Update on the Computer Fraud and Abuse Act

Update on the Computer Fraud and Abuse Act Sam Sneed March 2017 envision, strategize and actualize

DISCLAIMER This document has been provided for informational purposes only and is not intended and should not be construed to constitute legal advice. Please consult an attorney if you have specific legal issues. 2 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

18 U. S. C. § 1030 COMPUTER FRAUD AND ABUSE ACT 3 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

Brief History • 1984 Comprehensive Crime Control Act (CCCA) – Intended to prevent hacking – Protect financial records and gov’t computers • 1986 CFAA enacted, amended CCCA – Criminalized password trafficking – Criminalized DDOS attacks, malware distribution, similar exploits • 2008 amendments broadened application 4 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
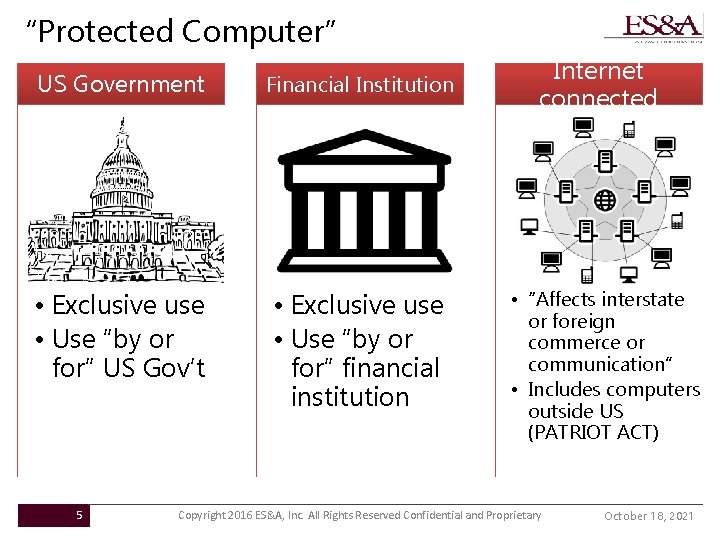
“Protected Computer” US Government Financial Institution • Exclusive use • Use “by or for” US Gov’t • Exclusive use • Use “by or for” financial institution 5 Internet connected • “Affects interstate or foreign commerce or communication” • Includes computers outside US (PATRIOT ACT) Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
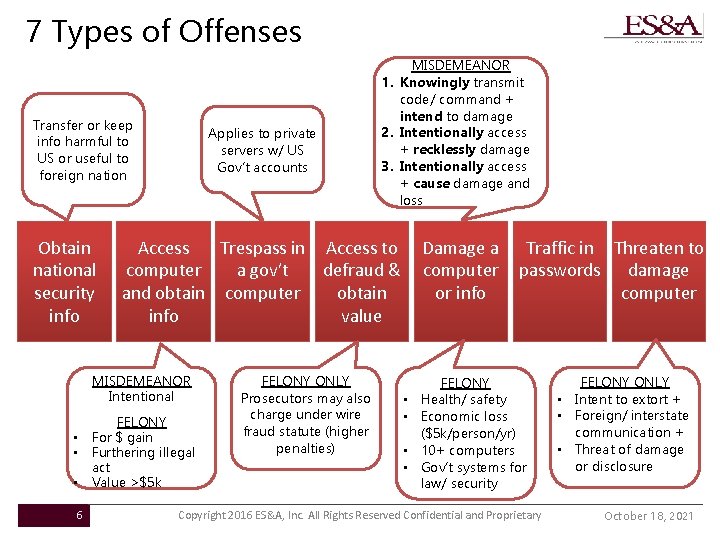
7 Types of Offenses Transfer or keep info harmful to US or useful to foreign nation Obtain national security info Applies to private servers w/ US Gov’t accounts Access Trespass in Access to computer a gov’t defraud & and obtain computer obtain info value MISDEMEANOR Intentional FELONY • For $ gain • Furthering illegal act • Value >$5 k 6 MISDEMEANOR 1. Knowingly transmit code/ command + intend to damage 2. Intentionally access + recklessly damage 3. Intentionally access + cause damage and loss FELONY ONLY Prosecutors may also charge under wire fraud statute (higher penalties) Damage a computer or info • • Traffic in Threaten to passwords damage computer FELONY Health/ safety Economic loss ($5 k/person/yr) 10+ computers Gov’t systems for law/ security Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary FELONY ONLY • Intent to extort + • Foreign/ interstate communication + • Threat of damage or disclosure October 18, 2021
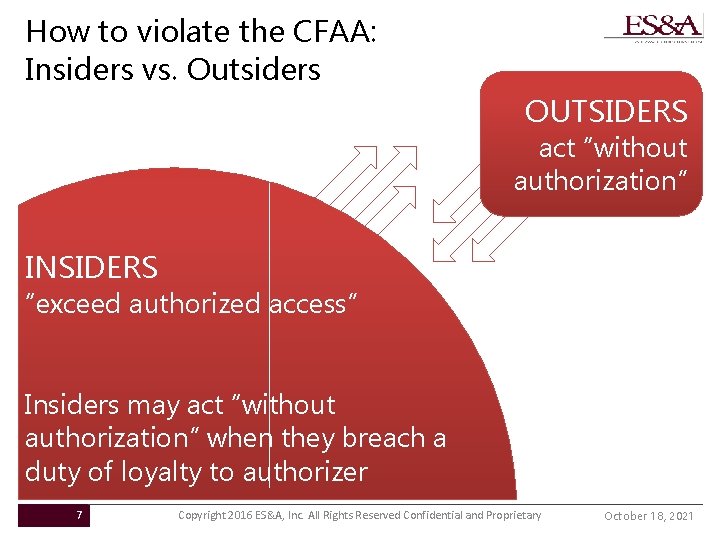
How to violate the CFAA: Insiders vs. Outsiders OUTSIDERS act “without authorization” INSIDERS “exceed authorized access” Insiders may act “without authorization” when they breach a duty of loyalty to authorizer 7 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
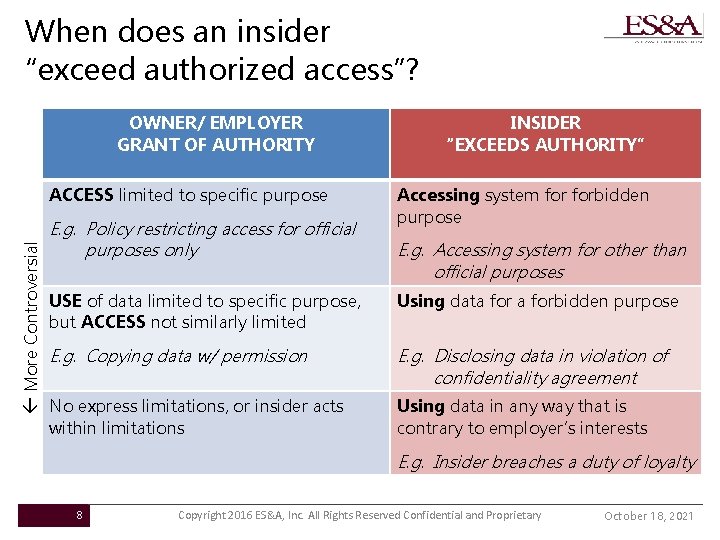
When does an insider “exceed authorized access”? OWNER/ EMPLOYER GRANT OF AUTHORITY More Controversial ACCESS limited to specific purpose E. g. Policy restricting access for official purposes only INSIDER “EXCEEDS AUTHORITY” Accessing system forbidden purpose E. g. Accessing system for other than official purposes USE of data limited to specific purpose, but ACCESS not similarly limited Using data forbidden purpose E. g. Copying data w/ permission E. g. Disclosing data in violation of confidentiality agreement No express limitations, or insider acts within limitations Using data in any way that is contrary to employer’s interests E. g. Insider breaches a duty of loyalty 8 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
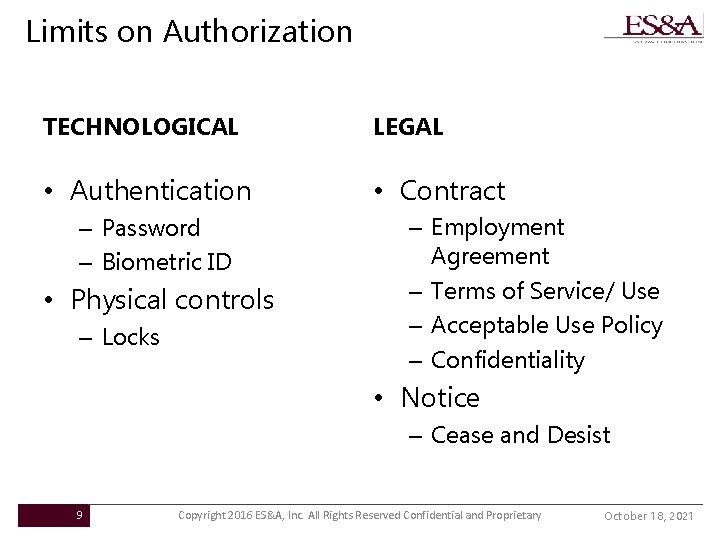
Limits on Authorization TECHNOLOGICAL LEGAL • Authentication • Contract – Password – Biometric ID • Physical controls – Locks – Employment Agreement – Terms of Service/ Use – Acceptable Use Policy – Confidentiality • Notice – Cease and Desist 9 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
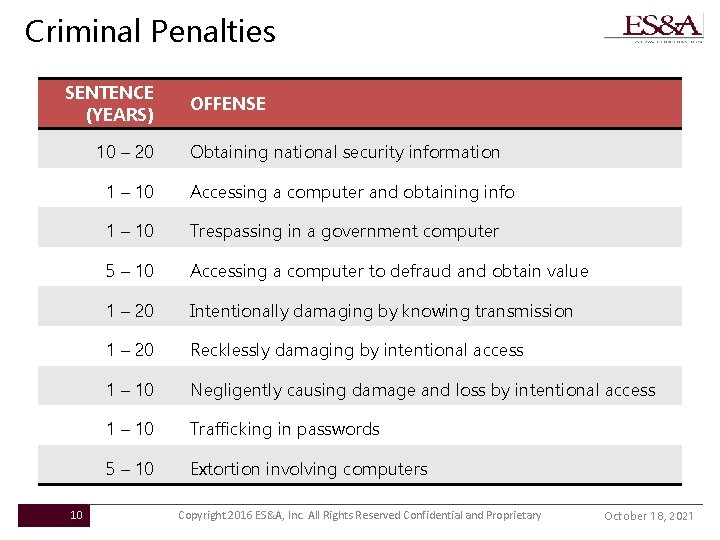
Criminal Penalties SENTENCE (YEARS) 10 – 20 10 OFFENSE Obtaining national security information 1 – 10 Accessing a computer and obtaining info 1 – 10 Trespassing in a government computer 5 – 10 Accessing a computer to defraud and obtain value 1 – 20 Intentionally damaging by knowing transmission 1 – 20 Recklessly damaging by intentional access 1 – 10 Negligently causing damage and loss by intentional access 1 – 10 Trafficking in passwords 5 – 10 Extortion involving computers Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

Civil Remedies • Types – Injunctive relief – Equitable relief – Compensatory damages • Restrictions and requirements – Statute of limitations – 2 years – No action for negligent design/ manufacture 11 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

Civil Remedies – Show Damages $5000 loss to individual w/in 1 year Medical treatment modified/impaired Threat to public health or safety Damage to US Gov’t computer used in national security, defense, or administration of justice • 10+ protected computers w/in 1 year • • 12 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

Controversy • Criminal penalties for breach of contract? – Aaron Swartz and JSTOR (2010 -2012) – Reform attempts to exclude TOS/TOU (“Aaron’s Law, ” 2013) • Overbroad/ ambiguous? • Protections under other laws? – Defend Trade Secrets Act 13 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

U. S. v. Nosal Facebook v. Power Ventures RECENT CASES INTERPRETING CFAA 14 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
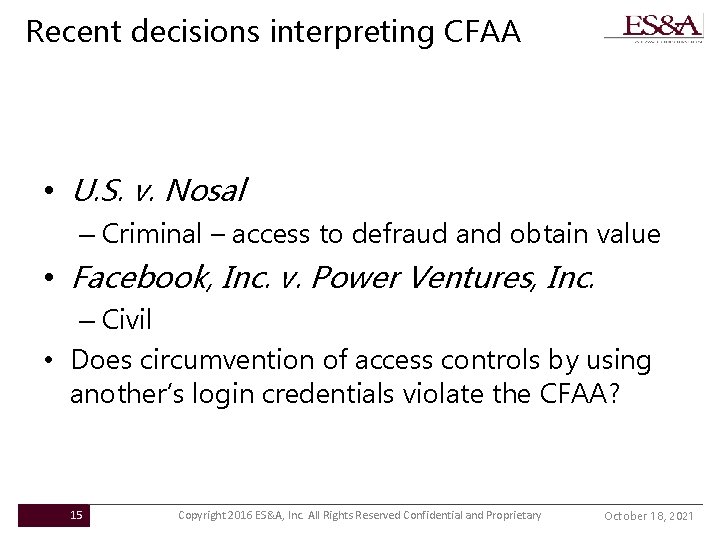
Recent decisions interpreting CFAA • U. S. v. Nosal – Criminal – access to defraud and obtain value • Facebook, Inc. v. Power Ventures, Inc. – Civil • Does circumvention of access controls by using another’s login credentials violate the CFAA? 15 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
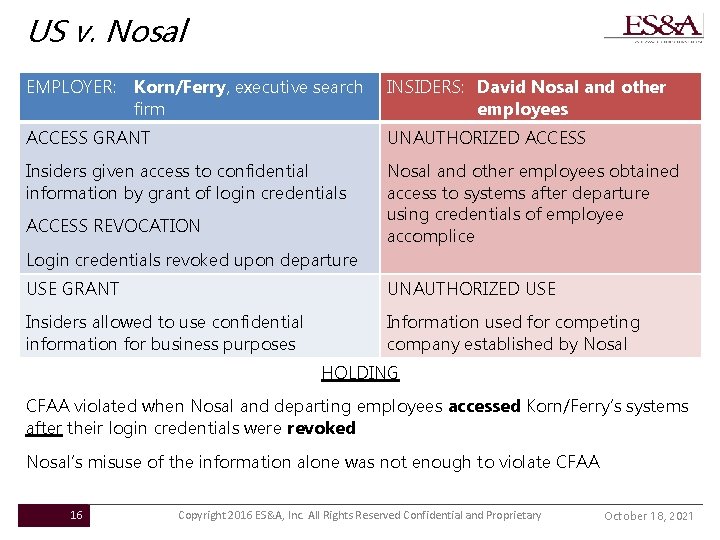
US v. Nosal EMPLOYER: Korn/Ferry, executive search firm INSIDERS: David Nosal and other employees ACCESS GRANT UNAUTHORIZED ACCESS Insiders given access to confidential information by grant of login credentials Nosal and other employees obtained access to systems after departure using credentials of employee accomplice ACCESS REVOCATION Login credentials revoked upon departure USE GRANT UNAUTHORIZED USE Insiders allowed to use confidential information for business purposes Information used for competing company established by Nosal HOLDING CFAA violated when Nosal and departing employees accessed Korn/Ferry’s systems after their login credentials were revoked Nosal’s misuse of the information alone was not enough to violate CFAA 16 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
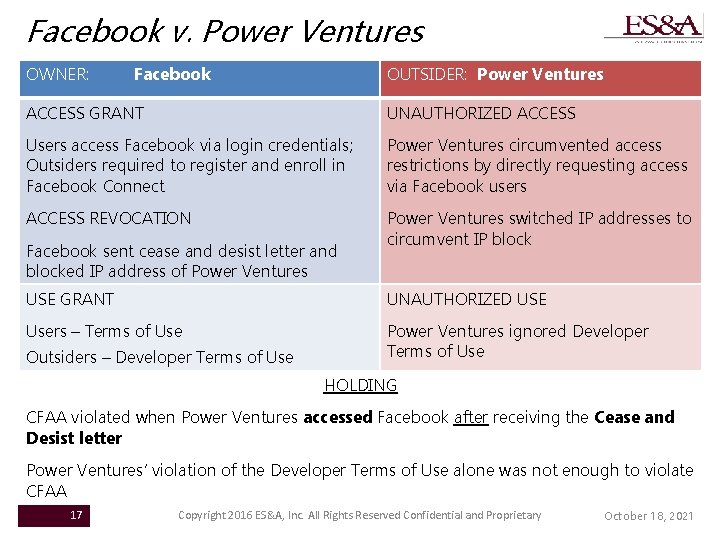
Facebook v. Power Ventures OWNER: OUTSIDER: Power Ventures Facebook ACCESS GRANT UNAUTHORIZED ACCESS Users access Facebook via login credentials; Outsiders required to register and enroll in Facebook Connect Power Ventures circumvented access restrictions by directly requesting access via Facebook users ACCESS REVOCATION Power Ventures switched IP addresses to circumvent IP block Facebook sent cease and desist letter and blocked IP address of Power Ventures USE GRANT UNAUTHORIZED USE Users – Terms of Use Power Ventures ignored Developer Terms of Use Outsiders – Developer Terms of Use HOLDING CFAA violated when Power Ventures accessed Facebook after receiving the Cease and Desist letter Power Ventures’ violation of the Developer Terms of Use alone was not enough to violate CFAA 17 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

OWNER/ EMPLOYER TAKEAWAYS 18 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
Using the CFAA • Broad – Low threshold for damages • Ambiguity - “exceeds authorized access”? – Access vs. use restrictions – Inconsistent case law • To be revised? – Controversial, old 19 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021

Best Practices • Explicit policies and agreements – Handbook – Acceptable Use – Confidentiality, Non-compete • Explicit revocation of permissions – Employee exit processing • Reminders of policies and agreements • Clearly revoke access to all systems – Cease and desist letter 20 Copyright 2016 ES&A, Inc. All Rights Reserved Confidential and Proprietary October 18, 2021
- Slides: 20