V 1 1 Deconstructing the Cybersecurity Act of
V 1. 1 Deconstructing the Cybersecurity Act of 2015: model, architecture, interfaces, expressions Tony Rutkowski, mailto: tony@yaanatech. com 01 Jan 2016 Copyright © Yaana Technologies LLC 2016

Cybersecurity Act of 2015: model basics • Establishes a new national paradigm for sharing “cyber threat indicators and defensive measures” among the private sector, Federal government agencies, and international partners – – • § 103 requires the Director of National Intelligence, the Secretary of Homeland Security, the Secretary of Defense, and the Attorney General, in consultation with the heads of the Commerce, Energy and Treasury, to facilitate and promote the model – • • • facilitates use of threat indicators and defensive measures includes grants of antitrust and litigation immunity to participating private sector parties Interim procedures to be jointly developed and issued by 16 Feb 2016 pursuant to § 105; to be finalized by 15 June 2016 §§ 104 & 106 authorize and provide liability protection for private sector monitoring, operation of defensive measures, sharing cyber threat indicators and defensive measures if filtered and protected § 203 reconstructs § 227 of the Homeland Security Act of 2002 to task the National Cybersecurity and Communications Integration Center (NCCIC) to accomplish the purposes of the Act § 224 includes development of advanced network security tools to improve visibility of network activity…to detect and mitigate intrusions and anomalous activity 01 Jan 2016 2
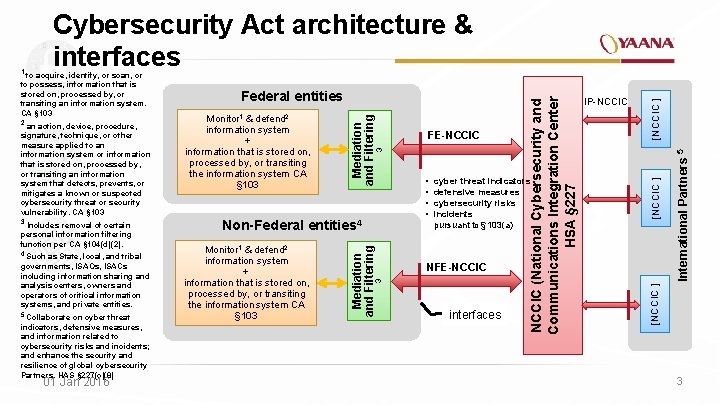
Cybersecurity Act architecture & interfaces 4 Such as State, local, and tribal governments, ISAOs, ISACs including information sharing and analysis centers, owners and operators of critical information systems, and private entities. 5 Collaborate on cyber threat indicators, defensive measures, and information related to cybersecurity risks and incidents; and enhance the security and resilience of global cybersecurity Partners. HAS § 227(c)(8) 01 Jan 2016 • • cyber threat indicators defensive measures cybersecurity risks incidents pursuant to § 103(a) NFE-NCCIC interfaces [NCCIC ] 3 Non-Federal entities 4 Monitor 1 & defend 2 information system + information that is stored on, processed by, or transiting the information system CA § 103 FE-NCCIC International Partners 5 personal information filtering function per CA § 104(d)(2). & information system + information that is stored on, processed by, or transiting the information system CA § 103 IP-NCCIC [NCCIC ] 3 Includes removal of certain defend 2 3 signature, technique, or other measure applied to an information system or information that is stored on, processed by, or transiting an information system that detects, prevents, or mitigates a known or suspected cybersecurity threat or security vulnerability. CA § 103 Monitor 1 Mediation and Filtering 2 an action, device, procedure, Federal entities Mediation and Filtering to possess, information that is stored on, processed by, or transiting an information system. CA § 103 NCCIC (National Cybersecurity and Communications Integration Center HSA § 227 1 to acquire, identify, or scan, or 3

Cybersecurity Act information exchange expressions cyber threat information that is necessary to describe or identify indicator (A) malicious reconnaissance, including anomalous patterns of communications that appear to be transmitted for the purpose of gathering technical information related to a cybersecurity threat or security vulnerability [malicious reconnaissance: a method for actively probing or passively monitoring an information system for the purpose of discerning security vulnerabilities of the information system, if such method is associated with a known or suspected cybersecurity threat. ] (B) a method of defeating a security control or exploitation of a security vulnerability; (C) a security vulnerability, including anomalous activity that appears to indicate the existence of a security vulnerability; (D) a method of causing a user with legitimate access to an information system or information that is stored on, processed by, or transiting an information system to unwittingly enable the defeat of a security control or exploitation of a security vulnerability; (E) malicious cyber command control [a method for unauthorized remote identification of, access to, or use of, an information system or information that is stored on, processed by, or transiting an information system. ] (F) the actual or potential harm caused by an incident, including a description of the information exfiltrated as a result of a particular cybersecurity threat; (G) any other attribute of a cybersecurity threat, if disclosure of such attribute is not otherwise prohibited by law; or (H) any combination thereof. [Cybersecurity threat: an action, . . . on or through an information system that may result in an unauthorized effort to adversely impact the security, availability, confidentiality, or integrity of an information system or information that is stored on, processed by, or transiting an information system. ] defensive an action, device, procedure, signature, technique, or other measure applied to an information system or information that is stored on, processed by, or measure transiting an information system that detects, prevents, or mitigates a known or suspected cybersecurity threat or security vulnerability. [Defensive measure does not include a measure that destroys, renders unusable, provides unauthorized access to, or substantially harms an information system or information stored on, processed by, or transiting such information system not owned by (i) the private entity operating the measure; or (ii) another entity or Federal entity that is authorized to provide consent and has provided consent to that private entity for operation of such measure. ] cybersecurity threats to and vulnerabilities of information or information systems and any related consequences caused by or resulting from unauthorized access, use, risk disclosure, degradation, disruption, modification, or destruction of such information or information systems [Includes related consequences caused by an act of terrorism] incident an occurrence that actually or imminently jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information on an information system, or actually or imminently jeopardizes, without lawful authority, an information system 01 Jan 2016 4
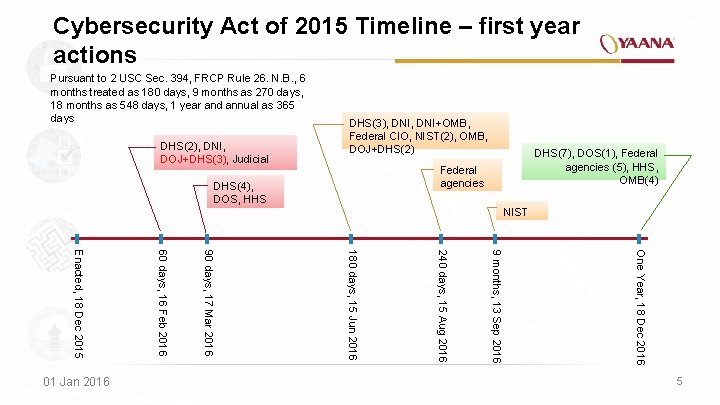
Cybersecurity Act of 2015 Timeline – first year actions Pursuant to 2 USC Sec. 394, FRCP Rule 26. N. B. , 6 months treated as 180 days, 9 months as 270 days, 18 months as 548 days, 1 year and annual as 365 days DHS(2), DNI, DOJ+DHS(3), Judicial DHS(3), DNI+OMB, Federal CIO, NIST(2), OMB, DOJ+DHS(2) DHS(7), DOS(1), Federal agencies (5), HHS, OMB(4) Federal agencies DHS(4), DOS, HHS NIST One Year, 18 Dec 2016 9 months, 13 Sep 2016 240 days, 15 Aug 2016 180 days, 15 Jun 2016 90 days, 17 Mar 2016 60 days, 16 Feb 2016 Enacted, 18 Dec 2015 01 Jan 2016 5
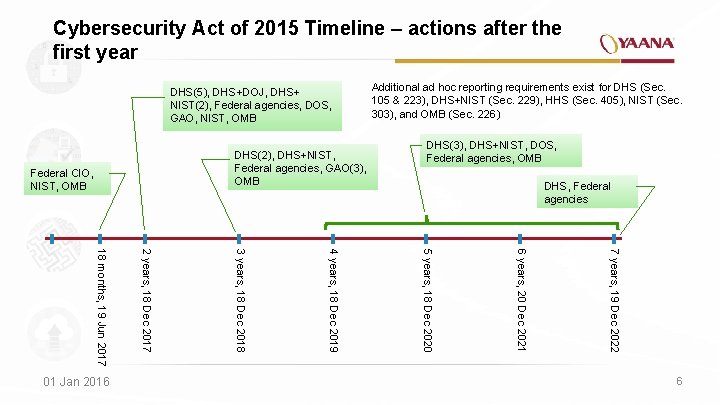
Cybersecurity Act of 2015 Timeline – actions after the first year DHS(5), DHS+DOJ, DHS+ NIST(2), Federal agencies, DOS, GAO, NIST, OMB DHS(2), DHS+NIST, Federal agencies, GAO(3), OMB Federal CIO, NIST, OMB DHS(3), DHS+NIST, DOS, Federal agencies, OMB DHS, Federal agencies 7 years, 19 Dec 2022 6 years, 20 Dec 2021 5 years, 18 Dec 2020 4 years, 18 Dec 2019 3 years, 18 Dec 2018 2 years, 18 Dec 2017 18 months, 19 Jun 2017 01 Jan 2016 Additional ad hoc reporting requirements exist for DHS (Sec. 105 & 223), DHS+NIST (Sec. 229), HHS (Sec. 405), NIST (Sec. 303), and OMB (Sec. 226) 6
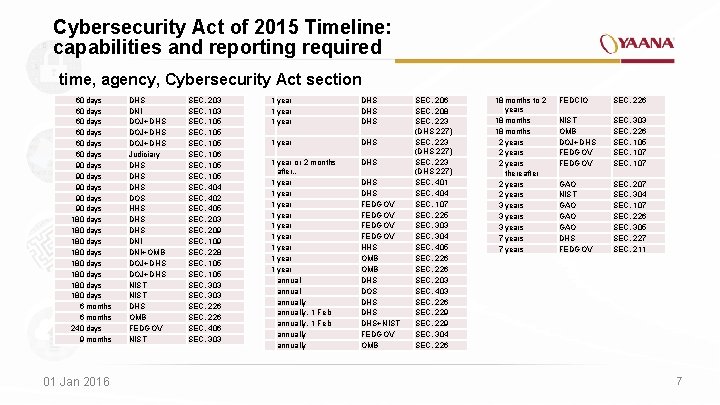
Cybersecurity Act of 2015 Timeline: capabilities and reporting required time, agency, Cybersecurity Act section 60 days 60 days 90 days 90 days 180 days 180 days 6 months 240 days 9 months 01 Jan 2016 DHS DNI DOJ+DHS Judiciary DHS DHS DOS HHS DHS DNI+OMB DOJ+DHS NIST DHS OMB FEDGOV NIST SEC. 203 SEC. 105 SEC. 106 SEC. 105 SEC. 404 SEC. 402 SEC. 405 SEC. 203 SEC. 209 SEC. 109 SEC. 228 SEC. 105 SEC. 303 SEC. 226 SEC. 406 SEC. 303 1 year DHS DHS 1 year or 2 months after… 1 year 1 year 1 year annually, 1 Feb annually DHS DHS FEDGOV HHS OMB DHS DOS DHS DHS+NIST FEDGOV OMB SEC. 206 SEC. 208 SEC. 223 (DHS 227) SEC. 401 SEC. 404 SEC. 107 SEC. 225 SEC. 303 SEC. 304 SEC. 405 SEC. 226 SEC. 203 SEC. 403 SEC. 226 SEC. 229 SEC. 304 SEC. 226 18 months to 2 years 18 months 2 years thereafter 2 years 3 years 7 years FEDCIO SEC. 226 NIST OMB DOJ+DHS FEDGOV SEC. 303 SEC. 226 SEC. 105 SEC. 107 GAO NIST GAO GAO DHS FEDGOV SEC. 207 SEC. 304 SEC. 107 SEC. 226 SEC. 305 SEC. 227 SEC. 211 7

Meeting the challenge: questions and options • What information exchange requirements exist at the three identified NCCIC interfaces? – – – • • • Federal-Entity Non-Federal Entity International Partner What assumptions should be made about the capabilities and architectures within these three domains? Are other interfaces needed? Are there sector-specific interface sub-types and what are they? What are the required information sharing expressions and other capabilities at these interfaces, and to what extent can existing specifications be mapped to these requirements? What are the algorithms for the “personal information of a specific individual or information that identifies a specific individual” filter function? Is it feasible to create an ad-hoc TC CTI or OASIS group to assist in the Act’s implementation similar to other compliance obligations? 01 Jan 2016 8

Key Monitoring and Defense Platforms Implicated 01 Jan 2016 9
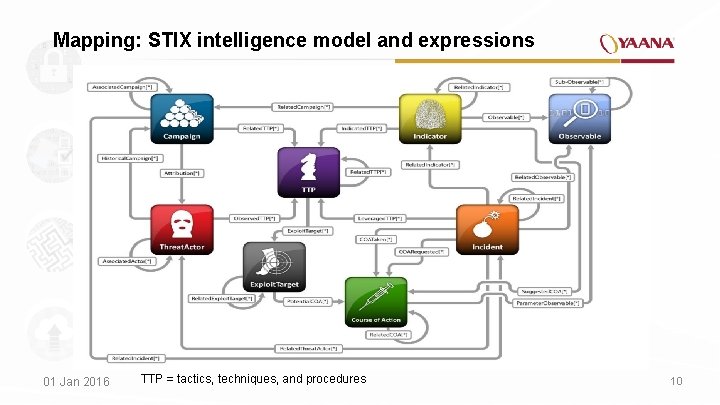
Mapping: STIX intelligence model and expressions 01 Jan 2016 TTP = tactics, techniques, and procedures 10

Mapping: STIX expression clusters Observables Encoding and communicating standardized high-fidelity information about cyber observables, whether dynamic events or stateful measures properties that are observable in the operational cyber domain (including those measured in an operational context as well as more abstract patterns for potential observables that may be targets for observation and analysis a priori) Indicators Specific Observable patterns combined with contextual information intended to represent artifacts and/or behaviors of interest within a cyber security context (consisting of one or more Observable patterns potentially mapped to a related TTP context and adorned with other relevant metadata) Incidents Discrete instances of Indicators along with information discovered or decided during an incident response investigation Tactics, Techniques and Behavior or modus operandi Procedures (TTP) Campaigns Instances of Actors pursuing an intent, as observed through sets of Incidents and/or TTP Actors Characterizations of malicious actors (or adversaries) representing a attack threat including presumed intent and historically observed behavior Vulnerabilities or weaknesses in software, systems, networks or configurations that are targeted for exploitation by the TTP of a Threat. Actor Specific measures to be taken to address threat whether they are corrective or preventative to address Exploit. Targets, or responsive to counter or mitigate the potential impacts of Incidents. Ability to represent markings of the data to specify things like handling restrictions given the potentially sensitive nature of many forms of information Exploit. Targets Courses. Of. Action Data Markings 01 Jan 2016 11

Mapping: The CIS Critical Security Controls for Effective Cyber Defense CSC 1: Inventory of Authorized and Unauthorized Devices CSC 2: Inventory of Authorized and Unauthorized Software CSC 3: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers CSC 4: Continuous Vulnerability Assessment and Remediation CSC 5: Controlled Use of Administrative Privileges CSC 6: Maintenance, Monitoring, and Analysis of Audit Logs CSC 7: Email and Web Browser Protections CSC 8: Malware Defenses CSC 9: Limitation and Control of Network Ports, Protocols, and Services CSC 10: Data Recovery Capability CSC 11: Secure Configurations for Network Devices such as Firewalls, Routers, and Switches CSC 12: Boundary Defense CSC 13: Data Protection CSC 14: Controlled Access Based on the Need to Know CSC 15: Wireless Access Control CSC 16: Account Monitoring and Control CSC 17: Security Skills Assessment and Appropriate Training to Fill Gaps CSC 18: Application Software Security CSC 19: Incident Response and Management CSC 20: Penetration Tests and Red Team Exercises 01 Jan 2016 12

Cybersecurity Act of 2015 Key Reference Model Sections 01 Jan 2016 13
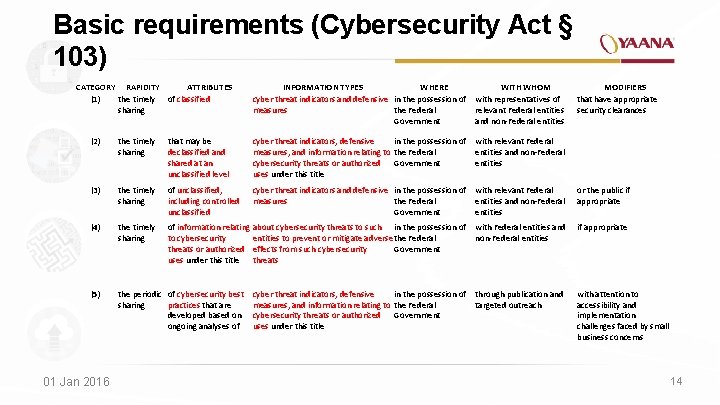
Basic requirements (Cybersecurity Act § 103) CATEGORY RAPIDITY ATTRIBUTES (1) the timely of classified sharing INFORMATION TYPES WHERE cyber threat indicators and defensive in the possession of measures the Federal Government WITH WHOM with representatives of relevant Federal entities and non-Federal entities MODIFIERS that have appropriate security clearances (2) the timely sharing that may be declassified and shared at an unclassified level cyber threat indicators, defensive in the possession of measures, and information relating to the Federal cybersecurity threats or authorized Government uses under this title with relevant Federal entities and non-Federal entities (3) the timely sharing of unclassified, including controlled unclassified cyber threat indicators and defensive in the possession of measures the Federal Government with relevant Federal entities and non-Federal entities or the public if appropriate (4) the timely sharing of information relating about cybersecurity threats to such in the possession of to cybersecurity entities to prevent or mitigate adverse the Federal threats or authorized effects from such cybersecurity Government uses under this title threats with Federal entities and non-Federal entities if appropriate (5) the periodic of cybersecurity best sharing practices that are developed based on ongoing analyses of through publication and targeted outreach with attention to accessibility and implementation challenges faced by small business concerns 01 Jan 2016 cyber threat indicators, defensive in the possession of measures, and information relating to the Federal cybersecurity threats or authorized Government uses under this title 14
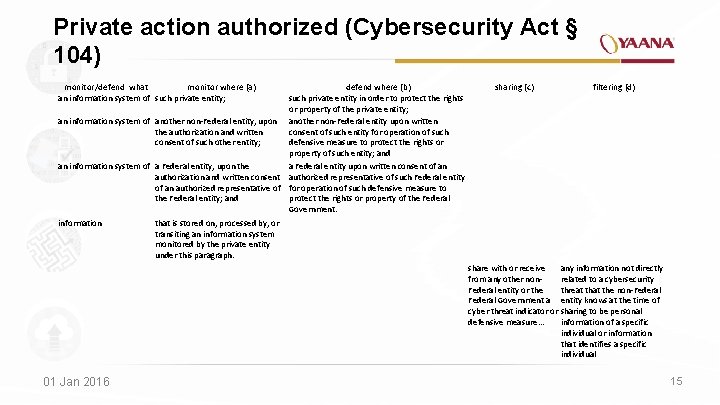
Private action authorized (Cybersecurity Act § 104) monitor/defend what monitor where (a) an information system of such private entity; defend where (b) such private entity in order to protect the rights or property of the private entity; an information system of another non-Federal entity, upon another non-Federal entity upon written the authorization and written consent of such entity for operation of such consent of such other entity; defensive measure to protect the rights or property of such entity; and an information system of a Federal entity, upon the a Federal entity upon written consent of an authorization and written consent authorized representative of such Federal entity of an authorized representative of for operation of such defensive measure to the Federal entity; and protect the rights or property of the Federal Government. information that is stored on, processed by, or transiting an information system monitored by the private entity under this paragraph. 01 Jan 2016 sharing (c) filtering (d) share with or receive from any other non. Federal entity or the Federal Government a cyber threat indicator or defensive measure. . . any information not directly related to a cybersecurity threat the non-Federal entity knows at the time of sharing to be personal information of a specific individual or information that identifies a specific individual 15

Sharing policies and procedures (Cybersecurity Act § 105) • Not later than [16 Feb 2016], the Attorney General and the Secretary of Homeland Security shall – in consultation with the heads of the appropriate Federal entities, jointly develop and submit to Congress interim policies and procedures relating to the receipt of cyber threat indicators and defensive measures by the Federal Government – jointly develop and make publicly available guidance to assist entities and promote sharing of cyber threat indicators with Federal entities • Not later than [15 Jun 2016], the Attorney General and the Secretary of Homeland Security shall, in consultation with the heads of the appropriate Federal entities, jointly issue and make publicly available final policies and procedures relating to the receipt of cyber threat indicators and defensive measures by the Federal Government 01 Jan 2016 16
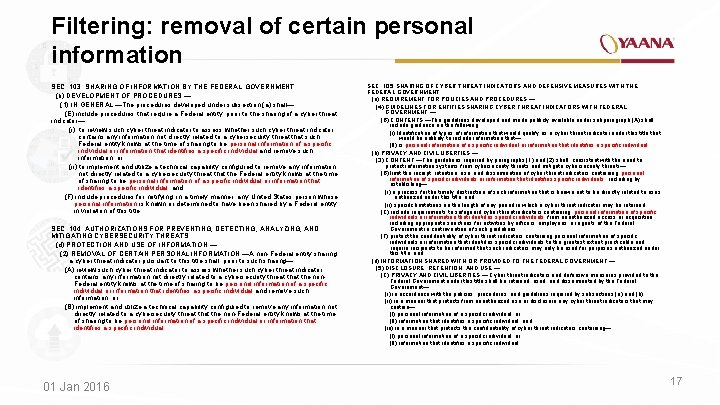
Filtering: removal of certain personal information SEC. 103. SHARING OF INFORMATION BY THE FEDERAL GOVERNMENT (b) DEVELOPMENT OF PROCEDURES. — (1) IN GENERAL. —The procedures developed under subsection (a) shall— (E) include procedures that require a Federal entity, prior to the sharing of a cyber threat indicator— (i) to review such cyber threat indicator to assess whether such cyber threat indicator contains any information not directly related to a cybersecurity threat that such Federal entity knows at the time of sharing to be personal information of a specific individual or information that identifies a specific individual and remove such information; or (ii) to implement and utilize a technical capability configured to remove any information not directly related to a cybersecurity threat the Federal entity knows at the time of sharing to be personal information of a specific individual or information that identifies a specific individual; and (F) include procedures for notifying, in a timely manner, any United States person whose personal information is known or determined to have been shared by a Federal entity in violation of this title. SEC. 104. AUTHORIZATIONS FOR PREVENTING, DETECTING, ANALYZING, AND MITIGATING CYBERSECURITY THREATS. (d) PROTECTION AND USE OF INFORMATION. — (2) REMOVAL OF CERTAIN PERSONAL INFORMATION. —A non-Federal entity sharing a cyber threat indicator pursuant to this title shall, prior to such sharing— (A) review such cyber threat indicator to assess whether such cyber threat indicator contains any information not directly related to a cybersecurity threat the non. Federal entity knows at the time of sharing to be personal information of a specific individual or information that identifies a specific individual and remove such information; or (B) implement and utilize a technical capability configured to remove any information not directly related to a cybersecurity threat the non-Federal entity knows at the time of sharing to be personal information of a specific individual or information that identifies a specific individual. 01 Jan 2016 SEC. 105. SHARING OF CYBER THREAT INDICATORS AND DEFENSIVE MEASURES WITH THE FEDERAL GOVERNMENT. (a) REQUIREMENT FOR POLICIES AND PROCEDURES. — (4) GUIDELINES FOR ENTITIES SHARING CYBER THREAT INDICATORS WITH FEDERAL GOVERNMENT. — (B) CONTENTS. —The guidelines developed and made publicly available under subparagraph (A) shall include guidance on the following: (i) Identification of types of information that would qualify as a cyber threat indicator under this title that would be unlikely to include information that— (II) is personal information of a specific individual or information that identifies a specific individual. (b) PRIVACY AND CIVIL LIBERTIES. — (3) CONTENT. —The guidelines required by paragraphs (1) and (2) shall, consistent with the need to protect information systems from cybersecurity threats and mitigate cybersecurity threats— (B) limit the receipt, retention, use, and dissemination of cyber threat indicators containing personal information of specific individuals or information that identifies specific individuals , including by establishing— (i) a process for the timely destruction of such information that is known not to be directly related to uses authorized under this title; and (ii) specific limitations on the length of any period in which a cyber threat indicator may be retained; (C) include requirements to safeguard cyber threat indicators containing personal information of specific individuals or information that identifies specific individuals from unauthorized access or acquisition, including appropriate sanctions for activities by officers, employees, or agents of the Federal Government in contravention of such guidelines; (F) protect the confidentiality of cyber threat indicators containing personal information of specific individuals or information that identifies specific individuals to the greatest extent practicable and require recipients to be informed that such indicators may only be used for purposes authorized under this title; and (d) INFORMATION SHARED WITH OR PROVIDED TO THE FEDERAL GOVERNMENT. — (5) DISCLOSURE, RETENTION, AND USE. — (C) PRIVACY AND CIVIL LIBERTIES. — Cyber threat indicators and defensive measures provided to the Federal Government under this title shall be retained, used, and disseminated by the Federal Government— (i) in accordance with the policies, procedures, and guidelines required by subsections (a) and (b); (ii) in a manner that protects from unauthorized use or disclosure any cyber threat indicators that may contain— (I) personal information of a specific individual; or (II) information that identifies a specific individual; and (iii) in a manner that protects the confidentiality of cyber threat indicators containing— (I) personal information of a specific individual; or (II) information that identifies a specific individual. 17

NCCIC functions (Homeland + Cybersecurity Acts § 227(c)) 1) a Federal civilian interface for – – – 2) 3) 4) 5) 6) 7) 8) 9) 10) 11) multi-directional and cross-sector sharing of information related to cyber threat indicators, defensive measures, cybersecurity risks, incidents, analysis, and warnings for Federal and non-Federal entities implementation of title I of the Cybersecurity Act of 2015 providing shared situational awareness to enable realtime, integrated, and operational actions across the Federal Government and non -Federal entities to address cybersecurity risks and incidents to Federal and non-Federal entities coordinating the sharing of information related to cyber threat indicators, defensive measures, cybersecurity risks, and incidents across the Federal Government facilitating cross-sector coordination to address cybersecurity risks and incidents, including cybersecurity risks and incidents that may be related or could have consequential impacts across multiple sectors; (A) conducting integration and analysis, including cross-sector integration and analysis, of cyber threat indicators, defensive measures, cybersecurity risks, and incidents; and (B) sharing the analysis with Federal and non-Federal entities upon request, providing timely technical assistance, risk management support, and incident response capabilities to Federal and non. Federal entities with respect to cyber threat indicators, defensive measures, cybersecurity risks, and incidents, which may include attribution, mitigation, and remediation providing information and recommendations on security and resilience measures to Federal and non-Federal entities, including information and recommendations to—(A) facilitate information security; (B) strengthen information systems against cybersecurity risks and incidents. (C) sharing cyber threat indicators and defensive measures engaging with international partners, in consultation with other appropriate agencies sharing cyber threat indicators, defensive measures, and other information related to cybersecurity risks and incidents with Federal and non-Federal entities, including across sectors of critical infrastructure and with State and major urban area fusion centers, as appropriate participating, as appropriate, in national exercises run by the Department assessing and evaluating consequence, vulnerability, and threat information regarding cyber incidents to public safety communications to help facilitate continuous improvements to the security and resiliency of such communications 01 Jan 2016 18

NCCIC composition (Homeland + Cybersecurity Acts § 227(d)(1)) A. Federal entities, such as sector-specific agencies, civilian and law enforcement agencies, and intelligence community B. Non-Federal entities, such as State, local, and tribal governments, ISAOs, ISACs including information sharing and analysis centers, owners and operators of critical information systems, and private entities C. components within the Center that carry out cybersecurity and communications activities D. a designated Federal official for operational coordination with and across each sector E. an entity that collaborates with State and local governments on cybersecurity risks and incidents and has entered into a voluntary information sharing relationship F. other appropriate representatives or entities, as determined by the Secretary (2) INCIDENTS. —In the event of an incident, during exigent circumstances the Secretary may grant a Federal or non-Federal entity immediate temporary access to the Center. 01 Jan 2016 19

NCCIC principles (Homeland + Cybersecurity Acts § 227(e)) A. timely, actionable, and relevant cyber threat indicators, defensive measures, and information related to cybersecurity risks, incidents, and analysis is shared; B. when appropriate, cyber threat indicators, defensive measures, and information related to cybersecurity risks, incidents, and analysis is integrated with other relevant information and tailored to the specific characteristics of a sector C. activities are prioritized and conducted based on the level of risk D. industry sector-specific, academic, and national laboratory expertise is sought and receives appropriate consideration E. continuous, collaborative, and inclusive coordination occurs: across sectors and with sector coordinating councils, ISAOs, and other appropriate non-Federal partners F. the Center works to develop and use mechanisms for sharing information related to cyber threat indicators, defensive measures, cybersecurity risks, and incidents that are technologyneutral, interoperable, real-time, cost-effective, and resilient G. the Center works with other agencies to reduce unnecessarily duplicative sharing of information related to cyber threat indicators, defensive measures, cybersecurity risks, and incidents H. the Center designates an agency contact for non-Federal entities; (2) information related to cyber threat indicators, defensive measures, cybersecurity risks, and incidents is appropriately safeguarded against unauthorized access or disclosure 01 Jan 2016 20

NCCIC automated information sharing (Homeland + Cybersecurity Acts § 227(g)) A. Standards and best practices in coordination with industry and other stakeholders, shall develop capabilities making use of existing information technology industry standards and best practices, as appropriate, that support and rapidly advance the development, adoption, and implementation of automated mechanisms for the sharing of cyber threat indicators and defensive measures in accordance with title I of the Cybersecurity Act of 2015 B. Voluntary information sharing PROCEDURES A. (A) IN GENERAL. —The Center may enter into a voluntary information sharing relationship with any consenting non-Federal B. entity for the sharing of cyber threat indicators and defensive measures for cybersecurity purposes in accordance with this section. Nothing in this subsection may be construed to require any non-Federal entity to enter into any such information sharing relationship with the Center or any other entity. The Center may terminate a voluntary information sharing relationship under this subsection, at the sole and unreviewable discretion of the Secretary, acting through the Under Secretary appointed under section 103(a)(1)(H), for any reason, including if the Center determines that the non-Federal entity with which the Center has entered into such a relationship has violated the terms of this subsection. (B) NATIONAL SECURITY. —The Secretary may decline to enter into a voluntary information sharing relationship under this subsection, at the sole and unreviewable discretion of the Secretary, acting through the Under Secretary appointed under section 103(a)(1)(H), for any reason, including if the Secretary determines that such is appropriate for national security. VOLUNTARY INFORMATION SHARING RELATIONSHIPS A voluntary information sharing relationship under this subsection may be characterized as an agreement (A) STANDARD AGREEMENT. —For the use of a non-Federal entity, the Center shall make available a standard agreement, consistent with this section, on the Department’s website. (B) NEGOTIATED AGREEMENT. —At the request of a non-Federal entity, and if determined appropriate by the Center, at the sole and unreviewable discretion of the Secretary, acting through the Under Secretary appointed under section 103(a)(1)(H) (C) EXISTING AGREEMENTS 01 Jan 2016 21
- Slides: 21