User Datagram Protocol UDP Ch 23 Ameera Almasoud











- Slides: 30

User Datagram Protocol (UDP) Ch 23 Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 1

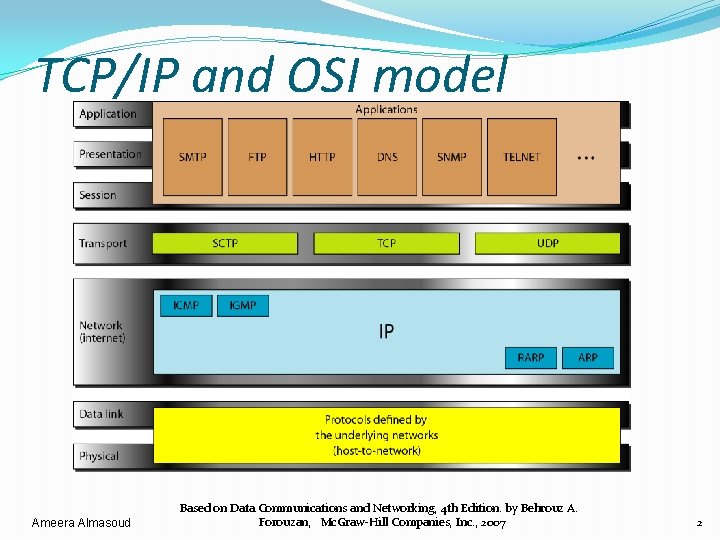
TCP/IP and OSI model Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 2

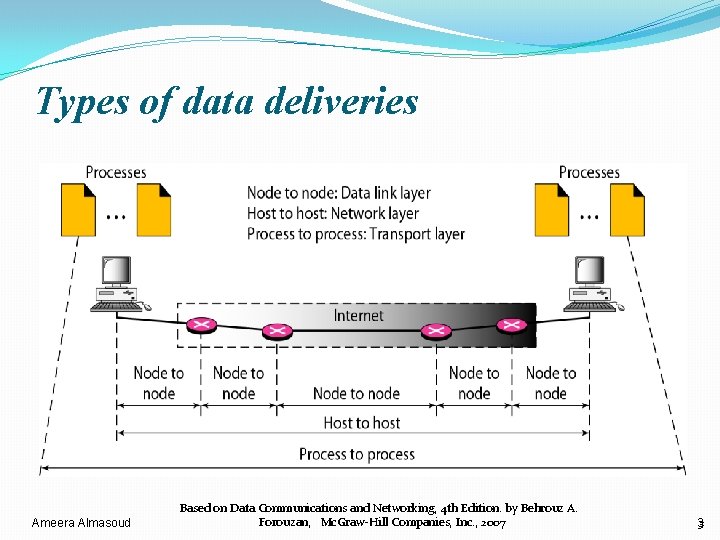
Types of data deliveries Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 3

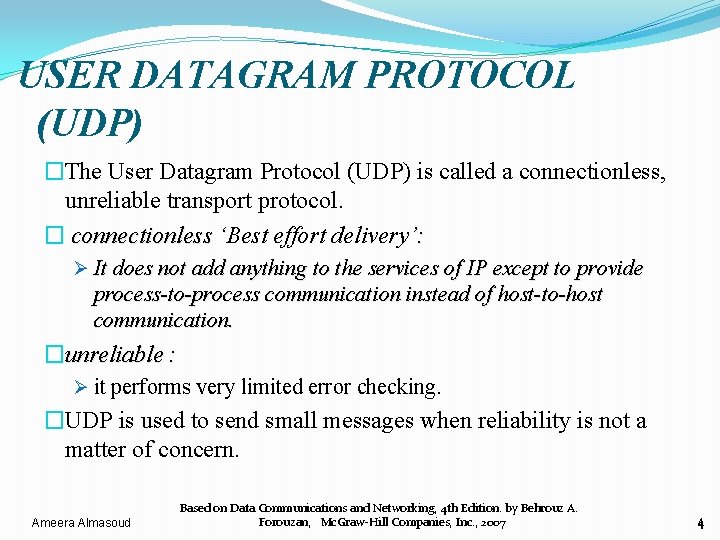
USER DATAGRAM PROTOCOL (UDP) �The User Datagram Protocol (UDP) is called a connectionless, unreliable transport protocol. � connectionless ‘Best effort delivery’: ‘ Ø It does not add anything to the services of IP except to provide process-to-process communication instead of host-to-host communication. �unreliable : Ø it performs very limited error checking. �UDP is used to send small messages when reliability is not a matter of concern. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 4

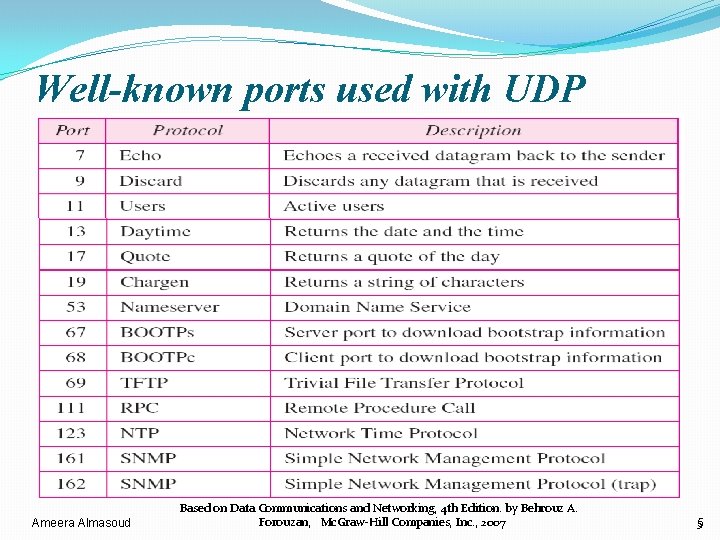
Well-known ports used with UDP Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 5

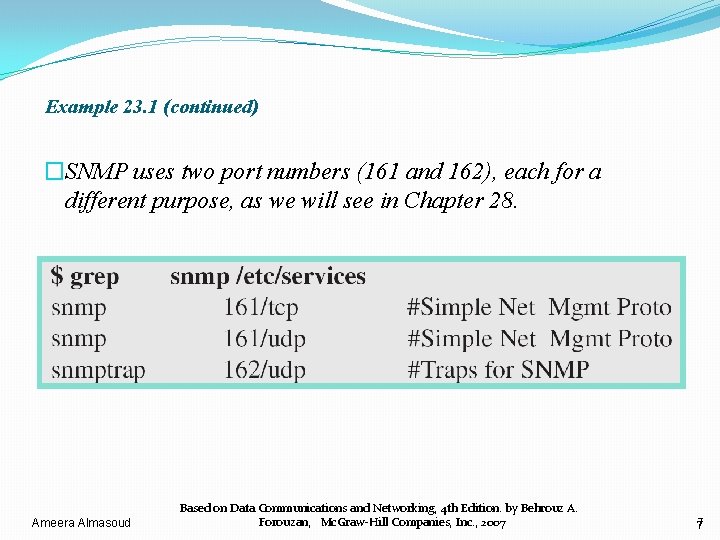
Example 23. 1 • In UNIX, the well-known ports are stored in a file called /etc/services. • Each line in this file gives the name of the server and the wellknown port number. • We can use the grep utility to extract the line corresponding to the desired application. • The following shows the port for FTP. Note that FTP can use port 21 with either UDP or TCP. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 6

Example 23. 1 (continued) �SNMP uses two port numbers (161 and 162), each for a different purpose, as we will see in Chapter 28. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 7

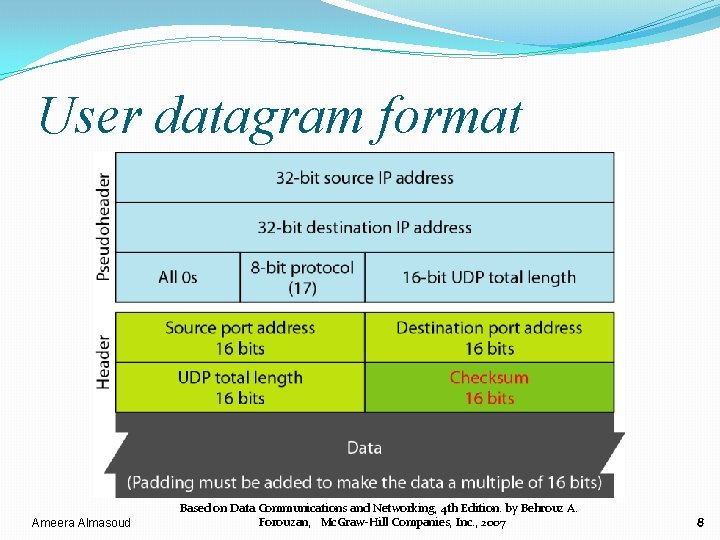
User datagram format Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 8

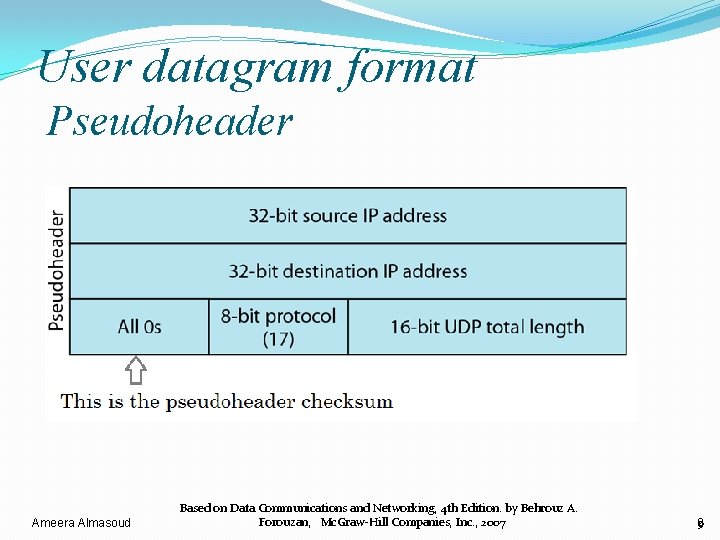
User datagram format Pseudoheader Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 9

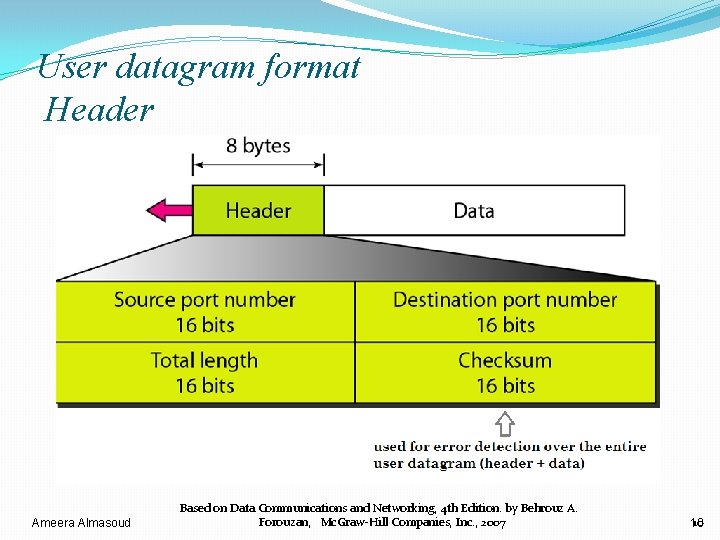
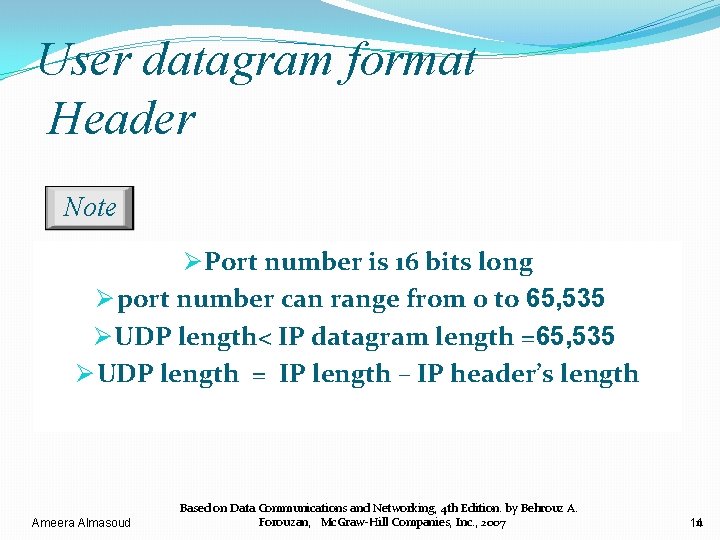
User datagram format Header Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 10 10

User datagram format Header Note Ø Port number is 16 bits long Ø port number can range from 0 to 65, 535 Ø UDP length< IP datagram length =65, 535 Ø UDP length = IP length – IP header’s length Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 11 11

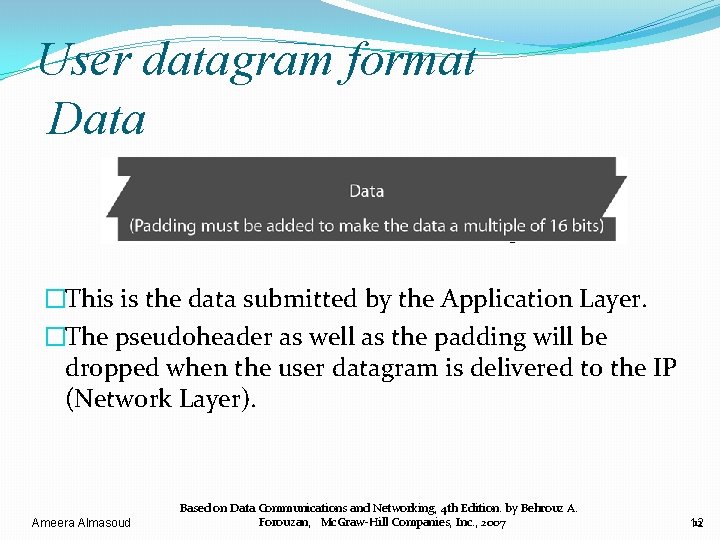
User datagram format Data �This is the data submitted by the Application Layer. �The pseudoheader as well as the padding will be dropped when the user datagram is delivered to the IP (Network Layer). Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 12 12

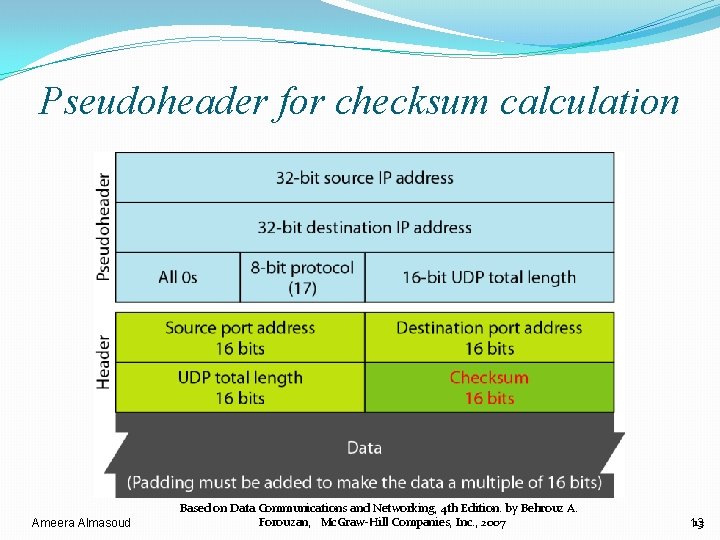
Pseudoheader for checksum calculation Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 13 13

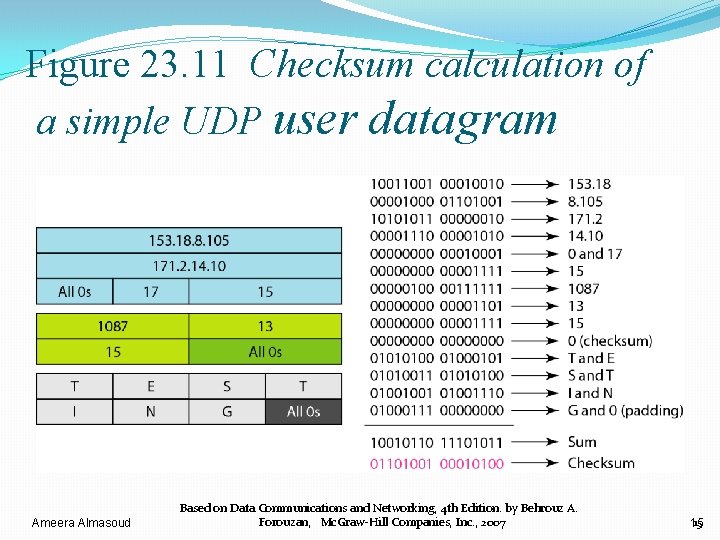
Example 23. 2 �Figure 23. 11 shows the checksum calculation for a very small user datagram with only 7 bytes of data. �Because the number of bytes of data is odd, padding is added for checksum calculation. �The pseudoheader as well as the padding will be dropped when the user datagram is delivered to IP. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 14 14

Figure 23. 11 Checksum calculation of a simple UDP user datagram Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 15 15

CIRCUIT-SWITCHED NETWORKS “THREE PHASES” �Communication in circuit-switched networks requires 3 phases: ü ü ü Setup Phase. Data Transfer Phase. Teardown Phase. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 16 16

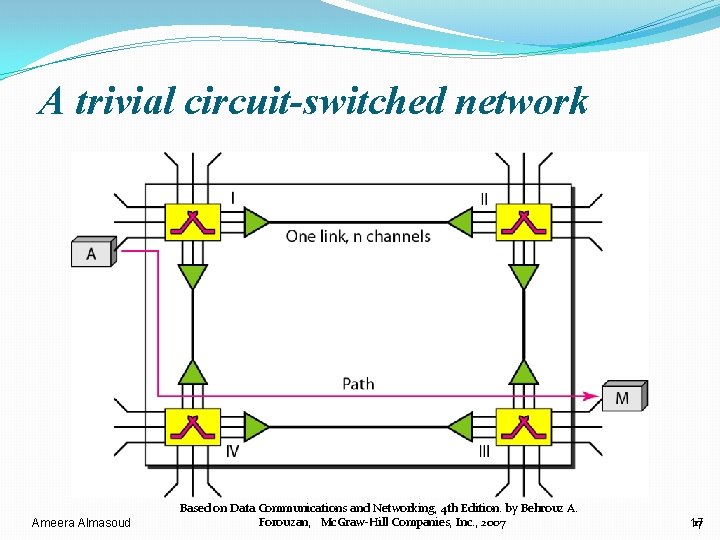
A trivial circuit-switched network Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 17 17

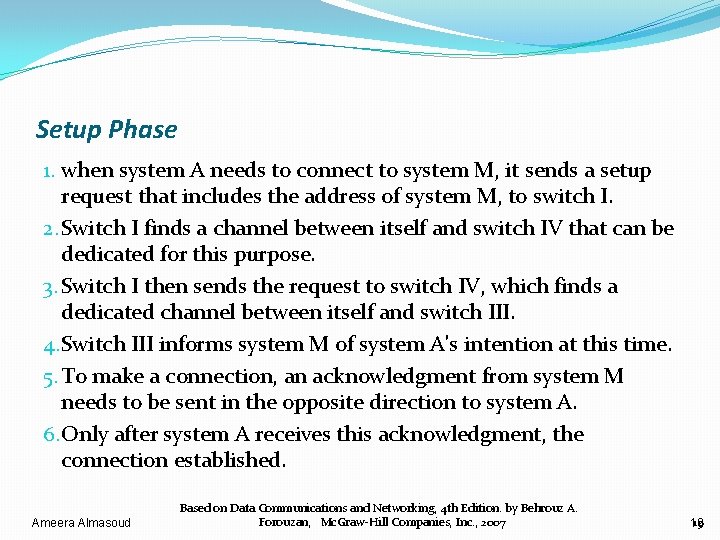
Setup Phase �Before the two parties can communicate, a dedicated circuit (combination of channels in links) needs to be established. �The end systems are normally connected through dedicated lines to the switches. Ø so connection setup means creating dedicated channels between the switches. �Each switch is provided with a table. Ø an entry is created when the setup phase is completed. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 18 18

Setup Phase 1. when system A needs to connect to system M, it sends a setup request that includes the address of system M, to switch I. 2. Switch I finds a channel between itself and switch IV that can be dedicated for this purpose. 3. Switch I then sends the request to switch IV, which finds a dedicated channel between itself and switch III. 4. Switch III informs system M of system A's intention at this time. 5. To make a connection, an acknowledgment from system M needs to be sent in the opposite direction to system A. 6. Only after system A receives this acknowledgment, the connection established. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 19 19

Data Transfer Phase �After the establishment of the dedicated circuit (channels), the two parties can transfer data. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 20

Teardown Phase �When one of the parties needs to disconnect, a signal is sent to each switch to release the resources. �These resources include: channels, switch buffers, switch input/output ports. �When the teardown phase is over, the corresponding entry is deleted from the switching table. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 21 21

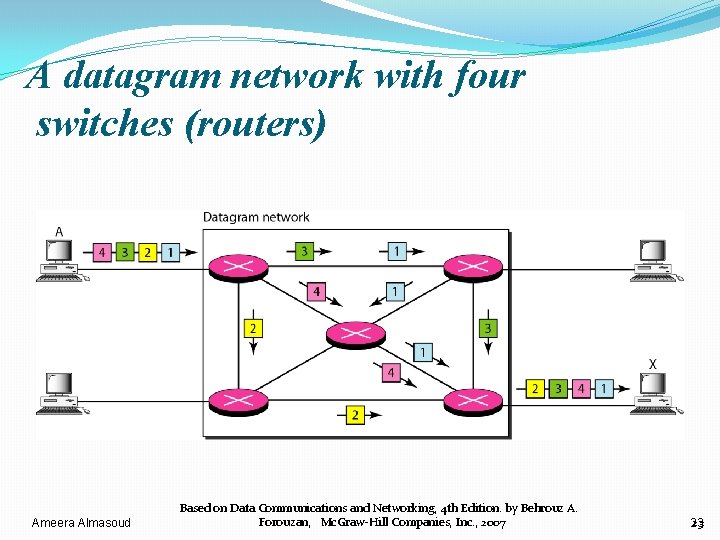
DATAGRAM NETWORKS “Routing ” �If the message is going to pass through a packet switched network, it needs to be divided into packets of fixed or variable size. �Each packet is treated independently of all others. �Packets of the same message may go through different paths to reach the same destination Ø This is because links may be busy in carrying packets from other messages. �datagrams of the same message may arrive at the destination with different delays and out of order. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 22 22

A datagram network with four switches (routers) Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 23 23

DATAGRAM NETWORKS “DATAGRAMS” �Packets may also be lost or dropped because of lack of resources. �It is the responsibility of an upper-layer protocol to reorder datagrams and to ask for losted datagrams Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 24

DATAGRAM NETWORKS /CONNECTIONLESS NETWORKS �The term “connectionless” means that the switch does not keep information about the connection state. �Each packet is treated the same by a switch regardless of its source or destination. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 25 25

UDP OPERATION �Connectionless Services. �Flow and Error Control. �Encapsulation and Decapsulation. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 26

UDP OPERATION Connectionless Services �UDP is connectionless Ø Datagrams are handled separately. Ø Datagrams can travel on different paths. Ø No path establishment between the source and destination. �UDP user datagrams are NOT numbered Ø UDP messages shouldn’t be divided. Ø UDP messages should fit in a SINGLE datagram. Ø Only processes sending short messages should use UDP. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 27 27

UDP OPERATION Flow and Error Control �There is no flow control Ø UDP is unreliable. Ø The receiver may overflow with incoming messages. �There is no error control Ø except for the “checksum” Ø The sender does not know if a message is lost Ø When the receiver detects an error through the checksum, the message is simply discarded. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 28

UDP OPERATION Encapsulation and Decapsulation. �To send a message from one process to another, the UDP protocol encapsulates and decapsulates messages in an IP datagram. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 29

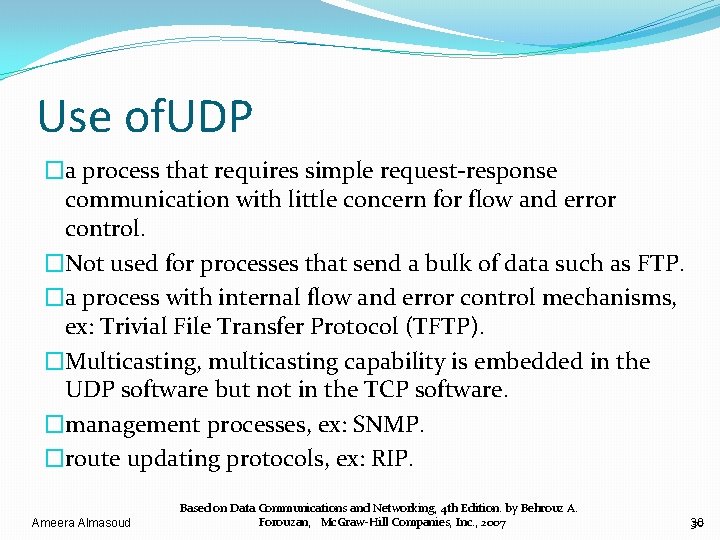
Use of. UDP �a process that requires simple request-response communication with little concern for flow and error control. �Not used for processes that send a bulk of data such as FTP. �a process with internal flow and error control mechanisms, ex: Trivial File Transfer Protocol (TFTP). �Multicasting, multicasting capability is embedded in the UDP software but not in the TCP software. �management processes, ex: SNMP. �route updating protocols, ex: RIP. Ameera Almasoud Based on Data Communications and Networking, 4 th Edition. by Behrouz A. Forouzan, Mc. Graw-Hill Companies, Inc. , 2007 30 30