VISION STRATEGY ARAMA TECH DATA PROTECTION PROFESSIONALS ARAMA




- Slides: 14

VISION & STRATEGY ARAMA TECH DATA PROTECTION PROFESSIONALS

ARAMA TECH VISION OBTAIN and MAINTAIN your GRIP and CONTROL over COMPLIANCE and RISKS is critical for your BUSINESS SUCCESS

OUR DIGITAL LIFE IS BECOMING MORE COMPLEX

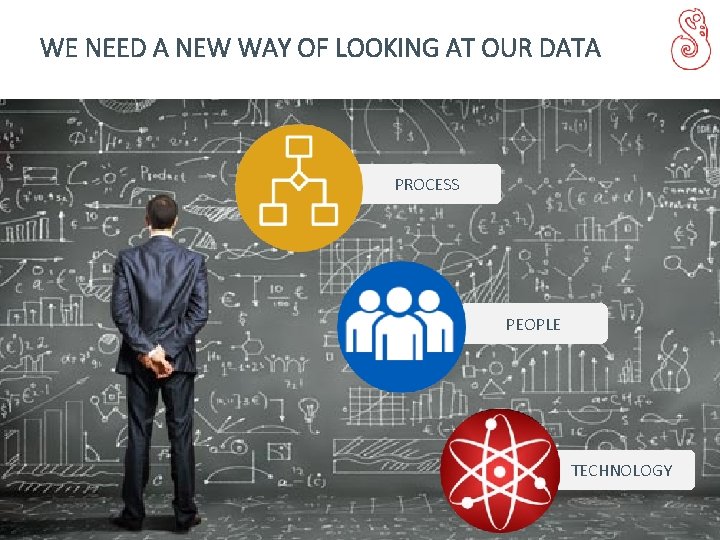
WE NEED A NEW WAY OF LOOKING AT OUR DATA PROCESS PEOPLE TECHNOLOGY

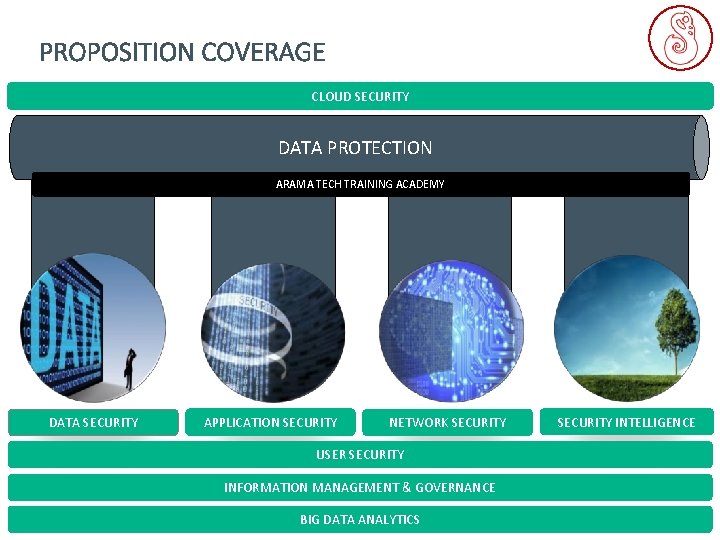
PROPOSITION COVERAGE CLOUD SECURITY DATA PROTECTION ARAMA TECH TRAINING ACADEMY DATA SECURITY APPLICATION SECURITY NETWORK SECURITY USER SECURITY INFORMATION MANAGEMENT & GOVERNANCE BIG DATA ANALYTICS SECURITY INTELLIGENCE

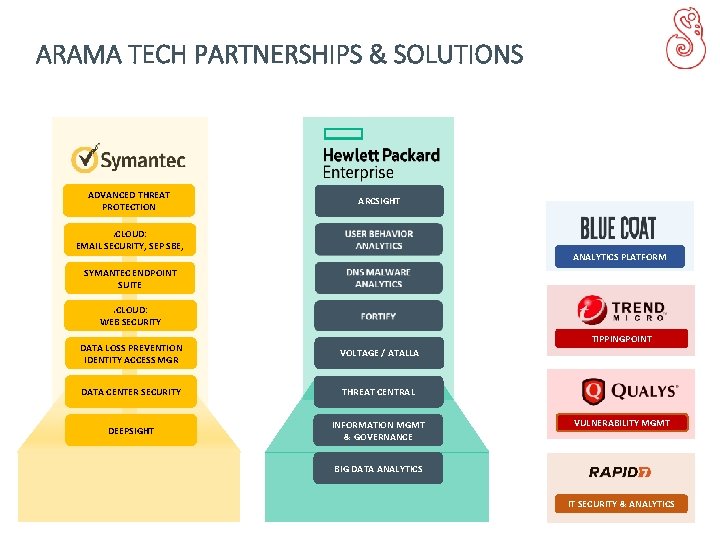
ARAMA TECH PARTNERSHIPS & SOLUTIONS ADVANCED THREAT PROTECTION ARCSIGHT . CLOUD: EMAIL SECURITY, SEP SBE, ANALYTICS PLATFORM SYMANTEC ENDPOINT SUITE. CLOUD: WEB SECURITY TIPPINGPOINT DATA LOSS PREVENTION IDENTITY ACCESS MGR VOLTAGE / ATALLA DATA CENTER SECURITY THREAT CENTRAL DEEPSIGHT INFORMATION MGMT & GOVERNANCE VULNERABILITY MGMT BIG DATA ANALYTICS IT SECURITY & ANALYTICS

PROACTIVE PROTECTION THE BEST WAY TO PREDICT THE FUTURE IS TO CREATE IT!

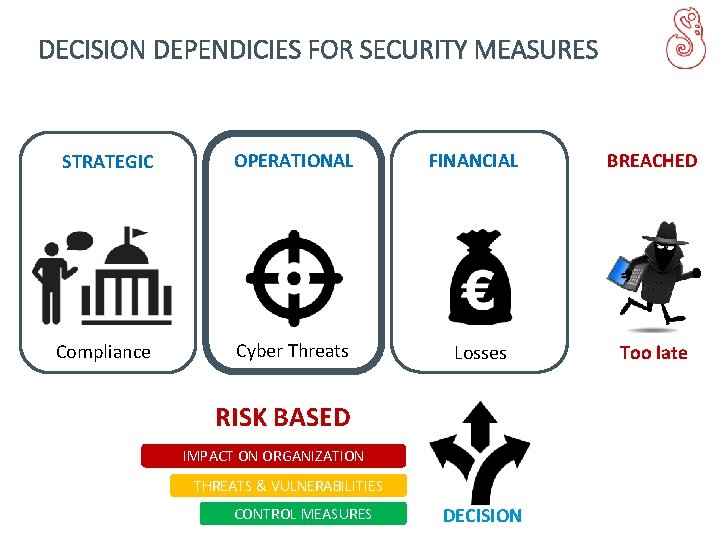
DECISION DEPENDICIES FOR SECURITY MEASURES STRATEGIC OPERATIONAL Compliance Cyber Threats FINANCIAL Losses RISK BASED IMPACT ON ORGANIZATION THREATS & VULNERABILITIES CONTROL MEASURES DECISION BREACHED Too late

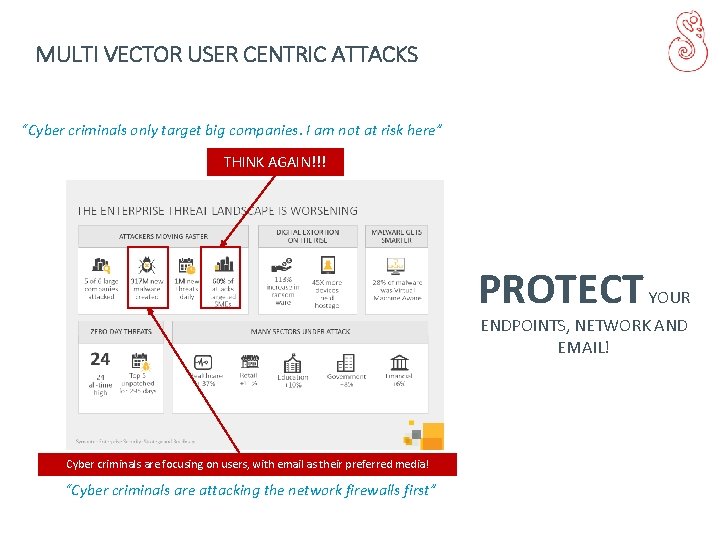
MULTI VECTOR USER CENTRIC ATTACKS “Cyber criminals only target big companies. I am not at risk here” THINK AGAIN!!! PROTECT YOUR ENDPOINTS, NETWORK AND EMAIL! Cyber criminals are focusing on users, with email as their preferred media! “Cyber criminals are attacking the network firewalls first”

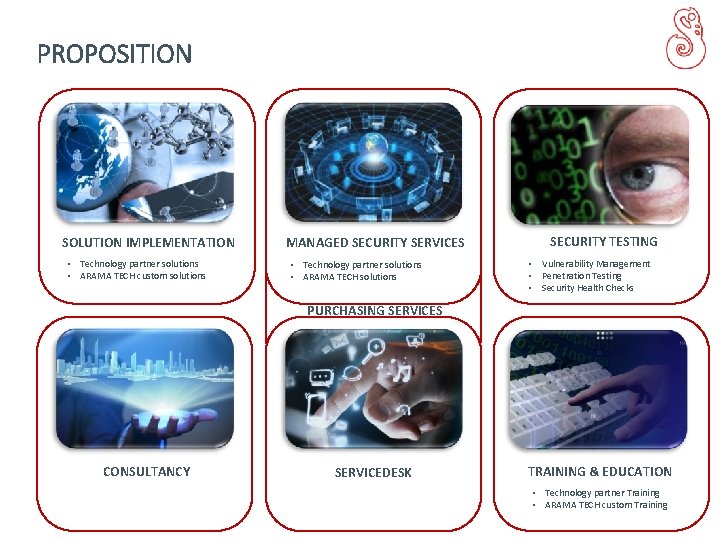
PROPOSITION SOLUTION IMPLEMENTATION • Technology partner solutions • ARAMA TECH custom solutions MANAGED SECURITY SERVICES • Technology partner solutions • ARAMA TECH solutions SECURITY TESTING • Vulnerability Management • Penetration Testing • Security Health Checks PURCHASING SERVICES CONSULTANCY SERVICEDESK TRAINING & EDUCATION • Technology partner Training • ARAMA TECH custom Training

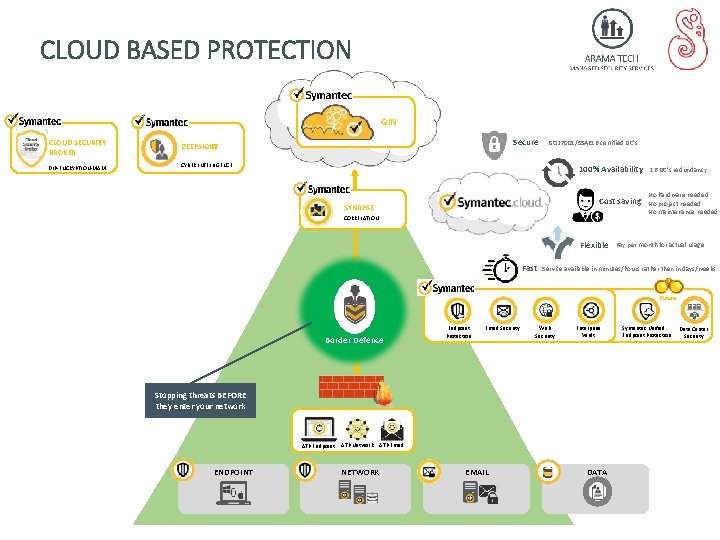
CLOUD BASED PROTECTION GIN CLOUD SECURITY BROKER DEEPSIGHT DLP-ENCRYPTION-MAM CYBER INTELLIGENCE Secure ISO 27001/SSAE 16 certified DC’s 100% Availability Cost saving SYNAPSE CORRELATION Flexible Fast 16 DC’s redundancy No hardware needed No project needed No maintenance needed Pay per month for actual usage Service available in minutes/hours rather then in days/weeks Future Border Defence Endpoint Protection Email Security Web Security Enterprise Vault Stopping threats BEFORE they enter your network ATP Endpoint ENDPOINT ATP Network NETWORK ATP Email EMAIL DATA Symantec Unified Endpoint Protection Data Center Security

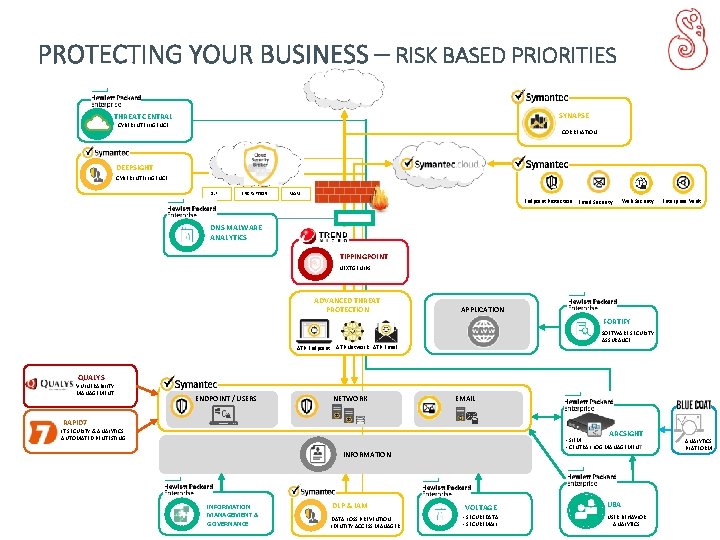
PROTECTING YOUR BUSINESS – RISK BASED PRIORITIES SYNAPSE THREAT CENTRAL CYBER INTELLIGENCE CORRELATION DEEPSIGHT CYBER INTELLIGENCE DLP ENCRYPTION MAM Endpoint Protection Email Security Web Security Enterprise Vault DNS MALWARE ANALYTICS TIPPINGPOINT NEXTGEN IPS ADVANCED THREAT PROTECTION APPLICATION FORTIFY ATP Endpoint SOFTWARE SECURITY ASSURANCE ATP Network ATP Email QUALYS VULNERABILITY MANAGEMENT ENDPOINT / USERS NETWORK EMAIL RAPID 7 IT SECURITY & ANALYTICS AUTOMATED PENTESTING ARCSIGHT - SIEM - CENTRAL LOG MANAGEMENT INFORMATION MANAGEMENT & GOVERNANCE DLP & IAM DATA LOSS PREVENTION IDENTITY ACCESS MANAGER VOLTAGE - SECUREDATA - SECUREMAIL UBA USER BEHAVIOR ANALYTICS PLATFORM

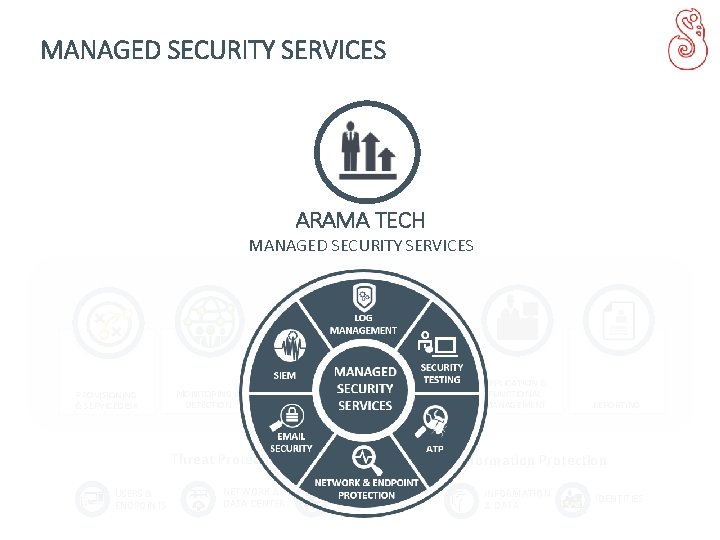
MANAGED SECURITY SERVICES ARAMA TECH MANAGED SECURITY SERVICES PROVISIONING & SERVICEDESK MONITORING & DETECTION INTELLIGENCE & ANALYSIS INCIDENT RESPONSE & MANAGEMENT Threat Protection USERS & ENDPOINTS NETWORK & DATA CENTER APPLICATION & FUNCTIONAL MANAGEMENT REPORTING Information Protection GATEWAYS INFORMATION & DATA IDENTITIES

ARAMA TECH DATA PROTECTION PROFESSIONALS www. aramatech. com Wildenborchlaan 13 3207 ZA Spijkenisse The Netherlands +31 10 340 1964 info@aramatech. com www. aramatech. com Ejbydalsvej 135 2600 Glostrup Denmark