UNIT V Advanced Wireless Technologies Vo IP Architecture


























- Slides: 63

UNIT V: Advanced Wireless Technologies: Vo. IP Architecture and Applications, Vehicular network, Delay tolerant network. 6 Hrs 10 -Jan-22 1

Vo. IP Architecture and Applications: Voice Over Internet Protocol (Vo. IP) Issues and Challenges William Mc. Crum 10 -Jan-22 2

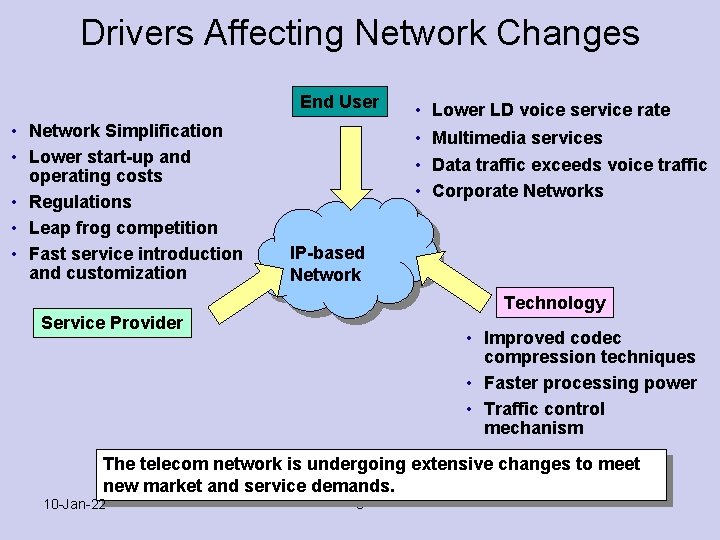
Drivers Affecting Network Changes End User • Network Simplification • Lower start-up and operating costs • Regulations • Leap frog competition • Fast service introduction and customization • Lower LD voice service rate • Multimedia services • Data traffic exceeds voice traffic • Corporate Networks IP-based Network Technology Service Provider • Improved codec compression techniques • Faster processing power • Traffic control mechanism The telecom network is undergoing extensive changes to meet new market and service demands. 10 -Jan-22 3

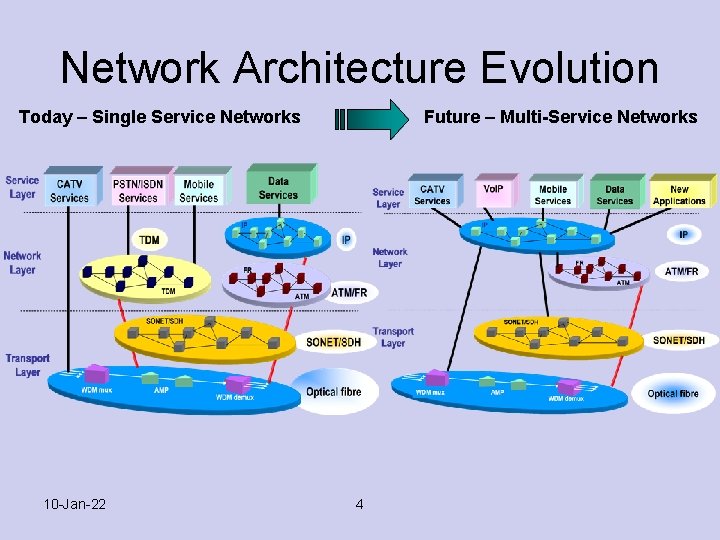
Network Architecture Evolution Today – Single Service Networks 10 -Jan-22 Future – Multi-Service Networks 4

Enters Vo. IP…What is it? • Many names, different meaning to different people: – Soft-switching – Next Generation Voice Network – IP Telephony – Voice over Internet Protocol – Voice over Packet – IP Communications Various implementations of Vo. IP systems and user expectations. 10 -Jan-22 5

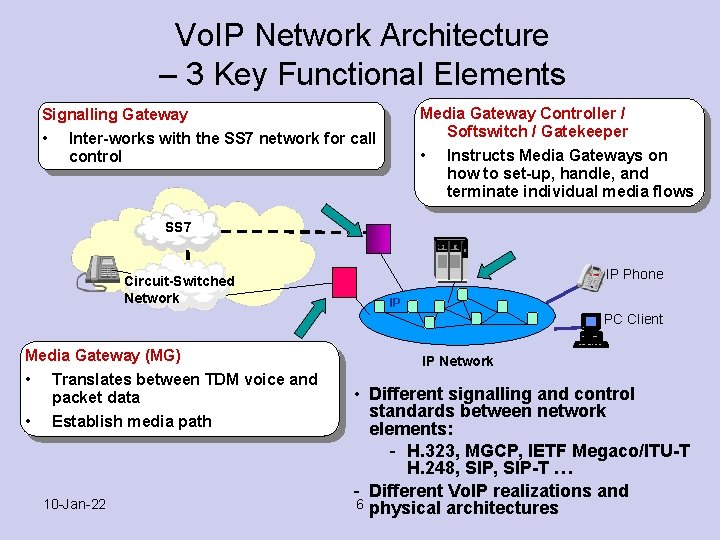
Vo. IP Network Architecture – 3 Key Functional Elements Media Gateway Controller / Softswitch / Gatekeeper • Instructs Media Gateways on how to set-up, handle, and terminate individual media flows Signalling Gateway • Inter-works with the SS 7 network for call control SS 7 Circuit-Switched Network IP Phone IP PC Client Media Gateway (MG) • Translates between TDM voice and packet data • Establish media path 10 -Jan-22 IP Network • Different signalling and control standards between network elements: - H. 323, MGCP, IETF Megaco/ITU-T H. 248, SIP-T … - Different Vo. IP realizations and 6 physical architectures

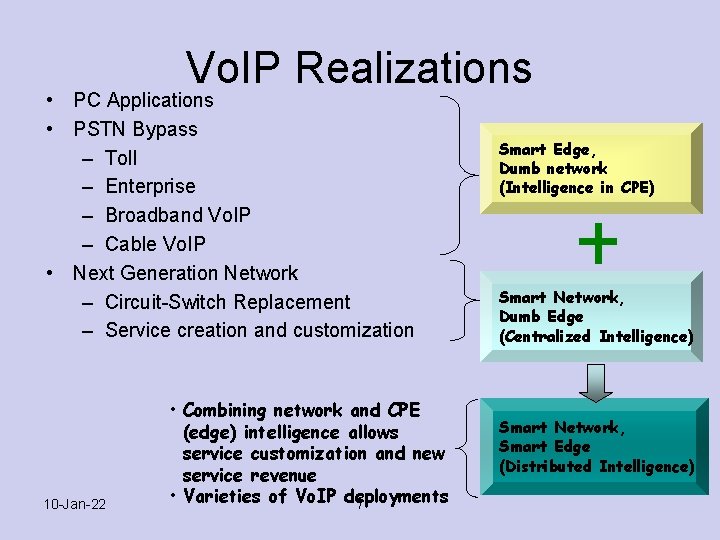
Vo. IP Realizations • PC Applications • PSTN Bypass – Toll – Enterprise – Broadband Vo. IP – Cable Vo. IP • Next Generation Network – Circuit-Switch Replacement – Service creation and customization 10 -Jan-22 • Combining network and CPE (edge) intelligence allows service customization and new service revenue • Varieties of Vo. IP deployments 7 Smart Edge, Dumb network (Intelligence in CPE) Smart Network, Dumb Edge (Centralized Intelligence) Smart Network, Smart Edge (Distributed Intelligence)

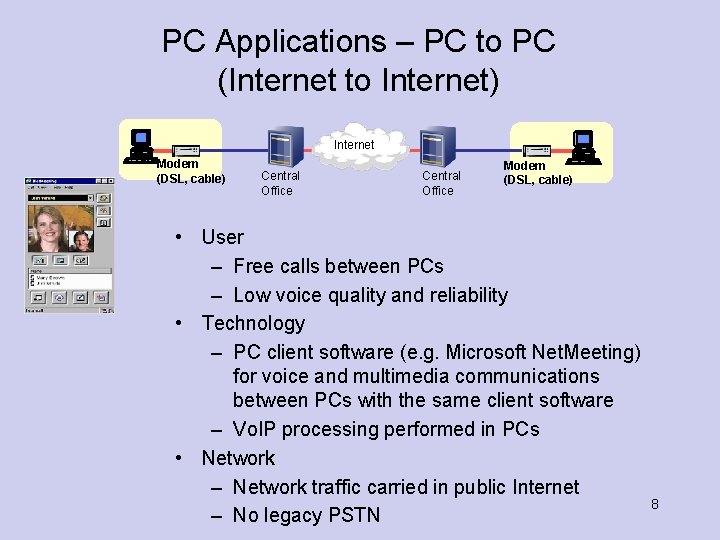
PC Applications – PC to PC (Internet to Internet) Internet Modem (DSL, cable) Central Office Modem (DSL, cable) • User – Free calls between PCs – Low voice quality and reliability • Technology – PC client software (e. g. Microsoft Net. Meeting) for voice and multimedia communications between PCs with the same client software – Vo. IP processing performed in PCs • Network – Network traffic carried in public Internet – No legacy PSTN 8

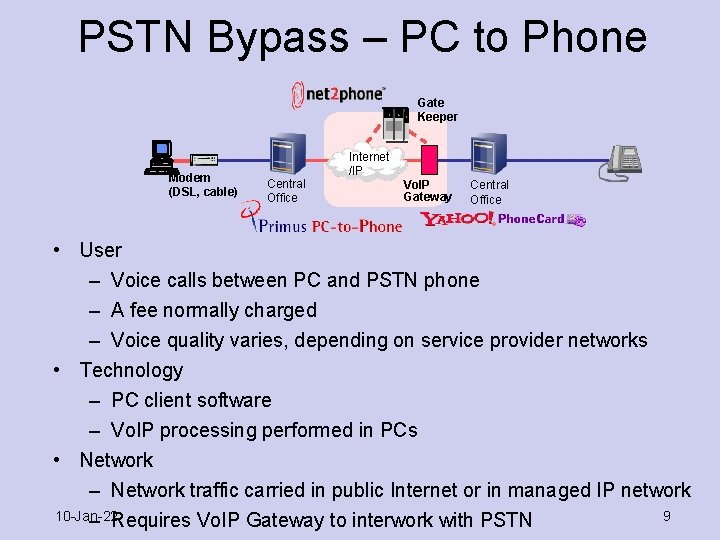
PSTN Bypass – PC to Phone Gate Keeper Modem (DSL, cable) Central Office Internet /IP Vo. IP Gateway Central Office • User – Voice calls between PC and PSTN phone – A fee normally charged – Voice quality varies, depending on service provider networks • Technology – PC client software – Vo. IP processing performed in PCs • Network – Network traffic carried in public Internet or in managed IP network 10 -Jan-22 9 – Requires Vo. IP Gateway to interwork with PSTN

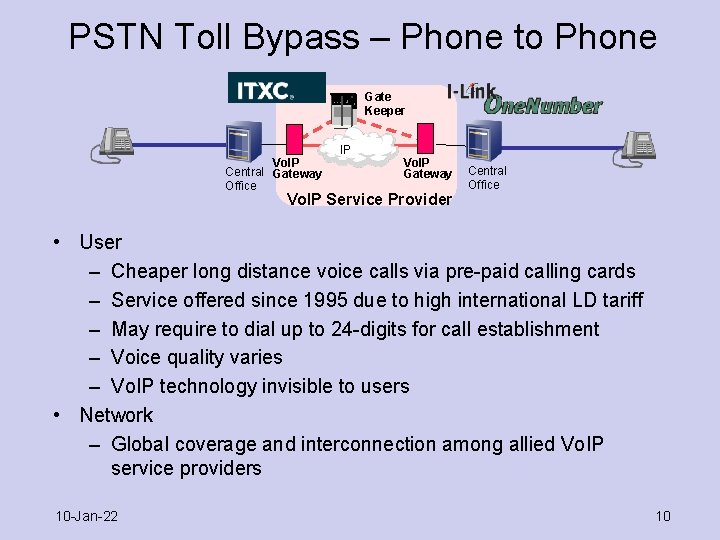
PSTN Toll Bypass – Phone to Phone Gate Keeper Vo. IP Central Gateway Office IP Vo. IP Gateway Vo. IP Service Provider Central Office • User – Cheaper long distance voice calls via pre-paid calling cards – Service offered since 1995 due to high international LD tariff – May require to dial up to 24 -digits for call establishment – Voice quality varies – Vo. IP technology invisible to users • Network – Global coverage and interconnection among allied Vo. IP service providers 10 -Jan-22 10

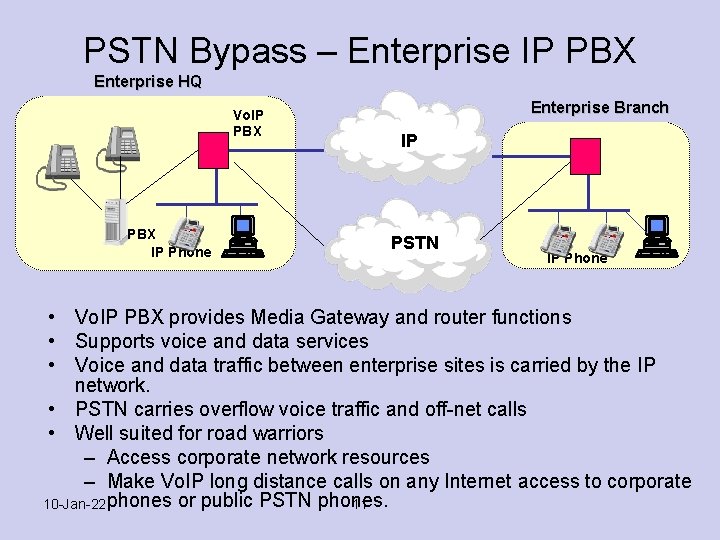
PSTN Bypass – Enterprise IP PBX Enterprise HQ Vo. IP PBX IP Phone Enterprise Branch IP PSTN IP Phone • Vo. IP PBX provides Media Gateway and router functions • Supports voice and data services • Voice and data traffic between enterprise sites is carried by the IP network. • PSTN carries overflow voice traffic and off-net calls • Well suited for road warriors – Access corporate network resources – Make Vo. IP long distance calls on any Internet access to corporate 10 -Jan-22 phones or public PSTN phones. 11

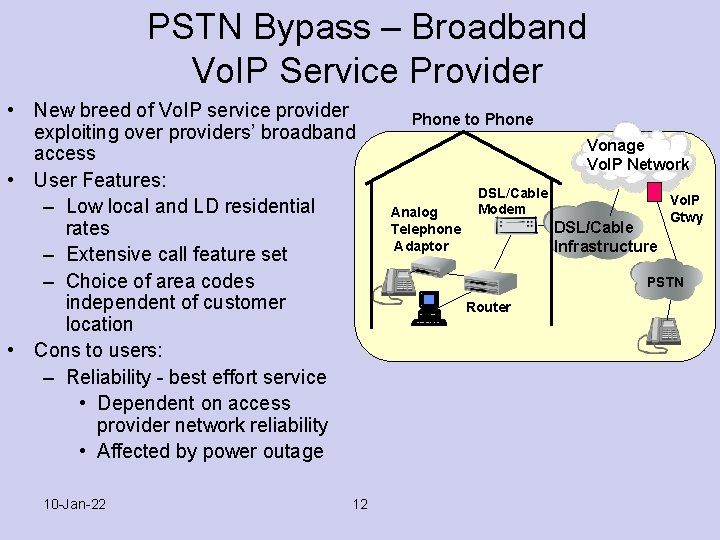
PSTN Bypass – Broadband Vo. IP Service Provider • New breed of Vo. IP service provider exploiting over providers’ broadband access • User Features: – Low local and LD residential rates – Extensive call feature set – Choice of area codes independent of customer location • Cons to users: – Reliability - best effort service • Dependent on access provider network reliability • Affected by power outage 10 -Jan-22 12 Phone to Phone Vonage Vo. IP Network Analog Telephone Adaptor DSL/Cable Modem DSL/Cable Infrastructure Vo. IP Gtwy PSTN Router

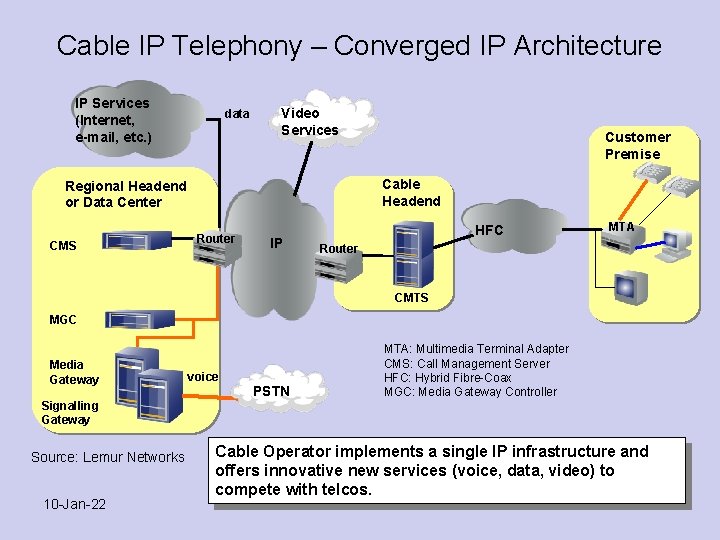
Cable IP Telephony – Converged IP Architecture IP Services (Internet, e-mail, etc. ) data Video Services Customer Premise Cable Headend Regional Headend or Data Center CMS Router IP HFC MTA Router CMTS MGC Media Gateway voice MTA: Multimedia Terminal Adapter CMS: Call Management Server HFC: Hybrid Fibre-Coax MGC: Media Gateway Controller PSTN Signalling Gateway Source: Lemur Networks 10 -Jan-22 Cable Operator implements a single IP infrastructure and offers innovative new services (voice, data, video) to compete with telcos. 13

Vo. IP Examples • • • Xbox Voice Windows messenger AOL Instant Messenger Motorola Phone Adapter (Vonage) Cisco Phone 10 -Jan-22 14

In brief: • Vo. IP is one of many higher-level communications capabilites among devices connected to the Internet. • Vo. IP is not an application. • Vo. IP is a capability that is part of many applications. • Vo. IP capabilities are already pervasive. – Microsoft Windows Messenger (part of XP) – AOL Instant Messenger – Xbox and Sony Playstation 10 -Jan-22 15

Vehicular Networks Why Vehicular Networks: Emergence of Vehicular Networks Applications: Congestion detection, Vehicle platooning, Road hazard warning, Collision alert, Stoplight, assistant, Toll collection, Deceleration warning, Emergency vehicle warning, Border clearance, Traction updates, Flat tire warning, Merge assistance , etc. Adversaries: Greedy drivers, Snoops, Pranksters, Industrial Insiders, Malicious Attackers, etc. Attacks: Denial of Service (Do. S), Message Suppression Attacks, Alteration Attacks, etc. Vehicular Network Challenges: Authentication vs. Privacy, Availability, Mobility, Key Distribution, Low Tolerance for Errors, Bootstrap, etc Ref: Challenges in Securing Vehicular Networks, Bryan Parno, Adrian Perrig, Carnegie Mellon University. 10 -Jan-22 16

Emergence of Vehicular Networks • In 1999, FCC allocated 5. 850 -5. 925 GHz band to promote safe and efficient highways – Intended for vehicle-to-vehicle and vehicle-to-infrastructure communication • Emerging radio standard for Dedicated Short-Range Communications (DSRC) – Based on an extension of 802. 11 • Must consider security, or these networks will create more problems than they solve 10 -Jan-22 17

Why Vehicular Networks? • Safety – On US highways (2014): • 42, 800 Fatalities, 12. 8 Million Injuries • ~$230. 6 Billion cost to society • Efficiency – Traffic jams waste time and fuel – In 2013, US drivers lost a total of 13. 5 billion hours and 15. 7 billion gallons of fuel to traffic congestion • Profit – Safety features and high-tech devices have become product differentiators 10 -Jan-22 18

Applications • Congestion detection • Deceleration warning • Vehicle platooning • Emergency vehicle warning • Road hazard warning • Collision alert • Stoplight assistant • Toll collection • Border clearance • Traction updates • Flat tire warning • Merge assistance 10 -Jan-22 19

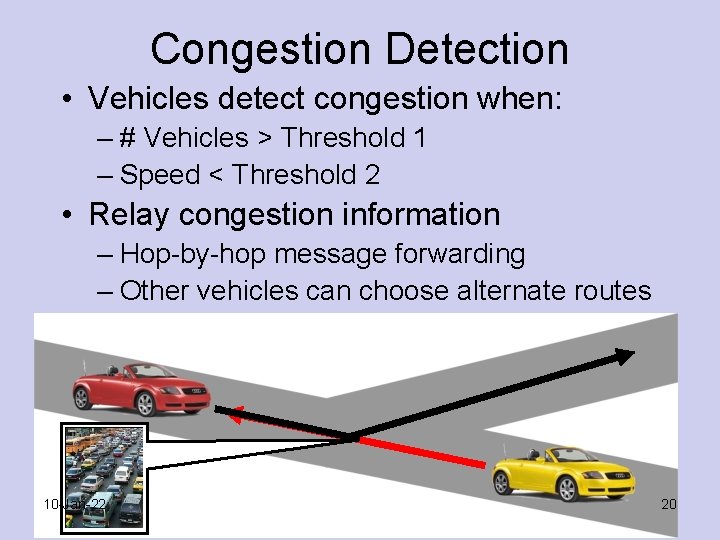
Congestion Detection • Vehicles detect congestion when: – # Vehicles > Threshold 1 – Speed < Threshold 2 • Relay congestion information – Hop-by-hop message forwarding – Other vehicles can choose alternate routes 10 -Jan-22 20

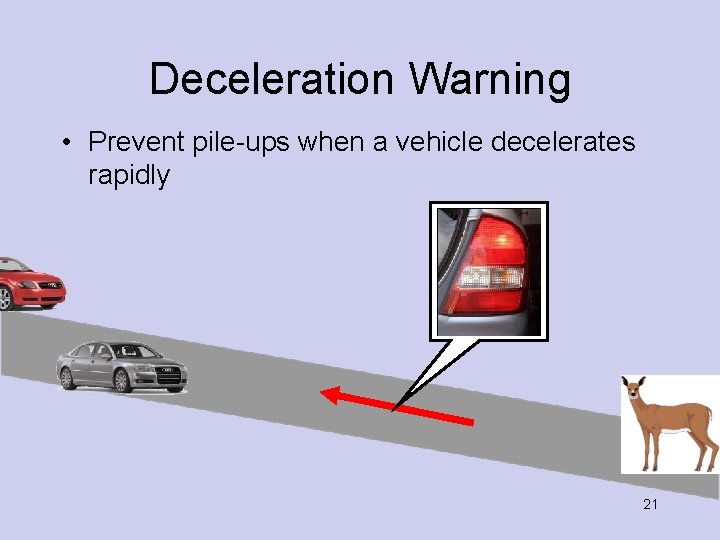
Deceleration Warning • Prevent pile-ups when a vehicle decelerates rapidly 21

Why Security? • Adding security as an afterthought is rarely pretty • Utility and ubiquity of vehicular networks will make them likely targets for attack • Attacks may have deadly consequences 10 -Jan-22 22

Outline • • Introduction Applications Adversaries and Attacks Vehicular Network Challenges Properties Supporting Security Primitives Related Work & Conclusions 10 -Jan-22 23

Adversaries • Greedy drivers 10 -Jan-22 24

Adversaries • • • Greedy drivers Snoops (watch secretly) Pranksters (practical Joking) Industrial Insiders (Corporate officers) Malicious Attackers 10 -Jan-22 25

Attacks • Denial of Service (Do. S) – Overwhelm computational or network capacity – Dangerous if users rely on the service • Message Suppression Attacks – Drop congestion alerts • Fabrication – Lie about congestion ahead or lie about identity • Alteration Attacks – Replay transmissions to simulate congestion 10 -Jan-22 26

Outline • • Introduction Applications Adversaries and Attacks Vehicular Network Challenges – – – Authentication vs. Privacy Availability Mobility Key Distribution Low Tolerance for Errors Bootstrap • Properties Supporting Security • Security Primitives • Related Work & Conclusions 10 -Jan-22 27

Challenges: Authentication vs. Privacy • Each vehicle should only have one identity – Prevents Sybil attacks (e. g. , spoofed congestion) – Allows use of external mechanisms (e. g. law enforcement) • Drivers value their privacy – Legal requirements vary from country to country – Vehicles today are only partially anonymous – Lack of privacy may lead to lack of security 10 -Jan-22 28

Challenges: Availability • Applications will require real-time responses • Increases vulnerability to Do. S • Unreliable communication medium – Studies show only 50 -60% of vehicles in range will receive a vehicle’s broadcast 10 -Jan-22 29

Challenges: Mobility • Mobility patterns will exhibit strong correlations • Transient neighborhood – Many neighbors will only be encountered once, ever – Makes reputation-based systems difficult • Brief periods of connectivity – Vehicles may only be in range for seconds – Limits interaction between sender and receiver 10 -Jan-22 30

Challenges: Key Distribution • Manufacturers – Requires cooperation and interoperability – Users must trust all manufacturers • Government – MV License distribution – Handled at the state level, so also requires cooperation and interoperability – Running a Certificate Authority is non-trivial (Seriously) 10 -Jan-22 31

Challenges: Low Tolerance for Errors • Strong need for resiliency – With 200 million cars in the US, if 5% use an application that works 99. 99999% of the time, still more likely to fail on some car – Life-and-death applications must be resilient to occasional failures • Focus on prevention, rather than detection & recovery – Safety-related applications may not have margin for driver reaction time 10 -Jan-22 32

Challenges: Bootstrap • Initially, only a small number of vehicles will have DSRC • Limited support deployment of infrastructure • Ad hoc network protocols allow manufacturers to incorporate security without deviating from their business model 10 -Jan-22 33

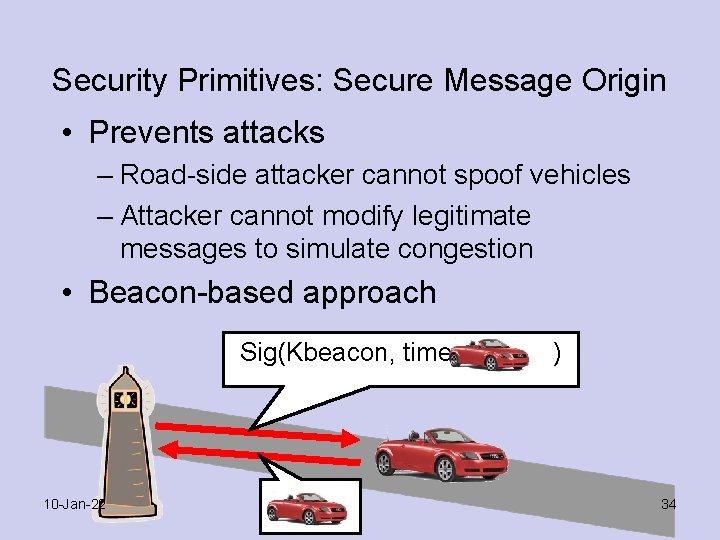
Security Primitives: Secure Message Origin • Prevents attacks – Road-side attacker cannot spoof vehicles – Attacker cannot modify legitimate messages to simulate congestion • Beacon-based approach Sig(Kbeacon, time, 10 -Jan-22 ) 34

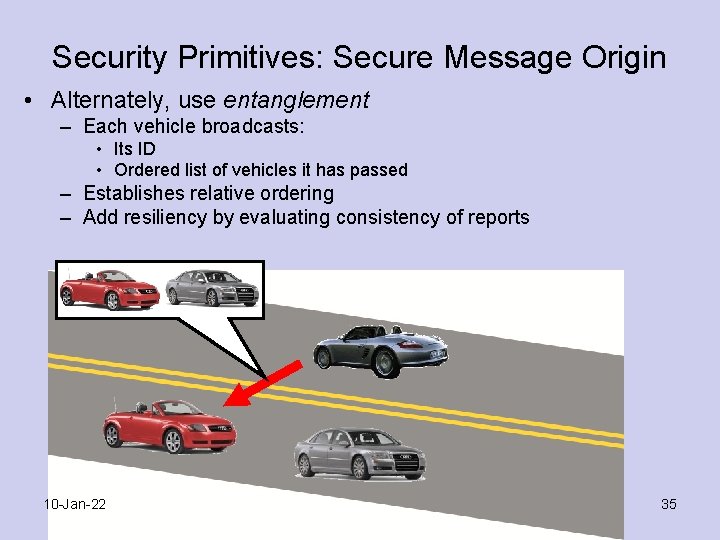
Security Primitives: Secure Message Origin • Alternately, use entanglement – Each vehicle broadcasts: • Its ID • Ordered list of vehicles it has passed – Establishes relative ordering – Add resiliency by evaluating consistency of reports 10 -Jan-22 35

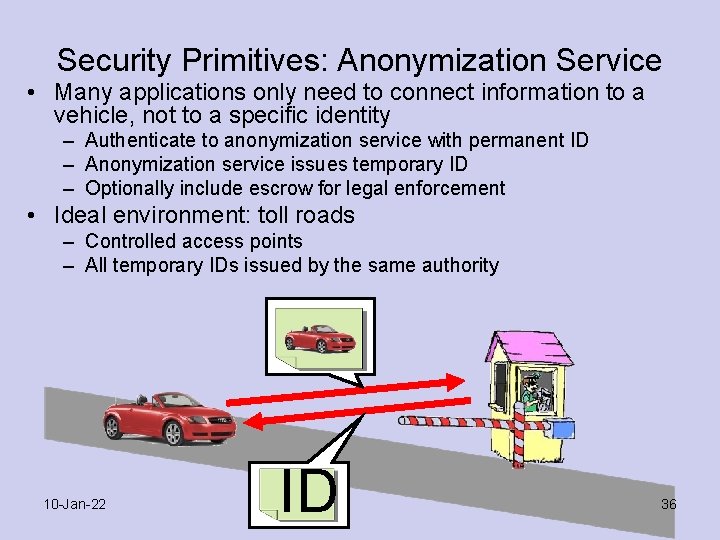
Security Primitives: Anonymization Service • Many applications only need to connect information to a vehicle, not to a specific identity – Authenticate to anonymization service with permanent ID – Anonymization service issues temporary ID – Optionally include escrow for legal enforcement • Ideal environment: toll roads – Controlled access points – All temporary IDs issued by the same authority 10 -Jan-22 ID 36

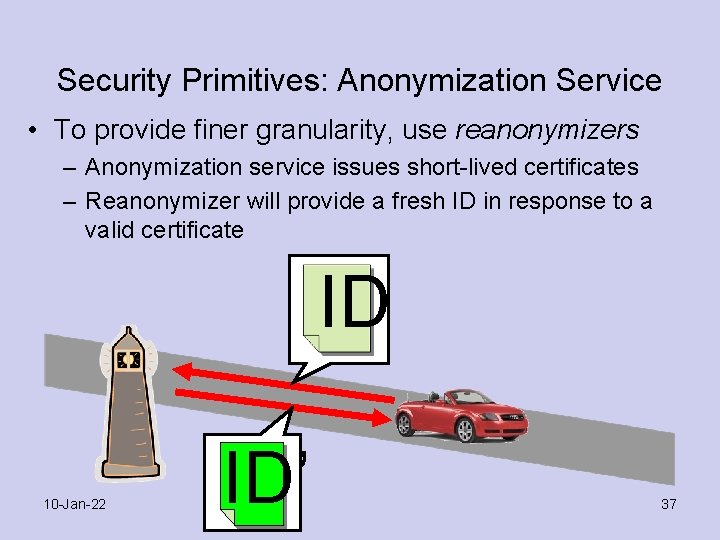
Security Primitives: Anonymization Service • To provide finer granularity, use reanonymizers – Anonymization service issues short-lived certificates – Reanonymizer will provide a fresh ID in response to a valid certificate ID 10 -Jan-22 ID’ 37

Additional Security Primitives • Secure Aggregation – Securely count vehicles to report congestion • Key Establishment – Temporary session keys for platooning or automatic cruise control • Message Authentication and Freshness – Prevent alteration and replay attacks 10 -Jan-22 38

Delay-Tolerant Networks (DTNs) 10 -Jan-22 39

Today’s Internet • Successful at interconnecting communication devices across the globe • Based on TCP/IP protocol suite and wired links • Connected in end-to-end, low-delay paths between sources and destinations • Low error rates and relatively symmetric bidirectional data rates 10 -Jan-22 40

Evolving Wireless Networks Outside the Internet • Independent networks, each supporting specialized communication requirements and adapted to a particular homogeneous communication region • Support long and variable delays, arbitrarily long periods of link disconnection, high error rates, and large bidirectional data-rate asymmetries 10 -Jan-22 41

Evolving Wireless Networks Outside the Internet • Examples – Terrestrial civilian networks connecting mobile wireless devices – Wireless military battlefield networks connecting troops, aircraft, satellites, and sensors – Outer-space networks, such as the Inter. Pla. Netary (IPN) Internet project • Require the intervention of an agent that can translate between incompatible networks characteristics and act as a buffer for mismatched network delays 10 -Jan-22 42

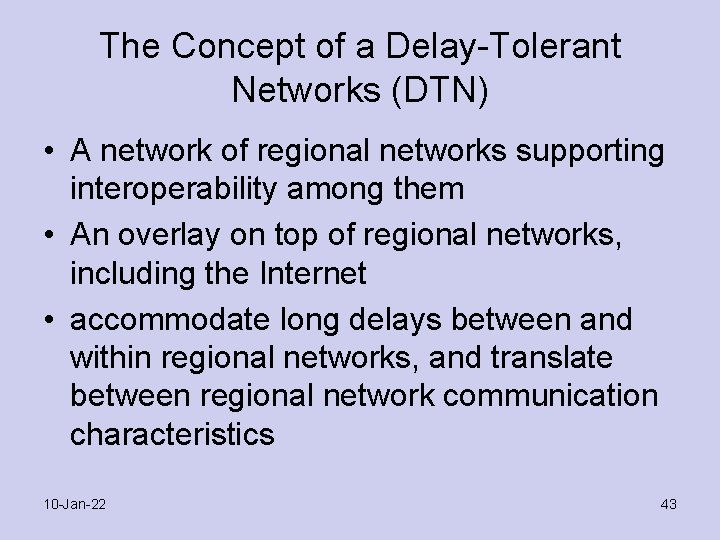
The Concept of a Delay-Tolerant Networks (DTN) • A network of regional networks supporting interoperability among them • An overlay on top of regional networks, including the Internet • accommodate long delays between and within regional networks, and translate between regional network communication characteristics 10 -Jan-22 43

Concept Delay-Tolerant Network (DTN) – is an overlay on top of regional networks • built on top of region-specific lower layers • messages are called bundles 10 -Jan-22 44

Concept Delay-Tolerant Network (DTN) – is a network of regional networks 10 -Jan-22 45

Concept Delay-Tolerant Network (DTN) – was originally designed to support the Inter. Planetary Internet (IPN) 10 -Jan-22 46

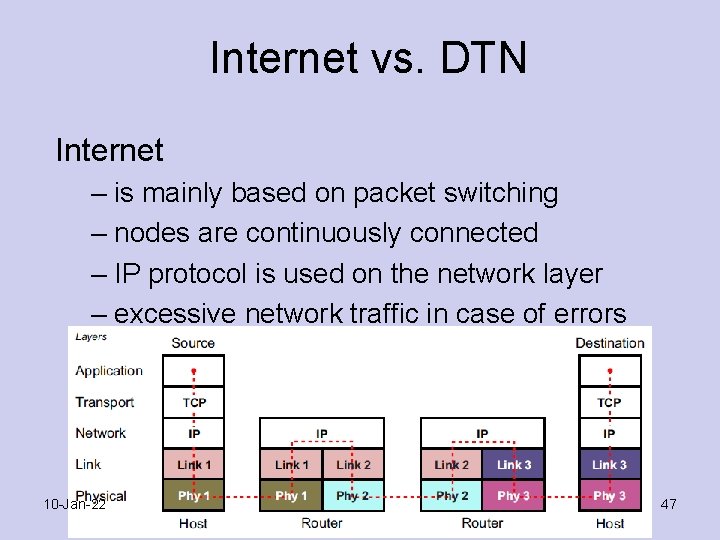
Internet vs. DTN Internet – is mainly based on packet switching – nodes are continuously connected – IP protocol is used on the network layer – excessive network traffic in case of errors 10 -Jan-22 47

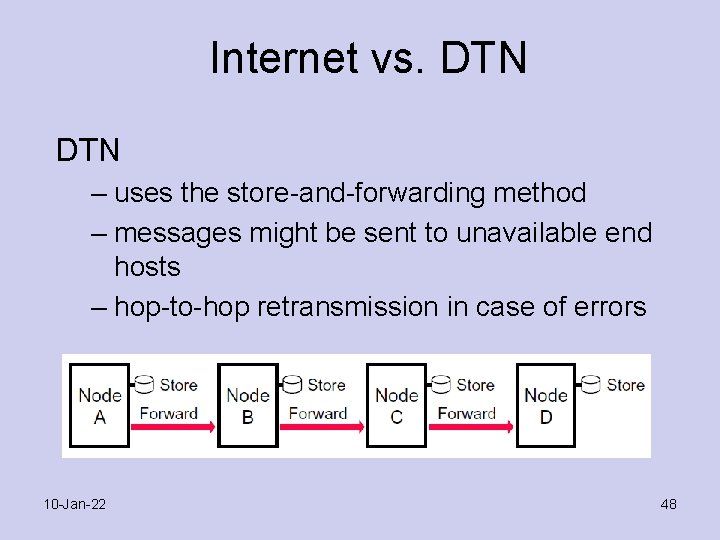
Internet vs. DTN – uses the store-and-forwarding method – messages might be sent to unavailable end hosts – hop-to-hop retransmission in case of errors 10 -Jan-22 48

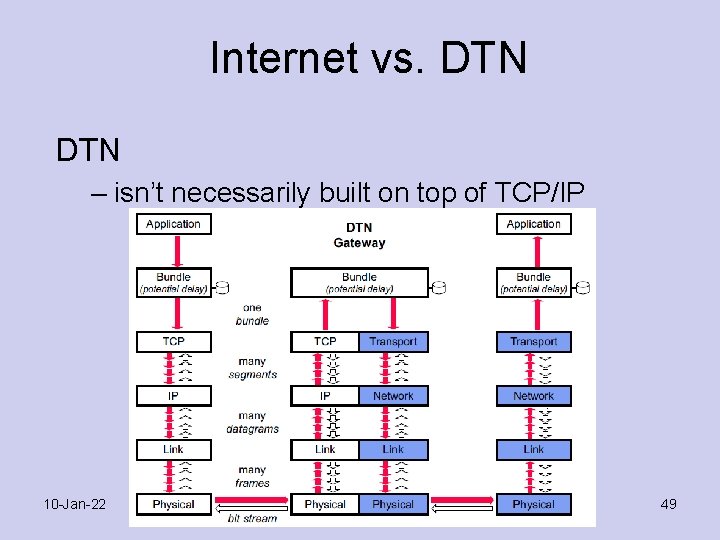
Internet vs. DTN – isn’t necessarily built on top of TCP/IP 10 -Jan-22 49

Internet vs. DTN Communication on the Internet is mainly based on packet switching DTNs use store-and-forward message switching – very similar to the way email systems work 10 -Jan-22 50

Features • Intermittent connectivity – Opportunistic contacts – Scheduled contacts • Non-conversational protocol • Security 10 -Jan-22 51

Why a Delay-Tolerant Network (DTN)? • The Internet’s underlying assumptions – – Continuous, bidirectional end-to-end path Short round-trips Symmetric data rates Low error rates • The characteristics of evolving and potential networks – – Intermittent connectivity Long or variable delay Asymmetric data rates High error rates • New architectural concept is needed! 10 -Jan-22 52

Store-And-Forward Message Switching • The problems of DTNs can be overcome by store-and-forward massage switching • DTN routers need persistent storage for their queues because – A communication link may not be available for a long time – One node may send or receive data much faster or more reliably than the other node – A message, once transmitted, may need to be retransmitted for some reasons 10 -Jan-22 53

The Bundle Layer • A new protocol layer overlaid on top of heterogeneous region-specific lower layers, with which application programs can communicate across multiple regions 10 -Jan-22 54

Bundles and Bundle Encapsulation • Bundles (messages) consist of – A source-application’s user data – Control information, provided by the source application for the destination application – A bundle header, inserted by the bundle layer 10 -Jan-22 55

A Non-Conversational Protocol • DTN bundle layers communicate between themselves using simple sessions with minimal or no round-trips • Any acknowledgement from the receiving node is optional, depending on the class of service selected 10 -Jan-22 56

DTN Nodes • An entity with a bundle layer – Host – sends and/or receives bundles, but does not forward them. Optionally supports custody transfers. – Router – forwards bundles within a single DTN region. Optionally supports custody transfers. – Gateway – forwards bundles between tow or more DTN regions. Must support custody transfers. 10 -Jan-22 57

Delay Isolation via Transport-Layer Termination • DTN routers and gateways terminate transport protocols at the bundle layer 10 -Jan-22 58

Custody Transfers • The bundle layer supports node-to-node retransmission by means of custody transfers • If no ACK is returned before the sender’s time-to -ACK expires, the sender retransmits the bundle • A bundle custodian must store a bundle until – Another node accepts custody, or – Expiration of the bundle’s time-to-live • Do not guarantee end-to-end reliability 10 -Jan-22 59

Moving Points of Retransmission Forward • The bundle layer uses reliable transportlayer protocols together with custody transfers to move points of retransmission progressively forward toward the destination 10 -Jan-22 60

Internet vs. DTN Routing • The protocol stacks of all nodes include both bundle and transport layers • DTN gateways can run different lowerlayer protocols (below the bundle layer) on each side of their double stack, which allows gateways to span two regions that use different lower-layer protocols 10 -Jan-22 61

Classes of Bundle Services • • • Custody Transfer Return Receipt Custody-Transfer Notification Bundle-Forwarding Notification Priority of Delivery Authentication 10 -Jan-22 62

• Thanks! 10 -Jan-22 63