Watch IT Who Watches Your IT Guy Noam













- Slides: 34

Watch. IT: Who Watches Your IT Guy? Noam Shalev Technion Idit Keidar Yaron Weinsberg Yosef Moatti Technion IBM Research SOSP 2017, October 31, Shanghai, China. Elad Ben-Yehuda IBM Research

Motivation “God, root, what’s the difference? ” Insider IT can steal valuable data E. g. , Edward Snowden. 2

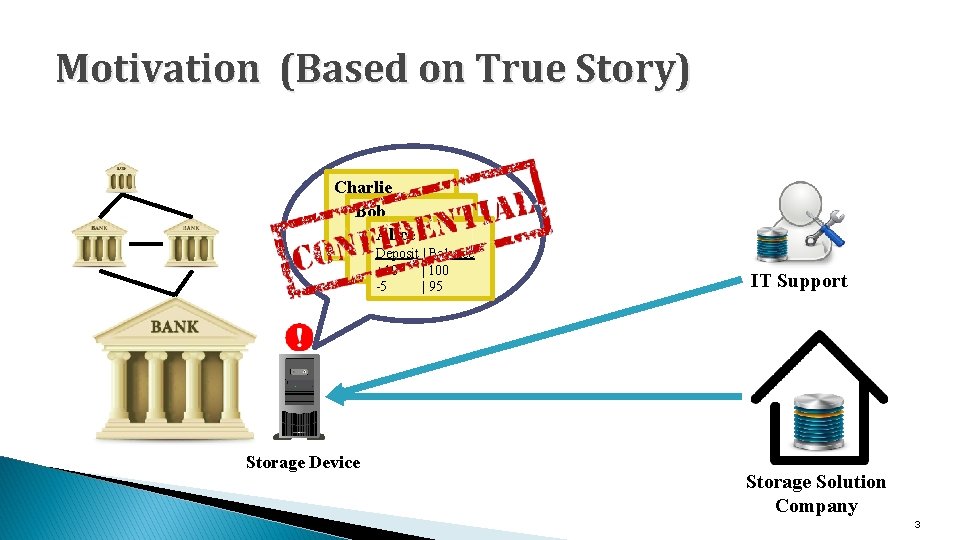
Motivation (Based on True Story) Charlie Bob Alice Deposit | Balance +10 | 100 -5 | 95 Storage Device IT Support Storage Solution Company 3

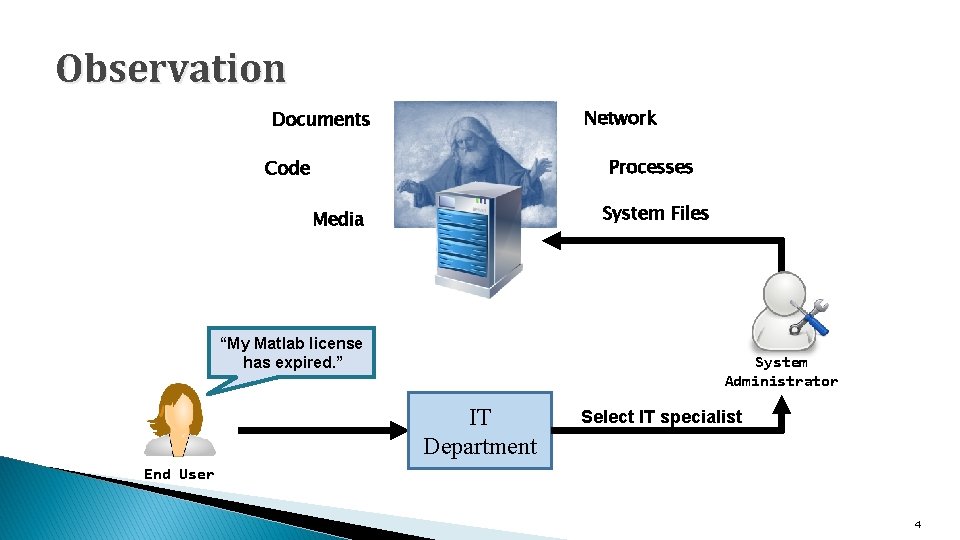
Observation Network Documents Processes Code System Files Media “My Matlab license has expired. ” System Administrator IT Department Select IT specialist End User 4

Observation Network Documents /programs/matlab/ Code Processes System Files Media “My Matlab license has expired. ” System Administrator IT Department Select IT specialist End User 5

Contributions Strategy that constrains IT personnel’s view of the system Watch. IT: POC implementation of our strategy A case study on the IT department of IBM Research, Israel. 6

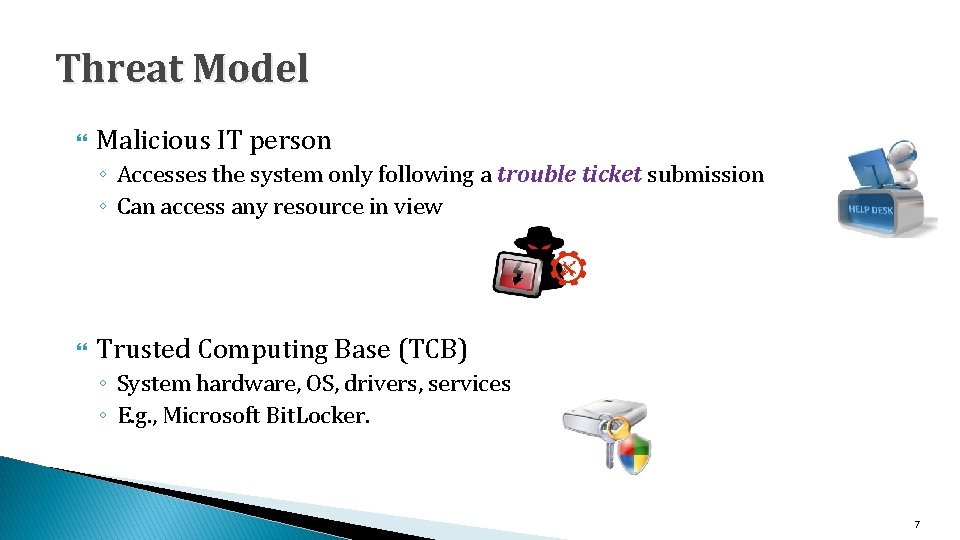
Threat Model Malicious IT person ◦ Accesses the system only following a trouble ticket submission ◦ Can access any resource in view Trusted Computing Base (TCB) ◦ System hardware, OS, drivers, services ◦ E. g. , Microsoft Bit. Locker. 7

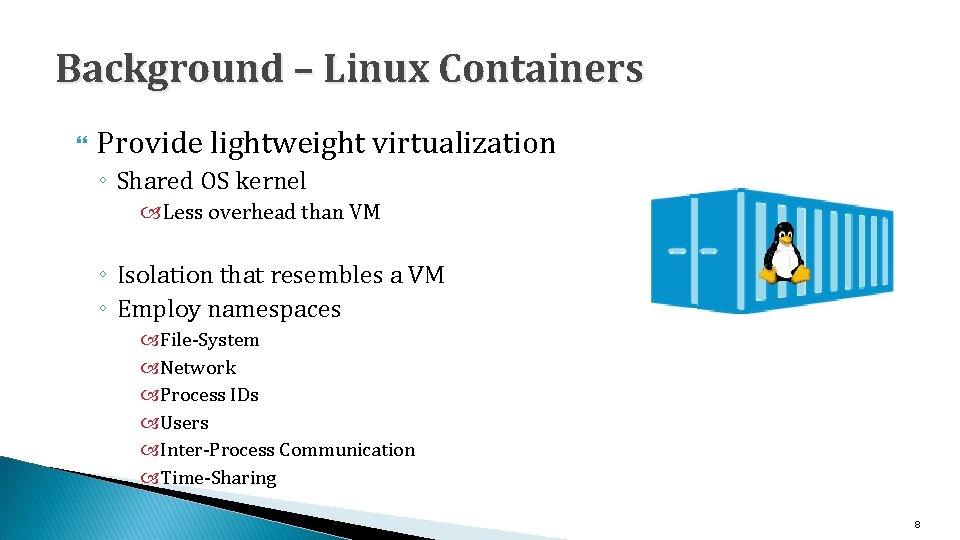
Background – Linux Containers Provide lightweight virtualization ◦ Shared OS kernel Less overhead than VM ◦ Isolation that resembles a VM ◦ Employ namespaces File-System Network Process IDs Users Inter-Process Communication Time-Sharing 8

Background – Linux Containers Provide lightweight virtualization ◦ Shared OS kernel Less overhead then VM Host (lnx-host) etc/ home/ / gcc init Container java etc/ home/ usr/ var/ con. FS/ proc/ progs/ (lnx-cont) bash 77. 139. 180. 15 77. 139. 180. 14 9

Key Idea Exploit the isolation of Linux containers Punch this isolation Create a new container type Confine system administrators in punched containers System Administrator 10

Key Idea Exploit the isolation of Linux containers Key advantages 1. Compartmentalize system administrator 2. Retain superuser privileges System Administrator 11

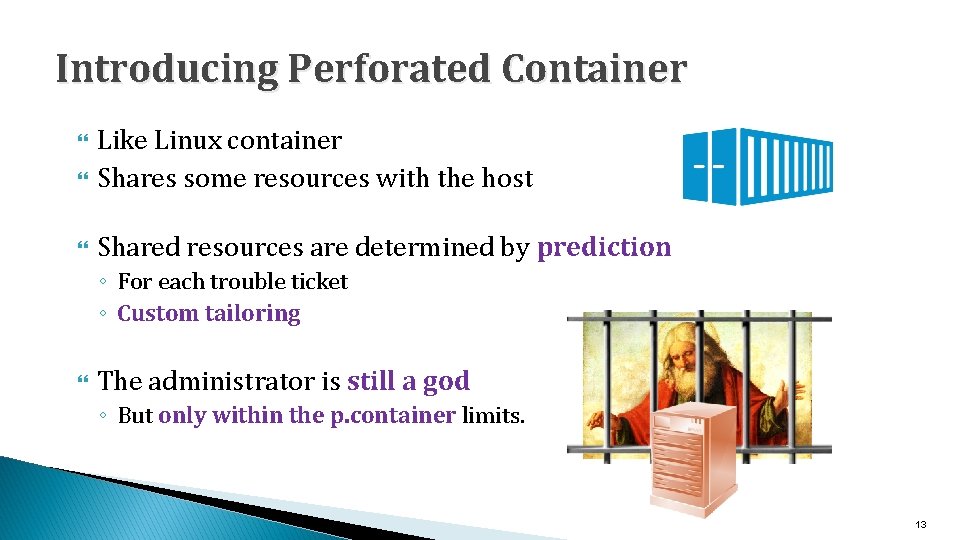
Introducing Perforated Container Like Linux container Shares some resources with the host Example Host / (lnx-host) etc/ home/ usr/ var/ con. FS/ progs/ Traditional Container (lnx-cont) etc/ gcc init java home/ Host bash usr/ var/ proc/ Traditional Container 77. 139. 180. 15 77. 139. 180. 14 / (lnx-host) etc/ home/ usr/ var/ con. FS/ progs/ Perforated Container (lnx-pcont) etc/ gcc init java home/ bash usr/ var/ proc/ 77. 139. 180. 14 Perforated Container 12

Introducing Perforated Container Like Linux container Shares some resources with the host Shared resources are determined by prediction ◦ For each trouble ticket ◦ Custom tailoring The administrator is still a god ◦ But only within the p. container limits. 13

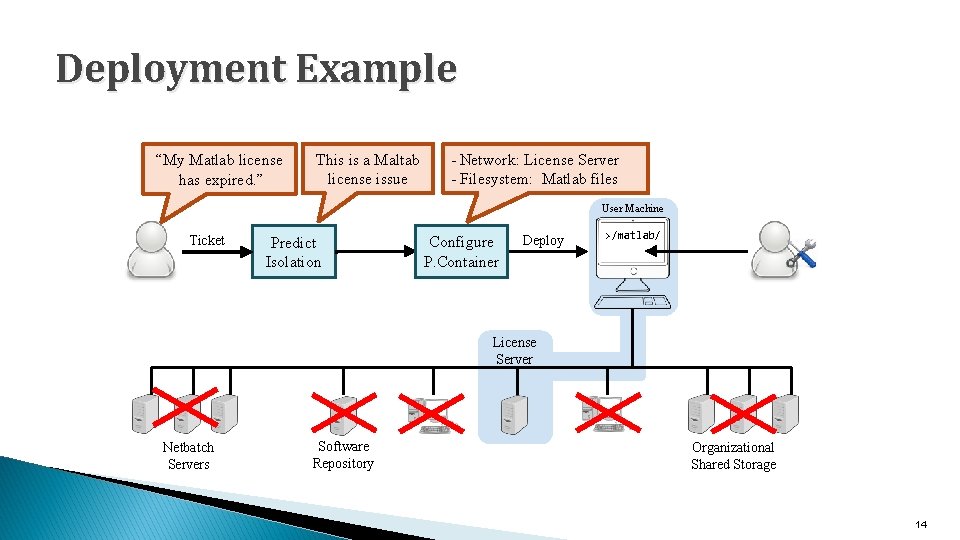
Deployment Example “My Matlab license has expired. ” This is a Maltab license issue - Network: License Server - Filesystem: Matlab files User Machine Ticket Predict Isolation Configure P. Container Deploy >/matlab/ License Server Netbatch Servers Software Repository Organizational Shared Storage 14

Perforated Container as a Sandbox Turn perforated container into a sandbox for administration Monitor the information that streams through the holes Network traffic Filesystem operations How? Network – existing solutions Filesystem – a new filesystem, ITFS. FS 15

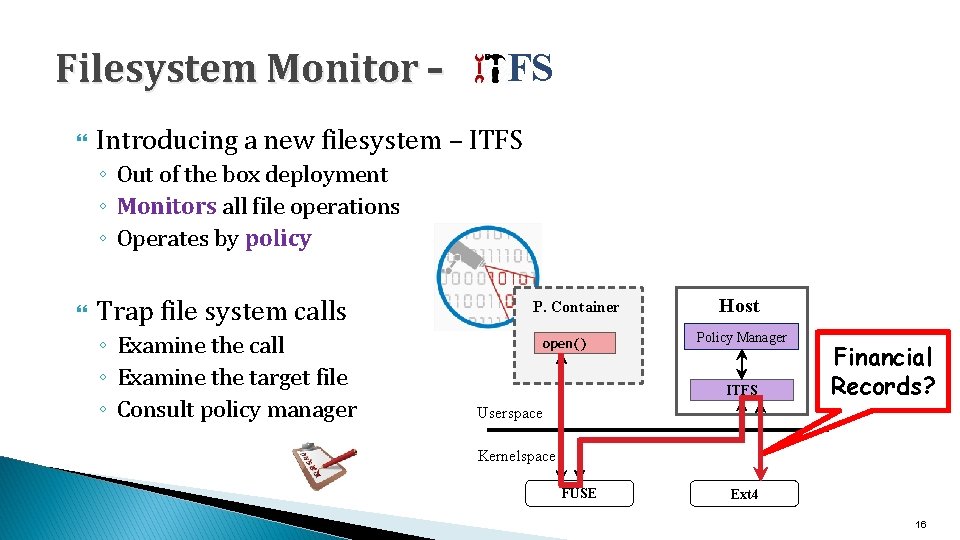
Filesystem Monitor – FS Introducing a new filesystem – ITFS ◦ Out of the box deployment ◦ Monitors all file operations ◦ Operates by policy Trap file system calls ◦ Examine the call ◦ Examine the target file ◦ Consult policy manager P. Container open() Host Policy Manager ITFS Financial Records? Userspace Kernelspace FUSE Ext 4 16

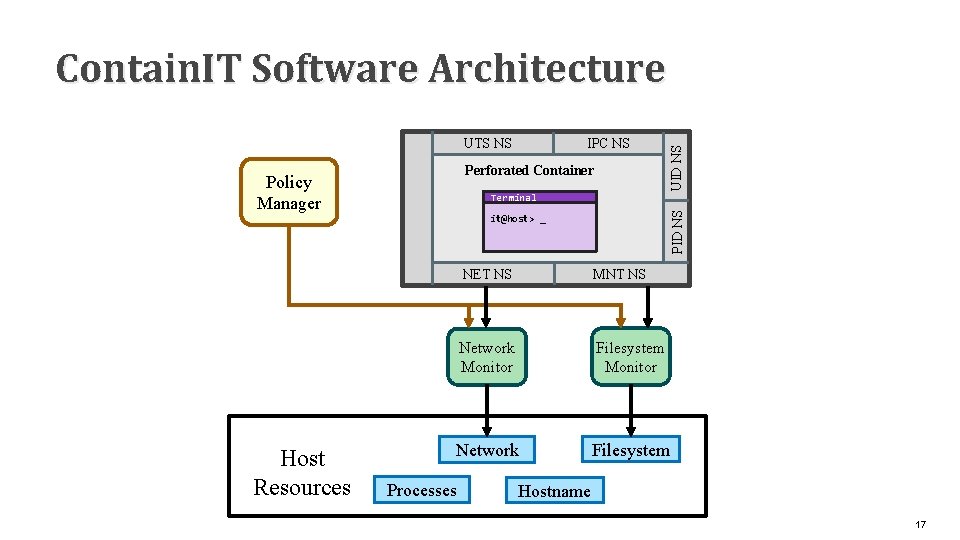
IPC NS UTS NS Perforated Container Policy Manager Host Resources PID NS Terminal UID NS Contain. IT Software Architecture it@host> _ NET NS MNT NS Network Monitor Filesystem Monitor Network Filesystem Processes Hostname 17

One More Thing… What if the perforated container limits are too restrictive? What if the prediction is wrong? 18

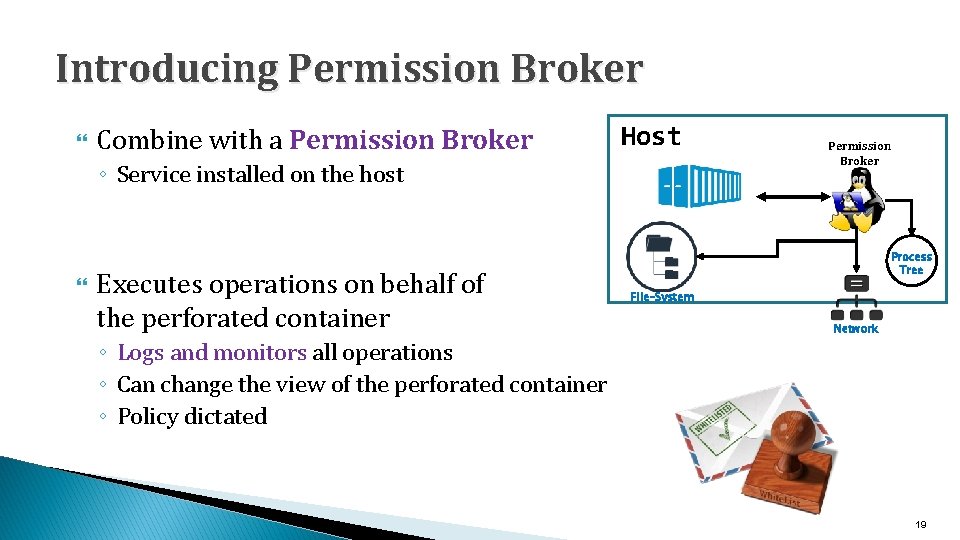
Introducing Permission Broker Combine with a Permission Broker Host ◦ Service installed on the host Executes operations on behalf of the perforated container ◦ Logs and monitors all operations ◦ Can change the view of the perforated container ◦ Policy dictated Permission Broker Process Tree File-System Network 19

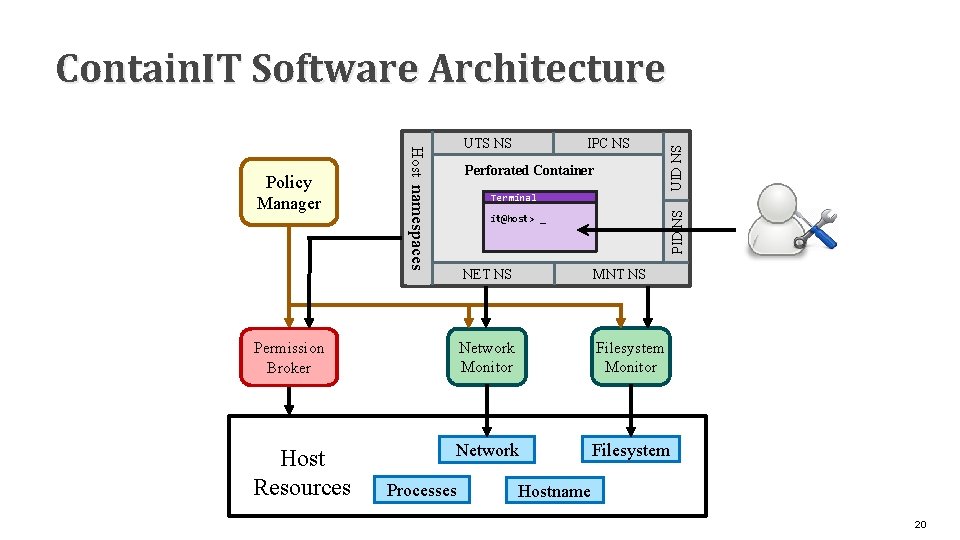
Host namespaces Perforated Container Terminal PID NS Policy Manager IPC NS UTS NS UID NS Contain. IT Software Architecture it@host> _ NET NS MNT NS Permission Broker Network Monitor Filesystem Monitor Host Resources Network Filesystem Processes Hostname 20

See the Paper For… Threat analysis ◦ Security measures ◦ Circumventing Watch. IT Exclusion (XCL) namespace Filesystem rerouting & evaluation On-line filesystem view adjustments Real world deployment implications 21

Case Study & Evaluation 22

Environment IT department of IBM Research, Israel ◦ ◦ ~64, 000 user reported trouble tickets ~16, 000 Linux related Free text Unclassified Goal: prove Watch. IT feasibility ◦ Effective isolation ◦ Low usage rate of permission broker 23

Methodology Three stages: 1. Database analysis § Based on previously reported tickets (~7 years) 2. Custom Tailoring 3. Test period § Based on newly arrived tickets (~3 months) 24

Database Analysis–Stage 1 Clustering using ML for topic extraction ◦ Latent Dirichlet Allocation (LDA) [Blei et al. ] Preprocessing ◦ ◦ Word stemming Stop word removal Non-informative word removal Obfuscation of addresses, server & project names. 25

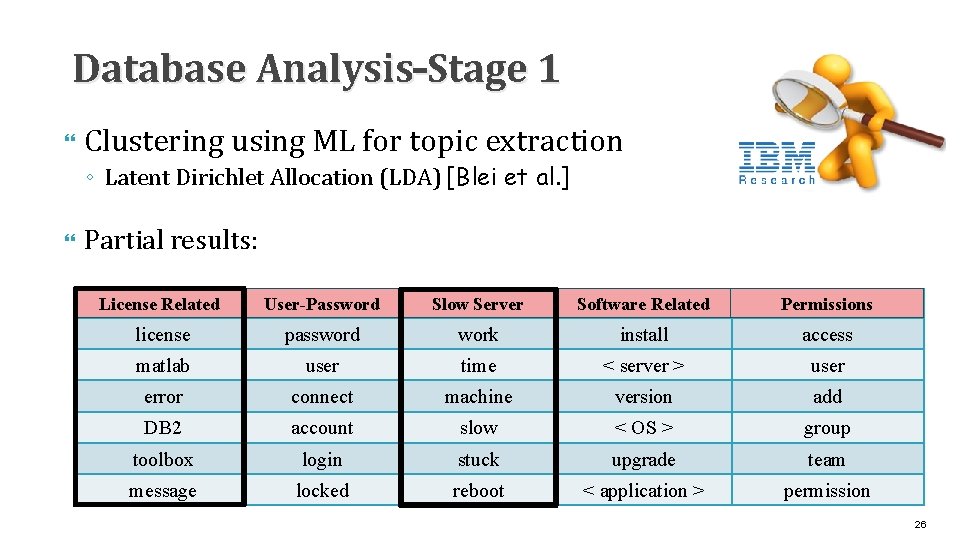
Database Analysis–Stage 1 Clustering using ML for topic extraction ◦ Latent Dirichlet Allocation (LDA) [Blei et al. ] Partial results: Topic. Related T-1 License User-Password Topic T-2 Topic T-5 Slow Server Topic. Related T-6 Software Topic T-10 Permissions license password work install access matlab user time < server > user error connect machine version add DB 2 account slow < OS > group toolbox login stuck upgrade team message locked reboot < application > permission 26

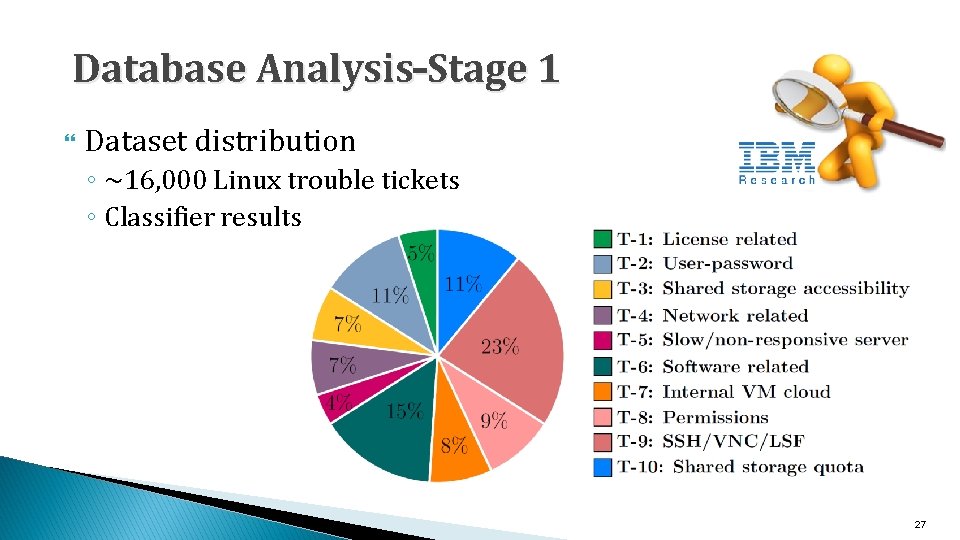
Database Analysis–Stage 1 Dataset distribution ◦ ~16, 000 Linux trouble tickets ◦ Classifier results 27

Custom Tailoring–Stage 2 File System Topic View Process View Root Directory Home Directory Network /etc/ License Server Target Machine License Slow Server VNC 28

Stage 3 – Test Period Three month test period (Dec 16’ to Feb 17’) ◦ ~400 tickets For each ticket ◦ Classify ◦ Record the used permissions ◦ Check whether the permission broker was needed 29

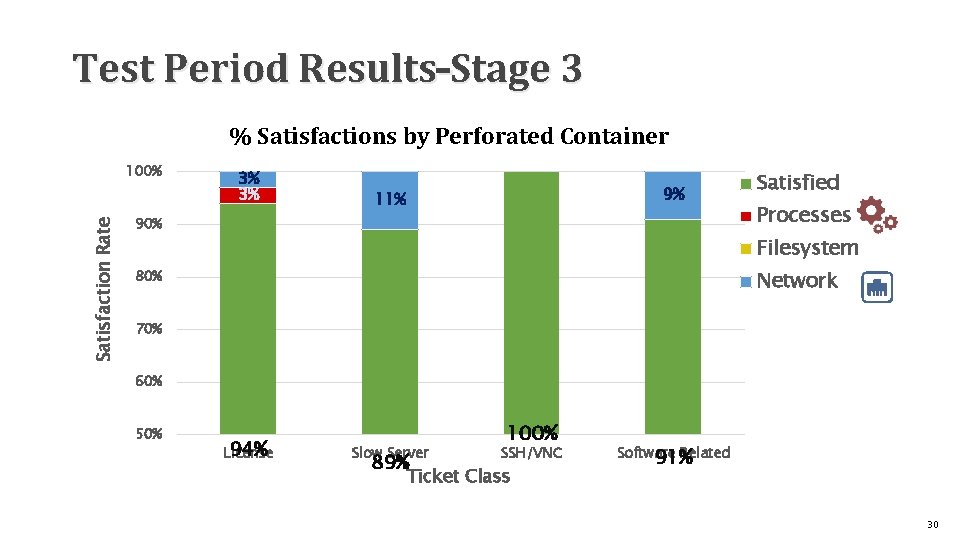
Test Period Results–Stage 3 % Satisfactions by Perforated Container Satisfaction Rate 100% 3% 3% 9% 11% 90% Satisfied Processes Filesystem Network 80% 70% 60% 50% 94% License Slow Server 89% 100% SSH/VNC Ticket Class Software Related 91% 30

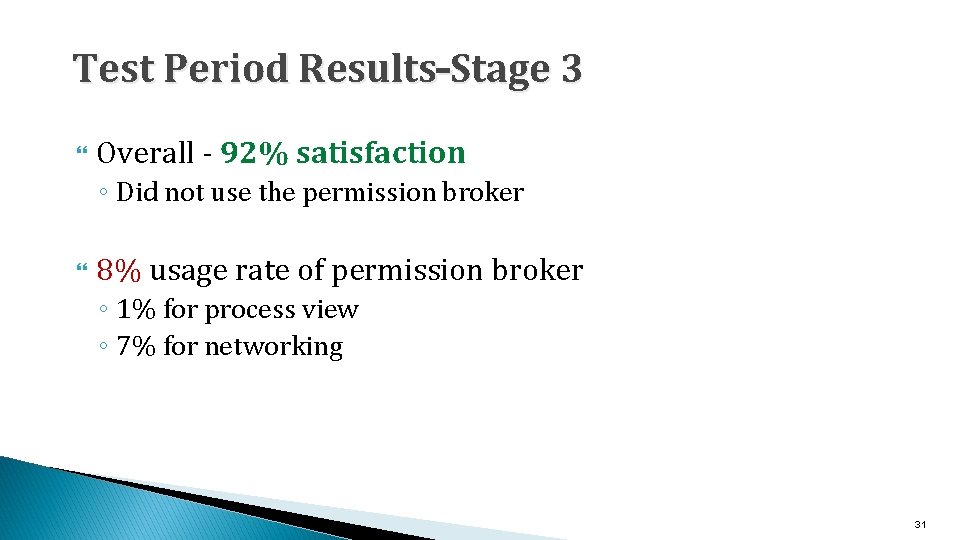
Test Period Results–Stage 3 Overall - 92% satisfaction ◦ Did not use the permission broker 8% usage rate of permission broker ◦ 1% for process view ◦ 7% for networking 31

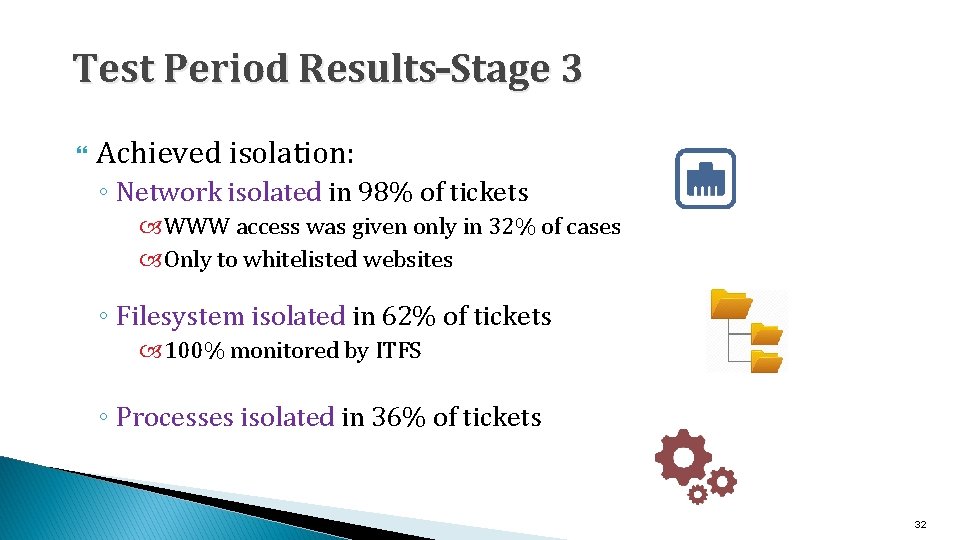
Test Period Results–Stage 3 Achieved isolation: ◦ Network isolated in 98% of tickets WWW access was given only in 32% of cases Only to whitelisted websites ◦ Filesystem isolated in 62% of tickets 100% monitored by ITFS ◦ Processes isolated in 36% of tickets 32

Conclusions We introduce the perforated container abstraction Sandbox for administration tasks Case study shows that Watch. IT approach is feasible Watch. IT raises the bar for a malicious IT insider 33

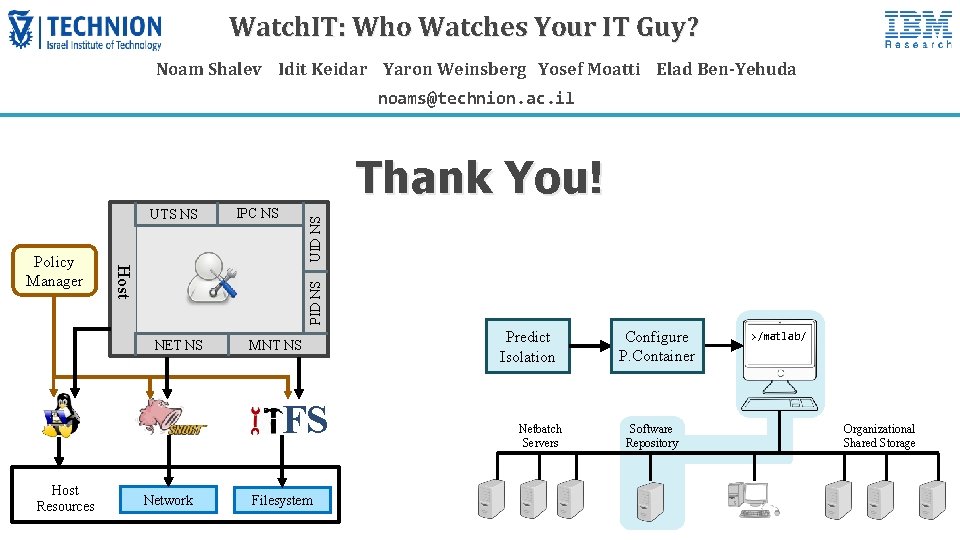
Watch. IT: Who Watches Your IT Guy? Noam Shalev Idit Keidar Yaron Weinsberg Yosef Moatti Elad Ben-Yehuda noams@technion. ac. il Thank You! PID NS Host Policy Manager IPC NS UID NS UTS NS NET NS MNT NS FS Host Resources Network Filesystem Predict Isolation Netbatch Servers Configure P. Container Software Repository >/matlab/ Organizational Shared Storage
 Which witch watches which watch
Which witch watches which watch Suppose your email program watches
Suppose your email program watches Taktik good guy bad guy
Taktik good guy bad guy The xbox came out before the wii fact or opinion
The xbox came out before the wii fact or opinion With up so floating many bells down
With up so floating many bells down Psalm 121 6
Psalm 121 6 John watches his grandmother bake bread
John watches his grandmother bake bread Afi 36-2903 watches
Afi 36-2903 watches Watching your grandmother bake bread
Watching your grandmother bake bread Heavenly father watches over me
Heavenly father watches over me Two witches were watching two watches
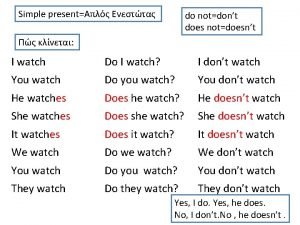
Two witches were watching two watches Simple present tense in sentence
Simple present tense in sentence Present simple watch
Present simple watch Noam brown
Noam brown Noam chomsky cryptocurrency
Noam chomsky cryptocurrency Noam goldberg
Noam goldberg Noam goldberg
Noam goldberg Noam tractinsky
Noam tractinsky Noam chomsky child development
Noam chomsky child development Context free grammar to chomsky normal form
Context free grammar to chomsky normal form Chomsky normal form 설명
Chomsky normal form 설명 Elikviz
Elikviz Noam čomski
Noam čomski Unlike b.f. skinner, noam chomsky believes that children
Unlike b.f. skinner, noam chomsky believes that children Noam rathaus
Noam rathaus Give us your hungry your tired your poor
Give us your hungry your tired your poor Watch your tone boy
Watch your tone boy Tone vs mood venn diagram
Tone vs mood venn diagram In your notebook write questions and short answers
In your notebook write questions and short answers Personal leadership philosophy sample
Personal leadership philosophy sample Two-step molar conversions worksheet answers
Two-step molar conversions worksheet answers Guy hewson
Guy hewson Was it a dream guy de maupassant
Was it a dream guy de maupassant La vendetta guy de maupassant
La vendetta guy de maupassant Guy derrick crane
Guy derrick crane