VIRTUAL PRIVATE NETWORKS VPN WAN Technology Comparison WAN






- Slides: 33

VIRTUAL PRIVATE NETWORKS (VPN)

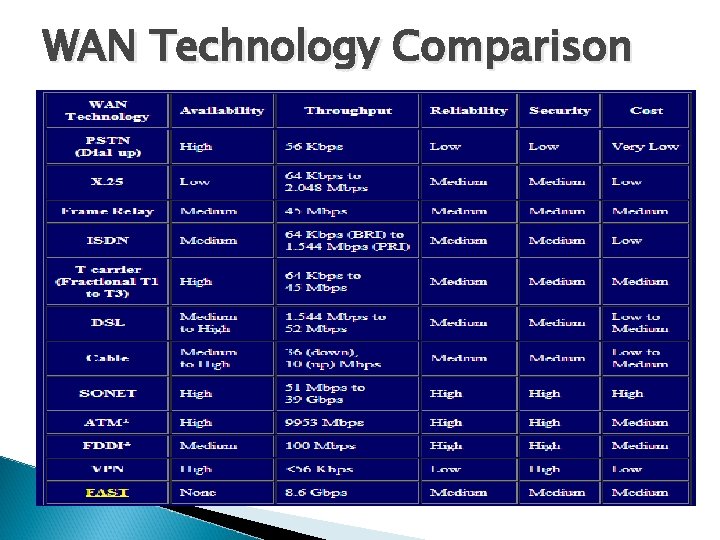
WAN Technology Comparison

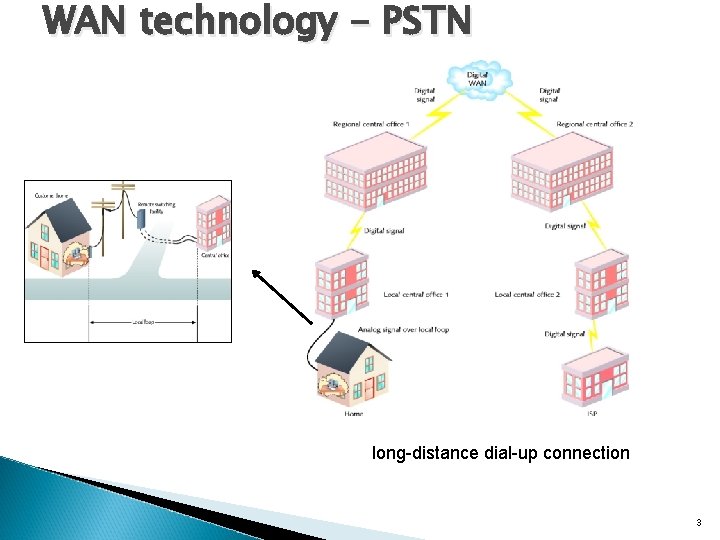
WAN technology - PSTN long-distance dial-up connection 3

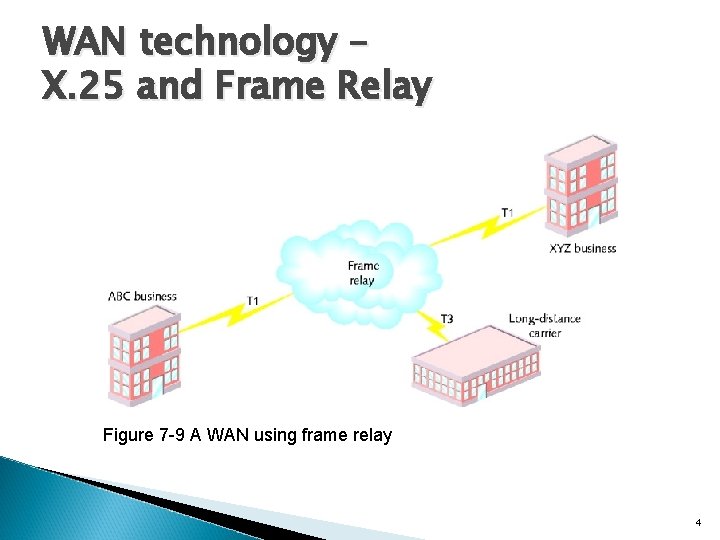
WAN technology – X. 25 and Frame Relay Figure 7 -9 A WAN using frame relay 4

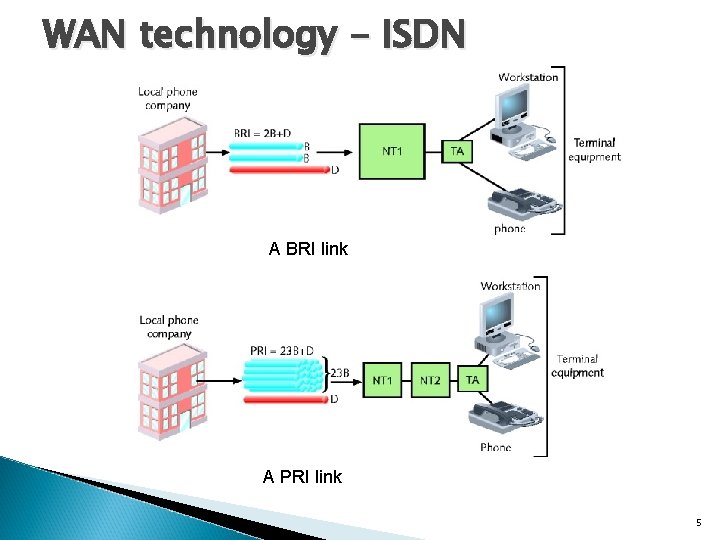
WAN technology - ISDN A BRI link A PRI link 5

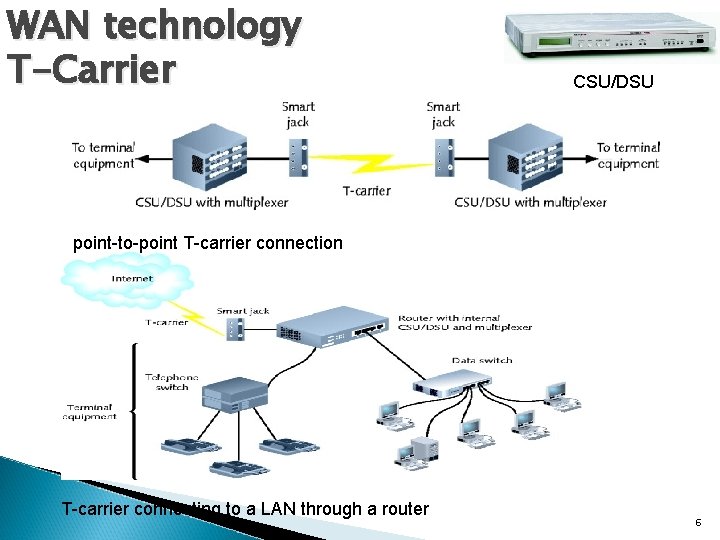
WAN technology T-Carrier CSU/DSU point-to-point T-carrier connection T-carrier connecting to a LAN through a router 6

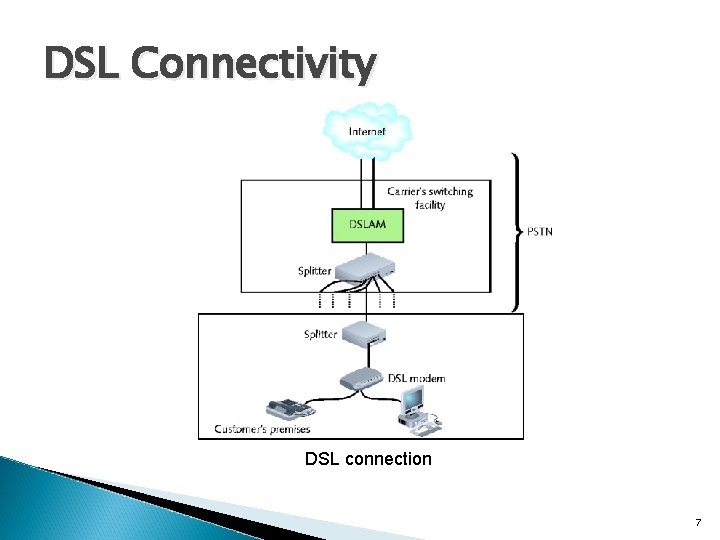
DSL Connectivity DSL connection 7

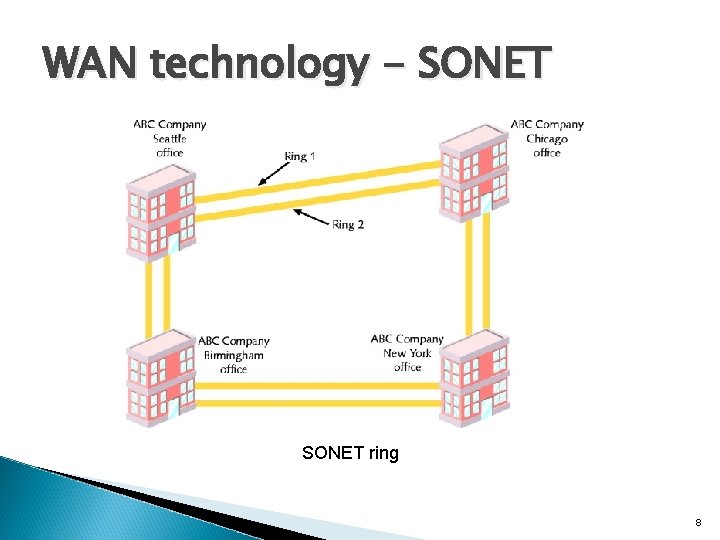
WAN technology - SONET ring 8

What is VPN? Ø Virtual Private Network is a type of private network that uses public telecommunication, such as the Internet, instead of leased lines to communicate. Ø Became popular as more employees worked in remote locations.

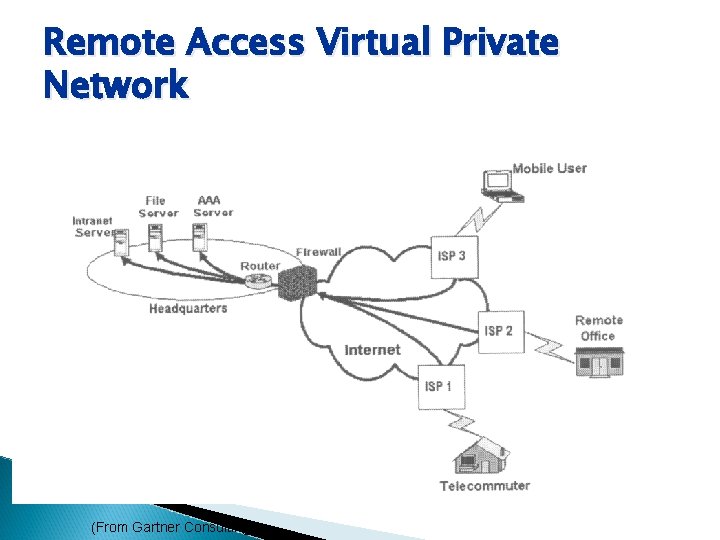
Remote Access Virtual Private Network (From Gartner Consulting)

VPN: Types Secure VPNs use cryptographic tunneling protocols. ◦ IPsec, SSL/TLS, Open. VPN, PPTP, L 2 TPv 3, VPNQ and MPVPN Trusted VPNs rely on the security of a single provider’s network to protect the traffic. ◦ MPLS and L 2 F

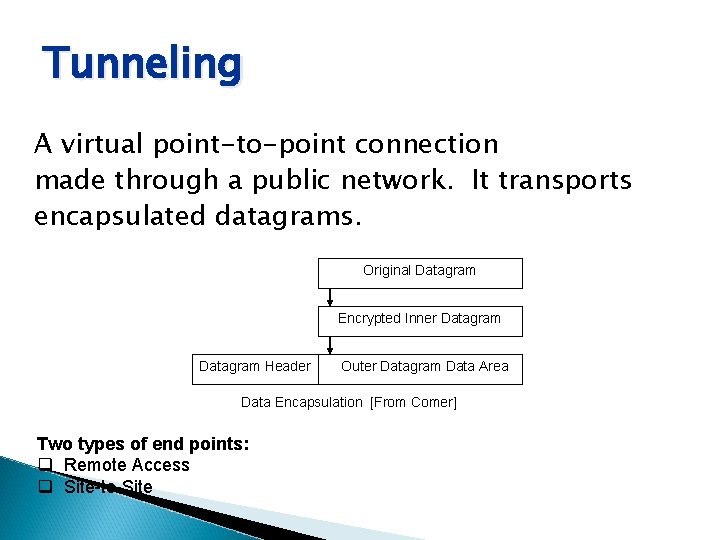
Tunneling A virtual point-to-point connection made through a public network. It transports encapsulated datagrams. Original Datagram Encrypted Inner Datagram Header Outer Datagram Data Area Data Encapsulation [From Comer] Two types of end points: q Remote Access q Site-to-Site

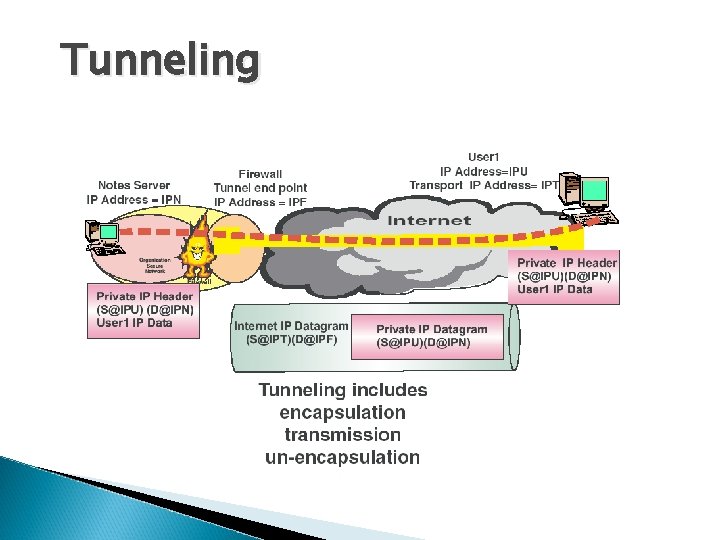
Tunneling

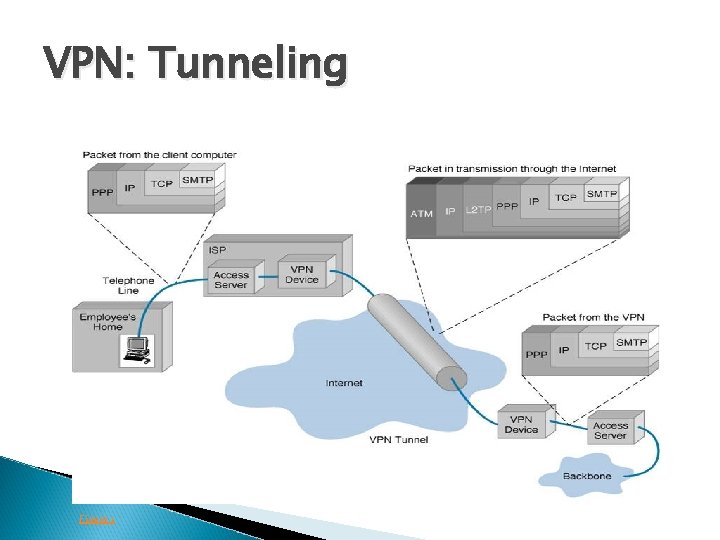
VPN: Tunneling Figure 1

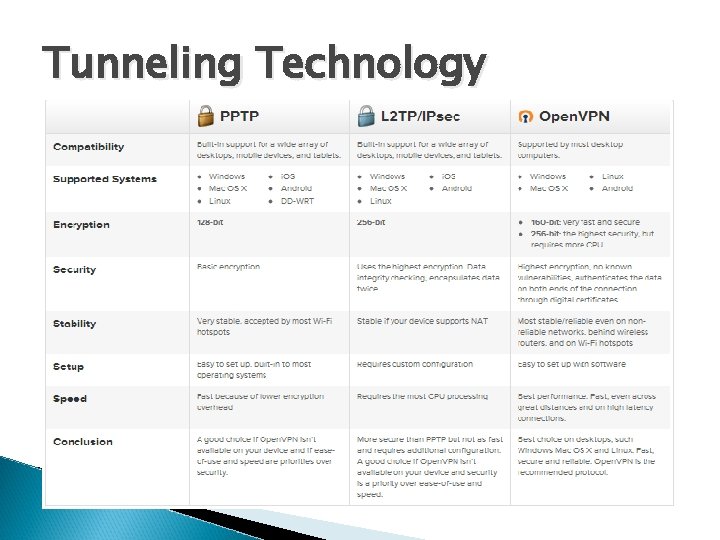
Tunneling Technology

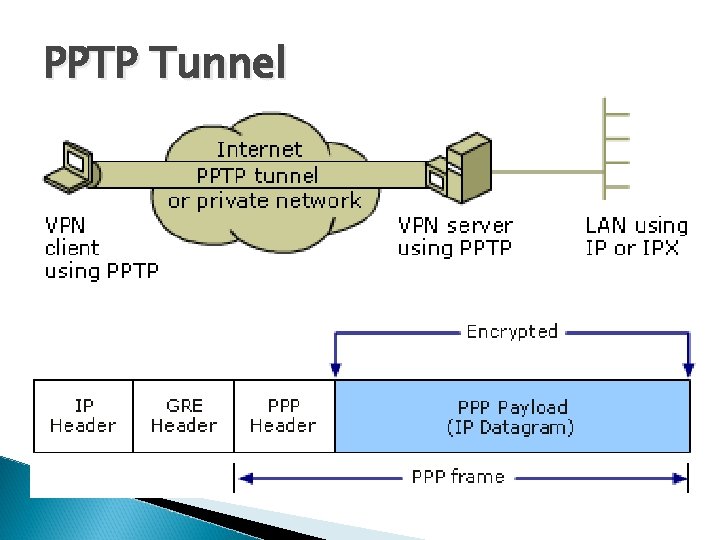
PPTP Tunnel

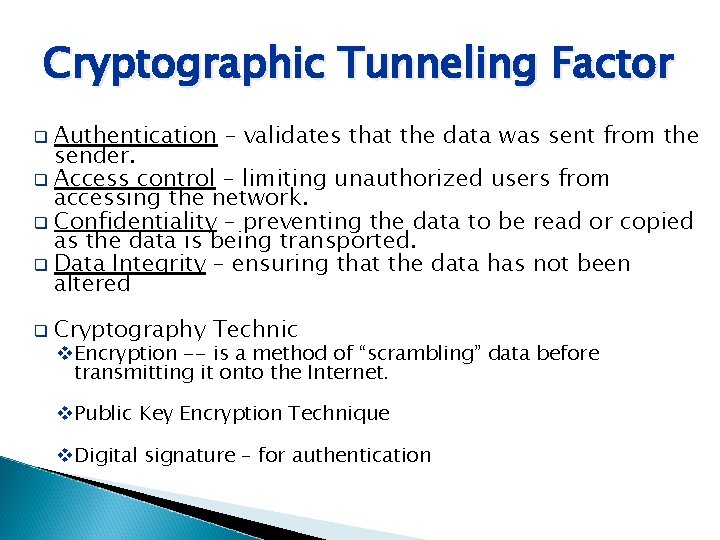
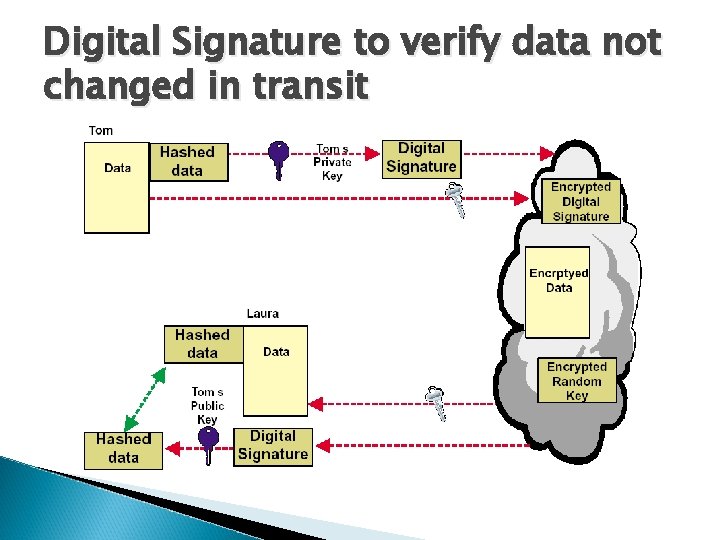
Cryptographic Tunneling Factor Authentication – validates that the data was sent from the sender. q Access control – limiting unauthorized users from accessing the network. q Confidentiality – preventing the data to be read or copied as the data is being transported. q Data Integrity – ensuring that the data has not been altered q q Cryptography Technic v. Encryption -- is a method of “scrambling” data before transmitting it onto the Internet. v. Public Key Encryption Technique v. Digital signature – for authentication

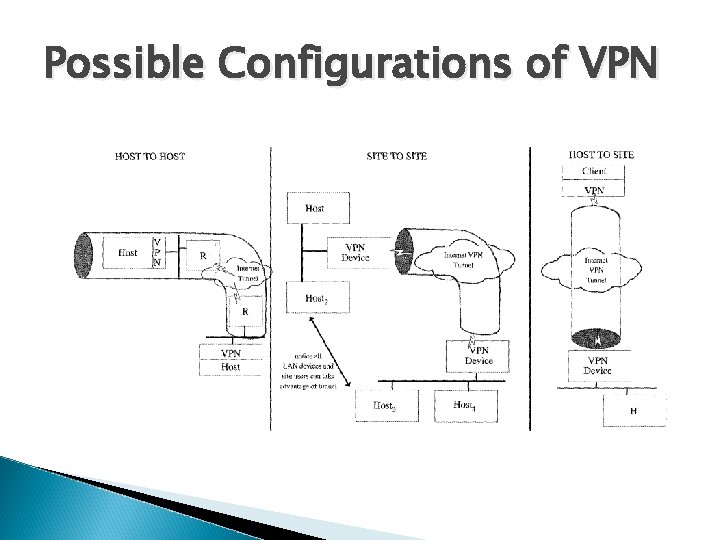
Virtual Private Networks VPN can be deployed in three ways : Host to host Site-to-Site Host-to-Site

Possible Configurations of VPN

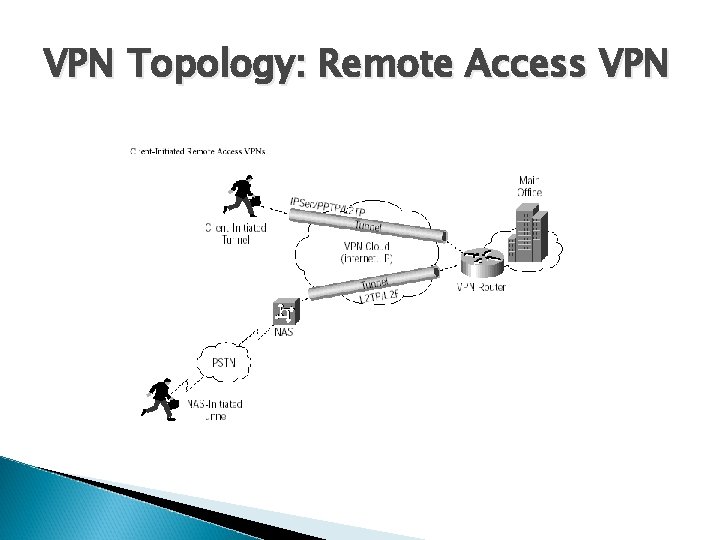
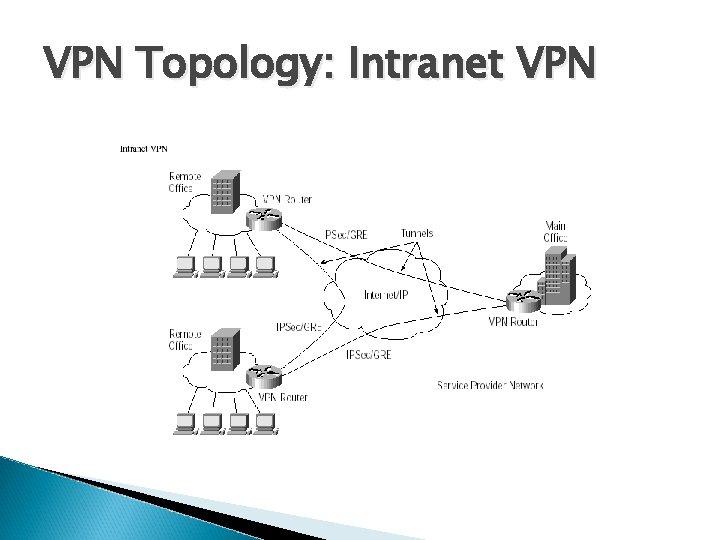
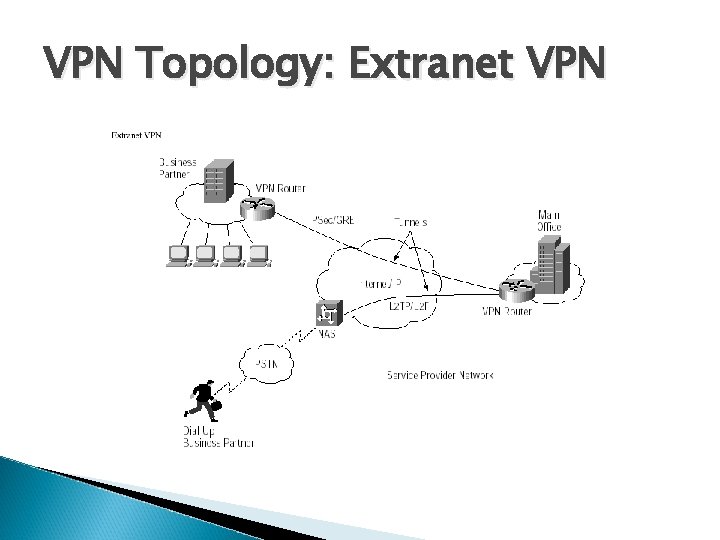
VPN Topology: Types of VPNs Remote access VPN Intranet VPN Extranet VPN

VPN Topology: Remote Access VPN

VPN Topology: Intranet VPN

VPN Topology: Extranet VPN

Digital Signature to verify data not changed in transit

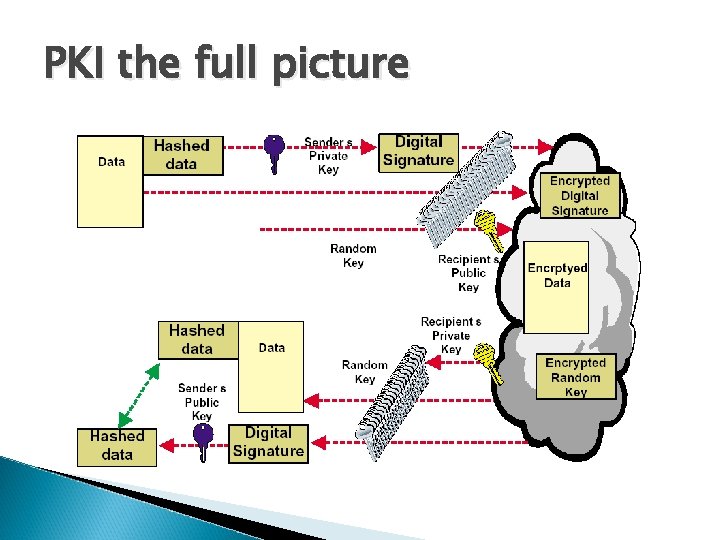
PKI the full picture

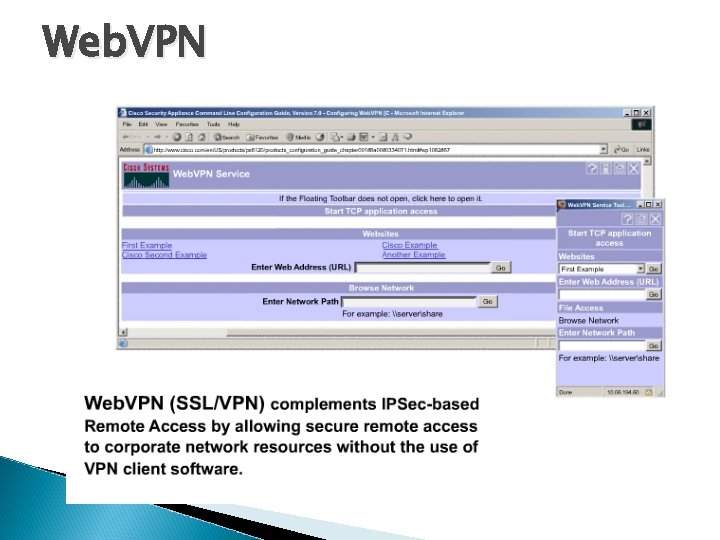
Web. VPN

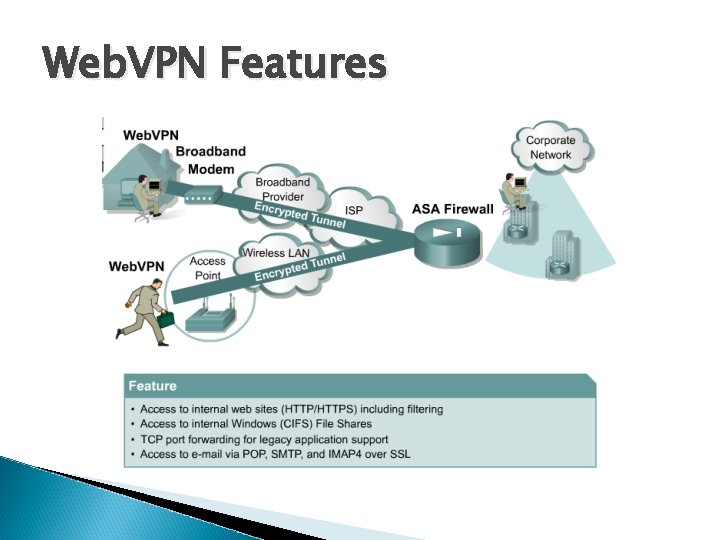
Web. VPN Features

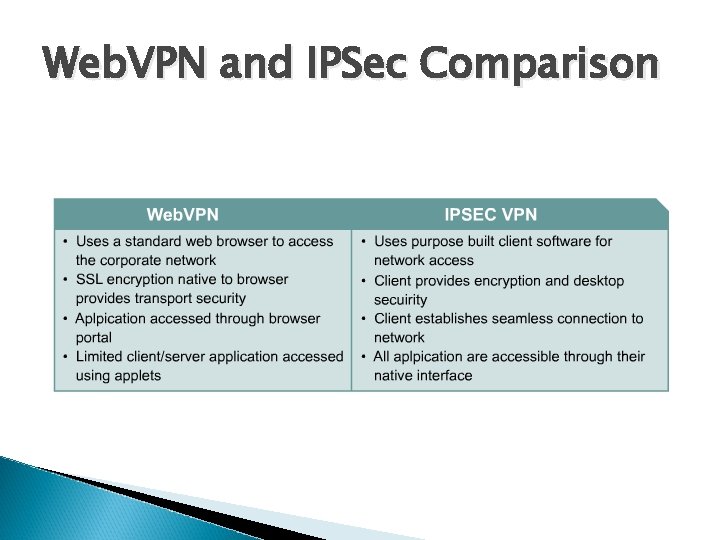
Web. VPN and IPSec Comparison

Intro to MPLS = Multi Protocol Label Switching Suatu metode forwarding (meneruskan data/paket melalui suatu jaringan dengan menggunakan informasi label yang dilekatkan pada I Memungkinkan router meneruskan paket dengan hanya melihat label yang melekat pada paket tersebut, sehinggap tidak perlu lagi melihat alamat IP tujuan)

Back

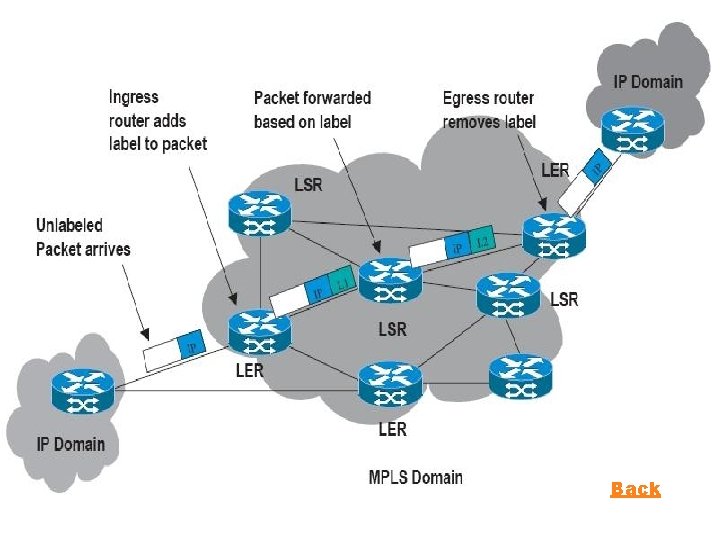
2. ARSITEKTUR MPLS Perpaduan mekanisme Label Swapping (Layer 2) dan Routing (Layer 3) Terdiri atas LSR yang saling terhubung, membentuk suatu LSP LSR pertama disebut ingress LSR terakhir disebut egress Bagian tepi dari jaringan LSR disebut LER Back

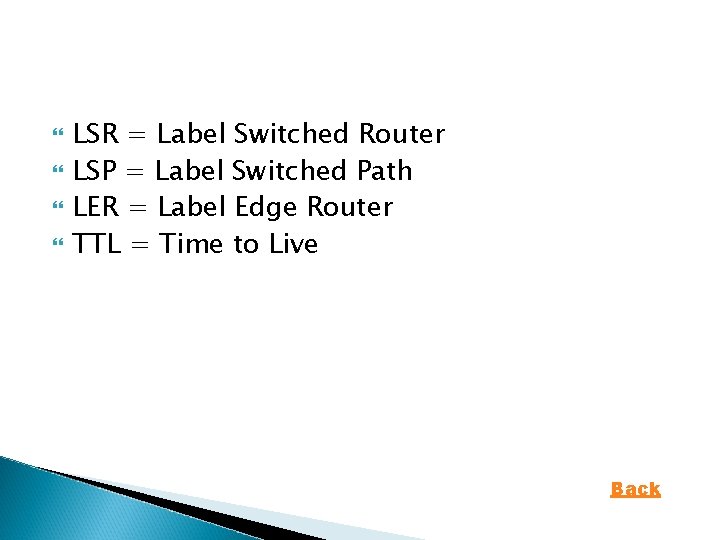
LSR = Label Switched Router LSP = Label Switched Path LER = Label Edge Router TTL = Time to Live Back

5. OPERASI MPLS Pembuatan label dan distribusi Pembuatan label dalam tiap router Pembuatan jalur label yang terhubung Pemasukan label Forwarding paket Back