University of Washington Buffer overflows Buffer overflows are

University of Washington Buffer overflows ¢ ¢ ¢ Buffer overflows are possible because C does not check array boundaries Buffer overflows are dangerous because buffers for user input are often stored on the stack Topics: § § Winter 2015 Address space layout Input buffers on the stack Overflowing buffers and injecting code Defenses against buffer overflows Buffer Overflow 1
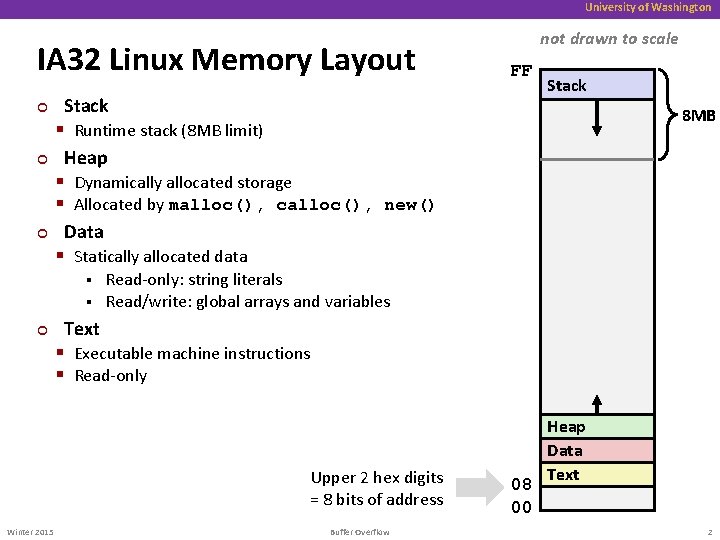
University of Washington IA 32 Linux Memory Layout ¢ ¢ ¢ not drawn to scale FF Stack § Runtime stack (8 MB limit) Heap § Dynamically allocated storage § Allocated by malloc(), calloc(), new() Data § Statically allocated data Stack 8 MB Read-only: string literals § Read/write: global arrays and variables § ¢ Text § Executable machine instructions § Read-only Upper 2 hex digits = 8 bits of address Winter 2015 Buffer Overflow 08 00 Heap Data Text 2
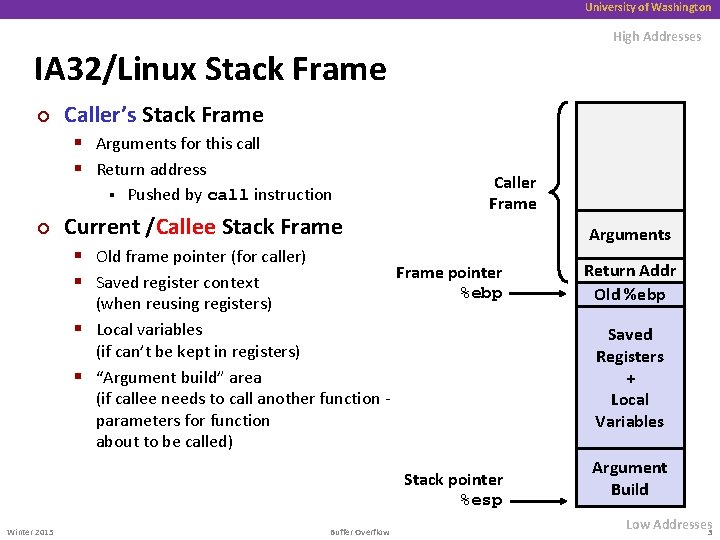
University of Washington High Addresses IA 32/Linux Stack Frame ¢ Caller’s Stack Frame § Arguments for this call § Return address § ¢ Pushed by call instruction Current /Callee Stack Frame § Old frame pointer (for caller) § Saved register context (when reusing registers) § Local variables (if can’t be kept in registers) § “Argument build” area (if callee needs to call another function parameters for function about to be called) Caller Frame Arguments Frame pointer %ebp Saved Registers + Local Variables Stack pointer %esp Winter 2015 Buffer Overflow Return Addr Old %ebp Argument Build Low Addresses 3
![University of Washington Memory Allocation Example not drawn to scale FF Stack char big_array[1<<24]; University of Washington Memory Allocation Example not drawn to scale FF Stack char big_array[1<<24];](http://slidetodoc.com/presentation_image_h2/4fb11120fe3dc3eff922a605041de553/image-4.jpg)
University of Washington Memory Allocation Example not drawn to scale FF Stack char big_array[1<<24]; /* 16 MB */ char huge_array[1<<28]; /* 256 MB */ int beyond; char *p 1, *p 2, *p 3, *p 4; int useless() { int { p 1 p 2 p 3 p 4 /* } return 0; } main() = malloc(1 Some print <<28); /* << 8); /* statements 256 256. . . MB B */ Where does everything go? Winter 2015 */ */ 08 00 Buffer Overflow Heap Data Text 4
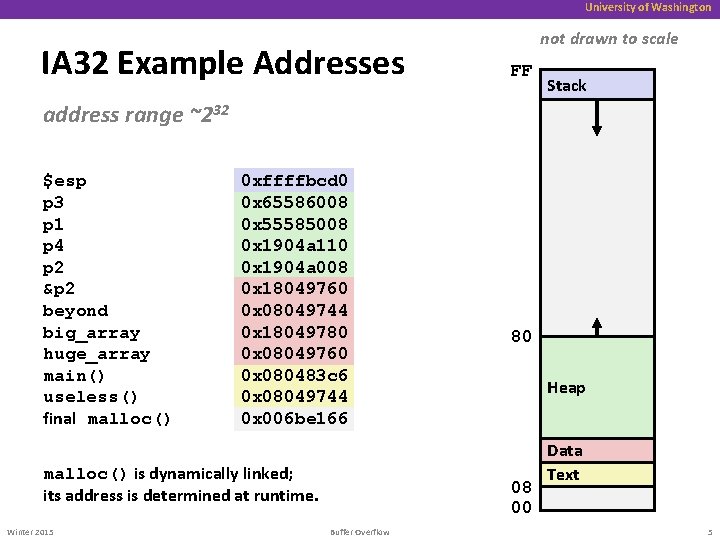
University of Washington IA 32 Example Addresses not drawn to scale FF Stack address range ~232 $esp p 3 p 1 p 4 p 2 &p 2 beyond big_array huge_array main() useless() final malloc() 0 xffffbcd 0 0 x 65586008 0 x 55585008 0 x 1904 a 110 0 x 1904 a 008 0 x 18049760 0 x 08049744 0 x 18049780 0 x 08049760 0 x 080483 c 6 0 x 08049744 0 x 006 be 166 malloc() is dynamically linked; its address is determined at runtime. Winter 2015 80 Heap 08 00 Buffer Overflow Data Text 5
University of Washington Internet Worm ¢ These characteristics of the traditional IA 32 Linux memory layout provide opportunities for malicious programs § Stack grows “backwards” in memory § Data and instructions both stored in the same memory ¢ November, 1988 § Internet Worm attacks thousands of Internet hosts. § How did it happen? ¢ Winter 2015 Stack buffer overflow exploits! Buffer Overflow 6

University of Washington Buffer Overflow in a nutshell ¢ ¢ ¢ Winter 2015 Many classic Unix/Linux/C functions do not check argument sizes C does not check array bounds Allows overflowing (writing past the end of) buffers (arrays) Overflows of buffers on the stack overwrite interesting data Attackers just choose the right inputs Probably the most common type of security vulnerability Buffer Overflow 7
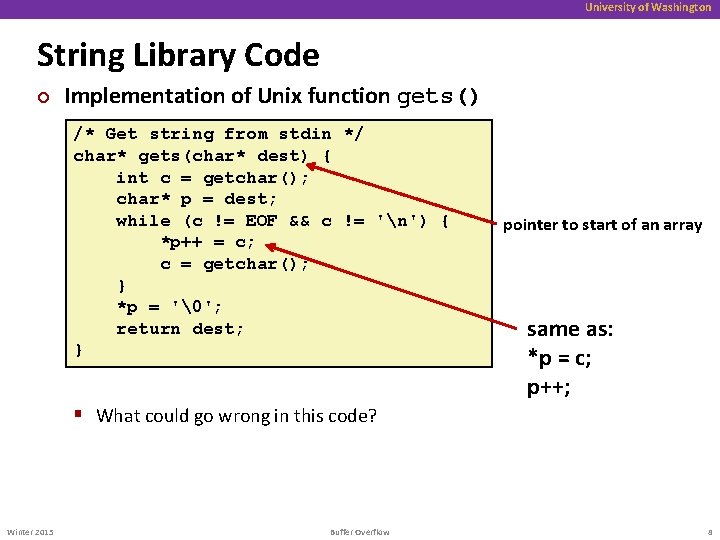
University of Washington String Library Code ¢ Implementation of Unix function gets() /* Get string from stdin */ char* gets(char* dest) { int c = getchar(); char* p = dest; while (c != EOF && c != 'n') { *p++ = c; c = getchar(); } *p = '�'; return dest; } pointer to start of an array same as: *p = c; p++; § What could go wrong in this code? Winter 2015 Buffer Overflow 8
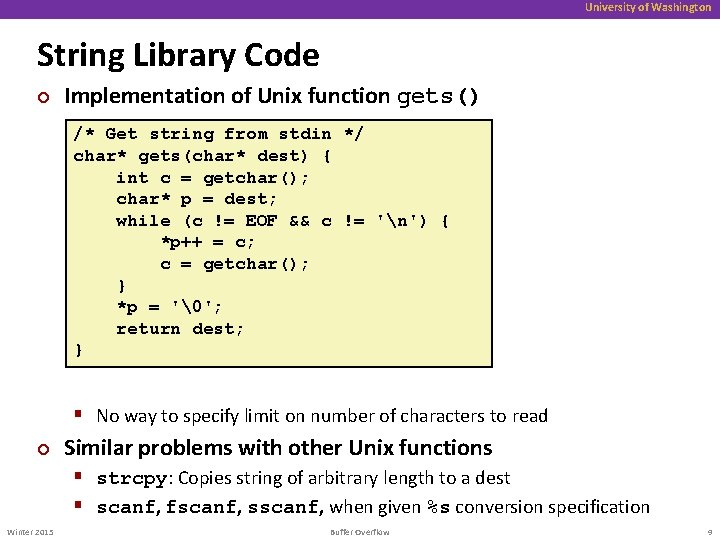
University of Washington String Library Code ¢ Implementation of Unix function gets() /* Get string from stdin */ char* gets(char* dest) { int c = getchar(); char* p = dest; while (c != EOF && c != 'n') { *p++ = c; c = getchar(); } *p = '�'; return dest; } § No way to specify limit on number of characters to read ¢ Similar problems with other Unix functions § strcpy: Copies string of arbitrary length to a dest § scanf, fscanf, sscanf, when given %s conversion specification Winter 2015 Buffer Overflow 9
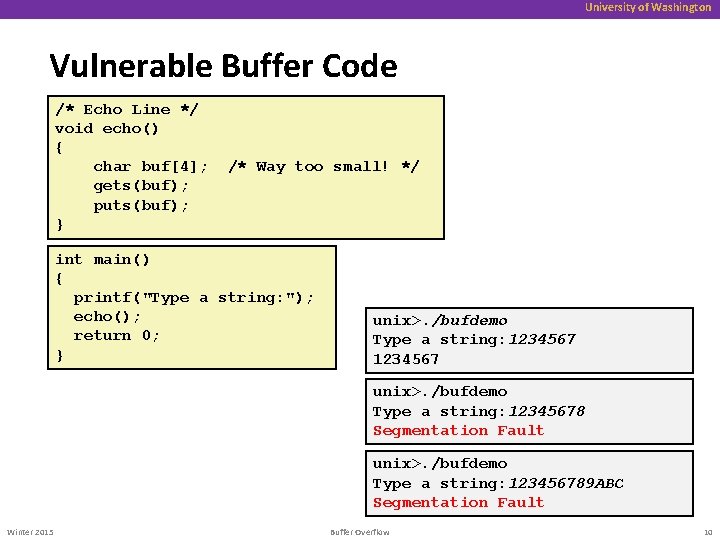
University of Washington Vulnerable Buffer Code /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } /* Way too small! */ int main() { printf("Type a string: "); echo(); return 0; } unix>. /bufdemo Type a string: 12345678 Segmentation Fault unix>. /bufdemo Type a string: 123456789 ABC Segmentation Fault Winter 2015 Buffer Overflow 10
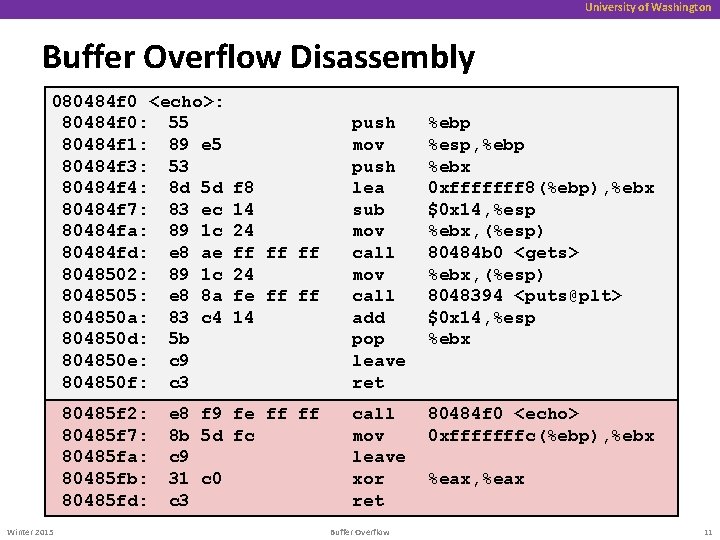
University of Washington Buffer Overflow Disassembly 080484 f 0 <echo>: 80484 f 0: 55 80484 f 1: 89 e 5 80484 f 3: 53 80484 f 4: 8 d 5 d 80484 f 7: 83 ec 80484 fa: 89 1 c 80484 fd: e 8 ae 8048502: 89 1 c 8048505: e 8 8 a 804850 a: 83 c 4 804850 d: 5 b 804850 e: c 9 804850 f: c 3 80485 f 2: 80485 f 7: 80485 fa: 80485 fb: 80485 fd: Winter 2015 f 8 14 24 ff ff ff 24 fe ff ff 14 push mov push lea sub mov call add pop leave ret %ebp %esp, %ebp %ebx 0 xfffffff 8(%ebp), %ebx $0 x 14, %esp %ebx, (%esp) 80484 b 0 <gets> %ebx, (%esp) 8048394 <puts@plt> $0 x 14, %esp %ebx e 8 f 9 fe ff ff 8 b 5 d fc c 9 31 c 0 c 3 call mov leave xor ret 80484 f 0 <echo> 0 xfffffffc(%ebp), %ebx Buffer Overflow %eax, %eax 11
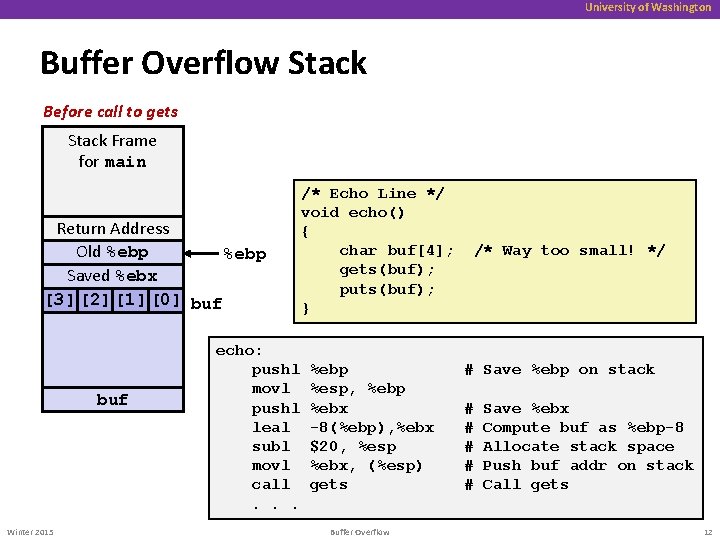
University of Washington Buffer Overflow Stack Before call to gets Stack Frame for main Return Address Old %ebp Saved %ebx [3] [2] [1] [0] buf Winter 2015 echo: pushl movl pushl leal subl movl call. . . /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } %ebp %esp, %ebp %ebx -8(%ebp), %ebx $20, %esp %ebx, (%esp) gets Buffer Overflow /* Way too small! */ # Save %ebp on stack # # # Save %ebx Compute buf as %ebp-8 Allocate stack space Push buf addr on stack Call gets 12
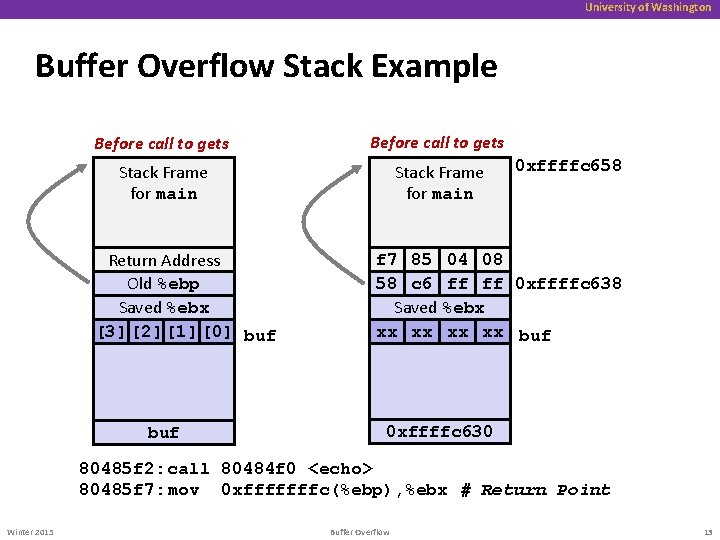
University of Washington Buffer Overflow Stack Example Before call to gets Stack Frame for main Return Address Old %ebp Saved %ebx [3] [2] [1] [0] buf 0 xffffc 658 f 7 85 04 08 58 c 6 ff ff 0 xffffc 638 Saved %ebx xx xx buf 0 xffffc 630 80485 f 2: call 80484 f 0 <echo> 80485 f 7: mov 0 xfffffffc(%ebp), %ebx # Return Point Winter 2015 Buffer Overflow 13
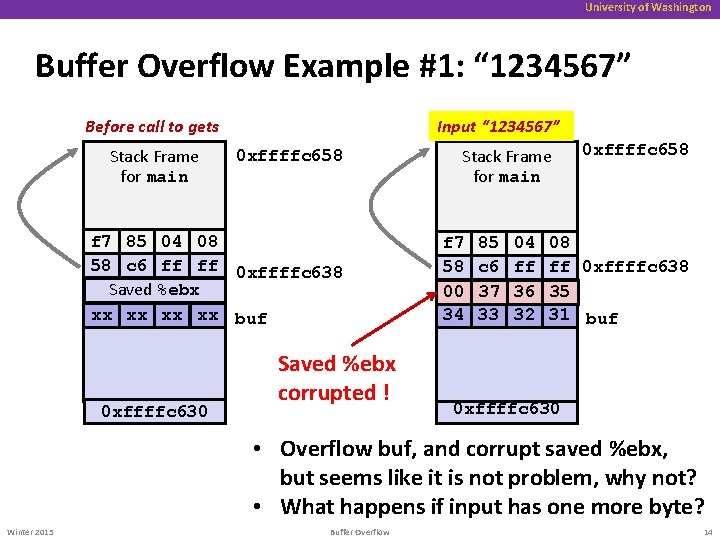
University of Washington Buffer Overflow Example #1: “ 1234567” Input “ 1234567” Before call to gets Stack Frame for main 0 xffffc 658 f 7 85 04 08 58 c 6 ff ff 0 xffffc 638 Saved %ebx xx xx buf 0 xffffc 630 Saved %ebx corrupted ! Stack Frame for main f 7 58 00 34 85 c 6 37 33 04 ff 36 32 0 xffffc 658 08 ff 0 xffffc 638 35 31 buf 0 xffffc 630 • Overflow buf, and corrupt saved %ebx, but seems like it is not problem, why not? • What happens if input has one more byte? Winter 2015 Buffer Overflow 14
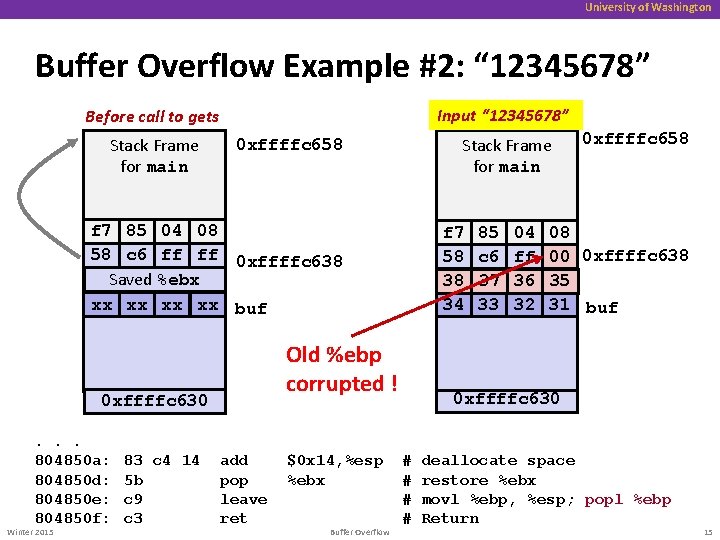
University of Washington Buffer Overflow Example #2: “ 12345678” Input “ 12345678” Before call to gets Stack Frame for main 0 xffffc 658 f 7 85 04 08 58 c 6 ff ff 0 xffffc 638 Saved %ebx xx xx buf Old %ebp corrupted ! 0 xffffc 630. . . 804850 a: 804850 d: 804850 e: 804850 f: Winter 2015 83 c 4 14 5 b c 9 c 3 f 7 58 38 34 add pop leave ret $0 x 14, %esp %ebx Buffer Overflow 85 c 6 37 33 04 ff 36 32 0 xffffc 658 08 00 0 xffffc 638 35 31 buf 0 xffffc 630 # # deallocate space restore %ebx movl %ebp, %esp; popl %ebp Return 15
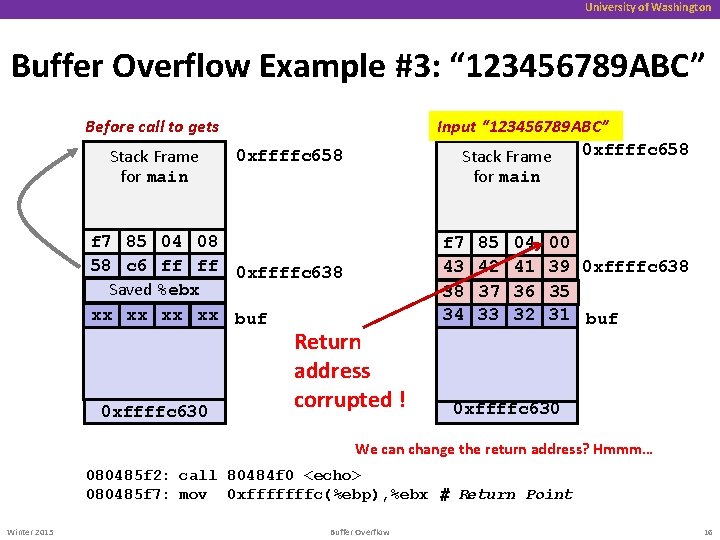
University of Washington Buffer Overflow Example #3: “ 123456789 ABC” Input “ 123456789 ABC” 0 xffffc 658 Stack Frame Before call to gets Stack Frame for main 0 xffffc 658 for main f 7 85 04 08 58 c 6 ff ff 0 xffffc 638 Saved %ebx xx xx buf 0 xffffc 630 f 7 43 38 34 Return address corrupted ! 85 42 37 33 04 41 36 32 00 39 0 xffffc 638 35 31 buf 0 xffffc 630 We can change the return address? Hmmm… 080485 f 2: call 80484 f 0 <echo> 080485 f 7: mov 0 xfffffffc(%ebp), %ebx # Return Point Winter 2015 Buffer Overflow 16
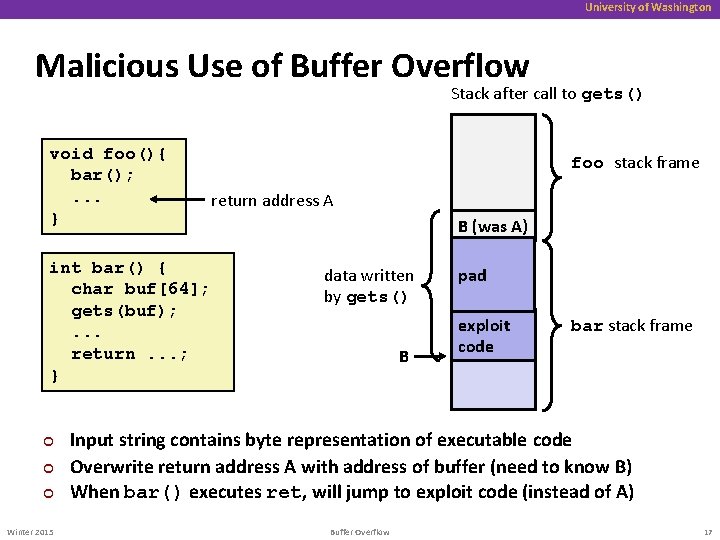
University of Washington Malicious Use of Buffer Overflow Stack after call to gets() void foo(){ bar(); . . . } int bar() { char buf[64]; gets(buf); . . . return. . . ; } ¢ ¢ ¢ Winter 2015 foo stack frame return address A B (was A) data written by gets() B pad exploit code bar stack frame Input string contains byte representation of executable code Overwrite return address A with address of buffer (need to know B) When bar() executes ret, will jump to exploit code (instead of A) Buffer Overflow 17
University of Washington Exploits Based on Buffer Overflows ¢ ¢ Buffer overflow bugs allow remote machines to execute arbitrary code on victim machines Internet worm § Early versions of the finger server (fingerd) used gets() to read the argument sent by the client: § finger droh@cs. cmu. edu § Worm attacked fingerd server by sending phony argument: § finger “exploit-code padding new-returnaddress” § exploit code: executed a root shell on the victim machine with a direct TCP connection to the attacker commandline facebook of the 80 s! Winter 2015 Buffer Overflow 18
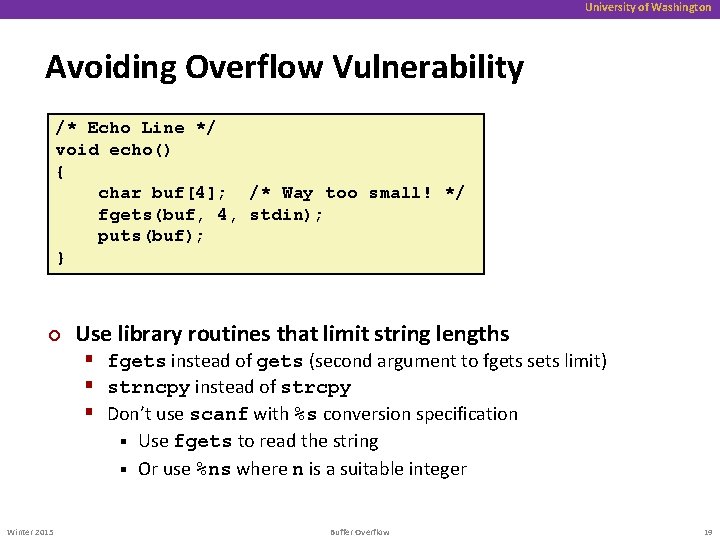
University of Washington Avoiding Overflow Vulnerability /* Echo Line */ void echo() { char buf[4]; /* Way too small! */ fgets(buf, 4, stdin); puts(buf); } ¢ Use library routines that limit string lengths § fgets instead of gets (second argument to fgets sets limit) § strncpy instead of strcpy § Don’t use scanf with %s conversion specification Use fgets to read the string § Or use %ns where n is a suitable integer § Winter 2015 Buffer Overflow 19
University of Washington System-Level Protections ¢ not drawn to scale FF Stack Randomized stack offsets § At start of program, allocate random amount of space on stack § Makes it difficult for exploit to predict beginning of inserted code ¢ Use techniques to detect stack corruption ¢ Nonexecutable code segments § Only allow code to execute from “text” sections of memory § Do NOT execute code in stack, data, or heap regions § Hardware support needed Winter 2015 Buffer Overflow 08 00 Heap Data Text 20
- Slides: 20