VNF Package Integrity and Authenticity Public key based
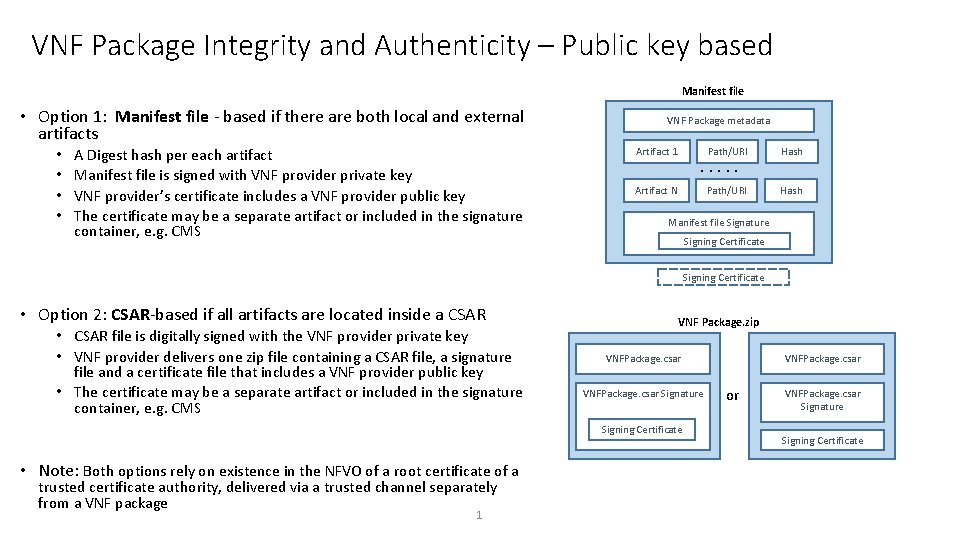
VNF Package Integrity and Authenticity – Public key based Manifest file • Option 1: Manifest file - based if there are both local and external artifacts • • A Digest hash per each artifact Manifest file is signed with VNF provider private key VNF provider’s certificate includes a VNF provider public key The certificate may be a separate artifact or included in the signature container, e. g. CMS VNF Package metadata Artifact 1 Path/URI Hash . . . Artifact N Manifest file Signature Signing Certificate • Option 2: CSAR-based if all artifacts are located inside a CSAR • CSAR file is digitally signed with the VNF provider private key • VNF provider delivers one zip file containing a CSAR file, a signature file and a certificate file that includes a VNF provider public key • The certificate may be a separate artifact or included in the signature container, e. g. CMS VNF Package. zip VNFPackage. csar Signature Signing Certificate • Note: Both options rely on existence in the NFVO of a root certificate of a trusted certificate authority, delivered via a trusted channel separately from a VNF package 1 VNFPackage. csar or VNFPackage. csar Signature Signing Certificate
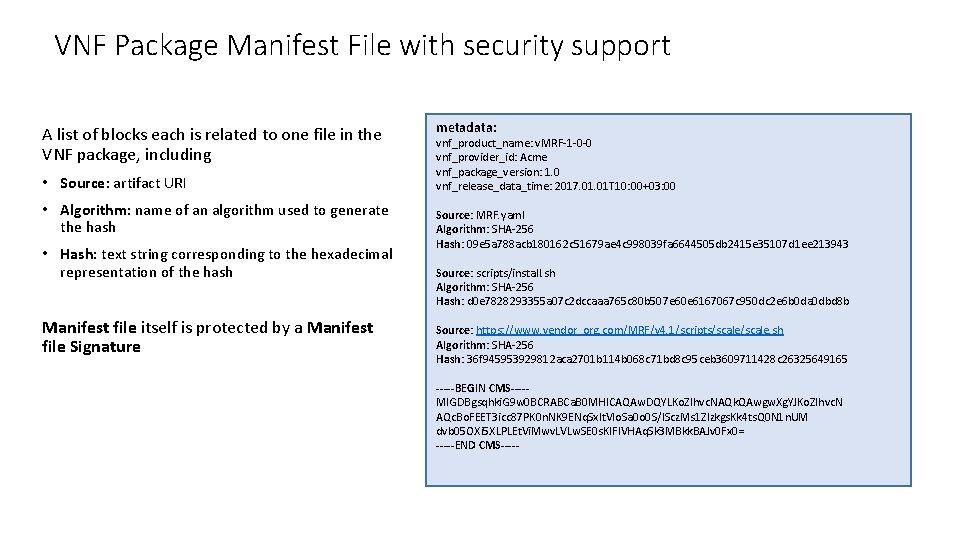
VNF Package Manifest File with security support A list of blocks each is related to one file in the VNF package, including • Source: artifact URI • Algorithm: name of an algorithm used to generate the hash • Hash: text string corresponding to the hexadecimal representation of the hash Manifest file itself is protected by a Manifest file Signature metadata: vnf_product_name: v. MRF-1 -0 -0 vnf_provider_id: Acme vnf_package_version: 1. 0 vnf_release_data_time: 2017. 01 T 10: 00+03: 00 Source: MRF. yaml Algorithm: SHA-256 Hash: 09 e 5 a 788 acb 180162 c 51679 ae 4 c 998039 fa 6644505 db 2415 e 35107 d 1 ee 213943 Source: scripts/install. sh Algorithm: SHA-256 Hash: d 0 e 7828293355 a 07 c 2 dccaaa 765 c 80 b 507 e 60 e 6167067 c 950 dc 2 e 6 b 0 da 0 dbd 8 b Source: https: //www. vendor_org. com/MRF/v 4. 1/scripts/scale. sh Algorithm: SHA-256 Hash: 36 f 945953929812 aca 2701 b 114 b 068 c 71 bd 8 c 95 ceb 3609711428 c 26325649165 -----BEGIN CMS----MIGDBgsqhki. G 9 w 0 BCRABCa. B 0 MHICAQAw. DQYLKo. ZIhvc. NAQk. QAwgw. Xg. YJKo. ZIhvc. N AQc. Bo. FEET 3 icc 87 PK 0 n. NK 9 ENq. Sx. It. VIo. Sa 0 o 0 S/IScz. Ms 1 ZIzkgs. Kk 4 ts. Q 0 N 1 n. UM dvb 05 OXi 5 XLPLEt. Vi. Mwv. LVLw. SE 0 s. Kl. FIVHAq. Sk 3 MBkk. BAJv 0 Fx 0= -----END CMS-----

Individual Artifacts Authenticity and Integrity • VNF provider sign individual artifacts adding a signature file in standard format (e. g. CMS, PKCS#7) • A certificate file with extension. cert accompany the signed artifact • The signature and certificate files have the same name and location as the signed artifact • If the signature format allows it, the certificate may be included in the signature file 3 !----- Artifacts !----- install. sh !----- images !----- MRF. img !----- MRF. cert !----- MRF. cms
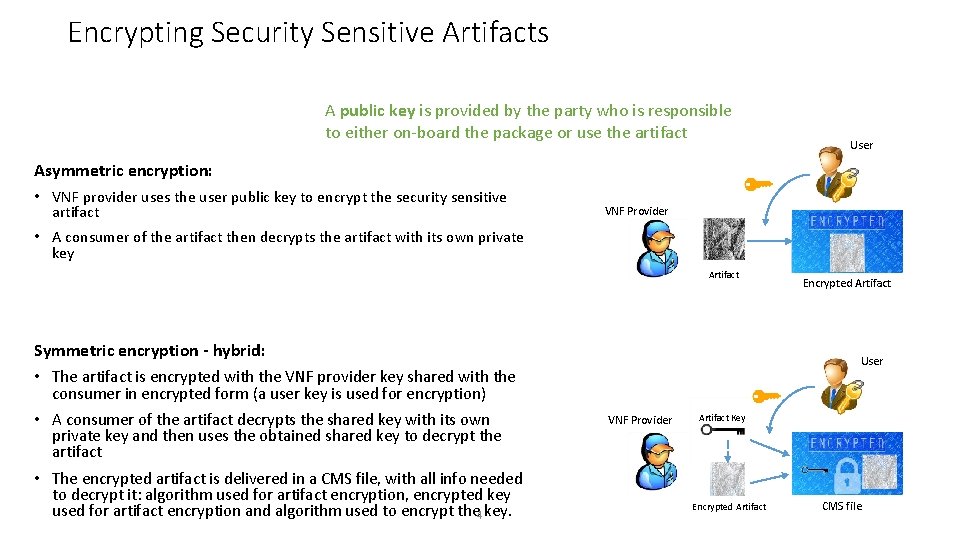
Encrypting Security Sensitive Artifacts A public key is provided by the party who is responsible to either on-board the package or use the artifact User Asymmetric encryption: • VNF provider uses the user public key to encrypt the security sensitive artifact VNF Provider • A consumer of the artifact then decrypts the artifact with its own private key Artifact Symmetric encryption - hybrid: • The artifact is encrypted with the VNF provider key shared with the Encrypted Artifact User consumer in encrypted form (a user key is used for encryption) • A consumer of the artifact decrypts the shared key with its own private key and then uses the obtained shared key to decrypt the artifact • The encrypted artifact is delivered in a CMS file, with all info needed to decrypt it: algorithm used for artifact encryption, encrypted key used for artifact encryption and algorithm used to encrypt the key. 4 VNF Provider Artifact Key Encrypted Artifact CMS file
- Slides: 4