Using UML Patterns and Java ObjectOriented Software Engineering

Using UML, Patterns, and Java Object-Oriented Software Engineering Art for Chapter 7 System Design: Addressing Design Goals
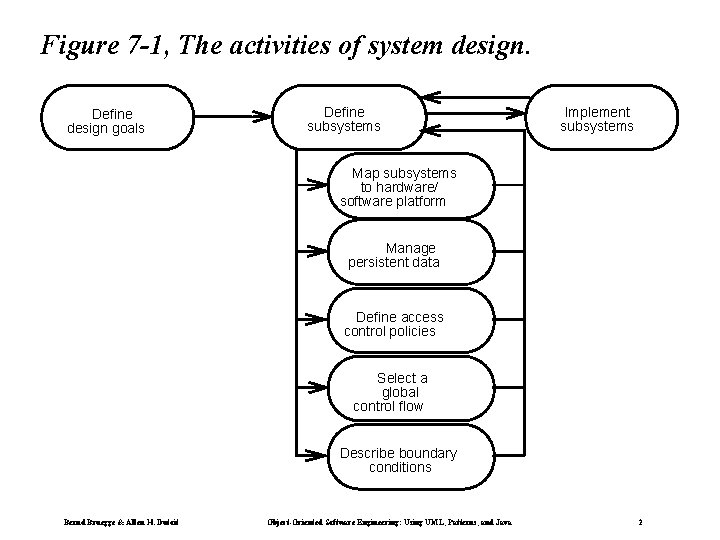
Figure 7 -1, The activities of system design. Define design goals Define subsystems Implement subsystems Map subsystems to hardware/ software platform Manage persistent data Define access control policies Select a global control flow Describe boundary conditions Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 2
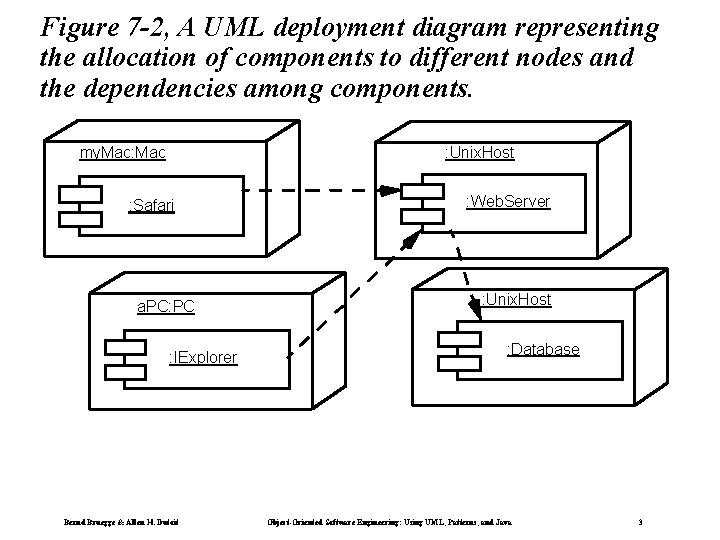
Figure 7 -2, A UML deployment diagram representing the allocation of components to different nodes and the dependencies among components. my. Mac: Mac : Unix. Host : Safari a. PC: PC : IExplorer Bernd Bruegge & Allen H. Dutoit : Web. Server : Unix. Host : Database Object-Oriented Software Engineering: Using UML, Patterns, and Java 3
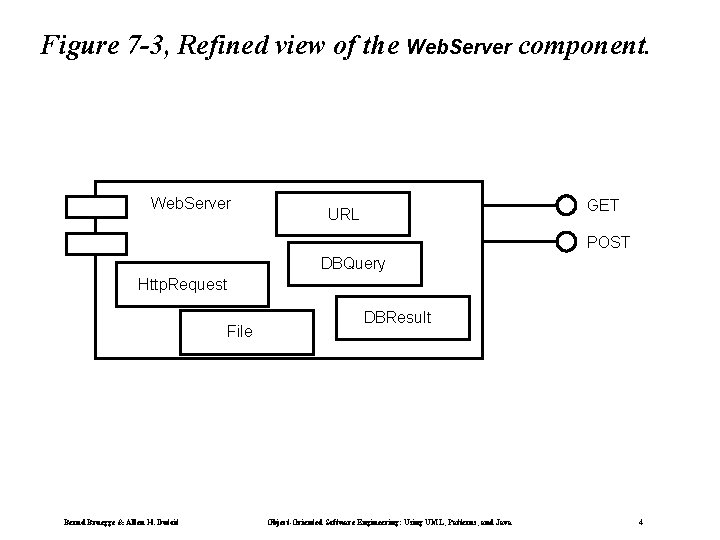
Figure 7 -3, Refined view of the Web. Server component. Web. Server GET URL POST DBQuery Http. Request File Bernd Bruegge & Allen H. Dutoit DBResult Object-Oriented Software Engineering: Using UML, Patterns, and Java 4
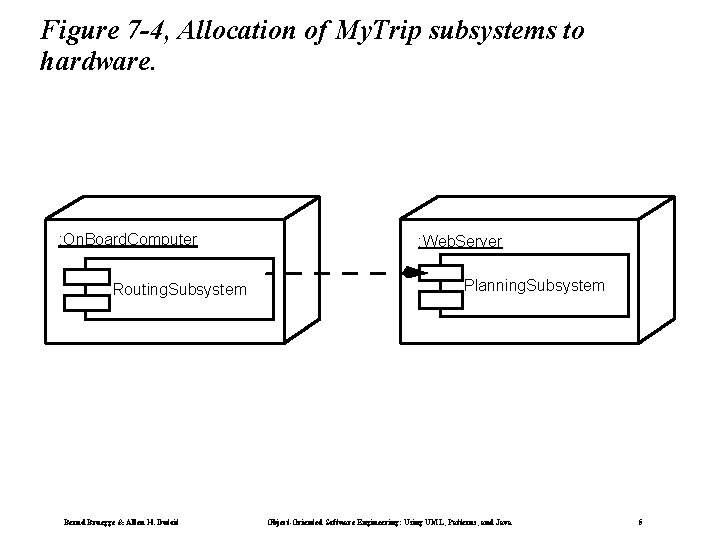
Figure 7 -4, Allocation of My. Trip subsystems to hardware. : On. Board. Computer Routing. Subsystem Bernd Bruegge & Allen H. Dutoit : Web. Server Planning. Subsystem Object-Oriented Software Engineering: Using UML, Patterns, and Java 5
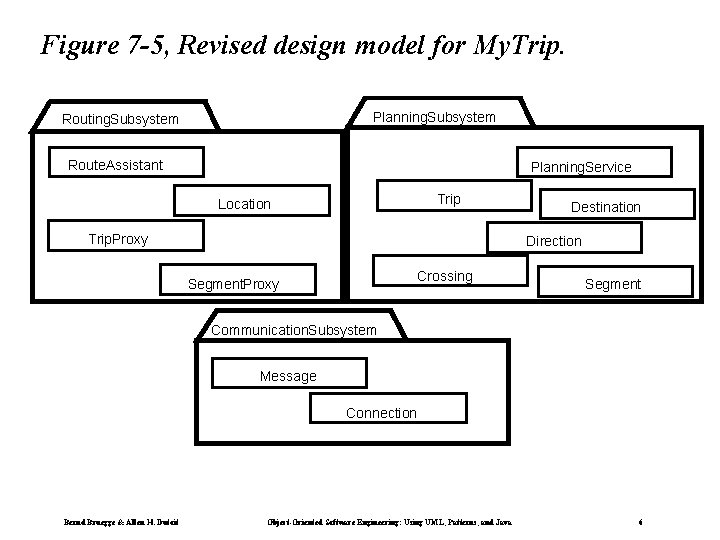
Figure 7 -5, Revised design model for My. Trip. Planning. Subsystem Route. Assistant Planning. Service Trip Location Trip. Proxy Destination Direction Crossing Segment. Proxy Segment Communication. Subsystem Message Connection Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 6
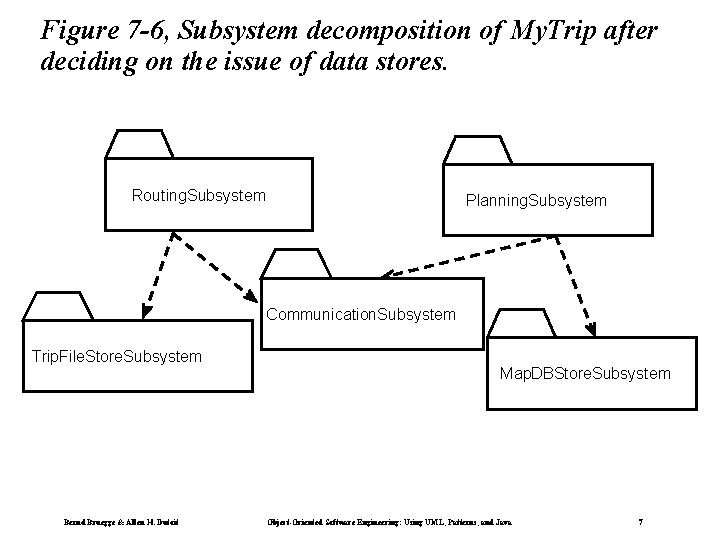
Figure 7 -6, Subsystem decomposition of My. Trip after deciding on the issue of data stores. Routing. Subsystem Planning. Subsystem Communication. Subsystem Trip. File. Store. Subsystem Bernd Bruegge & Allen H. Dutoit Map. DBStore. Subsystem Object-Oriented Software Engineering: Using UML, Patterns, and Java 7

Figure 7 -8, Packet filtering firewall: a filter, located at the router, allows or denies individual packets based on header information, such as source and destination. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 8
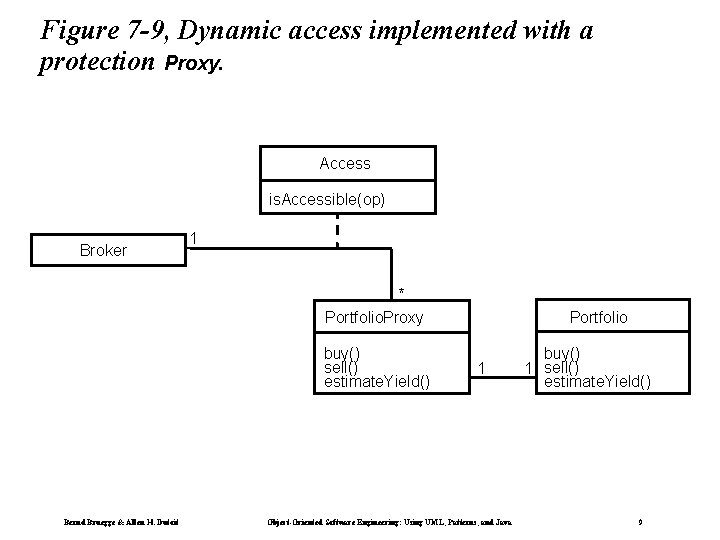
Figure 7 -9, Dynamic access implemented with a protection Proxy. Access is. Accessible(op) Broker 1 * Portfolio. Proxy buy() sell() estimate. Yield() Bernd Bruegge & Allen H. Dutoit Portfolio 1 Object-Oriented Software Engineering: Using UML, Patterns, and Java buy() 1 sell() estimate. Yield() 9
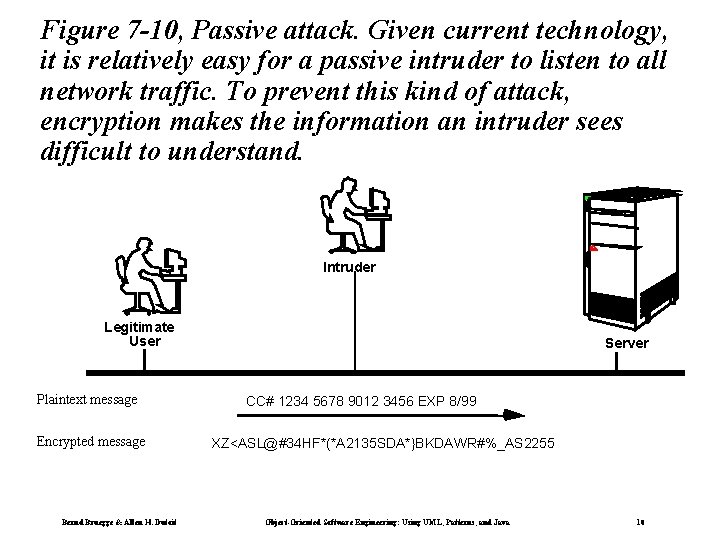
Figure 7 -10, Passive attack. Given current technology, it is relatively easy for a passive intruder to listen to all network traffic. To prevent this kind of attack, encryption makes the information an intruder sees difficult to understand. Intruder Legitimate User Plaintext message Encrypted message Bernd Bruegge & Allen H. Dutoit Server CC# 1234 5678 9012 3456 EXP 8/99 XZ<ASL@#34 HF*(*A 2135 SDA*}BKDAWR#%_AS 2255 Object-Oriented Software Engineering: Using UML, Patterns, and Java 10
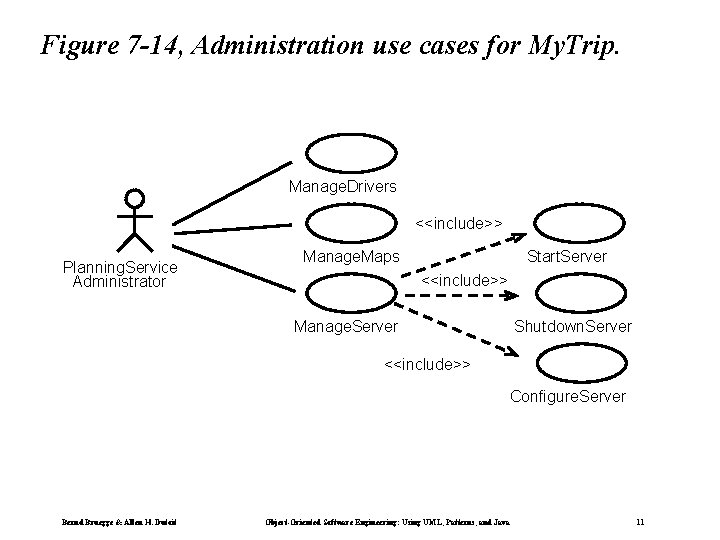
Figure 7 -14, Administration use cases for My. Trip. Manage. Drivers <<include>> Planning. Service Administrator Manage. Maps Start. Server <<include>> Manage. Server Shutdown. Server <<include>> Configure. Server Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 11
Figure 7 -18, ARENA subsystem decomposition, game organization part. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 12
Figure 7 -19, ARENA subsystem decomposition, game playing part. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 13
Figure 7 -20, ARENA hardware/software mapping. Bernd Bruegge & Allen H. Dutoit Object-Oriented Software Engineering: Using UML, Patterns, and Java 14
- Slides: 14