VDA Automotive SPICE for Cybersecurity 1 st edition

VDA Automotive SPICE® for Cybersecurity, 1 st edition 2021 Overview © VDA QMC of the content of the Yellow Volume

Overview Agenda Automotive SPICE ® for Cybersecurity (ASPICE CS) is an extension for the Automotive SPICE 3. 1 including a VDA Guideline Within this slide set the following topics are provided: The foundations and basics for its creation. The processes and work products within the model. Detailed view on the process The scope definition and rating 2

Information for SEC-PAM Introduction The need for a Security PAM results of: UNECE Regulation Adoption for EU 07/2022 (JP 01/2022) Type Approval and Cybersecurity management system (CSMS) support ASPICE is qualified to identify process related product risks Elaboration of an enhancement to PAM 3. 1 to cover cybersecurity aspects 3

Information for SEC-PAM Basic Concepts Using SEC-PAM requires an assessment on the VDA scope (it is an enhancement). The existence of a CSMS is anticipated with central management for vulnerabilities, events, incidents and data to support the evaluation and analysis of attacks. No underlying customer/supplier relationship New WPCs for cybersecurity can be created, existing ones to be modified. Preference on generic terms versus specific ones (integrate specific terms) Proposal for hypothetic type approval rating 4
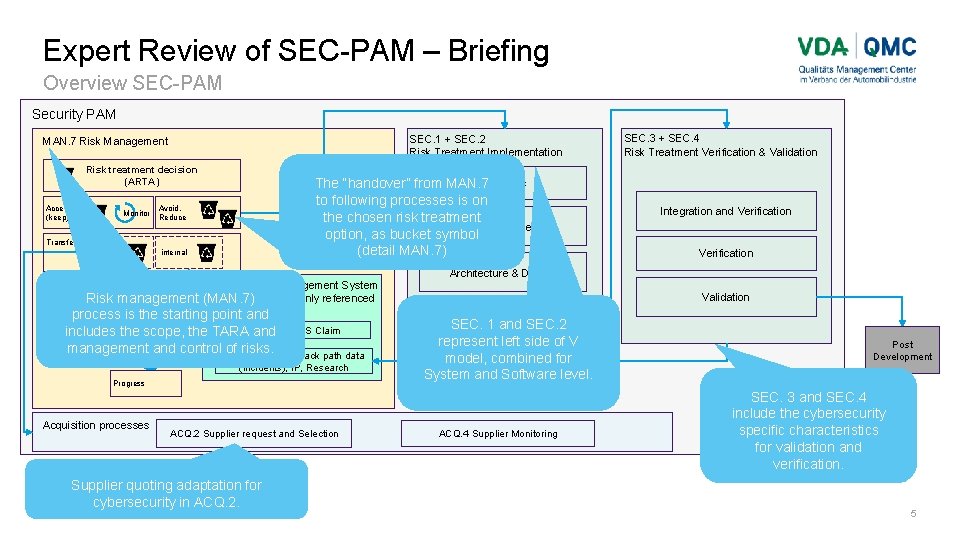
Expert Review of SEC-PAM – Briefing Overview SEC-PAM Security PAM SEC. 1 + SEC. 2 Risk Treatment Implementation MAN. 7 Risk Management Risk treatment decision (ARTA) Accept (keep) Monitor CS Goals The “handover” from MAN. 7 to following processes is on the chosen risk treatment CS Requirements option, as bucket symbol (detail MAN. 7) Avoid, Reduce Transfer external internal Cybersecurity Management System (not in scope itself, only referenced Risk management (MAN. 7) Interfaces process is the startingwith point and to it) Threat scenario CS Claim includes the scope, the TARAMonitoring, and path management Monitor and control Vulnerabilities, of risks. Attack path data Attack & Control (incidents), IP, Research Progress Acquisition processes ACQ. 2 Supplier request and Selection Supplier quoting adaptation for cybersecurity in ACQ. 2. SEC. 3 + SEC. 4 Risk Treatment Verification & Validation Integration and Verification Architecture & Design Validation Implementation SEC. 1 and SEC. 2 represent left side of V model, combined for System and Software level. ACQ. 4 Supplier Monitoring Post Development SEC. 3 and SEC. 4 include the cybersecurity specific characteristics for validation and verification. 5
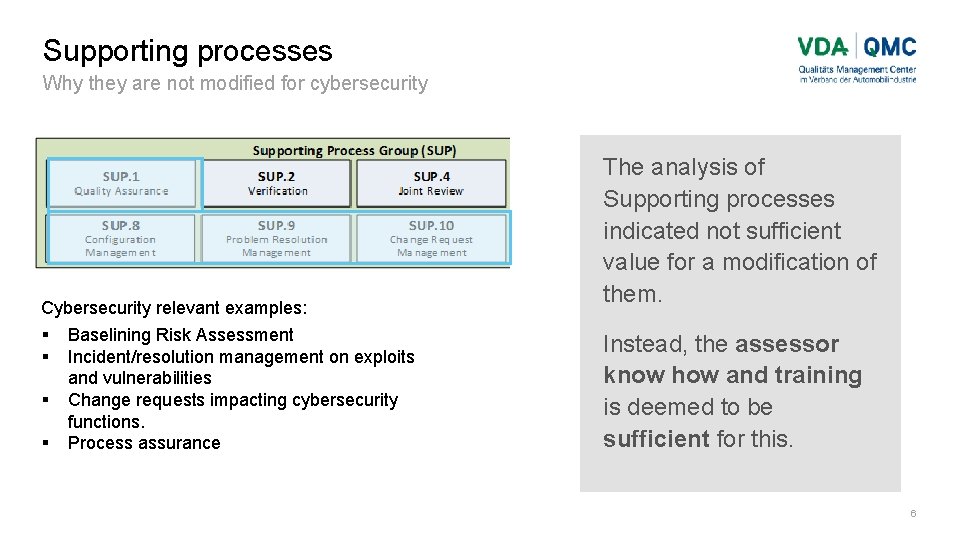
Supporting processes Why they are not modified for cybersecurity Cybersecurity relevant examples: Baselining Risk Assessment Incident/resolution management on exploits and vulnerabilities Change requests impacting cybersecurity functions. Process assurance The analysis of Supporting processes indicated not sufficient value for a modification of them. Instead, the assessor know how and training is deemed to be sufficient for this. 6
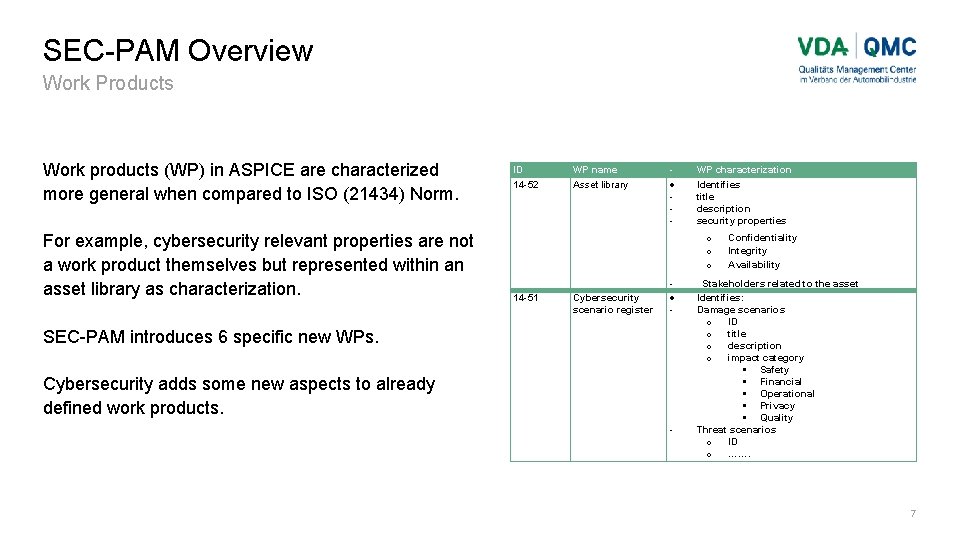
SEC-PAM Overview Work Products Work products (WP) in ASPICE are characterized more general when compared to ISO (21434) Norm. For example, cybersecurity relevant properties are not a work product themselves but represented within an asset library as characterization. ID 14 -52 WP name Asset library - WP characterization Identifies title description security properties o o o 14 -51 Cybersecurity scenario register - SEC-PAM introduces 6 specific new WPs. Cybersecurity adds some new aspects to already defined work products. - Confidentiality Integrity Availability Stakeholders related to the asset Identifies: Damage scenarios o ID o title o description o impact category Safety Financial Operational Privacy Quality Threat scenarios o ID o ……. 7

SEC-PAM Overview Work Products – the new ones ID WP name ACQ. 2 ACQ. 4 SEC. 1 SEC. 2 SEC. 3 SEC. 4 MAN. 7 WP_02 -50 Interface agreement WP_14 -51 Cybersecurity scenario register X WP_14 -52 Asset Library X WP_15 -50 Vulnerability analysis report WP_17 -51 Cybersecurity goals WP_17 -52 Cybersecurity controls X X X 6 new cybersecurity specific output work products. Annex B includes only WPs relevant for SEC-PAM. 8
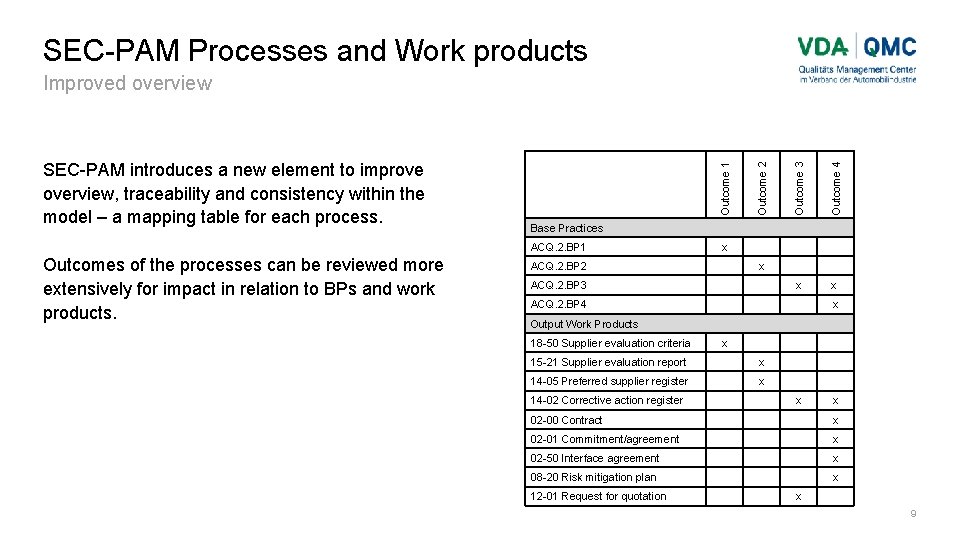
SEC-PAM Processes and Work products Outcome 3 Outcome 4 x x Base Practices ACQ. 2. BP 1 Outcomes of the processes can be reviewed more extensively for impact in relation to BPs and work products. Outcome 2 SEC-PAM introduces a new element to improve overview, traceability and consistency within the model – a mapping table for each process. Outcome 1 Improved overview x ACQ. 2. BP 2 x ACQ. 2. BP 3 ACQ. 2. BP 4 x Output Work Products 18 -50 Supplier evaluation criteria x 15 -21 Supplier evaluation report x 14 -05 Preferred supplier register x 14 -02 Corrective action register x x 02 -00 Contract x 02 -01 Commitment/agreement x 02 -50 Interface agreement x 08 -20 Risk mitigation plan x 12 -01 Request for quotation x 9
Guideline Similar to ASPICE 3. 1, the SEC-PAM is supported with a guideline chapter (Part 2) This guideline is also an enhancement, separated from the 3. 1 guideline. Rules + Recommendations Process relationships and cross process guidance (rules and recommendations) between SEC-PAM related processes and of ASPICE 3. 1 are not given! Assessment with both PAMs require both guidelines used in parallel. + 10

SEC-PAM – Detail In depth look on processes 11
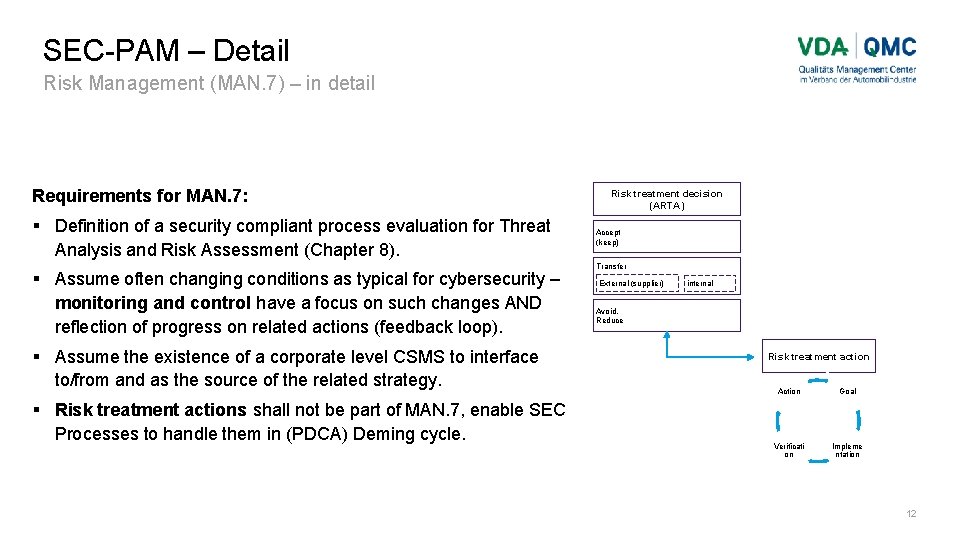
SEC-PAM – Detail Risk Management (MAN. 7) – in detail Requirements for MAN. 7: Definition of a security compliant process evaluation for Threat Analysis and Risk Assessment (Chapter 8). Assume often changing conditions as typical for cybersecurity – monitoring and control have a focus on such changes AND reflection of progress on related actions (feedback loop). Assume the existence of a corporate level CSMS to interface to/from and as the source of the related strategy. Risk treatment actions shall not be part of MAN. 7, enable SEC Processes to handle them in (PDCA) Deming cycle. Risk treatment decision (ARTA) Accept (keep) Transfer External (supplier) internal Avoid, Reduce Risk treatment action Action Goal Verificati on Impleme ntation 12
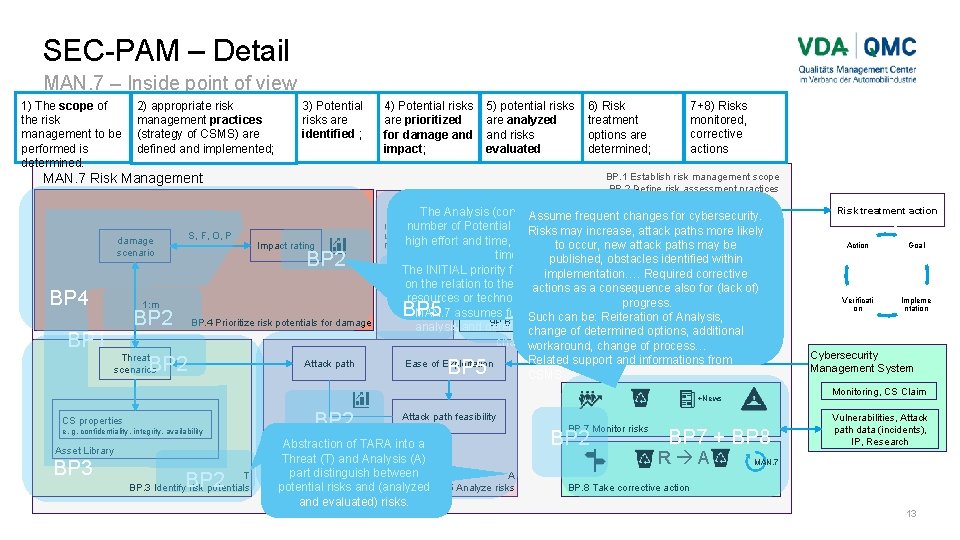
SEC-PAM – Detail MAN. 7 – Inside point of view 1) The scope of the risk management to be performed is determined. 2) appropriate risk management practices (strategy of CSMS) are defined and implemented; 3) Potential risks are identified ; 4) Potential risks are prioritized for damage and impact; 5) potential risks are analyzed and risks evaluated 7+8) Risks 6) Risk *ISO 21434 monitored, treatment corrective options are actions determined; MAN. 7 Risk Management BP. 1 Establish risk management scope BP. 2 Define risk assessment practices Risk treatment decision S, F, O, P damage scenario BP 4 Impact rating BP 2 1: m BP 2 BP 1 BP. 4 Prioritize risk potentials for damage Threat scenarios BP 2 Attack path The Analysis (comes. Assume next) offrequent a large changes for cybersecurity. (ARTA) number of Potential risks could consider a attack paths more likely Risks may increase, high effort and time, even critical to project Accept Avoid, to occur, new attack paths may be (keep) Reduce timeline. published, obstacles identified within The INITIAL priority for analysis is therefore Required corrective implementation…. Transfer on the relation to the max. damage on actions asinternal a(not consequence also for (lack of) external resources or technologies-cherry picking). progress. MAN. 7 assumes further prioritization in Such be: Reiteration of Analysis, BP. 6 Define riskcan treatment option analysis and determination as frequent change of determined options, additional change. workaround, change of process… BP 2 BP 5 BP 2 BP 6 BP 5 Ease of Exploitation Related support and informations from CSMS e. g. confidentiality, integrity, availability Asset Library BP 3 BP 2 T BP. 3 Identify risk potentials BP 2 Attack path feasibility Abstraction of TARA into a Threat (T) and Analysis (A) part distinguish between A potential risks and (analyzed BP. 5 Analyze risks and evaluated) risks. BP. 7 Monitor risks BP 2 BP 7 + BP 8 R A Action Goal Verificati on Impleme ntation Cybersecurity Management System Monitoring, CS Claim +News CS properties Risk treatment action Vulnerabilities, Attack path data (incidents), IP, Research MAN. 7 BP. 8 Take corrective action 13
SEC-PAM – Details SEC. 1 CS Requirements Elicitation and SEC. 2 CS Implementation SEC. 1 Cybersecurity Requirements Elicitation Covers the elicitation of CS goals and CS requirements are collected in a system or software requirements specification SEC. 2 Cybersecurity Implementation Covers the processing of risks that require risk mitigation (not CS claims) No distinction between system and software Covers architectural design, detailed design and implementation Covers identification and communication of vulnerabilities 14
SEC-PAM – Details Short introduction SEC. 3/SEC. 4 Coverage of risk treatment measures SEC. 3 Risk treatment verification Ø Compliance of the implementation to the cybersecurity requirements and the architectural design SEC. 4 Risk treatment validation Ø Compliance of the implementation to the cybersecurity goals Base practice structure according to Automotive SPICE 3. 1 V&V processes Ø Plan, specify, perform, achieve traceability/consistency, communicate No substructure for System/Software and Integration Ø Reduced effort Ø Focus on cybersecurity related measures defined in SEC. 1/SEC. 2 15

SEC-PAM – Details ACQ. 2 Supplier request and Selection/ACQ. 4 Supplier Monitoring General remarks Consideration of requirements/recommendations and work products ISO-IEC DIS 21434 (chapter 15) Implementation via changes/additions in process purpose, outcomes, base practices and ouput work products ACQ. 2 Supplier Request and Selection Relevant CS aspects of former non VDA scope processes ACQ. 3 (Contract Agreement), ACQ. 14 (Request for proposals) and ACQ. 15 (Supplier Qualification) combined into new process ACQ. 2 (Supplier Request and Selection) Focus on supplier evaluation, selection and contractual agreement of CS specific aspects Renamed output work product „ 12 -01 Request for proposal“ to „ 12 -01 Request for quote“ ACQ. 4 Supplier Monitoring Focus on alignment of responsibilities with supplier by interface agreement and corrective actions Re-application of existing process, no structural changes (base practices, additions via notes, etc. ) New output work product „ 02 -50 Interface agreement“ introduced 16
Assessment scope and rating Notes and concept 17
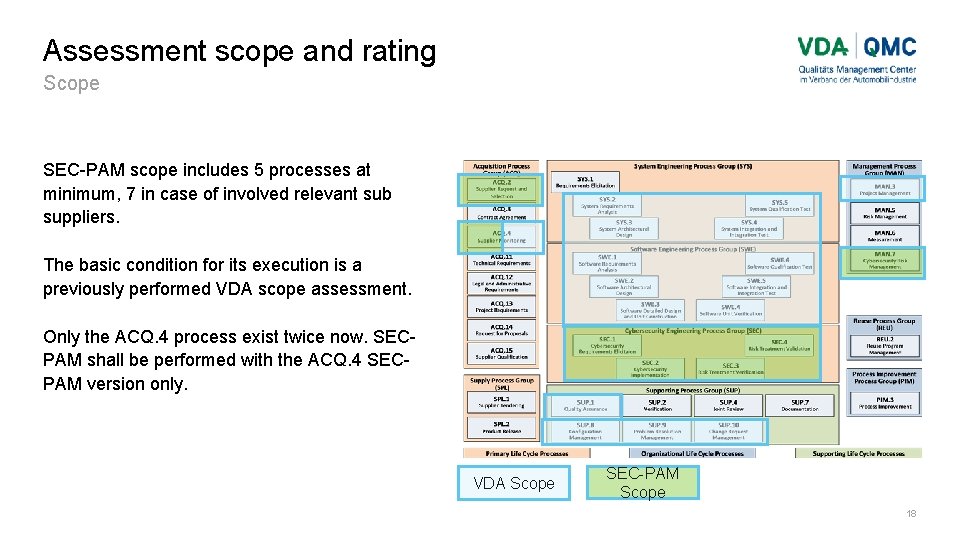
Assessment scope and rating Scope SEC-PAM scope includes 5 processes at minimum, 7 in case of involved relevant sub suppliers. The basic condition for its execution is a previously performed VDA scope assessment. Only the ACQ. 4 process exist twice now. SECPAM shall be performed with the ACQ. 4 SECPAM version only. VDA Scope SEC-PAM Scope 18
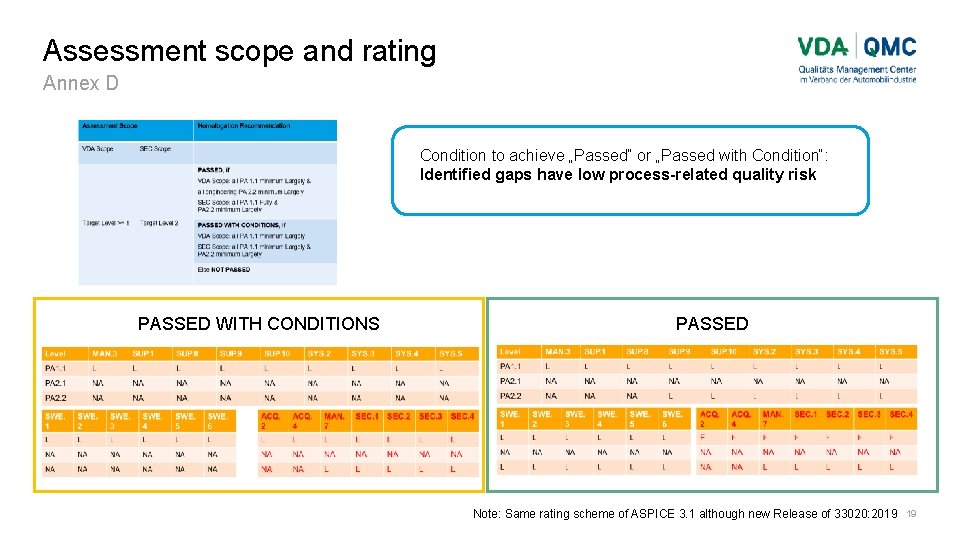
Assessment scope and rating Annex D Condition to achieve „Passed“ or „Passed with Condition“: Identified gaps have low process-related quality risk PASSED WITH CONDITIONS PASSED Note: Same rating scheme of ASPICE 3. 1 although new Release of 33020: 2019 19
Assessment scope and rating Example of planning use cases UC 1 Combined assessment: A-SPICE v 3. 1 VDA-scope and Automotive Cybersecurity SPICE o For ACQ. 4 Supplier Monitoring process instances shall be used: In case that supplier provides cybersecurity relevant content, use ACQ. 4 as defined in Automotive Cybersecurity SPICE, otherwise use ACQ. 4 as defined in Automotive. SPICE UC 2 Separate assessments for A-SPICE VDA-scope and Automotive SPICE for Cybersecurity A-SPICE VDA-scope assessment available and processes rating fulfills criteria for green homologation recommendation, then perform A-Cybersecurity SPICE assessment for SEC processes: MAN. 7, SEC. 1 -SEC. 4, ACQ. 2, ACQ. 4 only UC 2. 1 If Cybersecurity assessment DOES fulfill green homologation requirements Ø No further actions required o UC 2. 2 If Cybersecurity assessment DOES fulfill yellow homologation requirements: Ø Agreement with assessor is needed (improvement plan, reassessment, closure after improvement) o UC 2. 3 If Cybersecurity assessment DOES NOT fulfill yellow homologation requirements: Ø Reassessment for SEC scope is needed o 20

Assessment scope and rating Example of planning use cases Fulfills homologation criteria UC 2: Perform A-SPICE for Cybersecurity UC 2. 2 Agree with assessor on improvment plan and confirmation actions (review, reassessment, …) UC 2. 3 A-SPICE VDA scope assesment homologation criteria not fulfilled for CS scope Process rating Not available UC 1: Perform A-SPICE Assessment for VDA-Scope AND A-SPICE for Cybersecurity homologation criteria not fulfilled for both UC 2. 1 Legend for Homologation-Relevant Rating: Agreement fulfilled NOT PASSED with CONDITIONS input for type approval PASSED 21
- Slides: 21