Using COTS Routers for Lawful Intercept NetEDU Annual


- Slides: 14

Using COTS Routers for Lawful Intercept Net@EDU Annual Member Meeting February 8, 2006 Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1

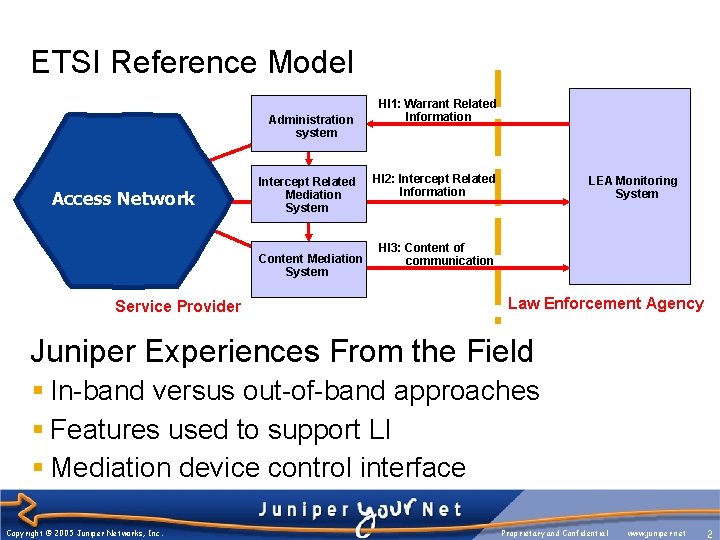
ETSI Reference Model Administration system Access Network Intercept Related Mediation System Content Mediation System Service Provider HI 1: Warrant Related Information HI 2: Intercept Related Information LEA Monitoring System HI 3: Content of communication Law Enforcement Agency Juniper Experiences From the Field § In-band versus out-of-band approaches § Features used to support LI § Mediation device control interface Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 2

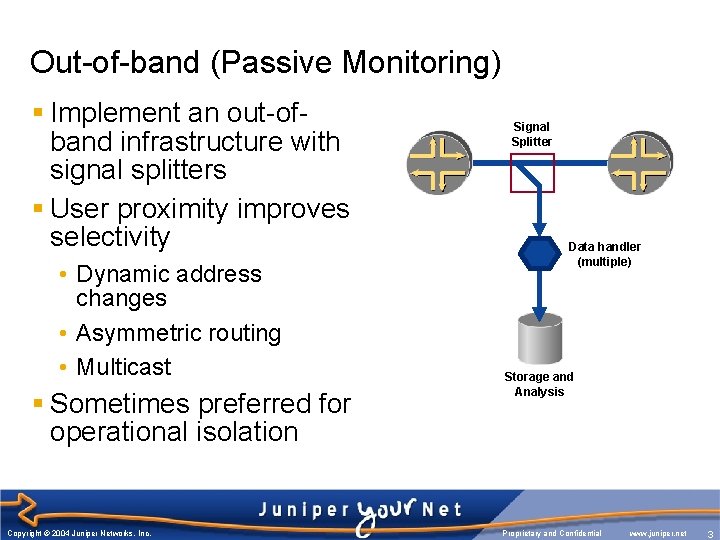
Out-of-band (Passive Monitoring) § Implement an out-ofband infrastructure with signal splitters § User proximity improves selectivity • Dynamic address changes • Asymmetric routing • Multicast § Sometimes preferred for operational isolation Copyright © 2004 Juniper Networks, Inc. Signal Splitter Data handler (multiple) Storage and Analysis Proprietary and Confidential www. juniper. net 3

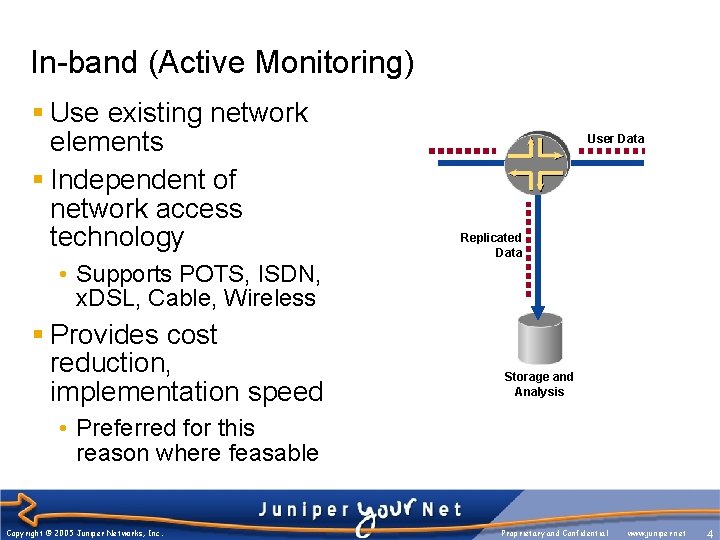
In-band (Active Monitoring) § Use existing network elements § Independent of network access technology User Data Replicated Data • Supports POTS, ISDN, x. DSL, Cable, Wireless § Provides cost reduction, implementation speed Storage and Analysis • Preferred for this reason where feasable Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 4

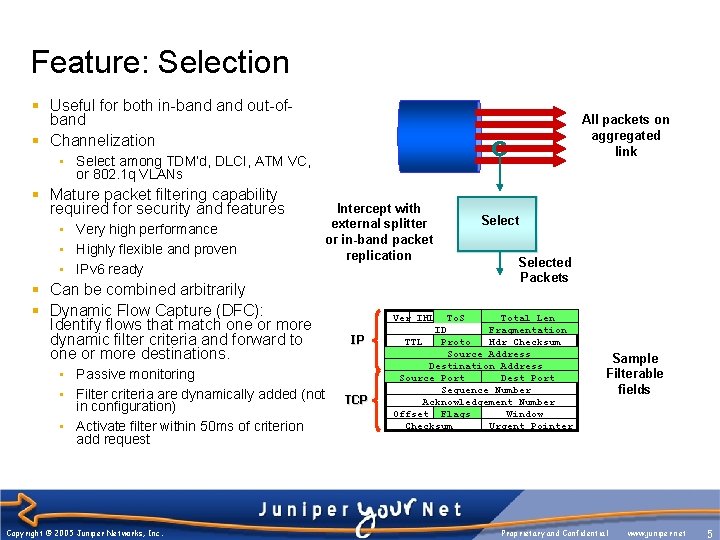
Feature: Selection § Useful for both in-band out-ofband § Channelization All packets on aggregated link • Select among TDM’d, DLCI, ATM VC, or 802. 1 q VLANs § Mature packet filtering capability required for security and features • Very high performance • Highly flexible and proven • IPv 6 ready Intercept with external splitter or in-band packet replication § Can be combined arbitrarily § Dynamic Flow Capture (DFC): Identify flows that match one or more dynamic filter criteria and forward to one or more destinations. • Passive monitoring • Filter criteria are dynamically added (not in configuration) • Activate filter within 50 ms of criterion add request Copyright © 2005 Juniper Networks, Inc. Selected Packets Ver IHL IP TCP To. S Total Len ID Fragmentation TTL Proto Hdr Checksum Source Address Destination Address Source Port Dest Port Sequence Number Acknowledgement Number Offset Flags Window Checksum Urgent Pointer Sample Filterable fields Proprietary and Confidential www. juniper. net 5

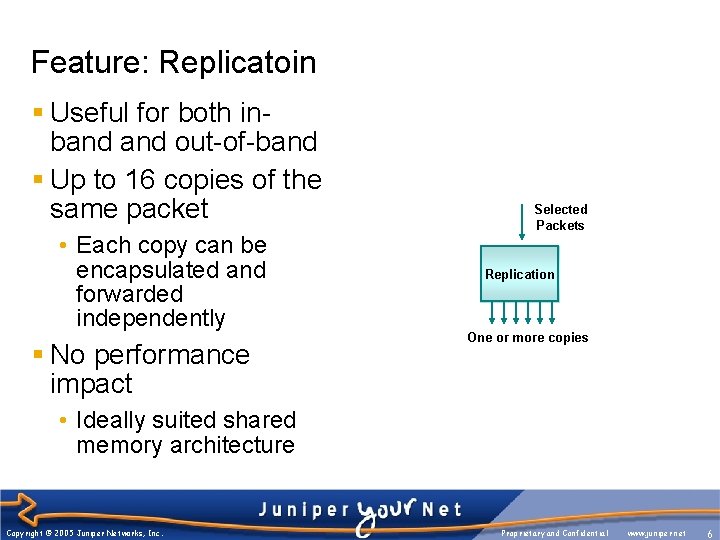
Feature: Replicatoin § Useful for both inband out-of-band § Up to 16 copies of the same packet • Each copy can be encapsulated and forwarded independently § No performance impact Selected Packets Replication One or more copies • Ideally suited shared memory architecture Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 6

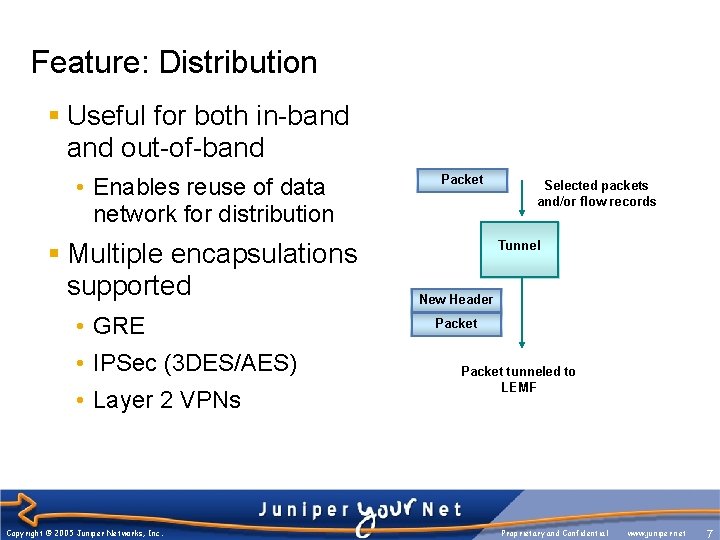
Feature: Distribution § Useful for both in-band out-of-band • Enables reuse of data network for distribution § Multiple encapsulations supported • GRE • IPSec (3 DES/AES) • Layer 2 VPNs Copyright © 2005 Juniper Networks, Inc. Packet Selected packets and/or flow records Tunnel New Header Packet tunneled to LEMF Proprietary and Confidential www. juniper. net 7

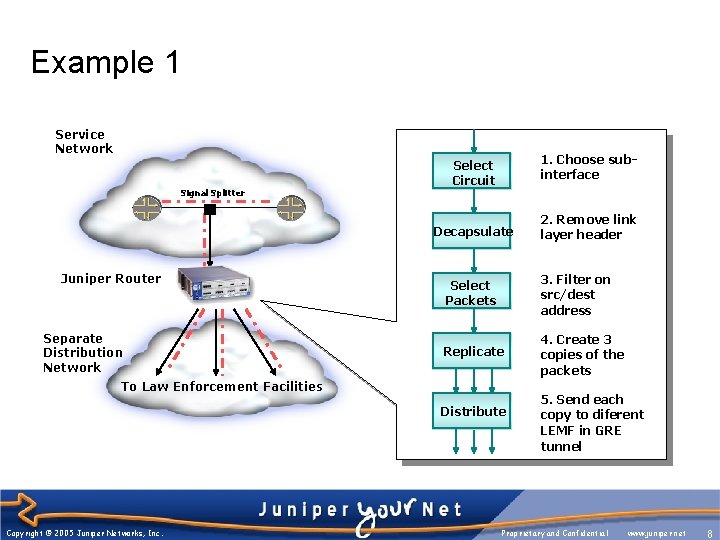
Example 1 Service Network Signal Splitter Juniper Router Separate Distribution Network Select Circuit 1. Choose subinterface Decapsulate 2. Remove link layer header Select Packets 3. Filter on src/dest address Replicate 4. Create 3 copies of the packets To Law Enforcement Facilities Distribute Copyright © 2005 Juniper Networks, Inc. 5. Send each copy to diferent LEMF in GRE tunnel Proprietary and Confidential www. juniper. net 8

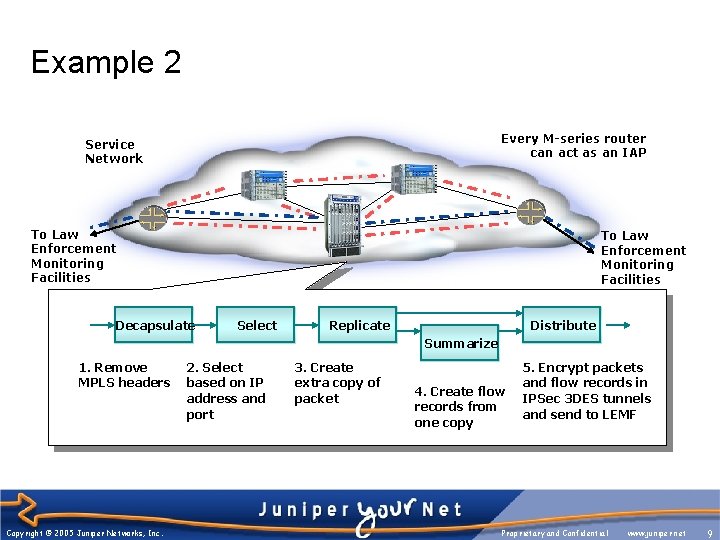
Example 2 Every M-series router can act as an IAP Service Network To Law Enforcement Monitoring Facilities Decapsulate Select Replicate Distribute Summarize 1. Remove MPLS headers Copyright © 2005 Juniper Networks, Inc. 2. Select based on IP address and port 3. Create extra copy of packet 4. Create flow records from one copy 5. Encrypt packets and flow records in IPSec 3 DES tunnels and send to LEMF Proprietary and Confidential www. juniper. net 9

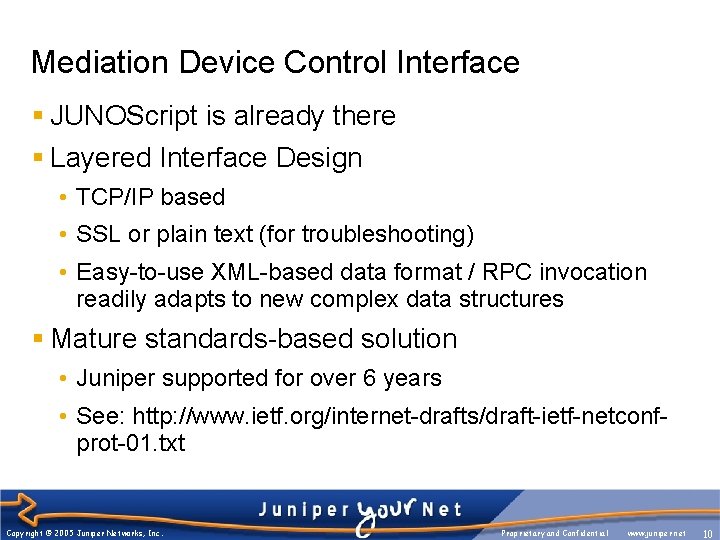
Mediation Device Control Interface § JUNOScript is already there § Layered Interface Design • TCP/IP based • SSL or plain text (for troubleshooting) • Easy-to-use XML-based data format / RPC invocation readily adapts to new complex data structures § Mature standards-based solution • Juniper supported for over 6 years • See: http: //www. ietf. org/internet-drafts/draft-ietf-netconfprot-01. txt Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10

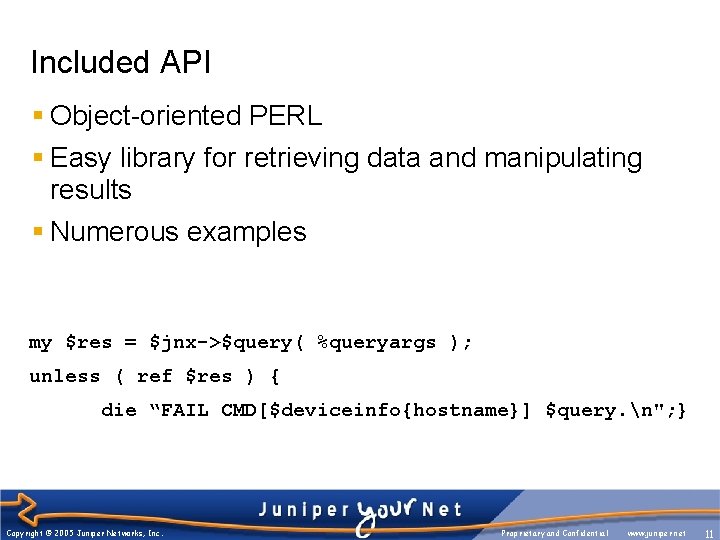
Included API § Object-oriented PERL § Easy library for retrieving data and manipulating results § Numerous examples my $res = $jnx->$query( %queryargs ); unless ( ref $res ) { die “FAIL CMD[$deviceinfo{hostname}] $query. n"; } Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 11

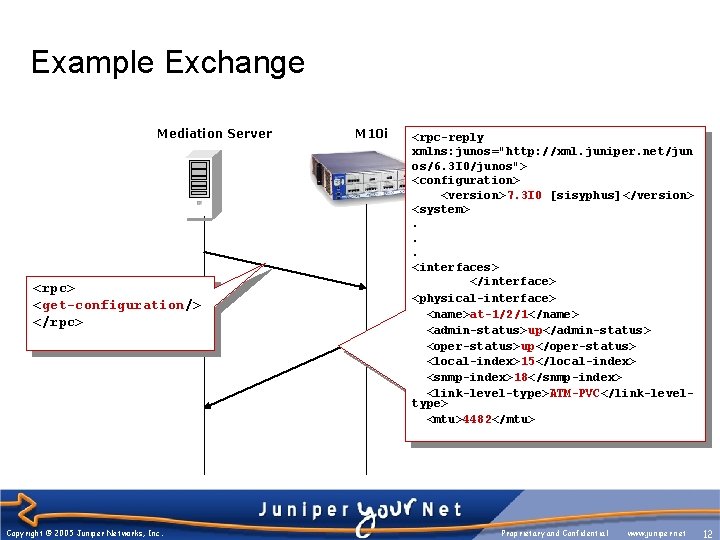
Example Exchange Mediation Server <rpc> <get-configuration/> </rpc> Copyright © 2005 Juniper Networks, Inc. M 10 i <rpc-reply xmlns: junos="http: //xml. juniper. net/jun os/6. 3 I 0/junos"> <configuration> <version>7. 3 I 0 [sisyphus]</version> <system>. . . <interfaces> </interface> <physical-interface> <name>at-1/2/1</name> <admin-status>up</admin-status> <oper-status>up</oper-status> <local-index>15</local-index> <snmp-index>18</snmp-index> <link-level-type>ATM-PVC</link-leveltype> <mtu>4482</mtu> Proprietary and Confidential www. juniper. net 12

Summary § Router based lawful intercept provides numerous advantages over dedicated hardware • Higher flexibility • Less time to implement and manage • Lower costs § Juniper E, M, and T series routers provide a set of functional building blocks to support any LI application § JUNOScript is well suited for a mediation interface Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 13

Ben Eater eater@juniper. net