Voice Over IP Security Mark D Collier Chief








![SIP Enumeration Directory Scanning Gathering Information Enumeration [root@attacker]# nc 192. 168. 1. 104 5060 SIP Enumeration Directory Scanning Gathering Information Enumeration [root@attacker]# nc 192. 168. 1. 104 5060](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-31.jpg)

![Gathering Information Enumeration TFTP Enumeration Using TFTPBRUTE [root@attacker]# perl tftpbrute. pl 192. 168. 1. Gathering Information Enumeration TFTP Enumeration Using TFTPBRUTE [root@attacker]# perl tftpbrute. pl 192. 168. 1.](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-34.jpg)
![SNMP Enumeration snmpwalk Gathering Information Enumeration [root@domain 2 ~]# snmpwalk -c public -v 1 SNMP Enumeration snmpwalk Gathering Information Enumeration [root@domain 2 ~]# snmpwalk -c public -v 1](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-38.jpg)


























- Slides: 112

Voice Over IP Security Mark D. Collier Chief Technology Officer Secure. Logix Corporation mark. collier@securelogix. com David Endler Director of Security Research Tipping. Point dendler@tippingpoint. com

Outline Overview Gathering Information: u Footprinting u Scanning u Enumeration Attacking the Network: u Network Infrastructure Denial of Service u Network Eavesdropping u Network and Application Interception Outline

Outline Attacking Vendor Platforms: u Avaya u Cisco Attacking the Application: u Fuzzing u Disruption of Service u Signaling and Media Manipulation Social Attacks: u Voice SPAM/SPIT u Voice Phishing Outline

Introduction Vo. IP systems are vulnerable: u Platforms, networks, and applications are vulnerable u Vo. IP-specific attacks are becoming more common u Security isn’t always a consideration during deployment The threat is increasing: u Vo. IP deployment is growing u Deployments are critical to business operations u Greater integration with the data network u More attack tools being published u The hacking community is taking notice

Gathering Information This is the process a hacker goes through to gather information about your organization and prepare their attack Consists of: u Footprinting u Scanning u Enumeration

Footprinting Gathering Information Footprinting Steps taken by a hacker to learn about your enterprise before they start the actual attack Consists of: u Public website research u Google hacking

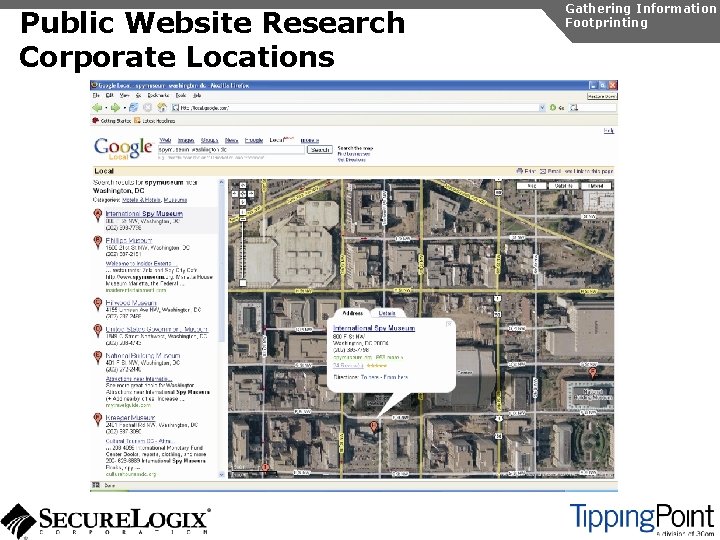
Public Website Research Introduction Gathering Information Footprinting An enterprise website often contains a lot of information that is useful to a hacker: u Organizational structure and corporate locations u Help and technical support u Job listings u Phone numbers and extensions

Public Website Research Corporate Locations Gathering Information Footprinting

Public Website Research Job Listings Gathering Information Footprinting Job listings can contain a ton of information about the enterprise Vo. IP system. Here is a portion of an actual job listing: Required Technical Skills: Minimum 3 -5 years experience in the management and implementation of Avaya telephone systems/voicemails: * Advanced programming knowledge of the Avaya Communication Servers and voicemails.

Public Website Research Phone Numbers Gathering Information Footprinting Google can be used to find all phone numbers on an enterprise web site: u Type: “ 111. . 999 -1000. . 9999 site: www. mcgraw-hill. com”

Public Website Research Voice Mail Gathering Information Footprinting By calling into some of these numbers, you can listen to the voice mail system and determine the vendor Check out our voice mail hacking database at: u www. hackingvoip. com

Public Website Research Countermeasures Gathering Information Footprinting It is difficult to control what is on your enterprise website, but it is a good idea to be aware of what is on it Try to limit amount of detail in job postings Remove technical detail from help desk web pages

Google Hacking Introduction Gathering Information Footprinting Google is incredibly good at finding details on the web: u Vendor press releases and case studies u Resumes of Vo. IP personnel u Mailing lists and user group postings u Web-based Vo. IP logins

Google Hacking Gathering Information Footprinting Vendors and enterprises may post press releases and case studies: u Type: “site: avaya. com case study” or “site: avaya. company” Users place resumes on the Internet when searching for jobs u Search Monster for resumes for company employees Mailing lists and user group postings: u www. inuaa. org u www. innua. org u forums. cisco. com u forums. digium. com

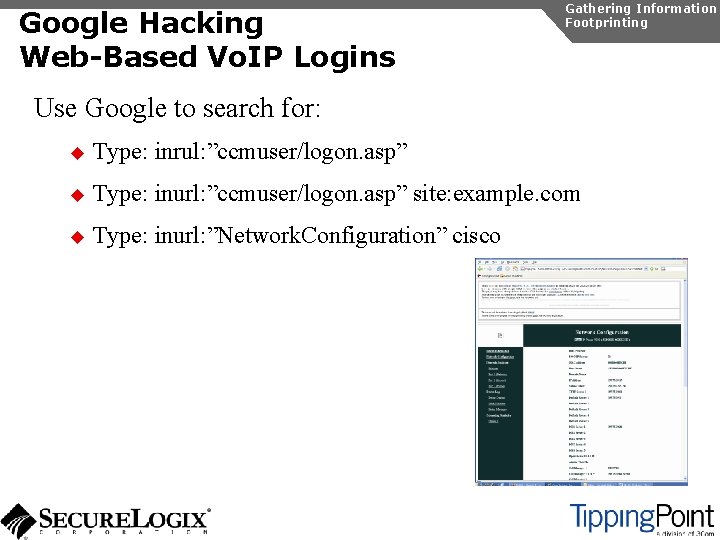
Google Hacking Web-Based Vo. IP Logins Gathering Information Footprinting Use Google to search for: u Type: inrul: ”ccmuser/logon. asp” u Type: inurl: ”ccmuser/logon. asp” site: example. com u Type: inurl: ”Network. Configuration” cisco

Google Hacking Countermeasures Gathering Information Footprinting Determine what your exposure is Be sure to remove any Vo. IP phones which are visible to the Internet Disable the web servers on your IP phones There are services that can help you monitor your exposure: u www. cyveilance. com u ww. baytsp. com

Scanning Introduction Gathering Information Scanning Steps taken by a hacker to identify IP addresses and hosts running Vo. IP Consists: u Gaining access u Host/device discovery and identification u Port scanning and service discovery

Scanning Gaining Access Attacking The Network Gaining Access Several attack vectors include: u Installing a simple wired hub u Wi-Fi sniffing u Compromising a network node u Compromising a Vo. IP phone u Compromising a switch u Compromising a proxy, gateway, or PC/softphone u ARP poisoning u Circumventing VLANs

Host/Device Discovery and Identification Gathering Information Scanning Consists of various techniques used to find hosts: u Ping sweeps u ARP pings u TCP ping scans u SNMP sweeps After hosts are found, the type of device can be determined Classifies host/device by operating system Network stack fingerprinting is a common technique for identifying hosts/devices

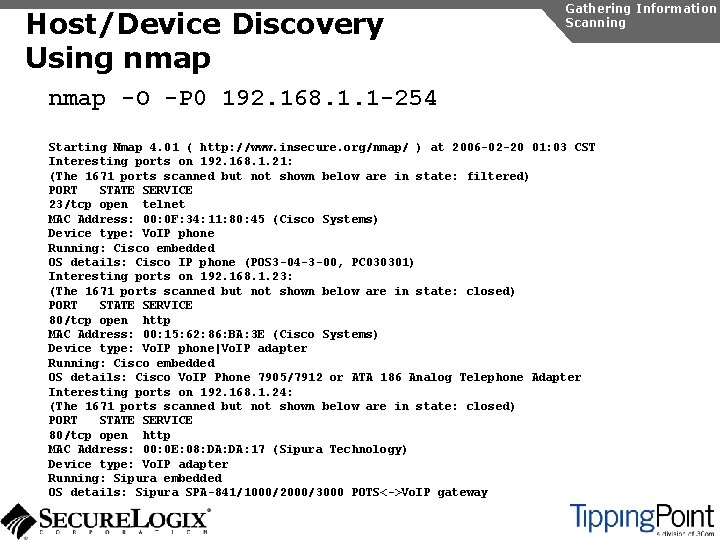
Host/Device Discovery Using nmap Gathering Information Scanning nmap -O -P 0 192. 168. 1. 1 -254 Starting Nmap 4. 01 ( http: //www. insecure. org/nmap/ ) at 2006 -02 -20 01: 03 CST Interesting ports on 192. 168. 1. 21: (The 1671 ports scanned but not shown below are in state: filtered) PORT STATE SERVICE 23/tcp open telnet MAC Address: 00: 0 F: 34: 11: 80: 45 (Cisco Systems) Device type: Vo. IP phone Running: Cisco embedded OS details: Cisco IP phone (POS 3 -04 -3 -00, PC 030301) Interesting ports on 192. 168. 1. 23: (The 1671 ports scanned but not shown below are in state: closed) PORT STATE SERVICE 80/tcp open http MAC Address: 00: 15: 62: 86: BA: 3 E (Cisco Systems) Device type: Vo. IP phone|Vo. IP adapter Running: Cisco embedded OS details: Cisco Vo. IP Phone 7905/7912 or ATA 186 Analog Telephone Adapter Interesting ports on 192. 168. 1. 24: (The 1671 ports scanned but not shown below are in state: closed) PORT STATE SERVICE 80/tcp open http MAC Address: 00: 0 E: 08: DA: 17 (Sipura Technology) Device type: Vo. IP adapter Running: Sipura embedded OS details: Sipura SPA-841/1000/2000/3000 POTS<->Vo. IP gateway

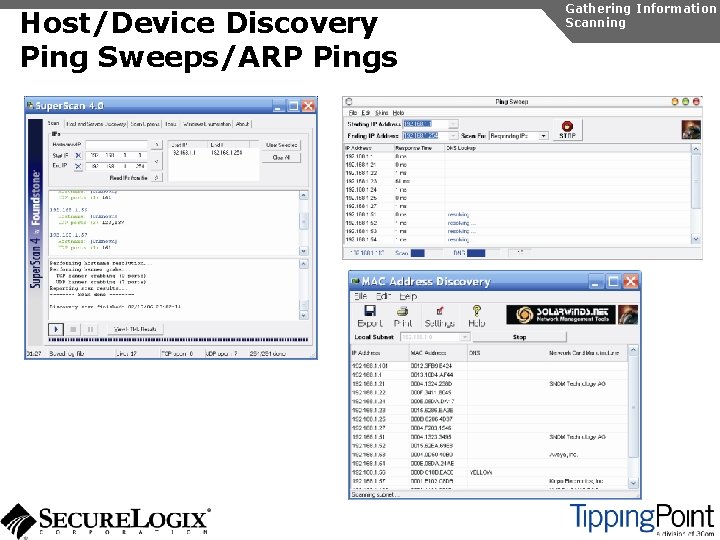
Host/Device Discovery Ping Sweeps/ARP Pings Gathering Information Scanning

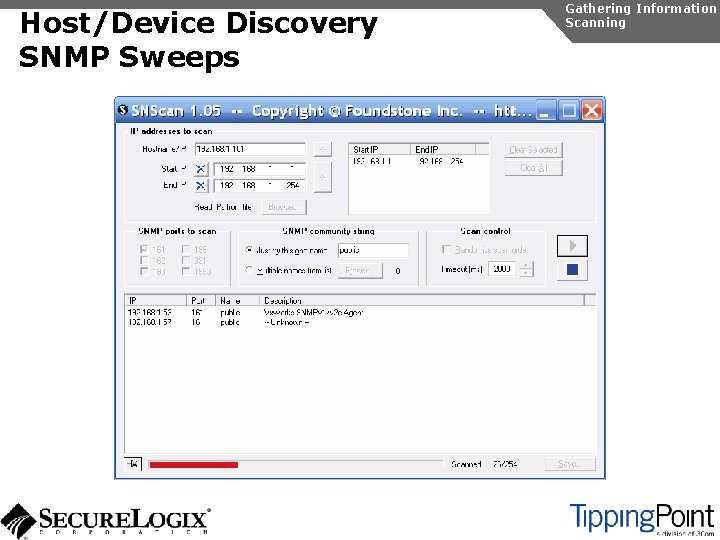
Host/Device Discovery SNMP Sweeps Gathering Information Scanning

Host/Device Discovery Countermeasures Gathering Information Scanning Use firewalls and Intrusion Prevention Systems (IPSs) to block ping and TCP sweeps VLANs can help isolate ARP pings Ping sweeps can be blocked at the perimeter firewall Use secure (SNMPv 3) version of SNMP Change SNMP public strings

Port Scanning/Service Discovery Gathering Information Scanning Consists of various techniques used to find open ports and services on hosts These ports can be targeted later nmap is the most commonly used tool for TCP SYN and UDP scans

Port Scanning/Service Discovery Countermeasures Gathering Information Scanning Using non-Internet routable IP addresses will prevent external scans Firewalls and IPSs can detect and possibly block scans VLANs can be used to partition the network to prevent scans from being effective

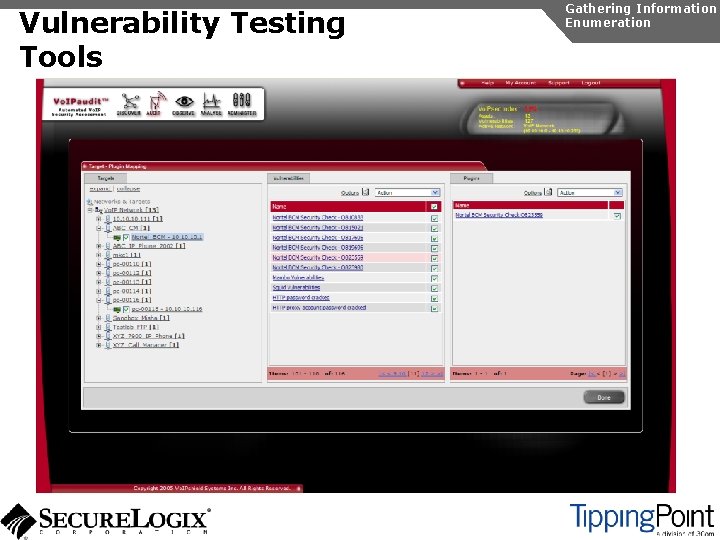
Enumeration Introduction Gathering Information Enumeration Involves testing open ports and services on hosts/devices to gather more information Includes running tools to determine if open services have known vulnerabilities Also involves scanning for Vo. IP-unique information such as phone numbers Includes gathering information from TFTP servers and SNMP

Vulnerability Testing Tools Gathering Information Enumeration

Vulnerability Testing Tools Gathering Information Enumeration

Vulnerability Testing Tools Gathering Information Enumeration

Vulnerability Testing Countermeasures Gathering Information Enumeration The best solution is to upgrade your applications and make sure you continually apply patches Some firewalls and IPSs can detect and mitigate vulnerability scans
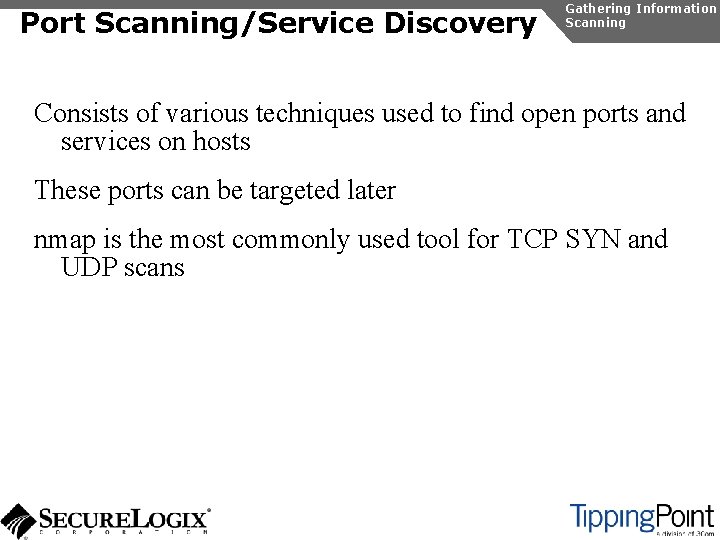
![SIP Enumeration Directory Scanning Gathering Information Enumeration rootattacker nc 192 168 1 104 5060 SIP Enumeration Directory Scanning Gathering Information Enumeration [root@attacker]# nc 192. 168. 1. 104 5060](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-31.jpg)
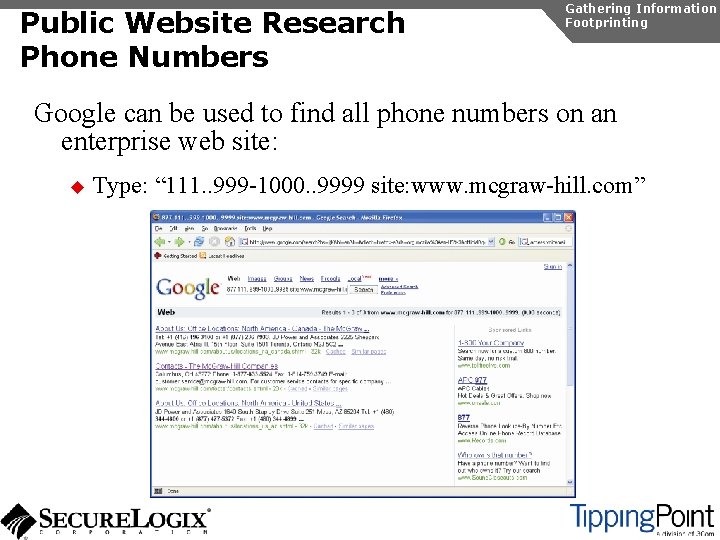
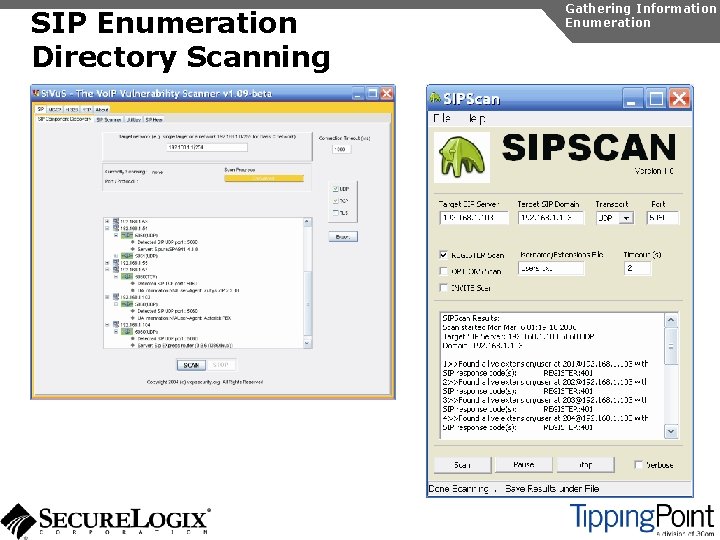
SIP Enumeration Directory Scanning Gathering Information Enumeration [root@attacker]# nc 192. 168. 1. 104 5060 OPTIONS sip: test@192. 168. 1. 104 SIP/2. 0 Via: SIP/2. 0/TCP 192. 168. 1. 120; branch=4 iv. Bc. Vj 5 Zn. PYgb To: alice <sip: test@192. 168. 1. 104> Content-Length: 0 SIP/2. 0 404 Not Found Via: SIP/2. 0/TCP 192. 168. 1. 120; branch=4 iv. Bc. Vj 5 Zn. PYgb; received=192. 168. 1. 103 To: alice sip: test@192. 168. 1. 104>; tag=b 27 e 1 a 1 d 33761 e 85846 fc 98 f 5 f 3 a 7 e 58. 0503 Server: Sip EXpress router (0. 9. 6 (i 386/linux)) Content-Length: 0 Warning: 392 192. 168. 1. 104: 5060 "Noisy feedback tells: pid=29801 req_src_ip=192. 168. 1. 120 req_src_port=32773 in_uri=sip: test@192. 168. 1. 104 out_uri=sip: test@192. 168. 1. 104 via_cnt==1"

SIP Enumeration Directory Scanning Gathering Information Enumeration

TFTP Enumeration Introduction Gathering Information Enumeration Almost all phones we tested use TFTP to download their configuration files The TFTP server is rarely well protected If you know or can guess the name of a configuration or firmware file, you can download it without even specifying a password The files are downloaded in the clear and can be easily sniffed Configuration files have usernames, passwords, IP addresses, etc. in them
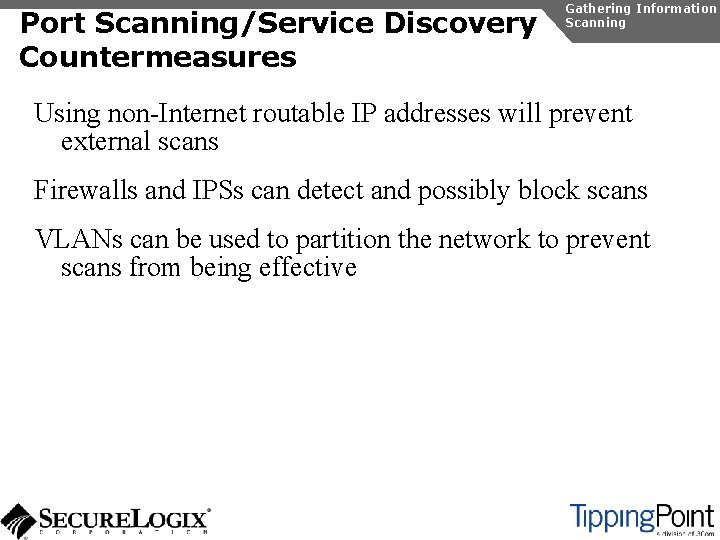
![Gathering Information Enumeration TFTP Enumeration Using TFTPBRUTE rootattacker perl tftpbrute pl 192 168 1 Gathering Information Enumeration TFTP Enumeration Using TFTPBRUTE [root@attacker]# perl tftpbrute. pl 192. 168. 1.](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-34.jpg)
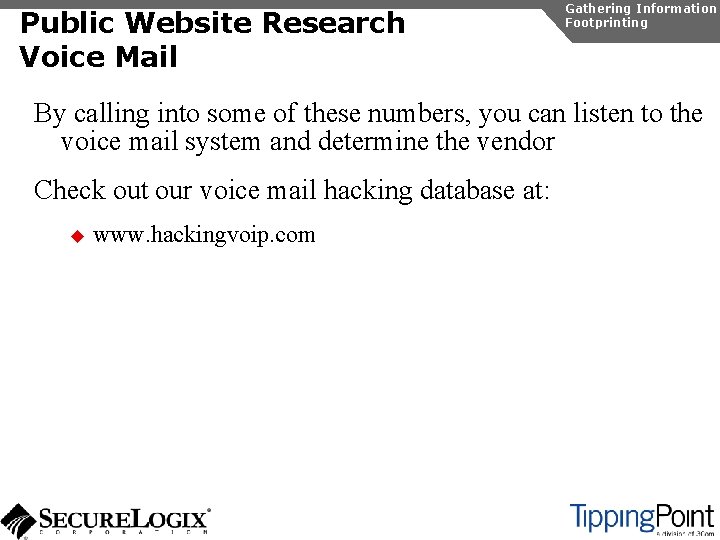
Gathering Information Enumeration TFTP Enumeration Using TFTPBRUTE [root@attacker]# perl tftpbrute. pl 192. 168. 1. 103 brutefile. txt 100 tftpbrute. pl, , V 0. 1 TFTP file word database: brutefile. txt TFTP server 192. 168. 1. 103 Max processes 100 Processes are: 1 <snip> Processes are: 12 *** Found TFTP server remote filename Processes are: 13 Processes are: 14 *** Found TFTP server remote filename : sip. cfg : 46 xxsettings. txt : sip_4602 D 02 A. txt : XMLDefault. cnf. xml : Sip. Default. cnf

TFTP Enumeration Countermeasures Gathering Information Enumeration It is difficult not to use TFTP, since it is so commonly used by Vo. IP vendors Some vendors offer more secure alternatives Firewalls can be used to restrict access to TFTP servers to valid devices

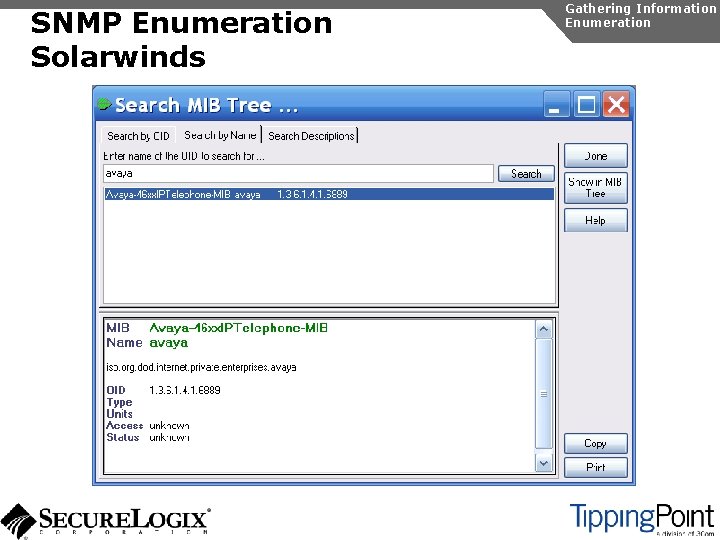
SNMP Enumeration Introduction Gathering Information Enumeration SNMP is enabled by default on most IP PBXs and IP phones Simple SNMP sweeps will garner lots of useful information If you know the device type, you can use snmpwalk with the appropriate OID You can find the OID using Solarwinds MIB Default “passwords”, called community strings, are common

SNMP Enumeration Solarwinds Gathering Information Enumeration
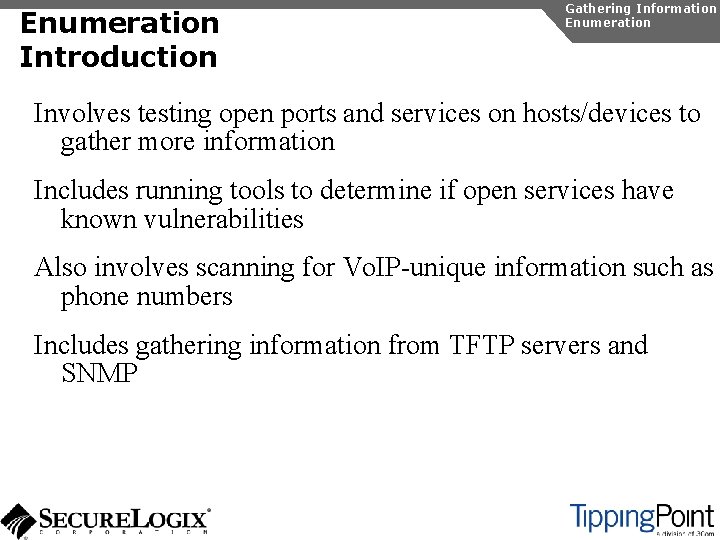
![SNMP Enumeration snmpwalk Gathering Information Enumeration rootdomain 2 snmpwalk c public v 1 SNMP Enumeration snmpwalk Gathering Information Enumeration [root@domain 2 ~]# snmpwalk -c public -v 1](https://slidetodoc.com/presentation_image_h2/57d2fc5797dd2844925da10e5869e92d/image-38.jpg)
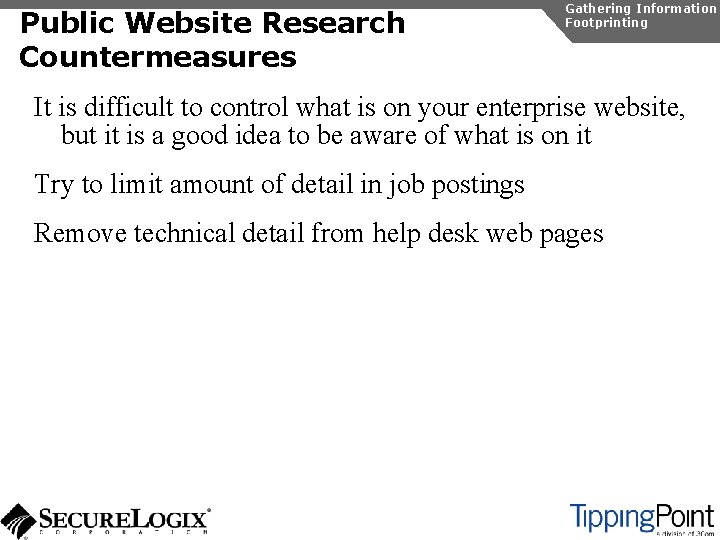
SNMP Enumeration snmpwalk Gathering Information Enumeration [root@domain 2 ~]# snmpwalk -c public -v 1 192. 168. 1. 53 1. 3. 6. 1. 4. 1. 6889 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 1. 0 = STRING: "Obsolete" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 2. 0 = STRING: "4620 D 01 B" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 3. 0 = STRING: "Avaya. Callserver" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 4. 0 = Ip. Address: 192. 168. 1. 103 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 5. 0 = INTEGER: 1719 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 6. 0 = STRING: "051612501065" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 7. 0 = STRING: "700316698" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 8. 0 = STRING: "051611403489" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 9. 0 = STRING: "00: 04: 0 D: 50: 40: B 0" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 10. 0 = STRING: "100" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 11. 0 = Ip. Address: 192. 168. 1. 53 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 12. 0 = INTEGER: 0 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 13. 0 = INTEGER: 0 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 14. 0 = INTEGER: 0 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 15. 0 = STRING: "192. 168. 1. 1" SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 16. 0 = Ip. Address: 192. 168. 1. 1 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 1. 17. 0 = Ip. Address: 255. 0. . . SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 4. 8. 0 = INTEGER: 20 SNMPv 2 -SMI: : enterprises. 6889. 2. 69. 1. 4. 9. 0 = STRING: "503"

SNMP Enumeration Countermeasures Gathering Information Enumeration Disable SNMP on any devices where it is not needed Change default public and private community strings Try to use SNMPv 3, which supports authentication

Attacking The Network The Vo. IP network and supporting infrastructure are vulnerable to attacks Most attacks will originate inside the network, once access is gained Attacks include: u Network infrastructure Do. S u Network eavesdropping u Network and application interception

Attacking The Network Gaining Access Some techniques for circumventing VLANs: u Without MAC filtering, disconnect a phone and connect a PC u Even if MAC filtering is used, you can easily spoof the MAC u Be especially cautious of Vo. IP phones in public areas Some other VLAN attacks: u MAC flooding attack u 802. 1 q and ISL tagging attack u Double-encapsulated 802. 1 q/Nested VLAN attack u Private VLAN attack u Spanning-tree protocol attack/VLAN trunking protocol attack

Network Infrastructure Do. S Attacking The Network Do. S The Vo. IP network and supporting infrastructure are vulnerable to attacks Vo. IP media/audio is particularly susceptible to any Do. S attack which introduces latency and jitter Attacks include: u Flooding attacks u Network availability attacks u Supporting infrastructure attacks

Flooding Attacks Introduction Attacking The Network Do. S Flooding attacks generate so many packets at a target, that it is overwhelmed and can’t process legitimate requests

Flooding Attacks Types of Floods Some types of floods are: u UDP floods u TCP SYN floods u ICMP and Smurf floods u Worm and virus oversubscription side effect u Qo. S manipulation u Application flooding Attacking The Network Do. S

Flooding Attacks Countermeasures Attacking The Network Do. S Layer 2 and 3 Qo. S mechanisms are commonly used to give priority to Vo. IP media (and signaling) Use rate limiting in network switches Use anti-Do. S/DDo. S products Some vendors have Do. S support in their products (in newer versions of software)

Network Availability Attacks Attacking The Network Do. S This type of attack involves an attacker trying to crash the underlying operating system: u Fuzzing involves sending malformed packets, which exploit a weakness in software u Packet fragmentation u Buffer overflows

Network Availability Attacks Countermeasures Attacking The Network Do. S A network IPS is an inline device that detects and blocks attacks Some firewalls also offer this capability Host based IPS software also provides this capability

Supporting Infrastructure Attacks Attacking The Network Do. S Vo. IP systems rely heavily on supporting services such as DHCP, DNS, TFTP, etc. DHCP exhaustion is an example, where a hacker uses up all the IP addresses, denying service to Vo. IP phones DNS cache poisoning involves tricking a DNS server into using a fake DNS response

Supporting Infrastructure Attacks Countermeasures Attacking The Network Do. S Configure DHCP servers not to lease addresses to unknown MAC addresses DNS servers should be configured to analyze info from nonauthoritative servers and dropping any response not related to queries

Network Eavesdropping Introduction Attacking The Network Eavesdropping Vo. IP configuration files, signaling, and media are vulnerable to eavesdropping Attacks include: u TFTP configuration file sniffing (already discussed) u Number harvesting and call pattern tracking u Conversation eavesdropping

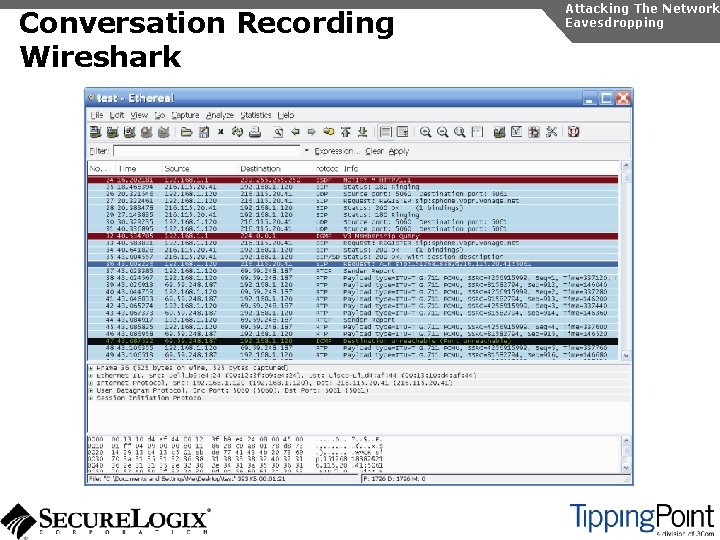
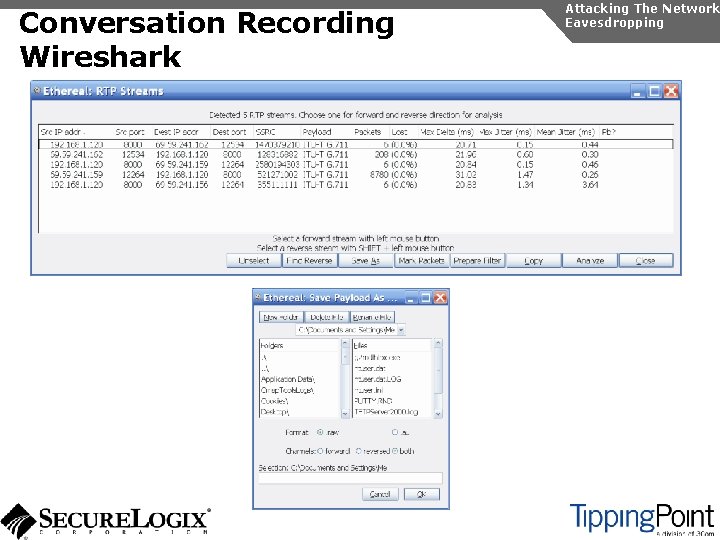
Numbers/Call Patterns Attacking The Network Eavesdropping By sniffing signaling, it is possible to build a directory of numbers and track calling patterns voipong automates the process of logging all calls Wireshark is very good at sniffing Vo. IP signaling

Conversation Recording Wireshark Attacking The Network Eavesdropping

Conversation Recording Wireshark Attacking The Network Eavesdropping

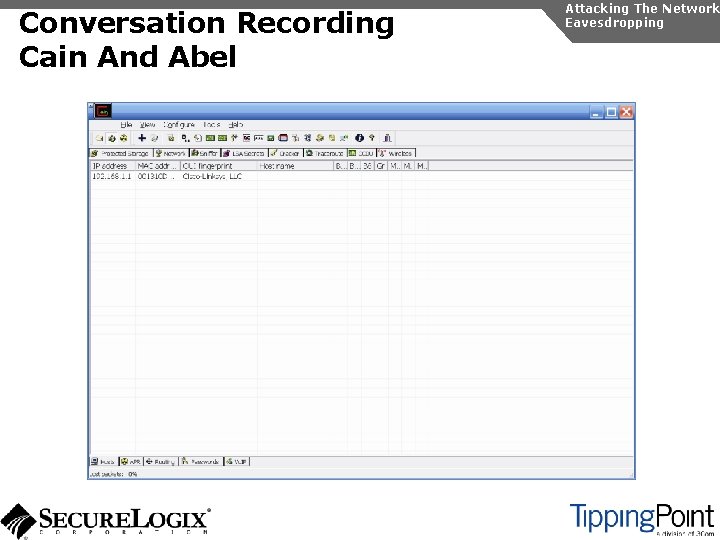
Conversation Recording Cain And Abel Attacking The Network Eavesdropping

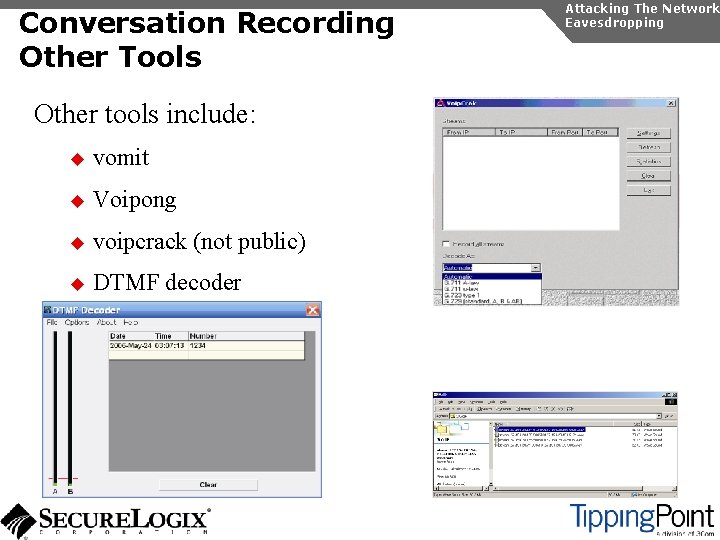
Conversation Recording Other Tools Other tools include: u vomit u Voipong u voipcrack (not public) u DTMF decoder Attacking The Network Eavesdropping

Network Eavesdropping Countermeasures Attacking The Network Eavesdropping Use encryption: u Many vendors offer encryption for signaling u Use the Transport Layer Security (TLS) for signaling u Many vendors offer encryption for media u Use Secure Real-time Transport Protocol (SRTP) u Use ZRTP u Use proprietary encryption if you have to

Network/Application Interception Introduction Attacking The Network Net/App Interception The Vo. IP network is vulnerable to Man-In-The-Middle (MITM) attacks, allowing: u Eavesdropping on the conversation u Causing a Do. S condition u Altering the conversation by omitting, replaying, or inserting media u Redirecting calls Attacks include: u Network-level interception u Application-level interception

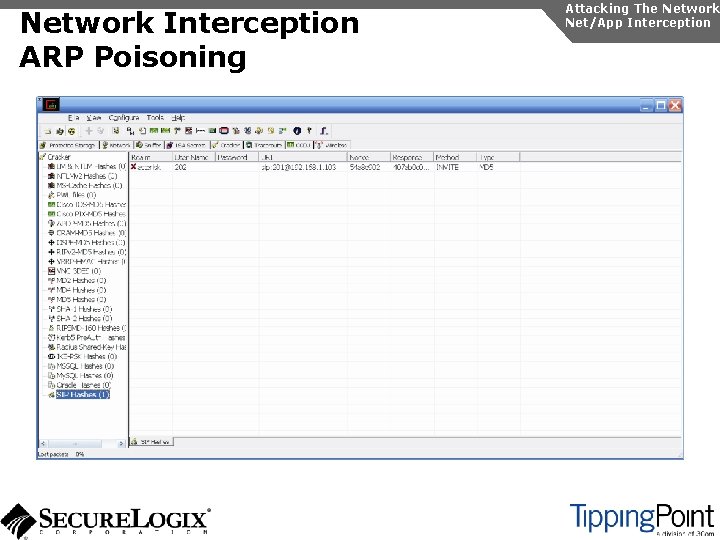
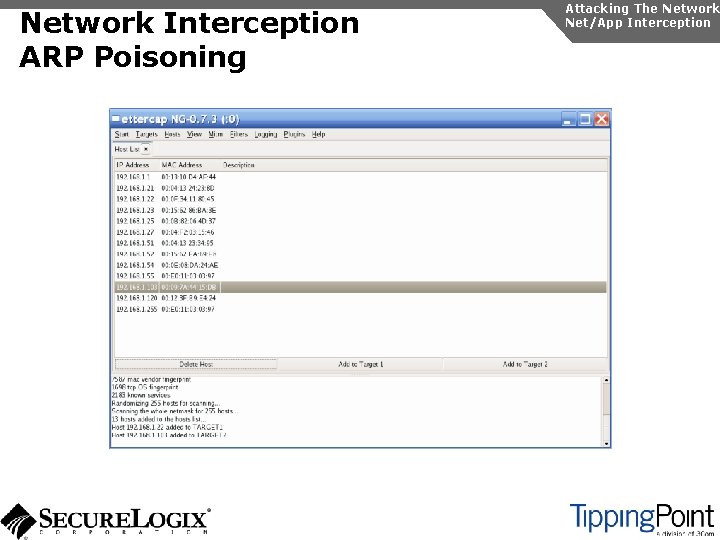
Network Interception ARP Poisoning Attacking The Network Net/App Interception The most common network-level MITM attack is ARP poisoning Involves tricking a host into thinking the MAC address of the attacker is the intended address There a number of tools available to support ARP poisoning: u Cain and Abel u ettercap u Dsniff u hunt

Network Interception ARP Poisoning Attacking The Network Net/App Interception

Network Interception ARP Poisoning Attacking The Network Net/App Interception

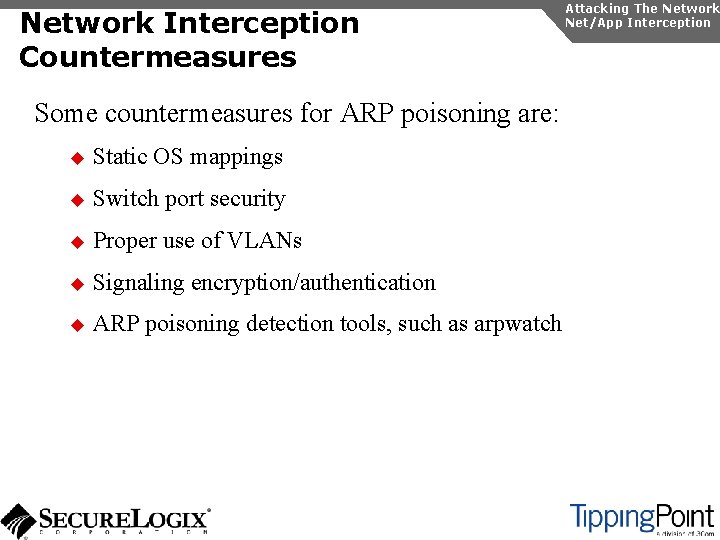
Network Interception Countermeasures Some countermeasures for ARP poisoning are: u Static OS mappings u Switch port security u Proper use of VLANs u Signaling encryption/authentication u ARP poisoning detection tools, such as arpwatch Attacking The Network Net/App Interception

Attacking The Platform This section describes unique attacks against specific Vo. IP vendor platforms, including: u Avaya u Cisco

Avaya Communication Manager Attacking The Platform Avaya The Avaya Communication Manager is Avaya’s enterpriseclass offering Offers strong security, but some default configuration should be changed Avaya uses Linux and Vx. Works as the underlying operating system on many components, which is arguably more secure than Windows

Avaya Communication Manager Attacking The Platform Avaya

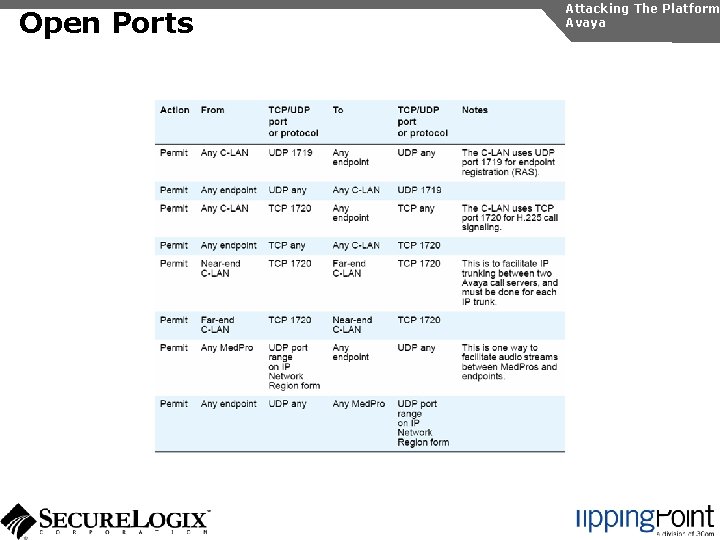
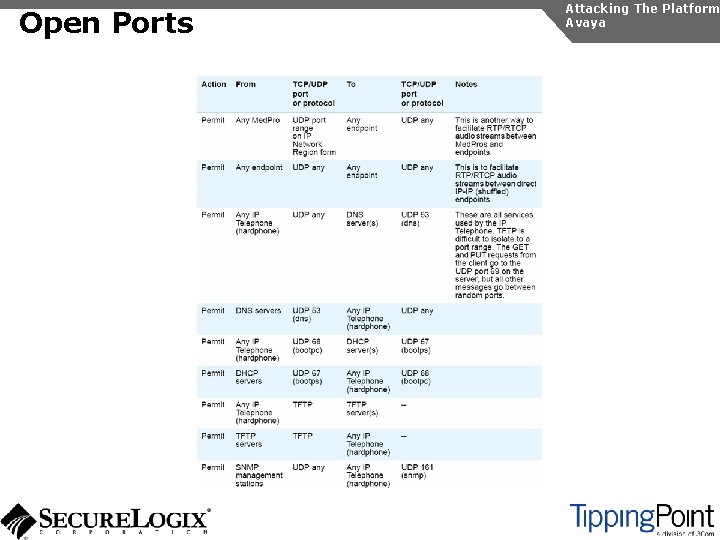
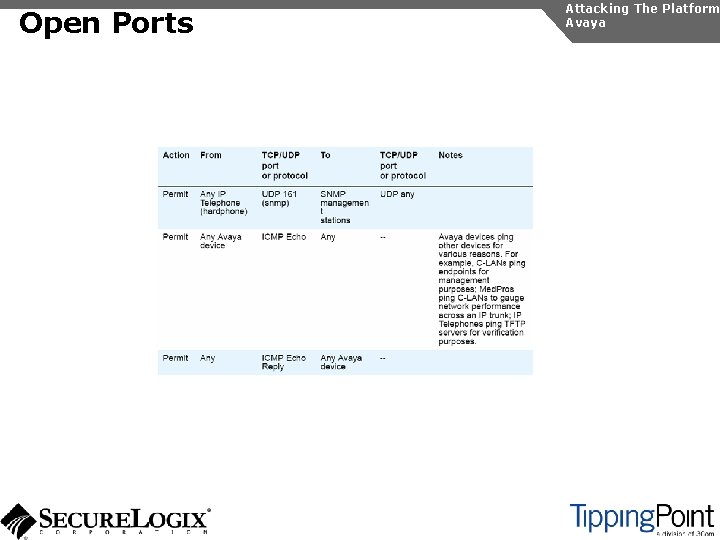
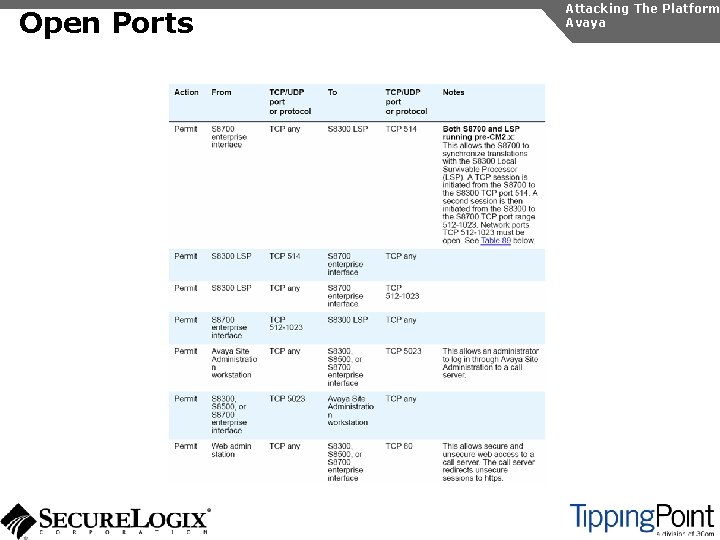
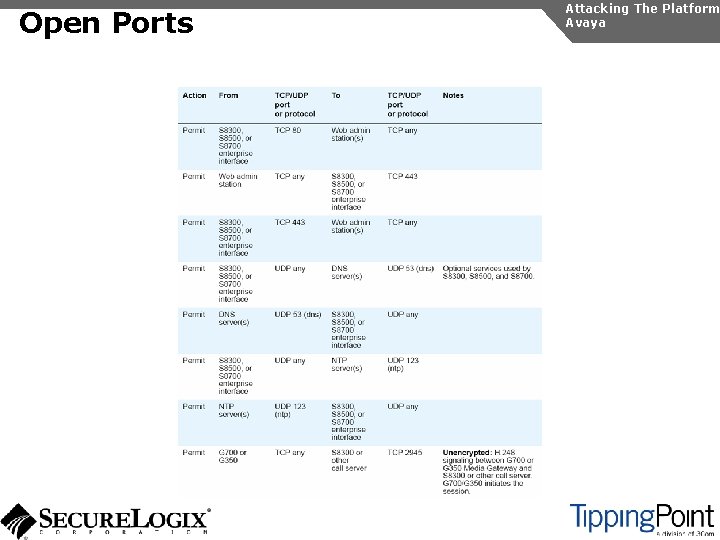
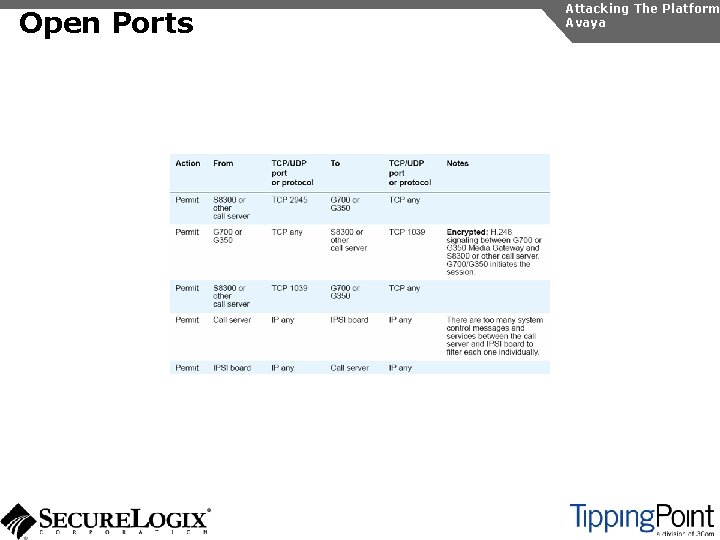
Open Ports Attacking The Platform Avaya

Open Ports Attacking The Platform Avaya

Open Ports Attacking The Platform Avaya

Open Ports Attacking The Platform Avaya

Open Ports Attacking The Platform Avaya

Open Ports Attacking The Platform Avaya

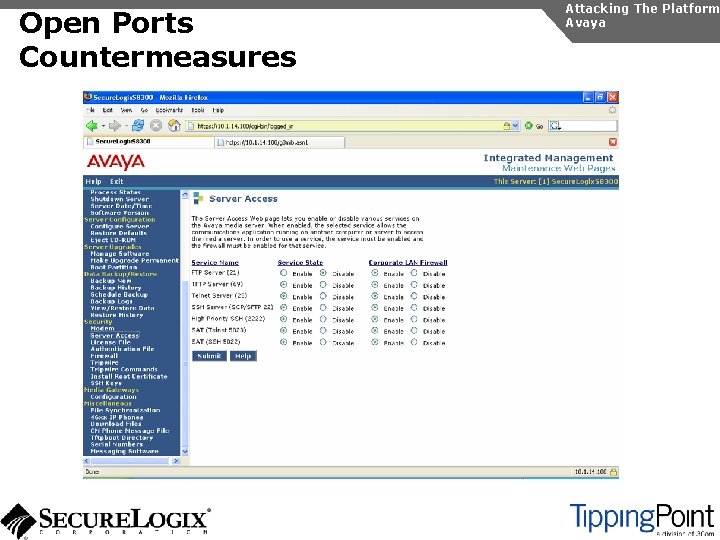
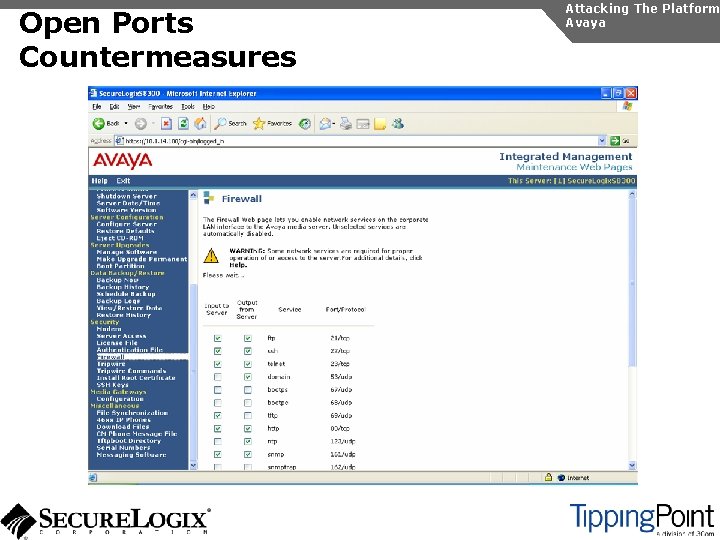
Open Ports Countermeasures Attacking The Platform Avaya

Open Ports Countermeasures Attacking The Platform Avaya

SNMP and TFTP Attacking The Platform Avaya uses TFTP and SNMP In 3. 0, SNMP is enabled by default on the IP PBX and IP phones Some components ship with default public and private community strings

SNMP and TFTP Countermeasures Attacking The Platform Avaya Use the same countermeasures as before Avaya provides a secure copy feature as an alternative to TFTP Communication Manager 4. 0 disables SNMP by default Version 2. 6 for IP phones does not ship with default community strings

Flooding Attacks Attacking The Platform Avaya We used udpflood and tcpsynflood to perform Do. S attacks against various components Unfortunately, these attacks were very disruptive

Flooding Attacks Countermeasures Attacking The Platform Avaya Use the same countermeasures as before Avaya C-LAN cards provide some level of Do. S mitigation Newer IP phone software provides better Do. S mitigation http: //support. avaya. com/security

Miscellaneous Security Issues Attacking The Platform Avaya signaling and media are vulnerable to eavesdropping Avaya uses some default passwords on key IP PBX components Password recommendations for IP phones are weak By default, Avaya IP phones can be reconfigured when booted

Miscellaneous Security Issues Countermeasures Attacking The Platform Avaya supports proprietary encryption for signaling and media. SRTP will be supported in Communication Manager 4. 0 Default passwords should be changed to strong values Local access to the IP phone can be controlled with a password

Cisco Unified Call Manager Attacking The Platform Avaya The Cisco Unified Call Manager is Cisco’s enterprise class offering Offers strong security, but requires some configuration Version 4. 1 is based on Windows. Version 5. 0 is based on Linux A Must Read Document is the Solution Reference Network Design (SRND) for Voice communications. (http: //tinyurl. com/gd 5 r 4). Includes great deployment scenarios and security use cases (lobby phone, desktop phone, call manager encryption how-to, etc. )

Cisco Introduction Attacking The Platform Cisco

Cisco Discovery Protocol Attacking The Platform Cisco Discovery Protocol – Cisco’s proprietary layer 2 network management protocol. Contains juicy information that is broadcast on the entire segment

Port Scanning Attacking The Platform Cisco Unified Call Manager requires a large number of open ports

Port Scanning Countermeasures Attacking The Platform Cisco IOS has a great feature called “autosecure” that” u disables a slew of services (finger, http, ICMP, source routing, etc. ) u enables some services (password encryption, TCP synwait-time, logging, etc. ). u And locks down the router and switch (enables only ssh, blocks private address blocks from traversing, enables netflow, etc. )

Flooding Countermeasures Attacking The Platform Cisco Network Flooding Countermeasures: u Another great feature from Cisco is Auto. Qos, a new IOS feature (auto qos command). u Enables Quality of Service for Vo. IP traffic across every Cisco router and switch u Scavenger class Qo. S also a relatively new Cisco strategy – rate shape all bursty non-Vo. IP traffic

Do. S and OS Exploitation Countermeasures Attacking The Platform Cisco Patch Management is key – use the Cisco Voice Technology Group Subscription Tool (http: //www. cisco. com/cgibin/Software/Newsbuilder/Builder/VOICE. cgi)

Eavesdropping and Interception Countermeasures Attacking The Platform Cisco Eavesdropping and Interception Countermeasures: u Enable port security on Cisco Switches to help mitigate ARP Spoofing u Enable Dynamic ARP inspection to thwart ARP Spoofing u Dynamically restrict Ethernet port access with 802. 1 x port authentication u Enable DHCP Snooping to prevent DHCP Spoofing u Configure IP source guard on Switches

Eavesdropping and Interception Countermeasures Attacking The Platform Cisco Eavesdropping and Interception Countermeasures: u Configure VTP Transparent Mode u Change the default Native VLAN Value to thwart VLAN hopping u Disable Dynamic Trunk Protocol (DTP) to thwart VLAN Hopping

Eavesdropping and Interception Countermeasures Attacking The Platform Cisco Eavesdropping and Interception Countermeasures: u Activate authentication and encryption of the signaling and media streams u Skinny over TLS u SRTP u Requires creating and distributing certificates on phones

Attacking The Application Vo. IP systems are vulnerable to application attacks against the various Vo. IP protocols Attacks include: u Fuzzing attacks u Flood-based Do. S u Signaling and media manipulation

Fuzzing Introduction Attacking The Application Fuzzing describes attacks where malformed packets are sent to a Vo. IP system in an attempt to crash it Research has shown that Vo. IP systems, especially those employing SIP, are vulnerable to fuzzing attacks

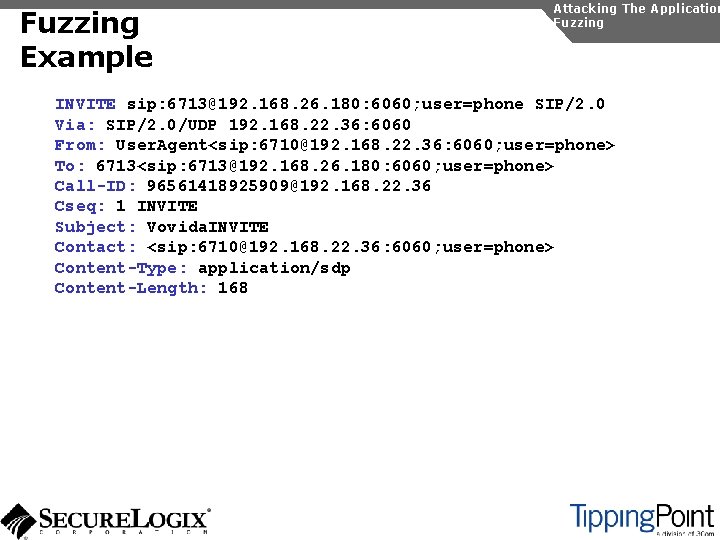
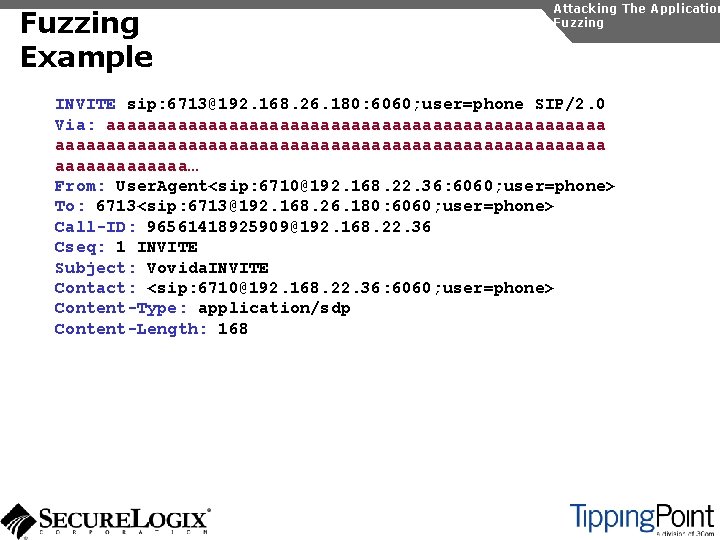
Fuzzing Example Attacking The Application Fuzzing INVITE sip: 6713@192. 168. 26. 180: 6060; user=phone SIP/2. 0 Via: SIP/2. 0/UDP 192. 168. 22. 36: 6060 From: User. Agent<sip: 6710@192. 168. 22. 36: 6060; user=phone> To: 6713<sip: 6713@192. 168. 26. 180: 6060; user=phone> Call-ID: 96561418925909@192. 168. 22. 36 Cseq: 1 INVITE Subject: Vovida. INVITE Contact: <sip: 6710@192. 168. 22. 36: 6060; user=phone> Content-Type: application/sdp Content-Length: 168

Fuzzing Example Attacking The Application Fuzzing INVITE sip: 6713@192. 168. 26. 180: 6060; user=phone SIP/2. 0 Via: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa… From: User. Agent<sip: 6710@192. 168. 22. 36: 6060; user=phone> To: 6713<sip: 6713@192. 168. 26. 180: 6060; user=phone> Call-ID: 96561418925909@192. 168. 22. 36 Cseq: 1 INVITE Subject: Vovida. INVITE Contact: <sip: 6710@192. 168. 22. 36: 6060; user=phone> Content-Type: application/sdp Content-Length: 168

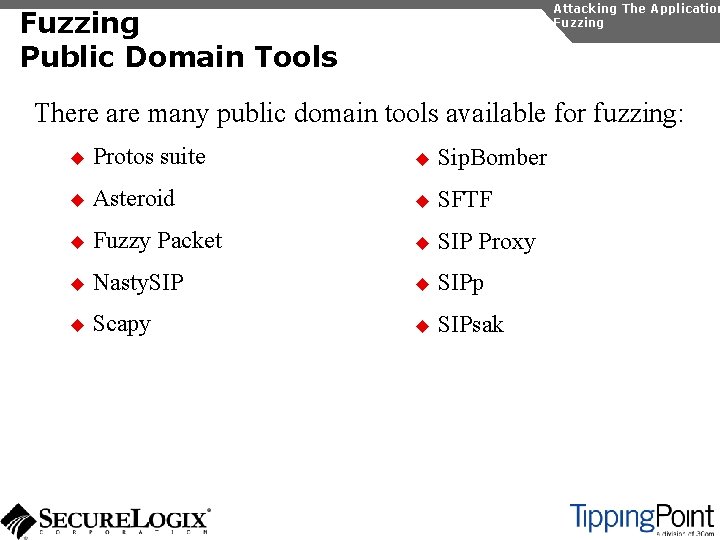
Attacking The Application Fuzzing Public Domain Tools There are many public domain tools available for fuzzing: u Protos suite u Sip. Bomber u Asteroid u SFTF u Fuzzy Packet u SIP Proxy u Nasty. SIP u SIPp u Scapy u SIPsak

Fuzzing Commercial Tools There are some commercial tools available: u Beyond Security Be. Storm u Codenomicon u Mu. Security Mu-4000 Security Analyzer u Security Innovation Hydra u Sipera Systems LAVA tools Attacking The Application Fuzzing

Fuzzing Countermeasures Attacking The Application Fuzzing Make sure your vendor has tested their systems for fuzzing attacks Consider running your own tests An Vo. IP-aware IPS can monitor for and block fuzzing attacks

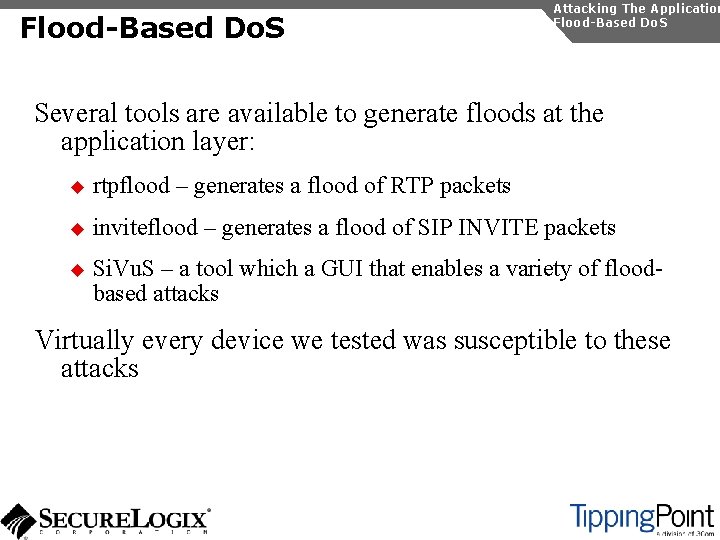
Flood-Based Do. S Attacking The Application Flood-Based Do. S Several tools are available to generate floods at the application layer: u rtpflood – generates a flood of RTP packets u inviteflood – generates a flood of SIP INVITE packets u Si. Vu. S – a tool which a GUI that enables a variety of floodbased attacks Virtually every device we tested was susceptible to these attacks

Flood-Based Do. S Countermeasures Attacking The Application Flood-Based Do. S There are several countermeasures you can use for floodbased Do. S: u Use VLANs to separate networks u Use TCP and TLS for SIP connections u Use rate limiting in switches u Enable authentication for requests u Use SIP firewalls/IPSs to monitor and block attacks

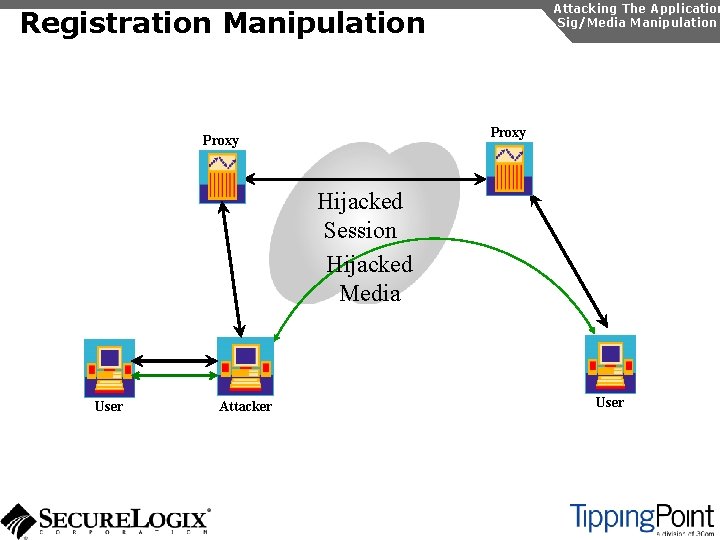
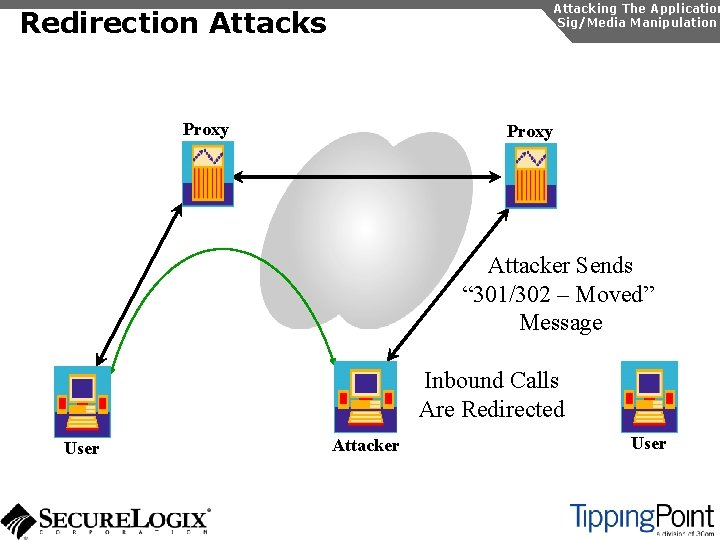
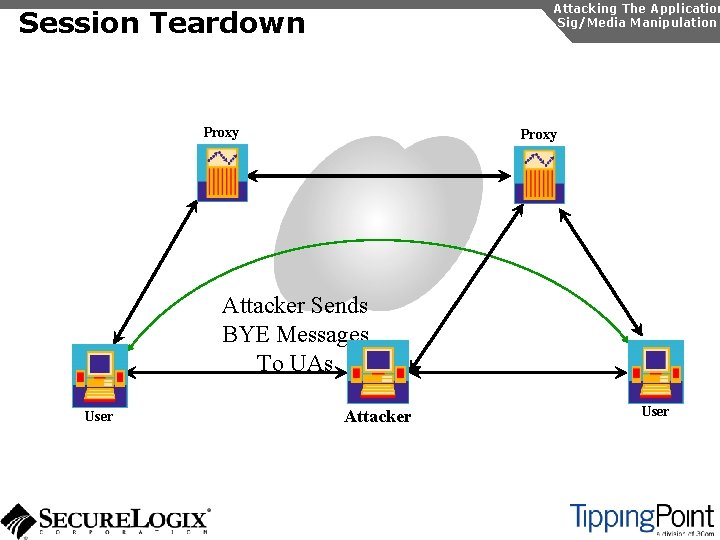
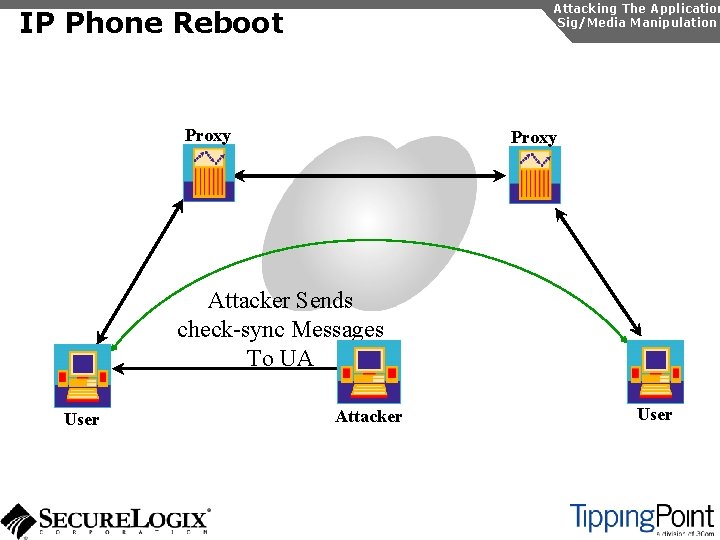
Signaling/Media Manipulation Introduction Attacking The Application Sig/Media Manipulation In SIP and RTP, there a number of attacks possible, which exploit the protocol: u Registration manipulation u Redirection attacks u Session teardown u SIP phone reboot u RTP insertion/mixing

Attacking The Application Sig/Media Manipulation Registration Manipulation Proxy Hijacked Session Hijacked Media User Attacker User

Attacking The Application Sig/Media Manipulation Redirection Attacks Proxy Attacker Sends “ 301/302 – Moved” Message Inbound Calls Are Redirected User Attacker User

Attacking The Application Sig/Media Manipulation Session Teardown Proxy Attacker Sends BYE Messages To UAs User Attacker User

Attacking The Application Sig/Media Manipulation IP Phone Reboot Proxy Attacker Sends check-sync Messages To UA User Attacker User

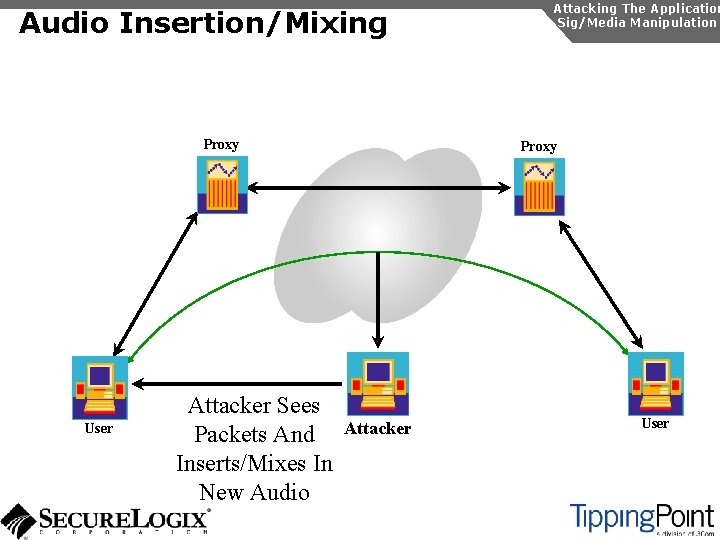
Audio Insertion/Mixing Proxy User Attacker Sees Packets And Inserts/Mixes In New Audio Attacking The Application Sig/Media Manipulation Proxy Attacker User

Signaling/Media Manipulation Countermeasures Attacking The Application Sig/Media Manipulation Some countermeasures for signaling and media manipulation include: u Use digest authentication where possible u Use TCP and TLS where possible u Use SIP-aware firewalls/IPSs to monitor for and block attacks u Use audio encryption to prevent RTP injection/mixing

Social Attacks There a couple of evolving social threats that will affect enterprises: u Voice SPAM or SPAM over Internet Telephony (SPIT) u Voice phishing

Voice SPAM Introduction Social Attacks Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: u The network makes it very inexpensive or free to generate calls u Attackers have access to Vo. IP networks that allow generation of a large number of calls It is easy to set up a voice SPAM operation, using Asterisk, tools like “spitter”, and free Vo. IP access

Voice SPAM Social Attacks Voice SPAM has the potential to be very disruptive because: u Voice calls tend to interrupt a user more than email u Calls arrive in realtime and the content can’t be analyzed to determine it is voice SPAM u Even calls saved to voice mail must be converted from audio to text, which is an imperfect process u There isn’t any capability in the protocols that looks like it will address Voice SPAM

Voice SPAM Countermeasures Social Attacks Voice SPAM Some potential countermeasures for voice SPAM are: u Authenticated identity movements, which may help to identify callers u Legal measures Enterprise voice SPAM filters: u Black lists/white lists u Approval systems u Audio content filtering u Turing tests

Vo. IP Phishing Introduction Social Attacks Phishing Similar to email phishing, but with a phone number delivered though email or voice When the victim dials the number, the recording requests entry of personal information The hacker comes back later and retrieves the touch tones or other information

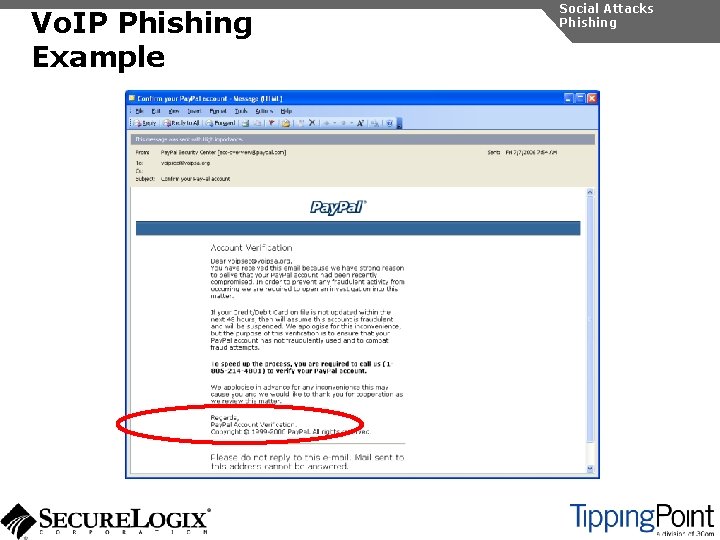
Vo. IP Phishing Example Social Attacks Phishing “Hi, this is Bob from Bank of America calling. Sorry I missed you. If you could give us a call back at 1 -866 -555 -1324 we have an urgent issue to discuss with you about your bank account. ” Hello. This is Bank of America. So we may best serve you, please enter your account number followed by your PIN.

Vo. IP Phishing Example Social Attacks Phishing

Vo. IP Phishing Countermeasures Traditional email spam/phishing countermeasures come in to play here. Educating users is a key Social Attacks Phishing