Virtual Private Networks VPNs By Ryan Joyce What

Virtual Private Networks (VPNs) By Ryan Joyce
What is a Virtual Network ? An interconnected group of networks (an internet) that appears as one large network to a specific user What is a Virtual Private Network? A Virtual Private Network is a Virtual Network that is secure and has attributes of LAN but over much larger scale.
History of VPNs u Started with • Wide Area Networks (WANS) Expansive leased lines u reliable u secure u Very expensive u • Intranets (LANs) Limited u reliable u Secure u Relatively inexpensive u
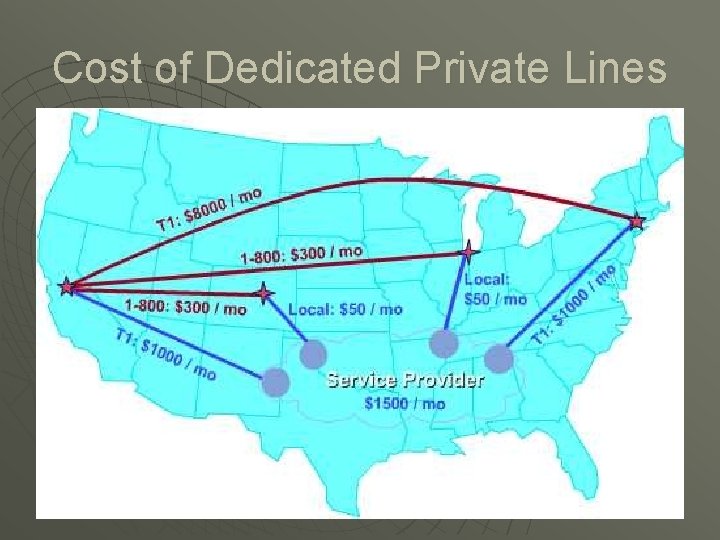
Cost of Dedicated Private Lines

History (continued) Virtual Private Networks are relatively new u Technology was created in the mid 90 s u Was not made mains stream until couple years ago u

Why have VPNs? Extend communications on a global scale u Create better communication with business partners u Decrease the cost of having to use traditional methods u Faster more effective reliable business u
Video u VPN Video
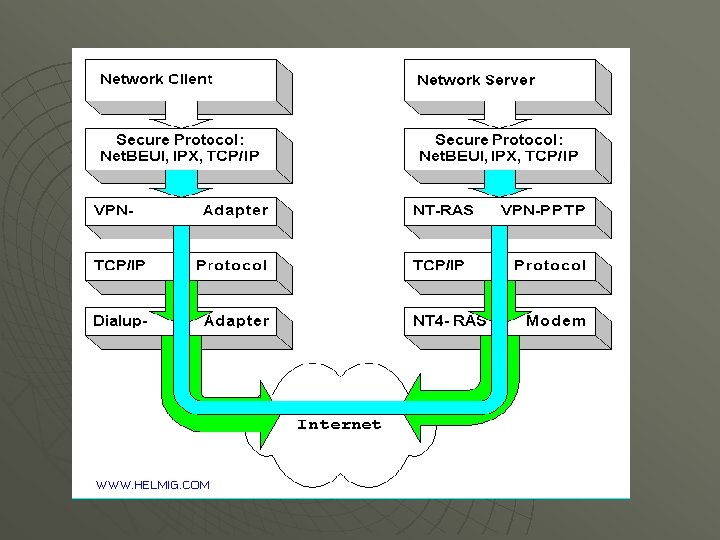
VPN Setups u Variety of Options • Hardware based VPN firewalls u edge routers u • Software base u VPN clients • Mixed

VPN Hardware

VPN Software

VPN Setups u Remote Users • Refers to communication access of a company’s network to remote or mobile employees (home users) • Requires monitoring and strong authentication practices • Scalability remains and important issue must be able to handle larger number of users.
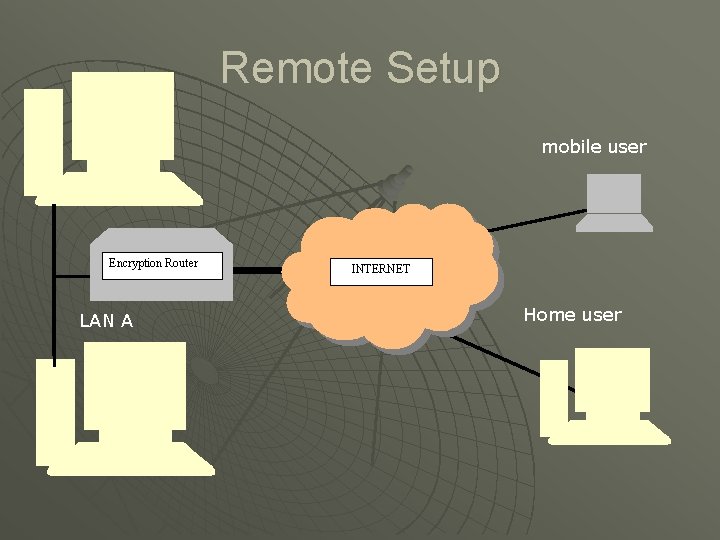
Remote Setup mobile user Encryption Router LAN A INTERNET Home user

VPN Setups u Intranet Setup • Refers to linking a companies internal branches or subsidiaries together • Requires high security, must be able to transmit and receive sensitive information • Requires high reliability, applications that effect day to day operations • Scalable to a point.
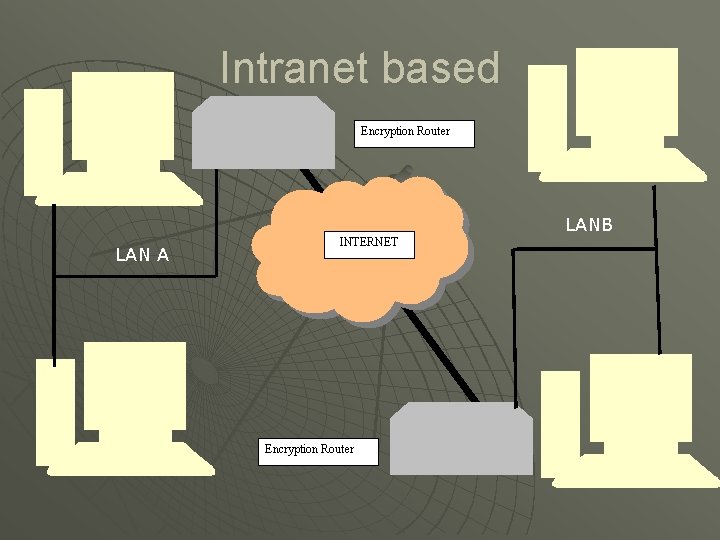
Intranet based Encryption Router LANB LAN A INTERNET Encryption Router

VPN Setups u Extranet Setups • Refers to VPN between companies customers and suppliers • Requires standardization the IPSec current standard for VPNs • Need for traffic control, networks must be monitored for accurate delivery of critical data
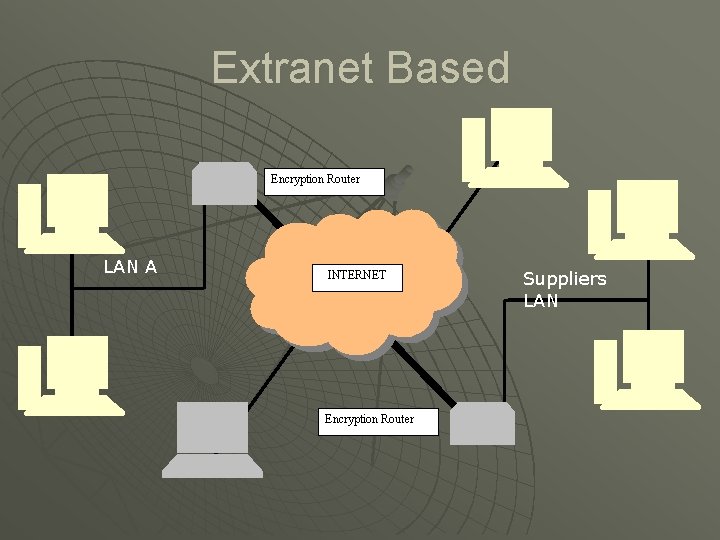
Extranet Based Encryption Router LAN A INTERNET Encryption Router Suppliers LAN
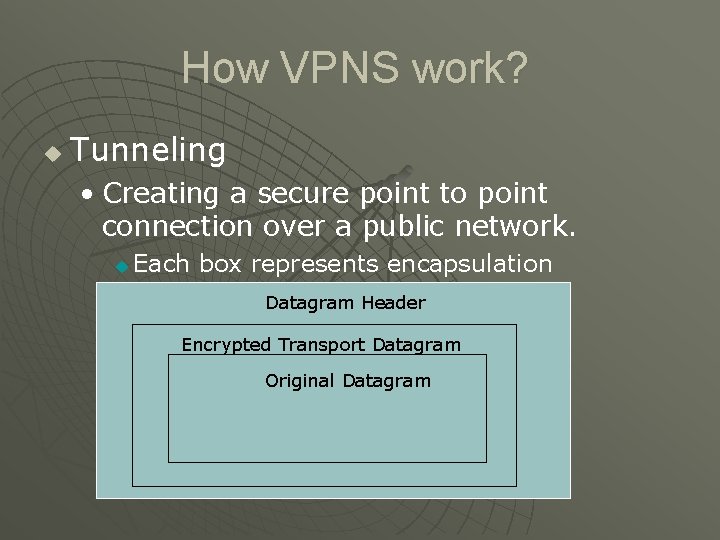
How VPNS work? u Tunneling • Creating a secure point to point connection over a public network. u Each box represents encapsulation Datagram Header Encrypted Transport Datagram Original Datagram

Security Requirements and Approaches u Confidentiality • refers to the privacy of information being exchanged between communicating parties. u Encryption • secret key cryptography • Public key cryptography

Encryption u u u Public Key Private Key MD 5 • Message digest “hashing” algorrithm u SET protocol • Secure electronic transactions u SSl protocol • Secure socket layer protocol

Security Requirements and Approaches u Data Integrity • Integrity ensures that information being transmitted over the public Internet is not altered in any way during transit. u Insuring Data • One way hash functions • Message-authentication codes • Digital signatures

Security Requirements and Approaches u Authentication • Ensuring the identities of all communicating parties. u Authentication practices • Password authentication • Digital certificates • Token cards created from a time stamp

VPN Protocols u IPSec (Internet Protocol Security) u • Developed by IETF • designed to address IP based networks • encapsulates a packet with another packet and encrypts the packet PPTP (Point to Point Tunneling Protocol) • Used for remote users • Encapsulates packets
VPN Protocols (continued) u L 2 TP (Layer 2 tunneling protocol) • • • u Evolved from PPTP Client aware tunneling Client transparent tunneling Socks 5 • • Circuit level protocol Originally designed to authenticate protocols mainly use for extranet configurations great for user level application control
Selecting A VPN Things to consider u Integration u • Will it be compatible with existing intranets • Software versus Hardware Software cheap more difficult to implement less reliable slower u Hardware more expensive easy to set up more reliable faster u
Applications of VPNs u Manufacturing • Factory operations linking corporate headquarters to all of its facilities u Retail • Local stores connected directly to regional offices delivering relevant sales data u Medical • Transferring patient data across hospital networks u Finance • Online banking transactions, remote user access
Applications VPNs u Home users Windows VPN connection u VPN Connection Video u

Problems with VPNs Setup Times u Difficult Trouble Shooting u Interoperability with other networks u Reliability with ISPs u Bandwidth Constraints u
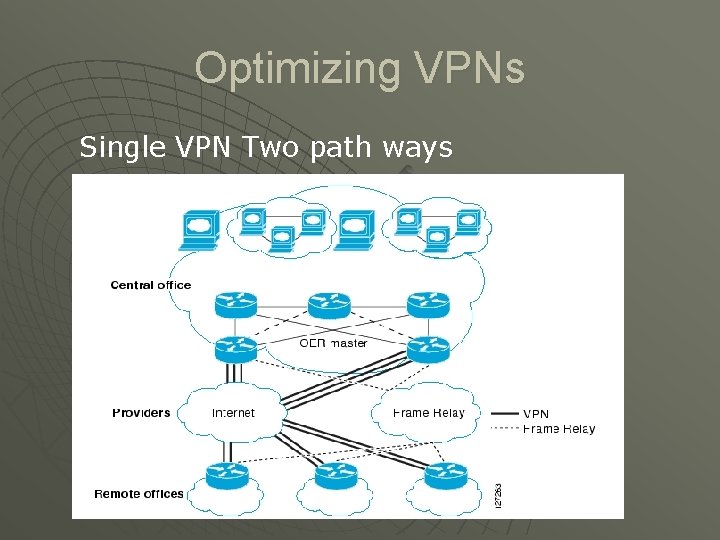
Optimizing VPNs Single VPN Two path ways
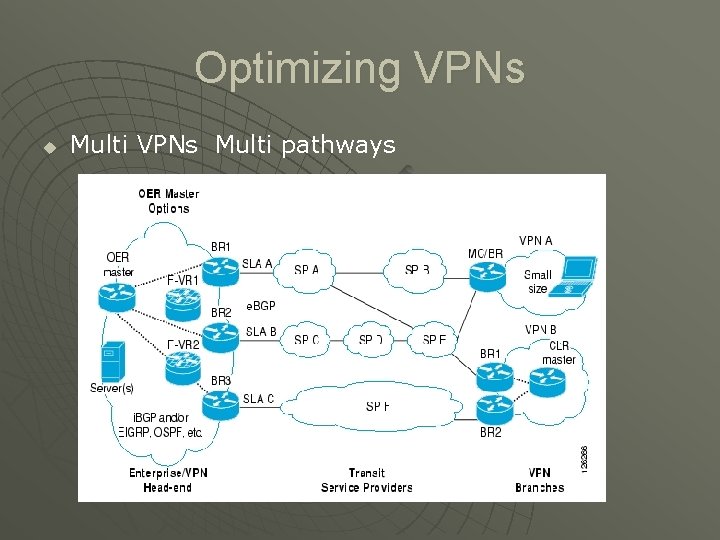
Optimizing VPNs u Multi VPNs Multi pathways

The Future of VPNs Protocol Standardization u New hardware u Better Software u Used more frequently u Will become the new business standard u

References u u Dunigan, Tom. Virtual Private Networks Retrieved October 15, 2007 Posted October 13, 2004 http: //www. csm. ornl. gov/~dunigan/vpn. html Mc. Donald, Christopher. Virtual Private Networks An overview Retrieved. October 16, 2007 from Intranet Journal. com http: //www. intranetjournal. com/foundation/vpn-1. shtml Virtual Private Networks. Retrieved October 16, 2007 from Cisco Posted October 12 , 2006. http: //www. cisco. com/univercd/cc/td/doc/cisintwk/ito_doc/vpn. ht m Virtual Private Networking Retrieved October 15, 2007 http: //www. microsoft. com/technet/isa/2004/help/fw_VPNIntro. ms px? mfr=true
- Slides: 32