Virtual LAN Virtual Local Area Network It is






















- Slides: 50

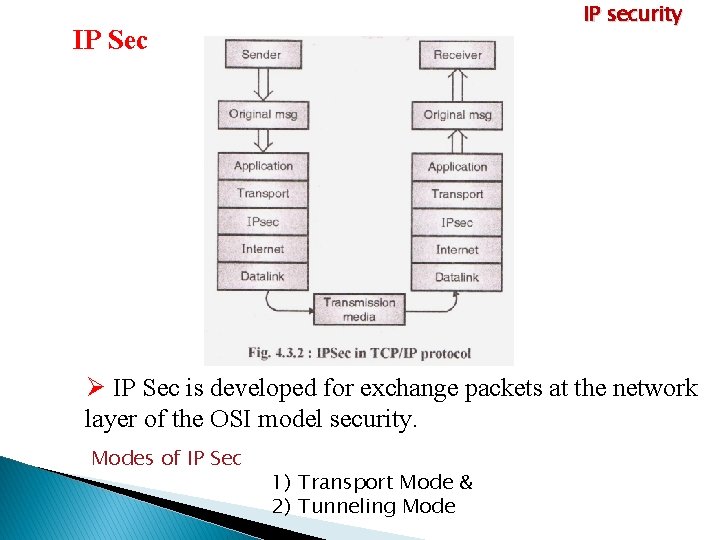
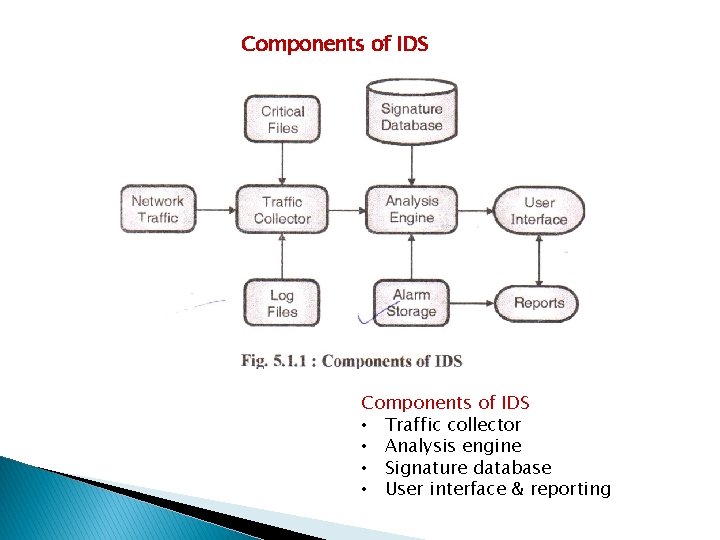
Virtual LAN Virtual Local Area Network • It is defined in IEEE 802. 1 q standard Technology. • It is the method of using a single switch and dividing the multiple broadcast doming or multiple network segment.

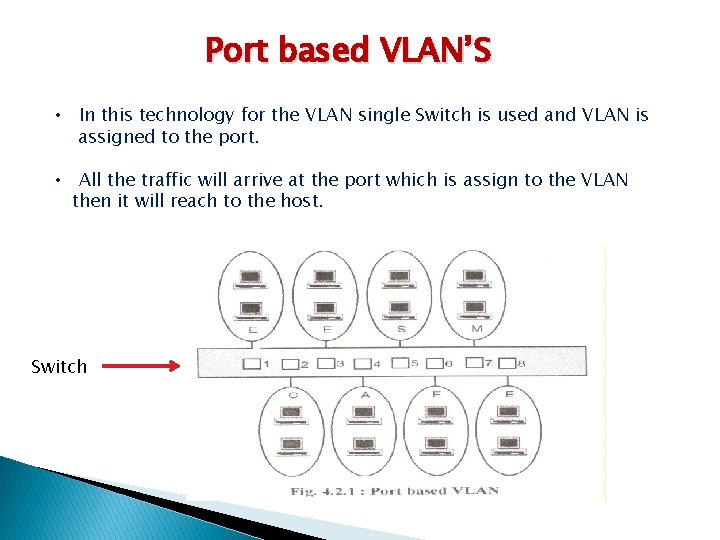
Port based VLAN’S • In this technology for the VLAN single Switch is used and VLAN is assigned to the port. • All the traffic will arrive at the port which is assign to the VLAN then it will reach to the host. Switch

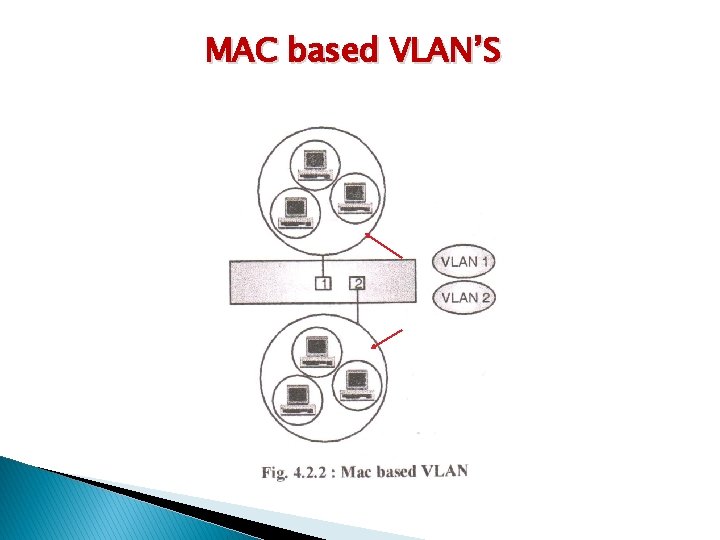
MAC based VLAN’S

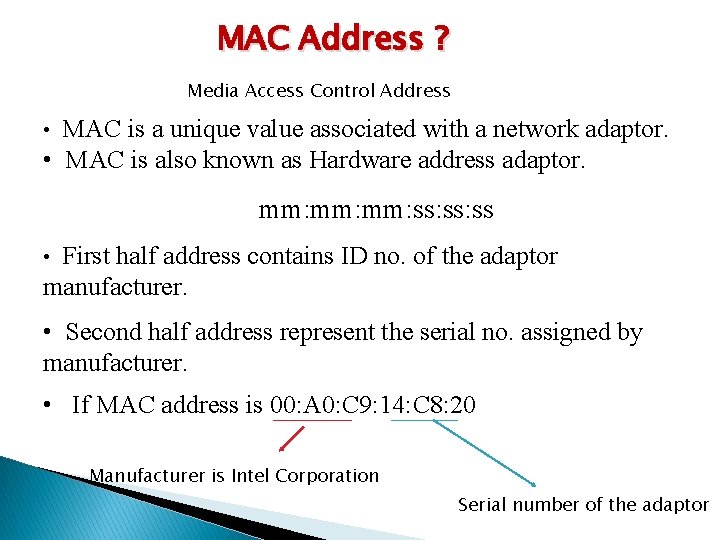
MAC Address ? Media Access Control Address • MAC is a unique value associated with a network adaptor. • MAC is also known as Hardware address adaptor. mm: mm: ss: ss • First half address contains ID no. of the adaptor manufacturer. • Second half address represent the serial no. assigned by manufacturer. • If MAC address is 00: A 0: C 9: 14: C 8: 20 Manufacturer is Intel Corporation Serial number of the adaptor

IP security • IT is the set of protocols developed by the IETF (Internet Engineering Task Force). • IP security supports secure exchange of packets at the IP layer. • It provides secure communication through public network. Security to IP Addressess + data

IP security What is the need of IP Security? Most serious types of Attacks, • Spoofing- (IP Spoofing by intruders with fake IP) • Readout the message i. e. confidentiality will be lost, • Packet sniffing, • Hacking, • Intruders, • Logon information, reading database contents, • Unauthorized traffic monitoring, All these types attacks can be done within the transmission. IAB (Internet Architecture Board) developed authentication & encryption as an necessary security in the next generation IP i. e. IPv 4 and IPv 6

IP security What IP Security Provides? • Provides secure comm. across Private LAN, WAN. • Provides secure comm. across Internet. • Provided authentication, confidentiality and a secure key exchange mechanism. • It support to encrypt and authenticate all the traffic at the IP level. • Provides security to all distributed applications like Remote Login. Client server. E-Mail. File transfer. Web access.

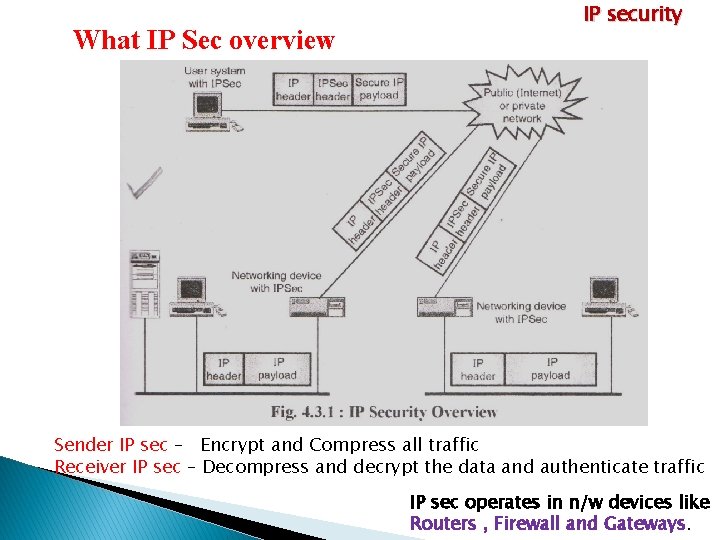
What IP Sec overview IP security Sender IP sec – Encrypt and Compress all traffic Receiver IP sec – Decompress and decrypt the data and authenticate traffic IP sec operates in n/w devices like Routers , Firewall and Gateways.

IP security Advantages of IP Sec: Ø IP Sec is implement in firewall, router and gateway. Ø Provides strong security for all traffic crossing the boundary. Ø All the traffic will pass through IP sec or Firewall. Ø There is no need to train the users on security mechanism. Ø IP sec can be provide security for individual users.

IP security IP Security Architecture: Security Policy Database: (SPD) SPD is used to determine how to handle message / packets. SPD has 3 legal actions 1) Discarding message 2) Applying security services to all the messages. 3) Forward message with no change. Security Association: (SA) • Used to enhance the security to channel along with packets. • It uses AH (Authentication Header) or ESP (Encapsulating Security Payload)

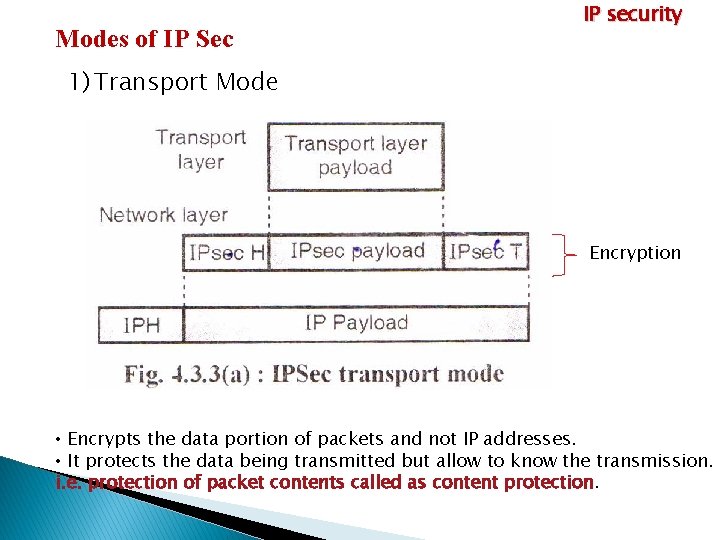
IP security IP Sec Ø IP Sec is developed for exchange packets at the network layer of the OSI model security. Modes of IP Sec 1) Transport Mode & 2) Tunneling Mode

Modes of IP Sec IP security 1) Transport Mode Encryption • Encrypts the data portion of packets and not IP addresses. • It protects the data being transmitted but allow to know the transmission. i. e. protection of packet contents called as content protection.

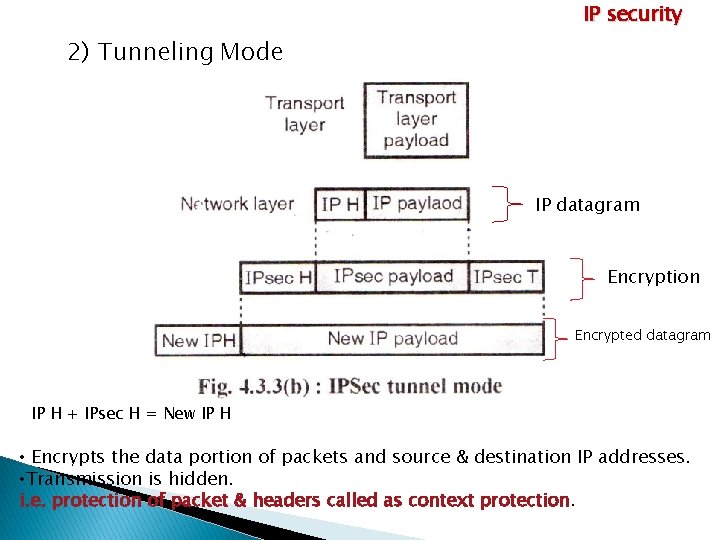
IP security 2) Tunneling Mode IP datagram Encryption Encrypted datagram IP H + IPsec H = New IP H • Encrypts the data portion of packets and source & destination IP addresses. • Transmission is hidden. i. e. protection of packet & headers called as context protection.

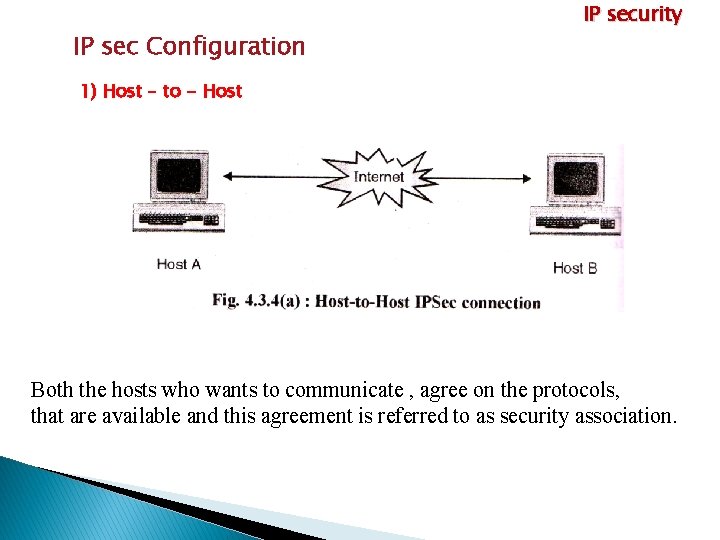
IP sec Configuration IP security 1) Host – to - Host Both the hosts who wants to communicate , agree on the protocols, that are available and this agreement is referred to as security association.

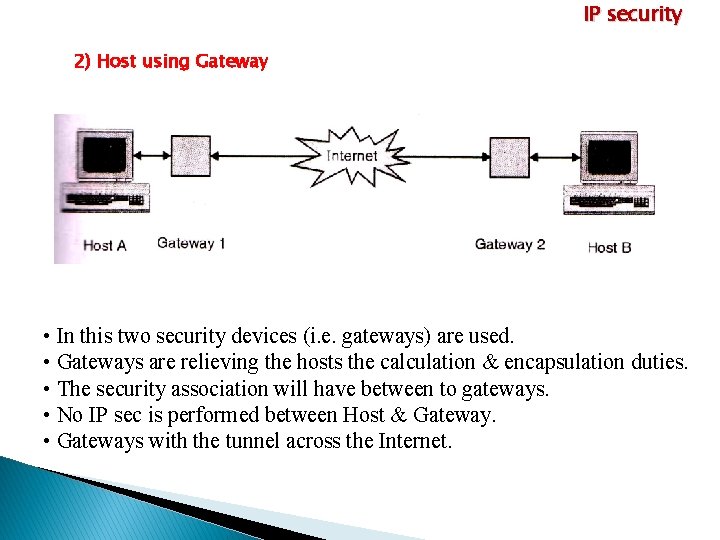
IP security 2) Host using Gateway • In this two security devices (i. e. gateways) are used. • Gateways are relieving the hosts the calculation & encapsulation duties. • The security association will have between to gateways. • No IP sec is performed between Host & Gateway. • Gateways with the tunnel across the Internet.

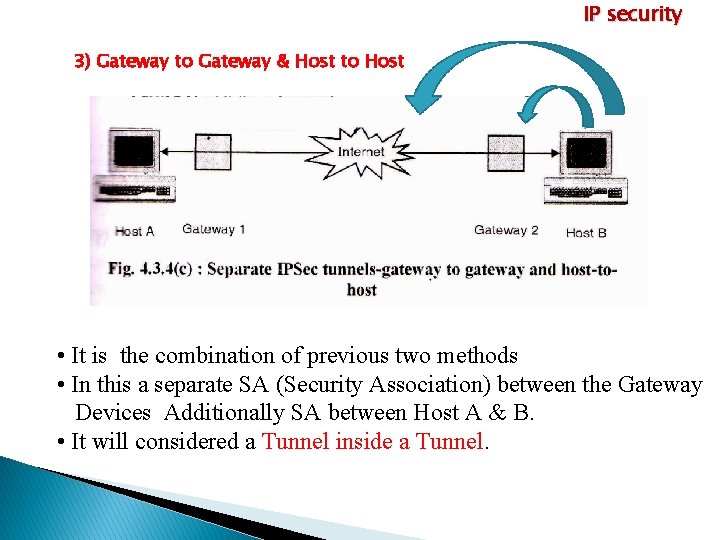
IP security 3) Gateway to Gateway & Host to Host • It is the combination of previous two methods • In this a separate SA (Security Association) between the Gateway Devices Additionally SA between Host A & B. • It will considered a Tunnel inside a Tunnel.

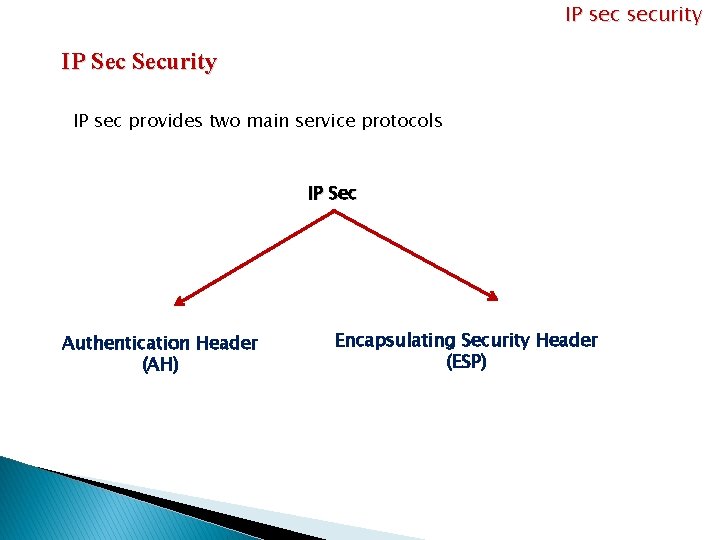
IP security IP Security IP sec provides two main service protocols IP Sec Authentication Header (AH) Encapsulating Security Header (ESP)

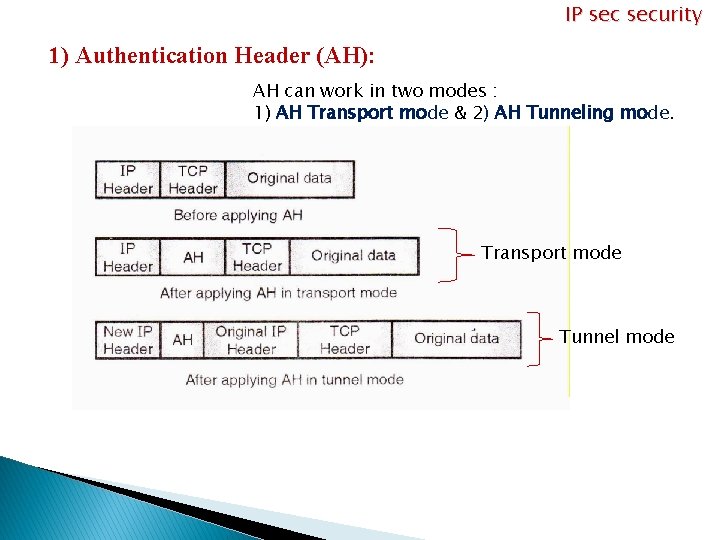
IP security 1) Authentication Header (AH): AH can work in two modes : 1) AH Transport mode & 2) AH Tunneling mode. Transport mode Tunnel mode

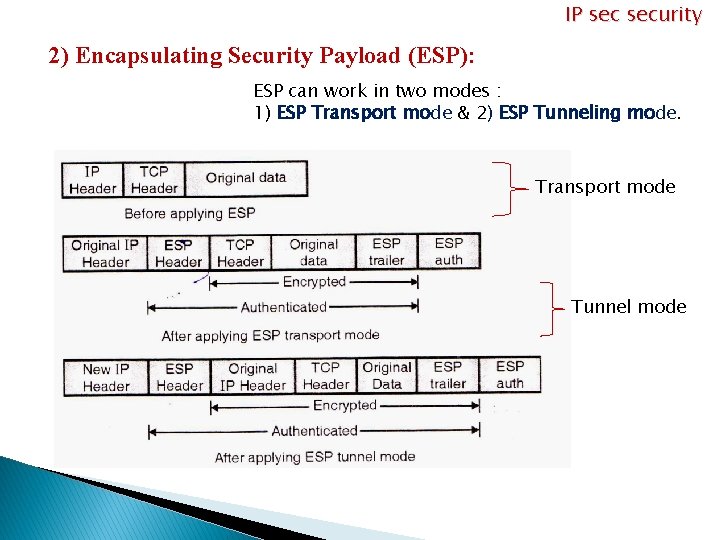
IP security 2) Encapsulating Security Payload (ESP): ESP can work in two modes : 1) ESP Transport mode & 2) ESP Tunneling mode. Transport mode Tunnel mode

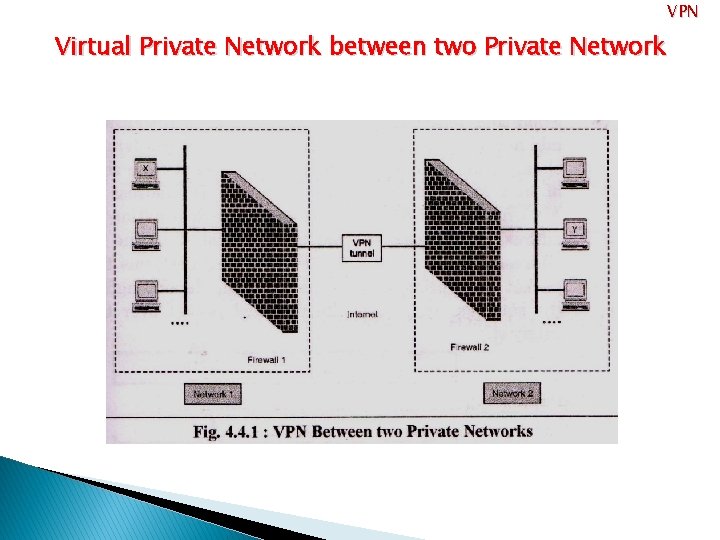
Virtual Private Network • A Virtual private Network is network that uses public Internet to provide secure access to their organizations network. • VPN is a mechanism it provides encryption, authentication and integrity Protection, so that the public network can use as Private Network. • VPN provides virtual connections, and do not have any physical presence.

VPN Virtual Private Network between two Private Network

Steps : - VPN

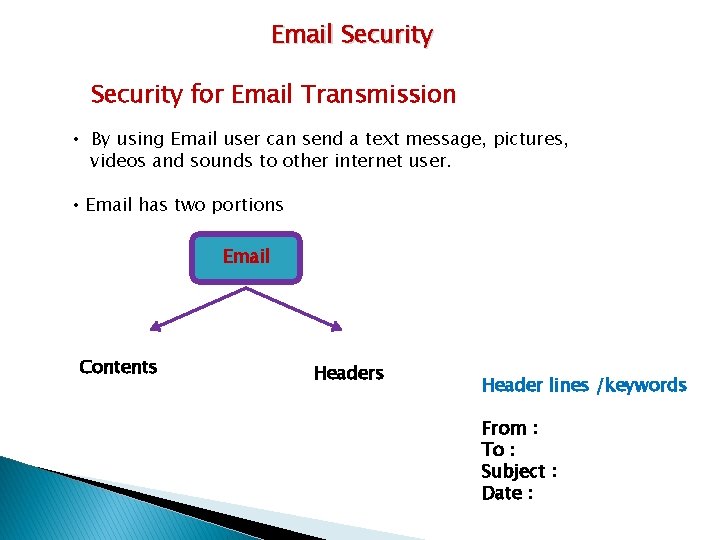
Email Security for Email Transmission • By using Email user can send a text message, pictures, videos and sounds to other internet user. • Email has two portions Email Contents Header lines /keywords From : To : Subject : Date :

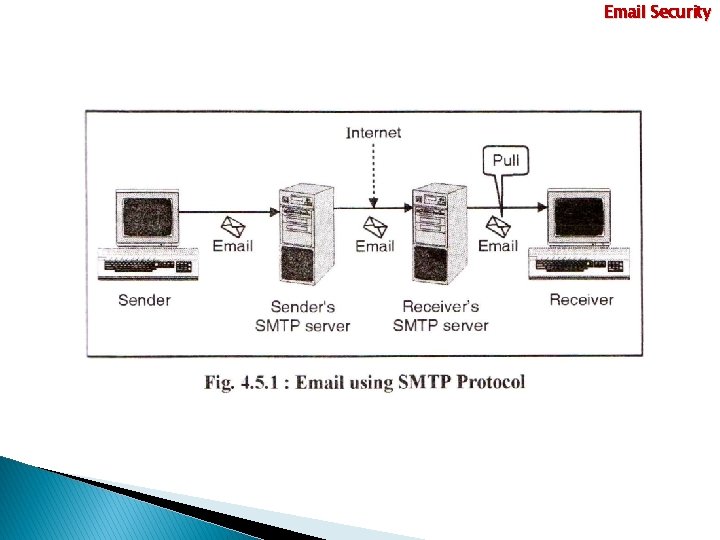
Email Security Email Protocol SMTP ( Simple Mail Transfer Protocol ) • SMTP protocol is used for email transport communication. • SMPT is “Request / Response “ based protocol. • Client will send the email message to the Email Server. • Sender’s SMTP server send email to the receivers SMTP server. • At the Receiver computer drags the email message from SMTP server using other email protocols like POP (Post Office Protocol) or IMAP (Internet Mail Access Protocol). • POP is used to only retrieve the message. • IMAP is combination of both i. e. SMTP & POP. It is plain text protocol. • IMAP is allow to user to send outgoing message. • IMAP is allows user to create directories.

Email Security

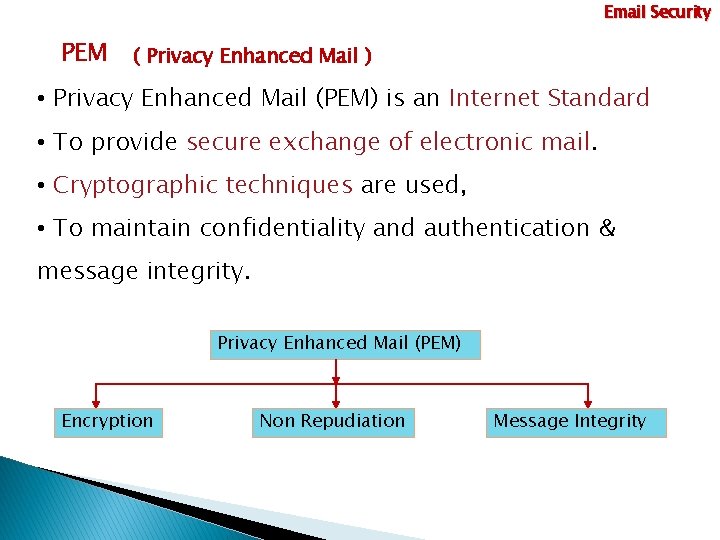
Email Security PEM ( Privacy Enhanced Mail ) • Privacy Enhanced Mail (PEM) is an Internet Standard • To provide secure exchange of electronic mail. • Cryptographic techniques are used, • To maintain confidentiality and authentication & message integrity. Privacy Enhanced Mail (PEM) Encryption Non Repudiation Message Integrity

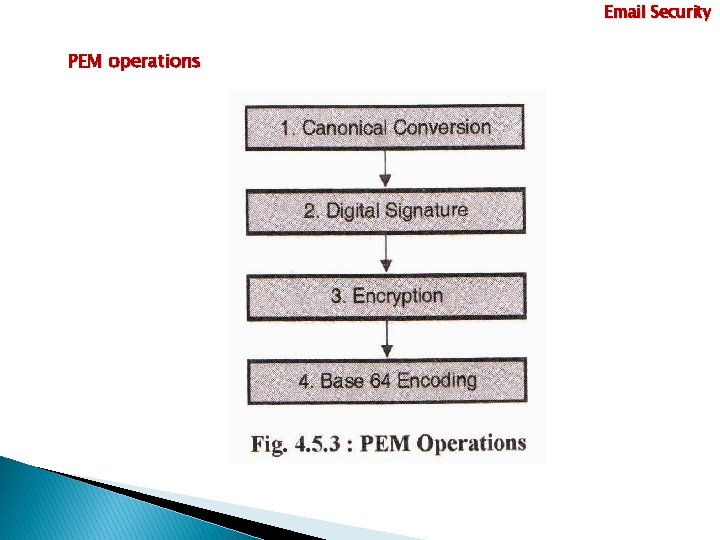
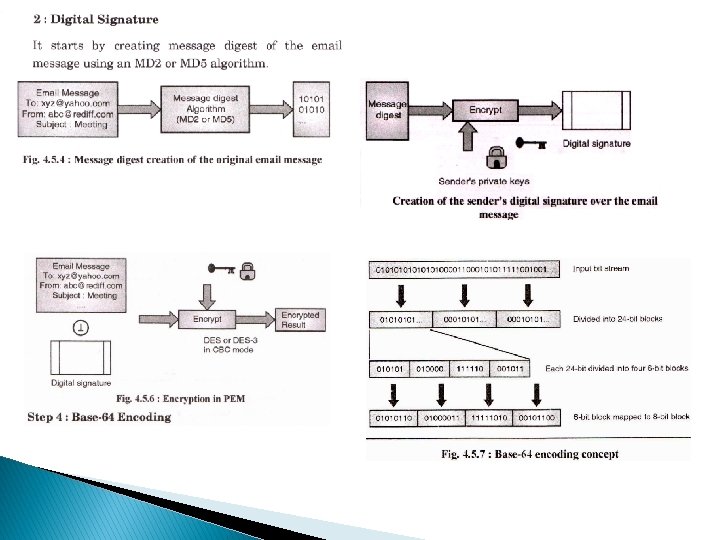
Email Security PEM operations


PGP ( Pretty Good Privacy) Email Security • It is a popular program used to encrypt & decrypt email over the internet. • Digital signature is also encrypted. • Low cost commercial version, used by many corporation. • Developed by Philip R. Zimmermann in 1991. • PGP used for Authentication and Confidentiality.

How it works? 1) Authentication Sender SHA-1 creates 160 bit hash code of message. Hash code encrypted by senders private key. Receiver – Decrypt the received hash code. Creates hash code by using received message. Compare both hash codes. 2)Confidentiality Sender – Generates a message and a random 128 bit number to be used as a session key for this message only. Message is encrypted with this session key. Session key is encrypted with receiver’s public key. Receiver by using its private key will decrypt it, and get the session key. By using session key it will decrypt the message.

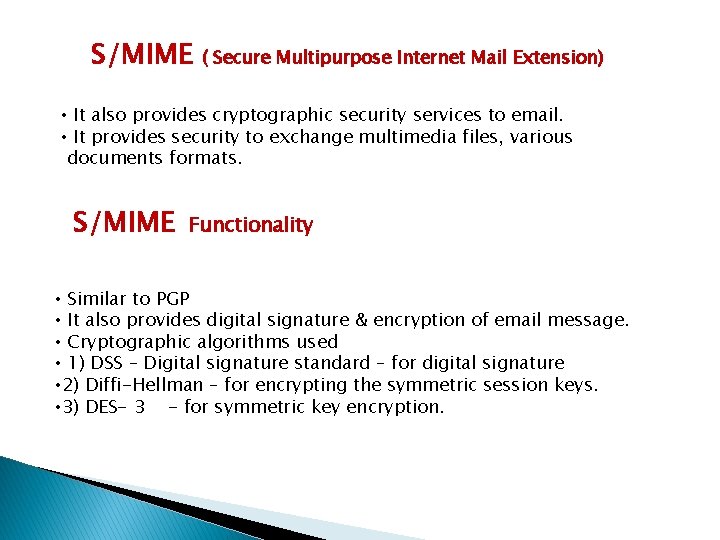
S/MIME ( Secure Multipurpose Internet Mail Extension) • It also provides cryptographic security services to email. • It provides security to exchange multimedia files, various documents formats. S/MIME Functionality • Similar to PGP • It also provides digital signature & encryption of email message. • Cryptographic algorithms used • 1) DSS – Digital signature standard – for digital signature • 2) Diffi-Hellman – for encrypting the symmetric session keys. • 3) DES- 3 - for symmetric key encryption.

SPAM • Type of electronic junk mail or unsolicited email. • It waste greater amount of bandwidth • waste user time for read and delete. • Forged addresses • flooding of email • email bomb • most spam for commercial advertisement. • • Types • Cancellable Usenet spam – single message which sent to 20 or more no. news of groups. • Can not replay to that spam email, because fake email ID. • Email Spam- It target individual user with direct mail message. • refers advt. , money related, to receive bank information and attacks • Blocking List – contact to vendor of spam fighting companies.

How its blocking – i. e. criteria 1) 2) 3) 4) 5) 6) Repetitive sources of addresses Source IP is having no MX record Recurring subjects Recurring source IP addresses More than one user per message Invalid message structure Snail Mail • It is a term, i. e. sent with the traditional way through Postal services rather than by email • Snail mail is very slow. (generally takes 2 -3 days.

Questions 1) What is IP Security? Describe authentication Header mode and ESP mode of IP security. 2) Describe Kerberos with neat diagram. 3) Describe Virtual Private Network. 4) Describe Firewall. List the types of firewall. 5) What is security topology? Describe security zones in detail. 6) How PGP is used for email security. 7) Describe PEM used for email security. 8) Describe DMZ with diagram.

Chapt. No. 5: SYSTEM SECURITY Types of Intruders: Ø Masquerader Ø Misfeasor Ø clandestine / Secret user Intrusion Detection Systems (IDS) Types: Ø Host Based IDS Ø Newtwork Based IDS Password Management Ø Vulnerabilities of password Ø Password selection strategies Ø Components of good passwords Operating system security: Ø Operating system hardening Ø Windows operating system Ø Unix/Linux based operating system Updates: Ø hot fix Ø patch Ø service pack

Intruders is the most publicized threats to security. Types of Intruders: Ø Masquerader Ø Misfeasor Ø clandestine / Secret user Masquerader: - An individual (i. e. outsider) (showing as a legal user) - Not authorized user - who enters in the systems & get the access controls of a legal users account. Misfeasor: - authorized user (i. e. insider) - who access data for those who are not authorized (for outsider) - misuse of his privilege. clandestine / Secret user : - an individual (insider / outsider) - who used managerial control to avoid auditing and access controls.

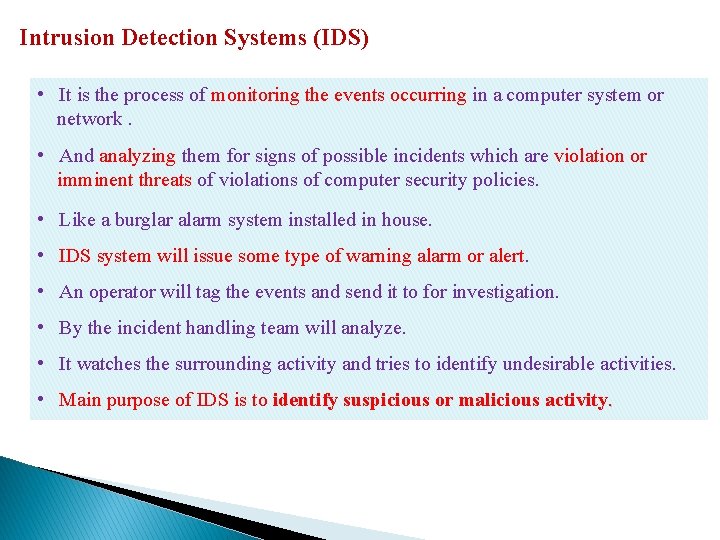
Intrusion Detection Systems (IDS) • It is the process of monitoring the events occurring in a computer system or network. • And analyzing them for signs of possible incidents which are violation or imminent threats of violations of computer security policies. • Like a burglar alarm system installed in house. • IDS system will issue some type of warning alarm or alert. • An operator will tag the events and send it to for investigation. • By the incident handling team will analyze. • It watches the surrounding activity and tries to identify undesirable activities. • Main purpose of IDS is to identify suspicious or malicious activity.

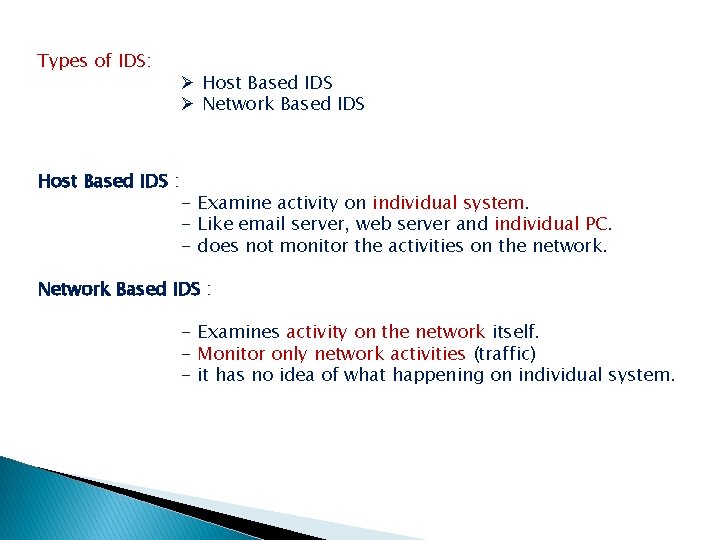
Types of IDS: Host Based IDS : Ø Host Based IDS Ø Network Based IDS - Examine activity on individual system. - Like email server, web server and individual PC. - does not monitor the activities on the network. Network Based IDS : - Examines activity on the network itself. - Monitor only network activities (traffic) - it has no idea of what happening on individual system.

Components of IDS • Traffic collector • Analysis engine • Signature database • User interface & reporting

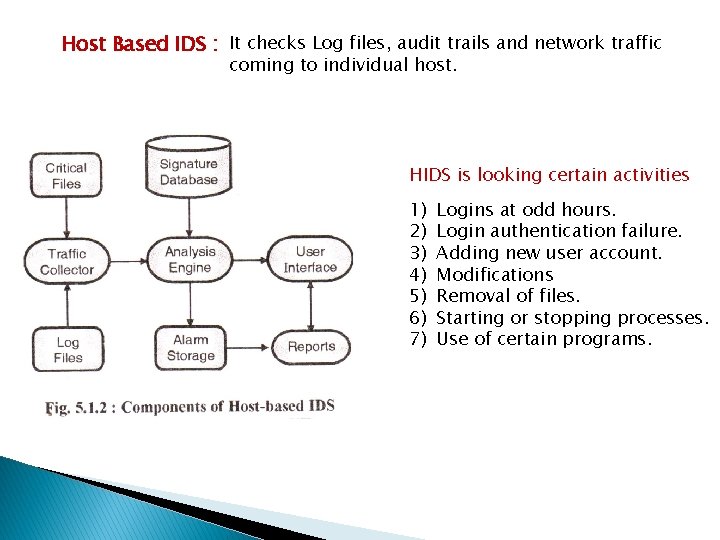
Host Based IDS : It checks Log files, audit trails and network traffic coming to individual host. HIDS is looking certain activities 1) 2) 3) 4) 5) 6) 7) Logins at odd hours. Login authentication failure. Adding new user account. Modifications Removal of files. Starting or stopping processes. Use of certain programs.

Advantages of HIDS 1) It is very specific operating system. 2) It examine data after decryption. 3) Can be used for specific applications also Disadvantages of HIDS: 1) IDS must have a process on every system you want to watch. 2) High cost and maintenance 3) IDS uses local system resources. 4) Can not relate to activity around it.

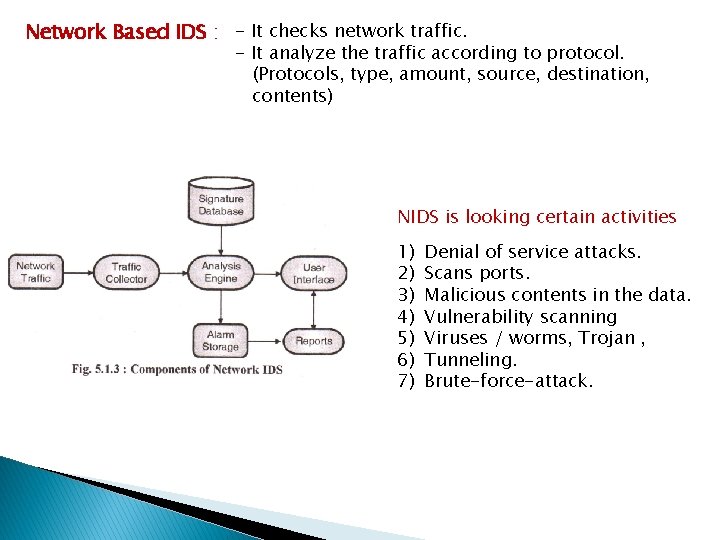
Network Based IDS : - It checks network traffic. - It analyze the traffic according to protocol. (Protocols, type, amount, source, destination, contents) NIDS is looking certain activities 1) 2) 3) 4) 5) 6) 7) Denial of service attacks. Scans ports. Malicious contents in the data. Vulnerability scanning Viruses / worms, Trojan , Tunneling. Brute-force-attack.

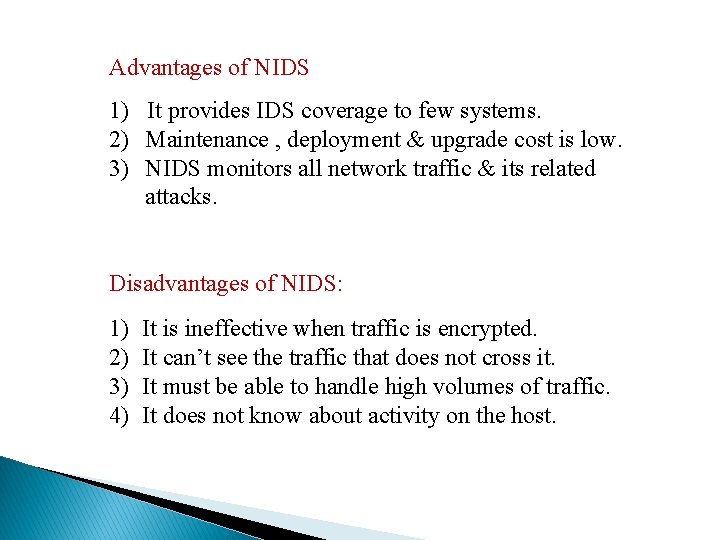
Advantages of NIDS 1) It provides IDS coverage to few systems. 2) Maintenance , deployment & upgrade cost is low. 3) NIDS monitors all network traffic & its related attacks. Disadvantages of NIDS: 1) 2) 3) 4) It is ineffective when traffic is encrypted. It can’t see the traffic that does not cross it. It must be able to handle high volumes of traffic. It does not know about activity on the host.

Password Management: 1) 2) 3) 4) Password security. Vulnerability of password. Password selection strategies. Components of good password. 1) Password security. 1) User ID determines the privileges according to the user. 2) Password required for authentication. 2) Vulnerability of password : 1) don’t use short password. 2) Password should not contain names, birth dates, mobile nos. . 3) Password Selection strategy : 1) More than 8 characters. 2) combinations of characters, no’s, special char. & Symbols. Etc. 3) change it within 3 to 6 months. 4) Components of good password: 1) user should not choose easy password that hacker can easily guess it. 2) Combination of A-Z, a-z, 0 -9, and symbols.

Operating system security: Ø Operating system hardening Ø Operating system (OS) is the basic software which handles i/p, o/p, display, memory management, detailed tasks to support the user. Ø Microsoft’s OS, windows 95, 98, Windows NT, Windows 2000, Mac OS, LINUX, UNIX, Solaris, Novell’s Networks systems are there. Ø The process of securing an operating system is known as operating system hardening. Ø Removing unnecessary applications and Utilities, Ø Disabling unnecessary services, Ø Setting of appropriate permissions on files, Ø Updating the operating system and application code to the latest version Ø Each OS has its own security but some different steps must be taken to secure OS.

Operating system security: Ø Windows operating system Ø Unix/Linux based operating system Windows operating system: (Windows 2000 or XP operating systems) 1) Disable all unnecessary services: Main purpose of Windows is to serve Web server, email server, DNS server, domain/login server etc. So system will be then disable a service which is not necessary. 2) Restrict permissions on files and access to the registry: Restrict permissions like read, write, execute certain files. 3) Remove unnecessary programs: Remove applications which is not required, It will reduces the chances of an attacker to exploiting the weaknesses. 4) Apply the latest patches and fix : Upgrade the system to fix the holes in systems. 5) Remove unnecessary accounts & ensure password guidelines:

Unix/Linux based operating system: Ø UNIX systems are not completely secure by default, it also needs some additional security configuration. Ø UNIX system is very powerful and flexible system so it is very challenging for securing. Ø Disable unnecessary services, restrict permissions on files and directories, apply password guidelines, remove unnecessary softwares, apply patches and remove unnecessary users accounts.

Updates: hot fix: Patch: Ø hot fix Ø patch Ø service pack • Hot fix is small software updates, & design to address a particular problem. • Hot fix discover the problem and fix it quickly. • • Patch is Large software updates. Design to address several or many software problems. Patches developed over a longer period of time. Patches contains additional capabilities and fixes for known bug. Service Pack : • collection of hot fix and patches. • used to update system up to the latest known rather than system to download several updates separately.

Questions 1) Explain any four password policies. 2) Describe the following terms a) hot fix b) patch c) service pack 3) What is operating system hardening? Describe general steps for securing Windows operating system. 4) What is Intrusion Detection System? Describe Host based IDS and Network base IDS.

Security ? ? ? Firewall