Vehicular Networks Lili Qiu lilics utexas edu Imagine














![n Push + Map based + Flooding solution [Caliskan’ 06] n Parking lots periodically n Push + Map based + Flooding solution [Caliskan’ 06] n Parking lots periodically](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-27.jpg)






![How to ensure reliability? n Use RTS/CTS & ACK [Korkamaz’ 01] [Zhao’ 07] n How to ensure reliability? n Use RTS/CTS & ACK [Korkamaz’ 01] [Zhao’ 07] n](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-34.jpg)


![Dissemination Approaches Flooding Relaying [Korkamaz’ 04] [Linda’ 00 a] [Nandan’ 06]* [Zhao’ 07] [Basu’ Dissemination Approaches Flooding Relaying [Korkamaz’ 04] [Linda’ 00 a] [Nandan’ 06]* [Zhao’ 07] [Basu’](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-38.jpg)






















![References n n n [Nadeem’ 06] Comparative study of data dissemination models for vanets, References n n n [Nadeem’ 06] Comparative study of data dissemination models for vanets,](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-72.jpg)
![References n n n [Lochert’ 07 a] The Feasibility of Information Dissemination in Vehicular References n n n [Lochert’ 07 a] The Feasibility of Information Dissemination in Vehicular](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-73.jpg)
![References n [Bensilmane’ 04] Optimized dissemination of alarm messages in vehicular ad-hoc networks, HSNMC References n [Bensilmane’ 04] Optimized dissemination of alarm messages in vehicular ad-hoc networks, HSNMC](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-74.jpg)
![Backup n Traffic View [Nadeem’ 06] q q q n Formal models for data Backup n Traffic View [Nadeem’ 06] q q q n Formal models for data](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-75.jpg)
![n Adhoc Relay [Zong’ 01] q q n Analytical Models [Wu’ 04 b] q n Adhoc Relay [Zong’ 01] q q n Analytical Models [Wu’ 04 b] q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-76.jpg)
![n Urban-Multihop [Korkamaz’ 01] q q q n Dissemination Messages [Linda’ 00 a] q n Urban-Multihop [Korkamaz’ 01] q q q n Dissemination Messages [Linda’ 00 a] q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-77.jpg)
![n VADD [Zhao’ 06] q q q n DP, DP-IB [Zhao’ 07] q q n VADD [Zhao’ 06] q q q n DP, DP-IB [Zhao’ 07] q q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-78.jpg)
![n SODAD/SOTIS [Wischhof’ 04] q q q n Data dissemination is achieved by abstracting n SODAD/SOTIS [Wischhof’ 04] q q q n Data dissemination is achieved by abstracting](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-79.jpg)

![Secure solutions for VANETs PKI, Shared Keys References [Raya’ 07] [Harsch’ 06] Authenticat ion Secure solutions for VANETs PKI, Shared Keys References [Raya’ 07] [Harsch’ 06] Authenticat ion](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-83.jpg)


- Slides: 88

Vehicular Networks Lili Qiu lili@cs. utexas. edu

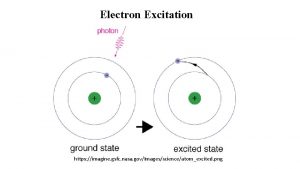
Imagine traveling on a highway with traffic jam miles ahead… • Data delivery latency is high • High deployment cost for data collection Can we do better?

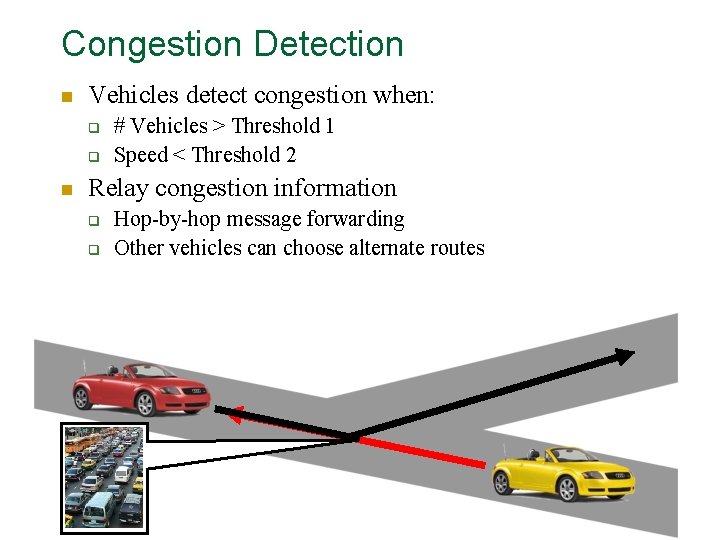
Congestion Detection n Vehicles detect congestion when: q q n # Vehicles > Threshold 1 Speed < Threshold 2 Relay congestion information q q Hop-by-hop message forwarding Other vehicles can choose alternate routes

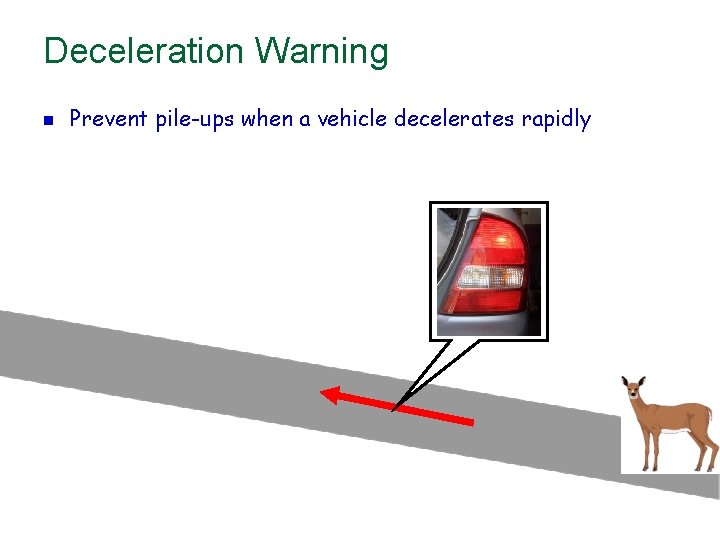
Deceleration Warning n Prevent pile-ups when a vehicle decelerates rapidly

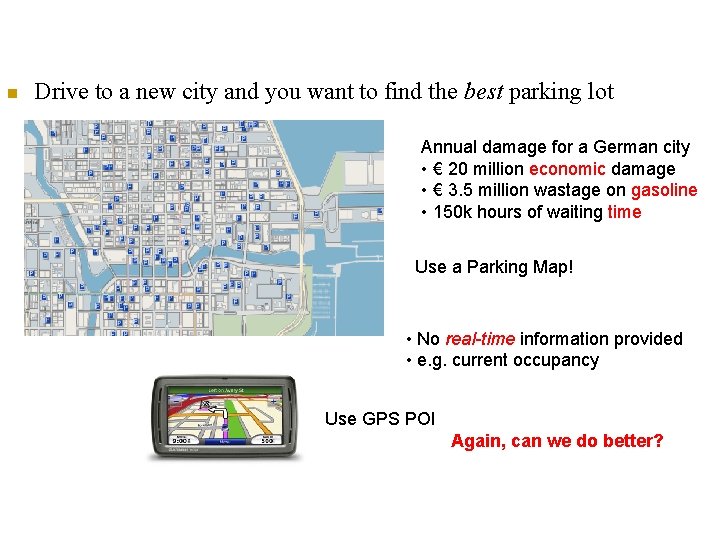
n Drive to a new city and you want to find the best parking lot Annual damage for a German city • € 20 million economic damage • € 3. 5 million wastage on gasoline • 150 k hours of waiting time Use a Parking Map! • No real-time information provided • e. g. current occupancy Use GPS POI Again, can we do better?

Why Vehicular Networks? n Safety q On US highways (2004): n n n 42, 800 Fatalities, 2. 8 Million Injuries ~$230. 6 Billion cost to society Efficiency q Traffic jams waste time and fuel q In 2003, US drivers lost a total of 3. 5 billion hours and 5. 7 billion gallons of fuel to traffic congestion Profit q Safety features and high-tech devices have become product differentiators Convenience and entertainment on-the-move

Applications n Congestion detection n Border clearance n Vehicle platooning n Traction updates n Road hazard warning n Flat tire warning n Collision alert n Merge assistance n Stoplight assistant n Email n Toll collection n Phone n Deceleration warning n Video n Emergency vehicle warning

Emergence of Vehicular Networks n In 1999, FCC allocated 5. 850 -5. 925 GHz band to promote safe and efficient highways q n Emerging radio standard for Dedicated Short-Range Communications (DSRC) q n n Intended for vehicle-to-vehicle and vehicle-to-infrastructure communication Based on an extension of 802. 11 Car 2 Car Consortium expects prototypes in March 2006 Must consider security, or these networks will create more problems than they solve

What system do we need? n Desirable system properties

What system do we need? n Desirable system properties q q n Data collection and distribution in a local environment Low information delivery latency Cheap deployment and communication Secure and privacy preserving What wireless technology to use? 10

What system do we need? n Desirable system properties q q n Probable solutions q q n Data collection and distribution in a local environment Low information delivery latency Cheap deployment and communication Secure and privacy preserving Cellular ? Service fees Satellite ? High latency Wi. Max? Low coverage Vehicular Networks ? What is a vehicular network? 11

What is a vehicular network? n n n Vehicles are equipped with sensing, computing and wireless devices Vehicles talk to road-side infrastructure (V 2 I) and other vehicles (V 2 V) Has all the desirable properties

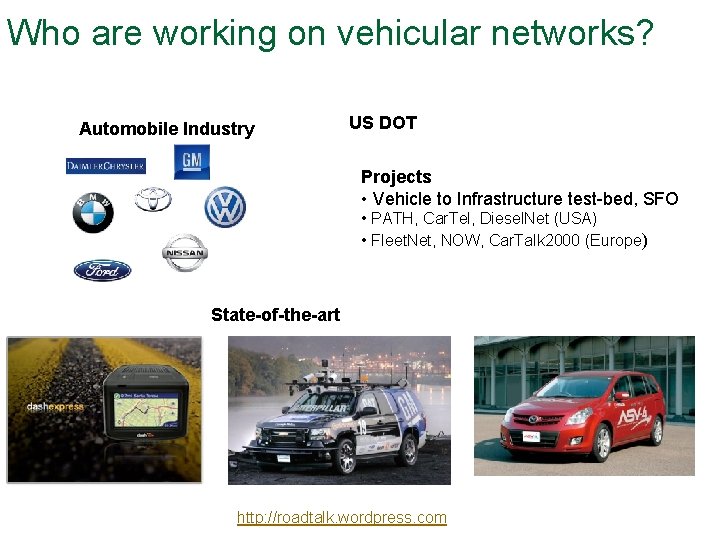
Who are working on vehicular networks? Automobile Industry US DOT Projects • Vehicle to Infrastructure test-bed, SFO • PATH, Car. Tel, Diesel. Net (USA) • Fleet. Net, NOW, Car. Talk 2000 (Europe) State-of-the-art http: //roadtalk. wordpress. com

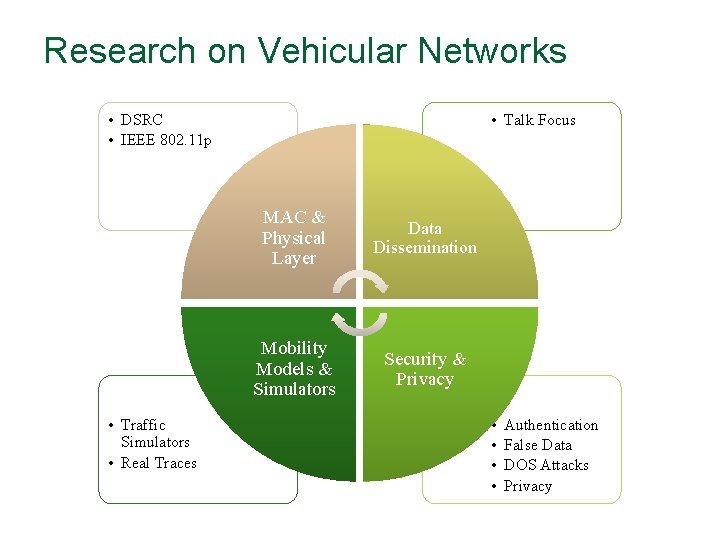
Research on Vehicular Networks • DSRC • IEEE 802. 11 p • Traffic Simulators • Real Traces • Talk Focus MAC & Physical Layer Data Dissemination Mobility Models & Simulators Security & Privacy • • Authentication False Data DOS Attacks Privacy

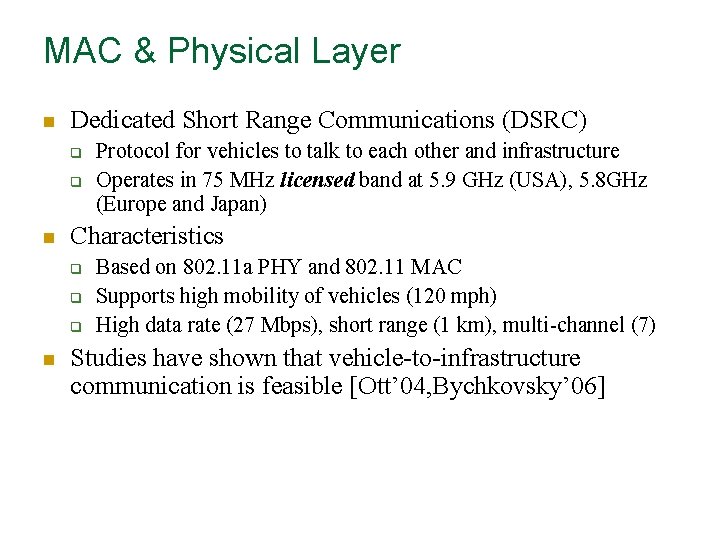
MAC & Physical Layer n Dedicated Short Range Communications (DSRC) q q n Characteristics q q q n Protocol for vehicles to talk to each other and infrastructure Operates in 75 MHz licensed band at 5. 9 GHz (USA), 5. 8 GHz (Europe and Japan) Based on 802. 11 a PHY and 802. 11 MAC Supports high mobility of vehicles (120 mph) High data rate (27 Mbps), short range (1 km), multi-channel (7) Studies have shown that vehicle-to-infrastructure communication is feasible [Ott’ 04, Bychkovsky’ 06]

Challenges in data dissemination in vehicular networks?

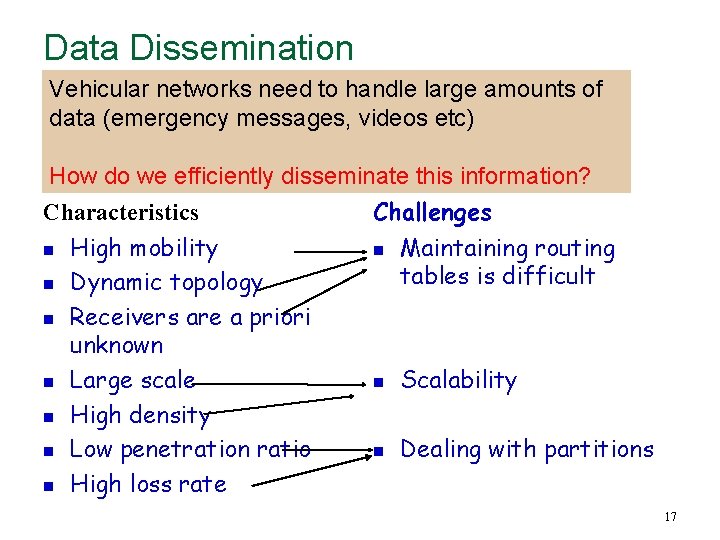
Data Dissemination Vehicular networks need to handle large amounts of data (emergency messages, videos etc) How do we efficiently disseminate this information? Challenges Characteristics n n n n High mobility Dynamic topology Receivers are a priori unknown Large scale High density Low penetration ratio High loss rate n Maintaining routing tables is difficult n Scalability n Dealing with partitions 17

How to disseminate data in vehicular networks?

Classification of Dissemination Approaches n V 2 I / I 2 V dissemination q q Push based Pull based

Push based dissemination n Infostation pushes out the data to everyone Applications: Traffic alerts, Weather alerts, Ads n Why is this useful? n q q n Good for popular data No cross traffic Low contention Drawback q Everyone might not be interested in the same data

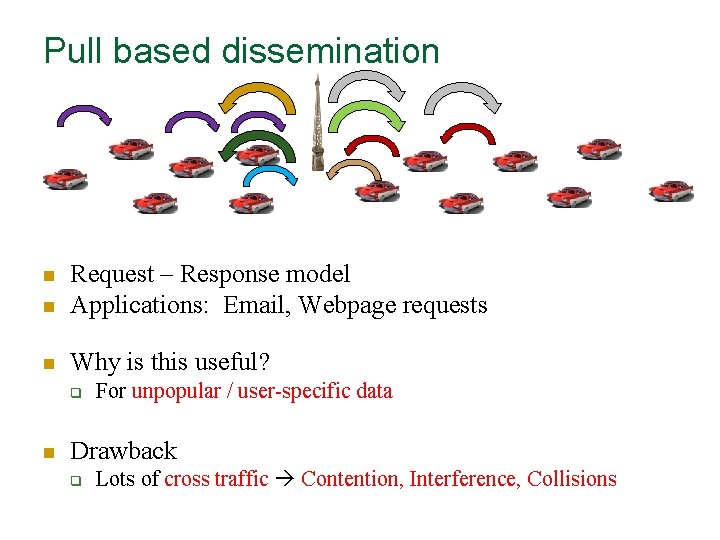
Pull based dissemination n Request – Response model Applications: Email, Webpage requests n Why is this useful? n q n For unpopular / user-specific data Drawback q Lots of cross traffic Contention, Interference, Collisions

Classification of Dissemination Approaches n V 2 I / I 2 V dissemination q q n Push based Pull based V 2 V dissemination

Flooding n Basic Idea q q n Advantages q q n Broadcast generated and received data to neighbors Usually everyone participates in dissemination “Good” for delay sensitive applications Suitable for sparse networks Key Challenges q How to avoid broadcast storm problem?

Techniques to avoid the broadcast problem n Simple forwarding q q n Map based / Geographic forwarding q q n Timer based [Linda’ 00] Hop limited [Nandan’ 06] Directed flooding [Sormani’ 06] Aggregation [Wischhof’ 04] [Nadeem’ 06] [Caliskan’ 06] Limitations?

Limitations n Flooding in general q n High message overhead Not scalable Map based / Geographic q q q Geographically closest doesn’t necessarily reflect the best path! Depend on a location based service Aggregation techniques tradeoff with accuracy

How to find available parking lots?
![n Push Map based Flooding solution Caliskan 06 n Parking lots periodically n Push + Map based + Flooding solution [Caliskan’ 06] n Parking lots periodically](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-27.jpg)
n Push + Map based + Flooding solution [Caliskan’ 06] n Parking lots periodically broadcast occupancy and price information to nearby vehicles n City map is divided into a quad-tree like structure Figure Source: Caliskan- VANETt’ 06 Decentralized Discovery of Parking Places

Decentralized discovery algorithm n Information of a single parking lot is distributed only in proximity n Aggregate information of a region is distributed over wide area n Why this particular solution? q q q Lots of vehicles are interested in the data Push Fast transmission of the information Flooding To avoid broadcast storm Map based

Classification of Dissemination Approaches n V 2 I / I 2 V dissemination q q n Push based Pull based V 2 V dissemination q q Flooding Relaying n n n 2 Challenges Solutions & Drawbacks / Limitations How to deal with network partitions q Opportunistic forwarding ?

Relaying n Basic Idea q q n Advantages q n Instead of flooding the network, select a relay (next hop) Relay node forwards the data to next hop and so on Reduced contention Scalable for dense networks Key Challenges q q How to select the relay neighbors? How to ensure reliability?

How to select a relay neighbor? n Simple forwarding q n Map based / Geographic forwarding q q n Select the node farthest from source [Korkmaz’ 04] [Zhao’ 07] Closest to the destination [Kikaiakos’ 05] Abstract topology into a weighted directed graph [Zhao’ 06] [Wu’ 04 a] Drawback / Limitations?

How to select a relay neighbor? n Simple forwarding q n Map based / Geographic forwarding q q n Select the node farthest from source [Korkmaz’ 04] [Zhao’ 07] Closest to the destination [Kikaiakos’ 05] Abstract topology into a weighted directed graph [Zhao’ 06] [Wu’ 04 a] Drawback / Limitations q q Locally best next hop may not be globally best ! Geographic proximity isn’t the same as physical proximity! 32

How to ensure reliability?
![How to ensure reliability n Use RTSCTS ACK Korkamaz 01 Zhao 07 n How to ensure reliability? n Use RTS/CTS & ACK [Korkamaz’ 01] [Zhao’ 07] n](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-34.jpg)
How to ensure reliability? n Use RTS/CTS & ACK [Korkamaz’ 01] [Zhao’ 07] n Use indirect acknowledgments [Benslimane’ 04] n Use cumulative and aggregate acknowledges n Drawbacks / Limitations q q RTS/CTS incurs lot of overhead Interference affects indirect acknowledgments

Classification of Dissemination Approaches n V 2 I / I 2 V dissemination q q n V 2 V dissemination q q n Push based Pull based Flooding Relaying How to deal with network partitions ?

Opportunistic Forwarding n Problem with partitioned networks q n Opportunistic Forwarding q q n Next hop is not always present Basic Idea: Store and Forward Challenge: What is the right re-broadcast interval? Solutions q q Broadcast repeatedly [Linda’ 00 b][Uichin’ 06][Wischhof’ 04] Cache at infostations [Lochert’ 07 a]

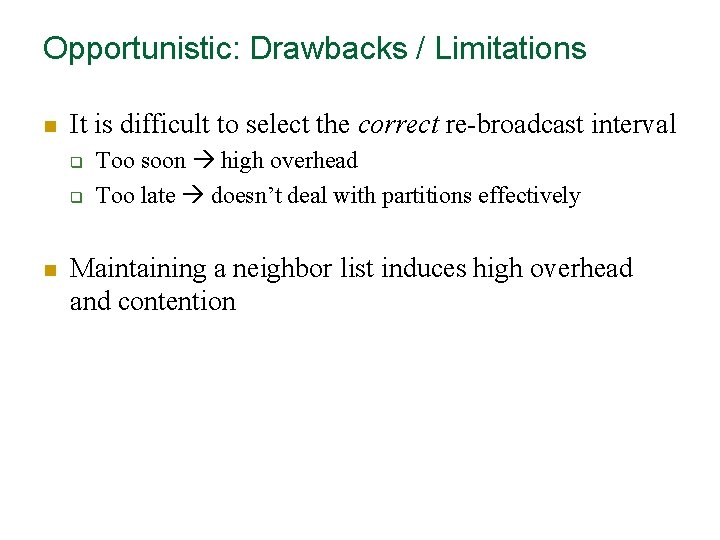
Opportunistic: Drawbacks / Limitations n It is difficult to select the correct re-broadcast interval q q n Too soon high overhead Too late doesn’t deal with partitions effectively Maintaining a neighbor list induces high overhead and contention
![Dissemination Approaches Flooding Relaying Korkamaz 04 Linda 00 a Nandan 06 Zhao 07 Basu Dissemination Approaches Flooding Relaying [Korkamaz’ 04] [Linda’ 00 a] [Nandan’ 06]* [Zhao’ 07] [Basu’](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-38.jpg)
Dissemination Approaches Flooding Relaying [Korkamaz’ 04] [Linda’ 00 a] [Nandan’ 06]* [Zhao’ 07] [Basu’ 04]* [Benslimane’ 04] [Our Work] [Wischhof’ 04] [Caliskan’ 06] [Sormani’ 06] [Nadeem’ 06] [Zhao’ 06]* [Kikaiakos’ 05]* [Wu’ 04 a] Opportunistic Forwarding [Zhong’ 01] [Wu’ 04 b] [Lochert’ 07 a] [Linda’ 00 b] [Uichin’ 06]* * PULL

Take Away V 2 I/I 2 V Dissemination Pros Cons Push Suitable for popular data Not suitable for unpopular data Pull Suitable for unpopular/ user-specific data Pros Cross traffic incurs heavy interference, collisions Cons Flooding Can reliably & quickly distribute data Not scalable for dense networks Relaying Works well even in dense networks Selecting best next hop & reliability is difficult Dissemination in Partitioned networks Pros Cons Opportunistic Suitable for network partitions Difficult to estimate re-broadcast interval High overhead in dense networks V 2 V Dissemination

Our Vehicular Network Research

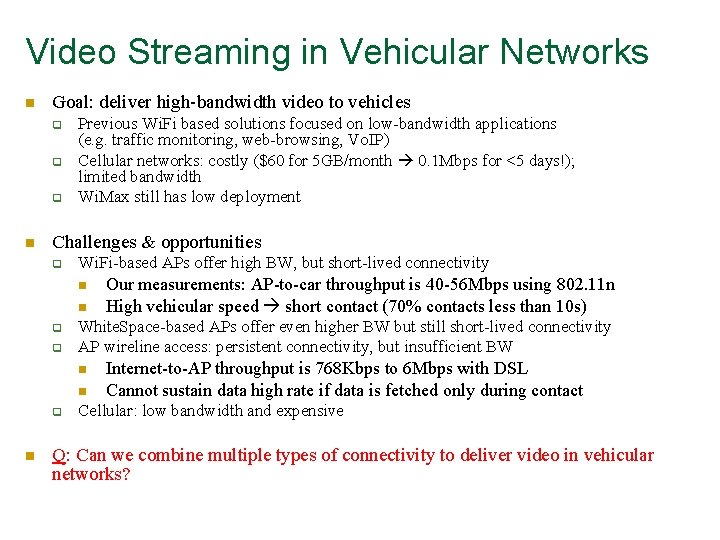
Video Streaming in Vehicular Networks n Goal: deliver high-bandwidth video to vehicles q q q n Previous Wi. Fi based solutions focused on low-bandwidth applications (e. g. traffic monitoring, web-browsing, Vo. IP) Cellular networks: costly ($60 for 5 GB/month 0. 1 Mbps for <5 days!); limited bandwidth Wi. Max still has low deployment Challenges & opportunities q Wi. Fi-based APs offer high BW, but short-lived connectivity n n q q White. Space-based APs offer even higher BW but still short-lived connectivity AP wireline access: persistent connectivity, but insufficient BW n n q n Our measurements: AP-to-car throughput is 40 -56 Mbps using 802. 11 n High vehicular speed short contact (70% contacts less than 10 s) Internet-to-AP throughput is 768 Kbps to 6 Mbps with DSL Cannot sustain data high rate if data is fetched only during contact Cellular: low bandwidth and expensive Q: Can we combine multiple types of connectivity to deliver video in vehicular networks?

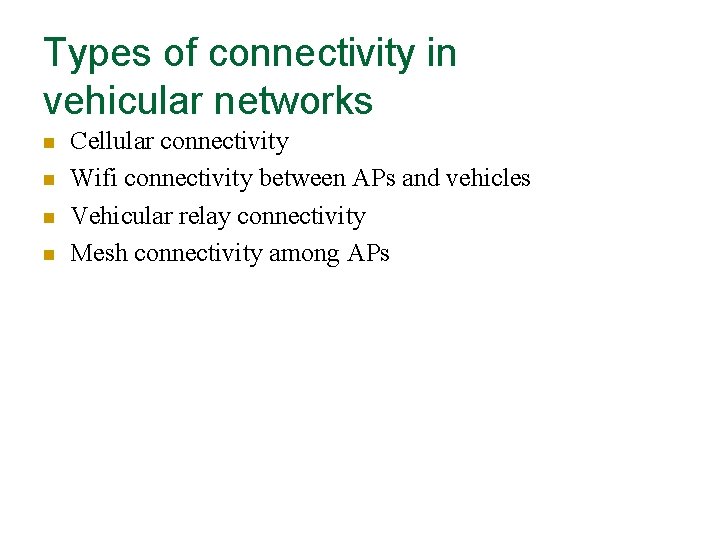
Types of connectivity in vehicular networks n n Cellular connectivity Wifi connectivity between APs and vehicles Vehicular relay connectivity Mesh connectivity among APs

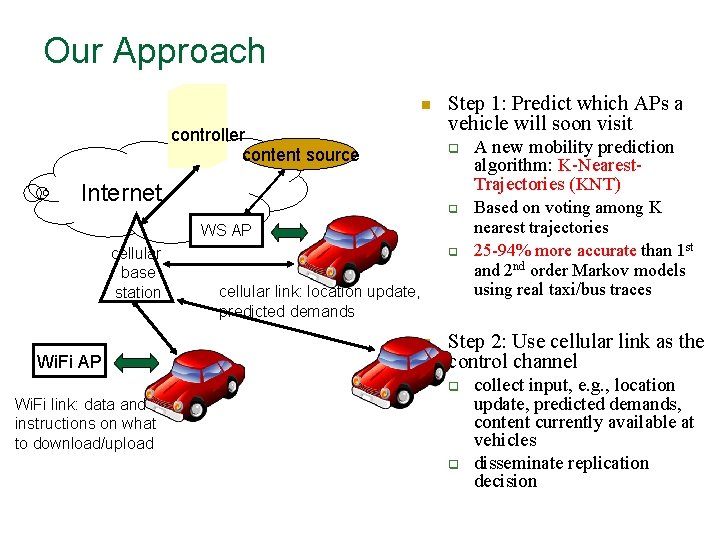
Our Approach n controller content source Step 1: Predict which APs a vehicle will soon visit q Internet q WS AP cellular base station q cellular link: location update, predicted demands n Wi. Fi AP A new mobility prediction algorithm: K-Nearest. Trajectories (KNT) Based on voting among K nearest trajectories 25 -94% more accurate than 1 st and 2 nd order Markov models using real taxi/bus traces Step 2: Use cellular link as the control channel q Wi. Fi link: data and instructions on what to download/upload q collect input, e. g. , location update, predicted demands, content currently available at vehicles disseminate replication decision

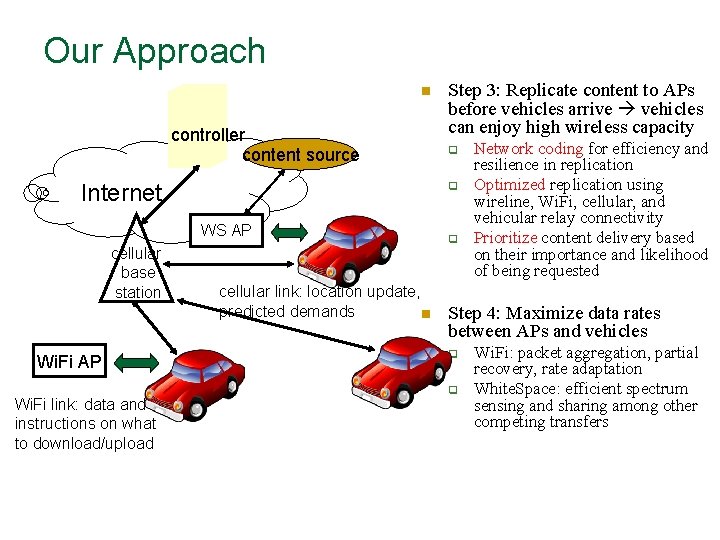
Our Approach n controller content source Internet Wi. Fi AP Wi. Fi link: data and instructions on what to download/upload q q WS AP cellular base station Step 3: Replicate content to APs before vehicles arrive vehicles can enjoy high wireless capacity cellular link: location update, predicted demands n q Network coding for efficiency and resilience in replication Optimized replication using wireline, Wi. Fi, cellular, and vehicular relay connectivity Prioritize content delivery based on their importance and likelihood of being requested Step 4: Maximize data rates between APs and vehicles q q Wi. Fi: packet aggregation, partial recovery, rate adaptation White. Space: efficient spectrum sensing and sharing among other competing transfers

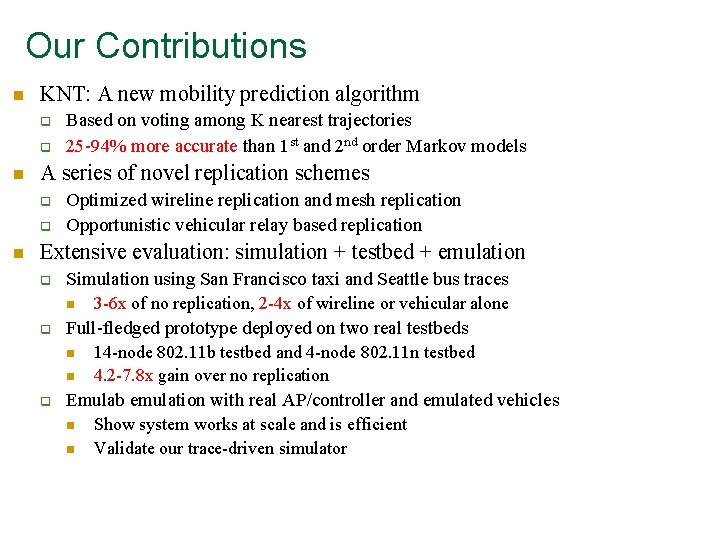
Our Contributions n KNT: A new mobility prediction algorithm q q n A series of novel replication schemes q q n Based on voting among K nearest trajectories 25 -94% more accurate than 1 st and 2 nd order Markov models Optimized wireline replication and mesh replication Opportunistic vehicular relay based replication Extensive evaluation: simulation + testbed + emulation q Simulation using San Francisco taxi and Seattle bus traces n q Full-fledged prototype deployed on two real testbeds n n q 3 -6 x of no replication, 2 -4 x of wireline or vehicular alone 14 -node 802. 11 b testbed and 4 -node 802. 11 n testbed 4. 2 -7. 8 x gain over no replication Emulab emulation with real AP/controller and emulated vehicles n n Show system works at scale and is efficient Validate our trace-driven simulator

Outline n Data dissemination n Vehicular network security q q q Introduction Applications Challenges n n n q q q Authentication vs. Privacy Availability Mobility Key Distribution Low Tolerance for Errors Bootstrap Properties supporting security Security primitives Related work & conclusions

Why Security? n n n Adding security as an afterthought is rarely pretty Utility and ubiquity of vehicular networks will make them likely targets for attack Attacks may have deadly consequences

Motivations for attacks

Motivations for attacks? n Greedy drivers

Adversaries n n n Greedy drivers Snoops Pranksters Industrial Insiders Malicious Attackers

What are possible attacks?

Attacks n Denial of Service (Do. S) q q n Message suppression attacks q n Drop congestion alerts Fabrication q n Overwhelm computational or network capacity Dangerous if users rely on the service Lie about congestion ahead or lie about identity Alteration attacks q Replay transmissions to simulate congestion

Challenges in vehicular network security?

Challenges: Authentication vs. Privacy n Each vehicle should only have one identity q q n Prevents Sybil attacks (e. g. , spoofed congestion) Allows use of external mechanisms (e. g. law enforcement) Drivers value their privacy q q q Legal requirements vary from country to country Vehicles today are only partially anonymous Lack of privacy may lead to lack of security

Challenges: Availability n n n Applications will require real-time responses Increases vulnerability to Do. S Unreliable communication medium q Studies show only 50 -60% of vehicles in range will receive a vehicle’s broadcast

Challenges: Mobility n n Mobility patterns will exhibit strong correlations Transient neighborhood q q n Many neighbors will only be encountered once ever Makes reputation-based systems difficult Brief periods of connectivity q q Vehicles may only be in range for seconds Limits interaction between sender and receiver

Challenges: Key Distribution n Manufacturers q q n Requires cooperation and interoperability Users must trust all manufacturers Government q q q DMV distribution Handled at the state level, so also requires cooperation and interoperability Running a Certificate Authority is non-trivial

Challenges: Low Tolerance for Errors n Strong need for resiliency q q n With 200 million cars in the US, if 5% use an application that works 99. 99999% of the time, still more likely to fail on some car Life-and-death applications must be resilient to occasional failures Focus on prevention, rather than detection & recovery q Safety-related applications may not have margin for driver reaction time

Challenges: Bootstrap n n n Initially, only a small number of vehicles will have DSRC Limited support deployment of infrastructure Ad hoc network protocols allow manufacturers to incorporate security without deviating from their business model

Opportunities?

Some Vehicular Properties Support Security n Regular Inspections q q q n Most states require annual inspection Download updates, CRLs, new certificates Use software attestation to verify vehicle Honest Majority q Most drivers prefer not to tinker with their cars n q May void warranty or violate the law Must protect against worms n n Leverage existing work for PCs Trusted hardware (e. g. , TPMs) may help eventually

Some Vehicular Properties Support Security n Additional input q q Presumed intelligent operator at each node Cannot distract driver, but can still gather or infer data n n E. g. , ignored deceleration warning may indicate a false positive Existing enforcement mechanisms q q For many attacks, attacker must be in close physical proximity May be sufficient to identify the attacker

What are necessary primitives?

Security Primitives: Secure Message Origin n Prevents attacks q q n Road-side attacker cannot spoof vehicles Attacker cannot modify legitimate messages to simulate congestion Beacon-based approach Sig(Kbeacon, time, )

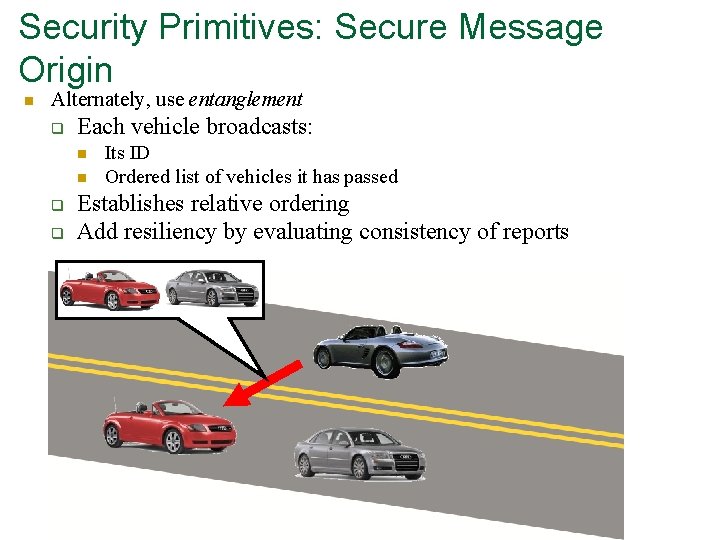
Security Primitives: Secure Message Origin n Alternately, use entanglement q Each vehicle broadcasts: n n q q Its ID Ordered list of vehicles it has passed Establishes relative ordering Add resiliency by evaluating consistency of reports

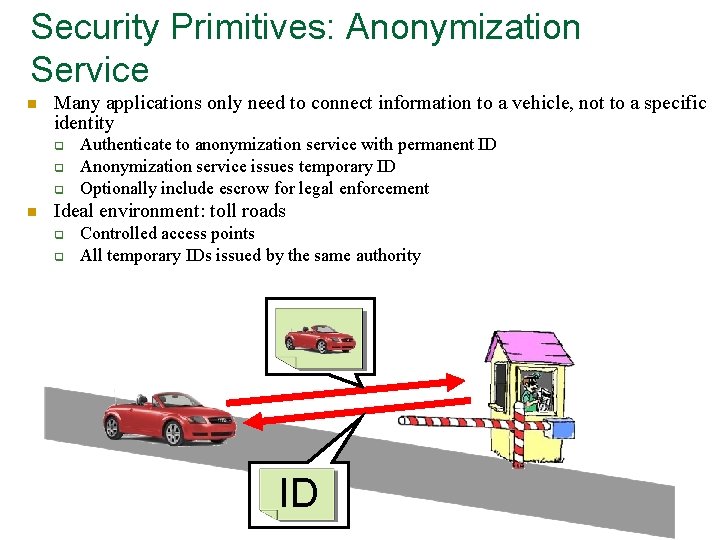
Security Primitives: Anonymization Service n Many applications only need to connect information to a vehicle, not to a specific identity q q q n Authenticate to anonymization service with permanent ID Anonymization service issues temporary ID Optionally include escrow for legal enforcement Ideal environment: toll roads q q Controlled access points All temporary IDs issued by the same authority ID

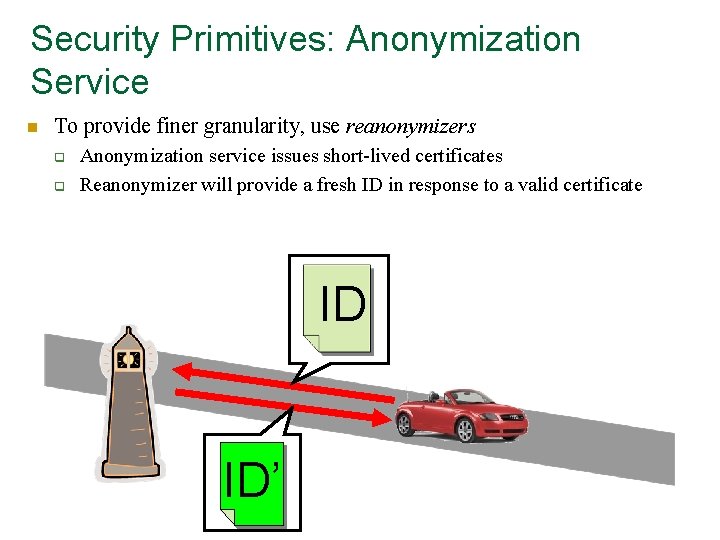
Security Primitives: Anonymization Service n To provide finer granularity, use reanonymizers q q Anonymization service issues short-lived certificates Reanonymizer will provide a fresh ID in response to a valid certificate ID ID’

Additional Security Primitives n Secure Aggregation q n Key Establishment q n Securely count vehicles to report congestion Temporary session keys for platooning or automatic cruise control Message Authentication and Freshness q Prevent alteration and replay attacks

Related Work n n n Driver Ad Hoc Networking Infrastructure (DAHNI) [Zarki et al. , 2002] Potential attacks and secure localization [Hubaux et al. , 2004] Key management and anonymous keys [Raya & Hubaux, 2005]

Summary n Vehicular network data dissemination q q n Challenging environment due to high mobility Modeling vehicular movement and exploiting the model to develop efficient dissemination protocol Vehicular network security q q q Proposed several security primitives, but more are needed. Vehicular networks pose interesting, open security research questions. Vehicular networks will soon be deployed, and their success and safety will depend on the secure solutions we develop.

Thank You for Listening
![References n n n Nadeem 06 Comparative study of data dissemination models for vanets References n n n [Nadeem’ 06] Comparative study of data dissemination models for vanets,](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-72.jpg)
References n n n [Nadeem’ 06] Comparative study of data dissemination models for vanets, Mobiquitous. [Wu’ 04 a] MDDV: A Mobility-Centric Data Dissemination Algorithm for Vehicular Networks, VANET. [Korkamaz’ 04] Urban multi-hop broadcast protocol for inter-vehicle communication systems, VANET. [Sun’ 00] GPS-Based Message Broadcasting for Inter-Vehicle Communication, ICCPP. [Zong’ 01] Ad Hoc Relay Wireless Networks over Moving Vehicles on Highways, Mobihoc. [Wu’ 04 b] Analytical Models for Information Propagation in Vehicle-to-Vehicle Networks, VTC. [Linda’ 00 a] Disseminating Messages among Highly Mobile Hosts based on Inter. Vehicle Communication, IV. [Sormani’ 06] Towards Lightweight Information Dissemination in Inter-Vehicular Networks, VANET [Zhao’ 06] VADD-Vehicle-Assisted Data Delivery in Vehicular Ad Hoc Networks, INFOCOM. [Caliskan’ 06] Decentralized Discovery of Free Parking Spaces, VANET [Basu’ 04] Wireless Ad Hoc Discovery of Parking Meters, WAMES. [Zhao’ 07] Data Pouring and Buffering on The Road: A New Data Dissemination Paradigm for Vehicular Ad Hoc Networks, Transactions on VT
![References n n n Lochert 07 a The Feasibility of Information Dissemination in Vehicular References n n n [Lochert’ 07 a] The Feasibility of Information Dissemination in Vehicular](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-73.jpg)
References n n n [Lochert’ 07 a] The Feasibility of Information Dissemination in Vehicular Ad-Hoc Networks, WON [Wischhof’ 04] Information Dissemination in Self-Organizing Inter-vehicle Networks, Trans on ITS [Uichin’ 06] Flea. Net: A Virtual Market Place on Vehicular Networks, Mobi. Quitos [Kikaiakos’ 05] VITP: An information transfer protocol for vehicular computing, VANET [Bai’ 06] Towards Characterizing and Classifying Communication-based Automotive Applications from a Wireless Networking Perspective, Research Report, GM [Nandan’ 06] Modeling Epidemic Query Dissemination in Ad. Torrent Network, CCNC [Linda’ 00 b] Role-Based Multicast in Highly Mobile but Sparsely Connected Ad Hoc Networks, Mobi. Hoc [Lochert’ 07 b] Probabilistic Aggregation for Data Dissemination in VANETs, VANET [Luo’ 04] A Survey of Inter-Vehicle Communication, Technical Report [Varghese’ 06] Survey of Routing Protocols for Inter-Vehicle Communications, Mobiquitos [Bychkovsky’ 06] A Measurement Study of Vehicular Internet Access Using In Situ Wi. Fi Networks, Mobi. Com [Choo’ 06] Performance Study of Robust Data Transfer Protocol for VANETs, LNCS.
![References n Bensilmane 04 Optimized dissemination of alarm messages in vehicular adhoc networks HSNMC References n [Bensilmane’ 04] Optimized dissemination of alarm messages in vehicular ad-hoc networks, HSNMC](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-74.jpg)
References n [Bensilmane’ 04] Optimized dissemination of alarm messages in vehicular ad-hoc networks, HSNMC n n n n [Bala’ 07] Web Search From a Bus, CHANTS. [Burgess’ 06] Max. Prop: Routing for Vehicle-Based Disruption-Tolerant Networks, INFOCOM. [Ott’ 04] Drive-thru Internet: IEEE 802. 11 b for “Automobile” Users, INFOCOM. [Hartenstein’ 01] Position-Aware Ad Hoc Wireless Networks for Inter-Vehicle Communications, Mobi. Hoc [Namboodiri’ 04] A study on the feasibility of mobile gateways for vehicular ad-hoc networks [Shahram’ 04] PAVAN: A Policy Framework for Content Availability in Vehicular Adhoc Networks, VANET [Raya’ 07] Securing Vehicular Networks, INFOCOM [Harsch’ 06] Secure Position Based Routing for VANETs, VTC
![Backup n Traffic View Nadeem 06 q q q n Formal models for data Backup n Traffic View [Nadeem’ 06] q q q n Formal models for data](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-75.jpg)
Backup n Traffic View [Nadeem’ 06] q q q n Formal models for data dissemination Bi-directional mobility considered Aggregation based flooding Not scalable for dense traffic Flooding is in general good for delay sensitive apps Targeted App: Traffic monitoring MDDV[Wu’ 04 a] q q q Opportunistic + trajectory + geographic forwarding Assumes vehicles have road map and know src, dest region Traffic flow information is fed to vehicles to abstract the road map and make forwarding decisions Group of vehicles near the message head can forward the data Forwarding phase to reach the destination region and then propagation phase to reach all the receivers in the region
![n Adhoc Relay Zong 01 q q n Analytical Models Wu 04 b q n Adhoc Relay [Zong’ 01] q q n Analytical Models [Wu’ 04 b] q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-76.jpg)
n Adhoc Relay [Zong’ 01] q q n Analytical Models [Wu’ 04 b] q q q n Opportunistic (pessimistic) forwarding based on store and forward approach Good for networks with low density Delay-sensitive applications cannot work with this Motion of vehicles significantly affect delivery latency Model an idealistic propagation scheme Consider partitioning of vehicles for information propagation Forward (intra-partition) and catchup(inter-partition) processes Models are for sparse (ignores in-partition propagation) and dense (traffic between cycles) networks Doesn’t model real networks VITP [Kikaiakos’ 05] q q Geographical routing to forward the query to the query region Nodes maintain a neighbor list Once query region is reached, nodes do flooding Reply is sent back to the source via flooding
![n UrbanMultihop Korkamaz 01 q q q n Dissemination Messages Linda 00 a q n Urban-Multihop [Korkamaz’ 01] q q q n Dissemination Messages [Linda’ 00 a] q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-77.jpg)
n Urban-Multihop [Korkamaz’ 01] q q q n Dissemination Messages [Linda’ 00 a] q q n Flooding based solution Nodes wait a time proportional to the distance from the source before broadcast Role based Multicast [Linda’ 00 b] q n Segment the road in the dissemination direction iteratively Select the node in the furthest segment as relay RTS/CTS like mechanism at MAC layer Distance from source decides black burst time Repeaters are used at intersections to propagate to different directions [Linda’ 00 a] + retransmissions based on change in the neighbor set Lightweight Dissemination [Sormani’ 06] q q Dissemination is based on propagation function Propagation function encodes destination region and trajectory Propose several flooding schemes (basic, probabilistic, function driven) Requires a map to create and evaluate the propagation function
![n VADD Zhao 06 q q q n DP DPIB Zhao 07 q q n VADD [Zhao’ 06] q q q n DP, DP-IB [Zhao’ 07] q q](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-78.jpg)
n VADD [Zhao’ 06] q q q n DP, DP-IB [Zhao’ 07] q q q n Pull based routing model to query a static location Map based information (trajectory, traffic) is used to select the next hop with least delay to the destination Models roads and intersections as graphs with estimated delays as weights Store and forward approach to tackle sparse networks Targeted App: To query a static information center Propose a data pouring and buffering dissemination scheme Nodes maintain neighbor list and select farthest node as relay RTS/CTS, Indirect Acks are used for reliability Ibers (Infostations) are deployed at intersections to rebroadcast data on the cross roads Analytical models developed for dissemination capacity and broadcast interval Feasibility [Lochert’ 07] q q Shows the feasbility of information dissemination w. r. t. penetration ratio in city Analytical model to show that connectivity decreases with length Propose installing SSUs (Info. Stations), networked and stand-alone to improve dissemination by re-broadcasting the information Vehicles periodically broadcast information to neighbors (Locomotion + Wireless propagation)
![n SODADSOTIS Wischhof 04 q q q n Data dissemination is achieved by abstracting n SODAD/SOTIS [Wischhof’ 04] q q q n Data dissemination is achieved by abstracting](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-79.jpg)
n SODAD/SOTIS [Wischhof’ 04] q q q n Data dissemination is achieved by abstracting the map into segments and aggregating information Analytical models (coverage processes) to show low penetration ratio leads to low multi-hop range Recurrent broadcasts to tackle with network partitions Adaptive broadcast interval based on provocation/mollification events to suit traffic conditions Targeted App: Vehicles sensing data for traffic info system Flea. Net [Uichin’ 06] q q Proposed an architecture for buy/sell queries dissemination Dissemination is basically by contacts…vehicles that receive queries store it in their db and see if there is a local match Source broadcasts queries periodically to its neighbors (opportunistic) LER routing is used to send notifications from buyers sellers

Some stats n Number of telemetric subscribers will reach >15 million by 2009 n Smart traffic lights can reduce waiting time by 28% during rush hours

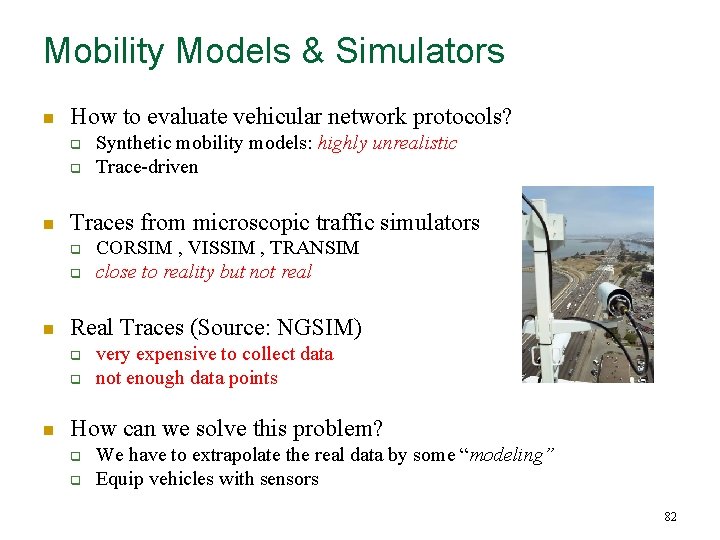
Mobility Models & Simulators n How to evaluate vehicular network protocols? q q n Traces from microscopic traffic simulators q q n CORSIM , VISSIM , TRANSIM close to reality but not real Real Traces (Source: NGSIM) q q n Synthetic mobility models: highly unrealistic Trace-driven very expensive to collect data not enough data points How can we solve this problem? q q We have to extrapolate the real data by some “modeling” Equip vehicles with sensors 82

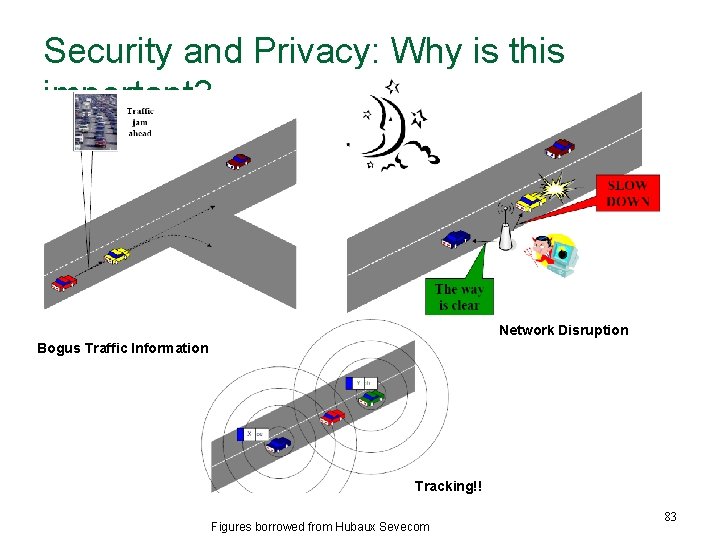
Security and Privacy: Why is this important? Network Disruption Bogus Traffic Information Tracking!! Figures borrowed from Hubaux Sevecom 83
![Secure solutions for VANETs PKI Shared Keys References Raya 07 Harsch 06 Authenticat ion Secure solutions for VANETs PKI, Shared Keys References [Raya’ 07] [Harsch’ 06] Authenticat ion](https://slidetodoc.com/presentation_image_h2/42eb7314a3c79dfb1a1f1f34377492f6/image-83.jpg)
Secure solutions for VANETs PKI, Shared Keys References [Raya’ 07] [Harsch’ 06] Authenticat ion Data Correlation Changing pseudonyms Privacy For more info: • http: //ivc. epfl. ch • http: //sevecom. org Security VANETs DOS attacks False Information Switch channels 84

Applications & Challenges n Lots of potential applications q q q n Safety: Emergency brake light, Collision warning etc Comfort: Toll services, Parking space locator etc Commercial: Map updates, Video download, Services etc What makes vehicular networks challenging? q q Combination of V 2 V + V 2 I communications They face the ‘worst case’ scenarios in real world 85

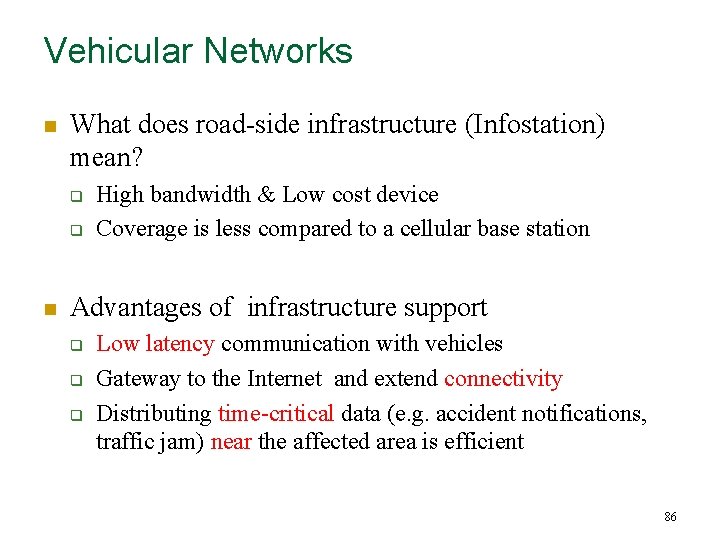
Vehicular Networks n What does road-side infrastructure (Infostation) mean? q q n High bandwidth & Low cost device Coverage is less compared to a cellular base station Advantages of infrastructure support q q q Low latency communication with vehicles Gateway to the Internet and extend connectivity Distributing time-critical data (e. g. accident notifications, traffic jam) near the affected area is efficient 86

Interesting open problems n Not much literature on V 2 I / I 2 V communication q q q n How to deal with cross-traffic in the pull scheme Scheduling transmissions? How to combine push and pull ? What is hybrid ? Mobility traces for evaluation of dissemination q q q Real traces (e. g. NGSIM) are expensive to collect Not enough data points for simulation Need to extrapolate 87

Interesting open problems (Cont. ) n Imagine a service provider wants to install infostations q q n What is the minimum infostation density required Impact of application parameters (size, lifetime) Analytical models q q Understand the bounds on performance Modeling network partitions Better opportunistic schemes 88

Interesting open problems (Cont. ) n Real experiments q q q n Equip vehicles with wireless devices and observe dissemination performance Can obtain real movement traces Designing and testing sample applications Real experiments might invalidate the design! q q Re-design the schemes based on the real observations Repeat! 89
 Korkamaz
Korkamaz Lili qiu
Lili qiu Lili qiu ut austin
Lili qiu ut austin Imagine and explore
Imagine and explore Gen.lib.rus.ece
Gen.lib.rus.ece Laits ut austin
Laits ut austin Momentum conservation law
Momentum conservation law Extricación rápida
Extricación rápida Pbis points hack
Pbis points hack Vehicular cloud
Vehicular cloud Jiezhong qiu
Jiezhong qiu Structure of ias computer
Structure of ias computer Dave shuwen
Dave shuwen Ye qiu
Ye qiu Xiaokang qiu
Xiaokang qiu A switched wan is normally implemented as a
A switched wan is normally implemented as a Backbone networks in computer networks
Backbone networks in computer networks Usahatani adalah
Usahatani adalah Coelenterata
Coelenterata Finančna uprava velenje
Finančna uprava velenje Lili marleen 1939
Lili marleen 1939 História da castanha lili
História da castanha lili Lili.org learning express
Lili.org learning express Bek balla lili
Bek balla lili Aspidochirota
Aspidochirota Lili et tom
Lili et tom A castanha lili
A castanha lili Prüfungsamt lili uni bielefeld
Prüfungsamt lili uni bielefeld Drapeau bronze golf
Drapeau bronze golf Madar lili adrienn
Madar lili adrienn Lili ruger
Lili ruger Intranet utcn
Intranet utcn Lili tancar
Lili tancar Lili me
Lili me Structure of enzymes
Structure of enzymes Edu.sharif.edu
Edu.sharif.edu Skull imagine
Skull imagine These are photos from your photo album
These are photos from your photo album Imagine you are a doctor
Imagine you are a doctor I can hardly imagine
I can hardly imagine I can hardly imagine
I can hardly imagine Locker problem
Locker problem Logomocja imagine komendy
Logomocja imagine komendy Imagine + gerund
Imagine + gerund Why is candy unable to imagine getting rid of his old dog
Why is candy unable to imagine getting rid of his old dog Alliteration in song lyrics
Alliteration in song lyrics Imagine this if you had $86 400
Imagine this if you had $86 400 Imagine you are studying english
Imagine you are studying english Pickit images
Pickit images Hindawi
Hindawi Imagine sparta
Imagine sparta Imagine metaforica pentru toamna
Imagine metaforica pentru toamna Work in pairs imagine you have survived an earthquake
Work in pairs imagine you have survived an earthquake Well imagine that
Well imagine that Imagine the compliance
Imagine the compliance Imagine
Imagine Imagine nation station
Imagine nation station Imagine there's no heaven
Imagine there's no heaven Geo
Geo Solucion
Solucion Imagine ho
Imagine ho Imagine school coachella
Imagine school coachella Hrii
Hrii Metaphors for the word imagine
Metaphors for the word imagine Imagine that you are preparing a project with your friend
Imagine that you are preparing a project with your friend Imagini bidimensionale
Imagini bidimensionale Imagine
Imagine Imagine-se em um centro urbano observando pessoas
Imagine-se em um centro urbano observando pessoas Imagine com kinder
Imagine com kinder Form a mental image of something; imagine
Form a mental image of something; imagine Imagine theres no lonely people
Imagine theres no lonely people In circuitul alaturat becurile sunt identice
In circuitul alaturat becurile sunt identice Close your eyes to what you cant imagine
Close your eyes to what you cant imagine No imagine
No imagine Msia certification
Msia certification 2.imagine
2.imagine Imagine you are going
Imagine you are going Paroles imagine john lennon
Paroles imagine john lennon Imagine que um
Imagine que um Imagine logo
Imagine logo Deserted island game
Deserted island game Imagine a single-loop circuit with a battery
Imagine a single-loop circuit with a battery Engineering design process song
Engineering design process song Development and quality plans
Development and quality plans Imagine logo lietuva
Imagine logo lietuva Imagine you are going
Imagine you are going Whats an adjectives
Whats an adjectives Titanic hole from iceberg
Titanic hole from iceberg Imagine yourself as a living house
Imagine yourself as a living house