Use of a Broken or Risky Cryptographic Algorithm
Sign up to view full document!
SIGN UP

Use of a Broken or Risky Cryptographic Algorithm System & Network Security Lab 석사 25기 유창훈 2013. 5. 16

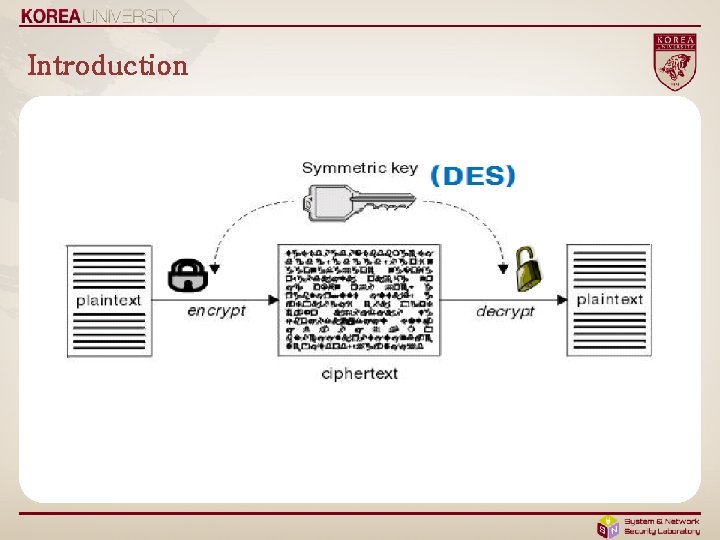
Introduction

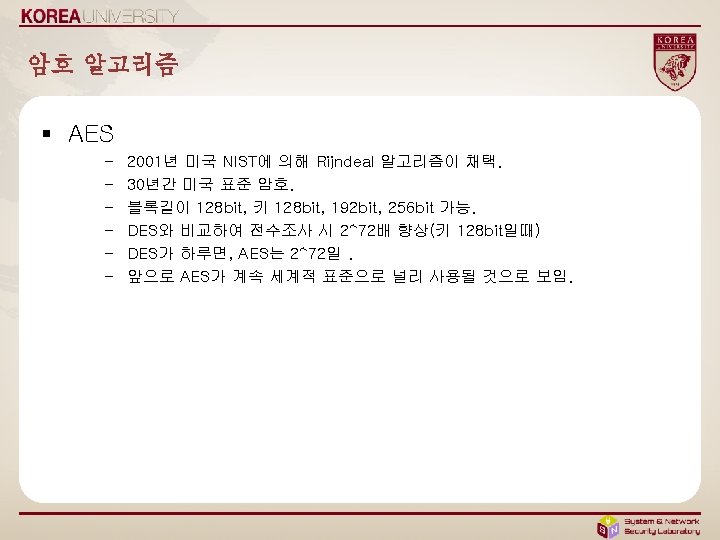
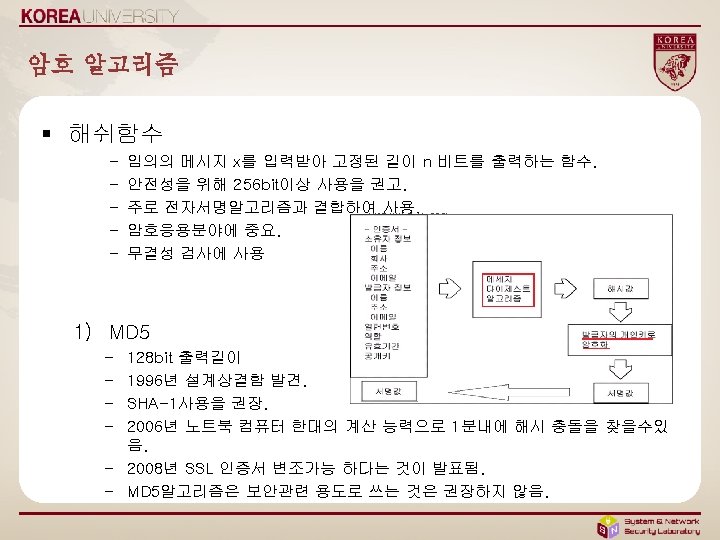
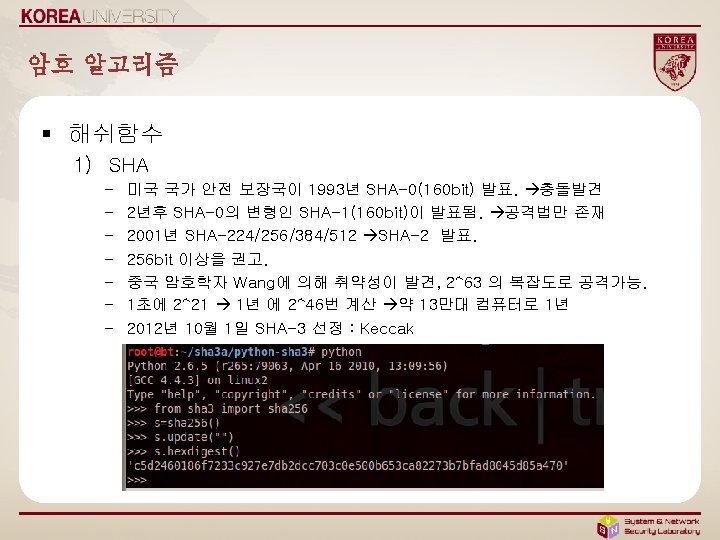
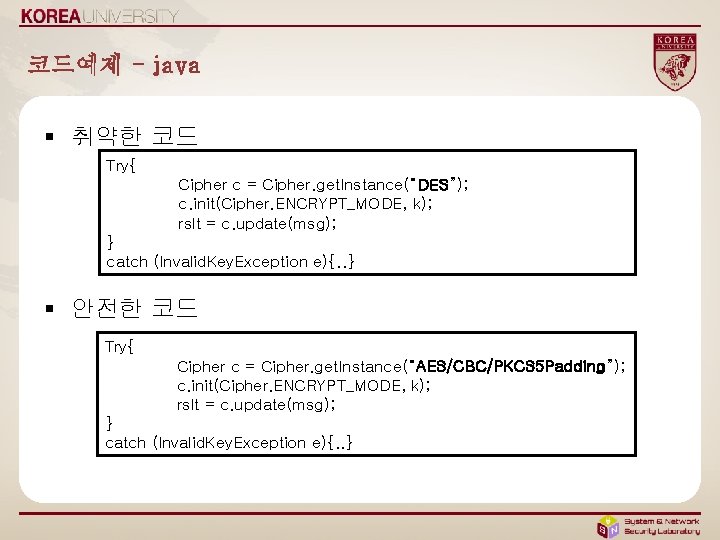
코드예제 - java § 취약한 코드 Try{ Cipher c = Cipher. get. Instance(“DES”); c. init(Cipher. ENCRYPT_MODE, k); rslt = c. update(msg); } catch (Invalid. Key. Exception e){. . } § 안전한 코드 Try{ Cipher c = Cipher. get. Instance(“AES/CBC/PKCS 5 Padding”); c. init(Cipher. ENCRYPT_MODE, k); rslt = c. update(msg); } catch (Invalid. Key. Exception e){. . }
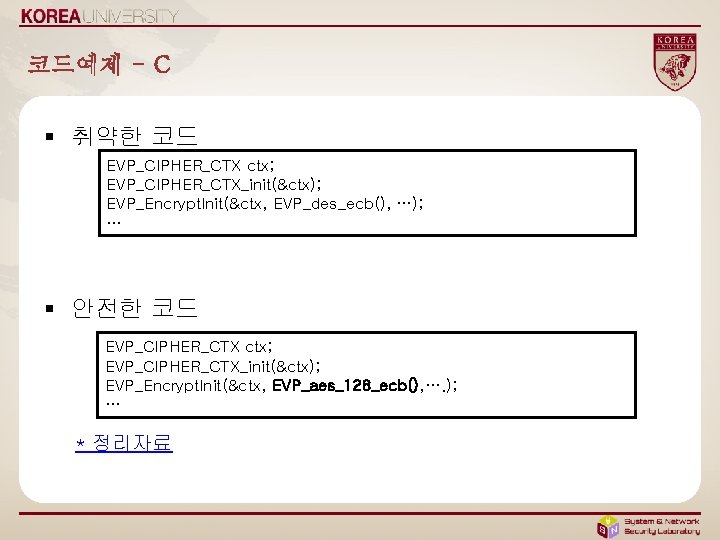
코드예제 - C § 취약한 코드 EVP_CIPHER_CTX ctx; EVP_CIPHER_CTX_init(&ctx); EVP_Encrypt. Init(&ctx, EVP_des_ecb(), …); … § 안전한 코드 EVP_CIPHER_CTX ctx; EVP_CIPHER_CTX_init(&ctx); EVP_Encrypt. Init(&ctx, EVP_aes_128_ecb(), …. ); … * 정리자료
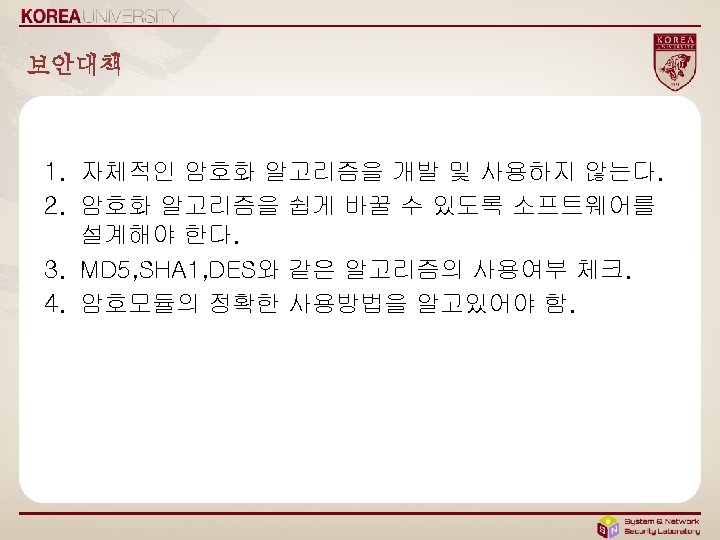

- Slides: 11