Unit 8 Network Security IP security IPsec protocol





- Slides: 12

Unit 8 Network Security

IP security (IPsec) • protocol suite for secure Internet Protocol (IP) • works by authenticating and encrypting each IP packet of a communication session • includes protocols for establishing mutual authentication between agents • can be used in protecting data flows between a pair of hosts (host-to-host), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host). • IPsec is an end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite • Used in VPN

IPSec security architecture • The IPsec is an open standard as a part of the IPv 4 suite. • IPsec uses the following protocols to perform various functions • Authentication Headers (AH) • provides connectionless data integrity and data origin authentication for IP datagrams and provides protection against replay attacks. [10][11] • Encapsulating Security Payloads (ESP) • provides confidentiality, connectionless integrity, data-origin authentication, an antireplay service (a form of partial sequence integrity), and limited traffic-flow confidentiality. • Security Associations (SA) • Provides the bundle of algorithms and data that provide the parameters necessary for AH and/or ESP operations. The Internet Security Association and Key Management Protocol (ISAKMP) provides a framework for authentication and key exchange

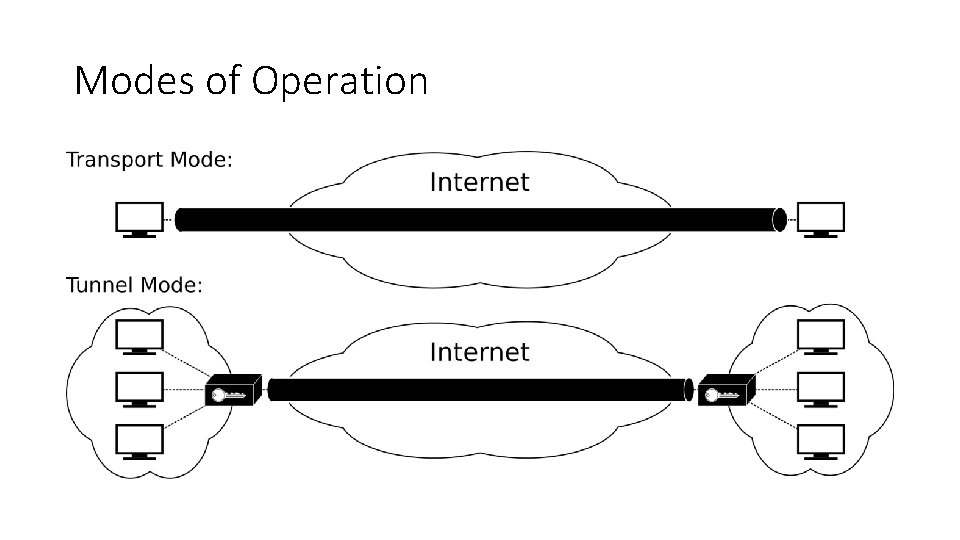
Modes of Operation • Transport mode • Only the payload of the IP packet is usually encrypted or authenticated. • The routing is intact, since the IP header is neither modified nor encrypted. • However, when the authentication header is used, the IP addresses cannot be modified by network address translation, as this always invalidates the hash value. • The transport and application layers are always secured by a hash, so they cannot be modified in any way • Tunnel mode • The entire IP packet is encrypted and authenticated. • It is then encapsulated into a new IP packet with a new IP header. • Tunnel mode is used to create virtual private networks for network-to-network communications (e. g. between routers to link sites), host-to-network communications (e. g. remote user access) and host-to-host communications (e. g. private chat).

Modes of Operation

Cryptographic Algorithm Used • SHA 1 / SHA 2 for integrity and authencity • 3 DES for confidentiality • AES for confidentiality and authentication together

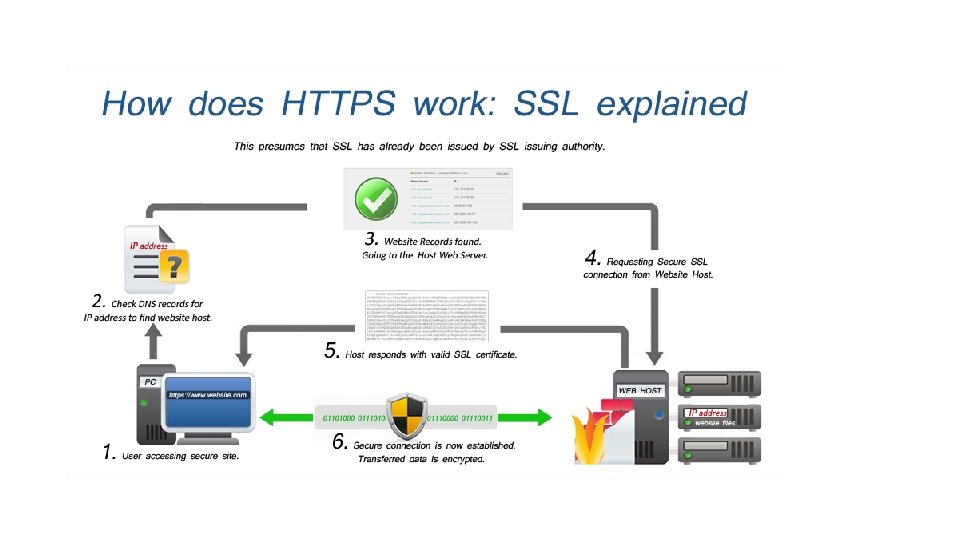
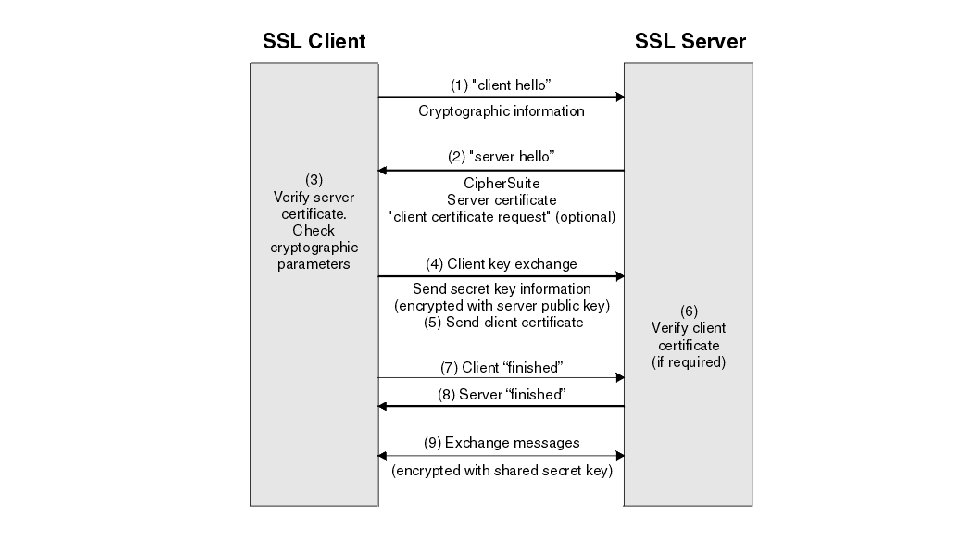
Secure Socket Layer (SSL) • Standard security technology for establishing an encrypted link between a web server and a browser. • This link ensures that all data passed between the web server and browsers remain private and integral • SSL is an industry standard and is used by millions of websites in the protection of their online transactions with their customers. • SSL session starts with SSL handshake [VIDEO]

SSL Connection • To be able to create an SSL connection a web server requires an SSL Certificate. • Use public key cryptography • Perform SSL handshake Successor of SSL is Transport Layer Security(TLS) Practically use https in web browser



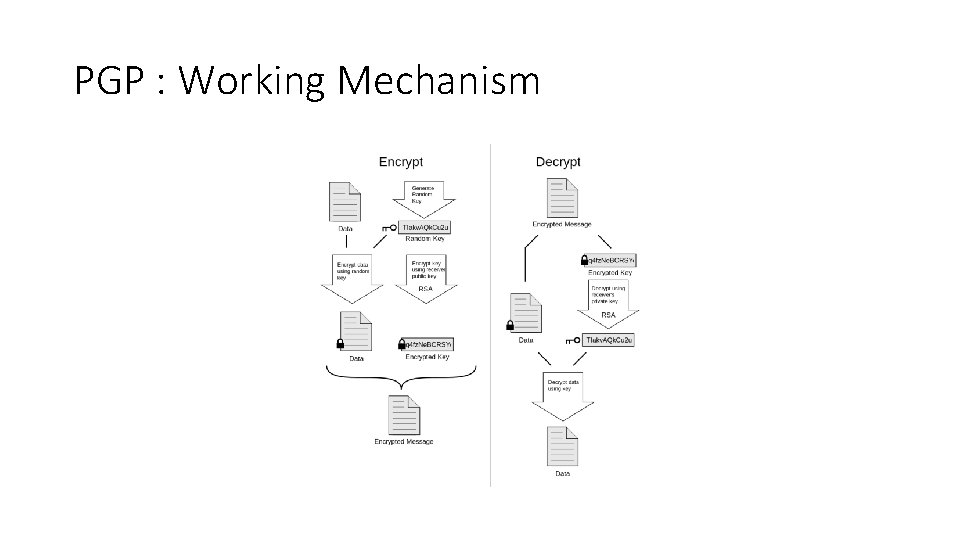
Pretty Good Privacy • Pretty Good Privacy or PGP is a popular program used to encrypt and decrypt email over the Internet, as well as authenticate messages with digital signatures and encrypted stored files.

PGP : Working Mechanism