UNIT7 Digital Signature Prof R K Karangiya rekha









- Slides: 28

UNIT-7 Digital Signature Prof. R. K. Karangiya rekha. karangiya@darshan. ac. in Information & Network Security (2170709) Darshan Institute of Engineering & Technology

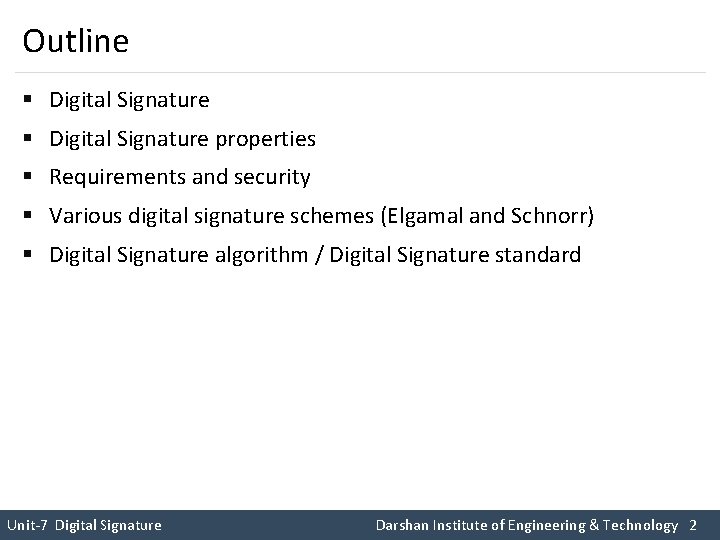
Outline § Digital Signature properties § Requirements and security § Various digital signature schemes (Elgamal and Schnorr) § Digital Signature algorithm / Digital Signature standard Unit-7 Digital Signature Darshan Institute of Engineering & Technology 2

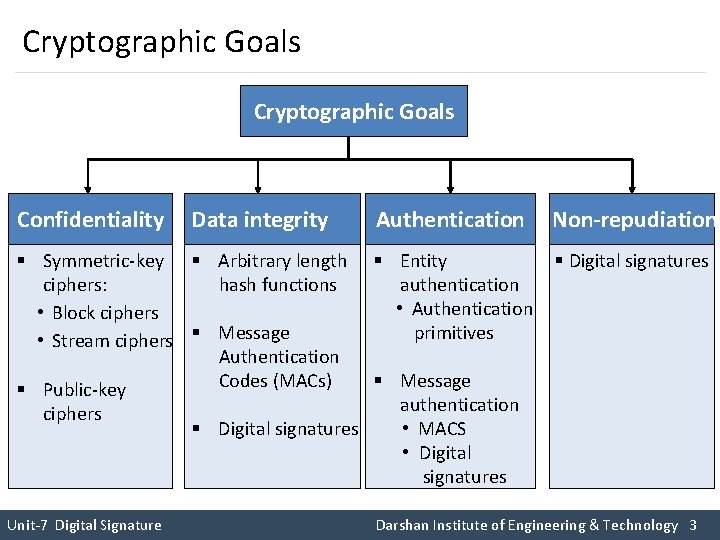
Cryptographic Goals Confidentiality Data integrity § Symmetric-key § Arbitrary length ciphers: hash functions • Block ciphers • Stream ciphers § Message Authentication Codes (MACs) § Public-key ciphers Unit-7 Digital Signature Authentication Non-repudiation § Entity authentication • Authentication primitives § Digital signatures § Message authentication • MACS § Digital signatures • Digital signatures Darshan Institute of Engineering & Technology 3

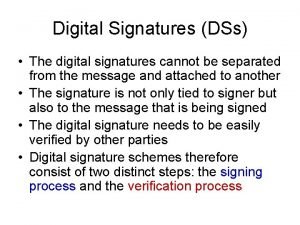
Digital Signature § A digital signature is an authentication mechanism that enables the creator of a message to attach a code that acts as a signature. § Typically the signature is formed by taking the hash of the message and encrypting the message with the creator’s private key. § The signature guarantees the source and integrity of the message. § The digital signature standard (DSS) is an NIST standard that uses the secure hash algorithm (SHA). Unit-7 Digital Signature Darshan Institute of Engineering & Technology 4

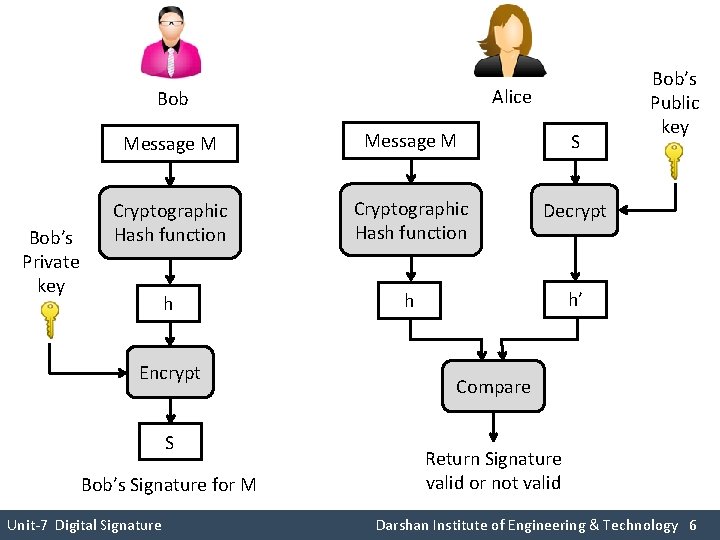
Alice Bob’s Private key Message M S Cryptographic Hash function Decrypt h h h’ Encrypt S Bob’s Signature for M Unit-7 Digital Signature Bob’s Public key Compare Return Signature valid or not valid Darshan Institute of Engineering & Technology 6

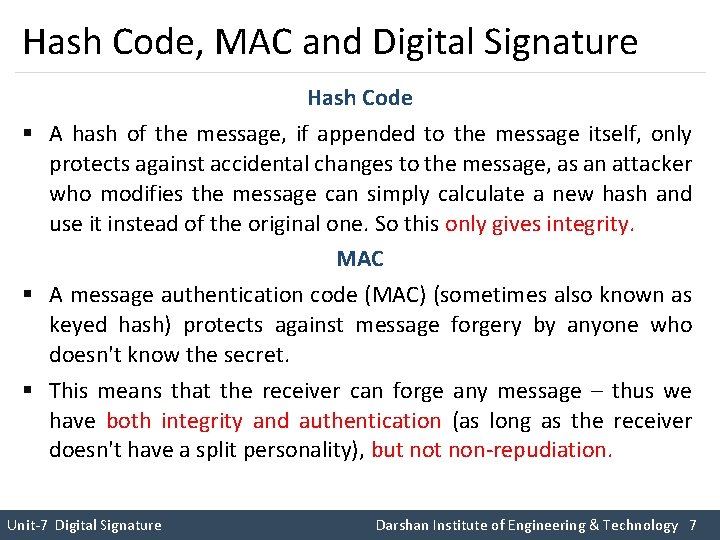
Hash Code, MAC and Digital Signature Hash Code § A hash of the message, if appended to the message itself, only protects against accidental changes to the message, as an attacker who modifies the message can simply calculate a new hash and use it instead of the original one. So this only gives integrity. MAC § A message authentication code (MAC) (sometimes also known as keyed hash) protects against message forgery by anyone who doesn't know the secret. § This means that the receiver can forge any message – thus we have both integrity and authentication (as long as the receiver doesn't have a split personality), but non-repudiation. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 7

Hash Code, MAC and Digital Signature § A digital signature is created with a private key, and verified with the corresponding public key of an asymmetric key-pair. § Only the holder of the private key can create this signature, and normally anyone knowing the public key can verify it. So digital signature provides non-repudiation. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 8

Attacks § C = Attacker, A = victim § Key-only attack: C only knows A’s public key. § Known message attack: C has set of messages, signatures. § Generic chosen message attack: C obtains A’s signatures on messages selected without knowledge of A’s public key. § Directed chosen message attack: C obtains A’s signatures on messages selected after knowing A’s public key. § Adaptive chosen message attack: C may request signatures on messages depending upon previous message-signature pairs. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 9

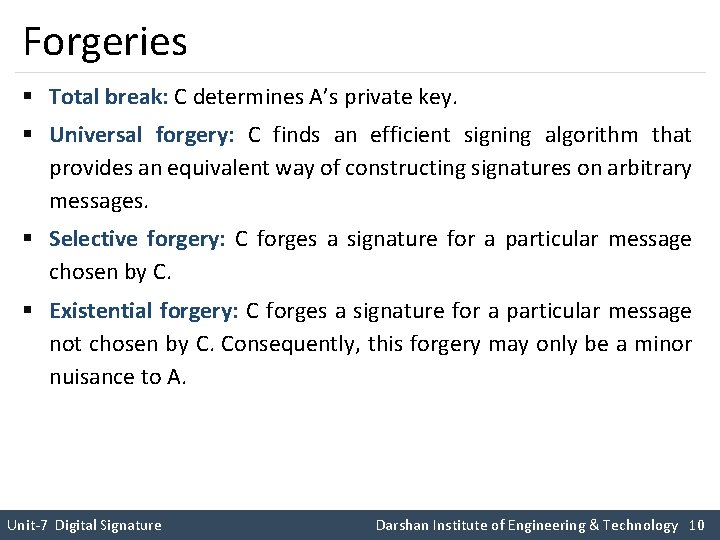
Forgeries § Total break: C determines A’s private key. § Universal forgery: C finds an efficient signing algorithm that provides an equivalent way of constructing signatures on arbitrary messages. § Selective forgery: C forges a signature for a particular message chosen by C. § Existential forgery: C forges a signature for a particular message not chosen by C. Consequently, this forgery may only be a minor nuisance to A. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 10

Digital Signature Requirements 1. The signature must be a bit pattern that depends on the message being signed. 2. The signature must use some information unique to the sender to prevent both forgery and denial. 3. It must be relatively easy to produce the digital signature. 4. It must be relatively easy to recognize and verify the digital signature. 5. It must be computationally infeasible to forge a digital signature, either by constructing a new message for an existing digital signature or by constructing a fraudulent digital signature for a given message. 6. It must be practical to retain a copy of the digital signature in storage. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 11

Digital Signature Standard / DSA § The DSS uses an algorithm that is designed to provide only the digital signature function. § Unlike RSA, it cannot be used for encryption or key exchange. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 12

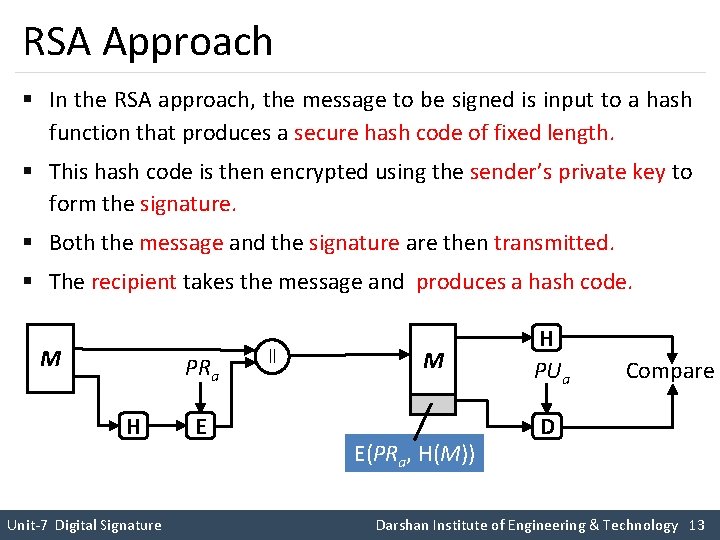
RSA Approach § In the RSA approach, the message to be signed is input to a hash function that produces a secure hash code of fixed length. § This hash code is then encrypted using the sender’s private key to form the signature. § Both the message and the signature are then transmitted. § The recipient takes the message and produces a hash code. M PRa H Unit-7 Digital Signature E ll M E(PRa, H(M)) H PUa Compare D Darshan Institute of Engineering & Technology 13

RSA Approach § The recipient also decrypts the signature using the sender’s public key. § If the calculated hash code matches the decrypted signature, the signature is accepted as valid. § Because only the sender knows the private key, only the sender could have produced a valid signature. Unit-7 Digital Signature Darshan Institute of Engineering & Technology 14

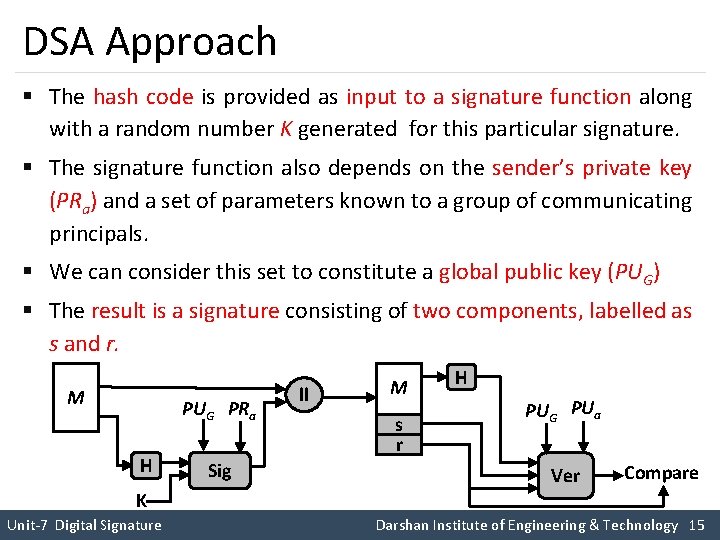
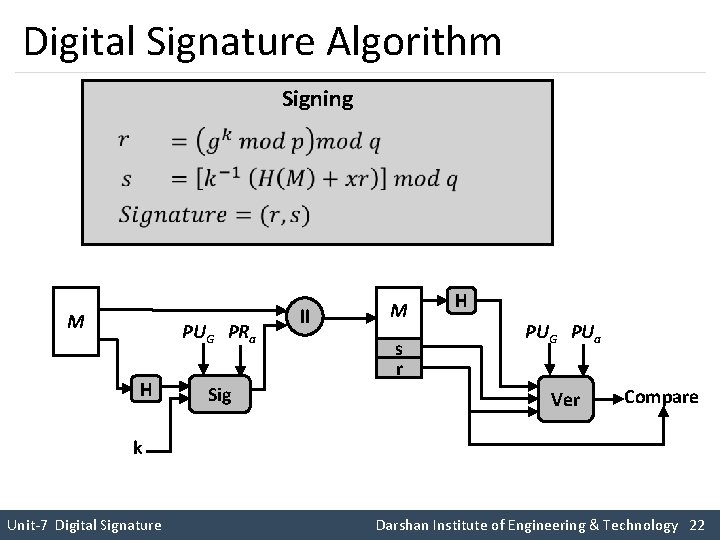
DSA Approach § The hash code is provided as input to a signature function along with a random number K generated for this particular signature. § The signature function also depends on the sender’s private key (PRa) and a set of parameters known to a group of communicating principals. § We can consider this set to constitute a global public key (PUG) § The result is a signature consisting of two components, labelled as s and r. M PUG PRa H Sig ll M s r H PUG PUa Ver Compare K Unit-7 Digital Signature Darshan Institute of Engineering & Technology 15

DSA Approach § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 16

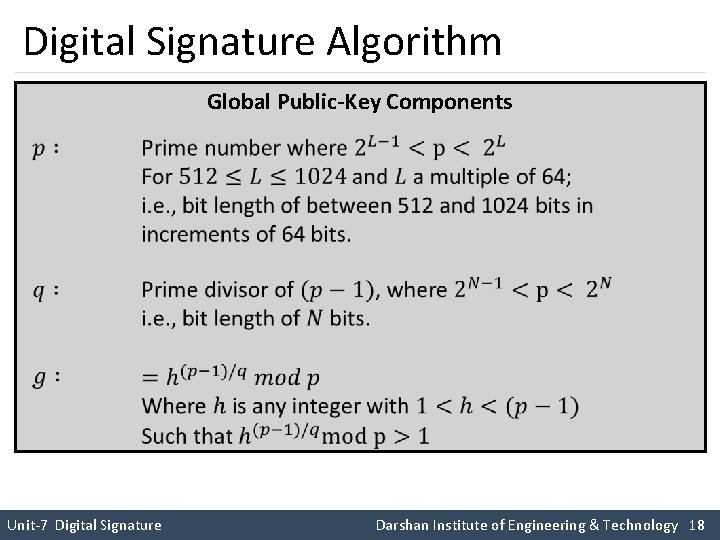
Digital Signature Algorithm Global Public-Key Components Unit-7 Digital Signature Darshan Institute of Engineering & Technology 18

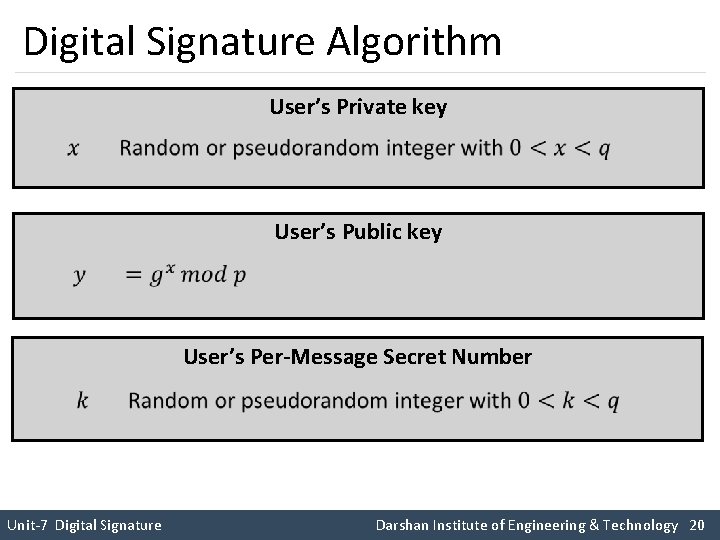
Digital Signature Algorithm User’s Private key User’s Public key User’s Per-Message Secret Number Unit-7 Digital Signature Darshan Institute of Engineering & Technology 20

Digital Signature Algorithm Signing M PUG PRa H Sig ll M s r H PUG PUa Ver Compare k Unit-7 Digital Signature Darshan Institute of Engineering & Technology 22

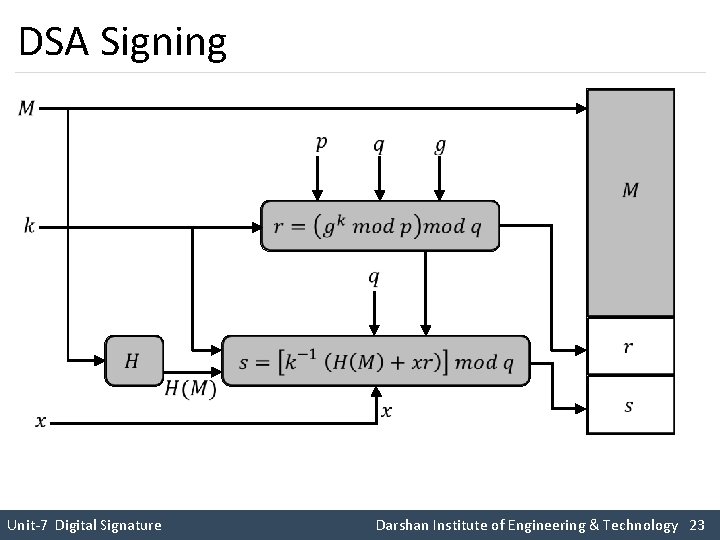
DSA Signing Unit-7 Digital Signature Darshan Institute of Engineering & Technology 23

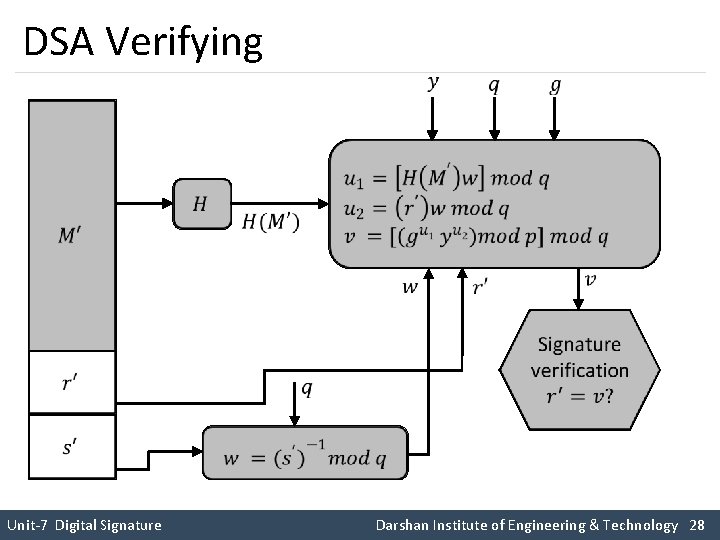
Digital Signature Algorithm Verifying M PUG PRa H Sig ll M s r H PUG PUa Ver Compare k Unit-7 Digital Signature Darshan Institute of Engineering & Technology 25

DSA Verifying Unit-7 Digital Signature Darshan Institute of Engineering & Technology 28

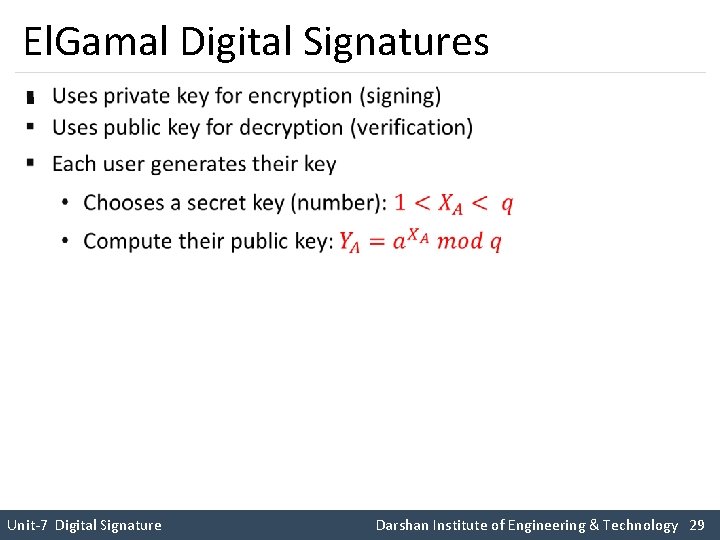
El. Gamal Digital Signatures § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 29

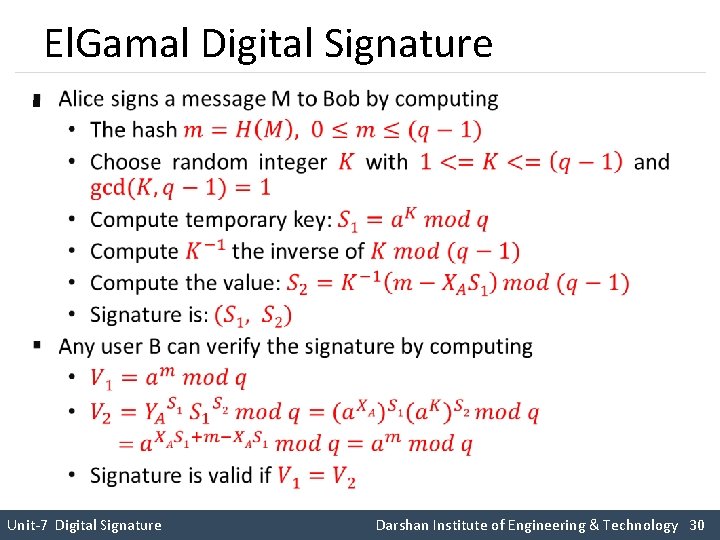
El. Gamal Digital Signature § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 30

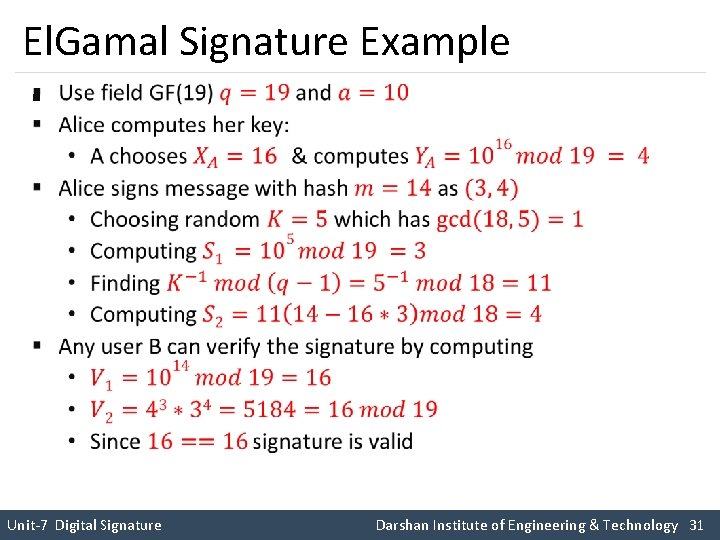
El. Gamal Signature Example § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 31

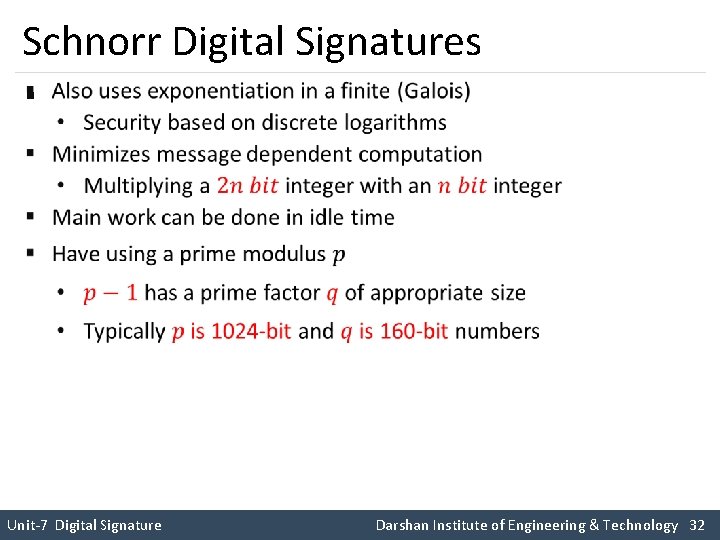
Schnorr Digital Signatures § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 32

Schnorr Key Setup § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 33

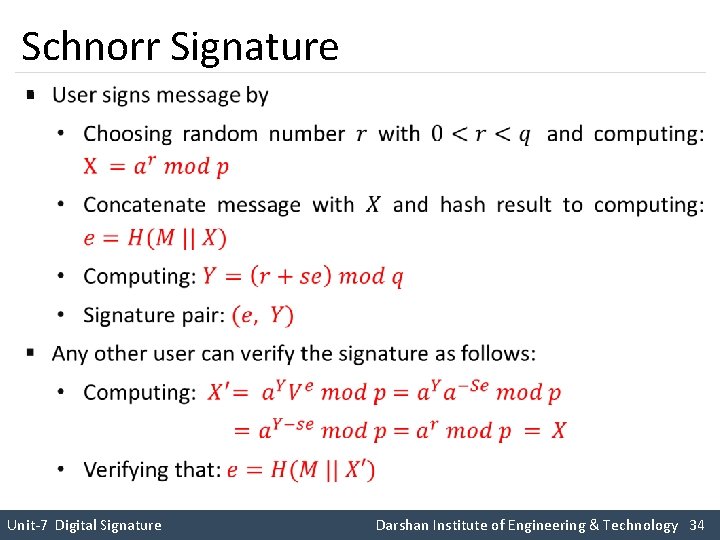
Schnorr Signature § Unit-7 Digital Signature Darshan Institute of Engineering & Technology 34

 Rekha sivapalan
Rekha sivapalan This picture
This picture Dr rekha gyanchand
Dr rekha gyanchand Rekha shukla joint secretary
Rekha shukla joint secretary Rekha vemuri
Rekha vemuri Rekha dahiya
Rekha dahiya Properties of digital signature
Properties of digital signature Digital signature authentication protocol
Digital signature authentication protocol Digital signature authentication protocol
Digital signature authentication protocol Java for pfms
Java for pfms Digital signature algorithm
Digital signature algorithm Rsa digital signature
Rsa digital signature Digital signature forgery
Digital signature forgery Cipher based message authentication code
Cipher based message authentication code Signature curve crossword
Signature curve crossword Digital signature
Digital signature Message authentication code
Message authentication code Dss digital signature
Dss digital signature Diffie hellman signature
Diffie hellman signature Integrity and authenticity
Integrity and authenticity Digital signature in cryptography and network security
Digital signature in cryptography and network security Digital signature authentication protocol
Digital signature authentication protocol Rsa digital signature
Rsa digital signature Attack on digital signature
Attack on digital signature Data encoding and modulation
Data encoding and modulation Healthtech mobility
Healthtech mobility Yang dimaksud dengan kewargaan digital
Yang dimaksud dengan kewargaan digital E-commerce: digital markets, digital goods
E-commerce: digital markets, digital goods Unique features of digital markets
Unique features of digital markets