W a i t Loading Loading Loading Design










- Slides: 21
W a i t


Loading

Loading

Loading

Design is G. T. E.

What is it? Any kind of fake software that appears to help protect your computer’s security.

What is the purpose of scareware ? Frighten people into buying something (anti-virus software) Scareware can refer to many different types of products it is typically associated with antivirus scams Suggest that your computer is either at risk or already infected. The scareware then offers the solution – a highly overpriced piece of software Offers to right all the wrongs that have been identified on your system

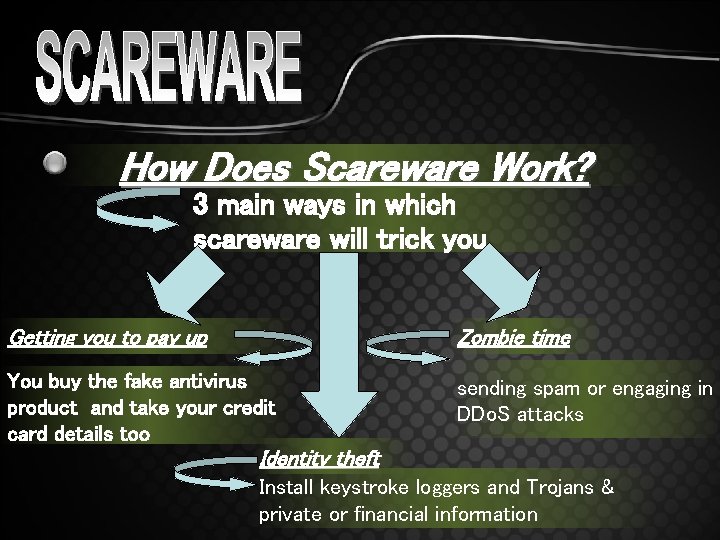
How Does Scareware Work? 3 main ways in which scareware will trick you Getting you to pay up Zombie time You buy the fake antivirus product and take your credit card details too sending spam or engaging in DDo. S attacks Identity theft Install keystroke loggers and Trojans & private or financial information

How to prevent? Close Your Browser Change Your Surfing Habits Be wary of email attachments Regular Checks Always read carefully Pop-up blocker

What is it? Short for "malicious software includes viruses and spyware designed to infiltrate a computer system

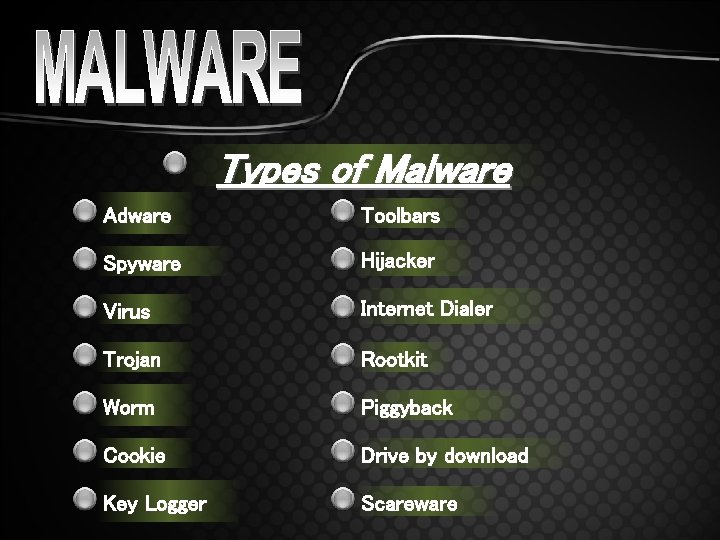
Types of Malware Adware Toolbars Spyware Hijacker Virus Internet Dialer Trojan Rootkit Worm Piggyback Cookie Drive by download Key Logger Scareware

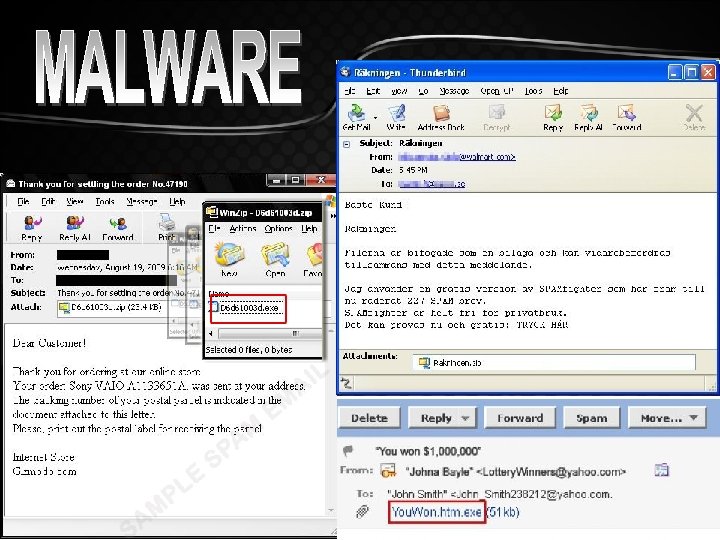
Malware sent via e-mail attachment Most common way to become infected with a virus. Sender will not know their e-mails are infected. File path is. exe


Malware sent via popup ads unexpected pop-up messages Asks you to install software or click it Offers great deal or free for everything


Effects of Malware Pop-up ads Browser hijack Unknown icons Slow system Infected E-mail Unusual things Installs software Collects password / information System hijack Leaves tracking cookies Change setting Alters browser Monitoring Rude message

How to prevent? Read carefully Avoid rogue websites Avoid free utilities Avoid using peer 2 peer Avoid Warez up-to-date as possible common sense Close pop-up ad with ctrl+w


http: //www. ait. brooklyn. cuny. edu/litrack/pdfs/ http: //arstechnica. com/security/news/2004/11/malware. ars http: //www. absoluteastronomy. com/topics/Pop-up_ad http: //www. onguardonline. gov/topics/malware. aspx http: //www. scientis. com/Security/Malware_Spyware. html http: //blogs. techrepublic. com/security/? p=1814 http: //www. spamlaws. com/how-scareware-works. html http: //www. isc. sans. org/diary. html? storyid=6529 http: //www. scambusters. org/protectionscam. html

BY. Any Kyung Question Rokfor. Han ? Thank you listen my presentation. Have a nice day!