Visual Secret Sharing Schemes for Plural Secret Images



- Slides: 8

Visual Secret Sharing Schemes for Plural Secret Images Allowing the Rotation of Shares Kazuki Yoneyama Wang Lei Noboru Kunihiro Mitsugu Iwamoto Kazuo Ohta The University of Electro-Communications

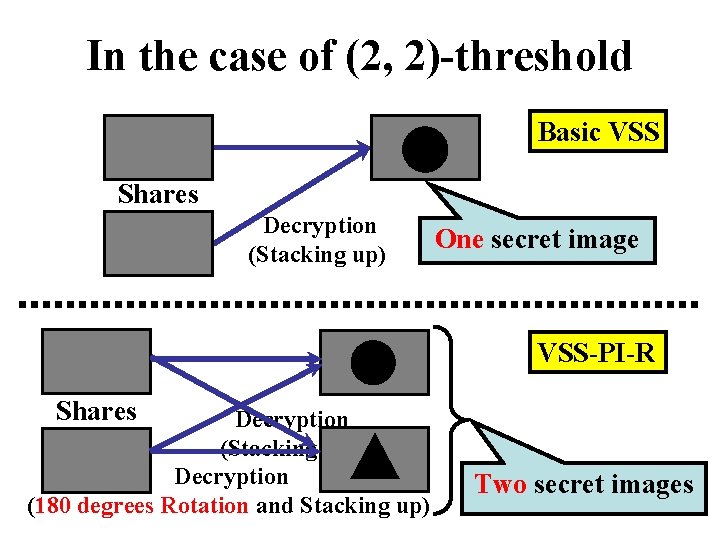
Basic VSS schemes V. S. Our scheme • Basic visual secret sharing schemes (VSS) – By stacking up shares, each secret image is decrypted. • VSS schemes for plural secret images with general access structures allowing the rotation (VSS-PI-R) – More secret images can be decrypted compared with the ordinal VSS. – We can construct any VSS-PI-R scheme for given access structure.

In the case of (2, 2)-threshold Basic VSS Shares Decryption (Stacking up) One secret image VSS-PI-R Shares Decryption (Stacking up) Decryption (180 degrees Rotation and Stacking up) Two secret images


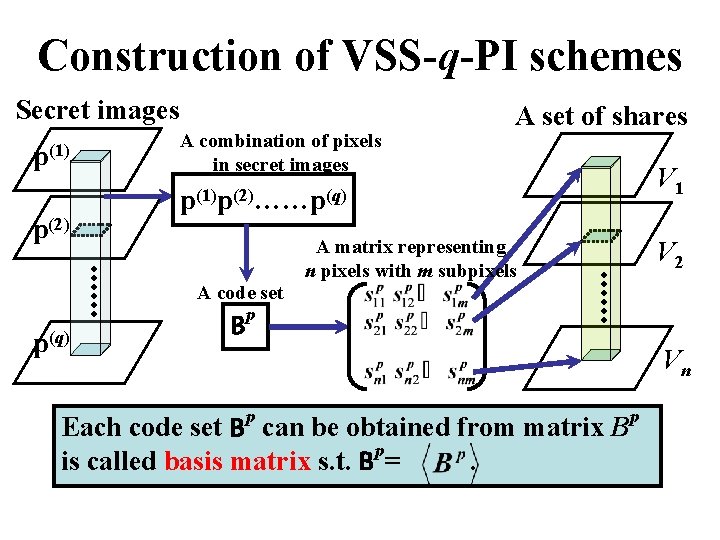
Construction of VSS-q-PI schemes Secret images p(1) p(2) A combination of pixels in secret images V 1 p(1)p(2)……p(q) A code set p(q) A set of shares A matrix representing n pixels with m subpixels V 2 Bp Vn p Each code set B can be obtained from matrix B p is called basis matrix s. t. B =. p

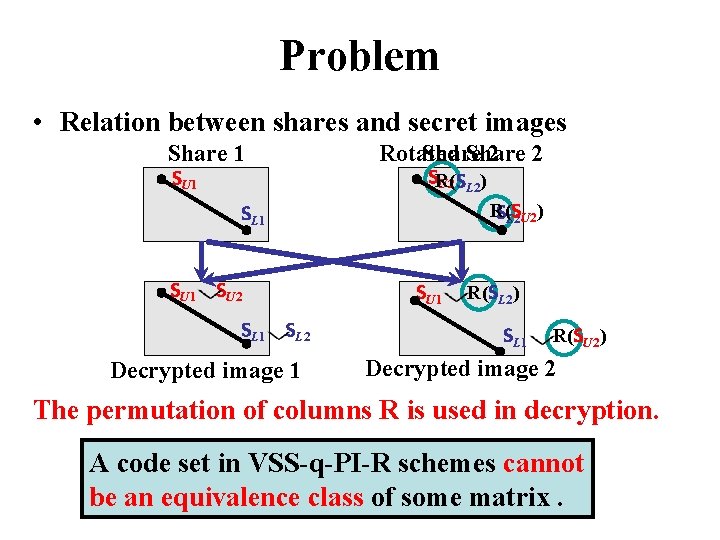
Problem • Relation between shares and secret images Share 1 Rotated Share 2 2 SR(S U 2 L 2) SU 1 R(S SL 2 U 2) SL 1 SU 2 SL 1 SU 1 SL 2 Decrypted image 1 R(SL 2) SL 1 R(SU 2) Decrypted image 2 The permutation of columns R is used in decryption. A code set in VSS-q-PI-R schemes cannot be an equivalence class of some matrix.

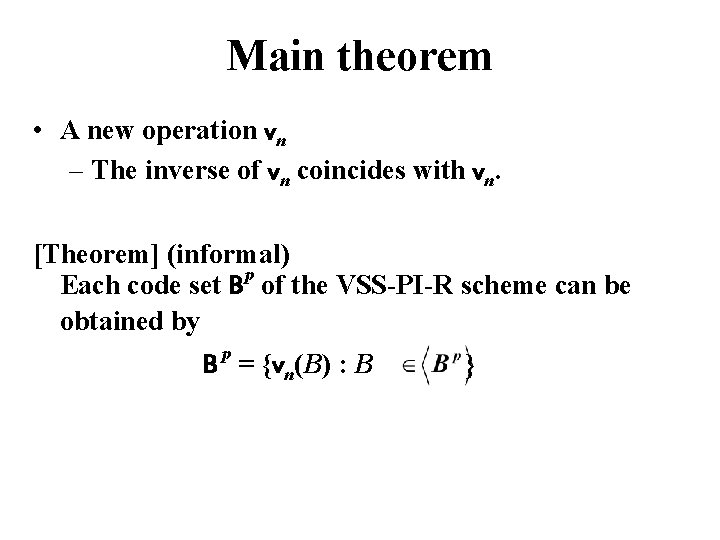
Main theorem • A new operation vn – The inverse of vn coincides with vn. [Theorem] (informal) p Each code set B of the VSS-PI-R scheme can be obtained by p B = {vn(B) : B }

Conclusion • The proposed technique can easily be applied to VSS -PI schemes allowing to reverse the shares besides stacking in decryption. • We will soon submit the paper corresponding to this talk in Cryptology e. Print Archive!