Virtually Secure Oded Horovitz VMware RD Can Sec












- Slides: 29

Virtually Secure Oded Horovitz VMware R&D Can. Sec. West March, 2008

2 Talk Overview Setup • Virtualization 101 • Talk Focus VM Introspection • Capabilities • Sample Use Cases (and demos) Magics • Retrospective Security Misc & QA

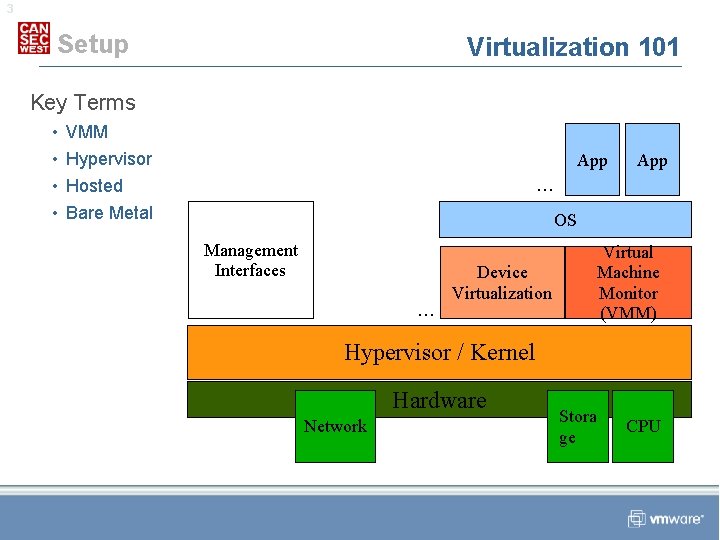
3 Setup Virtualization 101 Key Terms • • VMM Hypervisor App . . . Hosted Bare Metal App OS Management Interfaces . . . Virtual Machine Monitor (VMM) Device Virtualization Hypervisor / Kernel Hardware Network Stora ge CPU

4 Setup Virtualization Based Capabilities • Better than physical • Hypervisor as a Base of Trust • Security as an infrastructure service Also Important But not Today Secure Virtualization Infrastructure • Secure & Manageable Platform Physical Equivalent Security • Support existing tools and agents • Prevent security coverage loss when P 2 V Talk Focus

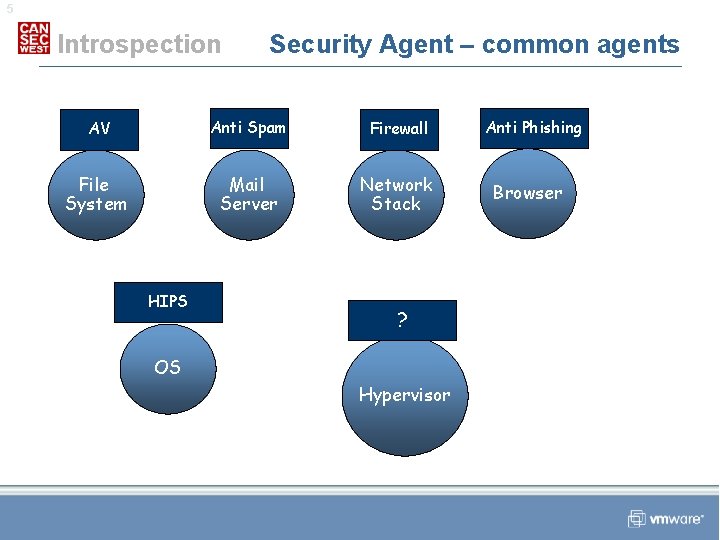
5 Introspection Security Agent – common agents AV Anti Spam Firewall File System Mail Server Network Stack HIPS ? OS Hypervisor Anti Phishing Browser

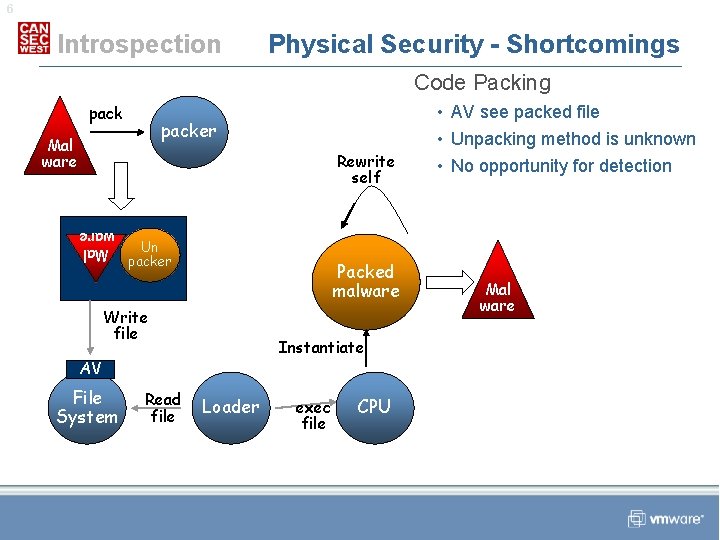
6 Introspection Physical Security - Shortcomings Code Packing packer Mal ware Rewrite self Un packer Packed malware Mal ware Write file Instantiate AV File System Read file Loader exec file CPU • AV see packed file • Unpacking method is unknown • No opportunity for detection Mal ware

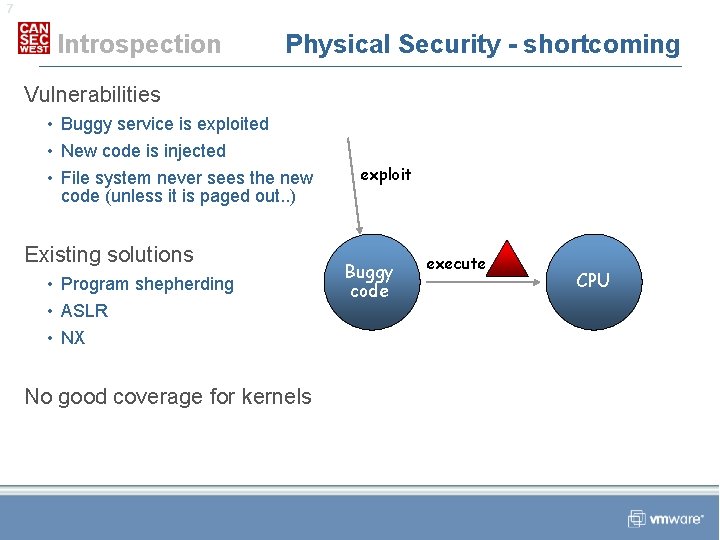
7 Introspection Physical Security - shortcoming Vulnerabilities • Buggy service is exploited • New code is injected • File system never sees the new code (unless it is paged out. . ) Existing solutions • Program shepherding • ASLR • NX No good coverage for kernels exploit Buggy code execute CPU

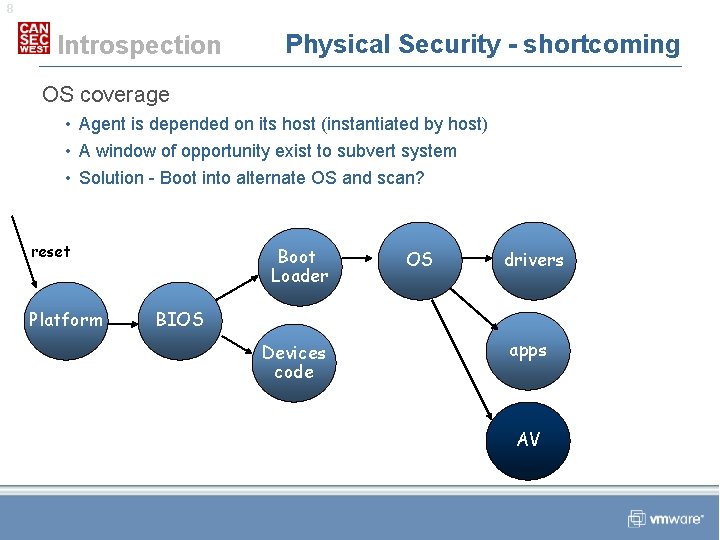
8 Introspection Physical Security - shortcoming OS coverage • Agent is depended on its host (instantiated by host) • A window of opportunity exist to subvert system • Solution - Boot into alternate OS and scan? reset Platform Boot Loader OS drivers BIOS Devices code apps AV

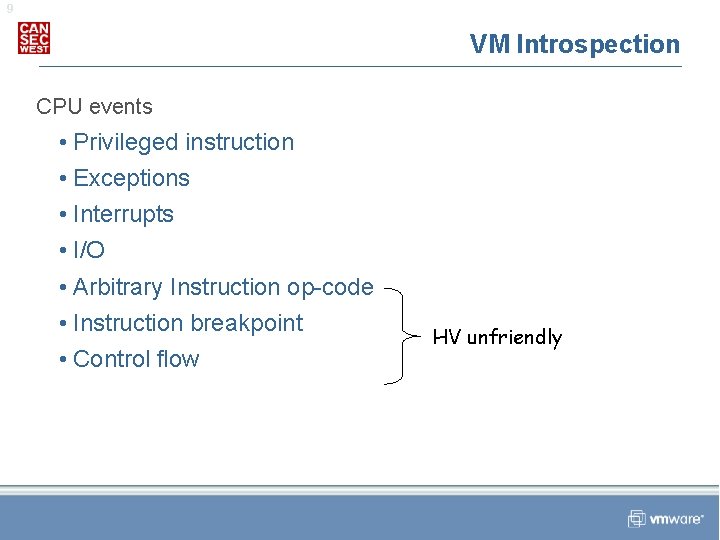
9 VM Introspection CPU events • Privileged instruction • Exceptions • Interrupts • I/O • Arbitrary Instruction op-code • Instruction breakpoint • Control flow HV unfriendly

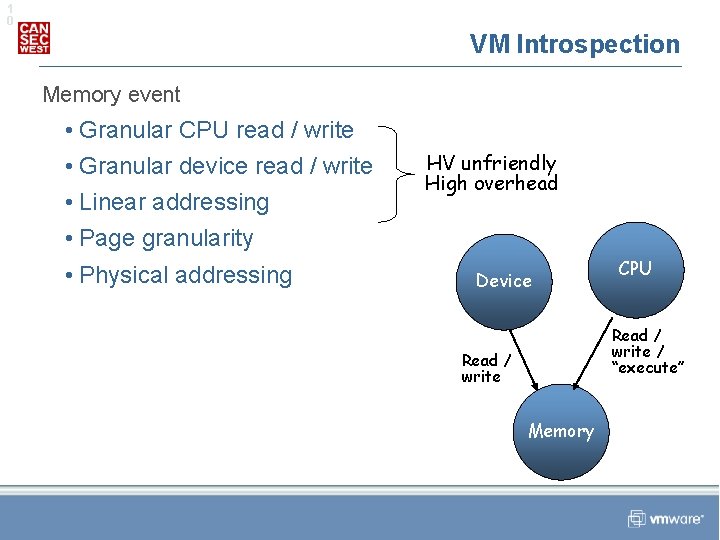
1 0 VM Introspection Memory event • Granular CPU read / write • Granular device read / write • Linear addressing • Page granularity • Physical addressing HV unfriendly High overhead Device CPU Read / write / “execute” Read / write Memory

1 1 VM Introspection – VMware initiatives VM Debugging • GDB like interface • Designed for human user • Agent is on the network • Capabilities • Examine CPU, memory • Single step • invisible breakpoints • Page table walker • Some symbol information support

1 2 VM Introspection – VMware Initiatives VProbes • dtrace like goals • Designed for human user / analysis tools • Agent runs within the hypervisor • Specialized scripting VM • Capabilities • Dynamic probing point installation • Inline execution with the hypervisor • Access to VM state • Access to hypervisor state

1 3 VM Introspection - VMware Initiatives Security API’s • Designed for security productization • Agent runs within a VM • Capabilities • Memory access events • Selected CPU events • VM lifecycle events • Access to VM memory & CPU state • Page Table walker

1 4 Introspection Security APIs (VMsafe) Goals • Better than physical • Exploit hypervisor interposition to place new security agent • Provide security coverage for the VM kernel (and applications) • Hypervisor as a Base of Trust • Divide responsibilities between the hypervisor and in-VM agent • The hypervisor covers the VM kernel, the rest is done from within the VM • Insure in-VM security agent execution and correctness • Security as an infrastructure service • “Agent less” security services for VMs • Flexible OS independent solutions

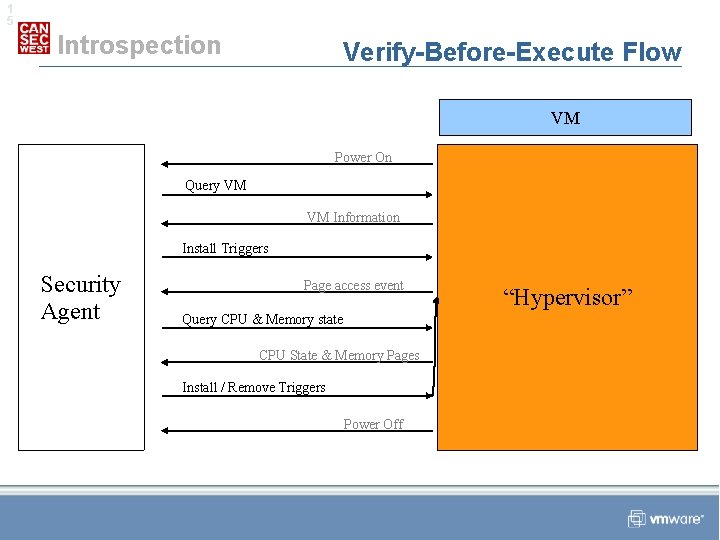
1 5 Introspection Verify-Before-Execute Flow VM Power On Query VM VM Information Install Triggers Security Agent Page access event Query CPU & Memory state CPU State & Memory Pages Install / Remove Triggers Power Off “Hypervisor”

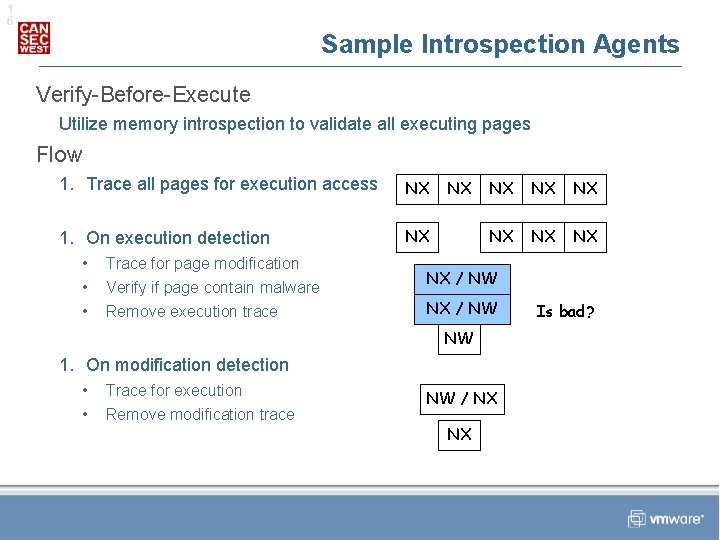
1 6 Sample Introspection Agents Verify-Before-Execute Utilize memory introspection to validate all executing pages Flow 1. Trace all pages for execution access NX 1. On execution detection NX • • • Trace for page modification Verify if page contain malware Remove execution trace NX NX / NW NX / NW NW 1. On modification detection • • Trace for execution Remove modification trace NW / NX NX Is bad?

1 7 Introspection Security APIs – Use cases VM Kernel coverage • Detect infection in early boot process • • Device opt ROM attacks Boot loader Boot records OS image Detect code injection due to kernel vulnerabilities Detect self modifying code in kernel Lock kernel after initialization

1 8 Introspection Case Study - Microsoft Patch Guard Goal • Prevent patching of (x 64 based) kernels • Force ISV to behave nicely • Prevent Root-kits ? ? Implementation • Obfuscated Invocation • Obfuscated Persistence • Evolving (Thanks to the awesome work from uninformed. org) What's The Problem? • Circumventable • Complicated • Only for x 64 based Windows Systems

1 9 Introspection Kernel Security Demo “My. Patch. Guard” • • Secure & Isolated Agent Inline enforcement using memory write triggers. Protect Windows XP guest syscalls table Simple.

2 0 Introspection Security APIs – Use cases cont’ Watch dog services • Liveness check for in-VM security agent • • • Detect agent presence Verify agent periodic execution Protect agent code and static data

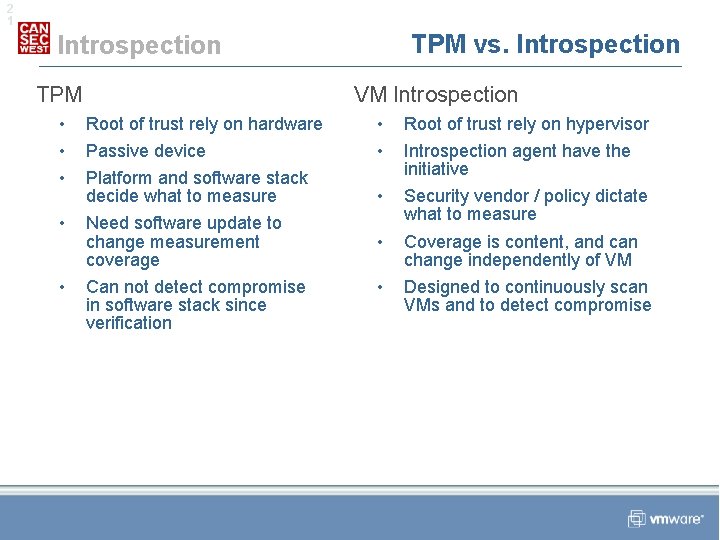
2 1 TPM vs. Introspection TPM VM Introspection • • • Root of trust rely on hardware Root of trust rely on hypervisor Passive device • • Platform and software stack decide what to measure • • Need software update to change measurement coverage Security vendor / policy dictate what to measure • Coverage is content, and can change independently of VM • Can not detect compromise in software stack since verification • Designed to continuously scan VMs and to detect compromise Introspection agent have the initiative

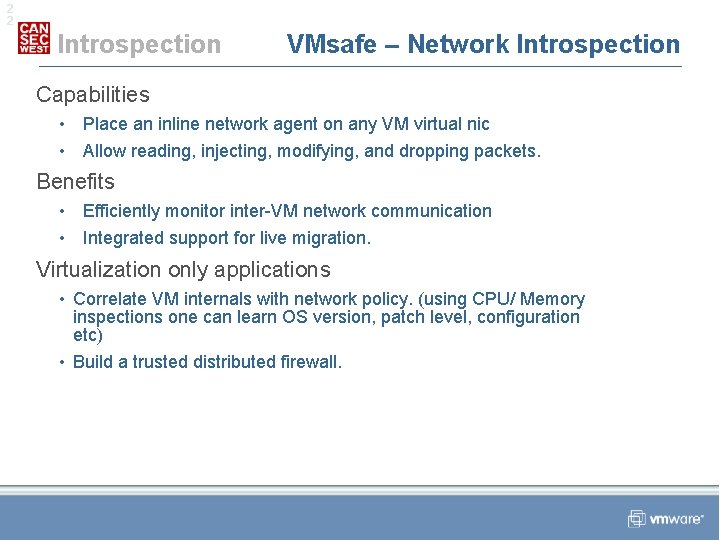
2 2 Introspection VMsafe – Network Introspection Capabilities • Place an inline network agent on any VM virtual nic • Allow reading, injecting, modifying, and dropping packets. Benefits • Efficiently monitor inter-VM network communication • Integrated support for live migration. Virtualization only applications • Correlate VM internals with network policy. (using CPU/ Memory inspections one can learn OS version, patch level, configuration etc) • Build a trusted distributed firewall.

2 3 Talk Overview Setup • Virtualization 101 • Talk Focus VM Introspection • Capabilities • Sample Use Cases (and demos) Magics • Retrospective Security Misc & QA

2 4 Magics Retrospective Security Motivation • Detect whether you have been attacked in the past • Detect if you might be still compromised by a past attack Method • VMware Record & Replay allow for a deterministic replay of VM using recorded logs • Potentially the recordings have captured an attack • The security API’s are detached from the recorded VM (unlike in. VM agent) and can attach to a replay session

2 5 Magics Retrospective Security Demo What is it good for? • Run more aggressive policies that will not be acceptable in production environments • Discover 0 days used to exploit your system • Learn how the malware / attacker have navigated your system • Use data tainting technique to detect any side effects that still exist on your system • Possibly clean the finding from last step on your production VM. • Learn about the scope of the damage done to your system, i. e. what is the extent of data leakage

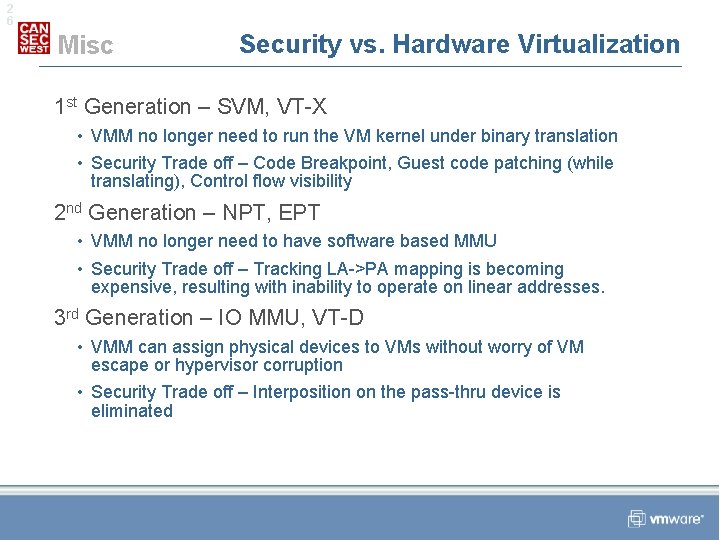
2 6 Misc Security vs. Hardware Virtualization 1 st Generation – SVM, VT-X • VMM no longer need to run the VM kernel under binary translation • Security Trade off – Code Breakpoint, Guest code patching (while translating), Control flow visibility 2 nd Generation – NPT, EPT • VMM no longer need to have software based MMU • Security Trade off – Tracking LA->PA mapping is becoming expensive, resulting with inability to operate on linear addresses. 3 rd Generation – IO MMU, VT-D • VMM can assign physical devices to VMs without worry of VM escape or hypervisor corruption • Security Trade off – Interposition on the pass-thru device is eliminated

2 7 Misc Some New Problems To Solve VM Escape • Though impossible by design, the hypervisor can still have implementation vulnerabilities * • As more trust is placed in the hypervisor the more motivation there will be to find VM escapes • VM escape provide a new “hyper escalation” that never existed before.

2 8 Misc Some New Problems To Solve New attacks to consider • VMs as malware • A malicious VM with the proper isolation configuration can exploit the host system using writable shared folder • In a similar way, a VM that is not firewalled properly can easily access the host network or any device reachable by the host network • Moral of the story – Handle suspicious VMs with care.

2 9 Conclusion Questions? Contact odedh@vmware. com