Using Trapdoor Permutations in a Complete Subtree Method
Using Trapdoor Permutations in a Complete Subtree Method for Boradcast Encryption Ryo Nojima, and Yuichi Kaji IEICE Transaction on Fundamentals, VOL. E 88 -A, NO. 2, pp. 568 -574, Feb 2005 Yu-Wei Su

Outline ● Introduction ● Complete Subtree Method ● Using Trapdoor Permutation ● Conclusions
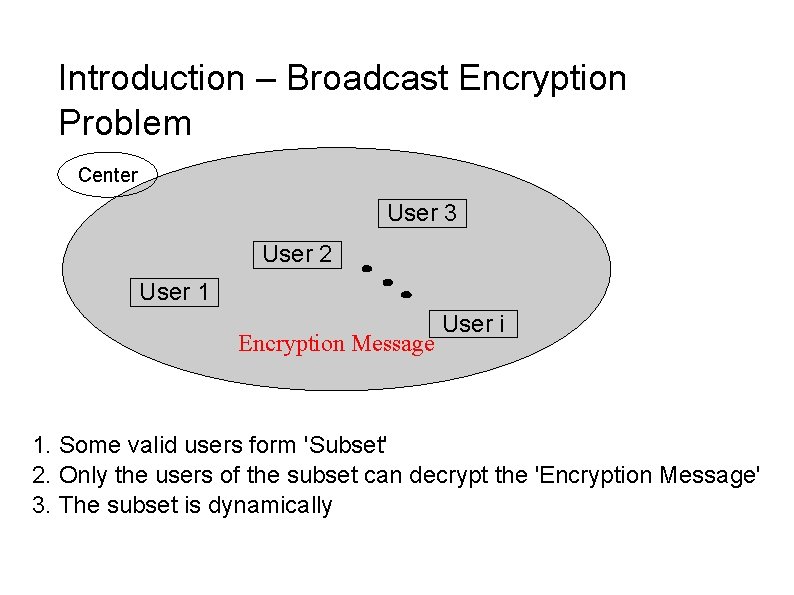
Introduction – Broadcast Encryption Problem Center User 3 User 2 User 1 Encryption Message User i 1. Some valid users form 'Subset' 2. Only the users of the subset can decrypt the 'Encryption Message' 3. The subset is dynamically
Complete Subtree Method (1/4) ● ● ● D. Naor, M. Naor, and J. B. Lotspiech, "Revocation and Tracing Schemes for Stateless Reveivers, " CRYPTO'01, LNCS 2139, pp. 41 -62, Springer Verlag, 2001 Binary tree structure used Symmetric key encryption scheme
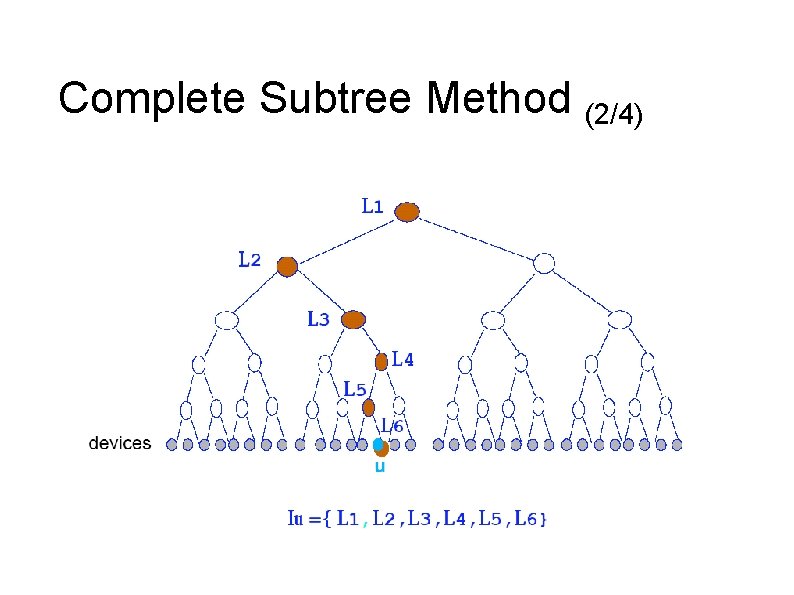
Complete Subtree Method (2/4)
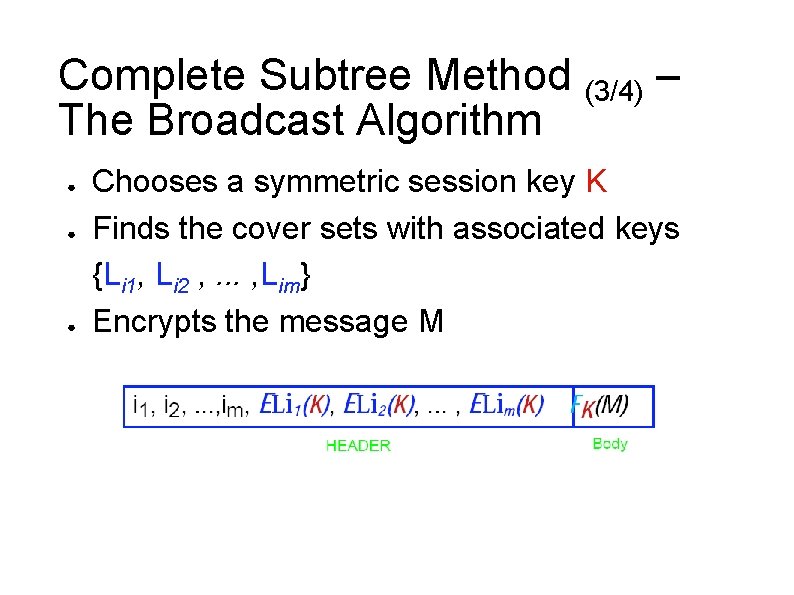
Complete Subtree Method (3/4) – The Broadcast Algorithm ● ● ● Chooses a symmetric session key K Finds the cover sets with associated keys {Li 1, Li 2 , . . . , Lim} Encrypts the message M
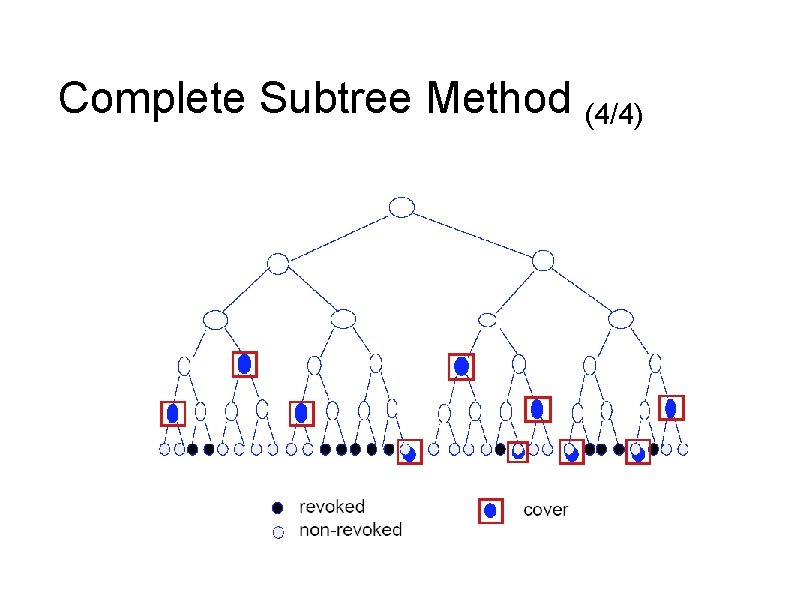
Complete Subtree Method (4/4)
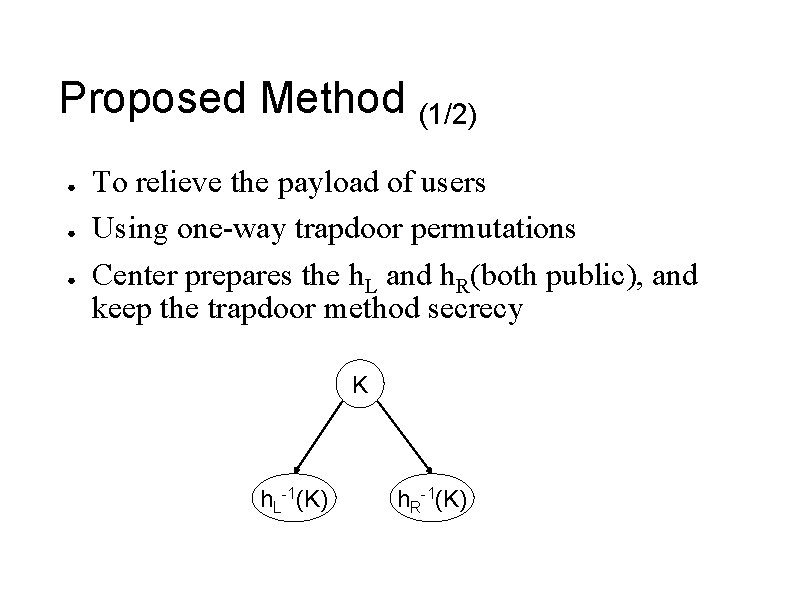
Proposed Method (1/2) ● ● ● To relieve the payload of users Using one-way trapdoor permutations Center prepares the h. L and h. R(both public), and keep the trapdoor method secrecy K h. L-1(K) h. R-1(K)
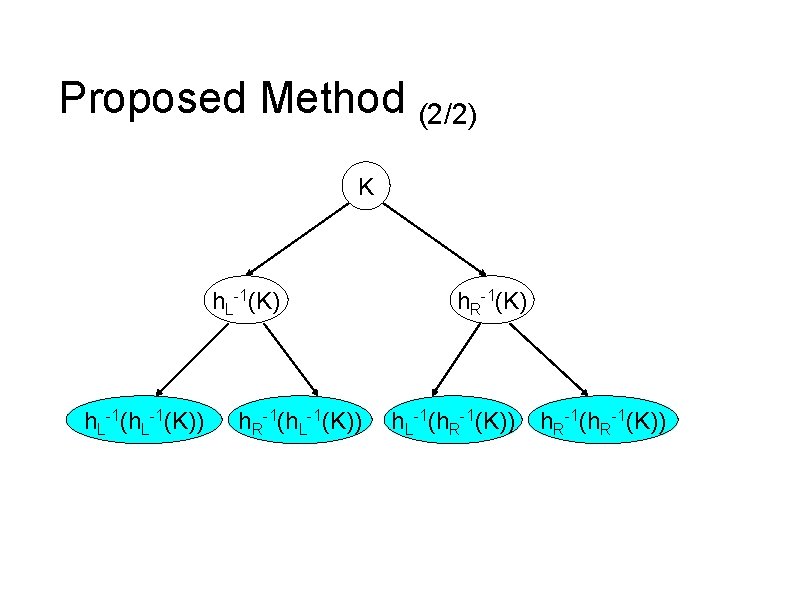
Proposed Method (2/2) K h. L-1(K)) h. R-1(h. L-1(K)) h. R-1(K) h. L-1(h. R-1(K))

Conclusions ● ● Simple idea Not scalable Make carefully choice of the one-way trapdoor permutations Must avoid h. R(h. L(x)) = h. L(h. R(x))
- Slides: 10