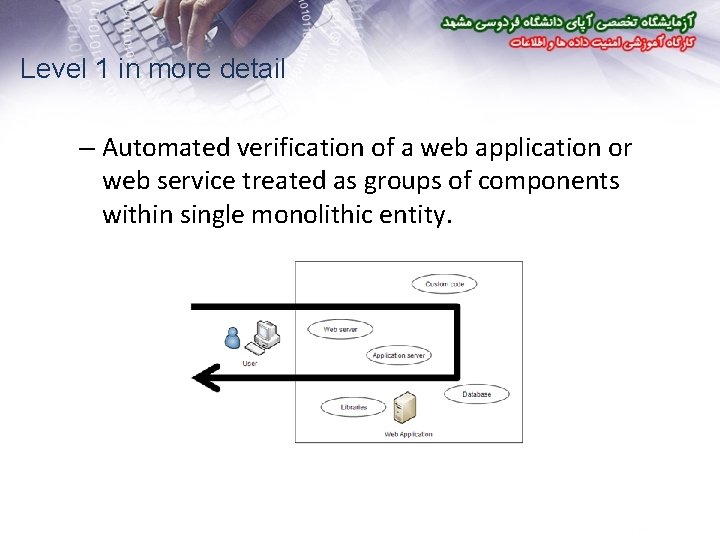
Level 1 in more detail – Automated verification of a web application or web service treated as groups of components within single monolithic entity.
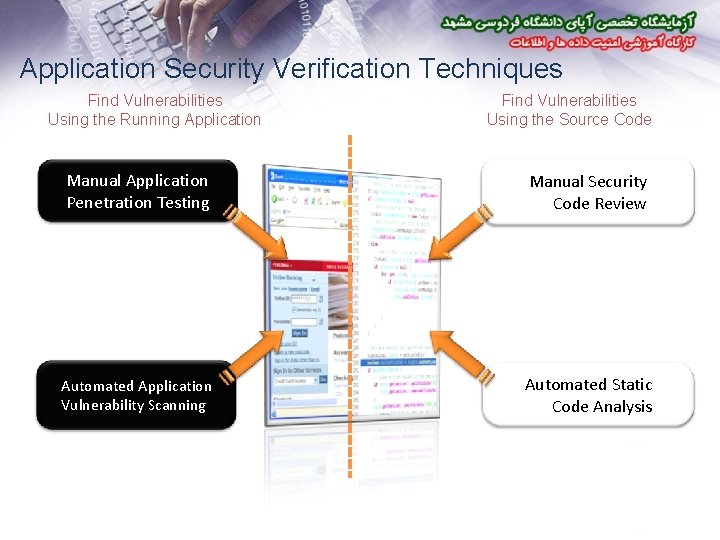
Application Security Verification Techniques Find Vulnerabilities Using the Running Application Find Vulnerabilities Using the Source Code Manual Application Penetration Testing Manual Security Code Review Automated Application Vulnerability Scanning Automated Static Code Analysis
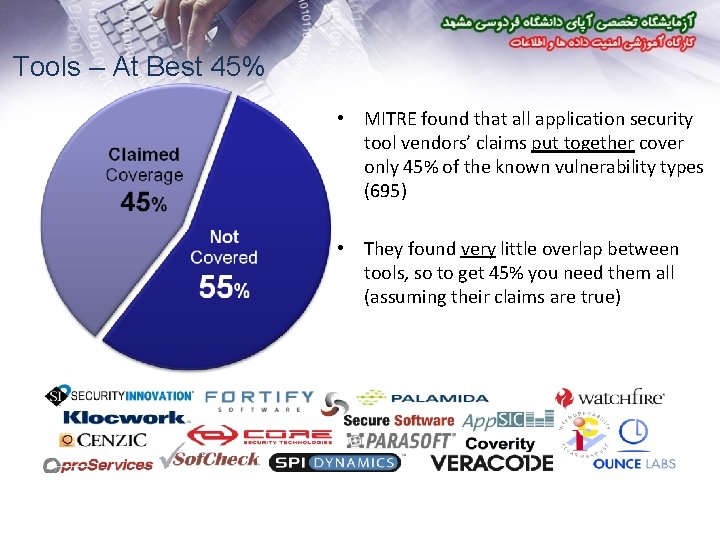
Tools – At Best 45% • MITRE found that all application security tool vendors’ claims put together cover only 45% of the known vulnerability types (695) • They found very little overlap between tools, so to get 45% you need them all (assuming their claims are true)

Level 2 Options • Level 2 A Manual Penetration Test • Level 2 B Manual Code Review l Need BOTH to achieve a full level 2 l But requirements can be filled by either

Level 2 in more detail – Manual verification of a web application or web service organized into a high-level architecture.
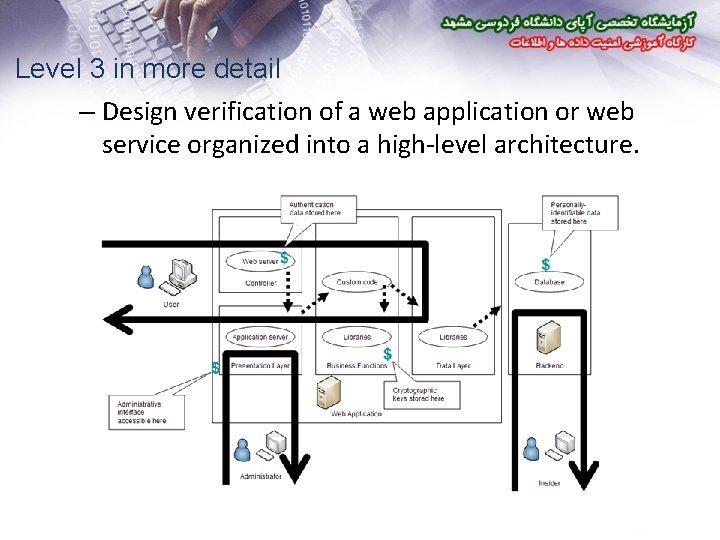
Level 3 in more detail – Design verification of a web application or web service organized into a high-level architecture.

Level 4 in more detail – Internal verification by searching for malicious code (not malware) and examining how security controls work.
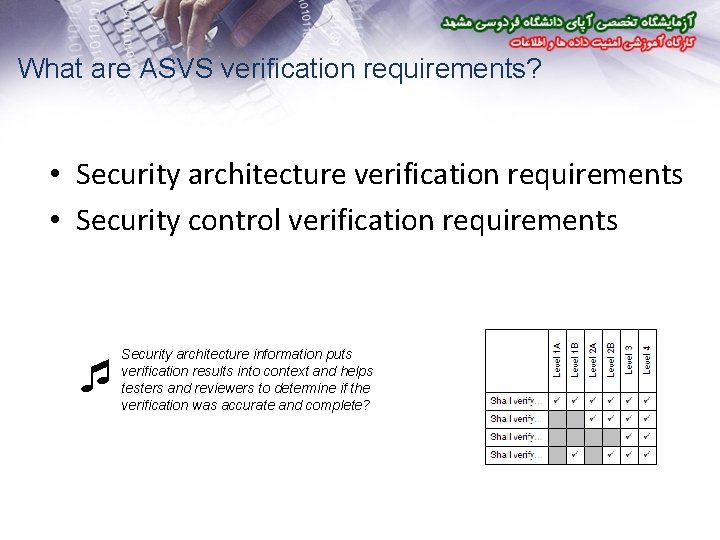
What are ASVS verification requirements? • Security architecture verification requirements • Security control verification requirements Security architecture information puts verification results into context and helps testers and reviewers to determine if the verification was accurate and complete?

A positive approach • Negative – The tester shall search for XSS holes • Positive – The tester shall verify that the application performs input validation and output encoding on all user input

Requirement Summary

Payment Card Industry (PCI) Data Security Standard (DSS)

Overview of PCI DSS • Applies to – all merchants that “store, process, or transmit cardholder data” – all payment (acceptance) channels, including brickand-mortar, mail, telephone, e-commerce (Internet) • Includes 12 requirements, based on – administrative controls (policies, procedures, etc. ) – physical security (locks, physical barriers, etc. ) – technical security (passwords, encryption, etc. )

PCI DSS requirements • Each requirement has many sub-requirements! 1. Install and maintain a firewall configuration to protect data 2. Do not use vendor-supplied defaults for system passwords and other security parameters 3. Protect stored data

PCI DSS requirements 4. Encrypt transmission of cardholder data and sensitive information across public networks 5. Use and regularly update anti-virus software 6. Develop and maintain secure systems and applications 7. Restrict access to data by business need-toknow

PCI DSS requirements 8. Assign a unique ID to each person with computer access 9. Restrict physical access to cardholder data 10. Track and monitor all access to network resources and cardholder data 11. Regularly test security systems and processes 12. Maintain a policy that addresses information security

Self-Assessment Questionnaire Types

Federal Information Security Management Act FISMA
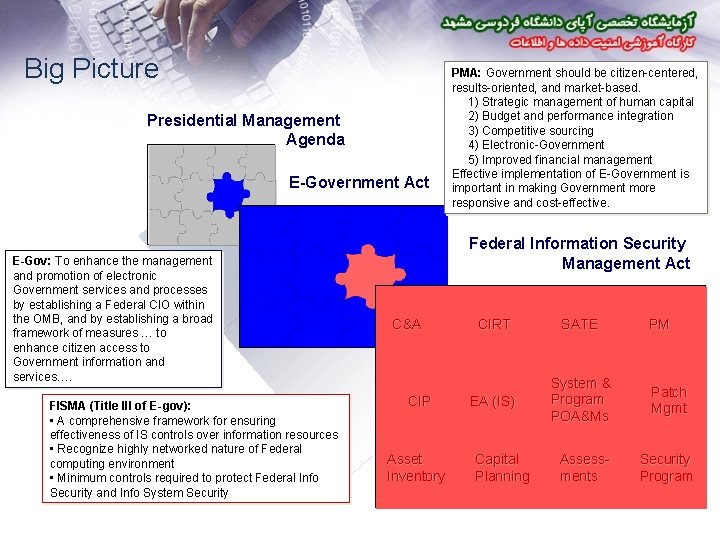
Big Picture Presidential Management Agenda E-Government Act E-Gov: To enhance the management and promotion of electronic Government services and processes by establishing a Federal CIO within the OMB, and by establishing a broad framework of measures … to enhance citizen access to Government information and services…. FISMA (Title III of E-gov): • A comprehensive framework for ensuring effectiveness of IS controls over information resources • Recognize highly networked nature of Federal computing environment • Minimum controls required to protect Federal Info Security and Info System Security PMA: Government should be citizen-centered, results-oriented, and market-based. 1) Strategic management of human capital 2) Budget and performance integration 3) Competitive sourcing 4) Electronic-Government 5) Improved financial management Effective implementation of E-Government is important in making Government more responsive and cost-effective. . Federal Information Security Management Act C&A CIP Asset Inventory CIRT SATE EA (IS) System & Program POA&Ms Capital Planning Assessments PM Patch Mgmt Security Program

FISMA Reporting Roles & Responsibilities Head of Agency • Ensure integration of security management processes • Ensure senior officials provide security info for operations & assets • Ensure personnel are trained in compliance with mandate • Ensure CIO reports annually on the IS program effectiveness CIO • Designates Senior Agency Information Security Officer to carry out security responsibilities • Ensures senior management support • Reports to Head of Agency on the IS program’s performance CISO (Senior Agency Information Security Officer) • Heads IS program office with mission and resources to ensure agency compliance with FISMA • Develops & maintains policy, procedures and techniques to address requirements • Train & overseas Information Security personnel • Assist senior agency officials concerning their responsibilities

FISMA • US Government organizations such as GAO, OMB, and NIST have identified fundamental management controls needed for effective information security. • These management controls are abstracted from long-standing requirements found in statutes, policies, and guidance. They cover topics such as: – – – Risk Management Security Control Reviews Contingency Planning Access Controls Incident Response

Fundamental security management principles and controls – NIST SP 800 -26, Security Self-Assessment Guide for Information Technology Systems – NIST SP 800 -14, Generally Accepted Principles and Practices for Securing Information Technology Systems – NIST SP 800 -12, An Introduction to Computer Security: The NIST Handbook – GAO Executive Guide, Information Security Management: Learning From Leading Organizations – FISMA and OMB Circular No. A-130 Appendix III

FISMA as part of the E-Government Act of 2002 • FISMA consolidates many security requirements and guidance into an overall framework for managing information security and protecting the nation’s critical information infrastructure from harm • FISMA requires executive agencies within the federal government to: – – Plan for security Ensure that appropriate officials are assigned security responsibility Review periodically the security controls in their information systems Authorize system processing prior to operations, and periodically after deploying • FISMA has three main sections – Annual security reporting requirement (Annual Program Review – CIO) – Independent Evaluation – (IG) and – Corrective action plan for remediation of security weaknesses
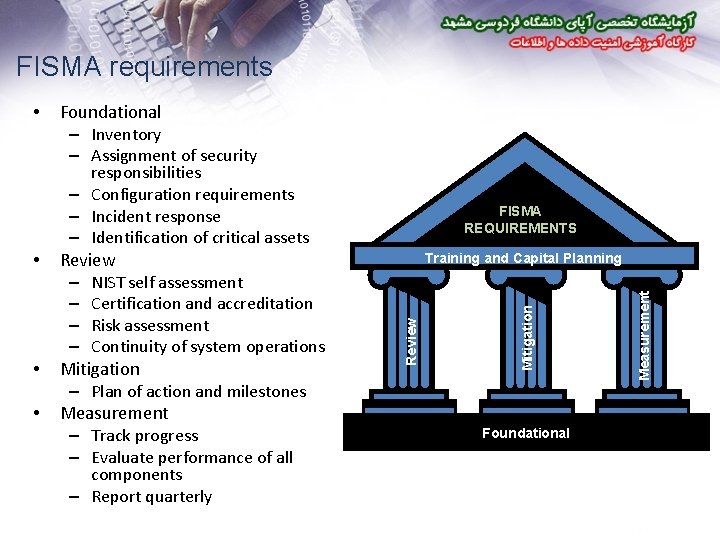
FISMA requirements Foundational – Inventory – Assignment of security responsibilities – Configuration requirements – Incident response – Identification of critical assets • components – Report quarterly Training and Capital Planning Foundational Measurement • Review – NIST self assessment – Certification and accreditation – Risk assessment – Continuity of system operations Mitigation – Plan of action and milestones Measurement – Track progress – Evaluate performance of all Review • FISMA REQUIREMENTS Mitigation •

Foundational • Senior information security official should appointed by and report to the CIO • An inventory program which is: – – Updated at least annually Made available to the Comptroller General Used to support information resources management Synchronized with their enterprise architecture inventory efforts • Identification of critical assets and their interdependencies with other assets • An established patch management process which assumes – a configuration management process exists – patches are tested prior to implementation • Incident response is closely tied to patch management Foundational

Review • Depth and breadth of an annual FISMA review depends on several factors such as: • Testing should also include management, operational and technical controls Review 1. The acceptable level of risk and magnitude of harm to the system or information 2. The extent to which system configurations and settings are documented and continuously monitored 3. The extent to which patch management is employed for the system 4. The relative comprehensiveness of the most recent past review 5. The vintage of the most recent in-depth testing and evaluation as part of system certification and final accreditation

Plan of Action and Milestones (POA&M) • Plan of Action and Milestones (POA&M) are: • OMB uses all Federal POA&Ms to conduct their assessment of the Federal government’s IT security maturity • IGs are asked this year to assess against specific criteria whether the agency has developed, implemented, and is managing an agency-wide POA&M process • The IG’s assessment in this area is critical • Effective remediation of IT security weaknesses is essential to achieving a mature IT security program Mitigation – Designed to facilitate review, analysis, and decision making for performance improvement in implementing corrective actions – Used as a point of comparison for a Department to compare an organization’s progress in the area of IT security – Reviewed within a Department and by OMB
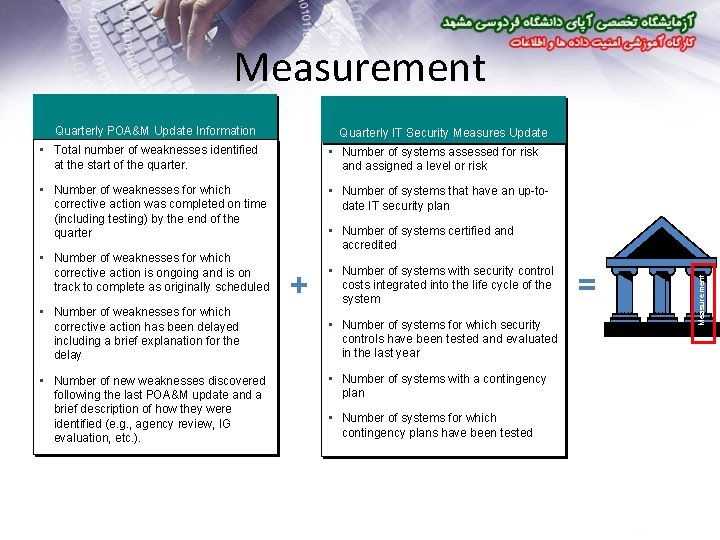
Measurement Quarterly POA&M Update Information Quarterly IT Security Measures Update • Total number of weaknesses identified at the start of the quarter. • Number of systems assessed for risk and assigned a level or risk • Number of weaknesses for which corrective action was completed on time (including testing) by the end of the quarter • Number of systems that have an up-todate IT security plan • Number of weaknesses for which corrective action has been delayed including a brief explanation for the delay • Number of new weaknesses discovered following the last POA&M update and a brief description of how they were identified (e. g. , agency review, IG evaluation, etc. ). + • Number of systems with security control costs integrated into the life cycle of the system • Number of systems for which security controls have been tested and evaluated in the last year • Number of systems with a contingency plan • Number of systems for which contingency plans have been tested = Measurement • Number of weaknesses for which corrective action is ongoing and is on track to complete as originally scheduled • Number of systems certified and accredited

Training and Capital Planning • Integrating IT security into the capital planning process – POA&Ms, annual FISMA reports, and executive summaries must be crossreferenced to the budget materials – Exhibit 300: Capital asset plan and justification – Exhibit 53: Summary of IT systems and expenditures. – Unique project identifier that stems from Exhibit 300 s and 53 s must be referenced in the “Resources Required” column of the POA&M. – Although the POA&M and Exhibit 300 s may cite the same unique project identifiers, the security costs will not match because the Exhibit 300 s also contains ongoing security maintenance costs. • Training and Capital Planning Mitigation – All parts of IT security management team need awareness and training – Responsibility to provide training is placed on CIO – Responsibility of program officials to complete training

FUM CERT Lab

Computer Emergency Response Team (CERT) q. A centralized location for Information Technology (IT) personnel both technical and non-technical to get or report incidents q. A centralized location to get or report vulnerabilities to systems; regardless of the platform q. Other resources such as tools and techniques, research and guideline, policy and government, and education q. Publications and events are hosted by CERT to help with protecting the nation’s networks

About APA آگﺎﻫﻲ ﺭﺳﺎﻧﻲ q APA is a CERT Center established by ICT Security Faculty of ITRC in Iran پﺸﺘﻴﺒﺎﻧﻲ ﺍﻣﺪﺍﺩ q APA is a center for cyberspace security incidents & vulnerabilities assistance. This Center attempts to provide reactive and proactive services in this field

APA’s sub centers v Ferdowsi University of Mashhad APA group (network service Lab) v Sharif University of Technology APA group (Database Lab) v Amirkabir University of technology APA group (Operating System Lab) v Isfahan University of Technology APA group (network equipment Lab) v Imam Hossein University APA group ( Cryptography Lab) v Yazd University APA group ( Application Softwares Lab) v Tarbiat Modares University APA group (Spam Lab)

FUM CERT Lab o Established 1387/10 o APA center at Ferdowsi University of Mashhad deals with reports on detection of security vulnerabilities in main network services such as DNS, DHCP, MAIL, etc are provided o Networks Services, such as Web E-mail DNS Remote Login Firewall Proxy & Cache Directory Service FTP o Wireless tools 802. 11 protocols and products category Wi-Fi 802. 16 Protocols category and Wi. MAX Products 802. 15. 1 Protocols category and Bluetooth products

APA Portal www. ircert. cc Ir. CERT Portal http: //cert. um. ac. ir FUM CERT Lab Portal
APA Portal q Vulnerabilities q Article § White Paper § Report validation vulnerability q News & Events q National Alarm q forum q FAQ

Activities q. Workshops q. Elearning Courses q. Security awareness q. Web Security q. ISMS q. Cyber. Law q. Penetration Testing q Available per request q Done by skilled security personnel q Security Certificate q Issuing OWASP ASVS L 1 A certificate q Bi. Weekly Seminar (For Members) q Electronic Newsletter

Activities q Conferences § APA Conferenc – ITRC – TEHRAN – 1388/03

Activities q Conferences § APA Conferenc – ITRC – TEHRAN – 1388/03

Activities q Workshop § Workshop in network security – 1388/04

Activities q Workshop § Workshop in network security – 1388/04
Registration Organizations Green Form In Fo ld er Organization Person

Demand Cooperation Persons Blue Form In Registration Table

- Slides: 57