Web Defacement in Cybercrime Teddy Mantoro teddyieee org

Web Defacement in Cybercrime Teddy Mantoro teddy@ieee. org Asian Institute of Technology, Bangkok, Thailand 2018 -07 -11 1

Outline • Introduction – What is web defacement? – How bad is web defacement? – The common defacement techniques • Web Defacement: Who are the victims and what are the targets – Web Defacement in Indonesia, Malaysia, Singapore Thailand • How to protect web server from defacing – Reverse proxy server 2

What is Web Defacement? Defacement is a kind of electronic graffiti and, as other forms of vandalism, is also used to spread messages by politically motivated "cyber protesters" or hacktivists[1]. Defacement is one of the big issue in Web security. There has been at least 50, 000 successful website defacement attacks each month for the past year, or that 55% of successful attacks are actually re-defacements[2]. 3
![How Bad is Web Security? Very bad, since 2007 [3] Web Application Security Consortium How Bad is Web Security? Very bad, since 2007 [3] Web Application Security Consortium](http://slidetodoc.com/presentation_image_h2/a4673b7575e5f8adc3047a1feb8a290f/image-4.jpg)
How Bad is Web Security? Very bad, since 2007 [3] Web Application Security Consortium (WASC) http: //www. webappsec. org/projects/statistics/ 4
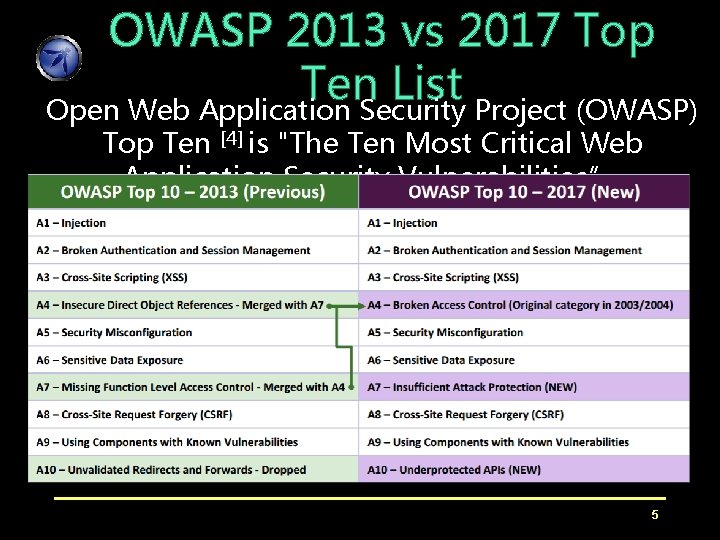
OWASP 2013 vs 2017 Top Ten List Open Web Application Security Project (OWASP) Top Ten [4] is "The Ten Most Critical Web Application Security Vulnerabilities”. 5
![Common defacement techniques[5] 1. 2. 3. 4. 5. SQL Injection Cross Site Scripting Remote Common defacement techniques[5] 1. 2. 3. 4. 5. SQL Injection Cross Site Scripting Remote](http://slidetodoc.com/presentation_image_h2/a4673b7575e5f8adc3047a1feb8a290f/image-6.jpg)
Common defacement techniques[5] 1. 2. 3. 4. 5. SQL Injection Cross Site Scripting Remote File Inclusion Local File Inclusion Exploiting Vulnerability (Brute Force Attack) Source: https: //www. hackingloops. com/6 -ways-to-hack-or-deface-websites-online/ 6
![Web Security and Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 7 Web Security and Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 7](http://slidetodoc.com/presentation_image_h2/a4673b7575e5f8adc3047a1feb8a290f/image-7.jpg)
Web Security and Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 7
![Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 8 Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 8](http://slidetodoc.com/presentation_image_h2/a4673b7575e5f8adc3047a1feb8a290f/image-8.jpg)
Defacement Statistics[6] Source: https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/ 8

Web Defacement in Indonesia 9
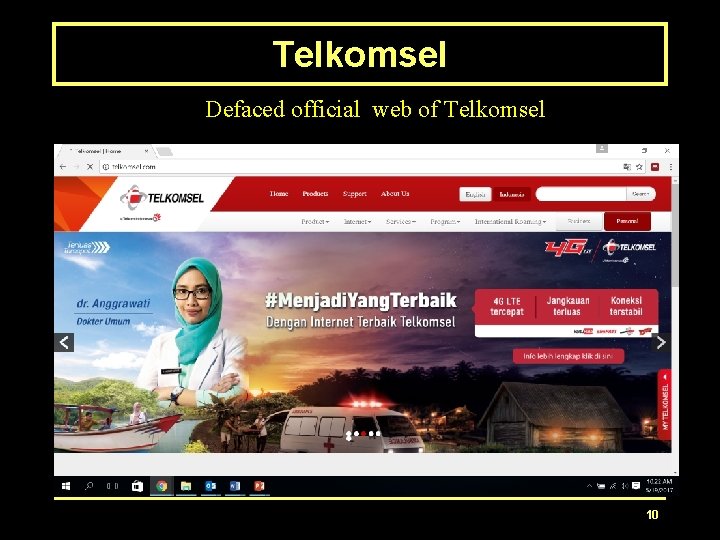
Telkomsel Defaced official web of Telkomsel 10
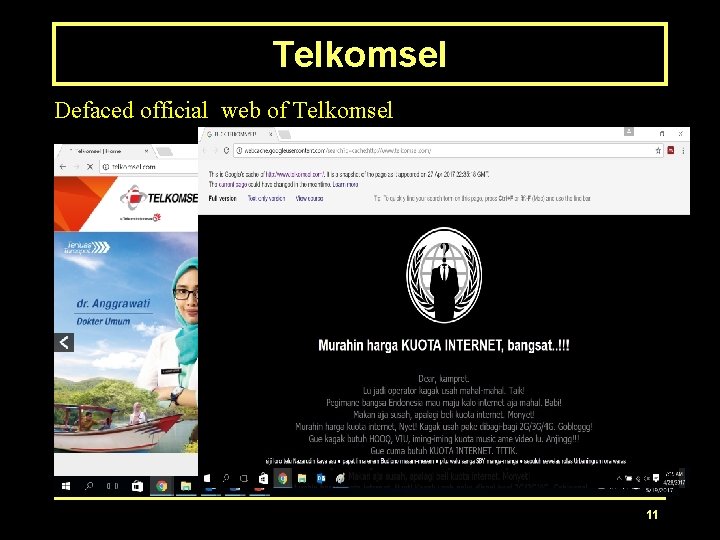
Telkomsel Defaced official web of Telkomsel 11
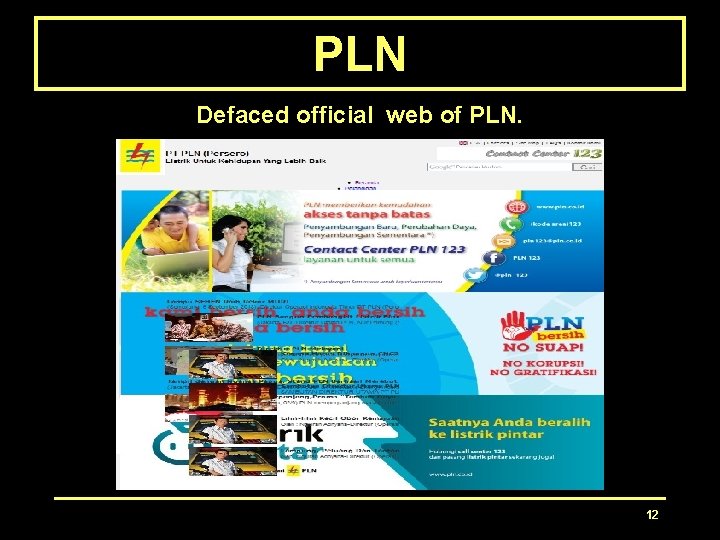
PLN Defaced official web of PLN. 12
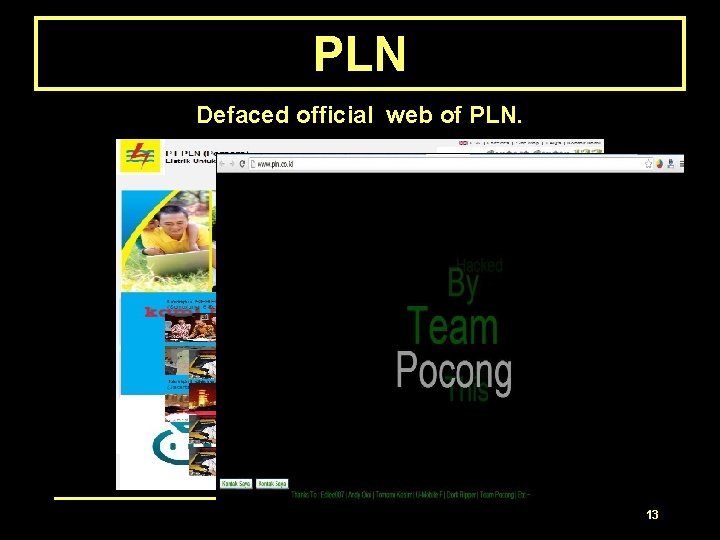
PLN Defaced official web of PLN. 13
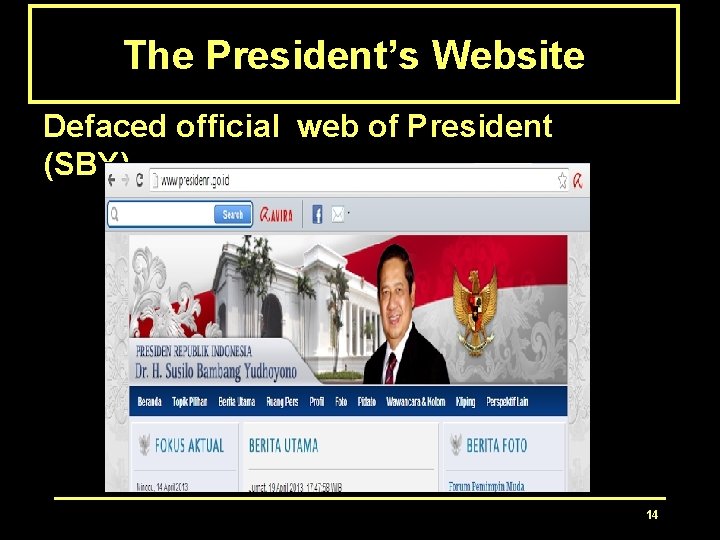
The President’s Website Defaced official web of President (SBY) 14
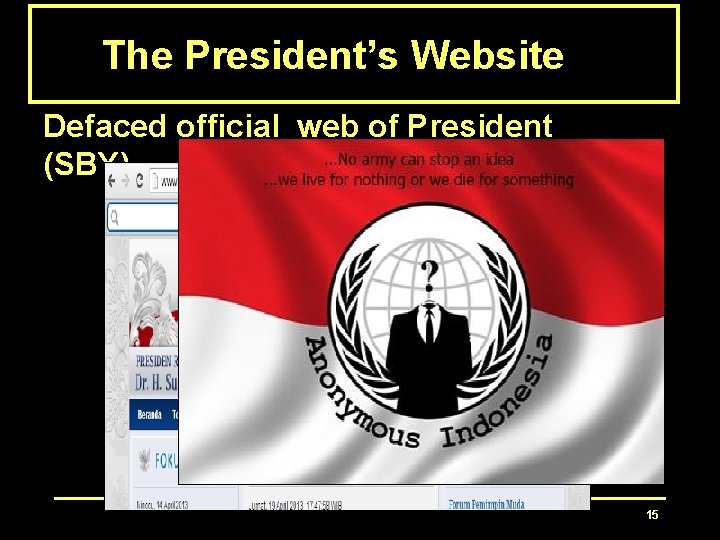
The President’s Website Defaced official web of President (SBY) 15

Web Defacement in Malaysia 16
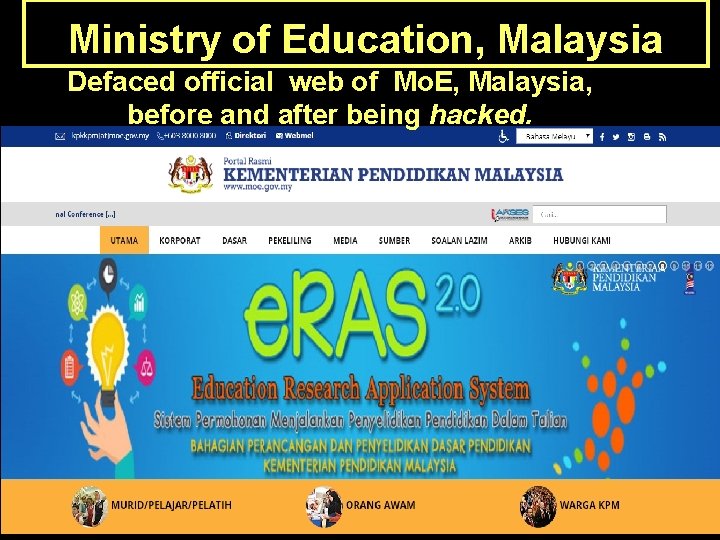
Ministry of Education, Malaysia Defaced official web of Mo. E, Malaysia, Before: Ministry of Education Malaysia - 2014 before and after being hacked.
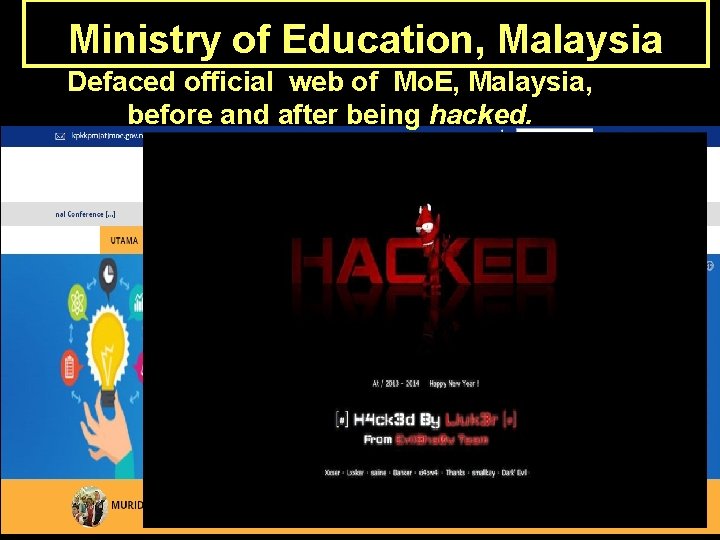
Ministry of Education, Malaysia Defaced official web of Mo. E, Malaysia, Before: Ministry of Education Malaysia - 2014 before and after being hacked.
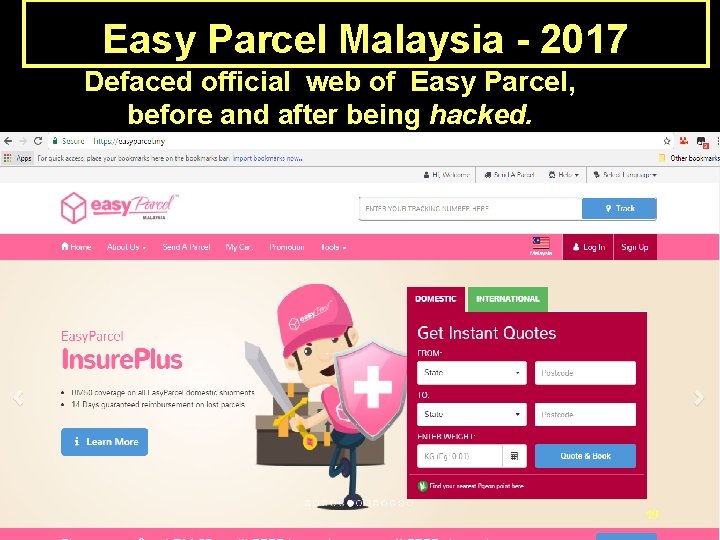
Easy Parcel Malaysia - 2017 Defaced official web of Easy Parcel, before and after being hacked. 19
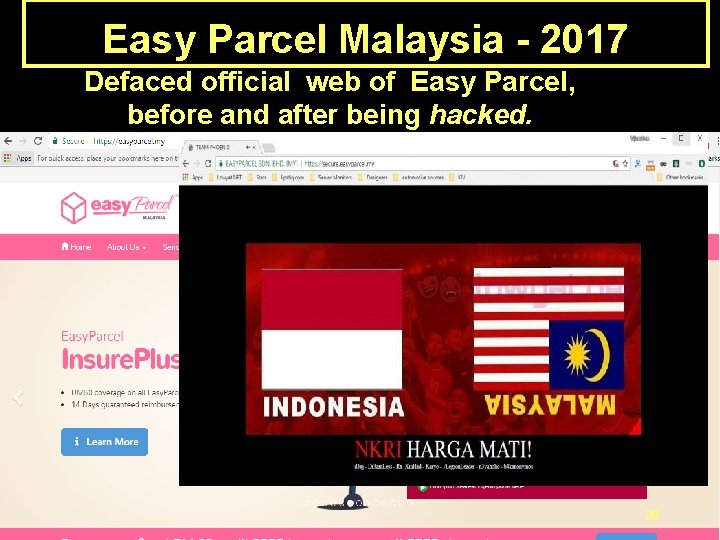
Easy Parcel Malaysia - 2017 Defaced official web of Easy Parcel, before and after being hacked. 20
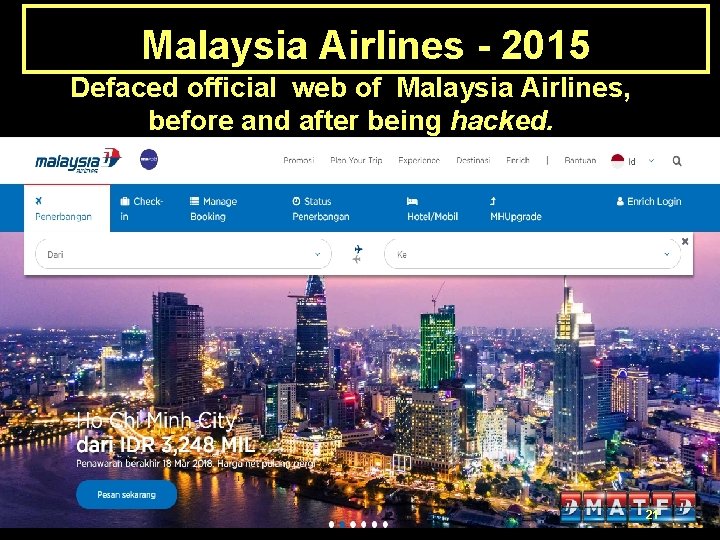
Malaysia Airlines - 2015 Defaced official web of Malaysia Airlines, before and after being hacked. 21
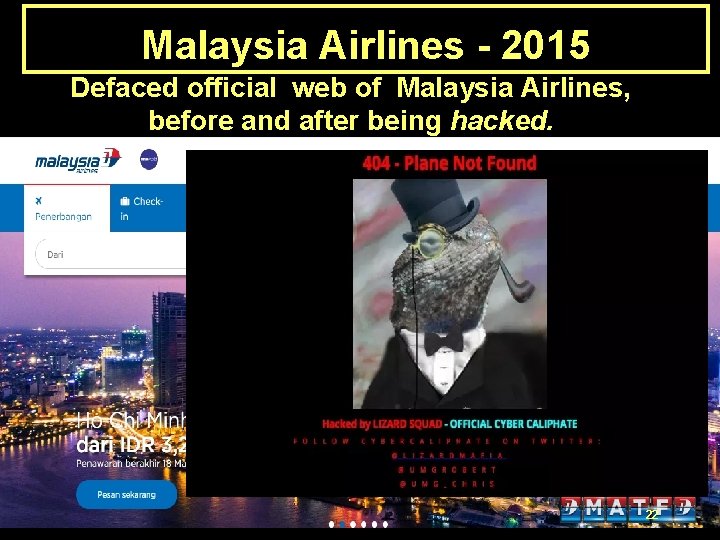
Malaysia Airlines - 2015 Defaced official web of Malaysia Airlines, before and after being hacked. 22

Web Defacement in Singapore 23
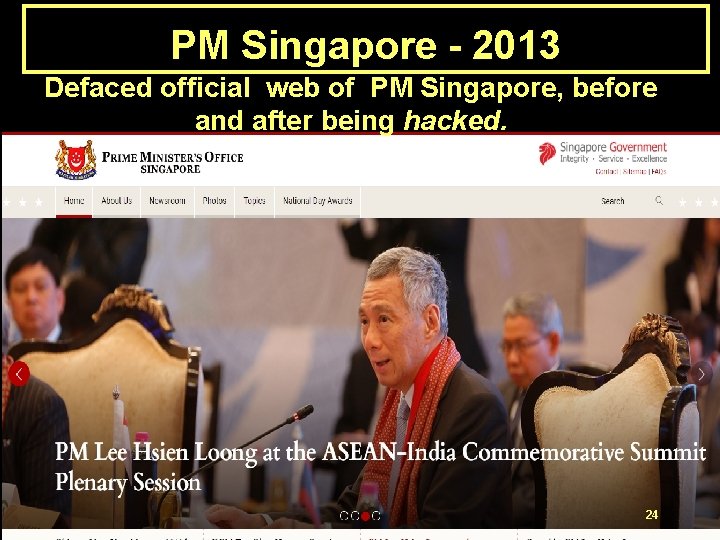
PM Singapore - 2013 Defaced official web of PM Singapore, before and after being hacked. 24
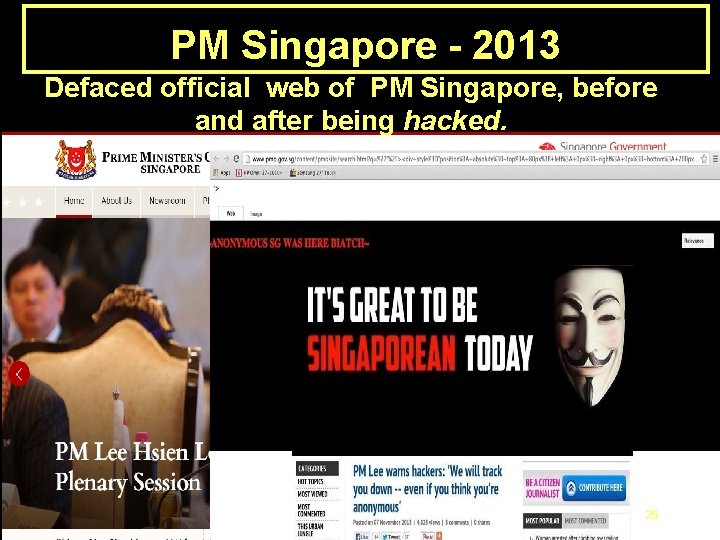
PM Singapore - 2013 Defaced official web of PM Singapore, before and after being hacked. 25

Web Defacement in Thailand 26
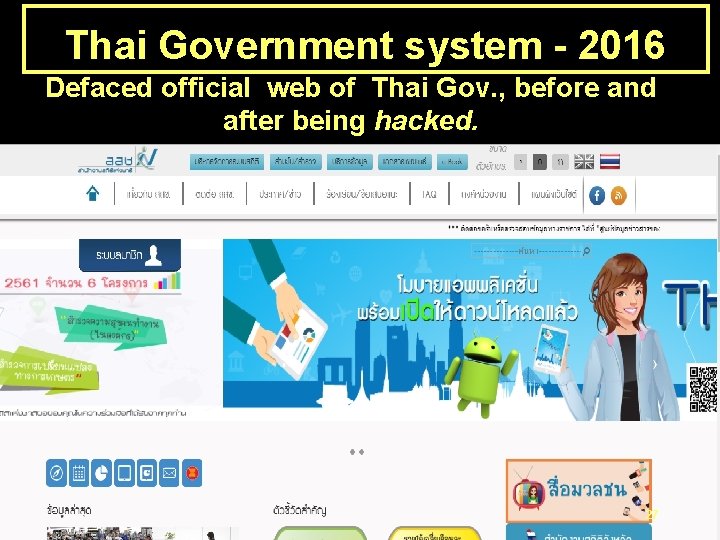
Thai Government system - 2016 Defaced official web of Thai Gov. , before and after being hacked. 27
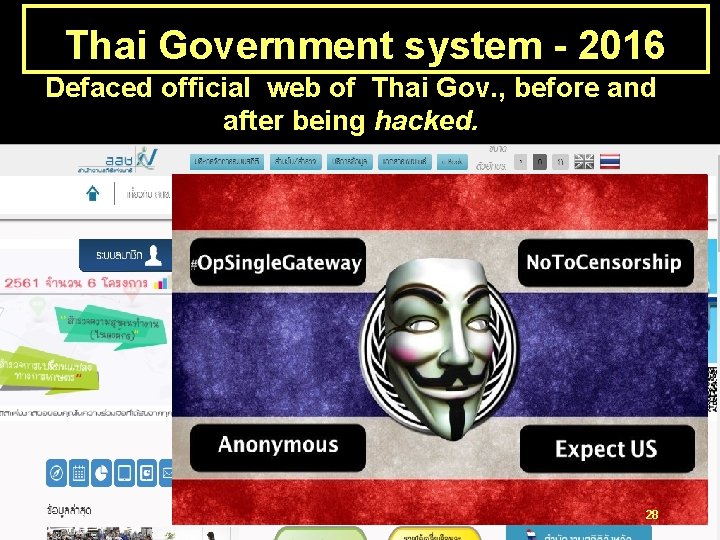
Thai Government system - 2016 Defaced official web of Thai Gov. , before and after being hacked. 28
![Proposed Solution[7] • Combining three security measures: – Deployment of a reverse proxy server Proposed Solution[7] • Combining three security measures: – Deployment of a reverse proxy server](http://slidetodoc.com/presentation_image_h2/a4673b7575e5f8adc3047a1feb8a290f/image-29.jpg)
Proposed Solution[7] • Combining three security measures: – Deployment of a reverse proxy server To avoid external clients to directly access Web servers – Deployment of the Mod. Security in the proxy a) Compare request against sets of rules for detection and prevention of attacks b) Log necessary data of client requests – Visualization of server’s log into graphic To aid in extensive log analysis 29

Reverse proxy server - 1 One of the promising solution is by deploying reverse proxy server with an intrusion and prevention mechanism against web attack especially SQLIA. By deploying reverse proxy server, it also developed server logging process. The problem is the attack sometime comes very quick and from different points, this make the log file large in size and in a short period of time, which is not easy to analyze. 30

Reverse proxy server - 2 • The log text messages is hard for administrator to perform auditing, as the text message could be extremely long and repeated message might occur in certain period of time. • Analyzing logs could be very time-consuming and tiresome. • The visual transformation of data reduces the workload of the administrator, so it can easier to be analyzed and compared without need to read the log line by line. 31
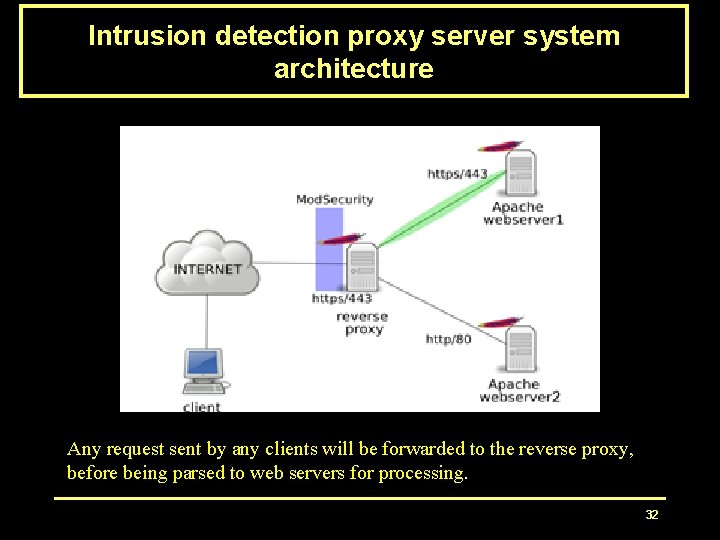
Intrusion detection proxy server system architecture Any request sent by any clients will be forwarded to the reverse proxy, before being parsed to web servers for processing. 32

Thank you … teddy@ieee. org 33

Reference 1. Romagna, M. ; van den Hout, N. J. (October 2017). "Hacktivism and Website Defacement: Motivations, Capabilities and potential Threats". Proceedings of the 27 th Virus Bulletin International Conference: 41– 50. Retrieved 8 October 2017. 2. https: //www. banffcyber. com/blog/web-security-and-defacement-statistics/, March 29, 2017. Last accessed on 22 June 2018. 3. Web Application Security Consortium (WASC), http: //www. webappsec. org/projects/statistics/, Last accessed on 22 June 2018. 4. Open Web Application Security Project (OWASP) Top Ten https: //www. owasp. org/images/7/72/OWASP_Top_10 -2017_%28 en%29. pdf 5. https: //www. hackingloops. com/6 -ways-to-hack-or-deface-websites-online/, Last accessed on 22 June 2018. 6. https: //www. banffcyber. com/knowledge-base/articles/web-security-defacement-statistics/. Last accessed on 22 June 2018. 7. T. Mantoro, N. A Aziz, N. D. M. Yusoff, N. A. A. Talib, “Log Visualization of Intrusion and prevention Reverse Proxy Server Against Web Attacks”, International Conference on Informatics and Creative Multimedia 2013 (ICICM’ 13), Kuala Lumpur, 3 -6 September 2013 34
- Slides: 34