Using Crypto in RDBMS Pg Day ru 2016

Using Crypto in RDBMS Pg. Day. ru – 2016 Saint-Petersburg July 7 -8, 2016 Dmitry Belyavskiy, Technical Centre of Internet
You have data! 2 ways of attack – 2 ways of protection: • The attacker may steal data • The attacker may modify data You want to protect data Rule 1: Do not invent your own crypto!
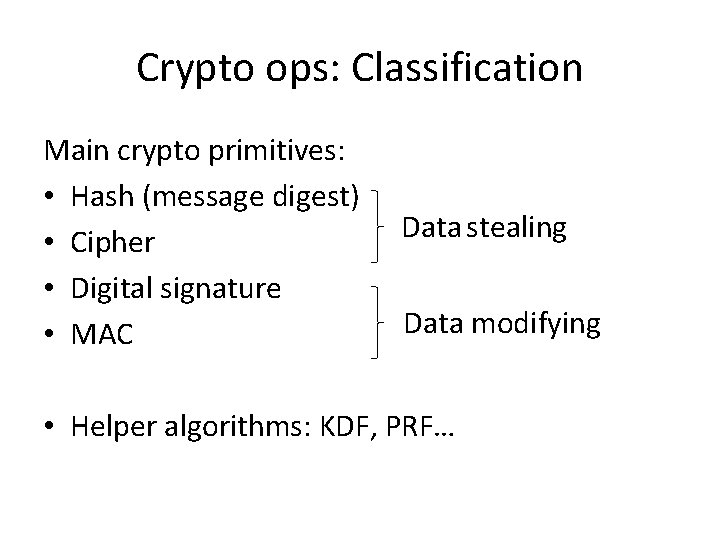
Crypto ops: Classification Main crypto primitives: • Hash (message digest) • Cipher • Digital signature • MAC Data stealing Data modifying • Helper algorithms: KDF, PRF…

Hash • Any data => fixed-length data – Non-revertible – Hard to find pre-image – Hard to find collision • Algorithms: MD 5, SHA 1, SHA 2, SHA 3… – Length: 128 -512 bits
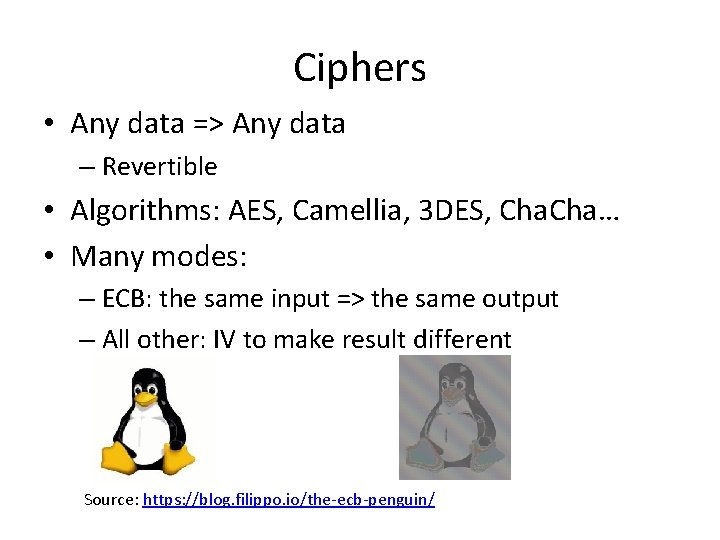
Ciphers • Any data => Any data – Revertible • Algorithms: AES, Camellia, 3 DES, Cha… • Many modes: – ECB: the same input => the same output – All other: IV to make result different Source: https: //blog. filippo. io/the-ecb-penguin/
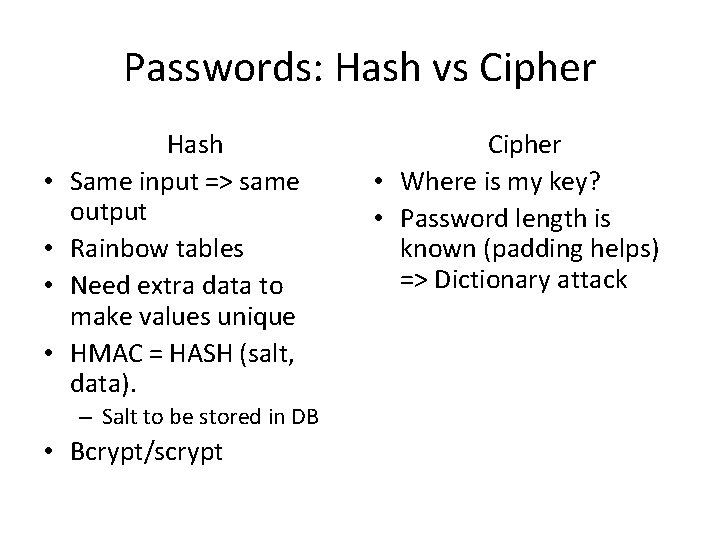
Passwords: Hash vs Cipher • • Hash Same input => same output Rainbow tables Need extra data to make values unique HMAC = HASH (salt, data). – Salt to be stored in DB • Bcrypt/scrypt Cipher • Where is my key? • Password length is known (padding helps) => Dictionary attack
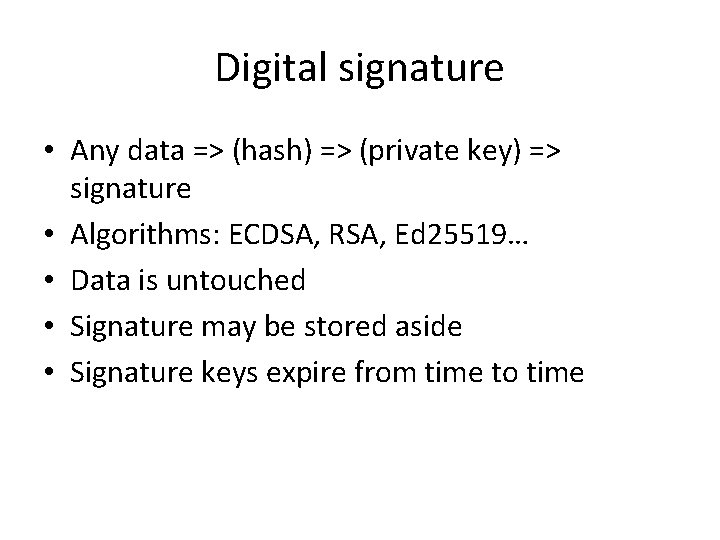
Digital signature • Any data => (hash) => (private key) => signature • Algorithms: ECDSA, RSA, Ed 25519… • Data is untouched • Signature may be stored aside • Signature keys expire from time to time

What do we protect? • Threat model – Protect traffic to database? Enable TLS! – Protect data in DB? Think about encrypted FS. – Postgre. SQL: patches to encipher the DB itself. • Long ago: http: //archives. postgresql. org/pgsql-hackers/201110/msg 01213. php • New: http: //www. cybertec. at/2016/06/postgresql-instance-levelencryption/ – Some parts of data? • • Where is the key? No search. No ORDER BY. At least now… Encryption for the DB owner – S/MIME, CMS… – Replication && backups! • http: //evol-monkey. blogspot. ru/2015/10/postgresql-94 -streamingreplication. html

Crypto implementation in Postgre. SQL • Pgcrypto https: //www. postgresql. org/docs/current/static/pgcrypto. html – Can use Open. SSL or not – PGP operations – crypt/gen_salt for storing passwords – Low-level operations • Some low-level crypto primitives (MD 5, SHA 1) are built-in.

To be done • Property-preserving encryption • Homomorphic encryption • Format-preserving encryption

Property-preserving encryption A B => Encrypt(A) Encrypt(B) • Description: – https: //css. csail. mit. edu/cryptdb/ – http: //research. microsoft. com/en-us/projects/cipherbase/ • Analysis: – http: //bristolcrypto. blogspot. co. at/2015/10/inference-attacks-onproperty. html – http: //outsourcedbits. org/2015/09/07/attacking-encrypted-databasesystems/

Homomorphic encryption Encrypt (AVG(A, B, C…)) = AVG(Encrypt(A), Encrypt(B), Encrypt(C)…) • Privacy to rule them all! – http: //research. microsoft. com/apps/pubs/default. aspx? id=148825 – http: //research. microsoft. com/apps/pubs/default. aspx? id=258435 – http: //research. microsoft. com/pubs/258435/Man ual. HEv 2. pdf

Format-preserving encryption Is the phone, SSN, or credit card encrypted or not? No changes to database schema! • NIST: Recommendation for Block Cipher Modes of Operation: Methods for Format-Preserving Encryption http: //nvlpubs. nist. gov/nistpubs/Special. Publicati ons/NIST. SP. 800 -38 G. pdf https: //app. box. com/shared/static/tvc 6 cgfyswdo cghv 3 cnffu 32 w 3 jndiu 9. pdf

Last but not least • PCI-DSS Compliance • The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes https: //wiki. postgresql. org/images/2/24/Achieving_ PCI_Compliace_Pg. Conf. NYC 2014. pdf
Questions? beldmit@tcinet. ru
- Slides: 15