Vulnerability An Ontological Analysis Eric Little Ph D

Vulnerability: An Ontological Analysis Eric Little, Ph. D Director, Center for Ontology and Interdisciplinary Studies D’Youville College Buffalo, NY little@dyc. edu eglittle@eng. buffalo. edu

Ontology for the Intel Community • Will include real world data (realism) • Will also include perspectival (e. g. , sensor) data (epistemic layering) • Knowledge/data is: incomplete, possibly unreliable, conflicting, fallacious, etc. • Involves many types of sub-ontologies: e. g. , physical ontologies, social ontologies, economic ontologies, etc. However … We can use the ontology to aid in the epistemological processing of a domain
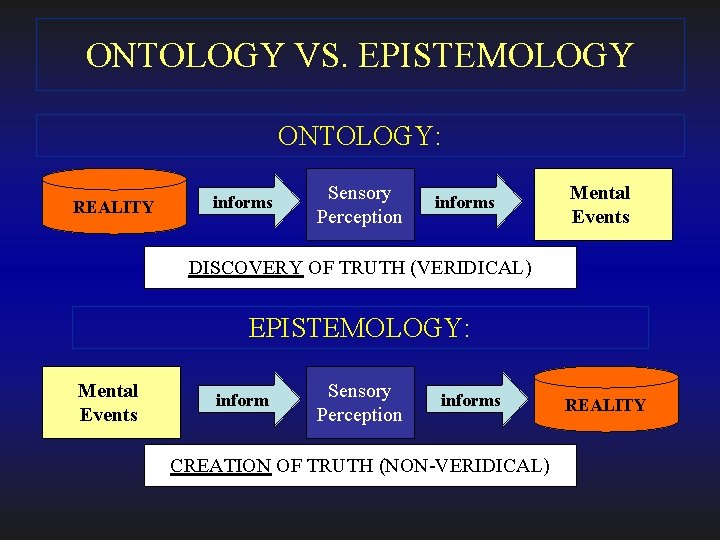
ONTOLOGY VS. EPISTEMOLOGY ONTOLOGY: REALITY informs Sensory Perception informs Mental Events DISCOVERY OF TRUTH (VERIDICAL) EPISTEMOLOGY: Mental Events inform Sensory Perception informs CREATION OF TRUTH (NON-VERIDICAL) REALITY

The Structure of an Ontology • Upper-Level (Formal): – Most general categories of existence (e. g. , existent item, spatial region, dependent part). – This Level of the ontology is rationally driven, meaning it is the product of philosophical reasoning. – Relies on a sound metaphysical description of the world (e. g. , realism).

The Structure of an Ontology • Domain – Specific Level: – Contains categories that are specific to a particular domain of interest (disaster, military/defense, medicine). – This level of the ontology is empirically driven, meaning it is produced by gathering expert knowledge about a given domain of interest. – The expert knowledge is used to create a consistent and comprehensive lexicon of terms.

The Lexical Task Lexicons need to be constructed to capture relevant data. -This is a manual task (not data/text mining task) -The lexicon will contain all the objects, attributes/properties, and relations representative of a given domain. -Realism + Perspectivalism is key. -Will serve as the basis of the ontology’s structure.

Example of Free Text Data Though they can var widely in shape and form, IEDs share a common set of components and consist of the following: • An initiation system or fuze; • Explosive fill; • A detonator; • A power supply for the detonator; and • A container. Improvised devices are characterized by varying employment techniques. • Coupling is a method of linking one mine or explosive device to another, usually with detonating cord. When the first device is detonated, it also detonates the linked explosive. This technique is often used to defeat countermine equipment, such as mine rollers • Rolling. The roller will pass over the initial, unfuzed device and set off the second fuzed device. This in turn detonates the overpassed device underneath the clearing vehicle. When the linked devices are directional fragmentation mines, they can create a large, lethal engagement area. • Boosting. Buried mines, UXOs, or other explosive devices are stacked on top of one another. The device buried deepest from the surface is fuzed. Fuzing only the deepest ordnance helps mask noand low-metal explosive hazards placed near the surface. This reduces the probability of detection by metal detectors, and it increases the force of the blast. • Sensitizing antitank (AT) mines. On some nonmetallic AT mines, the pressure plate is cracked and the spring is removed to reduce the pressure required to initiate the mine. Similarly, the pressure plate can be removed from metallic AT mines to create the same effect. A pressurefuzed AP mine can be placed on the top of an AT mine, thus creating a very large AP mine as an alternative method. • Daisy chaining. AP mines may be used in daisy chains linked with other explosive hazards. Enemy forces may link the mines together with trip wire or detonating cord. When the initial mine is detonated, the other mines may detonate. This may also create large, lethal engagement areas.
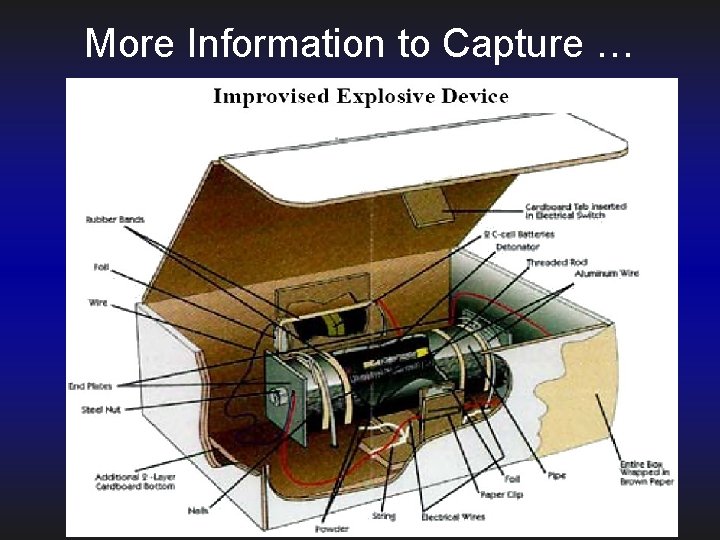
More Information to Capture …
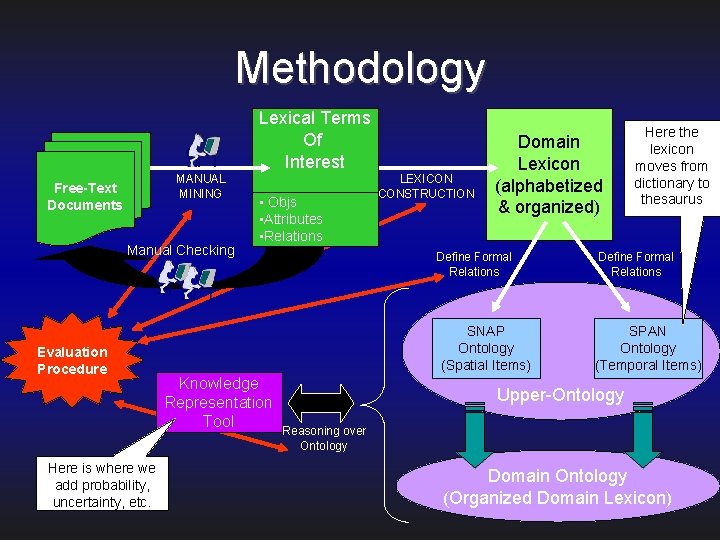
Methodology Lexical Terms Of Interest MANUAL MINING Free-Text Documents Manual Checking Evaluation Procedure Here is where we add probability, uncertainty, etc. • Objs • Attributes • Relations LEXICON CONSTRUCTION Domain Lexicon (alphabetized & organized) Define Formal Relations SNAP Ontology (Spatial Items) Knowledge Representation Tool Here the lexicon moves from dictionary to thesaurus Define Formal Relations SPAN Ontology (Temporal Items) Upper-Ontology Reasoning over Ontology Domain Ontology (Organized Domain Lexicon)

Threat Ontology (Thr. O)

Goals: • Understand what ‘threats’ and ‘vulnerabilities’ are ontologically. • Distinguish between different types of threat types (conventional vs. asymmetric). • Help decision-makers formulate plans of actions based upon an increased understanding of both formal and informal data structures. • Define ‘Centers of Gravity’ for each kind of item. – Defining these can aid in the management of a threat situation.

Situation & Threat Assessment (Higher-Level Fusion) Processes of reasoning about kinds of objects and events of interest, relations between them, their aggregates at different levels of granularity, and their behavior within a specific context. Calls formally structured context-dependent information about reality capable of capturing various sorts of threat entities and the plethora of relations between them. Formal Ontology of threat

What kinds of ontologies are needed for Threat Assessment? • Low-level fusion can be done (to a large degree) using existing tools such as OWL, Protégé, DAML - Oil, etc. • However, higher-level fusion processing is concerned with providing comprehensive and consistent descriptions of highly complex world states. • Hence we need a more “industrial strength” (cf. Musen) approach than is provided by many current fusion ontologies.

Complexities Abound… Frank White (Workshop II on Ontologies and Higher-lvl Fusion – Beaver Hollow)
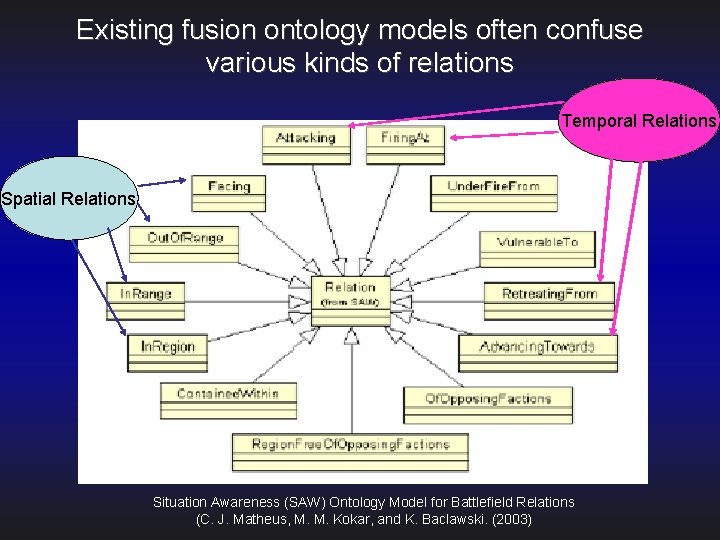
Existing fusion ontology models often confuse various kinds of relations Temporal Relations Spatial Relations Situation Awareness (SAW) Ontology Model for Battlefield Relations (C. J. Matheus, M. M. Kokar, and K. Baclawski. (2003)
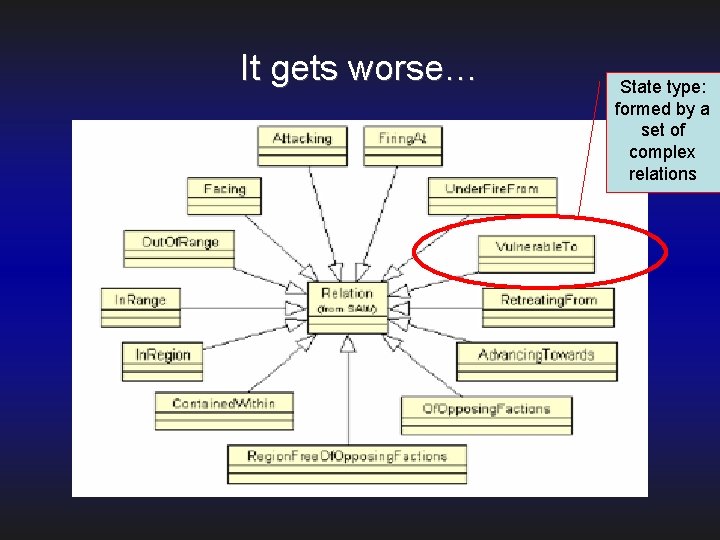
It gets worse… State type: formed by a set of complex relations
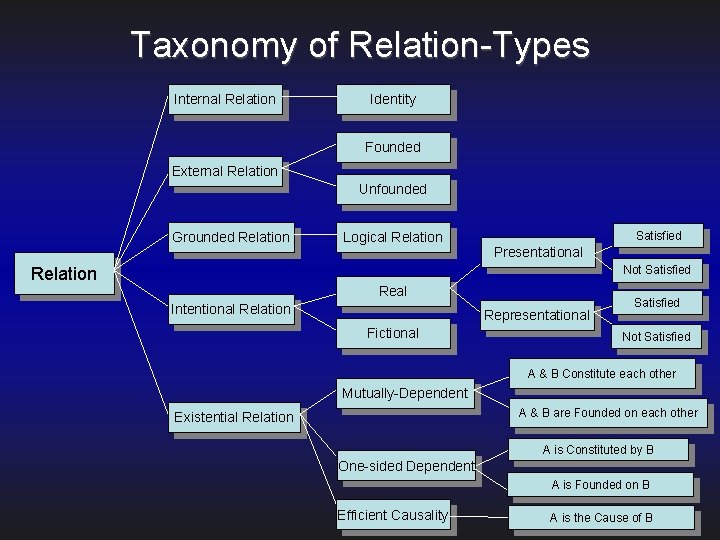
Taxonomy of Relation-Types Internal Relation Identity Founded External Relation Unfounded Grounded Relation Logical Relation Satisfied Presentational Relation Not Satisfied Real Intentional Relation Representational Fictional Satisfied Not Satisfied A & B Constitute each other Mutually-Dependent A & B are Founded on each other Existential Relation A is Constituted by B One-sided Dependent A is Founded on B Efficient Causality A is the Cause of B
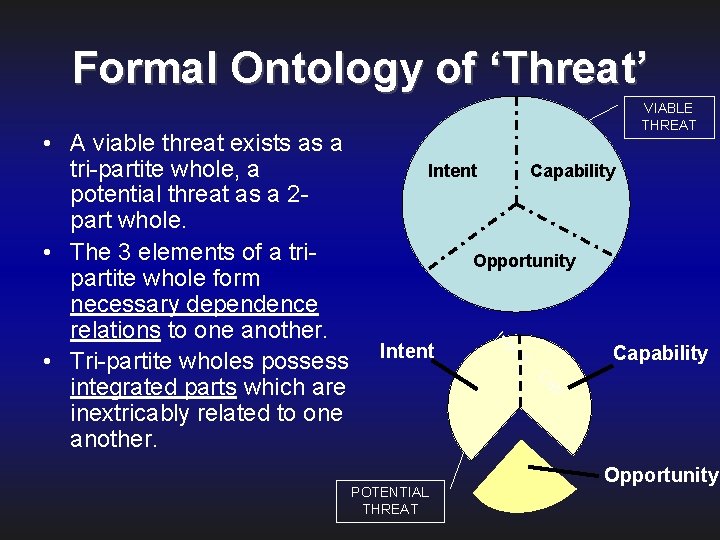
Formal Ontology of ‘Threat’ • A viable threat exists as a tri-partite whole, a potential threat as a 2 part whole. • The 3 elements of a tripartite whole form necessary dependence relations to one another. • Tri-partite wholes possess integrated parts which are inextricably related to one another. VIABLE THREAT Intent Capability Opportunity Intent POTENTIAL THREAT In te nt Ca p Capability Opportunity
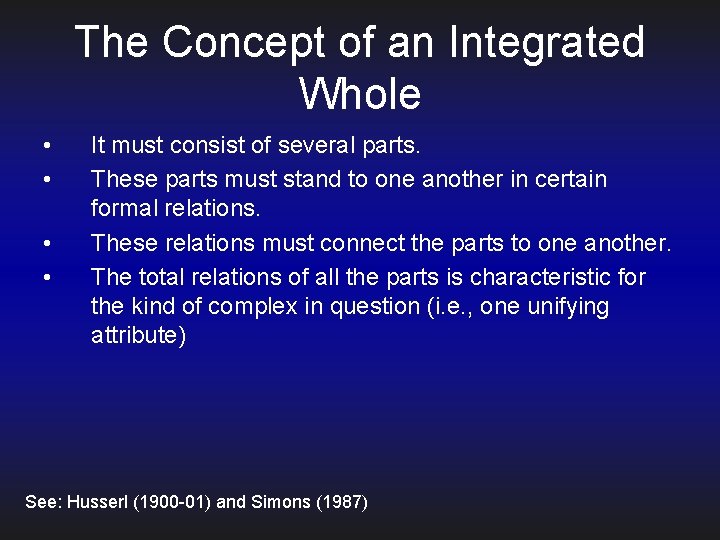
The Concept of an Integrated Whole • • It must consist of several parts. These parts must stand to one another in certain formal relations. These relations must connect the parts to one another. The total relations of all the parts is characteristic for the kind of complex in question (i. e. , one unifying attribute) See: Husserl (1900 -01) and Simons (1987)

Some Basic Metaphysical Components of Threat Ontology • Continuants and Occurrents (Grenon & Smith) • Granular partition theory (Bittner & Smith, Mark) • Mereotopology (Smith, Varzi, Casati)
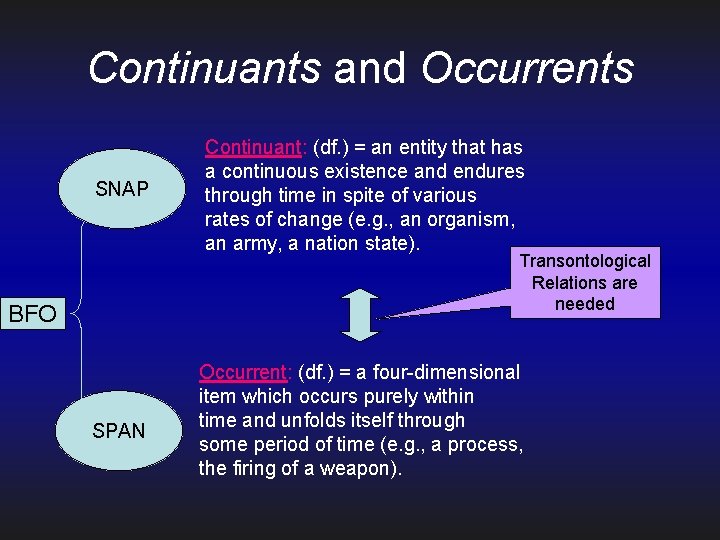
Continuants and Occurrents SNAP Continuant: (df. ) = an entity that has a continuous existence and endures through time in spite of various rates of change (e. g. , an organism, an army, a nation state). Transontological Relations are needed BFO SPAN Occurrent: (df. ) = a four-dimensional item which occurs purely within time and unfolds itself through some period of time (e. g. , a process, the firing of a weapon).
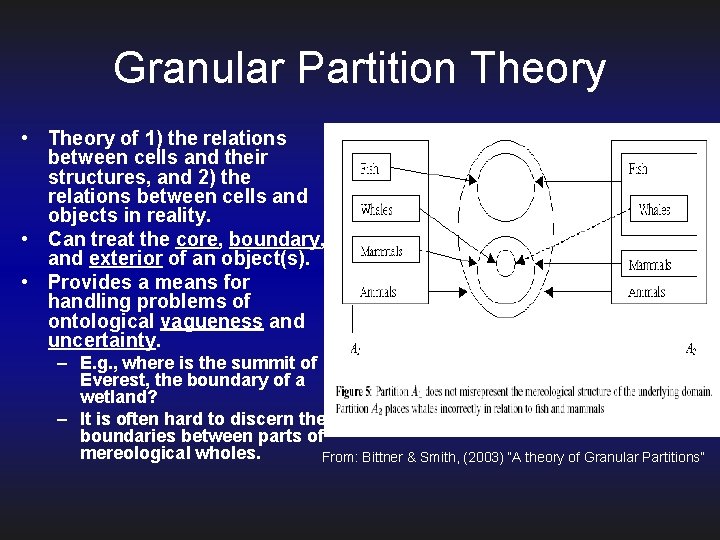
Granular Partition Theory • Theory of 1) the relations between cells and their structures, and 2) the relations between cells and objects in reality. • Can treat the core, boundary, and exterior of an object(s). • Provides a means for handling problems of ontological vagueness and uncertainty. – E. g. , where is the summit of Everest, the boundary of a wetland? – It is often hard to discern the boundaries between parts of mereological wholes. From: Bittner & Smith, (2003) “A theory of Granular Partitions”
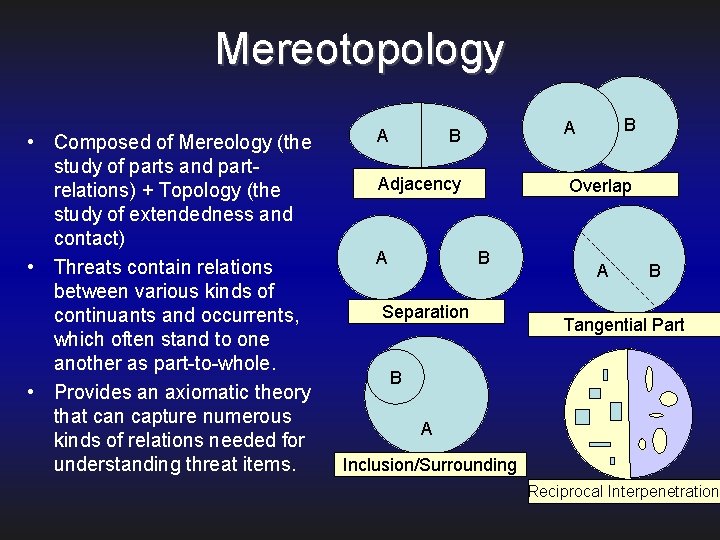
Mereotopology • Composed of Mereology (the study of parts and partrelations) + Topology (the study of extendedness and contact) • Threats contain relations between various kinds of continuants and occurrents, which often stand to one another as part-to-whole. • Provides an axiomatic theory that can capture numerous kinds of relations needed for understanding threat items. A Adjacency A B Overlap B Separation A B Tangential Part B A Inclusion/Surrounding Reciprocal Interpenetration
Dispersed vs. Compact Wholes Dispersed wholes are wholes, which are spatially, temporally or causally non-contiguous, but which nonetheless contain parts or members that stand to one another via a certain unifying characteristic of that whole. Dispersed wholes are very important for studying unconventional threats…. Proximity measures in the characteristics space and constraints permit for definition and understanding of dispersed wholes and the transition from dispersed to compact whole. Constraints are context specific.
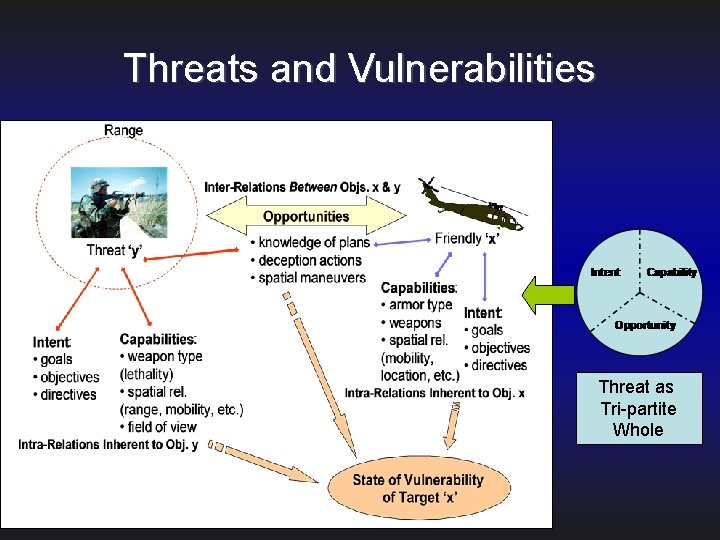
Threats and Vulnerabilities Threat as Tri-partite Whole
States such as ‘Vulnerability’ often consist of various complex relations (nested, etc. ) • spatial and temporal regions containing various objects (e. g. , x, y, …z, which can be both bounded or unbounded) • spatial distances between x and y (distances attributed to range, visibility, etc. ) • scattered temporal regions related to various processes of x and y • physical attributes/properties of x and y (mobility, armor, weapons, size, shape, etc. ) • nonphysical (e. g. , intentional) attributes of x and y (goals, plans, directives, perceptions, etc. ) • behaviors of x and y relative to one another (combinations of physical and nonphysical items leading to the manifestation of intentions/goals, carried out via opportunities)

Conclusions We have presented a general theory for designing an upper ontology for threat and vulnerability. Future work: • Formalize Threat Components: – Intent, Capability & OPPORTUNITY • Implementation – User needs (e. g. , CSE, GUI’s, scenarios) – Add in conditions for uncertainty and probability (of relations and situational items)
- Slides: 27