Update on UOCAVA Risk Assessment by UOCAVA Working

Update on UOCAVA Risk Assessment by UOCAVA Working Group Andrew Regenscheid National Institute of Standards and Technology http: //vote. nist. gov TGDC Meeting, December 2011

Outline n n n Background Risk assessment methodology Sources of data Status update on progress Next steps TGDC Meeting, December 2011 Page 2

Background n n All systems and processes have risks Current UOCAVA Vote-by-Mail (VBM) as baseline n n n We have implicitly accepted risks in the current UOCAVA voting process Director Carey has maintained future systems should be compared to the current system TGDC accepted task to develop a risk assessment on current UOCAVA processes TGDC Meeting, December 2011 Page 3

Charge n To describe risks in currently-used UOCAVA voting processes n n Vote by Mail (VBM) Electronic ballot delivery via e-mail, fax, and web sites Effort should facilitate comparisons between different types of risks Future efforts could look at remote electronic voting systems, once a system is defined TGDC Meeting, December 2011 Page 4

Risks From NIST SP 800 -30 rev 1: n Risk is a measure of the extent to which an entity is threatened by a potential circumstance or event, and is typically a function of: n n n The adverse impacts that would arise if the circumstance or event occurs; and The likelihood of occurrence A risk assessment is the process of identifying, prioritizing, and estimating information security risks TGDC Meeting, December 2011 Page 5
Methodology n n n Initial step: Define current UOCAVA voting processes Tailored methodology in NIST SP 80030 rev 1, Guide for Conducting Risk Assessments (draft) Major contents of risk assessment: n n n Threat event Vulnerability Threat source Impact Likelihood TGDC Meeting, December 2011 Page 6
Defining Current Processes (1) n n EAC whitepaper, UOCAVA Registration and Voting Processes, April 2011 Split UOCAVA Voting into 6 processes n n n Prepare and Submit Voter Registration Application Process Voter Registration Application Prepare and Deliver Blank Ballots Mark and Return Ballots Receive and Process Ballot Packets Count Ballots TGDC Meeting, December 2011 Page 7
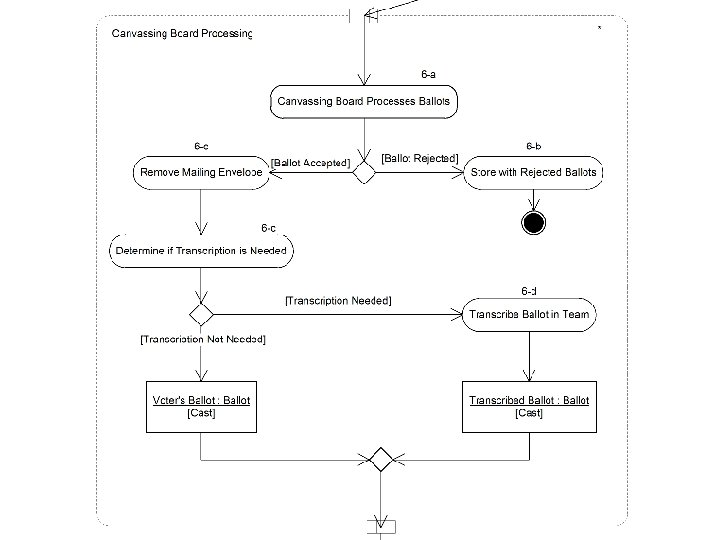
Defining Current Processes (2) n Each process could have several instantiations, e. g. , n n n For each process, we created flowcharts n n n Registration by mail, e-mail, fax, or web Ballot delivery by mail, e-mail, fax, or web UML 2 Activity Diagrams Currently only vote-by-mail diagrams are completed Activities in each diagram are tagged with an identifier TGDC Meeting, December 2011 Page 8

TGDC Meeting, December 2011 Page 9
TGDC Meeting, December 2011 Page 10
TGDC Meeting, December 2011 Page 11

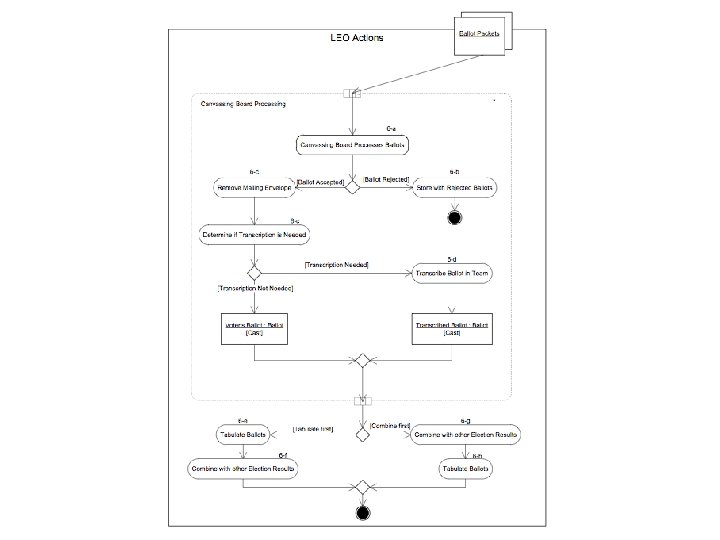
Risk Assessment n n n Diagrams represent the target system of the risk assessment Risks may be present at any step (i. e. , activity) of the processes To describe the risk, we need to identify the: n n n Threat event Vulnerability Threat source Impact Likelihood TGDC Meeting, December 2011 Page 12

Threat Event n n A threat event is any event or situation that has the potential for causing undesirable consequences or impact Undesirable impacts violate one of the following goals: n n n Correctness of election result Protect voter privacy Maintain public confidence in election Example: Blank Ballot is lost or delayed en route to voter A threat event involves the exploitation of a vulnerability by a threat source TGDC Meeting, December 2011 Page 13

Vulnerability n n A vulnerability is an inherent weakness in a system, security procedures, internal controls, or implementation that could be exploited by a threat source Example: Foreign and domestic mail services are not fully reliable TGDC Meeting, December 2011 Page 14

Threat Sources (1) n n A threat source is the adversary intending to exploit vulnerability, or it is a situation that may accidentally or incidentally exploit a vulnerability Types of threat sources n n Adversarial attacks Human errors of omission or commission Structural failures of jurisdiction-controlled resources Natural and man-made disasters, accidents, and failures beyond the control of the jurisdiction TGDC Meeting, December 2011 Page 15

Threat Sources (2) n Examples of threat sources: n Adversarial n n n Hostile individuals and groups Disgruntled election workers Non-adversarial n n Voters Election officials Postal agencies Natural disasters TGDC Meeting, December 2011 Page 16

Impact n n Impact is a measure of the harm done by the occurrence of a threat event Qualitative measure of two factors: Impact Severity n How “bad” is the event? n Low/Moderate/High TGDC Meeting, December 2011 Scale n How many voters/ballots are impacted? n Small/Large scale Page 17

Likelihood n n The likelihood of occurrence of a threat is an estimate of the likelihood that a threat event will occur and result in an adverse impact UOCAVA voting processes have different types of risks, e. g. , n n n System-wide risks that rarely occur Transactional risks that occur frequently We replace likelihood with Occurrences; that is, how often a given threat event is likely to occur in a given state during a Presidential election year TGDC Meeting, December 2011 Page 18

Occurrences n We have a 4 -point qualitative scale for estimating occurrences Uncommon Common TGDC Meeting, December 2011 (1) Rare The event is very unlikely to occur (2) Unlikely The event regularly occurs in elections, but is unlikely to occur in any given election (3) Infrequent The event is expected to occur a few times during an election (4) Frequent The event is expected to occur many times during an election Page 19
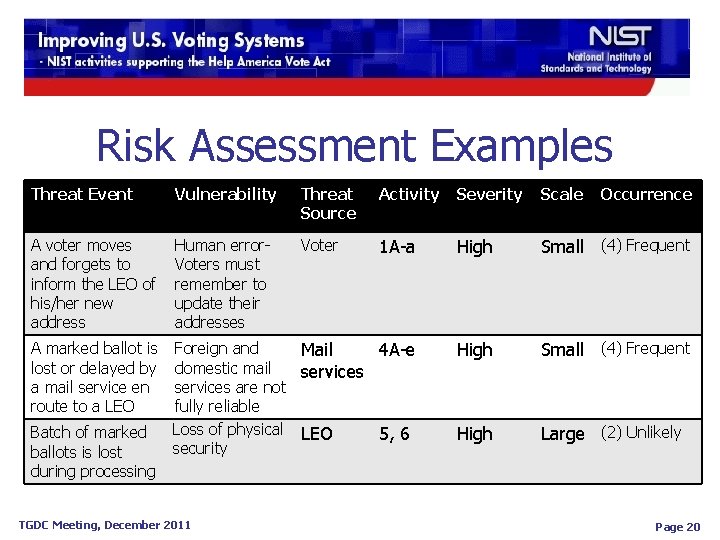
Risk Assessment Examples Threat Event Vulnerability Threat Source Activity Severity Scale A voter moves and forgets to inform the LEO of his/her new address Human error. Voters must remember to update their addresses Voter 1 A-a High Small (4) Frequent A marked ballot is lost or delayed by a mail service en route to a LEO Foreign and Mail 4 A-e domestic mail services are not fully reliable Loss of physical LEO 5, 6 security High Small (4) Frequent High Large (2) Unlikely Batch of marked ballots is lost during processing TGDC Meeting, December 2011 Occurrence Page 20

Data Sources n Government reports n n Other reports n n n 2010 EAC UOCAVA Report 2010 FVAP Post Election Survey 2010 Analysis of the Military Postal System Compliance with the MOVE Act Pew Overseas Vote Foundation Experiences/Anecdotal reports from Election Officials TGDC Meeting, December 2011 Page 21

Status Update n n n Completed activity diagrams for UOCAVA Vote-by-Mail processes Identified risks in those processes Currently estimating impact and occurrences of each risk TGDC Meeting, December 2011 Page 22

Next Steps n n n Complete UOCAVA Vote-by-Mail analysis Conduct risk assessments for blank ballot delivery Develop conclusions on major sources of risk in current processes TGDC Meeting, December 2011 Page 23
Discussion TGDC Meeting, December 2011 Page 24
- Slides: 24