Virtualization and Cloud Security Huzur Saran IIT Delhi








- Slides: 16

Virtualization and Cloud Security Huzur Saran IIT Delhi

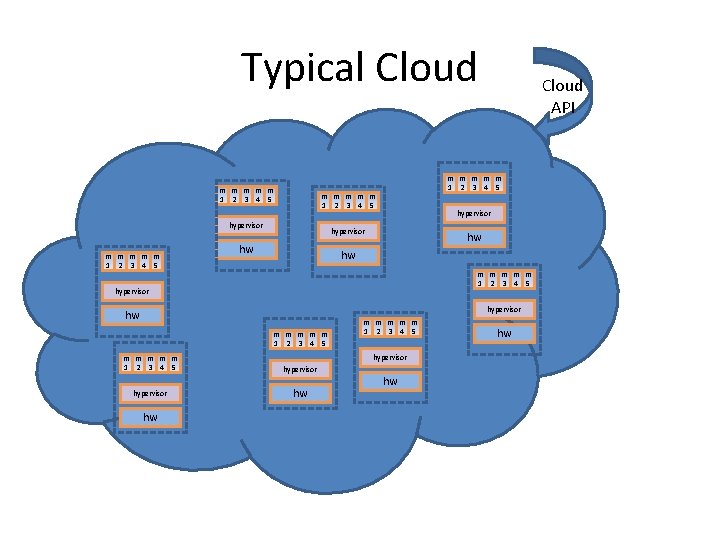
Typical Cloud m m m m m 1 2 3 4 5 hypervisor hw Cloud API hw hw m m m 1 2 3 4 5 hypervisor hw m m m m m 1 2 3 4 5 hypervisor hw hw m m m 1 2 3 4 5 hw hw

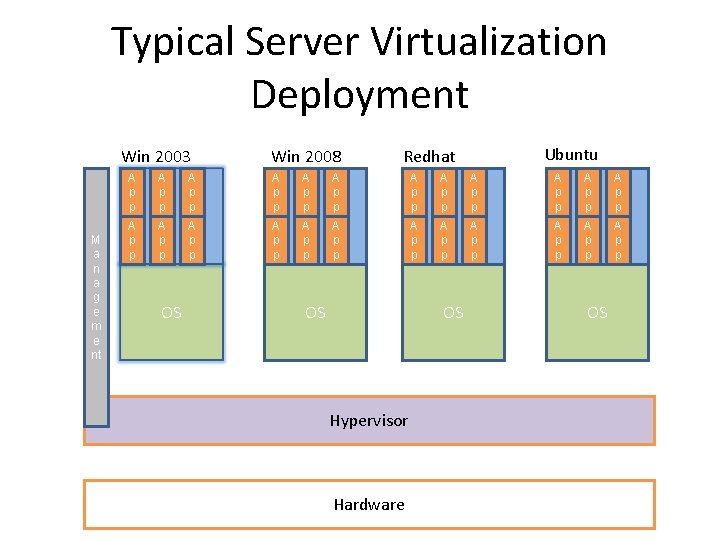
Typical Server Virtualization Deployment Win 2003 M a n a g e m e nt Win 2008 Ubuntu Redhat A p p A p p A p p A p p A p p A p p OS OS OS Hypervisor Hardware OS

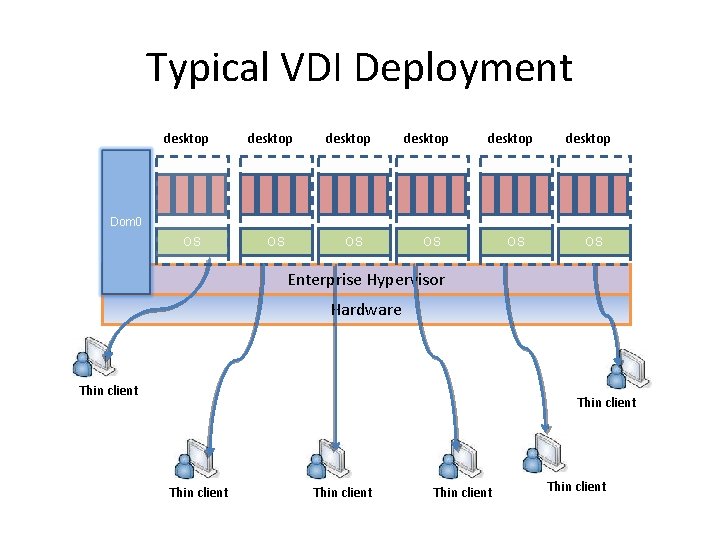
Typical VDI Deployment desktop desktop Dom 0 OS OS OS Enterprise Hypervisor Hardware Thin client Thin client

Security Issues • Hypervisor is the underlying component of all these architectures. It is a new layer which needs to be protected • Scale of deployments – Just the sheer scale of deployments make this a security nightmare. Imagine 150 machines running a simultaneous scheduled AV scan on the same physical host. Chokes IO/Disk bandwidth. • Isolation - Machines of a company and its competitor could be running on the same physical machine. Insufficient isolation could lead to disaster • New API’s to access Virtualization/Cloud services. Bugs in these could lead to compromise of entire infrastructure.

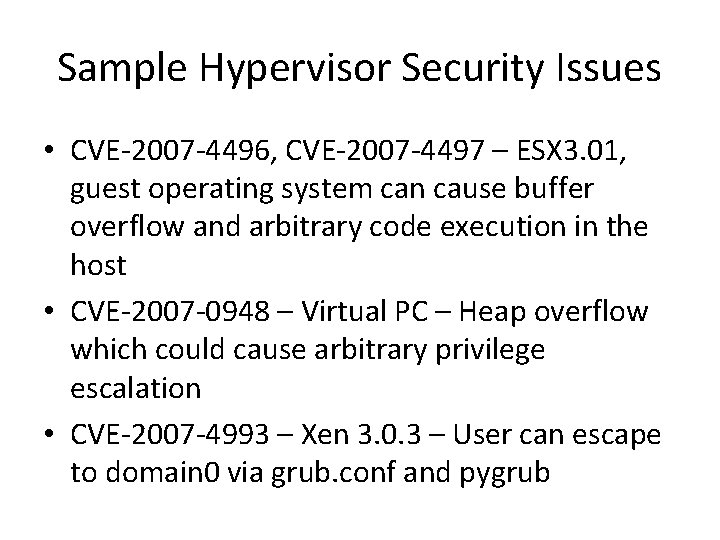
Sample Hypervisor Security Issues • CVE-2007 -4496, CVE-2007 -4497 – ESX 3. 01, guest operating system can cause buffer overflow and arbitrary code execution in the host • CVE-2007 -0948 – Virtual PC – Heap overflow which could cause arbitrary privilege escalation • CVE-2007 -4993 – Xen 3. 0. 3 – User can escape to domain 0 via grub. conf and pygrub

Security Issues – Why? • Hypervisors are written by humans. They have bugs – typically buffer overflows • Hypervisor are complex – Xen is about 300 K source lines of code • Complete isolation is hard – Most systems don’t have IOMMU’s which make it possible to DMA to arbitrary physical memory • Compromised Domain 0 on Xen pretty much means a hosed hypervisor. Domain 0 runs commodity OS’s which could have bugs.

Security Issues – Why? • DMA is a big problem on non IOMMU based systems: – Xen can setup DMA – Dom 0 can setup DMA – Driver domains can setup DMA • The range of physical addresses is not verified • IOMMU based systems can restrict the range of addresses but they are not present in commodity hardware • There are some techniques to even bypass IOMMU checks

Security Solutions • Trusted hypervisor – Hyperguard – Phoenix Technologies – A hypervisor integrity scanner in SMM. – Deepwatch – Intel project – Virtualization rootkit scanner • Domain 0 Hardening – Various security solutions to white-list and harden Dom 0

Security Opportunities • New breed of security products is now possible to protect guest OS’s from being hijacked • Hypervisor based security suites cannot be detected by malware running in the guest • Hypervisors allow introspection of very early boot sequences of the guest, thereby making possible an entire need breed of BIOS rootkit and kernel rootkit scanners

Security Opportunities • API’s like VMSAFE from VMWare allow introspection of interesting system events in the guests • These events can then be processed on a dedicated security appliance • These events include CPU state monitoring, page faults, memory/register accesses, Filesystem events, network events etc.

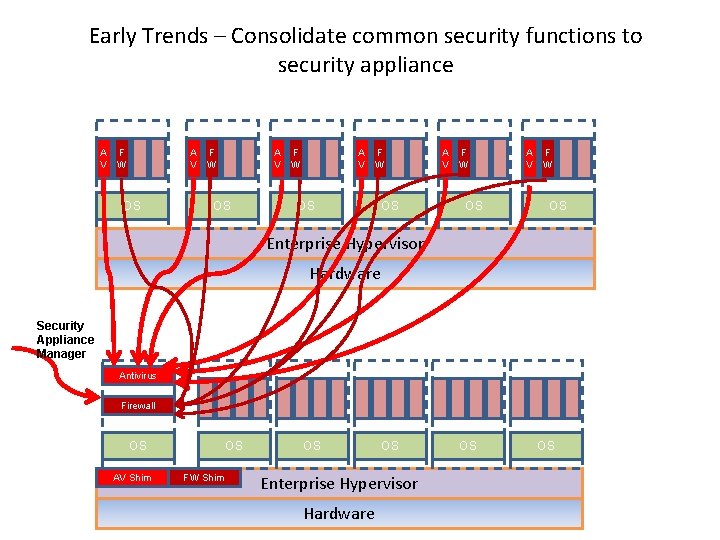
Early Trends – Consolidate common security functions to security appliance A F V W OS A F V W OS Enterprise Hypervisor Hardware Security Appliance Manager Antivirus Firewall OS AV Shim OS FW Shim OS OS Enterprise Hypervisor Hardware OS OS

Security is hard – at all levels A prisoner was wrongly released after a fax was received from a grocery store stating that the Kentucky Supreme Court had demanded his release: http: //www. cnn. com/2007/US/04/21/wrongly. freed. a p/index. html

Security principles Open design: you need all the help you can get Economy of mechanism: fewer things to get right Minimize secrets: secrets don’t remain secret Fail-safe defaults: most users won’t change them Least privilege: limit the damage of an accident Separation of privilege: dangerous operation should require multiple principals

Sample Security Issues • http: //taviso. decsystem. org/virtsec. pdf Paper detailing several bugs in Virtual PC, Xen, Vmware, Parallels and BOCHS. • http: //www. theregister. co. uk/2009/10/09/am azon_cloud_bitbucket_ddos_aftermath/ - UDP flood based DDo. S against Amazon EC 2 • Argument handling bugs in FLASK (Xen)

Example: A specially crafted poke to I/O port 0 x 1004, results in an out-ofbounds write to an attacker controlled location. By interacting with the power management subsystem in specific ways, a write to an arbitrary location can be performed upon restarting a suspended virtual machine. VMware PIIX 4 ACPI PM OOB Write section. text global _start: mov eax, 110 mov ebx, 3 int 0 x 80 a mov ax, 0 x 6 c 81 mov dx, 0 x 1004 out dx, ax xor ebx, ebx xor eax, eax inc eax int 0 x 80 a. iopl()