VINI Virtual Network Infrastructure Jennifer Rexford Princeton University





- Slides: 39

VINI: Virtual Network Infrastructure Jennifer Rexford Princeton University http: //www. cs. princeton. edu/~jrex Joint with Andy Bavier, Nick Feamster, Lixin Gao, Mark Huang, Larry Peterson 1

The Internet: A Remarkable Story • Tremendous success – From research experiment to global communications infrastructure • The brilliance of under-specifying – Best-effort packet delivery service – Key functionality at programmable end hosts • Enabled massive growth and innovation – Ease of adding hosts and link technologies – Ease of adding services (Web, P 2 P, Vo. IP, …) • But, change is easy only at the edge… 2

Internet is Showing Signs of Age • Security – Weak notions of identity that are easy to spoof – Protocols that rely on good behavior • Mobility – Hierarchical addressing closely tied with routing – Presumption that communicating hosts are connected • Availability – Poor visibility into underlying shared risks – Multiple interconnected protocols and systems • Network management – Many coupled, decentralized control loops 3

Variety of Architectural Solutions • Revisiting definition & placement of function – Naming, addressing, and location – Routing, forwarding, and addressing – Management, control, and data planes – End hosts, routers, and operators • Designing with new constraints in mind – Selfish and adversarial participants – Mobile hosts and disconnected operation – Large number of small, low-power devices – Ease of network management 4

Hurdle #1: Deployment Dilemma • An unfortunate catch-22 – Must deploy an idea to demonstrate feasibility – Can’t get an undemonstrated idea deployed • A corollary: the testbed dilemma – Production network: real users, but can’t change – Research testbed: easy changes, but no users • Bad for the research community – Good ideas sit on the shelf – Promising ideas do not grow up into good ones 5

Hurdle #2: Coordination Constraint • Difficult to deploy end-to-end services –Benefits only when most networks deploy –No single network wants to deploy first • Many deployment failures –Qo. S, IP multicast, secure routing, IPv 6, … –Despite solving real, pressing problems • Increasing commoditization of ISPs 1 sender 2 3 receiver 6

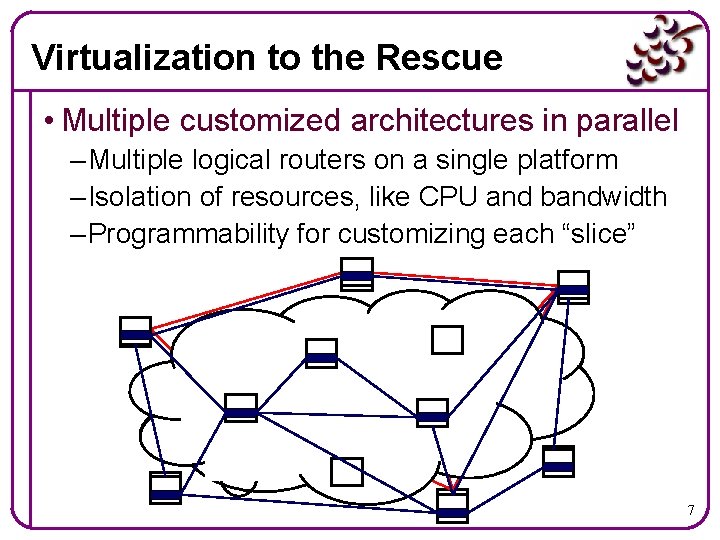
Virtualization to the Rescue • Multiple customized architectures in parallel – Multiple logical routers on a single platform – Isolation of resources, like CPU and bandwidth – Programmability for customizing each “slice” 7

Three Projects: GENI, VINI, CABO • Global Environment for Network Innovations – Large initiative for a shared experimental facility – Jointly between NSF CISE division & community – Distributed systems, wireless, optics, backbone • VIrtual Network Infrastructure – Baby step toward the design of GENI backbone – Systems research on network virtualization • Concurrent Architectures Better than One – Clean-slate architecture based on virtualization – Economic refactoring for end-to-end services See http: //www. geni. net and http: //www. vini-veritas. net 8

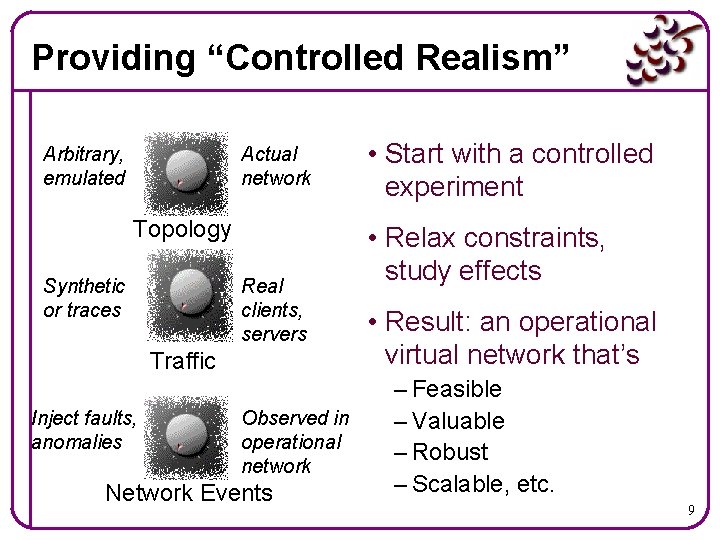
Providing “Controlled Realism” Arbitrary, emulated Actual network Topology Synthetic or traces Real clients, servers Traffic Inject faults, anomalies Observed in operational network Network Events • Start with a controlled experiment • Relax constraints, study effects • Result: an operational virtual network that’s – Feasible – Valuable – Robust – Scalable, etc. 9

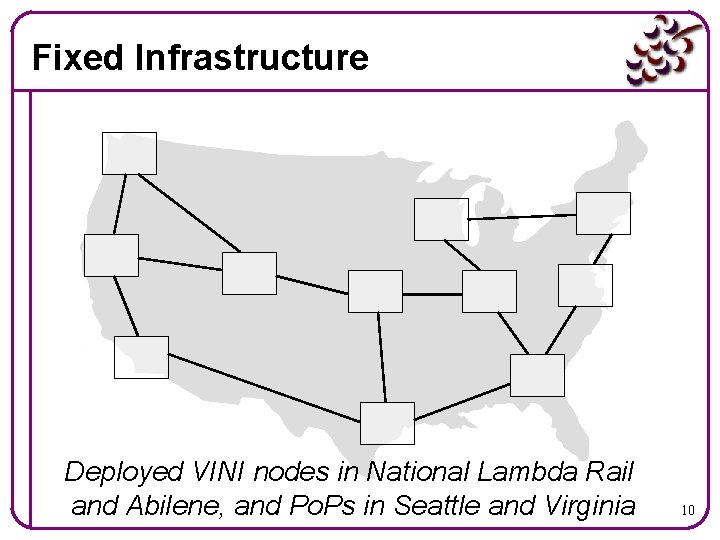
Fixed Infrastructure Deployed VINI nodes in National Lambda Rail and Abilene, and Po. Ps in Seattle and Virginia 10

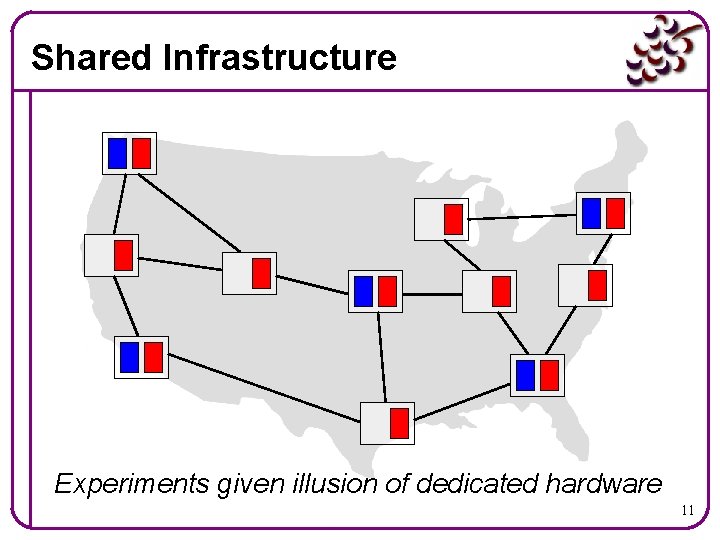
Shared Infrastructure Experiments given illusion of dedicated hardware 11

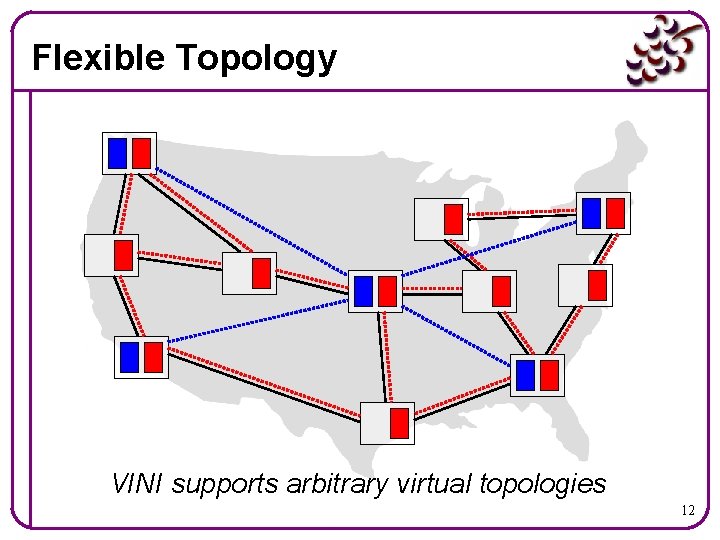
Flexible Topology VINI supports arbitrary virtual topologies 12

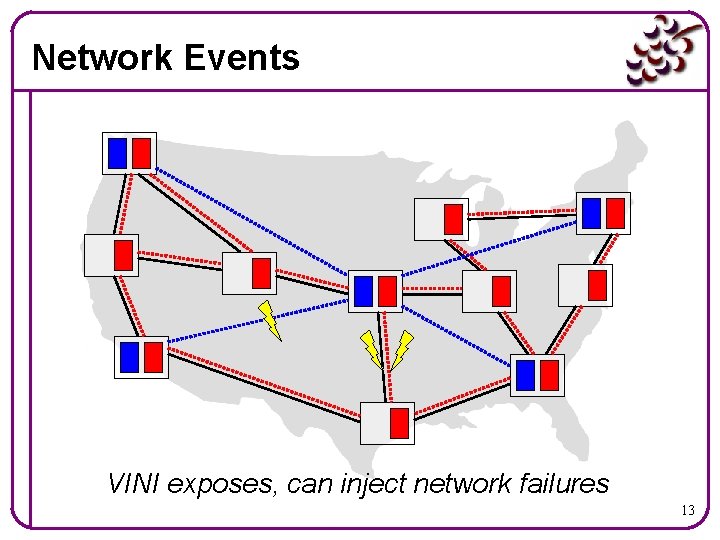
Network Events VINI exposes, can inject network failures 13

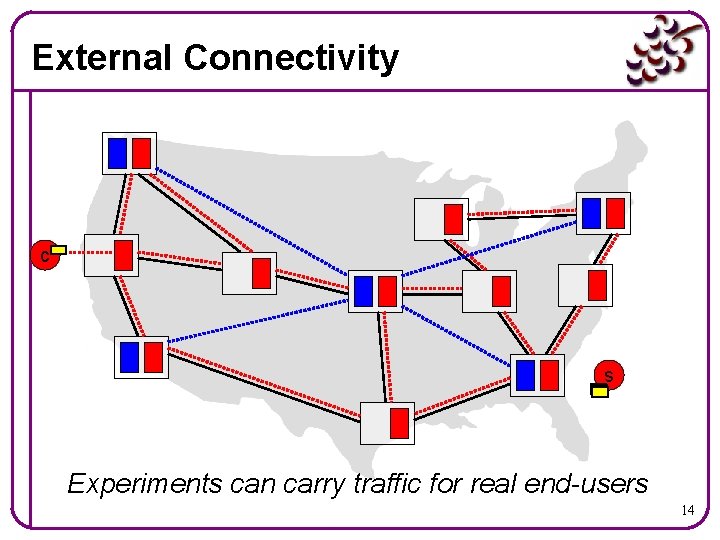
External Connectivity c s Experiments can carry traffic for real end-users 14

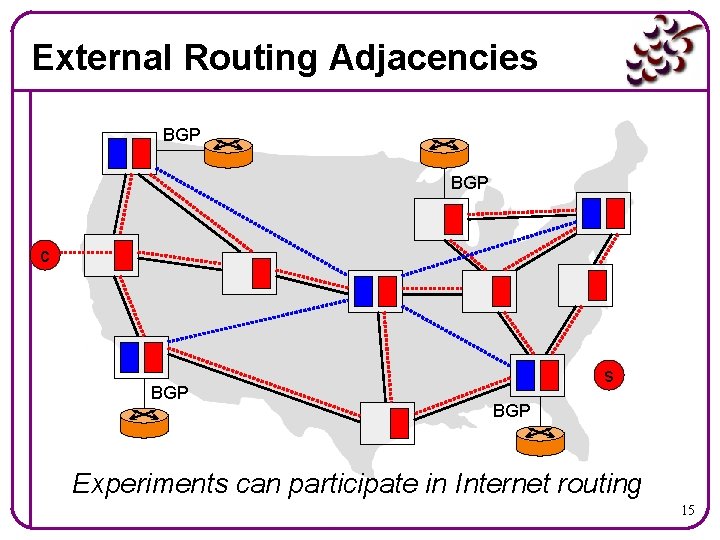
External Routing Adjacencies BGP c BGP s BGP Experiments can participate in Internet routing 15

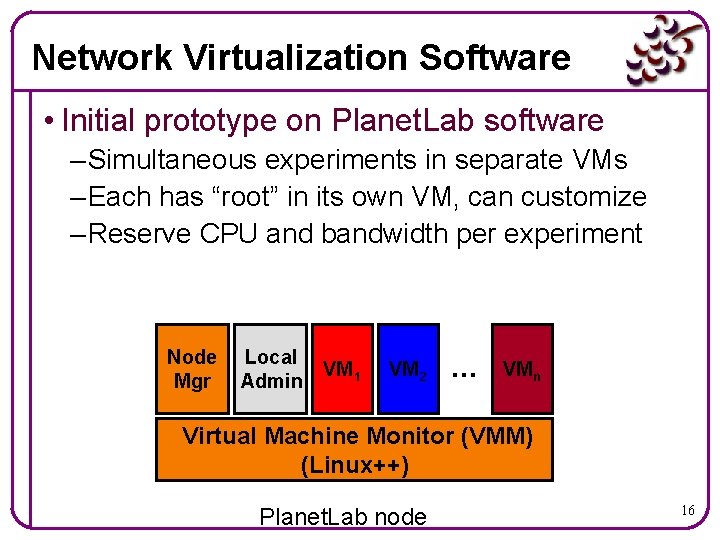
Network Virtualization Software • Initial prototype on Planet. Lab software – Simultaneous experiments in separate VMs – Each has “root” in its own VM, can customize – Reserve CPU and bandwidth per experiment Node Mgr Local Admin VM 1 VM 2 … VM n Virtual Machine Monitor (VMM) (Linux++) Planet. Lab node 16

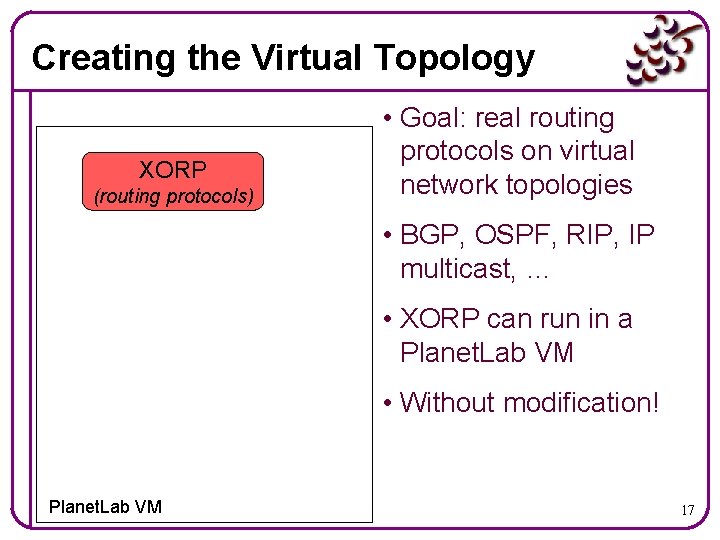
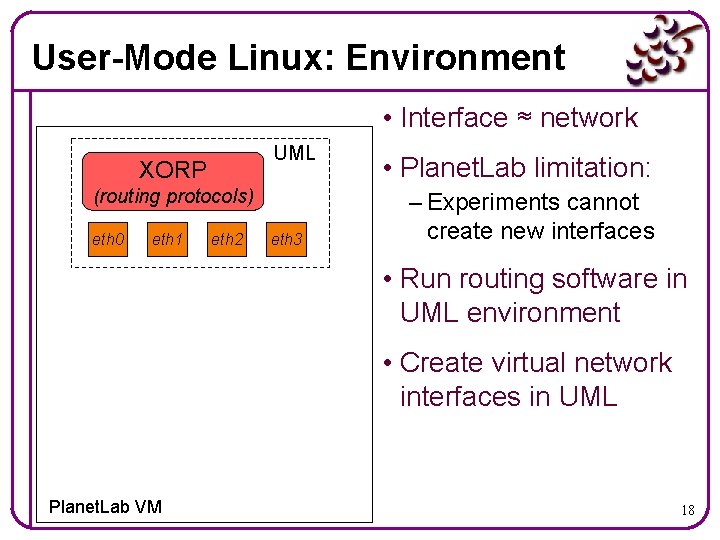
Creating the Virtual Topology XORP (routing protocols) • Goal: real routing protocols on virtual network topologies • BGP, OSPF, RIP, IP multicast, … • XORP can run in a Planet. Lab VM • Without modification! Planet. Lab VM 17

User-Mode Linux: Environment • Interface ≈ network UML XORP (routing protocols) eth 0 eth 1 eth 2 eth 3 • Planet. Lab limitation: – Experiments cannot create new interfaces • Run routing software in UML environment • Create virtual network interfaces in UML Planet. Lab VM 18

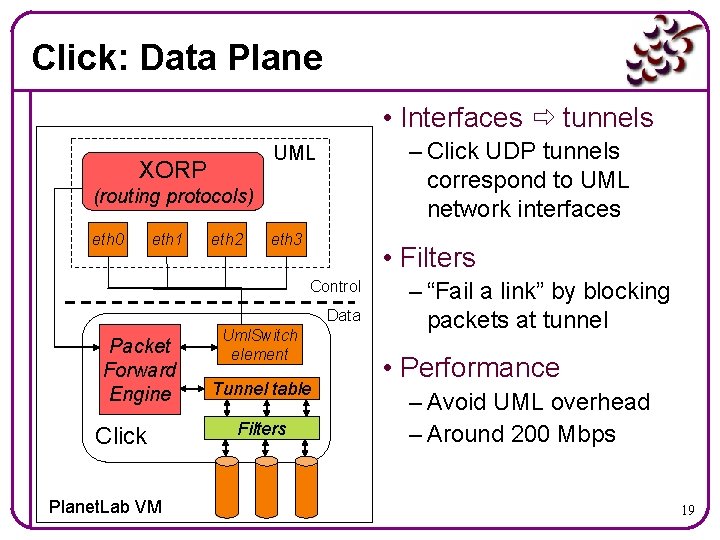
Click: Data Plane • Interfaces tunnels – Click UDP tunnels correspond to UML network interfaces UML XORP (routing protocols) eth 0 eth 1 eth 2 eth 3 • Filters Control Data Packet Forward Engine Click Planet. Lab VM Uml. Switch element Tunnel table Filters – “Fail a link” by blocking packets at tunnel • Performance – Avoid UML overhead – Around 200 Mbps 19

Ongoing Work: Faster Forwarding • Initial design entirely in user space – In order to avoid modifying the kernel – Clearly, this is a big performance limitation • Virtualized network stack in Linux – Network views that are bound to processes – Separate kernel forwarding tables per view • Hardware support through FPGAs and NPs – Nick Mc. Keown’s Net. FPGA project – Jon Turner’s Meta. Router project 20

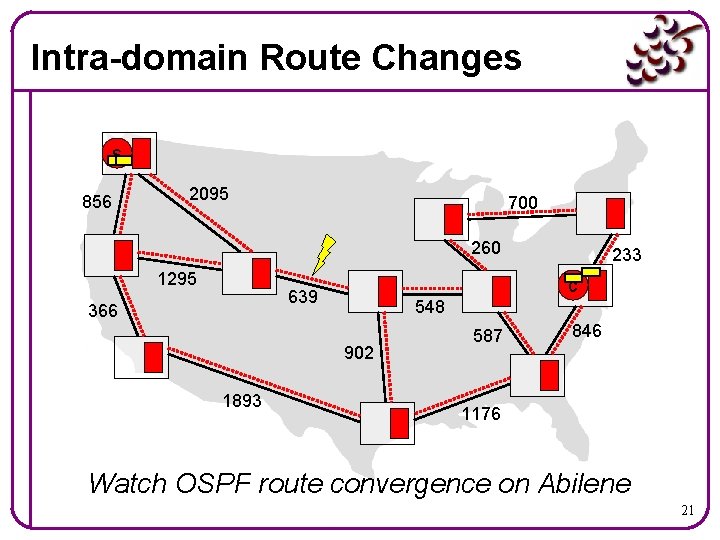
Intra-domain Route Changes s 856 2095 700 260 1295 c 639 366 548 902 1893 233 587 846 1176 Watch OSPF route convergence on Abilene 21

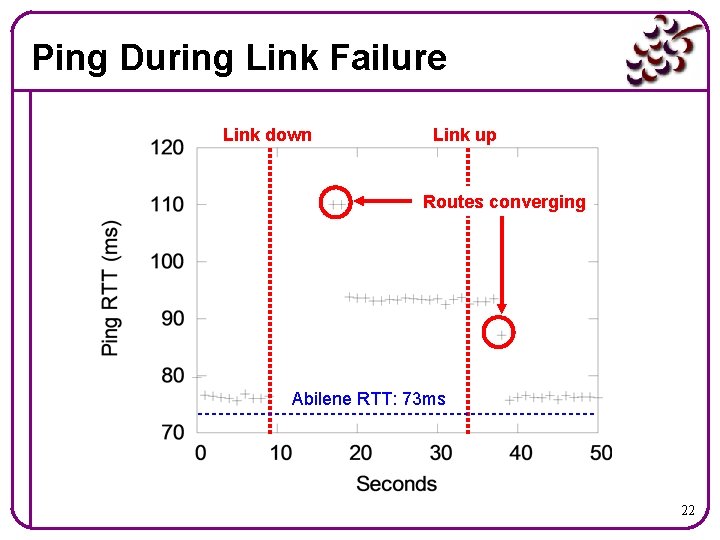
Ping During Link Failure Link down Link up Routes converging Abilene RTT: 73 ms 22

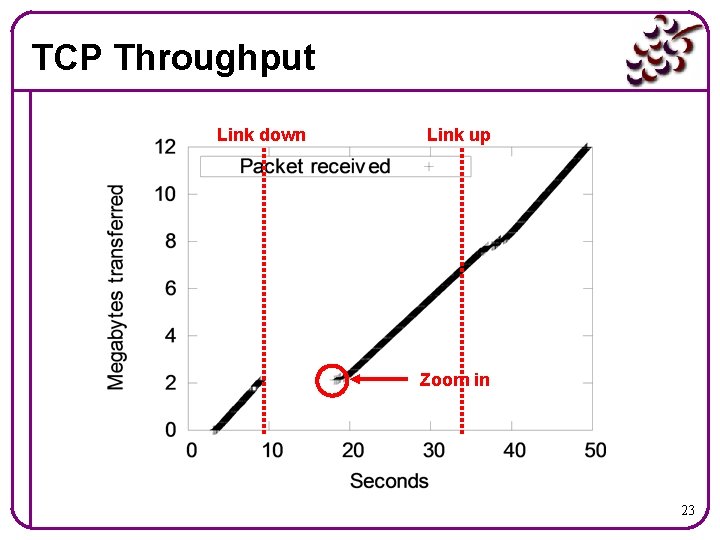
TCP Throughput Link down Link up Zoom in 23

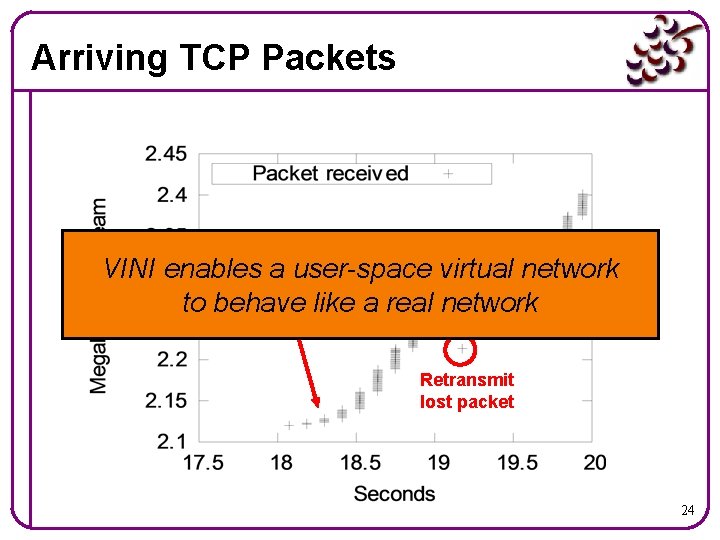
Arriving TCP Packets VINI enables. Slow a user-space virtual network start to behave like a real network Retransmit lost packet 24

Other Example VINI Experiments • Scaling Ethernet to a large enterprise • Routing-protocol support for mobile hosts • Network-layer support for overlay services • Piggybacking diagnostic data on packets • <Insert your prototype system here> • Where should this experimentation lead us? – Will we ever find the one true answer? ? ? 25

The Case for Pluralism • Suppose we can break down the barriers… – Enable realistic evaluation of new ideas – Overcome the coordination constraint • Maybe there isn’t just one right answer – Maybe the problem is over-constrained – Too many goals, some of them conflicting • Maybe the goals change over time – And we’ll always be reinventing ourselves – The only constant is change • So, perhaps we should design for change 26

It’s Hard to be a Routing Protocol… • Many, many design goals – Global reachability – Fast convergence – Efficient use of resources – Low protocol overhead – Secure control plane – Flexible routing policies – <your wish list here> • Perhaps we cannot satisfy all of these goals – No matter how hard we try… 27

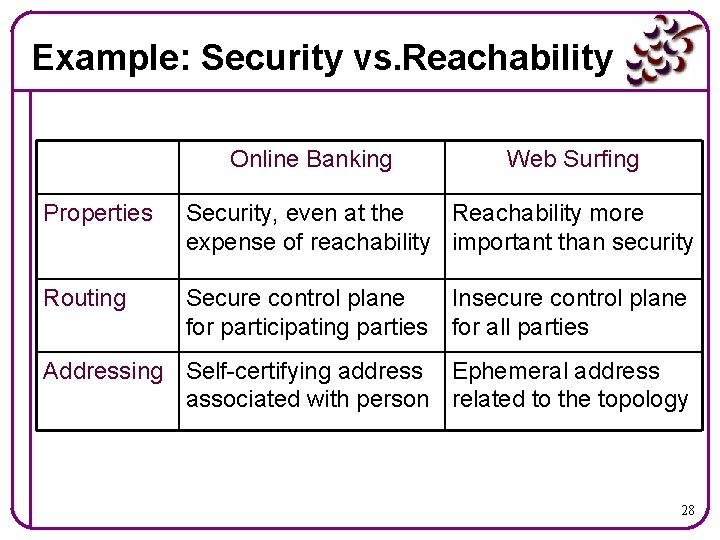
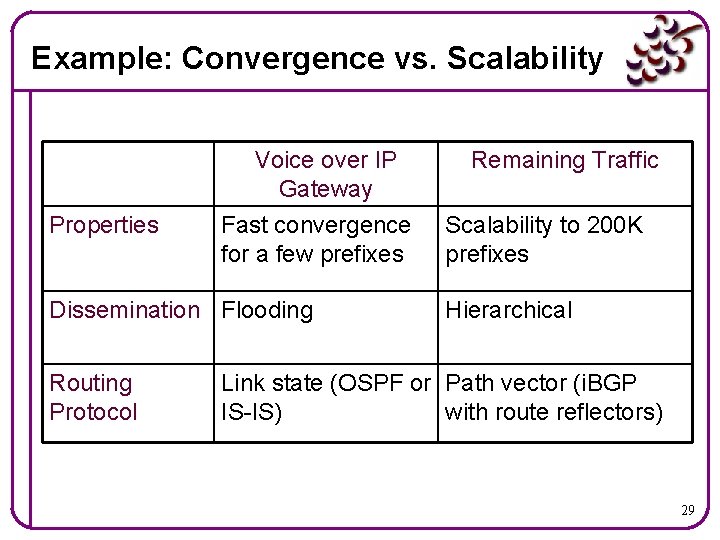
Example: Security vs. Reachability Online Banking Web Surfing Properties Security, even at the Reachability more expense of reachability important than security Routing Secure control plane Insecure control plane for participating parties for all parties Addressing Self-certifying address Ephemeral address associated with person related to the topology 28

Example: Convergence vs. Scalability Voice over IP Gateway Properties Fast convergence for a few prefixes Dissemination Flooding Routing Protocol Remaining Traffic Scalability to 200 K prefixes Hierarchical Link state (OSPF or Path vector (i. BGP IS-IS) with route reflectors) 29

Applications Within an Single ISP • Customized virtual networks – Security for online banking – Fast-convergence for Vo. IP and gaming – Specialized handling of suspicious traffic • Testing and deploying new protocols – Evaluate on a separate virtual network – Rather than in a dedicated test lab – Large scale and early-adopter traffic • Leasing virtual components to others – ISPs have unused node and link capacity – Can allow others to construct services on top 30

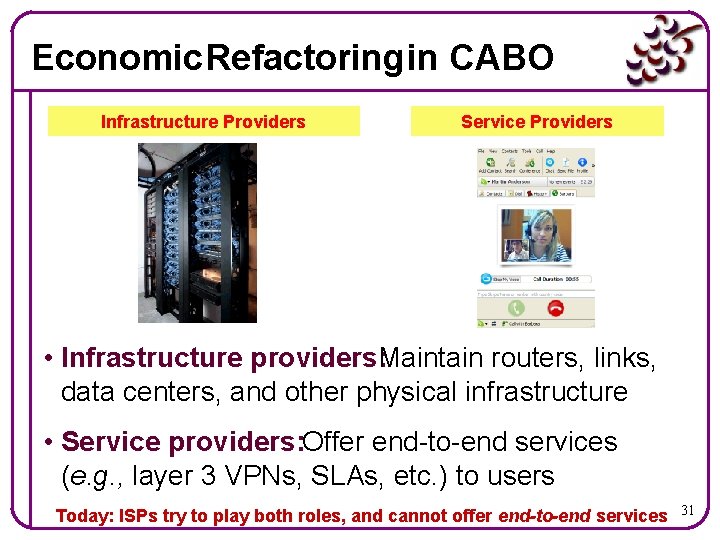
Economic Refactoring in CABO Infrastructure Providers Service Providers • Infrastructure providers: Maintain routers, links, data centers, and other physical infrastructure • Service providers: Offer end-to-end services (e. g. , layer 3 VPNs, SLAs, etc. ) to users Today: ISPs try to play both roles, and cannot offer end-to-end services 31

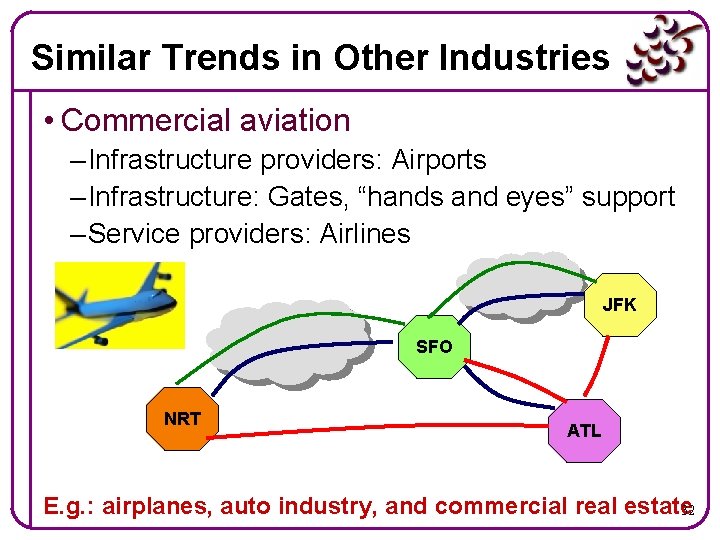
Similar Trends in Other Industries • Commercial aviation – Infrastructure providers: Airports – Infrastructure: Gates, “hands and eyes” support – Service providers: Airlines JFK SFO NRT ATL E. g. : airplanes, auto industry, and commercial real estate 32

Communications Networks, Too! • Two commercial examples in IP networks – Packet Fabric: share routers at exchange points – FON: resells users’ wireless Internet connectivity Broker • FON economic refactoring – Infrastructure providers : Buy upstream connectivity – Service provider: FON as the broker (www. fon. com) 33

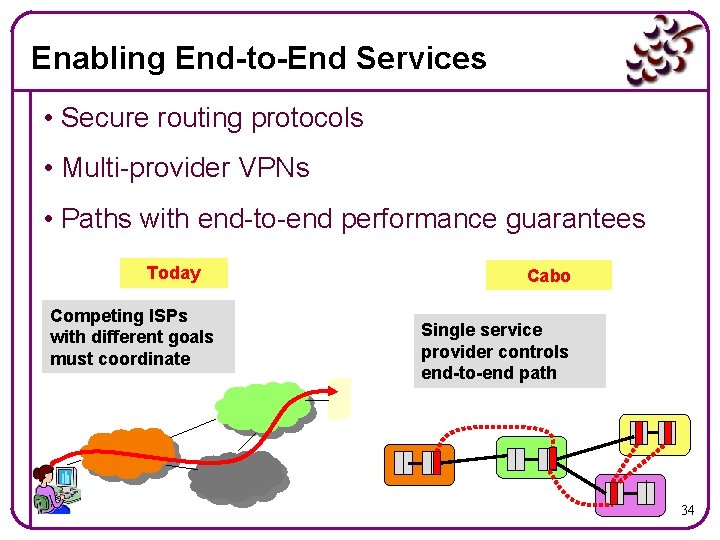
Enabling End-to-End Services • Secure routing protocols • Multi-provider VPNs • Paths with end-to-end performance guarantees Today Competing ISPs with different goals must coordinate Cabo Single service provider controls end-to-end path 34

Conclusion • The Internet needs to change – Security, mobility, availability, management, … • We can overcome barriers to change – Enable realistic experimentation with new ideas – Enable end-to-end deployment of new services • Network virtualization is the key – Run many research experiments in parallel – Offer customized end-to-end services in parallel • VINI as an enabling experimental platform 35

Backup Slides 36

Ongoing Work: Experiment Framework • Experiment specification and monitoring – Specifying topology and configuration • E. g. , Internet-in-A-Slice experiments – Collecting and visualizing packet traces • Distributed tcpdump and network animator • Instantiating virtual networks – Admission control • Book-keeping of node and link resources – Topology embedding • Finding available node and link resources 37

Other Example VINI Experiments • Scaling Ethernet to a large enterprise – Scalability of IP routing, self-config of Ethernet – Flat addressing & hash-based location resolution • Routing-protocol support for mobile hosts – Injecting host address into the routing protocol – Withdrawing and readvertising as host moves • Network-layer support for overlay services – Hosting overlay services directly on the routers – Notifying the overlay services of network events • <Insert your prototype system here> 38

Success Scenarios for VINI & GENI • Expand the research pipeline – Sound foundation for future network architectures – Experimental evaluation, rather than paper designs • Create new services – Demonstrate new services at scale – Attract real users • Aid the evolution of the Internet – Demonstrate ideas that ultimately see real deployment – Provide architectural clarity for evolutionary path • Lead to a future global network – Purist: converge on a single new architecture – Pluralist: virtualization supporting many architectures 39