Using UML Patterns and Java ObjectOriented Software Engineering

Using UML, Patterns, and Java Object-Oriented Software Engineering Chapter 8, Design Patterns Proxy
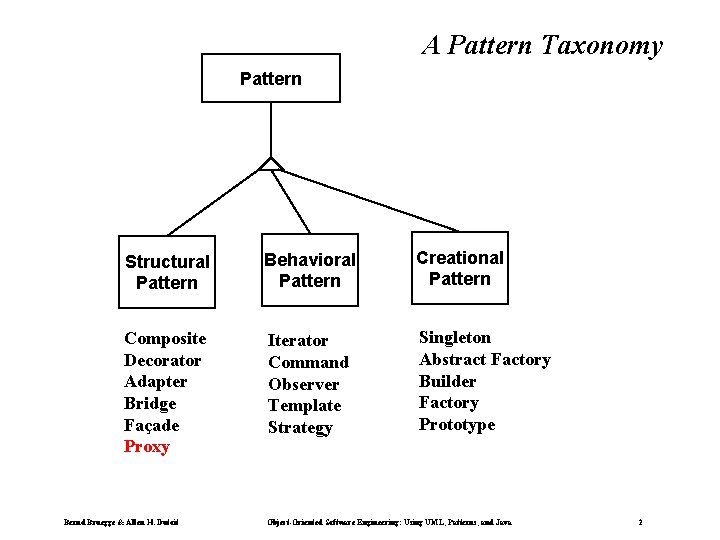
A Pattern Taxonomy Pattern Structural Pattern Behavioral Pattern Creational Pattern Composite Decorator Adapter Bridge Façade Proxy Iterator Command Observer Template Strategy Singleton Abstract Factory Builder Factory Prototype Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 2

Proxy Pattern: Motivation ¨ It is 3: 00 PM and I am sitting at my 14. 4 baud modem connection and retrieve a fancy web site. This is prime web time, so I am getting 10 bits/sec. ¨ What can I do? Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 3

Proxy Pattern ¨ What is expensive? w Object Creation w Object Initialization ¨ ¨ Defer object creation and object initialization to the time you need the object Proxy pattern: w Reduces the cost of accessing objects w Uses another object (“the proxy”) that acts as a stand-in for the real object w The proxy creates the real object only if the user asks for it Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 4
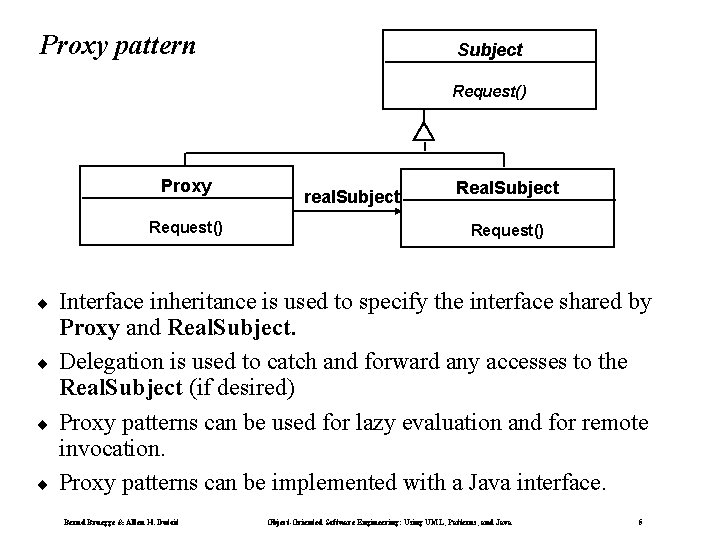
Proxy pattern Subject Request() Proxy Request() ¨ ¨ real. Subject Request() Interface inheritance is used to specify the interface shared by Proxy and Real. Subject. Delegation is used to catch and forward any accesses to the Real. Subject (if desired) Proxy patterns can be used for lazy evaluation and for remote invocation. Proxy patterns can be implemented with a Java interface. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 5
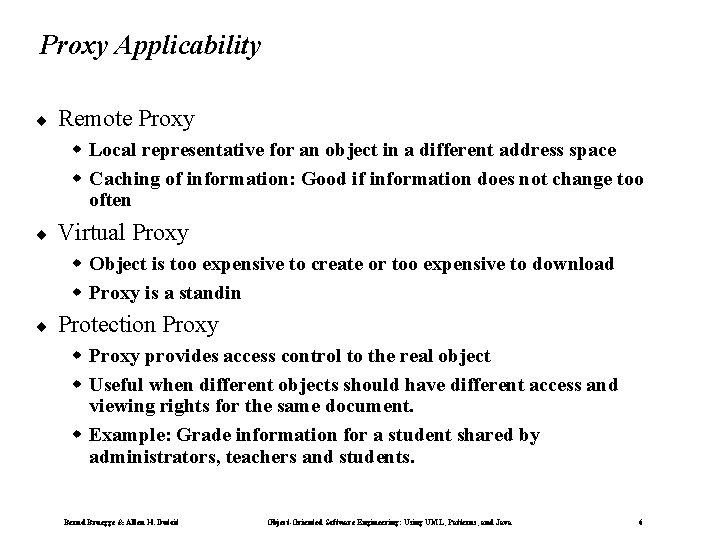
Proxy Applicability ¨ Remote Proxy w Local representative for an object in a different address space w Caching of information: Good if information does not change too often ¨ Virtual Proxy w Object is too expensive to create or too expensive to download w Proxy is a standin ¨ Protection Proxy w Proxy provides access control to the real object w Useful when different objects should have different access and viewing rights for the same document. w Example: Grade information for a student shared by administrators, teachers and students. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 6
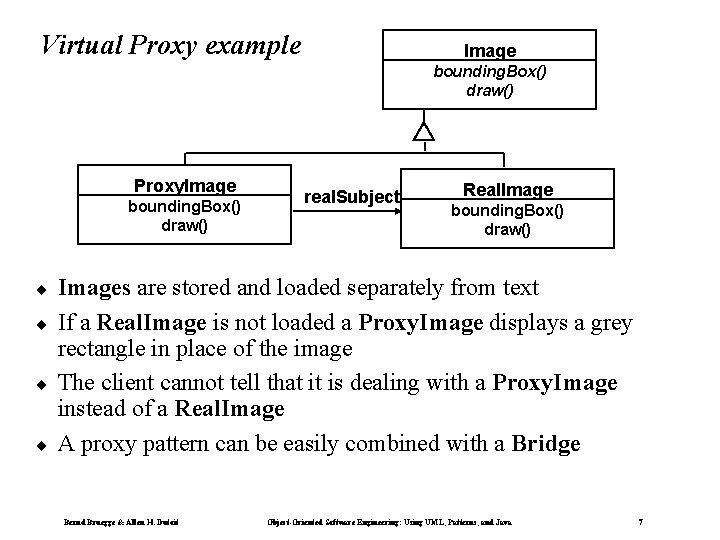
Virtual Proxy example Image bounding. Box() draw() Proxy. Image bounding. Box() draw() ¨ ¨ real. Subject Real. Image bounding. Box() draw() Images are stored and loaded separately from text If a Real. Image is not loaded a Proxy. Image displays a grey rectangle in place of the image The client cannot tell that it is dealing with a Proxy. Image instead of a Real. Image A proxy pattern can be easily combined with a Bridge Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 7
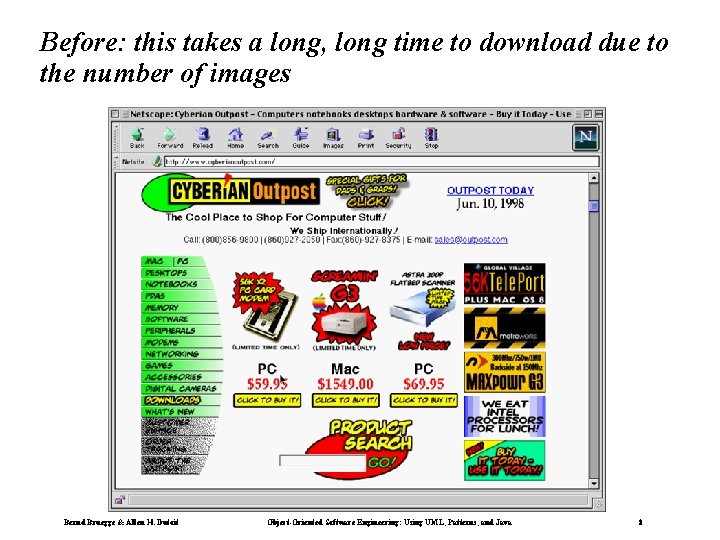
Before: this takes a long, long time to download due to the number of images Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 8
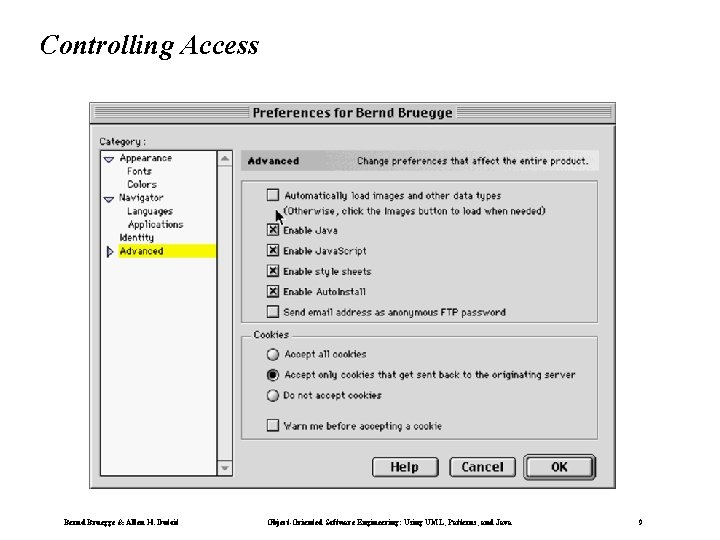
Controlling Access Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 9
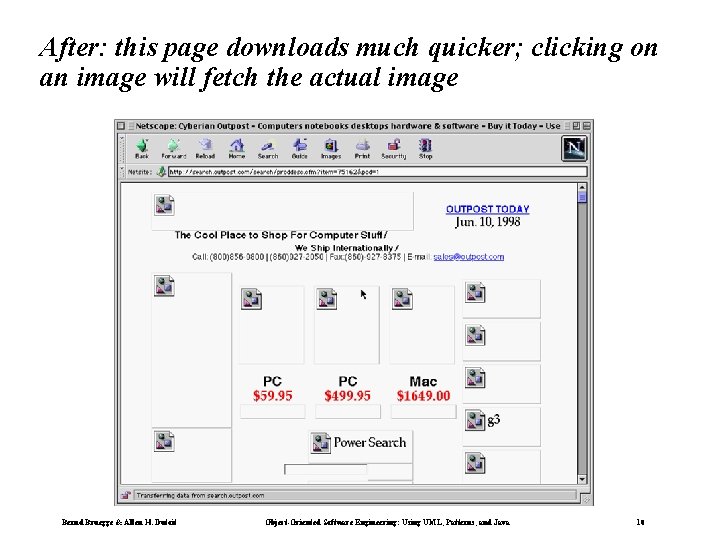
After: this page downloads much quicker; clicking on an image will fetch the actual image Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 10
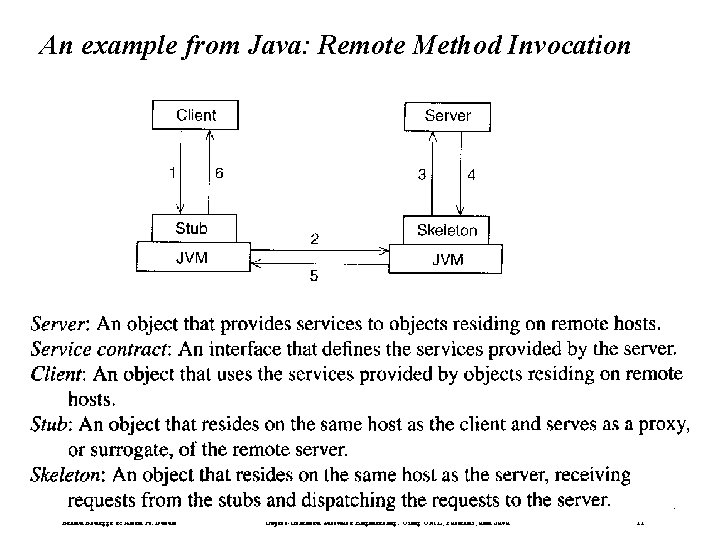
An example from Java: Remote Method Invocation Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 11
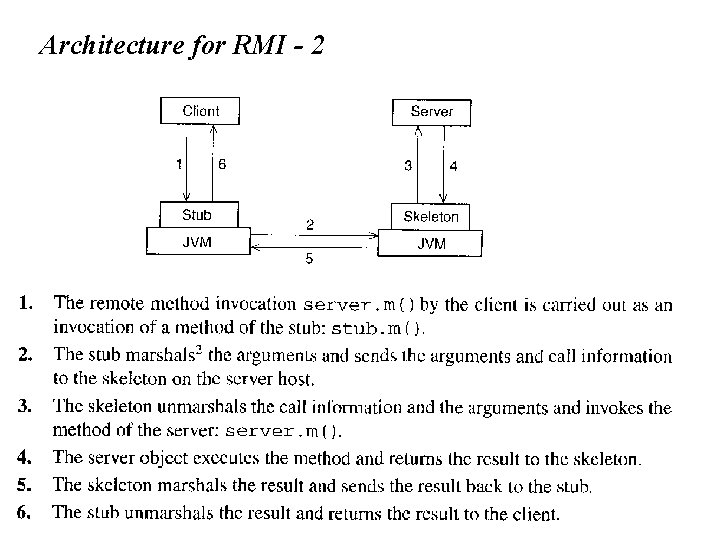
Architecture for RMI - 2 Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 12
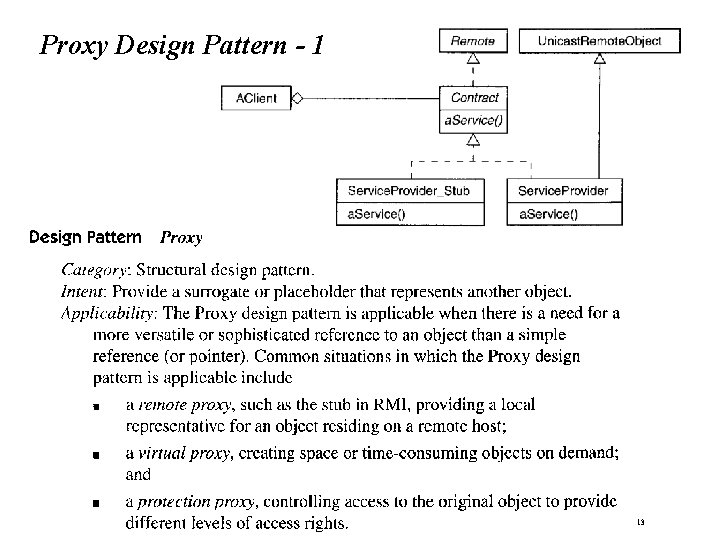
Proxy Design Pattern - 1 Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 13
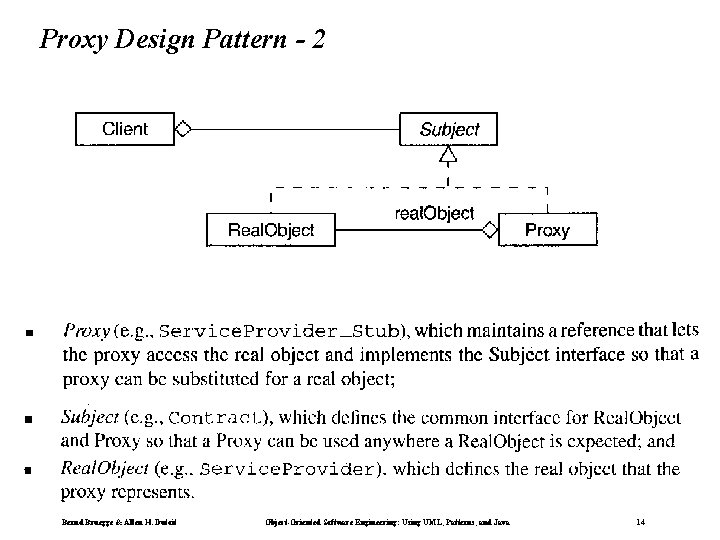
Proxy Design Pattern - 2 Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 14
- Slides: 14