UNIT4 Asymmetric Ciphers Prof R K Karangiya rekha







- Slides: 35

UNIT-4 Asymmetric Ciphers Prof. R. K. Karangiya rekha. karangiya@darshan. ac. in Information & Network Security (2170709) Darshan Institute of Engineering & Technology

Outline § Public Key Cryptosystems with Applications § Requirements and Cryptanalysis § RSA algorithm § RSA computational aspects and security § Diffie-Hillman Key Exchange algorithm § Man-in-Middle attack Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 2

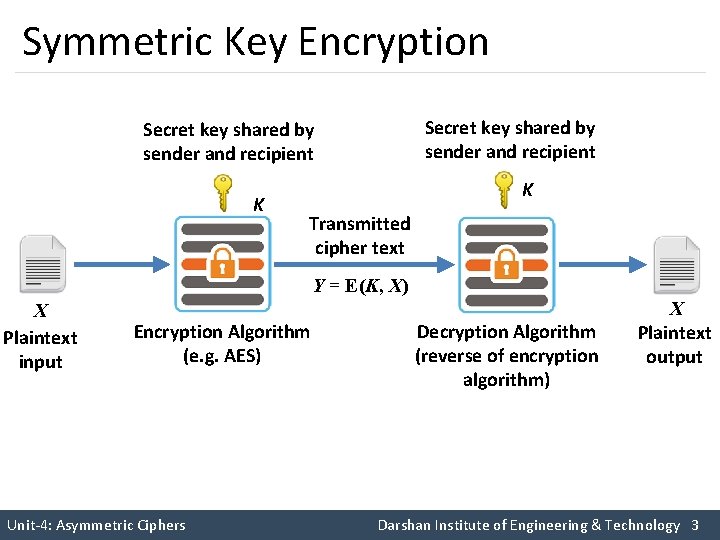
Symmetric Key Encryption Secret key shared by sender and recipient K Transmitted cipher text Y = E(K, X) X Plaintext input Encryption Algorithm (e. g. AES) Decryption Algorithm (reverse of encryption algorithm) X Plaintext output Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 3

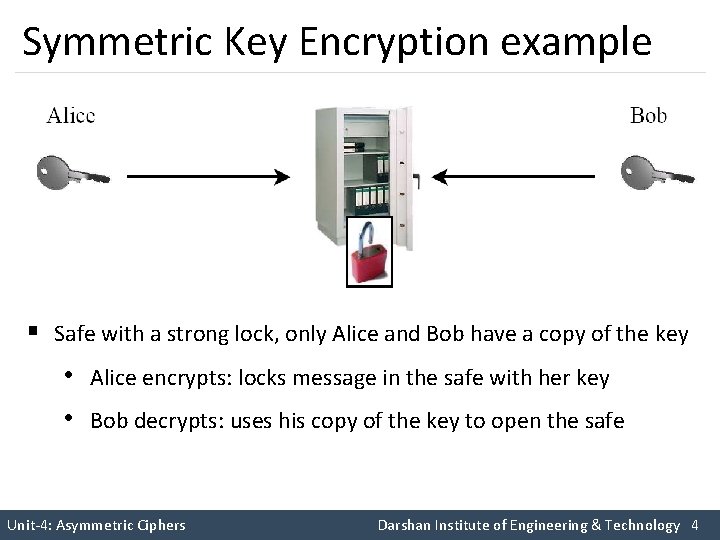
Symmetric Key Encryption example § Safe with a strong lock, only Alice and Bob have a copy of the key • Alice encrypts: locks message in the safe with her key • Bob decrypts: uses his copy of the key to open the safe Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 4

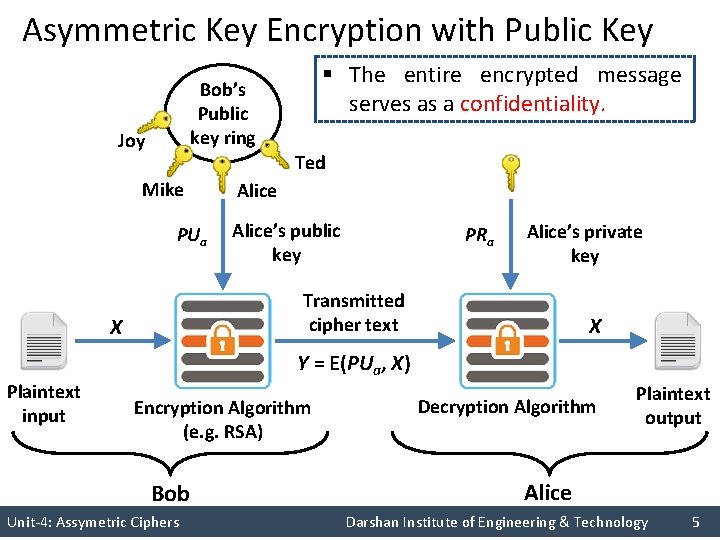
Asymmetric Key Encryption with Public Key § The entire encrypted message serves as a confidentiality. Bob’s Public key ring Joy Ted Mike PUa Alice’s public key PRa Alice’s private key Transmitted cipher text X X Y = E(PUa, X) Plaintext input Encryption Algorithm (e. g. RSA) Bob Decryption Algorithm Plaintext output Alice Unit-4: Assymetric Ciphers Darshan Institute of Engineering & Technology 5

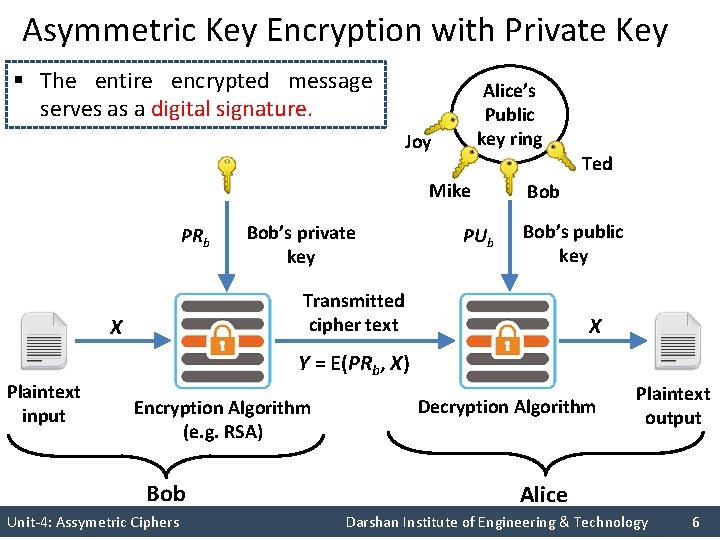
Asymmetric Key Encryption with Private Key § The entire encrypted message serves as a digital signature. Alice’s Public key ring Joy Ted Mike PRb Bob’s private key PUb Bob’s public key Transmitted cipher text X X Y = E(PRb, X) Plaintext input Encryption Algorithm (e. g. RSA) Bob Decryption Algorithm Plaintext output Alice Unit-4: Assymetric Ciphers Darshan Institute of Engineering & Technology 6

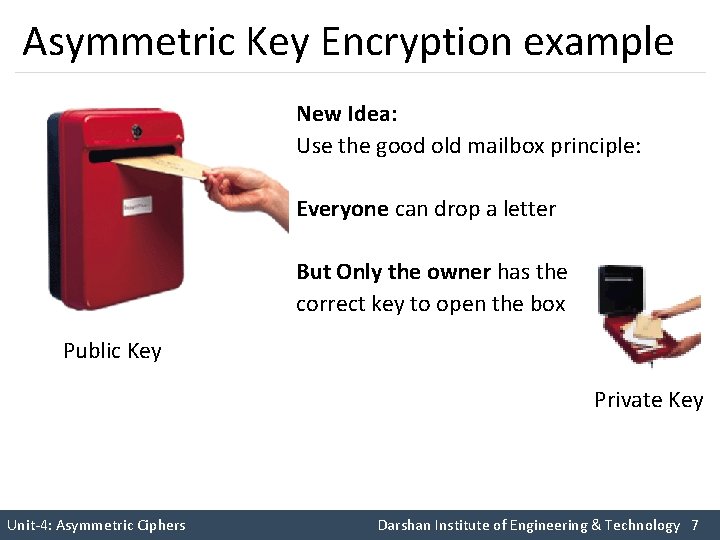
Asymmetric Key Encryption example New Idea: Use the good old mailbox principle: Everyone can drop a letter But Only the owner has the correct key to open the box Public Key Private Key Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 7

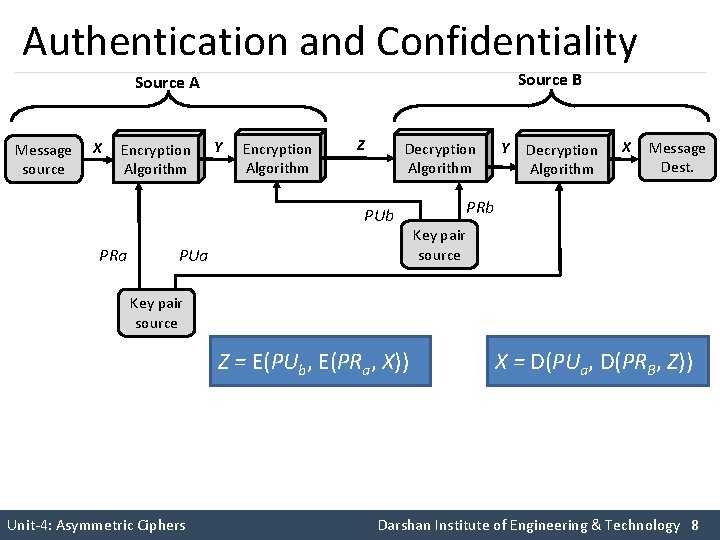
Authentication and Confidentiality Source B Source A Message source X Encryption Algorithm Y Encryption Algorithm Z Decryption Algorithm PUb PRa PUa Y Decryption Algorithm X Message Dest. PRb Key pair source Z = E(PUb, E(PRa, X)) X = D(PUa, D(PRB, Z)) Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 8

Applications for Public-Key Cryptosystems § Encryption/decryption: The sender encrypts a message with the recipient’s public key. § Digital signature: The sender “signs” a message with its private key. Signing is achieved by a cryptographic algorithm applied to the message or to a small block of data that is a function of the message. § Key exchange: Two sides cooperate to exchange a session key. Several different approaches are possible, involving the private key(s) of one or both parties. Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 9

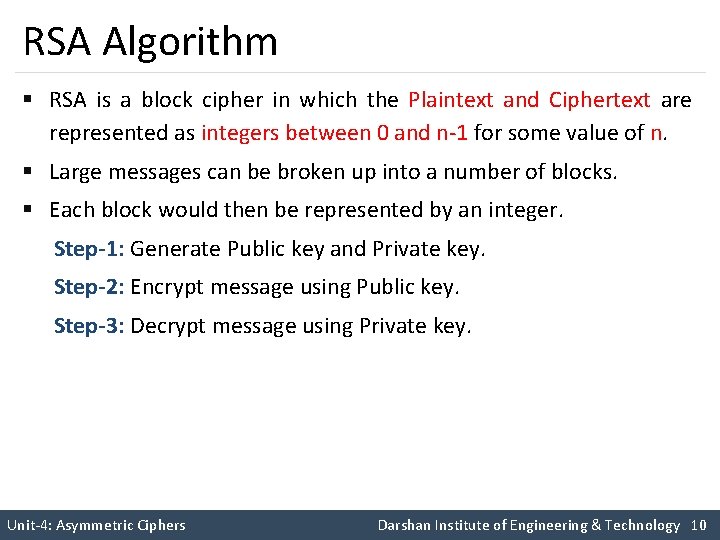
RSA Algorithm § RSA is a block cipher in which the Plaintext and Ciphertext are represented as integers between 0 and n-1 for some value of n. § Large messages can be broken up into a number of blocks. § Each block would then be represented by an integer. Step-1: Generate Public key and Private key. Step-2: Encrypt message using Public key. Step-3: Decrypt message using Private key. Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 10

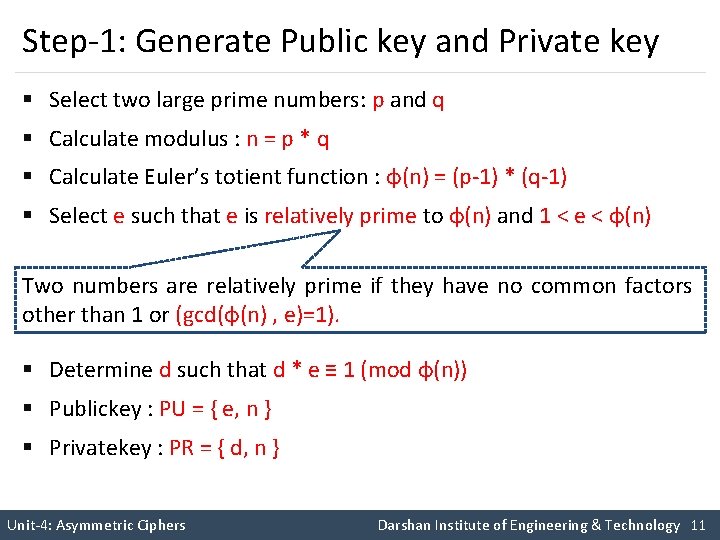
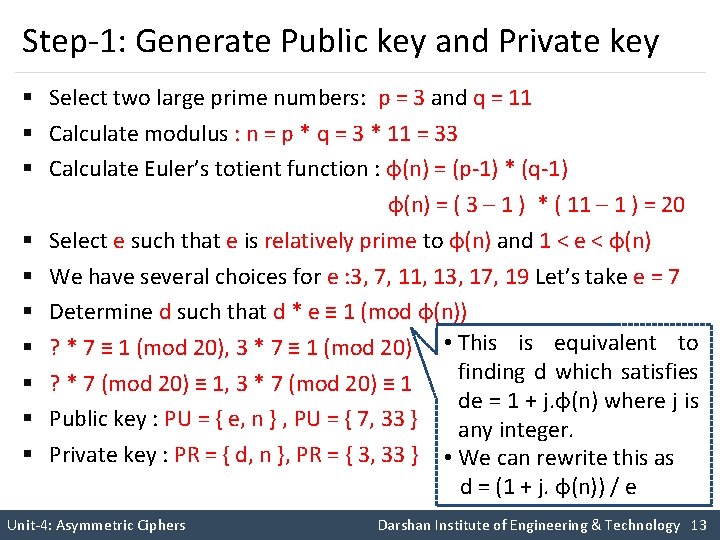
Step-1: Generate Public key and Private key § Select two large prime numbers: p and q § Calculate modulus : n = p * q § Calculate Euler’s totient function : φ(n) = (p-1) * (q-1) § Select e such that e is relatively prime to φ(n) and 1 < e < φ(n) Two numbers are relatively prime if they have no common factors other than 1 or (gcd(φ(n) , e)=1). § Determine d such that d * e ≡ 1 (mod φ(n)) § Publickey : PU = { e, n } § Privatekey : PR = { d, n } Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 11

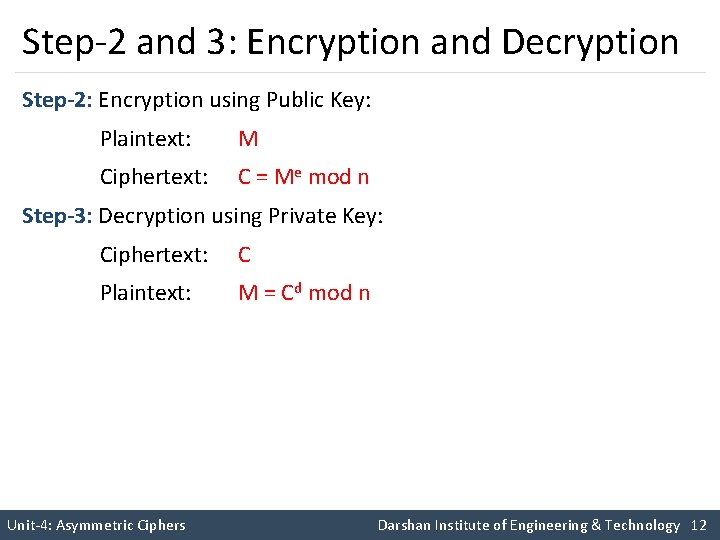
Step-2 and 3: Encryption and Decryption Step-2: Encryption using Public Key: Plaintext: M Ciphertext: C = Me mod n Step-3: Decryption using Private Key: Ciphertext: C Plaintext: M = Cd mod n Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 12

Step-1: Generate Public key and Private key § Select two large prime numbers: p = 3 and q = 11 § Calculate modulus : n = p * q = 3 * 11 = 33 § Calculate Euler’s totient function : φ(n) = (p-1) * (q-1) φ(n) = ( 3 – 1 ) * ( 11 – 1 ) = 20 § Select e such that e is relatively prime to φ(n) and 1 < e < φ(n) § We have several choices for e : 3, 7, 11, 13, 17, 19 Let’s take e = 7 § Determine d such that d * e ≡ 1 (mod φ(n)) § ? * 7 ≡ 1 (mod 20), 3 * 7 ≡ 1 (mod 20) • This is equivalent to finding d which satisfies § ? * 7 (mod 20) ≡ 1, 3 * 7 (mod 20) ≡ 1 de = 1 + j. φ(n) where j is § Public key : PU = { e, n } , PU = { 7, 33 } any integer. § Private key : PR = { d, n }, PR = { 3, 33 } • We can rewrite this as d = (1 + j. φ(n)) / e Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 13

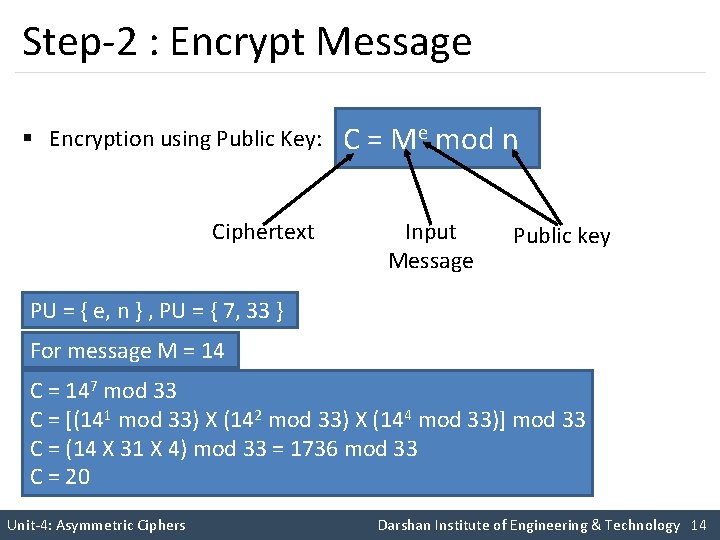
Step-2 : Encrypt Message § Encryption using Public Key: Ciphertext C = Me mod n Input Message Public key PU = { e, n } , PU = { 7, 33 } For message M = 14 C = 147 mod 33 C = [(141 mod 33) X (142 mod 33) X (144 mod 33)] mod 33 C = (14 X 31 X 4) mod 33 = 1736 mod 33 C = 20 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 14

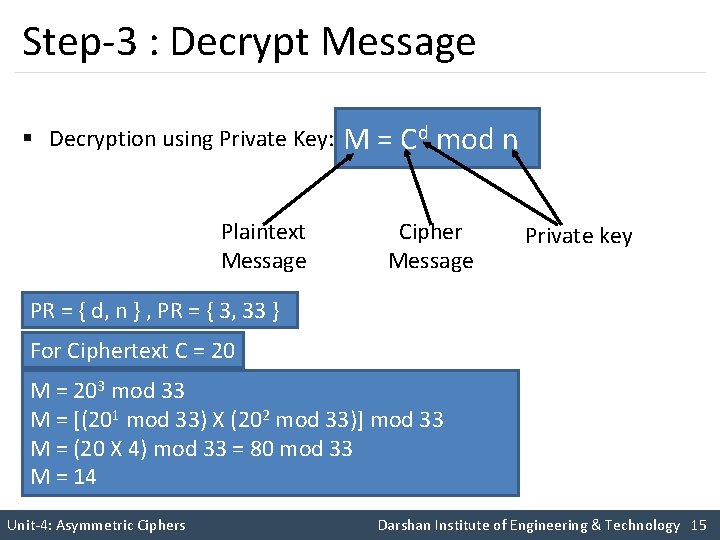
Step-3 : Decrypt Message § Decryption using Private Key: Plaintext Message M = Cd mod n Cipher Message Private key PR = { d, n } , PR = { 3, 33 } For Ciphertext C = 20 M = 203 mod 33 M = [(201 mod 33) X (202 mod 33)] mod 33 M = (20 X 4) mod 33 = 80 mod 33 M = 14 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 15

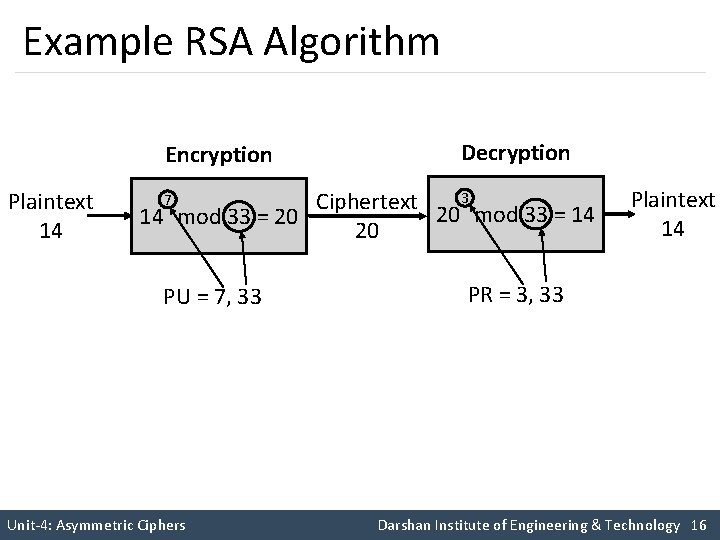
Example RSA Algorithm Encryption Plaintext 14 Decryption 3 Ciphertext 20 mod 33 = 14 14 mod 33 = 20 20 7 PU = 7, 33 Plaintext 14 PR = 3, 33 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 16

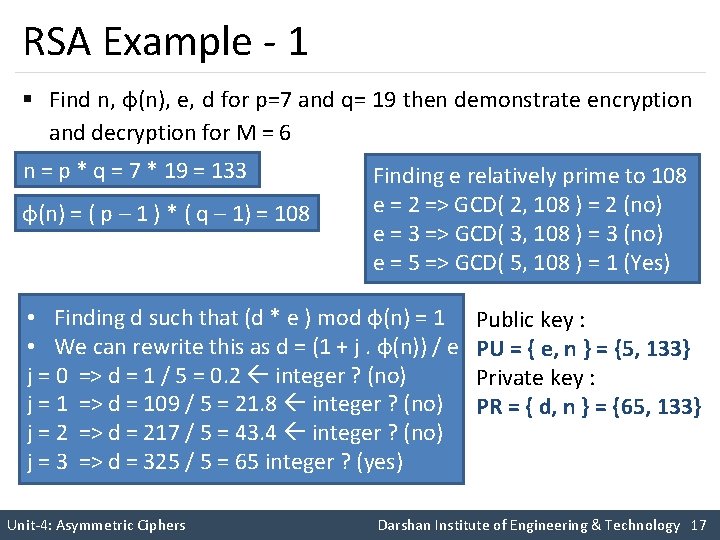
RSA Example - 1 § Find n, φ(n), e, d for p=7 and q= 19 then demonstrate encryption and decryption for M = 6 n = p * q = 7 * 19 = 133 φ(n) = ( p – 1 ) * ( q – 1) = 108 Finding e relatively prime to 108 e = 2 => GCD( 2, 108 ) = 2 (no) e = 3 => GCD( 3, 108 ) = 3 (no) e = 5 => GCD( 5, 108 ) = 1 (Yes) • Finding d such that (d * e ) mod φ(n) = 1 • We can rewrite this as d = (1 + j. φ(n)) / e j = 0 => d = 1 / 5 = 0. 2 integer ? (no) j = 1 => d = 109 / 5 = 21. 8 integer ? (no) j = 2 => d = 217 / 5 = 43. 4 integer ? (no) j = 3 => d = 325 / 5 = 65 integer ? (yes) Public key : PU = { e, n } = {5, 133} Private key : PR = { d, n } = {65, 133} Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 17

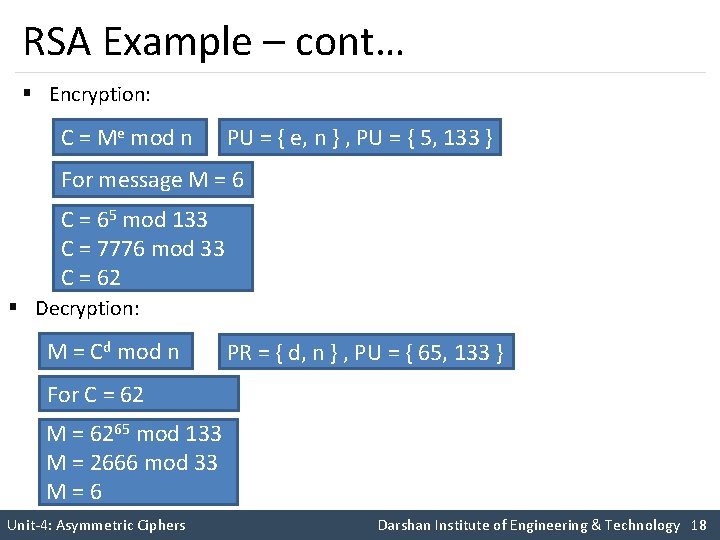
RSA Example – cont… § Encryption: C = Me mod n PU = { e, n } , PU = { 5, 133 } For message M = 6 C = 65 mod 133 C = 7776 mod 33 C = 62 § Decryption: M = Cd mod n PR = { d, n } , PU = { 65, 133 } For C = 62 M = 6265 mod 133 M = 2666 mod 33 M = 6 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 18

RSA Example - 2 § P and Q are two prime numbers. P=7, and Q=17. Take public key E=5. If plain text value is 10, then what will be cipher text value according to RSA algorithm? § n = 119 § φ(n) = 96 § e = 5 § d = 77 § PU = { 5, 119 } § PR = {77, 119} § C = 105 mod 119 => C = 40 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 19

RSA Example - 3 § P and Q are two prime numbers. P=17, and Q=11. If plain text value is 88, then what will be cipher text value according to RSA algorithm? § n = 187 § φ(n) = 160 § e = 7 § d = 23 § PU = { 7, 187 } § PR = {23, 187} § C = 887 mod 187 => C = 11 Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 20

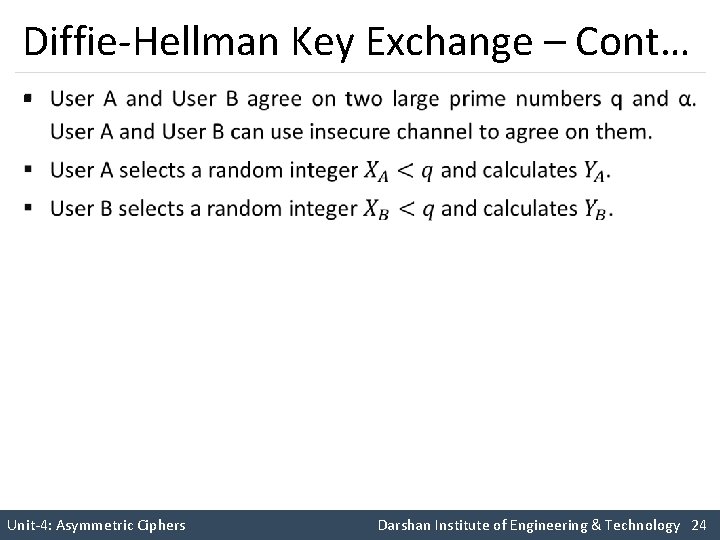
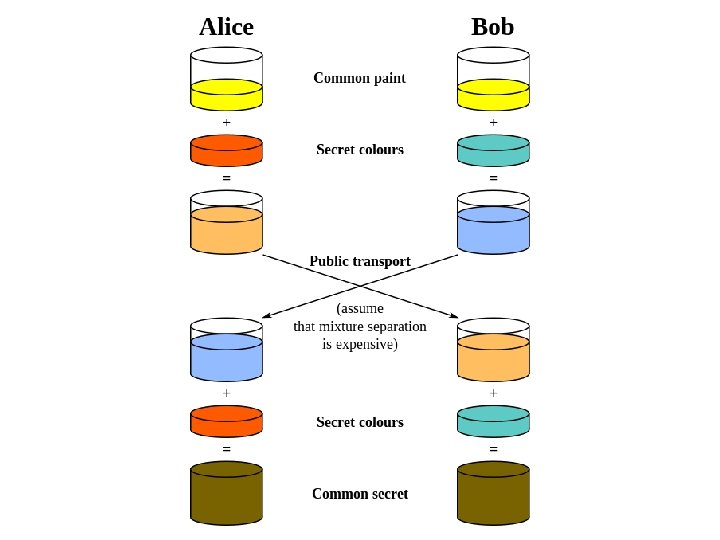
Diffie-Hellman key Exchange § The purpose of the Diffie-Hellman algorithm is to enable two users to securely exchange a key that can be used for subsequent encryption of message. § The effectiveness of an algorithm is depends on the difficulty of computing discrete logarithms. Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 21

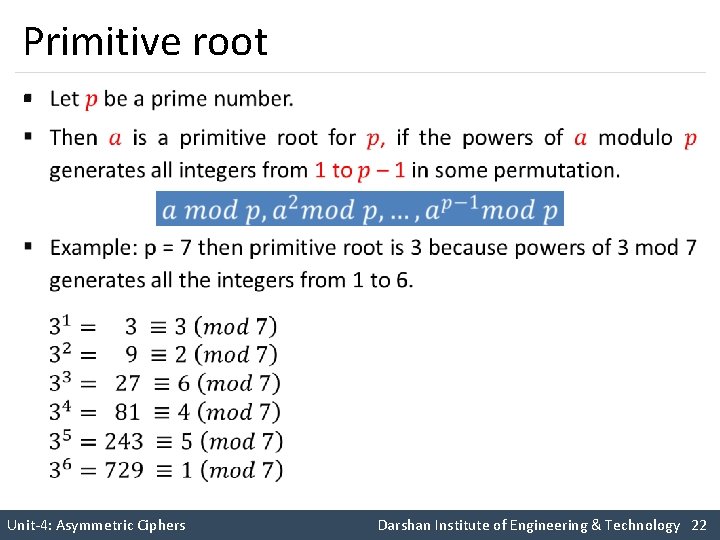
Primitive root § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 22

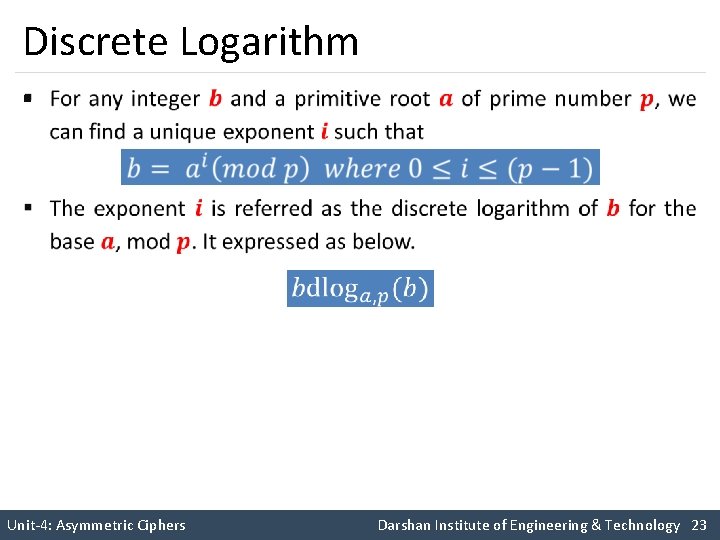
Discrete Logarithm § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 23

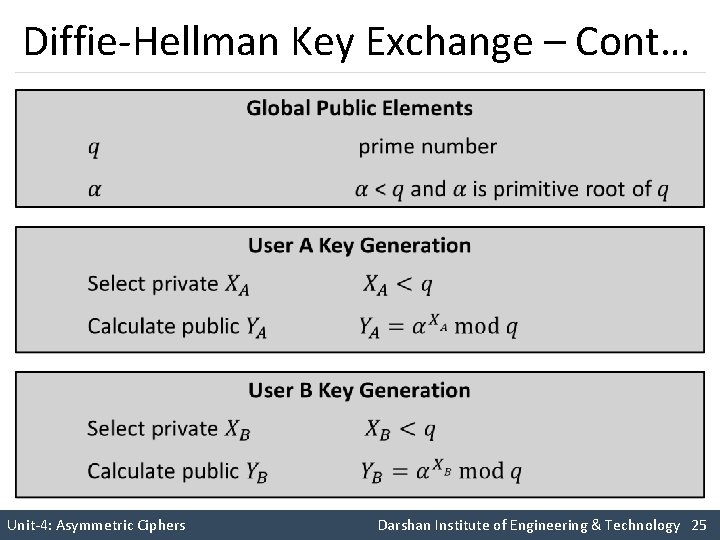
Diffie-Hellman Key Exchange – Cont… § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 24

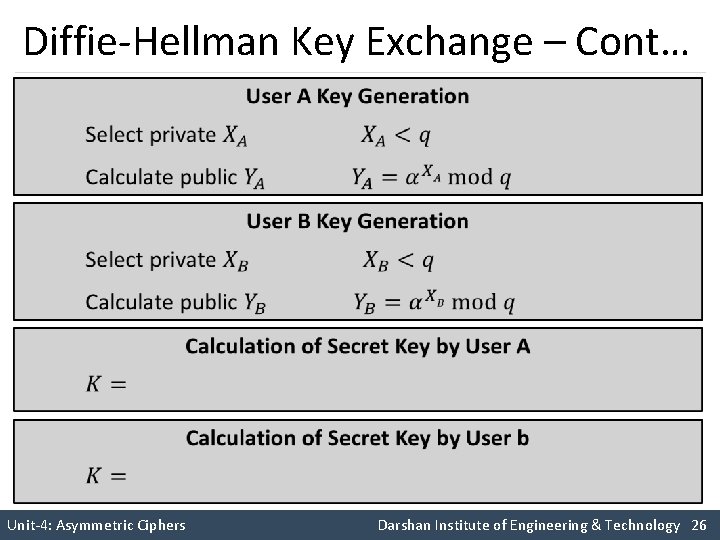
Diffie-Hellman Key Exchange – Cont… Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 25

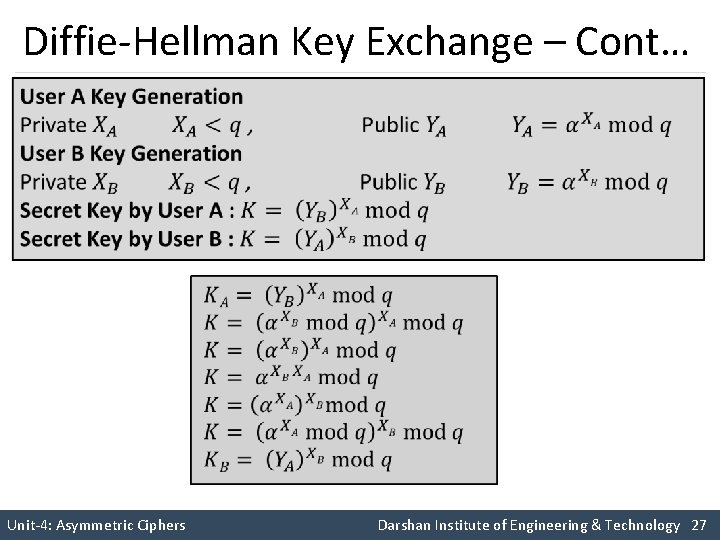
Diffie-Hellman Key Exchange – Cont… Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 26

Diffie-Hellman Key Exchange – Cont… Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 27


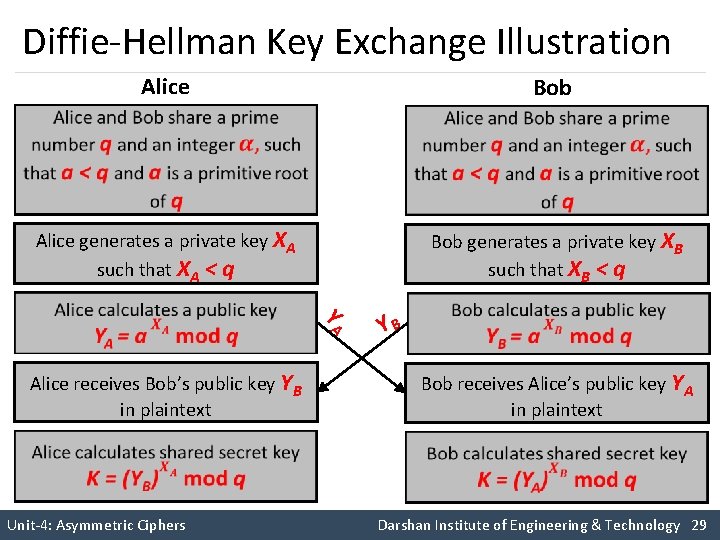
Diffie-Hellman Key Exchange Illustration Alice Bob Alice generates a private key XA such that XA < q Bob generates a private key XB such that XB < q Y A YB Alice receives Bob’s public key YB in plaintext Bob receives Alice’s public key YA in plaintext Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 29

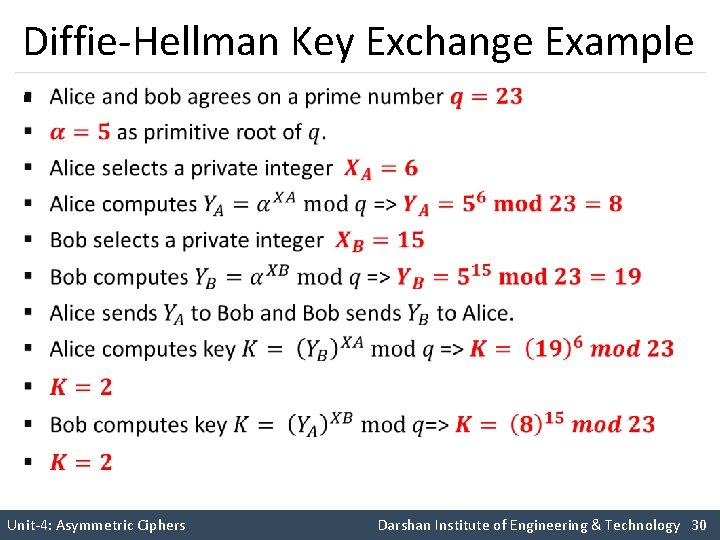
Diffie-Hellman Key Exchange Example § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 30

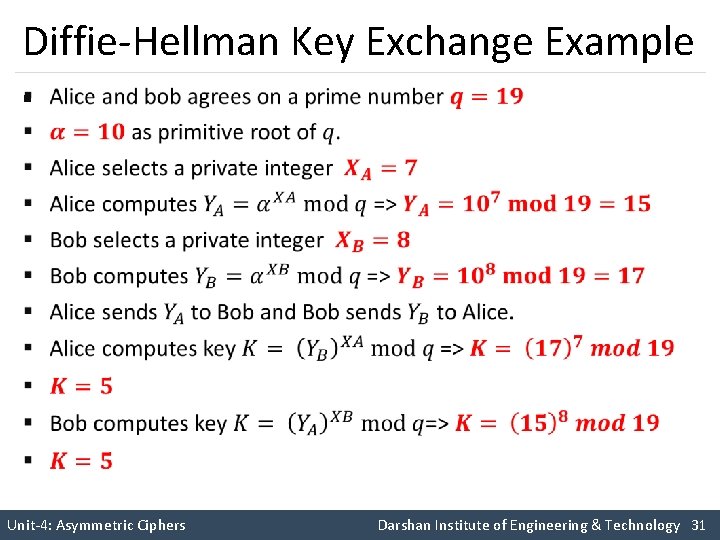
Diffie-Hellman Key Exchange Example § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 31

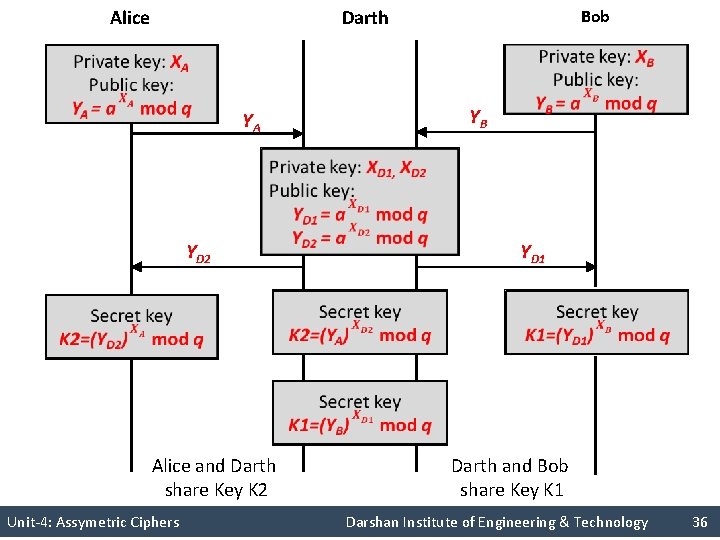
Man in the middle attack § Unit-4: Asymmetric Ciphers Darshan Institute of Engineering & Technology 33

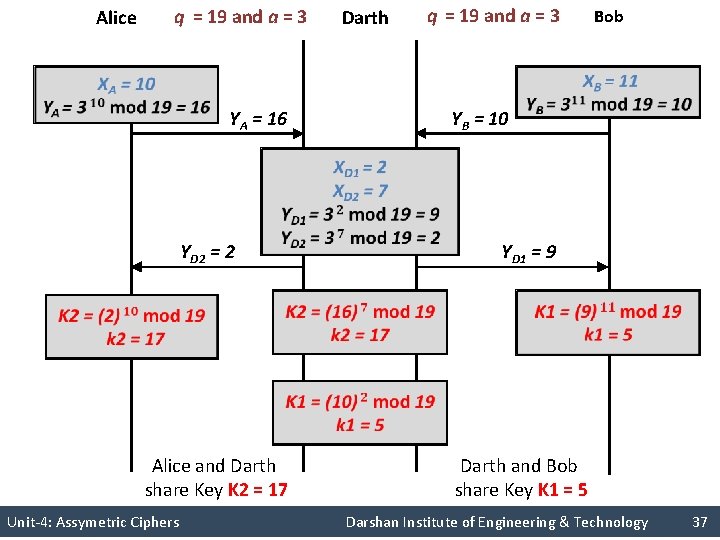
Alice Darth Bob YB YA YD 1 YD 2 Alice and Darth share Key K 2 Darth and Bob share Key K 1 Unit-4: Assymetric Ciphers Darshan Institute of Engineering & Technology 36

Alice q = 19 and a = 3 Darth q = 19 and a = 3 Bob YA = 16 YB = 10 YD 2 = 2 YD 1 = 9 Alice and Darth share Key K 2 = 17 Darth and Bob share Key K 1 = 5 Unit-4: Assymetric Ciphers Darshan Institute of Engineering & Technology 37
