VPN GREGeneric Route Encapsulation DMVPNDynamic Multipoint VPN MPLSmultiprotocol





































- Slides: 49




VPN의 종류 GRE(Generic Route Encapsulation) DMVPN(Dynamic Multipoint VPN) MPLS(multiprotocol label switching) SSL(secure socket layer)

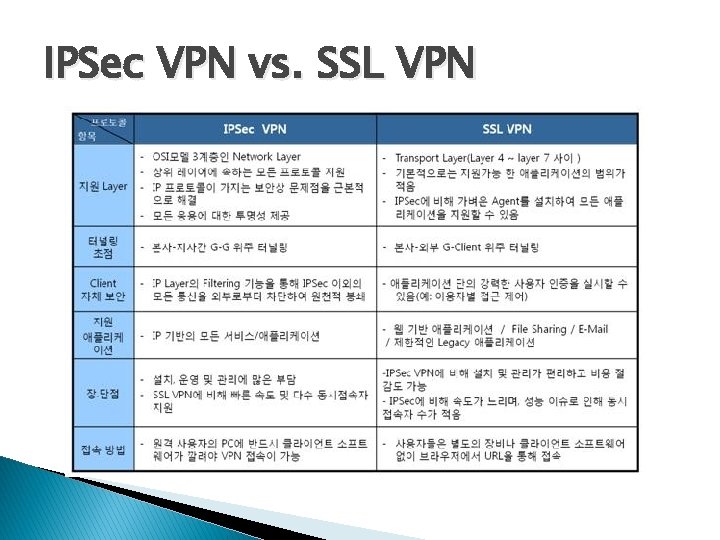
IPSec VPN vs. SSL VPN

IPSec VPN vs. SSL VPN


VPN의 보안 기능 장치간의 인증 및 보안연계(SA, security association) 프로토콜 � 연결되는 ◦ ISAKMP (Internet security association and key management protocol) ◦ IKE (Internet key exchange) � 인증 및 암호화 프로토콜 ◦ AH(Authentication Header): 데이터의 인증 및 무결성 ◦ ESP(Encapsulation Security Payload): 데이터 암호화



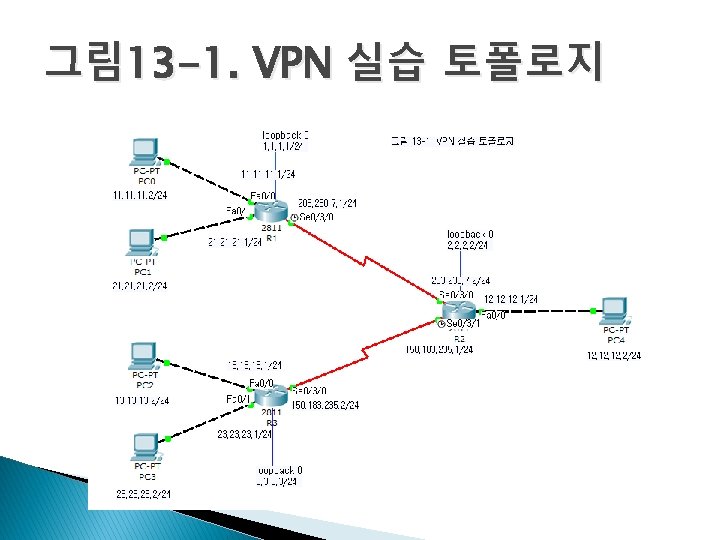
라우터 설정 R 2(config)#interface Fast. Ethernet 0/0 R 2(config-if)#no shutdown R 2(config-if)#ip address 12. 12. 1 255. 0 R 2(config-if)#exit R 1(config)#interface Fast. Ethernet 0/0 R 2(config)#interface Serial 0/3/0 R 1(config-if)#no shutdown R 2(config-if)#no shutdown R 1(config-if)#ip address 11. 11. 1 255. 0 R 2(config-if)#ip address 203. 230. 7. 2 255. 0 R 1(config-if)#exit R 2(config-if)#exit R 1(config)#interface Fast. Ethernet 0/1 R 2(config)#interface Serial 0/3/1 R 1(config-if)#no shutdown R 2(config-if)#no shutdown R 1(config-if)#ip address 21. 21. 1 255. 0 R 2(config-if)#clock rate 1000000 R 1(config-if)#exit R 2(config-if)#ip address 150. 183. 235. 1 255. 0 R 1(config)#interface Serial 0/3/0 R 2(config-if)#exit R 1(config-if)#no shutdown R 2(config)#int lo 0 R 1(config-if)#clock rate 1000000 R 2(config-if)#ip add 2. 2 255. 0 R 1(config-if)#ip address 203. 230. 7. 1 255. 0 R 2(config-if)#exit R 1(config-if)#exit R 2(config)#router ospf 7 R 3(config)#interface Fast. Ethernet 0/0 R 1(config)#int lo 0 R 2(config-router)#network 2. 2 0. 0 a 0 R 3(config-if)#no shutdown R 1(config-if)#ip add 1. 1 255. 0 R 2(config-router)#network 12. 12. 1 0. 0 a 0 R 3(config-if)#ip address 13. 13. 1 255. 0 R 1(config-if)#exit R 2(config-router)#network 203. 230. 7. 2 0. 0 a 0 R 3(config-if)#exit R 1(config)#router ospf 7 R 2(config-router)#network 150. 183. 235. 1 0. 0 a 0 R 3(config)#interface Fast. Ethernet 0/1 R 1(config-router)#network 1. 1 0. 0 a 0 R 3(config-if)#no shutdown R 1(config-router)#network 11. 11. 1 0. 0 a 0 R 3(config-if)#ip R 1(config-router)#network 21. 21. 1 0. 0 address 23. 23. 1 255. 0 R 3(config-if)#exit R 1(config-router)#network 203. 230. 7. 1 0. 0 a 0 R 3(config)#interface Serial 0/3/0 R 3(config-if)#no shutdown R 3(config-if)#ip address 150. 183. 235. 2 255. 0 R 3(config-if)#exit R 3(config)#int lo 0 R 3(config-if)#ip add 3. 3 255. 0 R 3(config-if)#exit R 3(config)#router ospf 7 R 3(config-router)#network 3. 3 0. 0 a 0 R 3(config-router)#network 13. 13. 1 0. 0 a 0 R 3(config-router)#network 23. 23. 1 0. 0 a 0 R 3(config-router)#network 150. 183. 235. 2 0. 0 a 0

라우팅 테이블 확인 R 1#show ip route 1. 0. 0. 0/24 is subnetted, 1 subnets R 2#show ip route C 1. 1. 1. 0 is directly connected, Loopback 0 1. 0. 0. 0/32 is subnetted, 1 subnets 2. 0. 0. 0/32 is subnetted, 1 subnets O 1. 1 [110/65] via 203. 230. 7. 1, 16: 23: 51, Serial 0/3/0 O 2. 2 [110/65] via 203. 230. 7. 2, 16: 22: 43, Serial 0/3/0 2. 0. 0. 0/24 is subnetted, 1 subnets 3. 0. 0. 0/32 is subnetted, 1 subnets C 2. 2. 2. 0 is directly connected, Loopback 0 O 3. 3 [110/129] via 203. 230. 7. 2, 00: 11: 12, Serial 0/3/0 3. 0. 0. 0/32 is subnetted, 1 subnets 11. 0. 0. 0/24 is subnetted, 1 subnets O 3. 3 [110/65] via 150. 183. 235. 2, 00: 12: 24, Serial 0/3/1 C 11. 11. 0 is directly connected, Fast. Ethernet 0/0 11. 0. 0. 0/24 is subnetted, 1 subnets 12. 0. 0. 0/24 is subnetted, 1 subnets O 11. 11. 0 [110/65] via 203. 230. 7. 1, 16: 23: 51, Serial 0/3/0 O 12. 12. 0 [110/65] via 203. 230. 7. 2, 16: 22: 43, Serial 0/3/0 12. 0. 0. 0/24 is subnetted, 1 subnets 13. 0. 0. 0/24 is subnetted, 1 subnets C 12. 12. 0 is directly connected, Fast. Ethernet 0/0 O 13. 13. 0 [110/129] via 203. 230. 7. 2, 00: 11: 12, Serial 0/3/0 13. 0. 0. 0/24 is subnetted, 1 subnets R 3#show ip route 21. 0. 0. 0/24 is subnetted, 1 subnets 1. 0. 0. 0/32 is subnetted, 1 subnets O 13. 13. 0 [110/65] via 150. 183. 235. 2, 00: 12: 24, Serial 0/3/1 C 21. 21. 0 is directly connected, Fast. Ethernet 0/1 O 1. 1 [110/129] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0 21. 0. 0. 0/24 is subnetted, 1 subnets 23. 0. 0. 0/24 is subnetted, 1 subnets 2. 0. 0. 0/32 is subnetted, 1 subnets O 21. 21. 0 [110/65] via 203. 230. 7. 1, 16: 23: 51, Serial 0/3/0 O 23. 23. 0 [110/129] via 203. 230. 7. 2, Serial 0/3/0 O 2. 200: 11: 12, [110/65] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0 23. 0. 0. 0/24 is subnetted, 1 subnets 150. 183. 0. 0/24 is subnetted, 1 subnets 3. 0. 0. 0/24 is subnetted, 1 subnets O 23. 23. 0 [110/65] via 150. 183. 235. 2, 00: 12: 24, Serial 0/3/1 O 150. 183. 235. 0 [110/128] via 00: 13: 17, Serial 0/3/0 C 203. 230. 7. 2, 3. 3. 3. 0 is directly connected, Loopback 0 150. 183. 0. 0/24 is subnetted, 1 subnets C 203. 230. 7. 0/24 is directly connected, Serial 0/3/0 11. 0. 0. 0/24 is subnetted, 1 subnets C 150. 183. 235. 0 is directly connected, Serial 0/3/1 O 11. 11. 0 [110/129] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0 C 203. 230. 7. 0/24 is directly connected, Serial 0/3/0 12. 0. 0. 0/24 is subnetted, 1 subnets O 12. 12. 0 [110/65] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0 13. 0. 0. 0/24 is subnetted, 1 subnets C 13. 13. 0 is directly connected, Fast. Ethernet 0/0 21. 0. 0. 0/24 is subnetted, 1 subnets O 21. 21. 0 [110/129] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0 23. 0. 0. 0/24 is subnetted, 1 subnets C 23. 23. 0 is directly connected, Fast. Ethernet 0/1 150. 183. 0. 0/24 is subnetted, 1 subnets C 150. 183. 235. 0 is directly connected, Serial 0/3/0 O 203. 230. 7. 0/24 [110/128] via 150. 183. 235. 1, 00: 13: 57, Serial 0/3/0

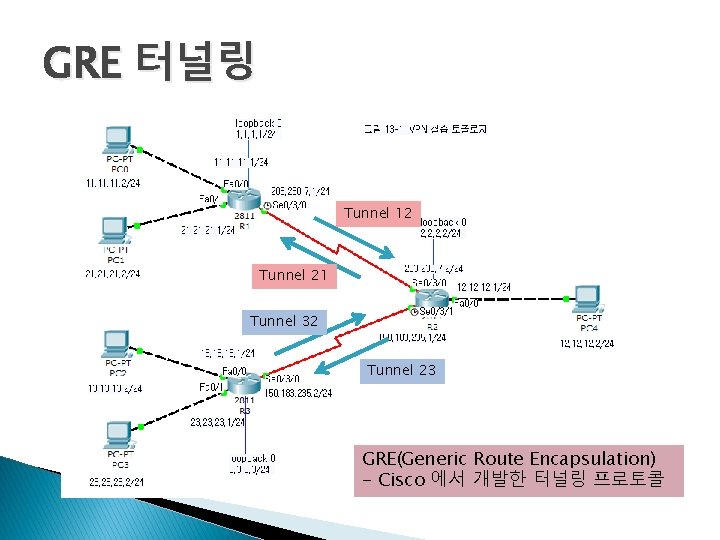
GRE 터널링 Tunnel 12 Tunnel 21 Tunnel 32 Tunnel 23 GRE(Generic Route Encapsulation) - Cisco 에서 개발한 터널링 프로토콜


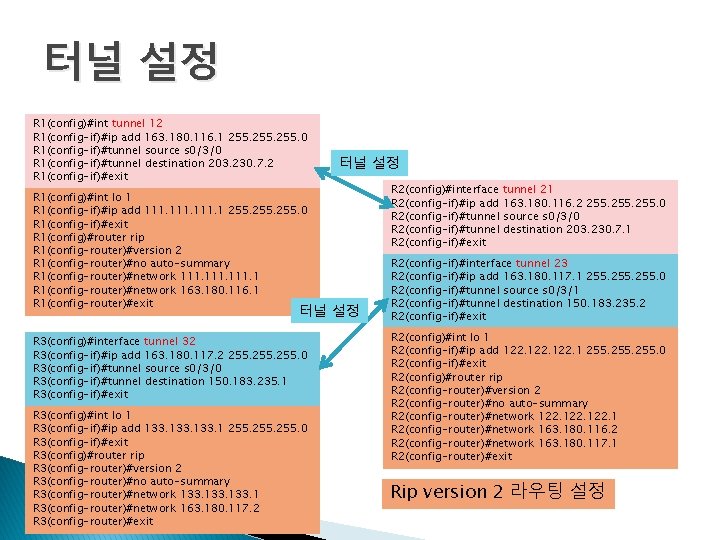
터널 설정 방법 111. 1/24 163. 180. 116. 1 122. 1/24 163. 180. 116. 2 163. 180. 117. 1 163. 180. 117. 2 133. 1/24 각 라우터에 터널링에 이용할 루프백 인터페이스 1번 추가 - 111. 1/24 - 122. 1/24 - 133. 1/24 터널링 설정 - Tunnel 12: - Tunnel 21: - Tunnel 23: - Tunnel 32: 163. 180. 116. 1 163. 180. 116. 2 163. 180. 117. 1 163. 180. 117. 2 터널간 RIPv 2 를 이용해 라우팅 설정

터널 설정 R 1(config)#int tunnel 12 R 1(config-if)#ip add 163. 180. 116. 1 255. 0 R 1(config-if)#tunnel source s 0/3/0 R 1(config-if)#tunnel destination 203. 230. 7. 2 R 1(config-if)#exit R 1(config)#int lo 1 R 1(config-if)#ip add 111. 1 255. 0 R 1(config-if)#exit R 1(config)#router rip R 1(config-router)#version 2 R 1(config-router)#no auto-summary R 1(config-router)#network 111. 1 R 1(config-router)#network 163. 180. 116. 1 R 1(config-router)#exit 터널 설정 R 3(config)#interface tunnel 32 R 3(config-if)#ip add 163. 180. 117. 2 255. 0 R 3(config-if)#tunnel source s 0/3/0 R 3(config-if)#tunnel destination 150. 183. 235. 1 R 3(config-if)#exit R 3(config)#int lo 1 R 3(config-if)#ip add 133. 1 255. 0 R 3(config-if)#exit R 3(config)#router rip R 3(config-router)#version 2 R 3(config-router)#no auto-summary R 3(config-router)#network 133. 1 R 3(config-router)#network 163. 180. 117. 2 R 3(config-router)#exit R 2(config)#interface tunnel 21 R 2(config-if)#ip add 163. 180. 116. 2 255. 0 R 2(config-if)#tunnel source s 0/3/0 R 2(config-if)#tunnel destination 203. 230. 7. 1 R 2(config-if)#exit R 2(config-if)#interface tunnel 23 R 2(config-if)#ip add 163. 180. 117. 1 255. 0 R 2(config-if)#tunnel source s 0/3/1 R 2(config-if)#tunnel destination 150. 183. 235. 2 R 2(config-if)#exit R 2(config)#int lo 1 R 2(config-if)#ip add 122. 1 255. 0 R 2(config-if)#exit R 2(config)#router rip R 2(config-router)#version 2 R 2(config-router)#no auto-summary R 2(config-router)#network 122. 1 R 2(config-router)#network 163. 180. 116. 2 R 2(config-router)#network 163. 180. 117. 1 R 2(config-router)#exit Rip version 2 라우팅 설정

터널링 결과 – 라우팅테이블 R 1#show ip route rip 122. 0. 0. 0/24 is subnetted, 1 subnets R 122. 0 [120/1] via 163. 180. 116. 2, 00: 22, Tunnel 12 133. 0. 0/24 is subnetted, 1 subnets R 133. 0 [120/2] via 163. 180. 116. 2, 00: 22, Tunnel 12 163. 180. 0. 0/24 is subnetted, 2 subnets R 163. 180. 117. 0 [120/1] via 163. 180. 116. 2, 00: 22, Tunnel 12 R 2#show ip route rip 111. 0. 0. 0/24 is subnetted, 1 subnets R 111. 0 [120/1] via 163. 180. 116. 1, 00: 22, Tunnel 21 133. 0. 0/24 is subnetted, 1 subnets R 133. 0 [120/1] via 163. 180. 117. 2, 00: 02, Tunnel 23 R 3#show ip route rip 111. 0. 0. 0/24 is subnetted, 1 subnets R 111. 0 [120/2] via 163. 180. 117. 1, 00: 17, Tunnel 32 122. 0. 0. 0/24 is subnetted, 1 subnets R 122. 0 [120/1] via 163. 180. 117. 1, 00: 17, Tunnel 32 163. 180. 0. 0/24 is subnetted, 2 subnets R 163. 180. 116. 0 [120/1] via 163. 180. 117. 1, 00: 17, Tunnel 32 OSPF – 물리적 인터페이스에 설정 RIP – 가상 터널인터페이스에 설정

터널링 결과 - Traceroute R 1#traceroute 13. 13. 2 Type escape sequence to abort. Tracing the route to 13. 13. 2 1 203. 230. 7. 2 9 msec 3 msec 4 msec 2 150. 183. 235. 2 7 msec 11 msec 8 msec 3 13. 13. 2 16 msec 15 msec R 1#traceroute 133. 1 Type escape sequence to abort. Tracing the route to 133. 1 1 163. 180. 116. 2 15 msec 1 msec 3 msec 2 163. 180. 117. 2 9 msec 20 msec 4 msec 물리 인터페이스를 통해 연결 터널 인터페이스를 통해 연결


라우터 설정 R 1(config)#interface Fast. Ethernet 0/0 R 1(config-if)#no shutdown R 1(config-if)#ip address 1. 1 255. 0 R 1(config-if)#exit R 1(config)#interface Serial 0/3/0 R 1(config-if)#no shutdown R 1(config-if)#clock rate 1000000 R 1(config-if)#ip address 203. 230. 7. 1 255. 0 R 1(config-if)#exit R 1(config)#router rip R 1(config-router)#version 2 R 1(config-router)#network 1. 1. 1. 0 R 1(config-router)#network 203. 230. 7. 0 R 1(config-router)#network 150. 183. 235. 0 R 1(config-router)#exit R 1(config)#int tunnel 1 R 1(config-if)#ip add 150. 183. 235. 1 255. 0 R 1(config-if)#tunnel source s 0/3/0 R 1(config-if)#tunnel destination 203. 230. 7. 2 R 1(config-if)#exit R 1(config)#ip route 2. 2. 2. 0 255. 0 150. 183. 235. 2 R 2(config)#interface Fast. Ethernet 0/0 R 2(config-if)#no shutdown R 2(config-if)#ip address 2. 2. 2. 1 255. 0 R 2(config-if)#exit R 2(config)#interface Serial 0/3/0 R 2(config-if)#no shutdown R 2(config-if)#ip address 203. 230. 7. 2 255. 0 R 2(config-if)#exit R 2(config)#router rip R 2(config-router)#version 2 R 2(config-router)#network 2. 2. 2. 0 R 2(config-router)#network 203. 230. 7. 0 R 2(config-router)#network 150. 183. 235. 0 R 2(config-router)#exit R 2(config)#int tunnel 2 R 2(config-if)#ip add 150. 183. 235. 2 255. 0 R 2(config-if)#tunnel source s 0/3/0 R 2(config-if)#tunnel destination 203. 230. 7. 1 R 2(config-if)#exit R 2(config)#ip route 1. 1. 1. 0 255. 0 150. 183. 235. 1

경로 확인 PC>tracert 203. 230. 7. 2 Tracing route to 203. 230. 7. 2 over a maximum of 30 hops: 1 6 ms 2 10 ms 5 ms 4 ms 1. 1 17 ms 203. 230. 7. 2 Trace complete. PC>tracert 2. 2 Tracing route to 2. 2 over a maximum of 30 hops: 1 3 ms 2 10 ms 3 10 ms 2 ms 3 ms 2 ms 4 ms 12 ms 8 ms 1. 1 150. 183. 235. 2 2. 2 Trace complete. 목적지가 203. 230. 7. 2인 경우에는 물리적인 인터페이스로 연결 목적지가 2. 2인 경우에는 터널 인터페이스로 연결

GRE + IPSec VPN � GRE 터널링은 데이터 보안성이 없음 � IPSec VPN을 GRE와 함께 사용하여 보안성 향상 가능 � ISAKMP 정책 ◦ ◦ Authentication: pre-share Encryption: AES 256 Hash: sha Lifetime: 3600초 � IPSec 정책 ◦ 대상트래픽: 각 라우터의 시리얼 인터페이스를 통해 나가는 모 든 트래픽 ◦ Encapsulation: esp-3 des ◦ Encryption: esp-aes 256 ◦ Hash: esp-md 5 -hmac

GRE + IPSec VPN 13 -4. GRE 터널을 이용한 IPSec VPN 설정 토폴로지 � 그림 ipsec transform-set STRONG Crypto map VPN 1 ACL 110 2901 라우터 이용 Crypto map VPN 2 ACL 120


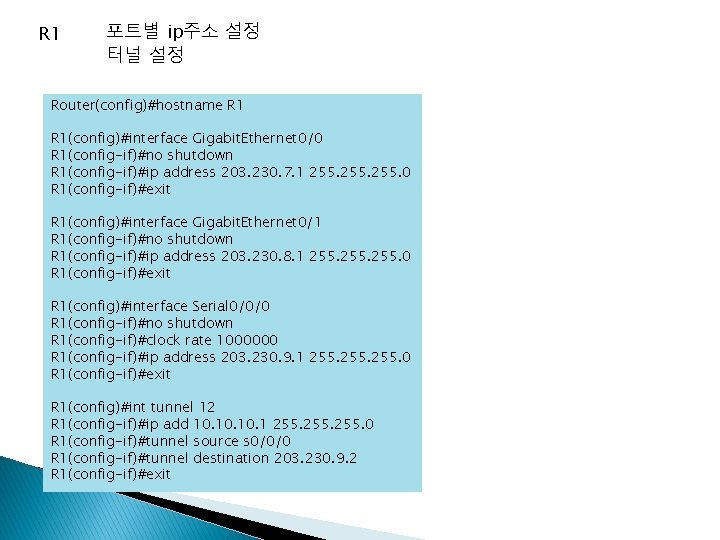
R 1 포트별 ip주소 설정 터널 설정 Router(config)#hostname R 1(config)#interface Gigabit. Ethernet 0/0 R 1(config-if)#no shutdown R 1(config-if)#ip address 203. 230. 7. 1 255. 0 R 1(config-if)#exit R 1(config)#interface Gigabit. Ethernet 0/1 R 1(config-if)#no shutdown R 1(config-if)#ip address 203. 230. 8. 1 255. 0 R 1(config-if)#exit R 1(config)#interface Serial 0/0/0 R 1(config-if)#no shutdown R 1(config-if)#clock rate 1000000 R 1(config-if)#ip address 203. 230. 9. 1 255. 0 R 1(config-if)#exit R 1(config)#int tunnel 12 R 1(config-if)#ip add 10. 10. 1 255. 0 R 1(config-if)#tunnel source s 0/0/0 R 1(config-if)#tunnel destination 203. 230. 9. 2 R 1(config-if)#exit

R 1 License 설정 저장, 재부팅 R 1(config)#license boot module c 2900 technology-package securityk 9 PLEASE READ THE FOLLOWING TERMS CAREFULLY. INSTALLING THE LICENSE OR LICENSE KEY PROVIDED FOR ANY CISCO PRODUCT FEATURE OR USING SUCH PRODUCT FEATURE CONSTITUTES YOUR FULL ACCEPTANCE OF THE FOLLOWING TERMS. YOU MUST NOT PROCEED FURTHER IF YOU ARE NOT WILLING TO BE BOUND BY ALL THE TERMS SET FORTH HEREIN. Use of this product feature requires an additional license from Cisco, together with an additional payment. You may use this product feature on an evaluation basis, without payment to Cisco, for 60 days. Your use of the product, including during the 60 day evaluation period, is ………………… ACCEPT? [yes/no]: y % use 'write' command to make license boot config take effect on next boot %LICENSE-6 -EULA_ACCEPTED: EULA for feature securityk 9 1. 0 has been accepted. UDI=CISCO 2901/K 9: FTX 1524 VE 24 -; Store. Index=0: Evaluation License Storage R 1(config)#: %IOS_LICENSE_IMAGE_APPLICATION-6 -LICENSE_LEVEL: Module name = C 2900 Next reboot level = securityk 9 and License = securityk 9 R 1(config)#do write Building configuration. . . [OK] R 1(config)#exit R 1#reload Proceed with reload? [confirm]y. System Bootstrap, Version 15. 1(4)M 4, RELEASE SOFTWARE (fc 1) Technical Support: http: //www. cisco. com/techsupport Copyright (c) 2010 by cisco Systems, Inc. Total memory size = 512 MB - On-board = 512 MB, DIMM 0 = 0 MB CISCO 2901/K 9 platform with 524288 Kbytes of main memory Main memory is configured to 72/-1(On-board/DIMM 0) bit mode with ECC disabled

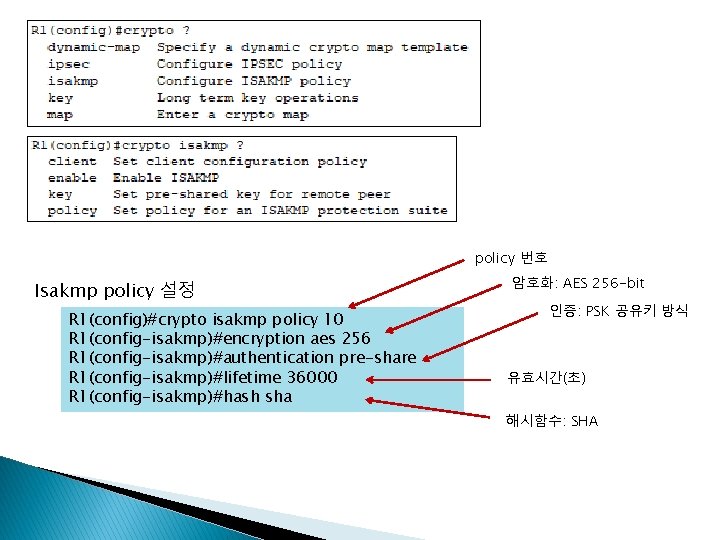
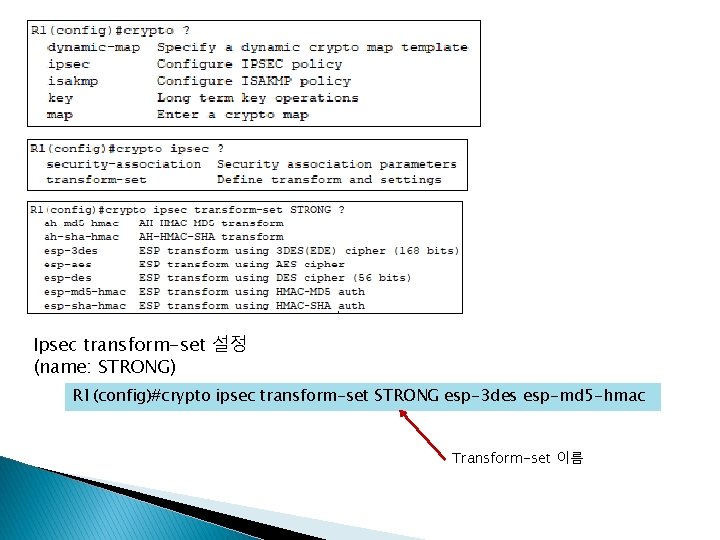
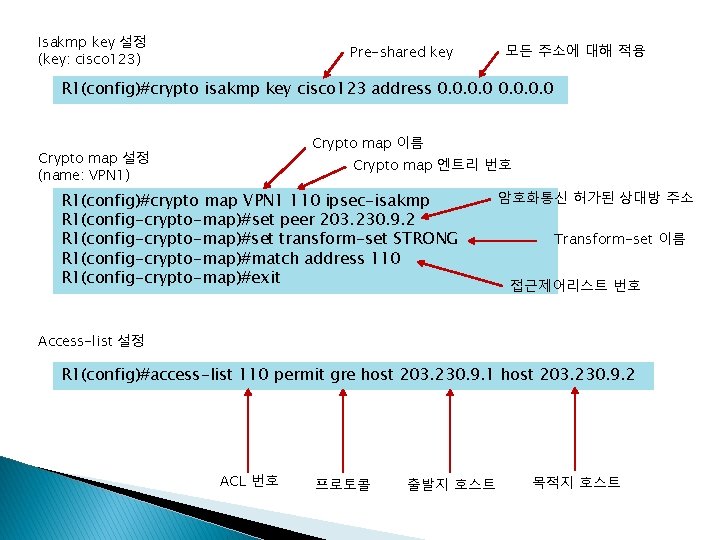
R 1 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN) Access-list 설정 인터페이스에 VPN 설정 라우팅 설정 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN 1) Access-list 설정 인터페이스에 VPN 1 설정 라우팅 설정 R 1(config)#crypto isakmp policy 10 R 1(config-isakmp)#encryption aes 256 R 1(config-isakmp)#authentication pre-share R 1(config-isakmp)#lifetime 36000 R 1(config-isakmp)#hash sha R 1(config-isakmp)#exit R 1(config)#crypto ipsec transform-set STRONG esp-3 des esp-md 5 -hmac R 1(config)#crypto isakmp key cisco 123 address 0. 0 R 1(config)#crypto map VPN 1 110 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. R 1(config-crypto-map)#set peer 203. 230. 9. 2 R 1(config-crypto-map)#set transform-set STRONG R 1(config-crypto-map)#match address 110 R 1(config-crypto-map)#exit R 1(config)#access-list 110 permit gre host 203. 230. 9. 1 host 203. 230. 9. 2 R 1(config)#int s 0/0/0 R 1(config-if)#crypto map VPN 1 *Jan 3 07: 16: 26. 785: %CRYPTO-6 -ISAKMP_ON_OFF: ISAKMP is ON R 1(config-if)#exit R 1(config)#router ospf 7 R 1(config-router)#network 203. 230. 7. 1 0. 0 area 0 R 1(config-router)#network 203. 230. 8. 1 0. 0 area 0 R 1(config-router)#network 203. 230. 9. 1 0. 0 area 0 R 1(config-router)#network 10. 10. 1 0. 0 area 0 R 1(config-router)#exit

policy 번호 Isakmp policy 설정 R 1(config)#crypto isakmp policy 10 R 1(config-isakmp)#encryption aes 256 R 1(config-isakmp)#authentication pre-share R 1(config-isakmp)#lifetime 36000 R 1(config-isakmp)#hash sha 암호화: AES 256 -bit 인증: PSK 공유키 방식 유효시간(초) 해시함수: SHA

Ipsec transform-set 설정 (name: STRONG) R 1(config)#crypto ipsec transform-set STRONG esp-3 des esp-md 5 -hmac Transform-set 이름

Isakmp key 설정 (key: cisco 123) Pre-shared key 모든 주소에 대해 적용 R 1(config)#crypto isakmp key cisco 123 address 0. 0 Crypto map 이름 Crypto map 설정 (name: VPN 1) Crypto map 엔트리 번호 R 1(config)#crypto map VPN 1 110 ipsec-isakmp R 1(config-crypto-map)#set peer 203. 230. 9. 2 R 1(config-crypto-map)#set transform-set STRONG R 1(config-crypto-map)#match address 110 R 1(config-crypto-map)#exit 암호화통신 허가된 상대방 주소 Transform-set 이름 접근제어리스트 번호 Access-list 설정 R 1(config)#access-list 110 permit gre host 203. 230. 9. 1 host 203. 230. 9. 2 ACL 번호 프로토콜 출발지 호스트 목적지 호스트

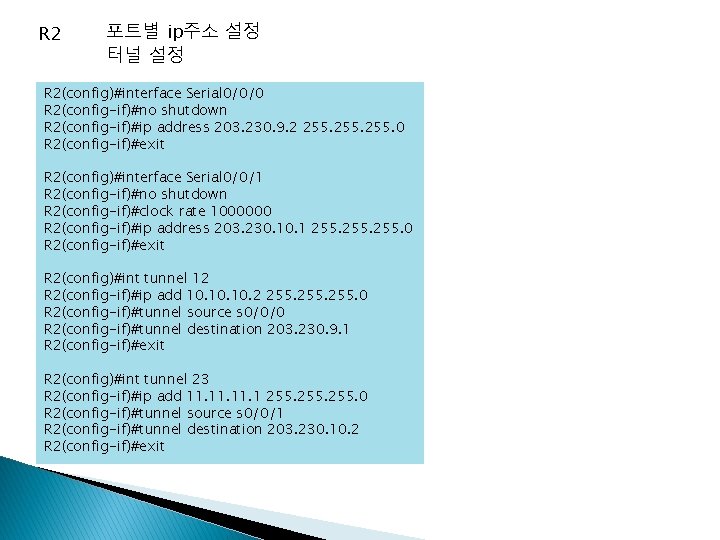
R 2 포트별 ip주소 설정 터널 설정 R 2(config)#interface Serial 0/0/0 R 2(config-if)#no shutdown R 2(config-if)#ip address 203. 230. 9. 2 255. 0 R 2(config-if)#exit R 2(config)#interface Serial 0/0/1 R 2(config-if)#no shutdown R 2(config-if)#clock rate 1000000 R 2(config-if)#ip address 203. 230. 1 255. 0 R 2(config-if)#exit R 2(config)#int tunnel 12 R 2(config-if)#ip add 10. 10. 2 255. 0 R 2(config-if)#tunnel source s 0/0/0 R 2(config-if)#tunnel destination 203. 230. 9. 1 R 2(config-if)#exit R 2(config)#int tunnel 23 R 2(config-if)#ip add 11. 11. 1 255. 0 R 2(config-if)#tunnel source s 0/0/1 R 2(config-if)#tunnel destination 203. 230. 10. 2 R 2(config-if)#exit

R 2 License 설정 저장, 재부팅 R 2(config)#license boot module c 2900 technology-package securityk 9 PLEASE READ THE FOLLOWING TERMS CAREFULLY. INSTALLING THE LICENSE OR LICENSE KEY PROVIDED FOR ANY CISCO PRODUCT FEATURE OR USING SUCH PRODUCT FEATURE CONSTITUTES YOUR FULL ACCEPTANCE OF THE FOLLOWING TERMS. YOU MUST NOT PROCEED FURTHER IF YOU ARE NOT WILLING TO BE BOUND BY ALL THE TERMS SET FORTH HEREIN. Use of this product feature requires an additional license from Cisco, together with an additional payment. You may use this product feature on an evaluation basis, without payment to Cisco, for 60 days. Your use of the product, including during the 60 day evaluation period, is ………………… ACCEPT? [yes/no]: y % use 'write' command to make license boot config take effect on next boot %LICENSE-6 -EULA_ACCEPTED: EULA for feature securityk 9 1. 0 has been accepted. UDI=CISCO 2901/K 9: FTX 1524 VE 24 -; Store. Index=0: Evaluation License Storage R 2(config)#: %IOS_LICENSE_IMAGE_APPLICATION-6 -LICENSE_LEVEL: Module name = C 2900 Next reboot level = securityk 9 and License = securityk 9 R 2(config)#do write Building configuration. . . [OK] R 2(config)#exit R 2#reload Proceed with reload? [confirm]y. System Bootstrap, Version 15. 1(4)M 4, RELEASE SOFTWARE (fc 1) Technical Support: http: //www. cisco. com/techsupport Copyright (c) 2010 by cisco Systems, Inc. Total memory size = 512 MB - On-board = 512 MB, DIMM 0 = 0 MB CISCO 2901/K 9 platform with 524288 Kbytes of main memory Main memory is configured to 72/-1(On-board/DIMM 0) bit mode with ECC disabled

R 2 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN) Access-list 설정 인터페이스에 VPN 설정 라우팅 설정 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN 1, VPN 2) Access-list 설정 인터페이스에 VPN 1, VPN 2 설정 라우팅 설정 R 2(config)#crypto isakmp policy 10 R 2(config-isakmp)#encryption aes 256 R 2(config-isakmp)#authentication pre-share R 2(config-isakmp)#lifetime 36000 R 2(config-isakmp)#hash sha R 2(config-isakmp)#exit R 2(config)#crypto ipsec transform-set STRONG esp-3 des esp-md 5 -hmac R 2(config)#crypto isakmp key cisco 123 address 0. 0 R 2(config)#crypto map VPN 1 110 ipsec-isakmp R 2(config-crypto-map)#set peer 203. 230. 9. 1 R 2(config-crypto-map)#set transform-set STRONG R 2(config-crypto-map)#match address 110 R 2(config-crypto-map)#exit R 2(config)#crypto map VPN 2 120 ipsec-isakmp R 2(config-crypto-map)#set peer 203. 230. 10. 2 R 2(config-crypto-map)#set transform-set STRONG R 2(config-crypto-map)#match address 120 R 2(config-crypto-map)#exit R 2(config)#access-list 110 permit gre host 203. 230. 9. 2 host 203. 230. 9. 1 R 2(config)#access-list 120 permit gre host 203. 230. 10. 2 R 2(config)#int s 0/0/0 R 2(config-if)#crypto map VPN 1 R 2(config-if)#exit R 2(config)#int s 0/0/1 R 2(config-if)#crypto map VPN 2 R 2(config-if)#exit R 2(config)#router ospf 7 R 2(config-router)#network 203. 230. 9. 2 0. 0 area 0 R 2(config-router)#network 203. 230. 1 0. 0 area 0 R 2(config-router)#network 10. 10. 2 0. 0 area 0 R 2(config-router)#network 11. 11. 1 0. 0 area 0 R 2(config-router)#exit

R 3 포트별 ip주소 설정 터널 설정 R 3(config)#interface Gigabit. Ethernet 0/0 R 3(config-if)#no shutdown R 3(config-if)#ip address 203. 230. 11. 1 255. 0 R 3(config-if)#exit R 3(config)#interface Gigabit. Ethernet 0/1 R 3(config-if)#no shutdown R 3(config-if)#ip address 203. 230. 12. 1 255. 0 R 3(config-if)#exit R 3(config)#interface Serial 0/0/0 R 3(config-if)#no shutdown R 3(config-if)#ip address 203. 230. 10. 2 255. 0 R 3(config-if)#exit R 3(config)#int tunnel 23 R 3(config-if)#ip add 11. 11. 2 255. 0 R 3(config-if)#tunnel source s 0/0/0 R 3(config-if)#tunnel destination 203. 230. 1 R 3(config-if)#exit

R 3 License 설정 저장, 재부팅 R 3(config)#license boot module c 2900 technology-package securityk 9 PLEASE READ THE FOLLOWING TERMS CAREFULLY. INSTALLING THE LICENSE OR LICENSE KEY PROVIDED FOR ANY CISCO PRODUCT FEATURE OR USING SUCH PRODUCT FEATURE CONSTITUTES YOUR FULL ACCEPTANCE OF THE FOLLOWING TERMS. YOU MUST NOT PROCEED FURTHER IF YOU ARE NOT WILLING TO BE BOUND BY ALL THE TERMS SET FORTH HEREIN. Use of this product feature requires an additional license from Cisco, together with an additional payment. You may use this product feature on an evaluation basis, without payment to Cisco, for 60 days. Your use of the product, including during the 60 day evaluation period, is ………………… ACCEPT? [yes/no]: y % use 'write' command to make license boot config take effect on next boot %LICENSE-6 -EULA_ACCEPTED: EULA for feature securityk 9 1. 0 has been accepted. UDI=CISCO 2901/K 9: FTX 1524 VE 24 -; Store. Index=0: Evaluation License Storage R 3(config)#: %IOS_LICENSE_IMAGE_APPLICATION-6 -LICENSE_LEVEL: Module name = C 2900 Next reboot level = securityk 9 and License = securityk 9 R 3(config)#do write Building configuration. . . [OK] R 3(config)#exit R 3#reload Proceed with reload? [confirm]y. System Bootstrap, Version 15. 1(4)M 4, RELEASE SOFTWARE (fc 1) Technical Support: http: //www. cisco. com/techsupport Copyright (c) 2010 by cisco Systems, Inc. Total memory size = 512 MB - On-board = 512 MB, DIMM 0 = 0 MB CISCO 2901/K 9 platform with 524288 Kbytes of main memory Main memory is configured to 72/-1(On-board/DIMM 0) bit mode with ECC disabled

R 3 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN) Access-list 설정 인터페이스에 VPN 설정 라우팅 설정 Isakmp policy 설정 Ipsec transform-set 설정 (name: STRONG) Isapkm key 설정 (key: cisco 123) Crypto map 설정 (name: VPN 2) Access-list 설정 인터페이스에 VPN 2 설정 라우팅 설정 R 3(config)#crypto isakmp policy 10 R 3(config-isakmp)#encryption aes 256 R 3(config-isakmp)#authentication pre-share R 3(config-isakmp)#lifetime 36000 R 3(config-isakmp)#hash sha R 3(config-isakmp)#exit R 3(config)#crypto ipsec transform-set STRONG esp-3 des esp-md 5 -hmac R 3(config)#crypto isakmp key cisco 123 address 0. 0 R 3(config)#crypto map VPN 2 120 ipsec-isakmp R 3(config-crypto-map)#set peer 203. 230. 1 R 3(config-crypto-map)#set transform-set STRONG R 3(config-crypto-map)#match address 120 R 3(config-crypto-map)#exit R 3(config)#access-list 120 permit gre host 203. 230. 10. 2 host 203. 230. 1 R 3(config)#int s 0/0/0 R 3(config-if)#crypto map VPN 2 R 3(config-if)#exit R 3(config)#router ospf 7 R 3(config-router)#network 203. 230. 11. 1 0. 0 area 0 R 3(config-router)#network 203. 230. 12. 1 0. 0 area 0 R 3(config-router)#network 203. 230. 10. 2 0. 0 area 0 R 3(config-router)#network 11. 11. 2 0. 0 area 0 R 3(config-router)#exit



R 1#show ip route 10. 0/8 is variably subnetted, 2 subnets, 2 masks C 10. 10. 0/24 is directly connected, Tunnel 12 L 10. 10. 1/32 is directly connected, Tunnel 12 11. 0. 0. 0/24 is subnetted, 1 subnets O 11. 11. 0/24 [110/1064] via 10. 10. 2, 00: 03: 34, Tunnel 12 203. 230. 7. 0/24 is variably subnetted, 2 subnets, 2 masks C 203. 230. 7. 0/24 is directly connected, Gigabit. Ethernet 0/0 L 203. 230. 7. 1/32 is directly connected, Gigabit. Ethernet 0/0 R 2#show ip route 203. 230. 8. 0/24 is variably subnetted, 2 subnets, 2 masks 10. 0/8 is variably subnetted, 2 subnets, 2 masks C 203. 230. 8. 0/24 is directly connected, Gigabit. Ethernet 0/1 C 10. 10. 0/24 is directly connected, Tunnel 12 L 203. 230. 8. 1/32 is directly connected, Gigabit. Ethernet 0/1 L 10. 10. 2/32 is directly connected, Tunnel 12 203. 230. 9. 0/24 is variably subnetted, 2 subnets, 2 masks 11. 0. 0. 0/8 is variably subnetted, 2 subnets, 2 masks C 203. 230. 9. 0/24 is directly connected, Serial 0/0/0 C 11. 11. 0/24 is directly connected, Tunnel 23 L 203. 230. 9. 1/32 is directly connected, Serial 0/0/0 L 11. 11. 1/32 is directly connected, Tunnel 23 O 203. 230. 10. 0/24 [110/128] via 10. 10. 2, 00: 03: 34, Tunnel 12 O 203. 230. 7. 0/24 [110/65] via 10. 10. 1, 00: 04: 24, Tunnel 12 O 203. 230. 11. 0/24 [110/129] via 10. 10. 2, 00: 03: 34, Tunnel 12 O 203. 230. 8. 0/24 [110/65] via 10. 10. 1, 00: 04: 24, Tunnel 12 O 203. 230. 12. 0/24 [110/129] via 10. 10. 2, 00: 03: 34, Tunnel 12 203. 230. 9. 0/24 is variably subnetted, 2 subnets, 2 masks C 203. 230. 9. 0/24 is directly connected, Serial 0/0/0 L 203. 230. 9. 2/32 is directly connected, Serial 0/0/0 203. 230. 10. 0/24 is variably subnetted, 2 subnets, 2 masks R 3#show ip route C 203. 230. 10. 0/24 is directly connected, Serial 0/0/1 10. 0/24 is subnetted, 1 subnets L 203. 230. 1/32 is directly connected, Serial 0/0/1 O 10. 10. 0/24 [110/1064] via 11. 11. 1, 00: 04: 35, Tunnel 23 O 203. 230. 11. 0/24 [110/65] via 11. 11. 2, 00: 04: 05, Tunnel 23 11. 0. 0. 0/8 is variably subnetted, 2 subnets, 2 masks O 203. 230. 12. 0/24 [110/65] via 11. 11. 2, 00: 04: 05, Tunnel 23 C 11. 11. 0/24 is directly connected, Tunnel 23 L 11. 11. 2/32 is directly connected, Tunnel 23 O 203. 230. 7. 0/24 [110/129] via 11. 11. 1, 00: 04: 35, Tunnel 23 O 203. 230. 8. 0/24 [110/129] via 11. 11. 1, 00: 04: 35, Tunnel 23 O 203. 230. 9. 0/24 [110/128] via 11. 11. 1, 00: 04: 35, Tunnel 23 203. 230. 10. 0/24 is variably subnetted, 2 subnets, 2 masks C 203. 230. 10. 0/24 is directly connected, Serial 0/0/0 L 203. 230. 10. 2/32 is directly connected, Serial 0/0/0 203. 230. 11. 0/24 is variably subnetted, 2 subnets, 2 masks C 203. 230. 11. 0/24 is directly connected, Gigabit. Ethernet 0/0 L 203. 230. 11. 1/32 is directly connected, Gigabit. Ethernet 0/0 203. 230. 12. 0/24 is variably subnetted, 2 subnets, 2 masks C 203. 230. 12. 0/24 is directly connected, Gigabit. Ethernet 0/1 L 203. 230. 12. 1/32 is directly connected, Gigabit. Ethernet 0/1 라우팅 테이블 원격 네트워크가 GRE 터널로 연결됨

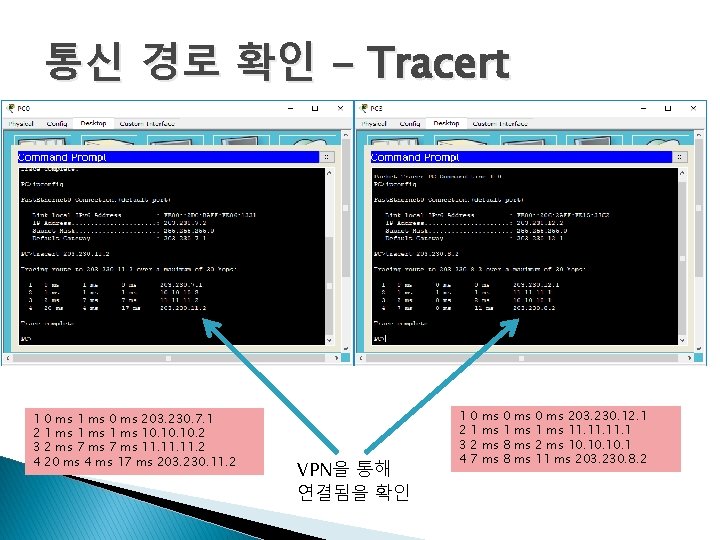
통신 경로 확인 - Tracert 1 2 3 4 0 ms 1 ms 0 ms 203. 230. 7. 1 1 ms 10. 10. 2 2 ms 7 ms 11. 11. 2 20 ms 4 ms 17 ms 203. 230. 11. 2 VPN을 통해 연결됨을 확인 1 2 3 4 0 1 2 7 ms ms 0 1 8 8 ms ms 0 ms 203. 230. 12. 1 1 ms 11. 11. 1 2 ms 10. 10. 1 11 ms 203. 230. 8. 2

VPN 정보 확인하기 � Show crypto ipsec transform-set � Show crypto ipsec sa � Show crypto isakmp policy � Show crypto isakmp sa � Show crypto map ◦ IPSec 설정이 올바로 적용되었는지 확인 ◦ VPN이 적용된 인터페이스별로 VPN에 관한 모든 정보 확인 ◦ ISAKMP 정책 확인 ◦ VPN의 출발지, 도착지, 현재 상태 확인 ◦ VPN의 연결정보, ACL 확인 R 2#show ipsec isakmp key map crypto ? Show IPSEC policy Show ISAKMP Show long term public keys Crypto maps

VPN 정보 – IPSec transform-set R 2#show crypto ipsec transform-set Transform set STRONG: { { esp-3 des esp-sha-hmac } will negotiate = { Tunnel, }, Transform set #$!default_transform_set_1: { esp-aes esp-sha-hmac } will negotiate = { Transport, }, Transform set #$!default_transform_set_0: { esp-3 des esp-sha-hmac } will negotiate = { Transport, },

R 2#show crypto ipsec sa 계속 interface: Serial 0/0/0 Crypto map tag: VPN 1, local addr 203. 230. 9. 2 interface: Serial 0/0/1 Crypto map tag: VPN 2, local addr 203. 230. 1 protected vrf: (none) local ident (addr/mask/prot/port): (203. 230. 9. 2/255. 255/47/0) remote ident (addr/mask/prot/port): (203. 230. 9. 1/255. 255/47/0) current_peer 203. 230. 9. 1 port 500 PERMIT, flags={origin_is_acl, } #pkts encaps: 130, #pkts encrypt: 130, #pkts digest: 0 #pkts decaps: 132, #pkts decrypt: 132, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 protected vrf: (none) local ident (addr/mask/prot/port): (203. 230. 1/255. 255/47/0) remote ident (addr/mask/prot/port): (203. 230. 10. 2/255. 255/47/0) current_peer 203. 230. 10. 2 port 500 PERMIT, flags={origin_is_acl, } #pkts encaps: 128, #pkts encrypt: 128, #pkts digest: 0 #pkts decaps: 126, #pkts decrypt: 126, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt. : 203. 230. 9. 2, remote crypto endpt. : 203. 230. 9. 1 path mtu 1500, ip mtu idb Serial 0/0/0 current outbound spi: 0 x 7 DCE 4 C 31(2110671921) local crypto endpt. : 203. 230. 1, remote crypto endpt. : 203. 230. 10. 2 path mtu 1500, ip mtu idb Serial 0/0/1 current outbound spi: 0 x 040 E 7 F 3 A(68058938) inbound esp sas: spi: 0 x 34 D 7194 D(886511949) transform: esp-3 des esp-md 5 -hmac , in use settings ={Tunnel, } conn id: 2009, flow_id: FPGA: 1, crypto map: VPN 1 sa timing: remaining key lifetime (k/sec): (4525504/2690) IV size: 16 bytes replay detection support: N Status: ACTIVE inbound esp sas: spi: 0 x 6 F 220173(1864499571) transform: esp-3 des esp-md 5 -hmac , in use settings ={Tunnel, } conn id: 2001, flow_id: FPGA: 1, crypto map: VPN 2 sa timing: remaining key lifetime (k/sec): (4525504/2709) IV size: 16 bytes replay detection support: N Status: ACTIVE inbound ah sas: inbound pcp sas: inbound ah sas: Show crypto ipsec sa outbound esp sas: spi: 0 x 7 DCE 4 C 31(2110671921) transform: esp-3 des esp-md 5 -hmac , in use settings ={Tunnel, } conn id: 2010, flow_id: FPGA: 1, crypto map: VPN 1 sa timing: remaining key lifetime (k/sec): (4525504/2690) IV size: 16 bytes replay detection support: N Status: ACTIVE outbound ah sas: outbound pcp sas: 계속 inbound pcp sas: outbound esp sas: spi: 0 x 040 E 7 F 3 A(68058938) transform: esp-3 des esp-md 5 -hmac , in use settings ={Tunnel, } conn id: 2002, flow_id: FPGA: 1, crypto map: VPN 2 sa timing: remaining key lifetime (k/sec): (4525504/2709) IV size: 16 bytes replay detection support: N Status: ACTIVE outbound ah sas: outbound pcp sas:

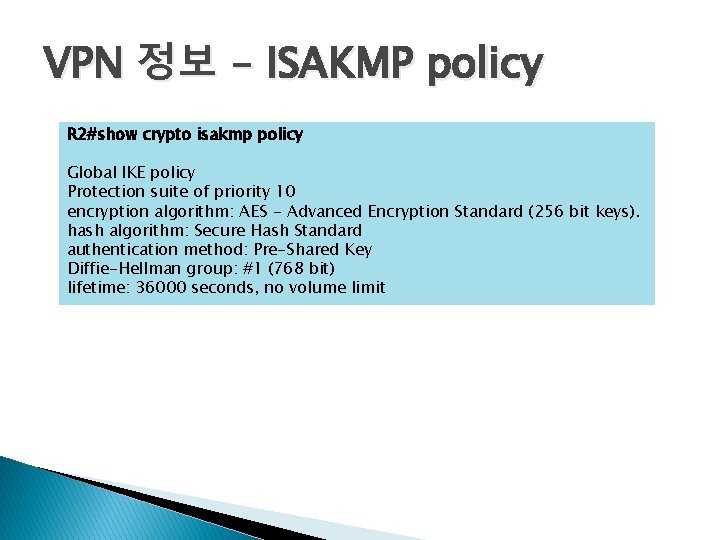
VPN 정보 – ISAKMP policy R 2#show crypto isakmp policy Global IKE policy Protection suite of priority 10 encryption algorithm: AES - Advanced Encryption Standard (256 bit keys). hash algorithm: Secure Hash Standard authentication method: Pre-Shared Key Diffie-Hellman group: #1 (768 bit) lifetime: 36000 seconds, no volume limit

VPN 정보 – ISAKMP sa R 1#show crypto isakmp sa IPv 4 Crypto ISAKMP SA dst src state conn-id slot status 203. 230. 9. 2 203. 230. 9. 1 QM_IDLE 1074 0 ACTIVE IPv 6 Crypto ISAKMP SA R 2#show crypto isakmp sa IPv 4 Crypto ISAKMP SA dst src state conn-id slot status 203. 230. 9. 1 203. 230. 9. 2 QM_IDLE 1010 0 ACTIVE 203. 230. 10. 2 203. 230. 1 QM_IDLE 1010 0 ACTIVE IPv 6 Crypto ISAKMP SA R 3#show crypto isakmp sa IPv 4 Crypto ISAKMP SA dst src state conn-id slot status 203. 230. 10. 2 QM_IDLE 1063 0 ACTIVE IPv 6 Crypto ISAKMP SA

VPN 정보 – crypto map R 2#show crypto map Crypto Map VPN 1 110 ipsec-isakmp Peer = 203. 230. 9. 1 Extended IP access list 110 access-list 110 permit gre host 203. 230. 9. 2 host 203. 230. 9. 1 Current peer: 203. 230. 9. 1 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): N Transform sets={ STRONG, } Interfaces using crypto map VPN 1: Serial 0/0/0 Crypto Map VPN 2 120 ipsec-isakmp Peer = 203. 230. 10. 2 Extended IP access list 120 access-list 120 permit gre host 203. 230. 10. 2 Current peer: 203. 230. 10. 2 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): N Transform sets={ STRONG, } Interfaces using crypto map VPN 2: Serial 0/0/1 R 1#show crypto map Crypto Map VPN 1 110 ipsec-isakmp Peer = 203. 230. 9. 2 Extended IP access list 110 access-list 110 permit gre host 203. 230. 9. 1 host 203. 230. 9. 2 Current peer: 203. 230. 9. 2 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): N Transform sets={ STRONG, } Interfaces using crypto map VPN 1: Serial 0/0/0 R 3#show crypto map Crypto Map VPN 2 120 ipsec-isakmp Peer = 203. 230. 1 Extended IP access list 120 access-list 120 permit gre host 203. 230. 10. 2 host 203. 230. 1 Current peer: 203. 230. 1 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): N Transform sets={ STRONG, } Interfaces using crypto map VPN 2: Serial 0/0/0



 Dynamic multipoint vpn
Dynamic multipoint vpn Generic routing encapsulation vpn
Generic routing encapsulation vpn Route sheets in ppc
Route sheets in ppc Route distinguisher vs route target
Route distinguisher vs route target Multichannel multipoint distribution service
Multichannel multipoint distribution service Prlc switchboard
Prlc switchboard Point to multipoint communication
Point to multipoint communication Multipoint control unit open source
Multipoint control unit open source Multipoint dashboard
Multipoint dashboard Multipoint competition theory
Multipoint competition theory Corporate strategy
Corporate strategy Retrenchment strategy
Retrenchment strategy Advantages and disadvantages of cup and bob viscometer
Advantages and disadvantages of cup and bob viscometer Ssl vpn vs ipsec
Ssl vpn vs ipsec Spispy
Spispy Service point addressing
Service point addressing Encapsulation tcp/ip
Encapsulation tcp/ip What is inline function
What is inline function Underfilling encapsulation protection solutions
Underfilling encapsulation protection solutions Jesse wu vmware
Jesse wu vmware Abstract data type c#
Abstract data type c# Encapsulation design pattern
Encapsulation design pattern Abstraction encapsulation inheritance polymorphism
Abstraction encapsulation inheritance polymorphism Contoh information hiding
Contoh information hiding Goals of computer network
Goals of computer network What is encapsulation?
What is encapsulation? Encapsulation of arp packet
Encapsulation of arp packet Encapsulation inheritance polymorphism
Encapsulation inheritance polymorphism Encapsulation decapsulation osi model
Encapsulation decapsulation osi model Encapsulation in ada
Encapsulation in ada Contoh encapsulation
Contoh encapsulation Geneve encapsulation
Geneve encapsulation Domain separation cybersecurity
Domain separation cybersecurity Encapsulation osi
Encapsulation osi Isl encapsulation
Isl encapsulation Encapsulation
Encapsulation Oop inheritance polymorphism encapsulation abstraction
Oop inheritance polymorphism encapsulation abstraction Four principles of oop
Four principles of oop Encapsulation constructs in ppl
Encapsulation constructs in ppl Encapsulation in java
Encapsulation in java Oop encapsulation inheritance polymorphism
Oop encapsulation inheritance polymorphism Encapsulation programming
Encapsulation programming Dsl architecture
Dsl architecture Encapsulation inheritance polymorphism
Encapsulation inheritance polymorphism Free route airspace czech republic
Free route airspace czech republic Benzodiazepine receptor agonist
Benzodiazepine receptor agonist En route vers le secondaire
En route vers le secondaire Impression formation
Impression formation Route
Route Pourquoi le poulet a-t-il traversé la route
Pourquoi le poulet a-t-il traversé la route