UNIX File System Go Climb a Tree Weiyu
UNIX File System Go Climb a Tree Weiyu Zhang (96142) COSC 513 Operating Systems Southeastern University 1

Introduction n n In UNIX, the thing we spend most of our time working with is files. Treating files consistently is one of the greatest strengths in UNIX. 2
What is “consistent”? n UNIX use the same method to save all the files. u For example, an executable script has the same format as a text file. n n Simplify the file system. The idea is widely used later. (In DOS, Win 95/98, etc. ) 3
Three types of UNIX Files n n n Regular files Directory files Device files 4
Regular files n n n Most common type Hold programs and data Example: u Source code of a program u Email received from friend u Executable programs and applications (such as ls, cat, etc. ) 5

Directory files n n n Basic management tools in UNIX file system Like a cabinet in real life, the files that contain other files Save information of files (such as location, size, etc. ) 6

Devices files n n Each hardware is treated like a file Example u Terminals u Printers u Keyboards, etc. 7
More about device file n Example: the user input read from a keyboard device file. u Print a text file Copy the file to the printer device file. u Read n Convenient to handle 8
File system organization n A bottom-up tree with root on the top All the files must be put into directory files Root (/), a special directory file u Exact one u Can not been deleted 9
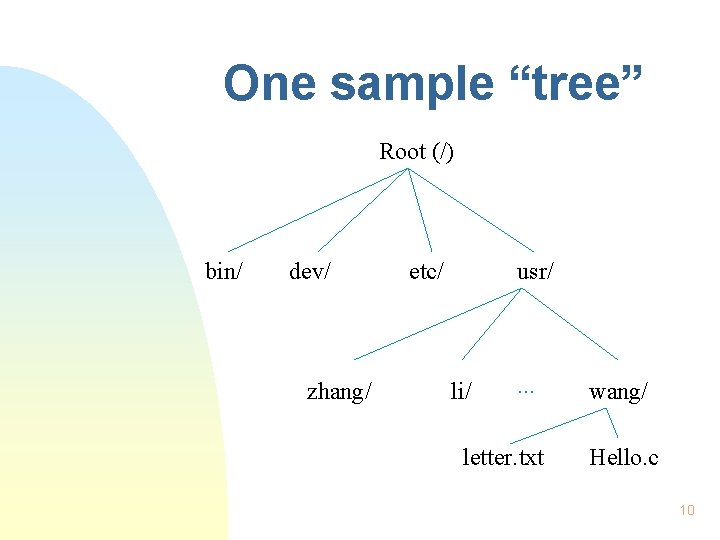
One sample “tree” Root (/) bin/ dev/ zhang/ etc/ usr/ li/ . . . letter. txt wang/ Hello. c 10

Find a file in UNIX n n n Start from the root Go down (or climb) the tree, record the path Each file has a name 11
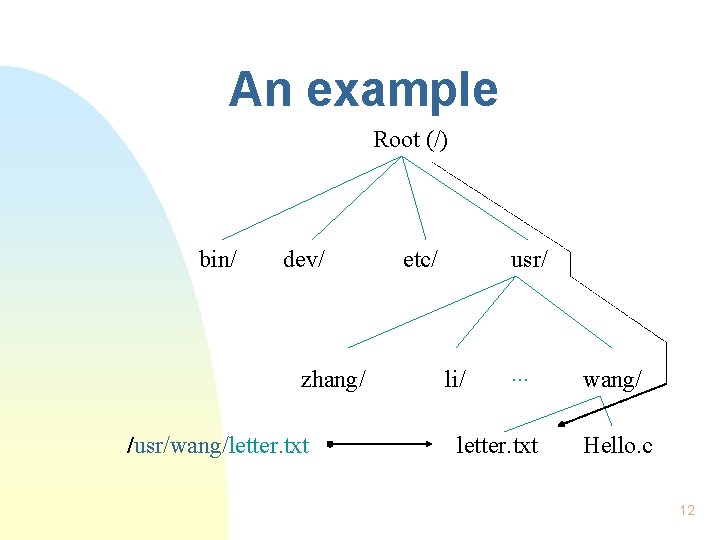
An example Root (/) bin/ dev/ zhang/ /usr/wang/letter. txt etc/ usr/ li/ . . . letter. txt wang/ Hello. c 12
File and directory permission n n Only need in a multi-user OS Keep your own secrets Three classes of users Three permissions 13
Three classes of users n n n Owner: I created the file. Group: The owner and I are in the same working group. World (a. k. a. other): I just want to use the file. 14

Three permissions n n Read permission: read Write permission: modify, delete Execute permission: run No exact priority, normally write permission is the most important one 15
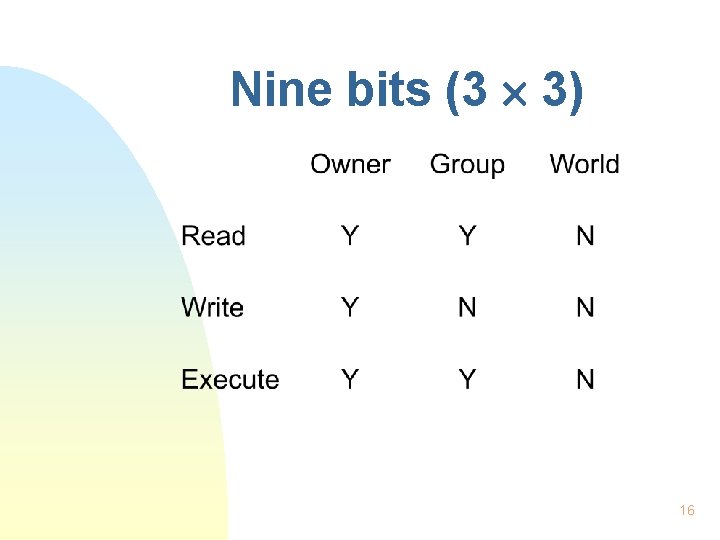
Nine bits (3 3) 16
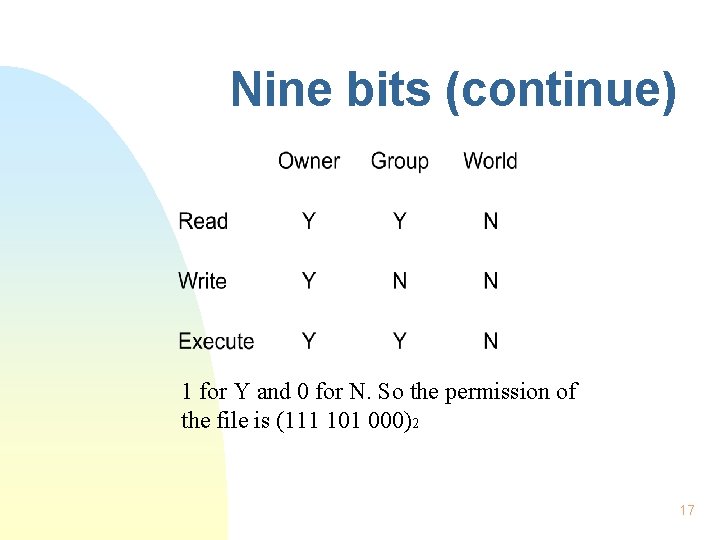
Nine bits (continue) 1 for Y and 0 for N. So the permission of the file is (111 101 000)2 17

Why permission n Keep your secrets. u In the above example, world user can not read the file, group user can not modify or delete the file. 18

Why permission (cont) n n Keep your secrets. Show more information about a file. u Since the files are saved consistently, only those which have the execute permission set can be run. 19

Why permission (cont) n n n Keep your secrets. Show more information about a file. Avoid wrong operation u Setting the owner write permission to be ‘N’ (or 0) can avoid the careless delete of very important files. 20
21

Conclusions n n n Everything is a file. Bottom-up tree organization Easy but safe 22
The End 23
- Slides: 23