Virtual Private Networks VPNs motivation vinstitutions often want





- Slides: 16

Virtual Private Networks (VPNs) motivation: vinstitutions often want private networks for security. § costly: separate routers, links, DNS infrastructure. v. VPN: institution’s inter-office traffic is sent over public Internet instead § encrypted before entering public Internet § logically separate from other traffic Network Security 8 -1

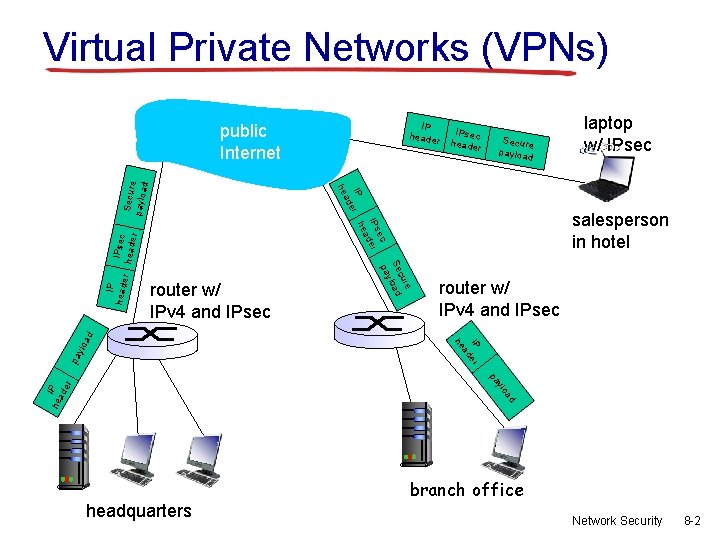
Virtual Private Networks (VPNs) IP header Secure payloa d IPsec heade r r router w/ IPv 4 and IPsec pa IP er ad he ylo a d router w/ IPv 4 and IPsec laptop w/ IPsec salesperson in hotel e cur Se load y pa IP heade IPsec header ec IPs der ea IP r h e ad he Secur e payloa d public Internet ad ylo I he P ad er pa headquarters branch office Network Security 8 -2

IPsec services v v v data integrity origin authentication replay attack prevention confidentiality two protocols providing different service models: § AH § ESP Network Security 8 -3

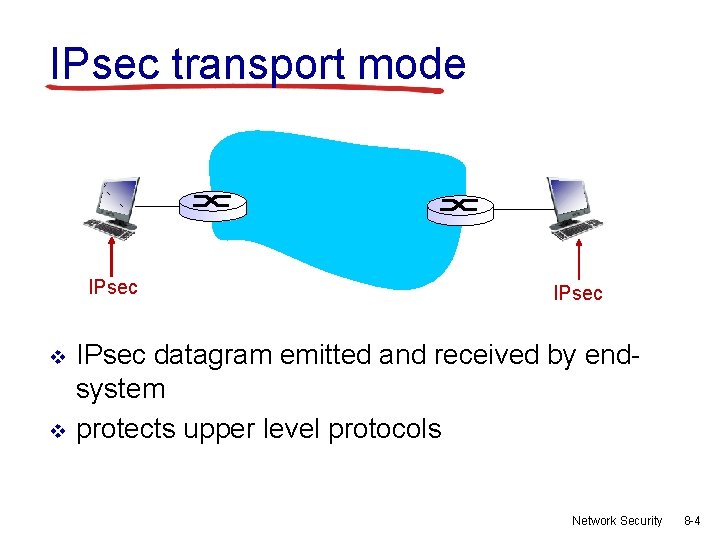
IPsec transport mode IPsec v v IPsec datagram emitted and received by endsystem protects upper level protocols Network Security 8 -4

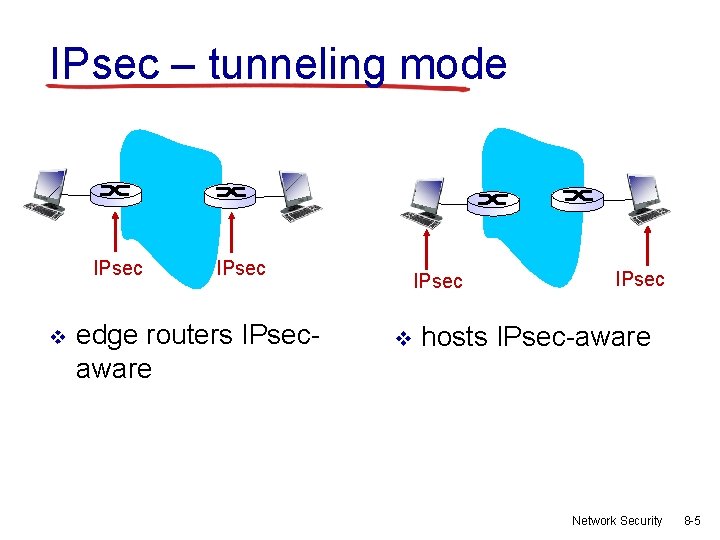
IPsec – tunneling mode IPsec v IPsec edge routers IPsecaware IPsec v IPsec hosts IPsec-aware Network Security 8 -5

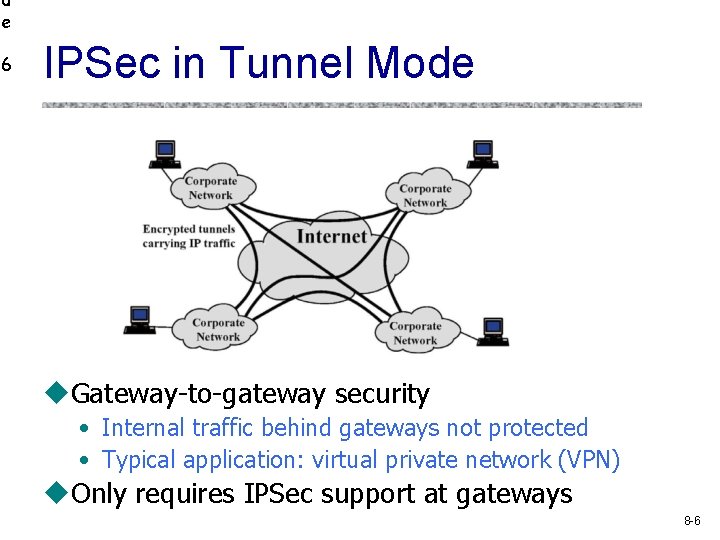
d e 6 IPSec in Tunnel Mode Gateway-to-gateway security • Internal traffic behind gateways not protected • Typical application: virtual private network (VPN) Only requires IPSec support at gateways 8 -6

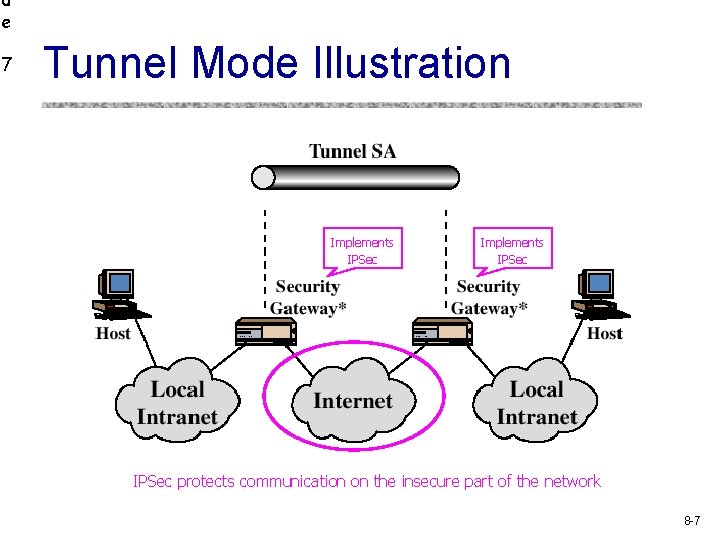
d e 7 Tunnel Mode Illustration Implements IPSec protects communication on the insecure part of the network 8 -7

Security associations (SAs) v before sending data, “security association (SA)” established from sending to receiving entity § SAs are simplex: for only one direction v ending, receiving entitles maintain state information about SA § recall: TCP endpoints also maintain state info § IP is connectionless; IPsec is connection-oriented! v how many SAs in VPN w/ headquarters, branch office, and n traveling salespeople? Network Security 8 -8

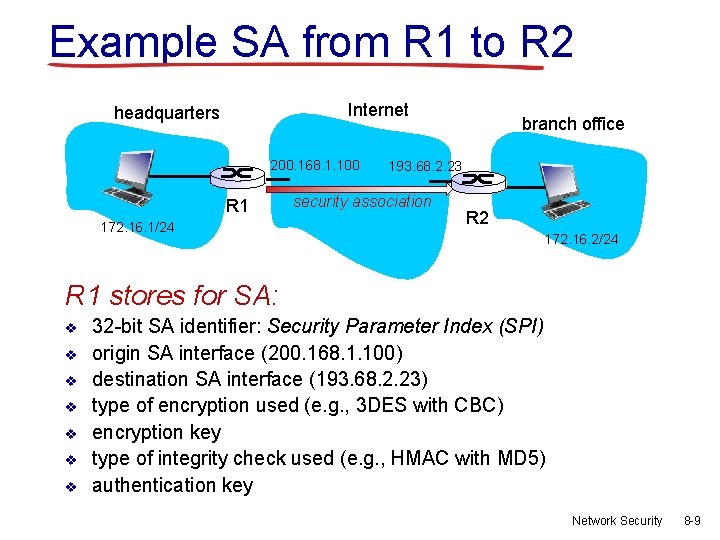
Example SA from R 1 to R 2 Internet headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 branch office 193. 68. 2. 23 security association R 2 172. 16. 2/24 R 1 stores for SA: v v v v 32 -bit SA identifier: Security Parameter Index (SPI) origin SA interface (200. 168. 1. 100) destination SA interface (193. 68. 2. 23) type of encryption used (e. g. , 3 DES with CBC) encryption key type of integrity check used (e. g. , HMAC with MD 5) authentication key Network Security 8 -9

Security Association Database (SAD) endpoint holds SA state in security association database (SAD), where it can locate them during processing. v with n salespersons, 2 + 2 n SAs in R 1’s SAD v when sending IPsec datagram, R 1 accesses SAD to determine how to process datagram. v when IPsec datagram arrives to R 2, R 2 examines SPI in IPsec datagram, indexes SAD with SPI, and processes datagram accordingly. v Network Security 8 -10

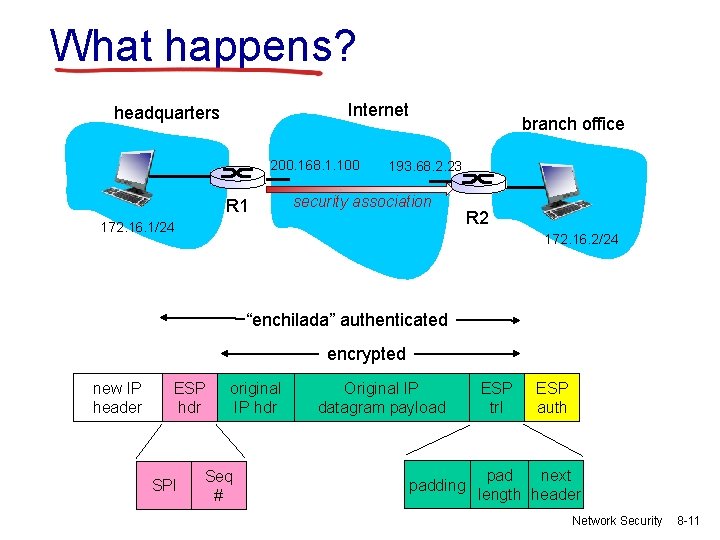
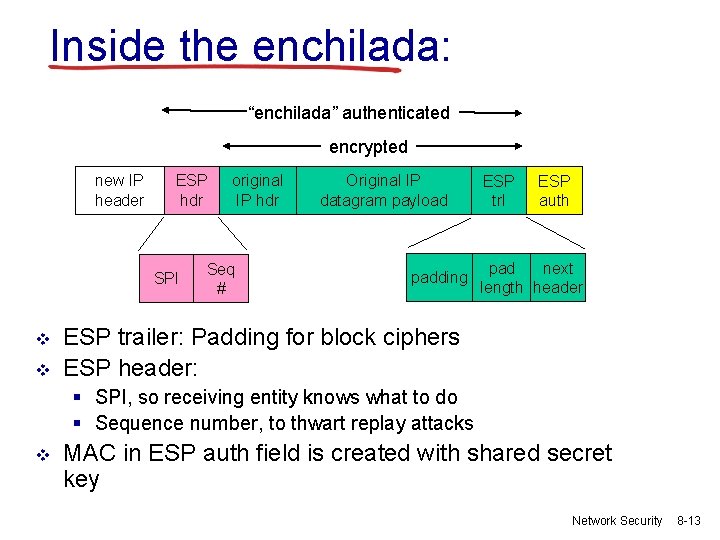
What happens? Internet headquarters 200. 168. 1. 100 R 1 branch office 193. 68. 2. 23 security association 172. 16. 1/24 R 2 172. 16. 2/24 “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header Network Security 8 -11

R 1: convert original datagram to IPsec datagram v v v appends to back of original datagram (which includes original header fields!) an “ESP trailer” field. encrypts result using algorithm & key specified by SA. appends to front of this encrypted quantity the “ESP header, creating “enchilada”. creates authentication MAC over the whole enchilada, using algorithm and key specified in SA; appends MAC to back of enchilada, forming payload; creates brand new IP header, with all the classic IPv 4 header fields, which it appends before payload. Network Security 8 -12

Inside the enchilada: “enchilada” authenticated encrypted new IP header ESP hdr SPI v v original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header ESP trailer: Padding for block ciphers ESP header: § SPI, so receiving entity knows what to do § Sequence number, to thwart replay attacks v MAC in ESP auth field is created with shared secret key Network Security 8 -13

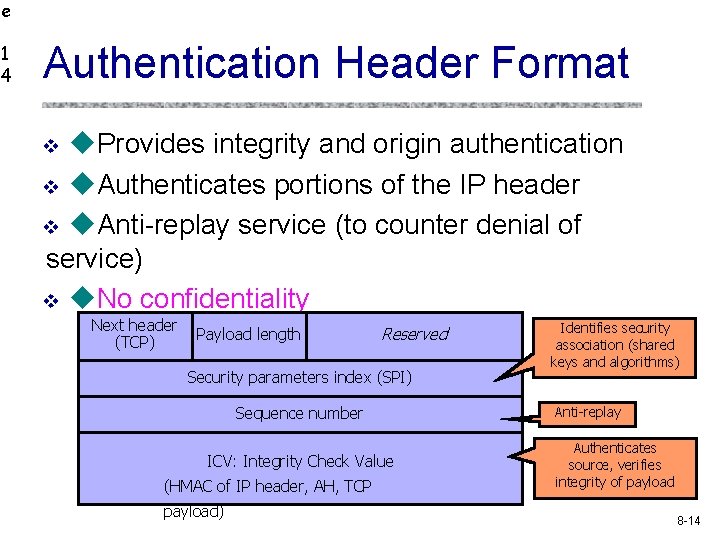
e 1 4 Authentication Header Format Provides integrity and origin authentication v Authenticates portions of the IP header v Anti-replay service (to counter denial of service) v No confidentiality v Next header (TCP) Payload length Reserved Security parameters index (SPI) Sequence number ICV: Integrity Check Value (HMAC of IP header, AH, TCP payload) Identifies security association (shared keys and algorithms) Anti-replay Authenticates source, verifies integrity of payload 8 -14

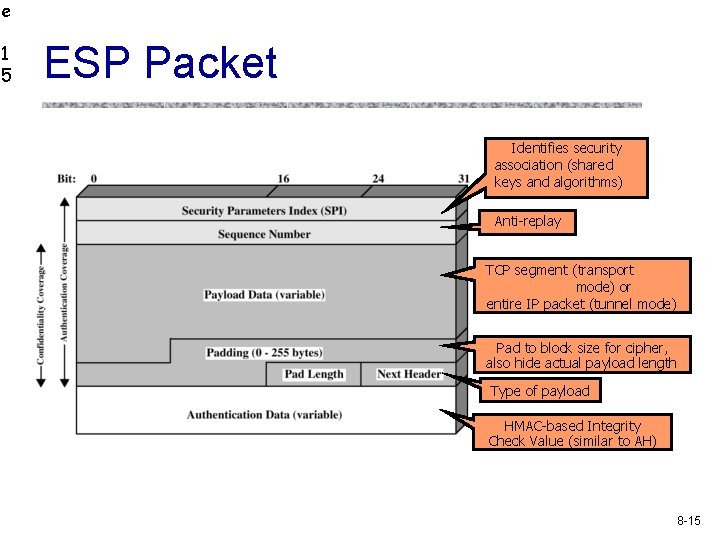
e 1 5 ESP Packet Identifies security association (shared keys and algorithms) Anti-replay TCP segment (transport mode) or entire IP packet (tunnel mode) Pad to block size for cipher, also hide actual payload length Type of payload HMAC-based Integrity Check Value (similar to AH) 8 -15

IPsec sequence numbers v v for new SA, sender initializes seq. # to 0 each time datagram is sent on SA: § sender increments seq # counter § places value in seq # field v goal: § prevent attacker from sniffing and replaying a packet § receipt of duplicate, authenticated IP packets may disrupt service v method: § destination checks for duplicates Network Security § doesn’t keep track of all received packets; instead 8 -16