Vetting SSL Usage in Applications with SSLINT Boyuan
![Vetting SSL Usage in Applications with SSLINT Boyuan He[1], Vaibhav Rastogi[2], Yinzhi Cao[3], Yan Vetting SSL Usage in Applications with SSLINT Boyuan He[1], Vaibhav Rastogi[2], Yinzhi Cao[3], Yan](https://slidetodoc.com/presentation_image_h2/bc742fab85327610eb0939f0b3b58351/image-1.jpg)
Vetting SSL Usage in Applications with SSLINT Boyuan He[1], Vaibhav Rastogi[2], Yinzhi Cao[3], Yan Chen[2][1], Venkatakrishnan[4], Runqing Yang[1], Zhenrui Zhang[1] Lab of Internet and Security Technology (LIST) [1] Zhejiang University, China [2] Northwestern University, USA [3] Columbia University, USA [4] University of Illinois, Chicago, USA
Motivation & Problem Statement TCP SSL/TLS HTTP SMTP POP 3 IMAP Use an X 509 certificate for authentication 2

Motivation & Problem Statement Many application vulnerabilities due to improper usage of SSL/TLS are mentioned in previous papers. l Georgiev et al. [CCS’ 12] (Black-box testing) Is it possible to automatically detect such SSL vulnerabilities in large scale and in a more general way with high efficiency and accuracy? 3
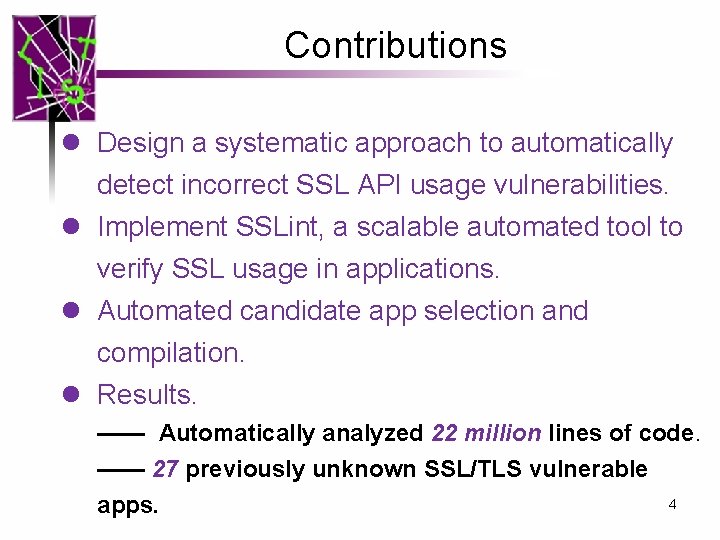
Contributions l Design a systematic approach to automatically detect incorrect SSL API usage vulnerabilities. l Implement SSLint, a scalable automated tool to verify SSL usage in applications. l Automated candidate app selection and compilation. l Results. —— Automatically analyzed 22 million lines of code. —— 27 previously unknown SSL/TLS vulnerable 4 apps.

Agenda 1. Motivation & Problem Statement 2. Background on SSL Vulnerabilities 3. SSLint Design and Implementation 4. Results 5
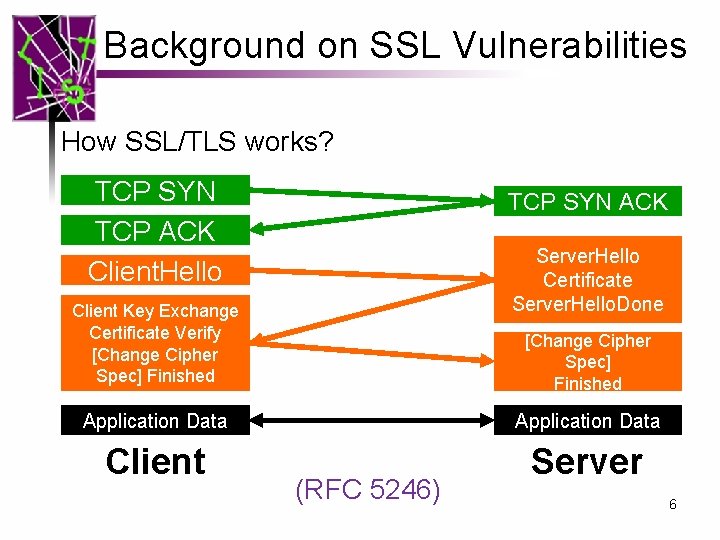
Background on SSL Vulnerabilities How SSL/TLS works? TCP SYN TCP ACK Client. Hello TCP SYN ACK Server. Hello Certificate Server. Hello. Done Client Key Exchange Certificate Verify [Change Cipher Spec] Finished Application Data Client Server (RFC 5246) 6
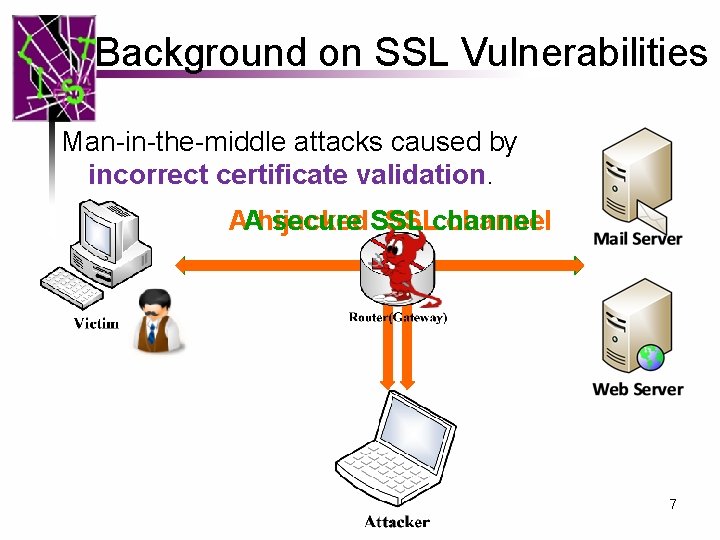
Background on SSL Vulnerabilities Man-in-the-middle attacks caused by incorrect certificate validation. AAhijacked secure SSLchannel 7
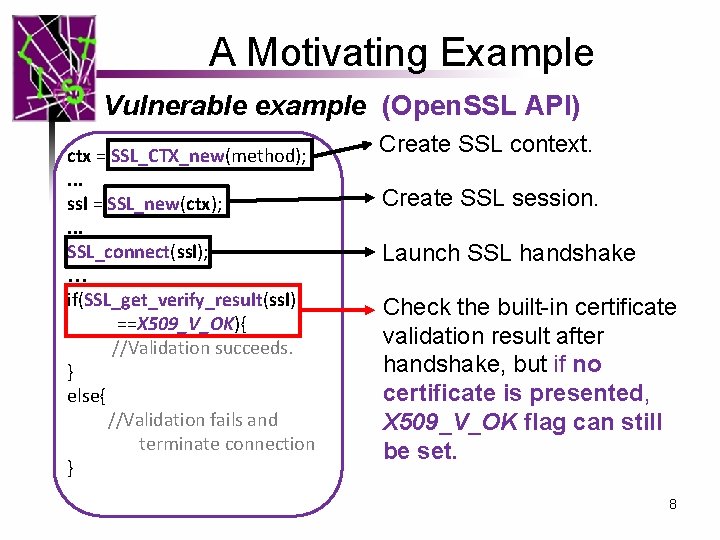
A Motivating Example Vulnerable example (Open. SSL API) ctx = SSL_CTX_new(method); . . . ssl = SSL_new(ctx); . . . SSL_connect(ssl); … if(SSL_get_verify_result(ssl) ==X 509_V_OK){ //Validation succeeds. } else{ //Validation fails and terminate connection } Create SSL context. Create SSL session. Launch SSL handshake Check the built-in certificate validation result after handshake, but if no certificate is presented, X 509_V_OK flag can still be set. 8
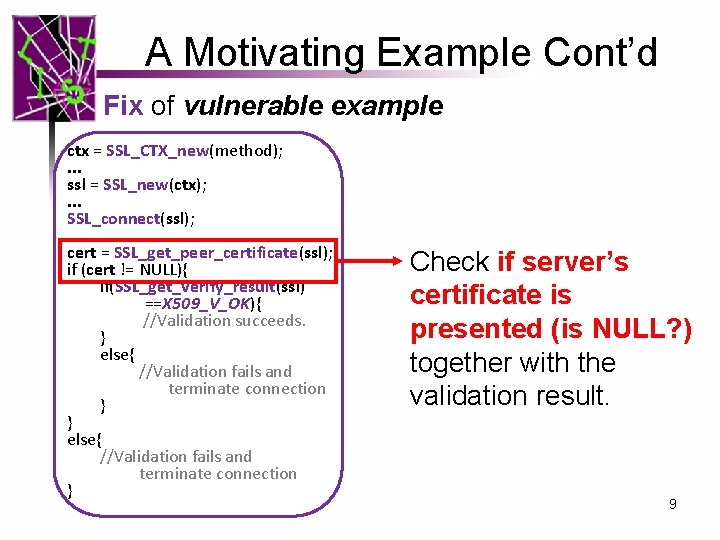
A Motivating Example Cont’d Fix of vulnerable example ctx = SSL_CTX_new(method); . . . ssl = SSL_new(ctx); . . . SSL_connect(ssl); … cert = SSL_get_peer_certificate(ssl); if (cert != NULL){ if(SSL_get_verify_result(ssl) ==X 509_V_OK){ //Validation succeeds. } else{ //Validation fails and terminate connection } Check if server’s certificate is presented (is NULL? ) together with the validation result. 9
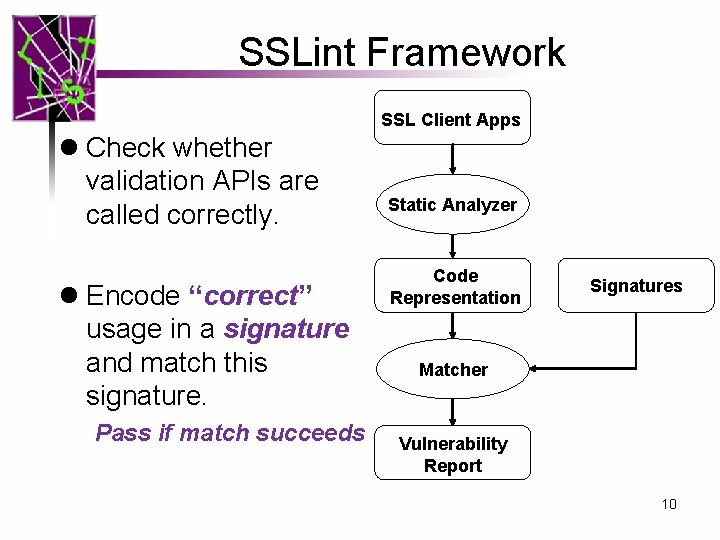
SSLint Framework SSL Client Apps l Check whether validation APIs are called correctly. l Encode “correct” usage in a signature and match this signature. Pass if match succeeds Static Analyzer Code Representation Signatures Matcher Vulnerability Report 10
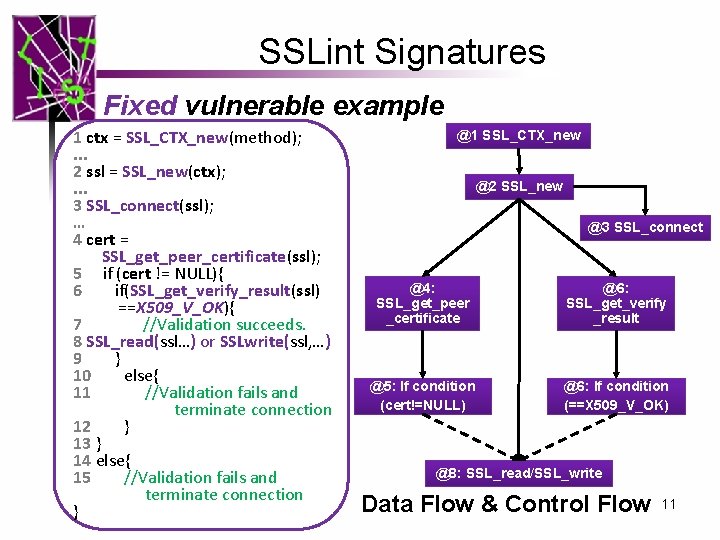
SSLint Signatures Fixed vulnerable example 1 ctx = SSL_CTX_new(method); . . . 2 ssl = SSL_new(ctx); . . . 3 SSL_connect(ssl); … 4 cert = SSL_get_peer_certificate(ssl); 5 if (cert != NULL){ 6 if(SSL_get_verify_result(ssl) ==X 509_V_OK){ 7 //Validation succeeds. 8 SSL_read(ssl…) or SSLwrite(ssl, …) 9 } 10 else{ 11 //Validation fails and terminate connection 12 } 13 } 14 else{ 15 //Validation fails and terminate connection } @1 SSL_CTX_new @2 SSL_new @3 SSL_connect @4: SSL_get_peer _certificate @6: SSL_get_verify _result @5: If condition (cert!=NULL) @6: If condition (==X 509_V_OK) @8: SSL_read/SSL_write Data Flow & Control Flow 11
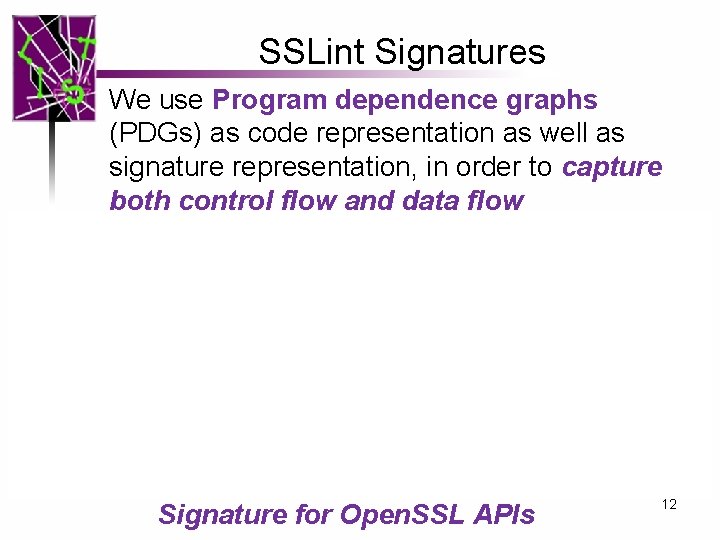
SSLint Signatures We use Program dependence graphs (PDGs) as code representation as well as signature representation, in order to capture both control flow and data flow Signature for Open. SSL APIs 12
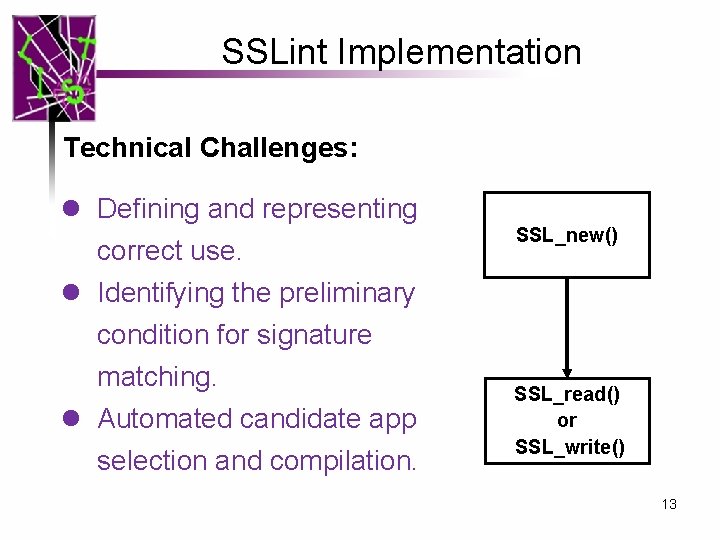
SSLint Implementation Technical Challenges: l Defining and representing correct use. l Identifying the preliminary condition for signature matching. l Automated candidate app selection and compilation. SSL_new() SSL_read() or SSL_write() 13
SSLint Implementation • Certificate Validation Vulnerability Scanner • Code. Surfer provides static analysis • 2. 6 K Lo. C (in C++) • Generated PDGs matched with signatures – Signature Expressions motivated from Cypher, a graph query language – Custom algorithm to perform the matches 14
Results • Signatures implemented for Open. SSL and Gnu. TLS – the most popular two SSL/TLS libraries • Scanned the entire Ubuntu distribution – Scanned 22 million Lo. C in static analysis. – 485 applications using Open. SSL and Gnu. TLS • Detected 27 vulnerabilities – All reported and confirmed – 4 fixed, 14 responses from developers 15

Results l Vulnerable E-mail Software – Xfce 4 -Mailwatch-Plugin, Mailfilter, Exim, Dragon. Fly Mail Agent, spamc l Vulnerable IRC Software – Enhanced Programmable irc. II client (EPIC), Scrollz l Other Vulnerable Software Web(https): Prayer front end, xxxterm Database: Free. TDS Admin tool: nagircbot, nagios-nrpe-plugin, syslog-ng Performance testing tool: siege, httperf, httping 16
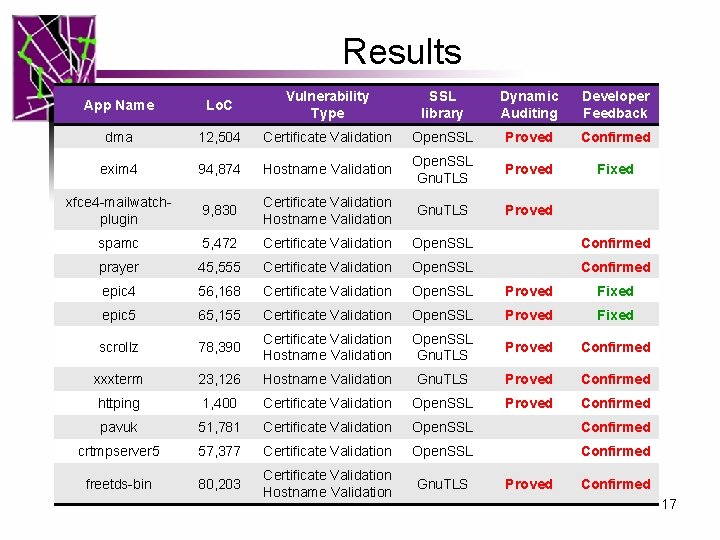
Results App Name Lo. C Vulnerability Type SSL library Dynamic Auditing Developer Feedback dma 12, 504 Certificate Validation Open. SSL Proved Confirmed exim 4 94, 874 Hostname Validation Open. SSL Gnu. TLS Proved Fixed xfce 4 -mailwatchplugin 9, 830 Certificate Validation Hostname Validation Gnu. TLS Proved spamc 5, 472 Certificate Validation Open. SSL Confirmed prayer 45, 555 Certificate Validation Open. SSL Confirmed epic 4 56, 168 Certificate Validation Open. SSL Proved Fixed epic 5 65, 155 Certificate Validation Open. SSL Proved Fixed scrollz 78, 390 Certificate Validation Hostname Validation Open. SSL Gnu. TLS Proved Confirmed xxxterm 23, 126 Hostname Validation Gnu. TLS Proved Confirmed httping 1, 400 Certificate Validation Open. SSL Proved Confirmed pavuk 51, 781 Certificate Validation Open. SSL Confirmed crtmpserver 5 57, 377 Certificate Validation Open. SSL Confirmed freetds-bin 80, 203 Certificate Validation Hostname Validation Gnu. TLS Proved Confirmed 17
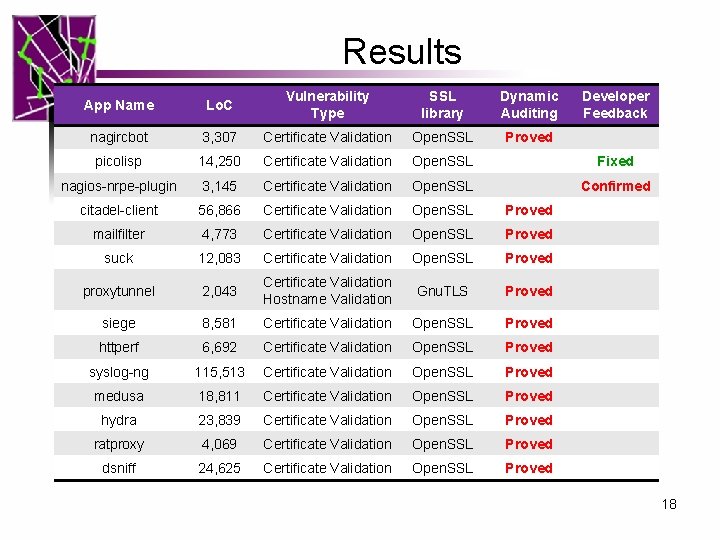
Results App Name Lo. C Vulnerability Type SSL library Dynamic Auditing Developer Feedback nagircbot 3, 307 Certificate Validation Open. SSL Proved picolisp 14, 250 Certificate Validation Open. SSL Fixed nagios-nrpe-plugin 3, 145 Certificate Validation Open. SSL Confirmed citadel-client 56, 866 Certificate Validation Open. SSL Proved mailfilter 4, 773 Certificate Validation Open. SSL Proved suck 12, 083 Certificate Validation Open. SSL Proved proxytunnel 2, 043 Certificate Validation Hostname Validation Gnu. TLS Proved siege 8, 581 Certificate Validation Open. SSL Proved httperf 6, 692 Certificate Validation Open. SSL Proved syslog-ng 115, 513 Certificate Validation Open. SSL Proved medusa 18, 811 Certificate Validation Open. SSL Proved hydra 23, 839 Certificate Validation Open. SSL Proved ratproxy 4, 069 Certificate Validation Open. SSL Proved dsniff 24, 625 Certificate Validation Open. SSL Proved 18
Conclusion & Ongoing work l Conclusion – We design and implement SSLint to verify SSL API usage in large scale. (22 M Lo. C) – We discover 27 previously unknown vulnerable apps due to misuse l Ongoing work – SSLint is our 1 st step to verify API usage by static analysis. (A generic approach? ) – Fix failed applications in analysis by automatically identify SSL-relevant modules in application code. 19

Demo Attack Demo Video against Xfce 4 -mailwatch-plugin 20

Thank you! http: //list. zju. edu. cn/ http: //list. cs. northwestern. edu/ Questions? 21

Back. Up 22
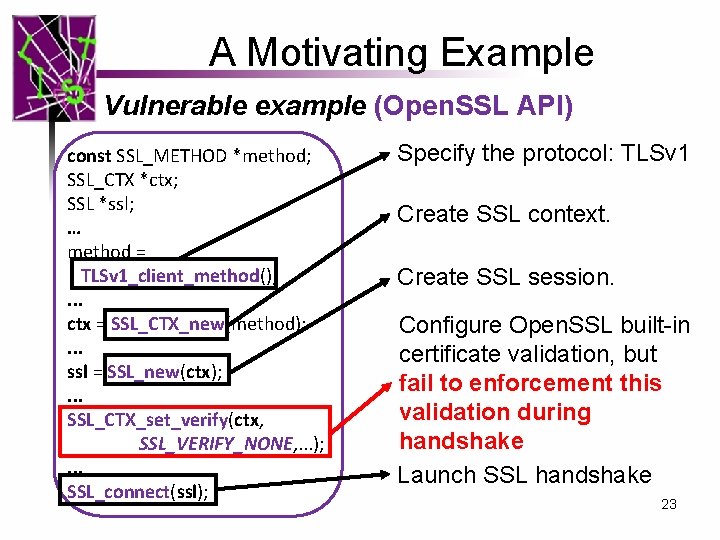
A Motivating Example Vulnerable example (Open. SSL API) const SSL_METHOD *method; SSL_CTX *ctx; SSL *ssl; … method = TLSv 1_client_method(); . . . ctx = SSL_CTX_new(method); . . . ssl = SSL_new(ctx); . . . SSL_CTX_set_verify(ctx, SSL_VERIFY_NONE, . . . ); . . . SSL_connect(ssl); Specify the protocol: TLSv 1 Create SSL context. Create SSL session. Configure Open. SSL built-in certificate validation, but fail to enforcement this validation during handshake Launch SSL handshake 23
A Motivating Example Cont’d Fix of Vulnerable example const SSL_METHOD *method; SSL_CTX *ctx; SSL *ssl; … method = TLSv 1_client_method(); . . . ctx = SSL_CTX_new(method); . . . ssl = SSL_new(ctx); . . . SSL_CTX_set_verify(ctx, SSL_VERIFY_PEER, . . . ); . . . SSL_connect(ssl); Use SSL_VERIFY_PEER flag instead of SSL_VERIFY_NONE to enforce Open. SSL built-in certificate validation during handshake. 24
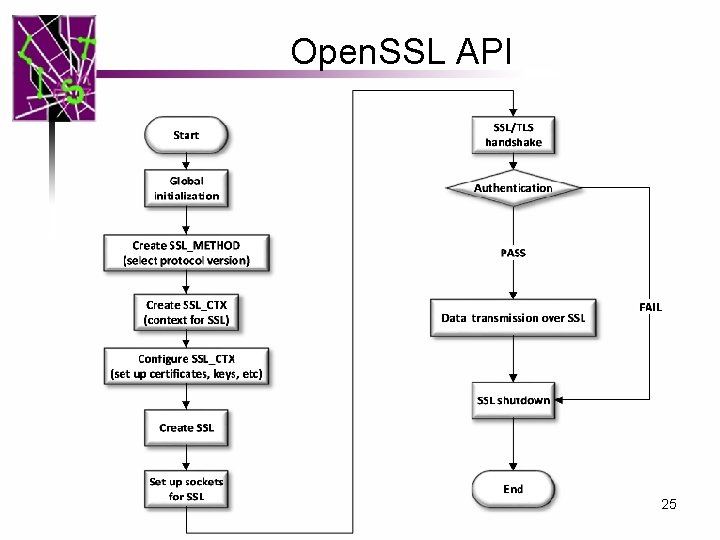
Open. SSL API 25
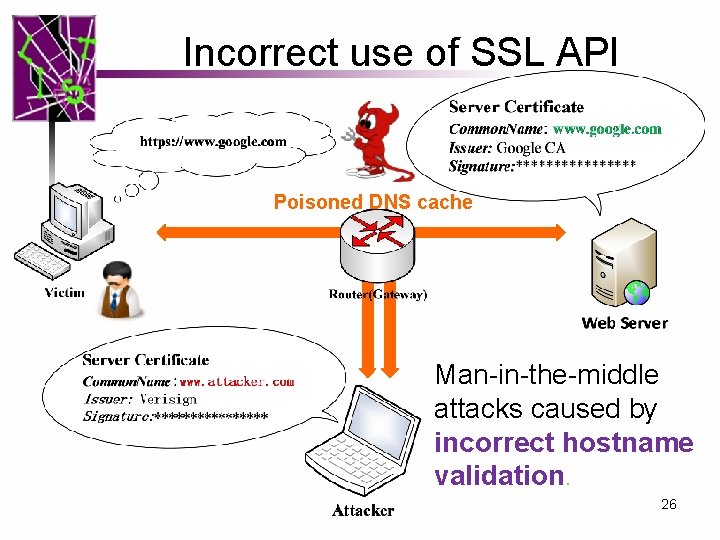
Incorrect use of SSL API Poisoned DNS cache Man-in-the-middle attacks caused by incorrect hostname validation. 26
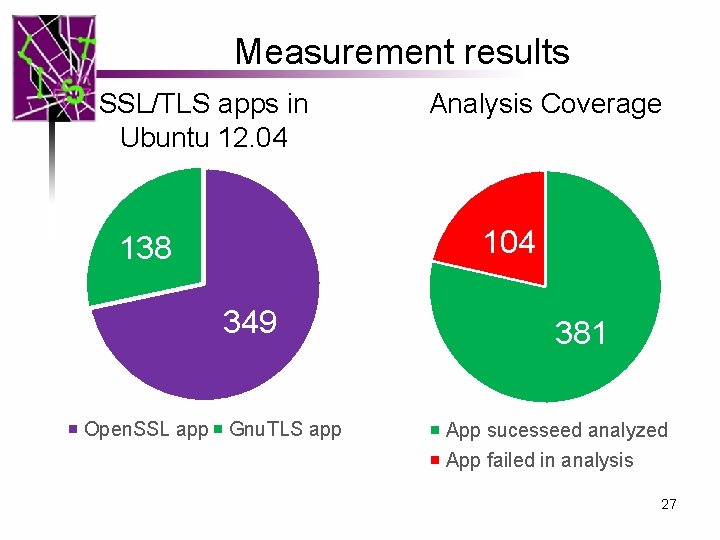
Measurement results SSL/TLS apps in Ubuntu 12. 04 Analysis Coverage 104 138 349 Open. SSL app Gnu. TLS app 381 App sucesseed analyzed App failed in analysis 27
Accuracy 28
Static Analysis 29
- Slides: 29