Visualbased Anomaly Detection for BGP Origin AS Change
Visual-based Anomaly Detection for BGP Origin AS Change (OASC) Soon-Tee Teoh 1, Kwan-Liu Ma 1, S. Felix Wu 1, Dan Massey 2, Xiao-Liang Zhao 2, Dan Pei 3, Lan Wang 3, Lixia Zhang 3, Randy Bush 4 UC Davis, USC/ISI, UCLA, IIJ 10/21/2003 DSOM'2003, Heidelberg, Germany 1

Elisha: the long-term goal • Monitoring and management of a largescale complex system that we do not fully understand its behavior. • Integration of human and machine intelligence to adaptively develop the domain knowledge for the target system. 10/21/2003 DSOM'2003, Heidelberg, Germany 2
In this talk… • Knowledge Acquisition via Visualization – cognitive pattern matching – event correlation and explanation • Outline – Background: Origin AS in BGP – The Elisha/OASC tool – One example and demo 10/21/2003 DSOM'2003, Heidelberg, Germany 3
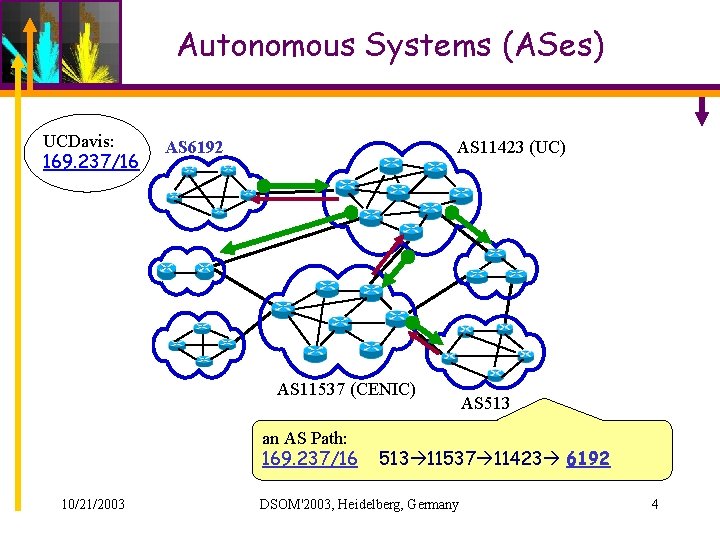
Autonomous Systems (ASes) UCDavis: 169. 237/16 AS 6192 AS 11423 (UC) AS 11537 (CENIC) an AS Path: 169. 237/16 10/21/2003 AS 513 11537 11423 6192 DSOM'2003, Heidelberg, Germany 4
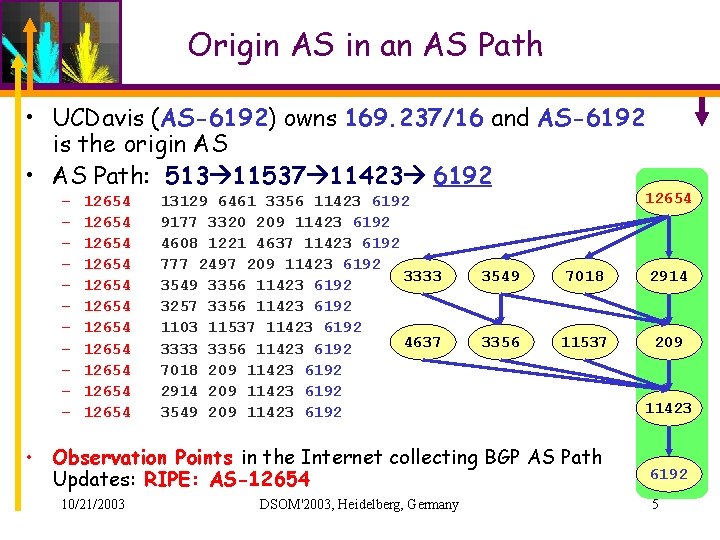
Origin AS in an AS Path • UCDavis (AS-6192) owns 169. 237/16 and AS-6192 is the origin AS • AS Path: 513 11537 11423 6192 – – – 12654 12654 12654 13129 6461 3356 11423 6192 9177 3320 209 11423 6192 4608 1221 4637 11423 6192 777 2497 209 11423 6192 3333 3549 3356 11423 6192 3257 3356 11423 6192 1103 11537 11423 6192 4637 3333 3356 11423 6192 7018 209 11423 6192 2914 209 11423 6192 3549 7018 2914 3356 11537 209 • Observation Points in the Internet collecting BGP AS Path Updates: RIPE: AS-12654 10/21/2003 DSOM'2003, Heidelberg, Germany 12654 11423 6192 5
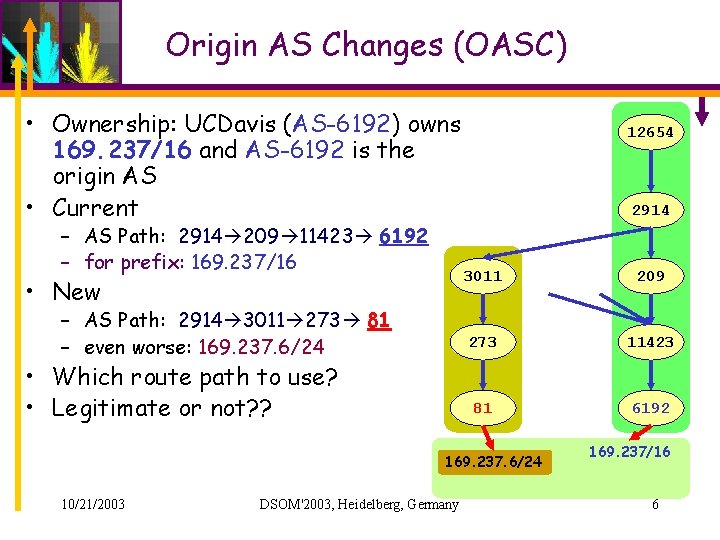
Origin AS Changes (OASC) • Ownership: UCDavis (AS-6192) owns 169. 237/16 and AS-6192 is the origin AS • Current – AS Path: 2914 209 11423 6192 – for prefix: 169. 237/16 • New – AS Path: 2914 3011 273 81 – even worse: 169. 237. 6/24 • Which route path to use? • Legitimate or not? ? 12654 2914 3011 209 273 11423 81 6192 169. 237. 6/24 10/21/2003 DSOM'2003, Heidelberg, Germany 169. 237/16 6
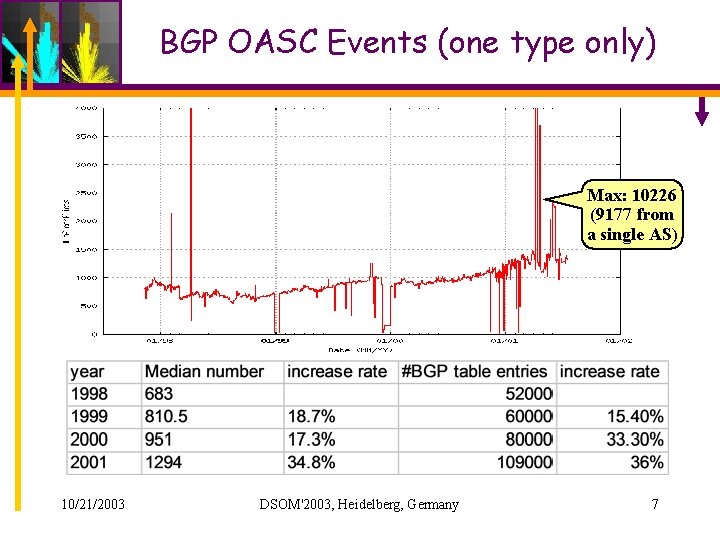
BGP OASC Events (one type only) Max: 10226 (9177 from a single AS) 10/21/2003 DSOM'2003, Heidelberg, Germany 7
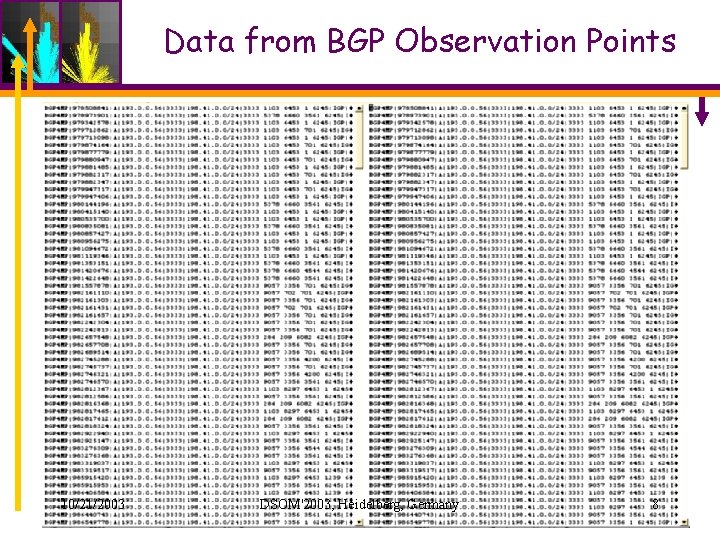
Data from BGP Observation Points 10/21/2003 DSOM'2003, Heidelberg, Germany 8

Anomaly Detection • False positive versus false negative • Anomaly analysis: – To find the “meaning”, “explanation, ” and “knowledge” behind those detected anomalies 10/21/2003 DSOM'2003, Heidelberg, Germany 9
Visual-based Anomaly Detection • “Visual” Anomalies – Something catches your eyes… • Mental/Cognitive “long-term” profile or normal behavior – We build the “long-term” profile in your mind. – Human experts can incorporate “domain knowledge” about the target system/protocol. 10/21/2003 DSOM'2003, Heidelberg, Germany 10
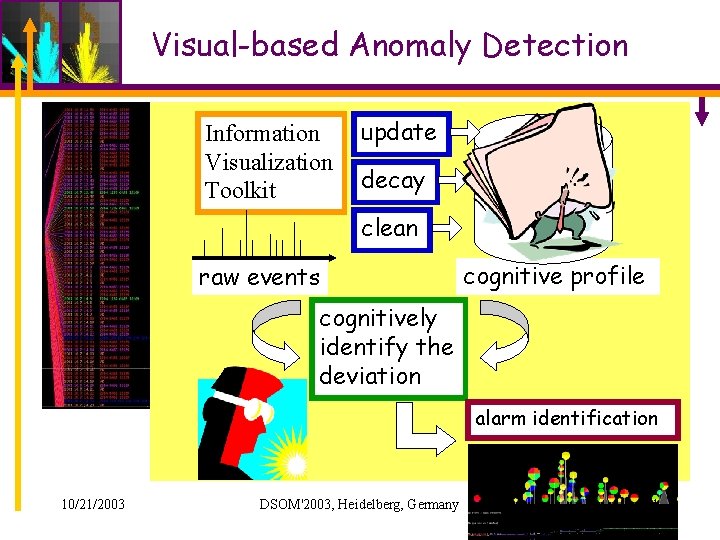
Visual-based Anomaly Detection Information Visualization Toolkit update decay clean raw events cognitive profile cognitively identify the deviation alarm identification 10/21/2003 DSOM'2003, Heidelberg, Germany 11

ELISHA/OASC • Events: – Low level events: – High level events: BGP Route Updates OASC • Still 1000+ per day and max 10226 per day for the whole Internet • Information to represent visually: – IP address blocks – Origin AS in BGP Update Messages – Different Types of OASC Events 10/21/2003 DSOM'2003, Heidelberg, Germany 12
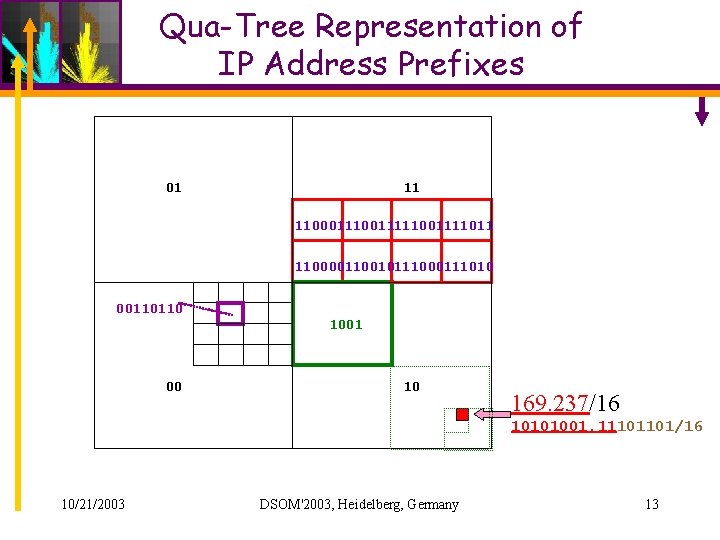
Qua-Tree Representation of IP Address Prefixes 01 11 1100011111001111011 110000110010111000111010 00110110 1001 00 10 169. 237/16 10101001. 11101101/16 10/21/2003 DSOM'2003, Heidelberg, Germany 13
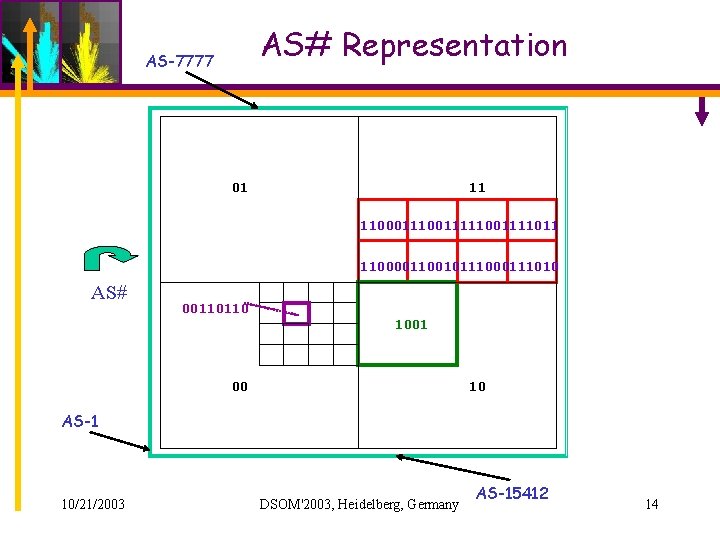
AS# Representation AS-7777 01 11 1100011111001111011 110000110010111000111010 AS# 00110110 1001 00 10 AS-1 10/21/2003 DSOM'2003, Heidelberg, Germany AS-15412 14
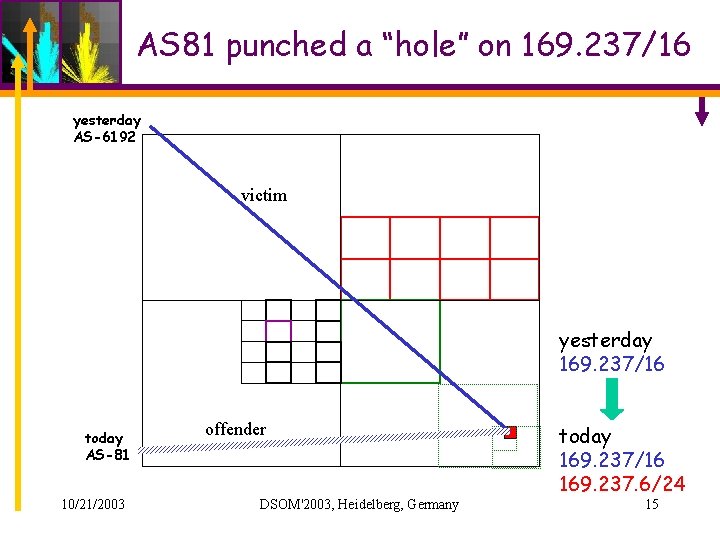
AS 81 punched a “hole” on 169. 237/16 yesterday AS-6192 victim yesterday 169. 237/16 today AS-81 10/21/2003 offender DSOM'2003, Heidelberg, Germany today 169. 237/16 169. 237. 6/24 15
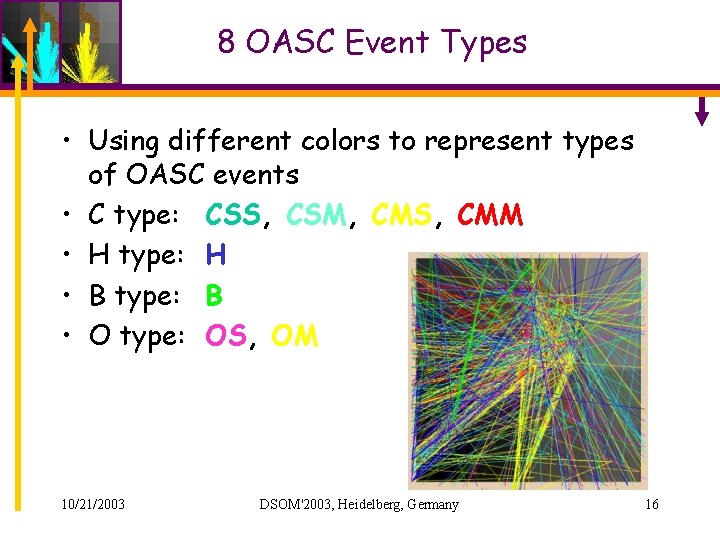
8 OASC Event Types • Using different colors to represent types of OASC events • C type: CSS, CSM, CMS, CMM • H type: H • B type: B • O type: OS, OM 10/21/2003 DSOM'2003, Heidelberg, Germany 16
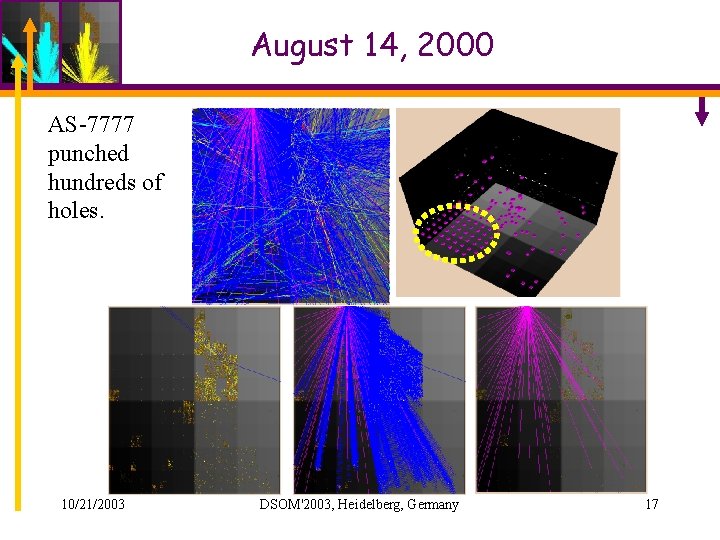
August 14, 2000 AS-7777 punched hundreds of holes. 10/21/2003 DSOM'2003, Heidelberg, Germany 17
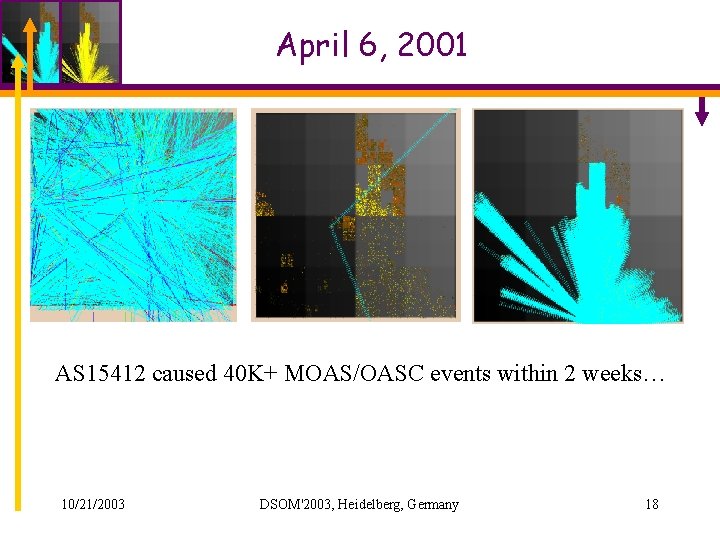
April 6, 2001 AS 15412 caused 40 K+ MOAS/OASC events within 2 weeks… 10/21/2003 DSOM'2003, Heidelberg, Germany 18
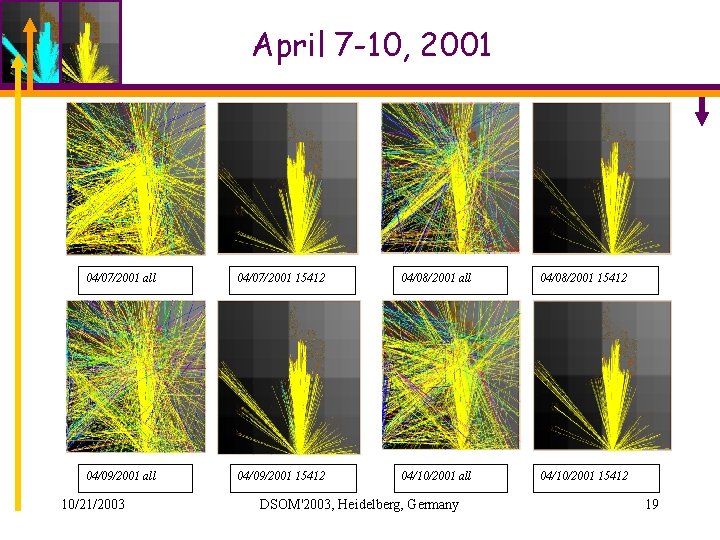
April 7 -10, 2001 04/07/2001 all 04/07/2001 15412 04/08/2001 all 04/08/2001 15412 04/09/2001 all 04/09/2001 15412 04/10/2001 all 04/10/2001 15412 10/21/2003 DSOM'2003, Heidelberg, Germany 19
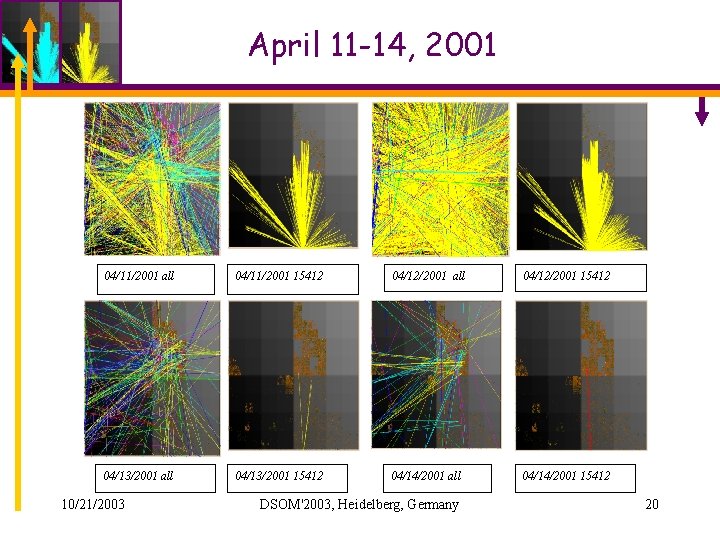
April 11 -14, 2001 04/11/2001 all 04/11/2001 15412 04/12/2001 all 04/12/2001 15412 04/13/2001 all 04/13/2001 15412 04/14/2001 all 04/14/2001 15412 10/21/2003 DSOM'2003, Heidelberg, Germany 20
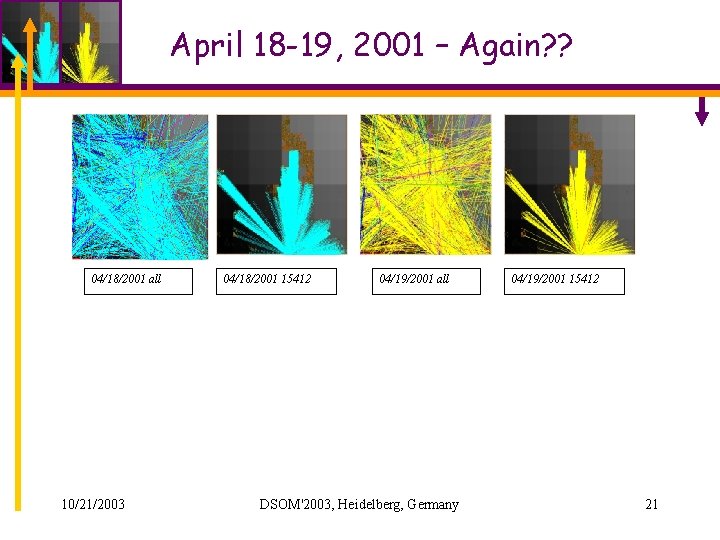
April 18 -19, 2001 – Again? ? 04/18/2001 all 10/21/2003 04/18/2001 15412 04/19/2001 all DSOM'2003, Heidelberg, Germany 04/19/2001 15412 21

Remarks • The Elisha/OASC prototype discovered and helped to explain real-world BGP anomalies. • Integration with Statistical approaches. • Elisha: open source available – http: //www. cs. ucdavis. edu/~wu/Elisha/ – Linux/Windows 10/21/2003 DSOM'2003, Heidelberg, Germany 22
- Slides: 22