Web Application Security and SQL Injection OWASP Nov

Web Application Security and SQL Injection OWASP Nov 3, 2004 Copyright © 2004 – Durkee Consulting, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. Durkee Consulting www. rd 1. net 1

Ralph Durkee SANS Certified Mentor/Instructor CISSP, GSEC, GCIH Network Security and Software Development Consulting Durkee Consulting www. rd 1. net 2

Paul Cupo Eljan Enterprises Network and Application Security Consulting MS Certified Partner ASP. NET Web Application Development Durkee Consulting www. rd 1. net 3

Agenda Intro and Definition Web Application Risk Overview Threat Categories Overview Top 10 Vulnerabilities Examine some sample SQL Injection vulnerabilities SQL Injection Demonstration by Paul Cupo Durkee Consulting www. rd 1. net 4
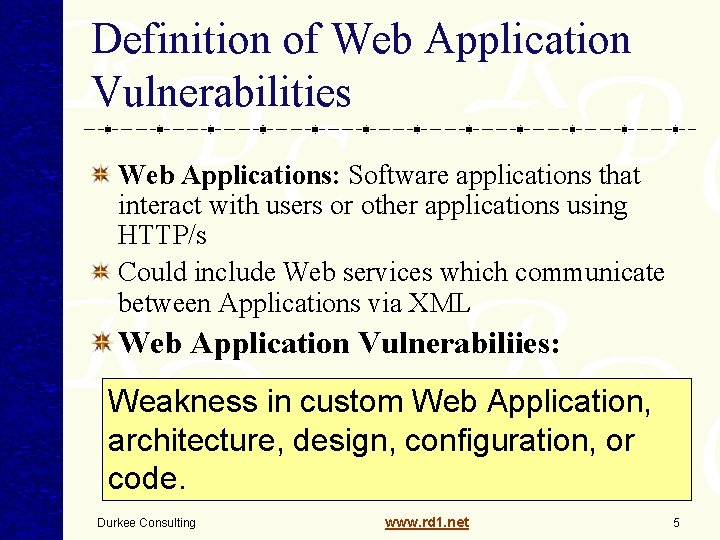
Definition of Web Application Vulnerabilities Web Applications: Software applications that interact with users or other applications using HTTP/s Could include Web services which communicate between Applications via XML Web Application Vulnerabiliies: Weakness in custom Web Application, architecture, design, configuration, or code. Durkee Consulting www. rd 1. net 5
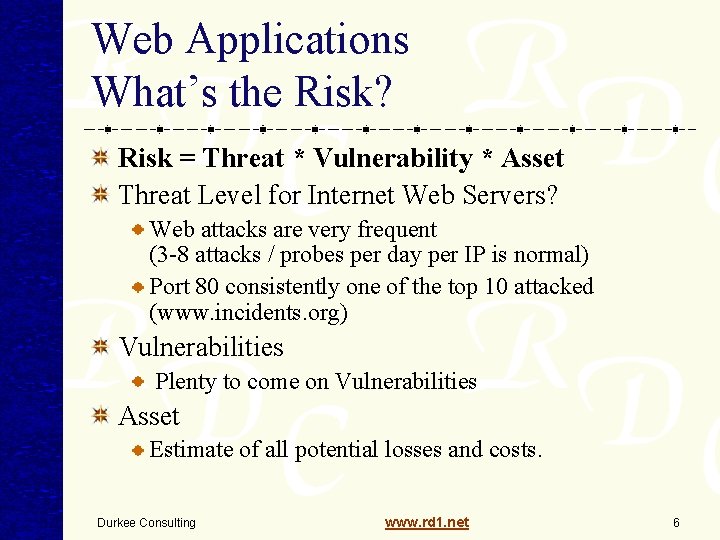
Web Applications What’s the Risk? Risk = Threat * Vulnerability * Asset Threat Level for Internet Web Servers? Web attacks are very frequent (3 -8 attacks / probes per day per IP is normal) Port 80 consistently one of the top 10 attacked (www. incidents. org) Vulnerabilities Plenty to come on Vulnerabilities Asset Estimate of all potential losses and costs. Durkee Consulting www. rd 1. net 6
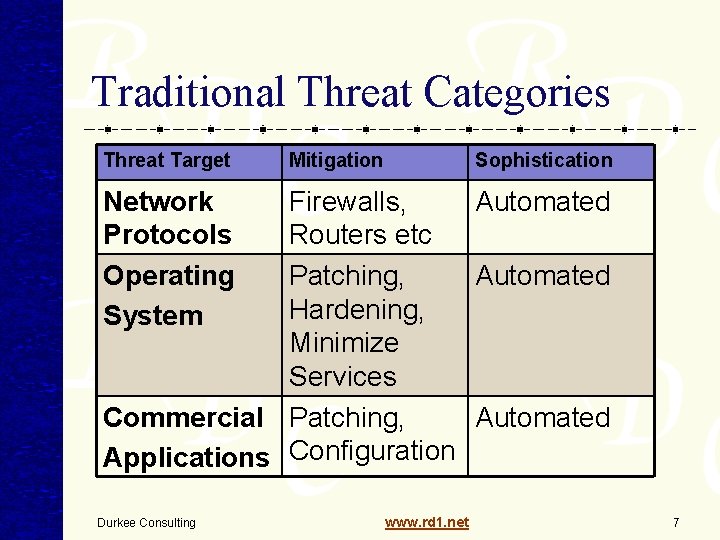
Traditional Threat Categories Threat Target Mitigation Sophistication Network Protocols Operating System Firewalls, Automated Routers etc Patching, Automated Hardening, Minimize Services Commercial Patching, Automated Applications Configuration Durkee Consulting www. rd 1. net 7
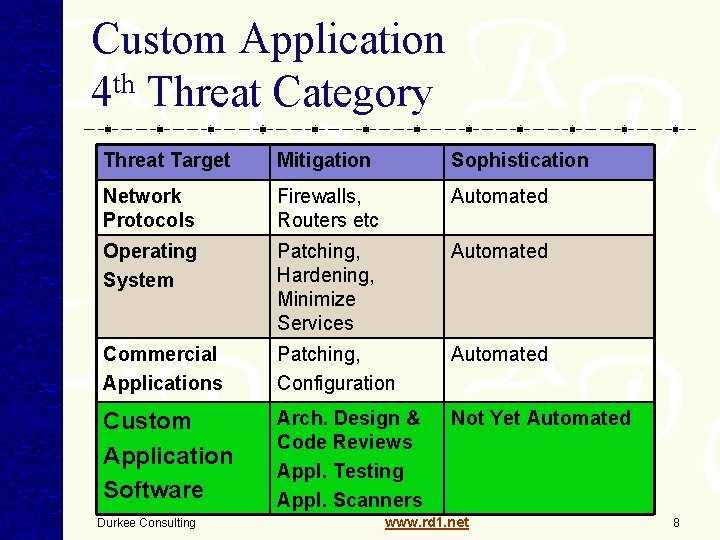
Custom Application 4 th Threat Category Threat Target Mitigation Sophistication Network Protocols Firewalls, Routers etc Automated Operating System Patching, Hardening, Minimize Services Automated Commercial Applications Patching, Configuration Automated Custom Application Software Arch. Design & Code Reviews Appl. Testing Appl. Scanners Not Yet Automated Durkee Consulting www. rd 1. net 8

How Bad Is It? Sanctum reports 97% of 300 Web Applications Audited were Vulnerable Gartner reports 75% of attacks today are at the Application Level If it really is that bad, why aren’t majority of web sites defaced and infected with worms? Durkee Consulting www. rd 1. net 9

If it really is that bad, Why? Why aren’t majority of web sites defaced and infected with worms? Very difficult to write automated worms against custom software. Good news: What can be automated by attackers, can also be discovered by security scanners. Without automation, attack of web applications is semi-manual one-off process. Durkee Consulting www. rd 1. net 10

If it really is that bad, Why? (continued) Technical difficulty eliminates the lowest level script kiddies, but do-able by even intermediate attackers. Difficult to estimate the number of Web Applications already compromised especially if attackers are quietly keeping “ownership” rather than defacing. Durkee Consulting www. rd 1. net 11

OWASP Open Web Application Security Project WWW. OWASP. ORG Dedicated to helping organizations understand improve the security of their web application and web services. Publish Top 10 Web App. Vulnerabilities Open Source Projects (Web. Goat, Web. Scarab) Durkee Consulting www. rd 1. net 12
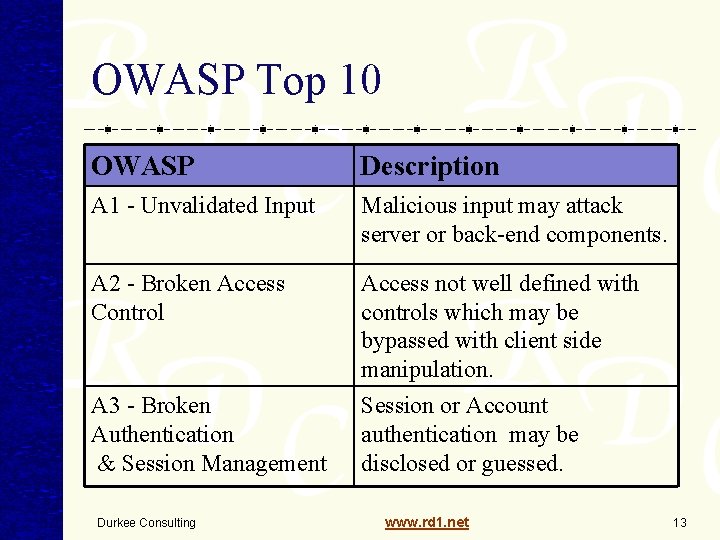
OWASP Top 10 OWASP Description A 1 - Unvalidated Input Malicious input may attack server or back-end components. A 2 - Broken Access Control Access not well defined with controls which may be bypassed with client side manipulation. A 3 - Broken Authentication & Session Management Session or Account authentication may be disclosed or guessed. Durkee Consulting www. rd 1. net 13
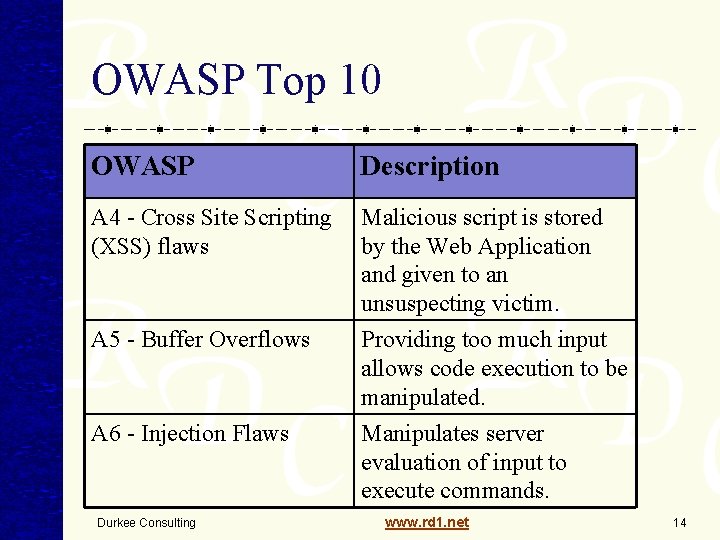
OWASP Top 10 OWASP Description A 4 - Cross Site Scripting (XSS) flaws Malicious script is stored by the Web Application and given to an unsuspecting victim. A 5 - Buffer Overflows Providing too much input allows code execution to be manipulated. Manipulates server evaluation of input to execute commands. A 6 - Injection Flaws Durkee Consulting www. rd 1. net 14
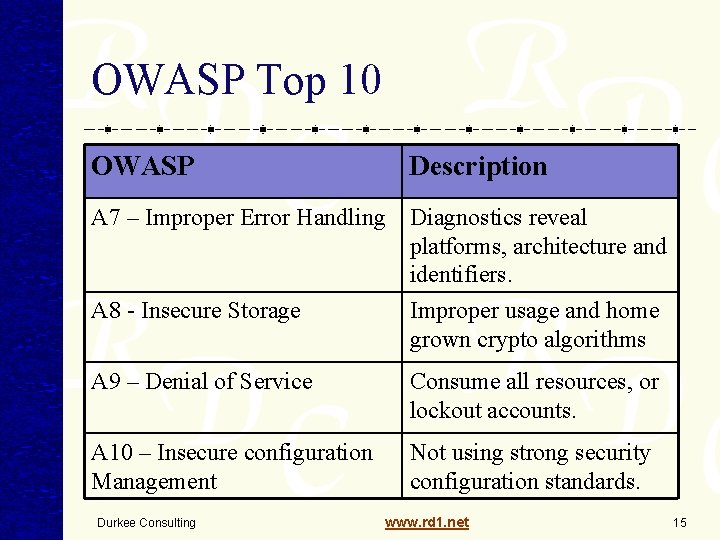
OWASP Top 10 OWASP Description A 7 – Improper Error Handling Diagnostics reveal platforms, architecture and identifiers. A 8 - Insecure Storage Improper usage and home grown crypto algorithms A 9 – Denial of Service Consume all resources, or lockout accounts. A 10 – Insecure configuration Management Not using strong security configuration standards. Durkee Consulting www. rd 1. net 15

Command or SQL injection Input may contain special Meta-characters Some Meta-characters will have significance to the script, OS or database interpreter Meta-characters may be encoded to attempt to circumvent filtering CERT URL http: //www. cert. org/tech_tips/malicious_code_mit igation. html Durkee Consulting www. rd 1. net 16
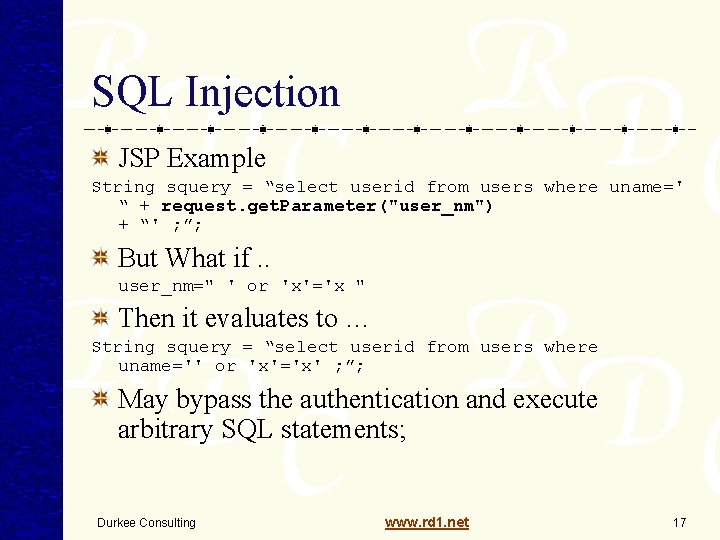
SQL Injection JSP Example String squery = “select userid from users where uname=' “ + request. get. Parameter("user_nm") + “' ; ”; But What if. . user_nm=" ' or 'x'='x " Then it evaluates to … String squery = “select userid from users where uname='' or 'x'='x' ; ”; May bypass the authentication and execute arbitrary SQL statements; Durkee Consulting www. rd 1. net 17

SQL Injection with Encoding What if the application filters out quotes? Same JSP Example String squery = “select userid from users where uname=“ + request. get. Parameter("user_nm”) +“; ”; Now What if. . user_nm="%27 or %27 x%27=%27 x" The %27 is an encoded quote and can may be used to bypass a filter preventing quotes. May still bypass the authentication and execute arbitrary SQL statements Durkee Consulting www. rd 1. net 18

Error Response Information Helpful Debug messages Provides way too much information! Very helpful to potential attacker. Microsoft OLE DB Provider for ODBC Drivers error '80004005' [Microsoft][ODBC Microsoft Access 97 Driver] Can't open database ‘VDPROD'. Durkee Consulting www. rd 1. net 19

Improper Error Handling Possible Denial of Service Java Exceptions and Stack traces Very revealing! java. sql. SQLException: ORA-00600: internal error code, arguments: [ttcgnd-1], [0], [], [], at oracle. jdbc. dbaccess. DBError. throw. Sql. Exception (DBError. java: 169) at oracle. jdbc. ttc 7. TTIoer. process. Error (TTIoer. java: 208) Durkee Consulting www. rd 1. net 20

Inappropriate Information Disclosure Web Responses may provide inappropriate information. Example 1: Helpful web pages that let you know when a valid user id has been guessed. Response for valid user/invalid password should be exactly identical to invalid user. Even subtle differences are sufficient Example 2: Source html comments. Durkee Consulting www. rd 1. net 21
Input Encoding Malicious Input can be encoded in many ways Each software layer and script languages has additional encoding. Attempts to avoid negative filtration. Examples; & & Double encoding: & amp; Triple ? Durkee Consulting www. rd 1. net 22
Where to Validate Client validation -- is helpful but does not provide security Server validation – Everything received from client must be suspect Validate before usage or interpretation. Durkee Consulting www. rd 1. net 23

How to validate Positive filtering preferred rather than Negative Canonical form (decode) where appropriate Encode special characters where appropriate Many types of encoding OWASP has a Java and a ASP filters projects. Durkee Consulting www. rd 1. net 24

Prevention Code Review all DB & System calls Use Parameterized Stored Procedures Avoid simple string concatenation of SQL statements Avoid Scripting and Operating System evaluation of Unvalidated user input Run Web Application without Privileges Durkee Consulting www. rd 1. net 25

Resources www. OWASP. org/ Top Ten Web Application Vulnerabilities OWASP guide Web. Goat News, e-mail lists, articles etc. www. Security. Focus. com/ Vulnerability information News, e-mail lists articles etc. Durkee Consulting www. rd 1. net 26

More Resources How to Build an HTTP Request Validation Engine for Your J 2 EE Application by Jeff Williams http: //www. owasp. org/columns/jwilliam s 2. html Have Your Cake and Eat It Too (ASP. Net validation) by Jeremy Poteet http: //www. owasp. org/columns/jpoteet 2. ht ml Durkee Consulting www. rd 1. net 27
- Slides: 27