Unit 6 Wireless LAN Security Introduction WLAN Security













![[Lack of] Security at Hot Spots ¢ ¢ ¢ After association, a user is [Lack of] Security at Hot Spots ¢ ¢ ¢ After association, a user is](https://slidetodoc.com/presentation_image_h2/ae16cb3c9a3e8e6a28bb8b1ad3c0bf6f/image-37.jpg)
![[Lack of] Security at Hot Spots ¢ ¢ ¢ Hot Spots (airport, hotel, coffee [Lack of] Security at Hot Spots ¢ ¢ ¢ Hot Spots (airport, hotel, coffee](https://slidetodoc.com/presentation_image_h2/ae16cb3c9a3e8e6a28bb8b1ad3c0bf6f/image-38.jpg)











- Slides: 65

Unit 6: Wireless LAN Security ¢ ¢ ¢ Introduction WLAN Security Threat Network Security Review 802. 11 Security - WEP Wi-Fi Protected Access (WPA) l l ¢ Wi-Fi Protected Access 2. 0 l l ¢ IEEE 802. 1 X TKIP/MIC IEEE 802. 11 i AES/CCMP Summary

Dangerous Wireless World! ¢ ¢ A poll of 500 organizations with WLAN deployed shows that less than half have implemented security solutions. A war drive test by Air. Defense at Atlanta, Chicago, and San Francisco: l l 57% of 1, 136 detected Access Points (AP) have no encryption. 77% broadcast their Service Set ID (SSID). 9% found to be rogue AP. Many APs use default setting. Source: Fran Howarth, Securing Wireless LANs, Faulkner Information Services

Evolution of WLAN Security ¢ ¢ ¢ There are many threats to WLAN security. Solutions are available to address most known threats. There will be threats to today’s solutions. Technology does not address all issues. Many security issues can be addressed by user awareness, policies, processes, sound practices, etc. A sound network design may also address many security issues.

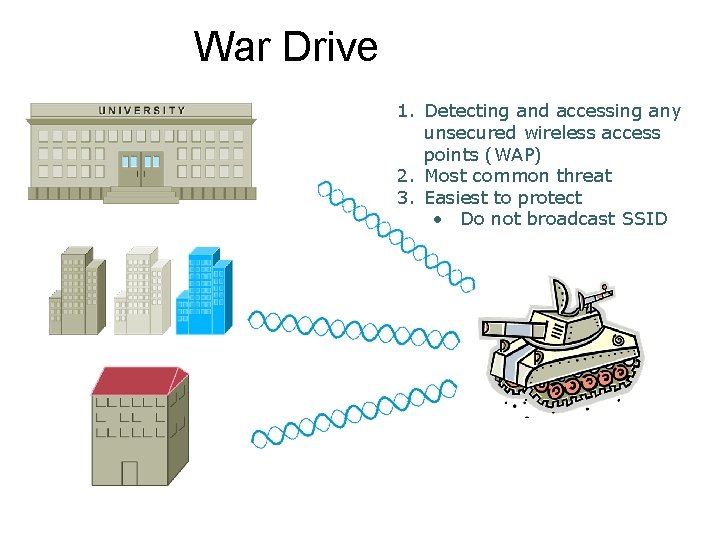
Common Attacks on Wireless LAN War Drive ¢ Eavesdropping ¢ Rogue AP ¢ Windows Bridge ¢ Man-in-the-Middle ¢ Denial of Service (Do. S) ¢

War Drive 1. Detecting and accessing any unsecured wireless access points (WAP) 2. Most common threat 3. Easiest to protect • Do not broadcast SSID

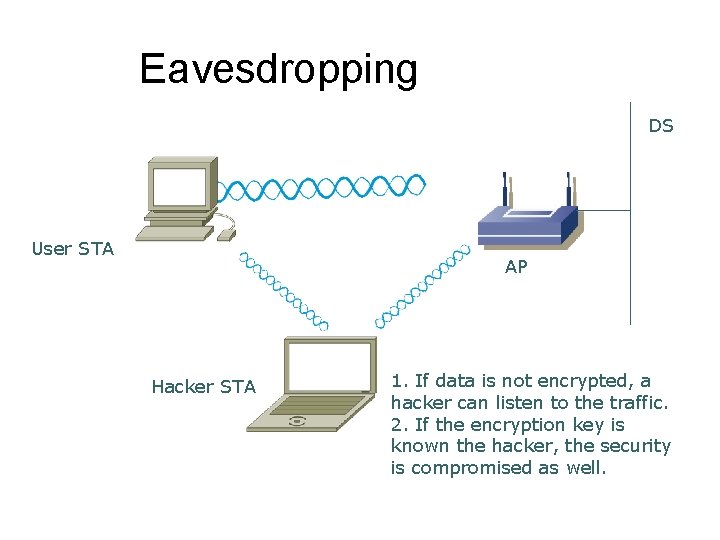
Eavesdropping DS User STA AP Hacker STA 1. If data is not encrypted, a hacker can listen to the traffic. 2. If the encryption key is known the hacker, the security is compromised as well.

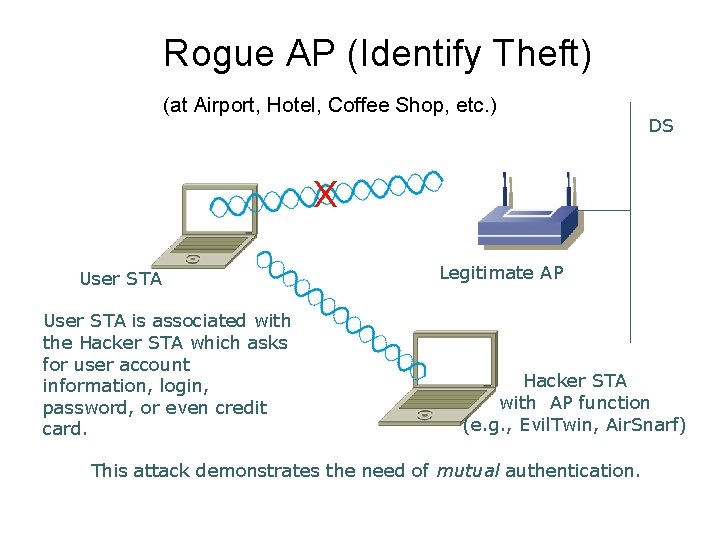
Rogue AP (Identify Theft) (at Airport, Hotel, Coffee Shop, etc. ) DS X User STA is associated with the Hacker STA which asks for user account information, login, password, or even credit card. Legitimate AP Hacker STA with AP function (e. g. , Evil. Twin, Air. Snarf) This attack demonstrates the need of mutual authentication.

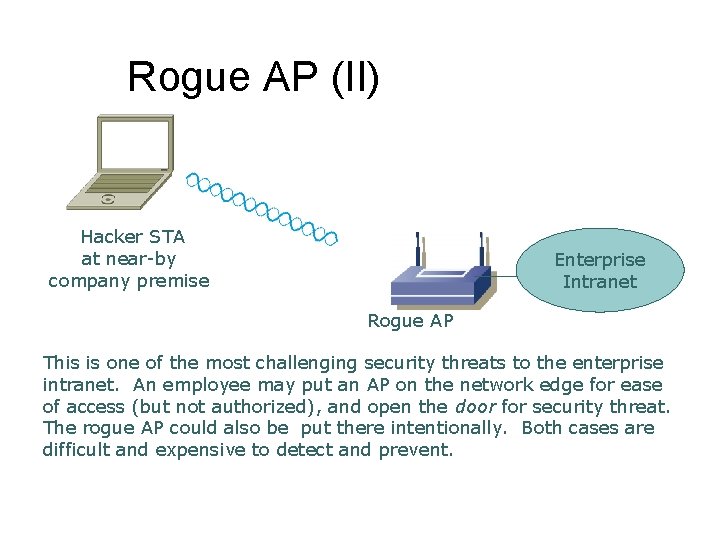
Rogue AP (II) Hacker STA at near-by company premise Enterprise Intranet Rogue AP This is one of the most challenging security threats to the enterprise intranet. An employee may put an AP on the network edge for ease of access (but not authorized), and open the door for security threat. The rogue AP could also be put there intentionally. Both cases are difficult and expensive to detect and prevent.

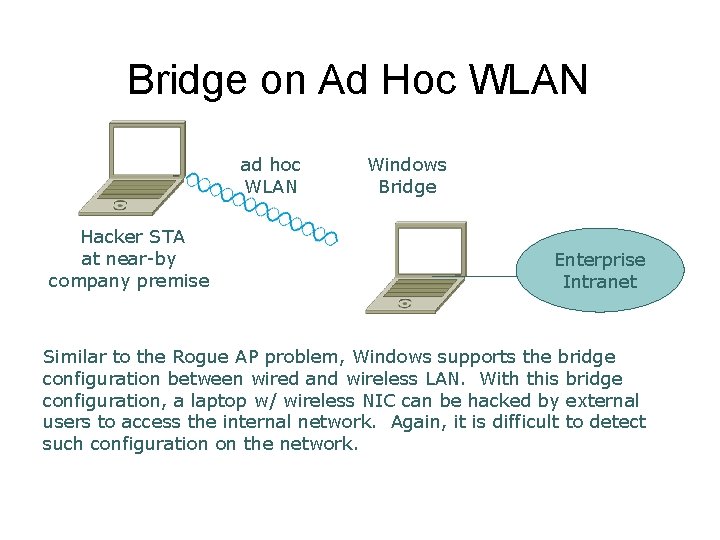
Bridge on Ad Hoc WLAN ad hoc WLAN Hacker STA at near-by company premise Windows Bridge Enterprise Intranet Similar to the Rogue AP problem, Windows supports the bridge configuration between wired and wireless LAN. With this bridge configuration, a laptop w/ wireless NIC can be hacked by external users to access the internal network. Again, it is difficult to detect such configuration on the network.

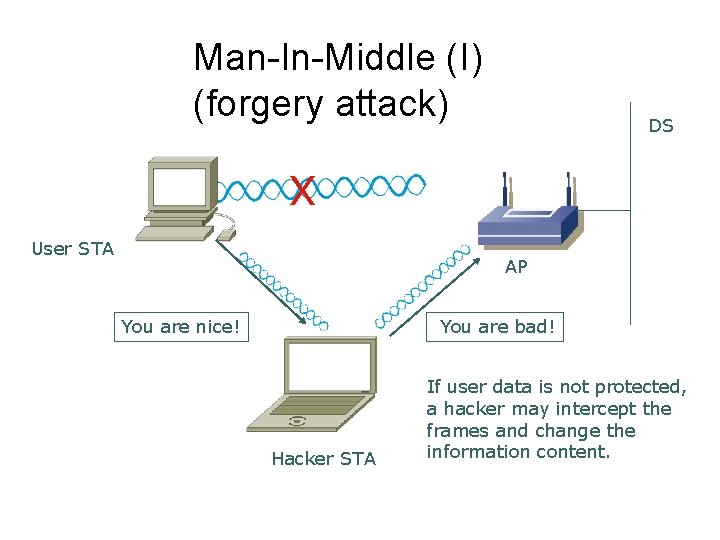
Man-In-Middle (I) (forgery attack) DS X User STA AP You are nice! You are bad! Hacker STA If user data is not protected, a hacker may intercept the frames and change the information content.

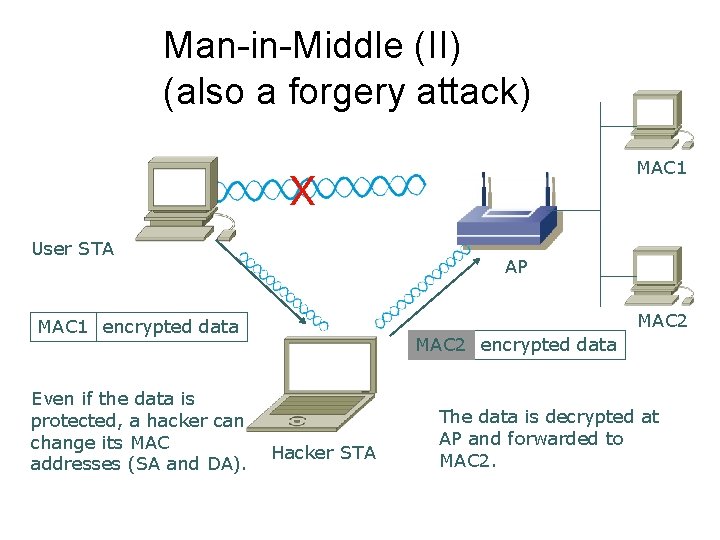
Man-in-Middle (II) (also a forgery attack) MAC 1 X User STA AP MAC 2 MAC 1 encrypted data Even if the data is protected, a hacker can change its MAC addresses (SA and DA). MAC 2 encrypted data Hacker STA The data is decrypted at AP and forwarded to MAC 2.

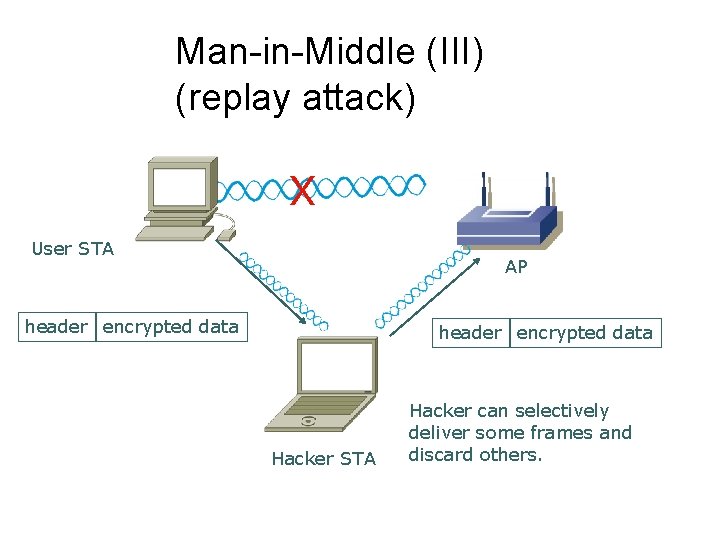
Man-in-Middle (III) (replay attack) X User STA AP header encrypted data Hacker STA Hacker can selectively deliver some frames and discard others.

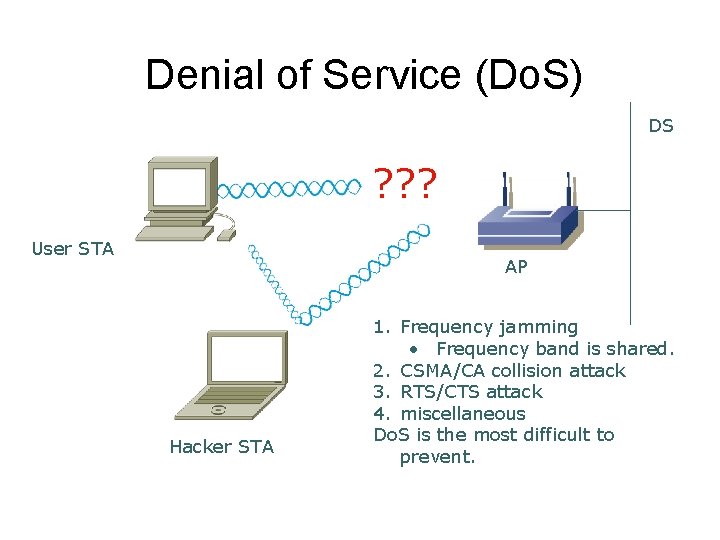
Denial of Service (Do. S) DS ? ? ? User STA AP Hacker STA 1. Frequency jamming • Frequency band is shared. 2. CSMA/CA collision attack 3. RTS/CTS attack 4. miscellaneous Do. S is the most difficult to prevent.

Network Security Overview ¢ ¢ Network Monitor Association l ¢ Authentication l l ¢ Who are you? login + password Authorization l l ¢ Physical connectivity What can you do? applications, duration, time of day, etc. Encryption l Key Management • private key (single key) • public key (key pair) l Encryption Algorithm

Wireless Network Sensor/Monitor ¢ ¢ ¢ What is it: deploying wireless sensor/monitor at various locations of the company premises. l Wireless Intrusion detection System (WIDS) Purpose: detection of (1) Rogue APs, (2) improperly configured APs, (3) ad hoc network, (4) intrusion wireless stations. There are no standards or protocols on how to monitor the networks, and each vendor has its own proprietary solution. Security policy and employee awareness are also important to detect unintentional use of rogue AP and wireless ad hoc network. Portable monitoring devices are available. If all wired ports are authenticated, there will be no issues with rogue APs. l not a practical solution, yet.

Association ¢ ¢ ¢ ¢ The RF connection between STA and AP Antenna selection (sectional or omni-directional) Antenna Transmission power Selection of non-overlapping channel (3 for 802. 11 b/g and 8 for 802. 11 a) Service Set ID (SSID) l Broadcast vs. non-broadcast SSID l default: broadcast Association request (from STA to AP) MAC filtering: accept or reject based on the STA MAC address l default: no MAC filtering

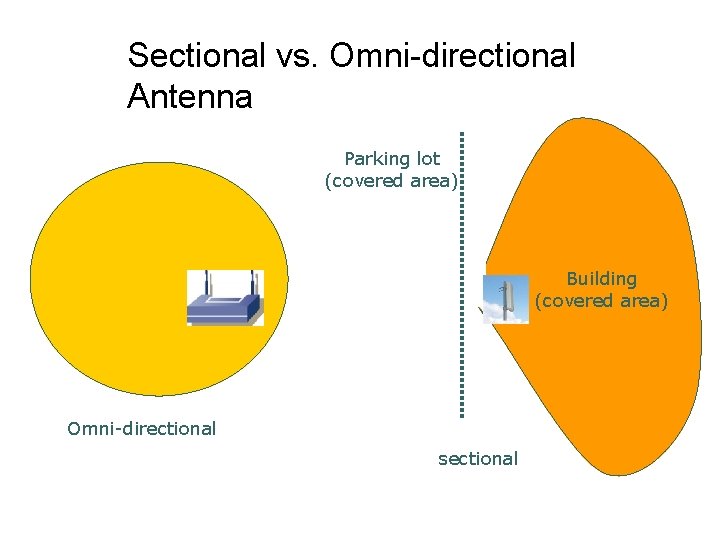
Sectional vs. Omni-directional Antenna Parking lot (covered area) Building (covered area) Omni-directional sectional

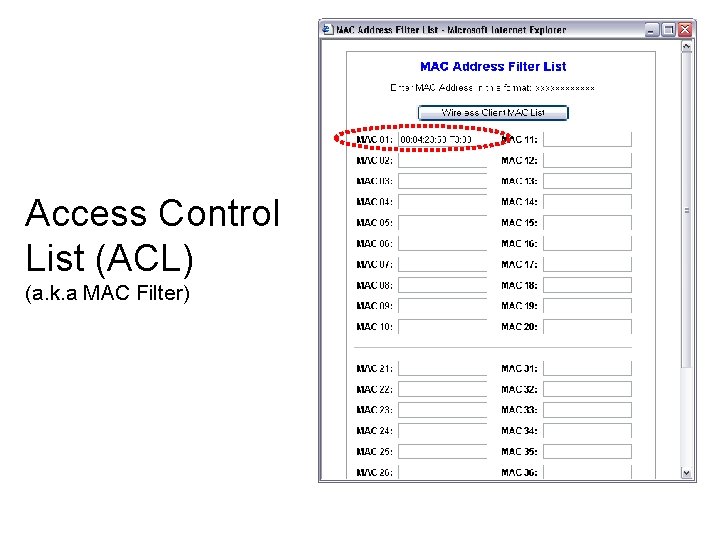
Association – MAC filtering ¢ ¢ ¢ User MAC addresses are registered on the network device (AP). This MAC list is also known as Access Control List (ACL). When an AP receives an association request, the AP checks its MAC address. If the MAC address is on the ACL, the request is accepted. Otherwise, the request is rejected. A STA can send/receive data from an AP only after it is associated with the AP.

Caveat: MAC Spoofing ¢ ¢ MAC Address can be easily spoofed. Windows – Mac. Makeup www. gorlani. com/publicprj/macmakeup. asp ¢ Linux l ifconfig eth 0 hw ether 00: 00: 01: 01 up X User STA 00: 00: 01: 01 Hacker STA 00: 00: 01: 01

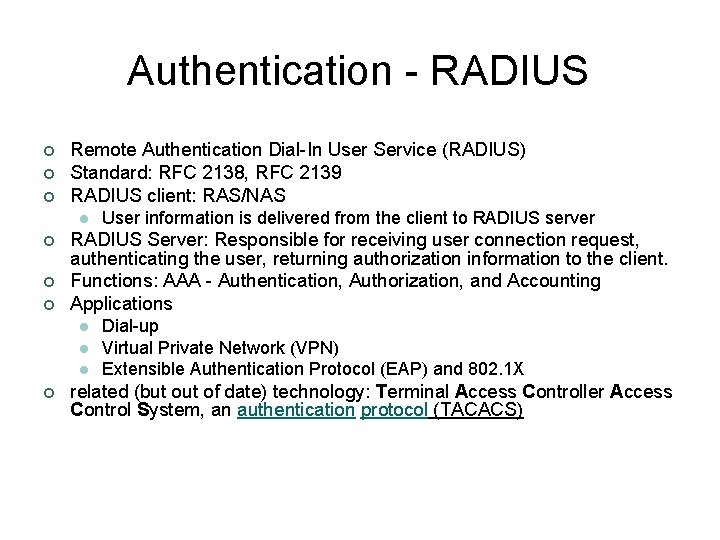
Authentication - RADIUS ¢ ¢ ¢ Remote Authentication Dial-In User Service (RADIUS) Standard: RFC 2138, RFC 2139 RADIUS client: RAS/NAS l ¢ ¢ ¢ RADIUS Server: Responsible for receiving user connection request, authenticating the user, returning authorization information to the client. Functions: AAA - Authentication, Authorization, and Accounting Applications l l l ¢ User information is delivered from the client to RADIUS server Dial-up Virtual Private Network (VPN) Extensible Authentication Protocol (EAP) and 802. 1 X related (but of date) technology: Terminal Access Controller Access Control System, an authentication protocol (TACACS)

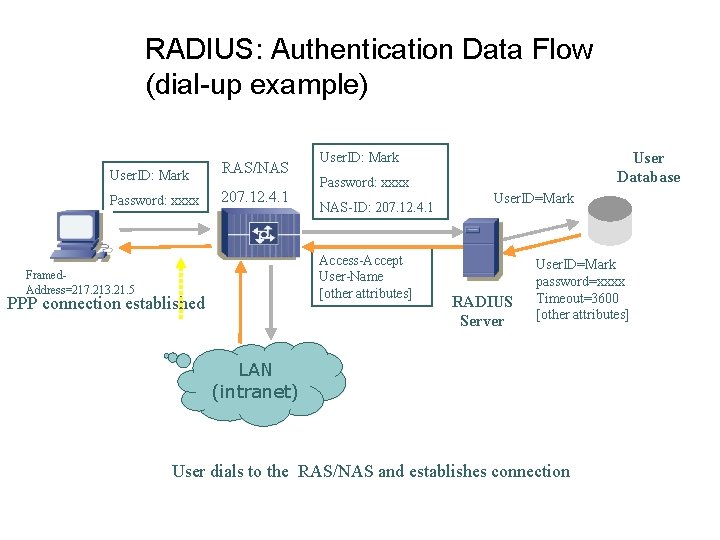
RADIUS: Authentication Data Flow (dial-up example) User. ID: Mark RAS/NAS Password: xxxx 207. 12. 4. 1 Password: xxxx NAS-ID: 207. 12. 4. 1 Access-Accept User-Name [other attributes] Framed. Address=217. 213. 21. 5 PPP connection established User Database User. ID: Mark User. ID=Mark RADIUS Server User. ID=Mark password=xxxx Timeout=3600 [other attributes] LAN (intranet) User dials to the RAS/NAS and establishes connection

Authorization – Access Control ¢ Restriction that network administrators can use to strengthen the security of their networks l l l Restrict user access on certain time only Restrict access to a fixed duration for each login session (or for each day) Restrict certain user access on specific workstations only. Restrict user applications (e. g. , HTTP traffic only) Set a limit on how many unsuccessful login attempts from a single user the server will accept before blocking that ID from even attempting to log on

Encryption ¢ ¢ Use of an algorithm to scramble data into a format that can be read only by reversing the algorithm In order to protect data, encryption provides the following assurances: l l l Data were not modified after the sender transmitted them and before receiver picked them up Data can only be viewed by their intended recipient (or at their intended destination) All of the data received at intended destination were truly issued by the stated sender and not forged by an intruder

Encryption ¢ The most popular kind of encryption weaves a key (random string of characters) into the original data’s bits to generate a unique data block l The scrambled data block is known as cipher text l The longer the key, the more difficult the cipher text can be decrypted by an unauthorized system

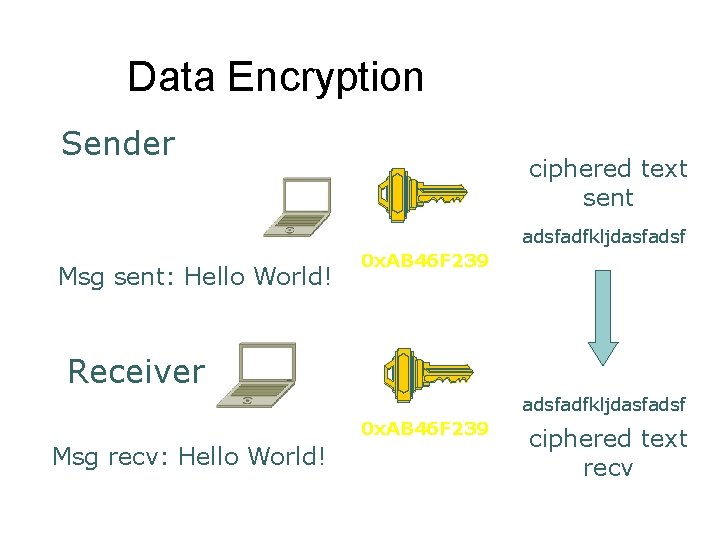
Data Encryption Sender ciphered text sent adsfadfkljdasfadsf Msg sent: Hello World! 0 x. AB 46 F 239 Receiver adsfadfkljdasfadsf 0 x. AB 46 F 239 Msg recv: Hello World! ciphered text recv

Private Key Encryption Data are encrypted using a single key that only the sender and receiver know ¢ Symmetric encryption ¢ The most popular private key encryption is the data encryption standard (DES) ¢ Triple-DES – applying DES three times with three different keys ¢

Private Key Encryption ¢ ¢ Sender and receiver share the same key Sender uses the key to encrypt the message to be sent l l ¢ ciphered msg = F(msg, key) F: encryption algorithm Receiver uses the same key to decrypt the message l l msg = F-1(ciphered msg, key) F-1: inverse of F

Public Key Encryption ¢ Public key encryption l l ¢ Public-key server l ¢ ¢ Data are encrypted using two keys Also know as asymmetric encryption Provides a list of users’ public keys Combination of public key and private key is known as key pair The public key is used to encrypt the data and the private key is used to decrypt the data.

Public Key Encryption ¢ ¢ Key management (KM) server generates the key pair (one public key and one private key). The sender requests a public key from the KM server. The sender uses the public key to encrypt the message l ciphered msg = F(msg, public key) l F: encryption algorithm The receiver uses the private key to decrypt the message l msg = G(cipered msg, private key) l G: decryption algorithm

802. 11 Security Mechanism ¢ Service Set Identification (SSID) l ¢ Access Control List (MAC filtering) l ¢ ¢ Not in the standard, but supported by almost all vendors Wired Equivalent Privacy (WEP) Shared key encryption l l l ¢ For station association Stations use the same key for encryption. RC 4 encryption algorithm Key: 40 bits or 128 bits User Authentication l Not specified in 802. 11.

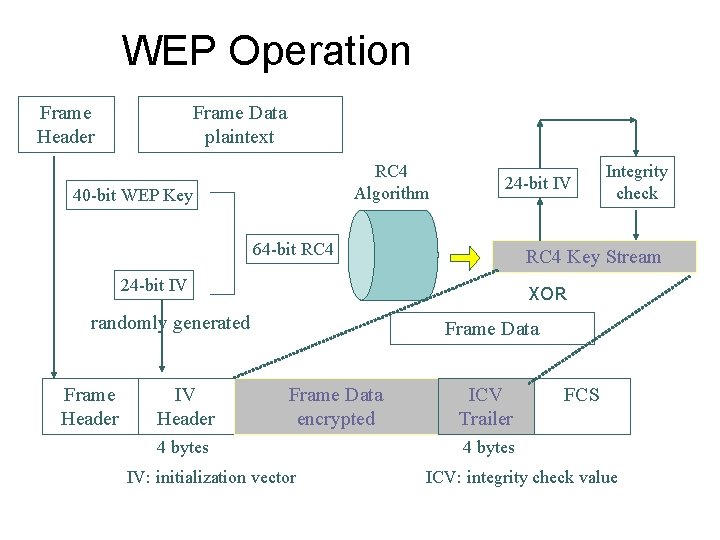
WEP Operation Frame Header Frame Data plaintext RC 4 Algorithm 40 -bit WEP Key 24 -bit IV 64 -bit RC 4 Key Stream 24 -bit IV XOR randomly generated Frame Header IV Header Integrity check Frame Data encrypted 4 bytes IV: initialization vector ICV Trailer FCS 4 bytes ICV: integrity check value

Security for Home and SOHO ¢ 802. 11 security is considered sufficient for home and SOHO networks if users turn on the security mechanisms: l Carefully select the location for AP • Away from the windows l l l Change the SSID (don’t use the default) Do not broadcast SSID Use WEP keys • Change the key regularly l Enable Access Control List (ACL)

WEP Security Configuration (I) (Do not broadcast your SSID)

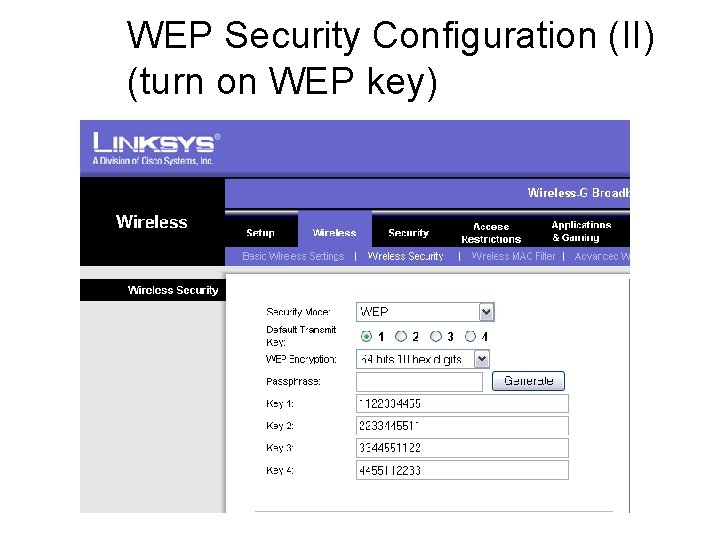
WEP Security Configuration (II) (turn on WEP key)

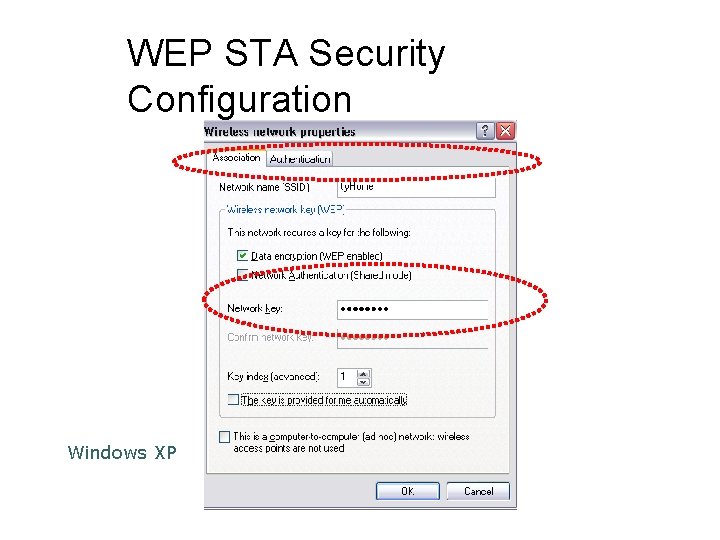
WEP STA Security Configuration Windows XP

Access Control List (ACL) (a. k. a MAC Filter)
![Lack of Security at Hot Spots After association a user is [Lack of] Security at Hot Spots ¢ ¢ ¢ After association, a user is](https://slidetodoc.com/presentation_image_h2/ae16cb3c9a3e8e6a28bb8b1ad3c0bf6f/image-37.jpg)
[Lack of] Security at Hot Spots ¢ ¢ ¢ After association, a user is granted an IP address to access a web site for registration and/or authentication. First time users are required to provide credit information to register an account. l After the registration, users are granted a login and a password. After entering login and password, the user is authenticated, and the station MAC address is added to the ACL. The management software continuously monitors the connectivity of the wireless station. When the station is disconnected from the network, its MAC address is removed from ACL. (Otherwise, a hacker may steal a MAC address. ) Users need to re-enter login/password to access the network next time.
![Lack of Security at Hot Spots Hot Spots airport hotel coffee [Lack of] Security at Hot Spots ¢ ¢ ¢ Hot Spots (airport, hotel, coffee](https://slidetodoc.com/presentation_image_h2/ae16cb3c9a3e8e6a28bb8b1ad3c0bf6f/image-38.jpg)
[Lack of] Security at Hot Spots ¢ ¢ ¢ Hot Spots (airport, hotel, coffee shop, library, etc. ) usually perform user authentication, and seldom use data encryption. It is difficult, if not impossible, to distribute encryption keys to the client workstations. Without encryption, hackers can easily sniff the packets over the WLAN network. Users should avoid using WLAN at hot spots to access the company intranet unless the connection is over the company VPN. Places that offer free wireless LAN have more security threats. How do you know you are connecting to a legitimate AP?

Problems of WEP ¢ No Authentication Scheme l ¢ No key management protocol in WEP l l ¢ l Hacker can decipher the key after collecting sufficient number of frames This is a major design issue of WEP. One way authentication verification l ¢ Hacker can intercept and change the destination MAC address. Weak Encryption Algorithm l ¢ key is shared and manually entered. This is a major distribution issue of WEP. No protection on 802. 11 frame header l ¢ SSID is an association scheme Rogue AP’s WEP is NOT acceptable to the enterprise network.

WEP Key Attacks ¢ Active Attack l IV/WEP key replay • send known plaintext and observe received ciphertext l Frame Bit flipping • Toggle some bits in frame, observe ciphertext error, and compare it to predicted error message ¢ Passive Attack l l Capture 1 M frames and you can statistically determine the WEP key Hackers can easily snoop WLAN frames over the wireless network.

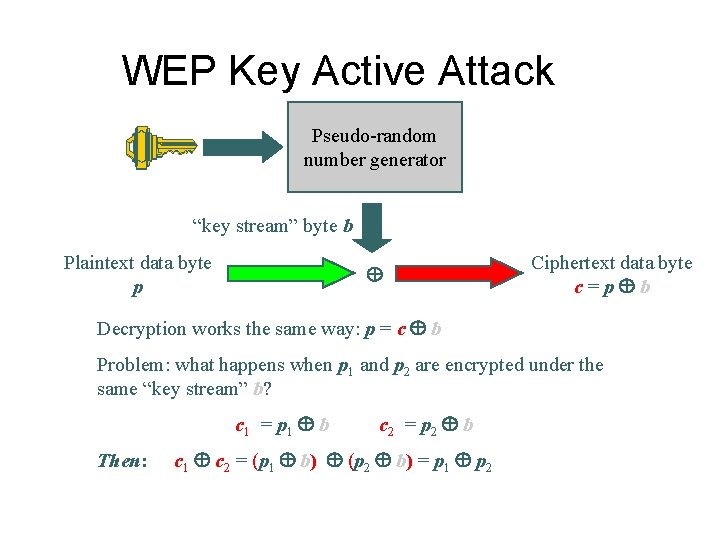
WEP Key Active Attack Pseudo-random number generator “key stream” byte b Plaintext data byte p Ciphertext data byte c=p b Decryption works the same way: p = c b Problem: what happens when p 1 and p 2 are encrypted under the same “key stream” b? c 1 = p 1 b Then: c 2 = p 2 b c 1 c 2 = (p 1 b) (p 2 b) = p 1 p 2

WEP Key Passive Attack ¢ If hackers collect enough frames, they can decipher the shared key. l theoretically: IV has 24 bits (224 frames) l In practice, because of the weakness of the RC 4 algorithm, the decipher algorithm needs only 1 M frames. • It is about 18 min on 802. 11 b. ¢ Available Tools l Air. Snort, WEPCrack, Air. Crack 1, 000 frames × 1, 500 bytes/frame × 8 bits/byte ------------------------------ ≈ 18 min 11 Mbits/sec

Solutions to WEP Problems ¢ ¢ ¢ IP-based Virtual Private Network (VPN) Authentication l 802. 1 X + standard authentication methods Key Distribution and Management l 802. 1 X+ Encryption l Temporal Key Integrity Protocol (TKIP) l Advanced Encryption System (AES) 802. 11 i: 802. 1 X + TKIP + AES/CCMP Wi-Fi Protected Access (WPA) l Standard organization for product certification to ensure standard conformance and interoperability. l WPA 1. 0: 802. 1 X + TKIP l WPA 2. 0: 802. 1 X + AES

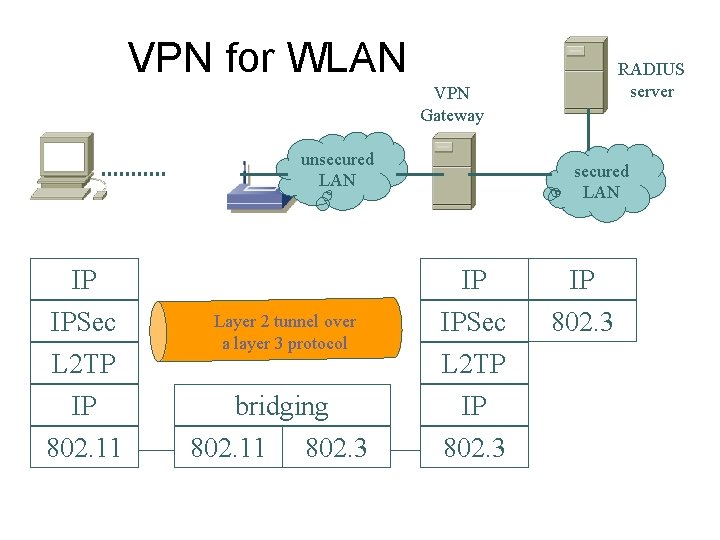
VPN for WLAN RADIUS server VPN Gateway unsecured LAN IP IPSec L 2 TP IP 802. 11 Layer 2 tunnel over a layer 3 protocol bridging 802. 11 802. 3 secured LAN IP IPSec L 2 TP IP 802. 3

Notes on VPN for WLAN ¢ ¢ ¢ It addresses many (but not all) WLAN security issues. Use IP-VPN at WLAN hot spots However, l l It does not protect the man-in-the-middle attack. The client must support IP-based VPN. • It is OK for Windows XP clients, but Many WLAN appliances do not support it. l l It has significant performance overhead. Other issues: multicast, IP mobility, network management.

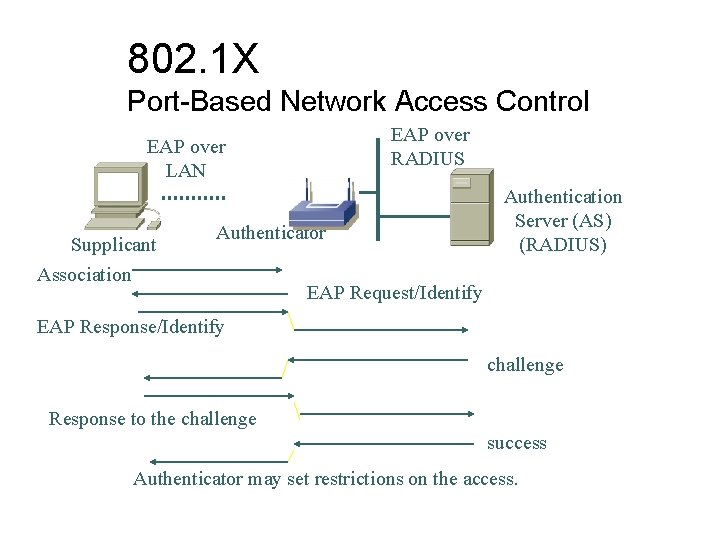
802. 1 X and EAP ¢ ¢ Extensible Authentication Protocol (EAP) is an IETF standard and adopted by IEEE as the basis for 802. 1 X. It is called the port based network access control. It supports a mutual authentication process l ¢ STA and AP are authenticated to each other. 802. 1 X does not specify the key management, but most implementations support a mechanism of dynamic key management.

802. 1 X and EAP • • 802. 1 X does not specify the authentication method; instead, it supports several authentication methods. 802. 1 X also supports multiple layer 2 protocols, PPP, 802. 3, 802. 5, and 802. 11. MD 5 TLS TTLS LEAP PEAP PPP 802. 3 802. 11 802. 5

802. 1 X Port-Based Network Access Control EAP over RADIUS EAP over LAN Supplicant Authenticator Association Authentication Server (AS) (RADIUS) EAP Request/Identify EAP Response/Identify challenge Response to the challenge success Authenticator may set restrictions on the access.

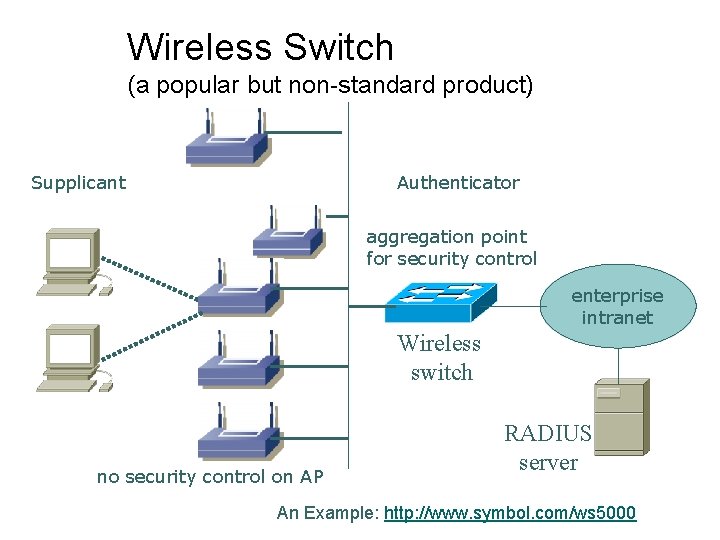
Wireless Switch (a popular but non-standard product) Supplicant Authenticator aggregation point for security control enterprise intranet Wireless switch no security control on AP RADIUS server An Example: http: //www. symbol. com/ws 5000

802. 1 X-based Key Management ¢ ¢ ¢ After the authentication, the AS (authentication server) includes a session key to the AP (authenticator) in the success message. The session key is also known as a pairwise key. AP uses the key to encrypt a message to the supplicant. The supplicant uses the content in the key message and local information (e. g. , MAC address and/or password) to define the encryption key. The session key is unique to each association between supplicant and AP.

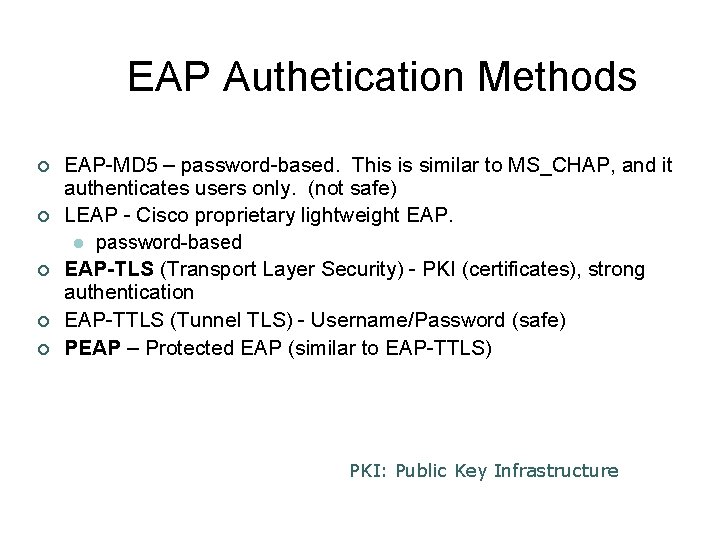
EAP Authetication Methods ¢ ¢ ¢ EAP-MD 5 – password-based. This is similar to MS_CHAP, and it authenticates users only. (not safe) LEAP - Cisco proprietary lightweight EAP. l password-based EAP-TLS (Transport Layer Security) - PKI (certificates), strong authentication EAP-TTLS (Tunnel TLS) - Username/Password (safe) PEAP – Protected EAP (similar to EAP-TTLS) PKI: Public Key Infrastructure

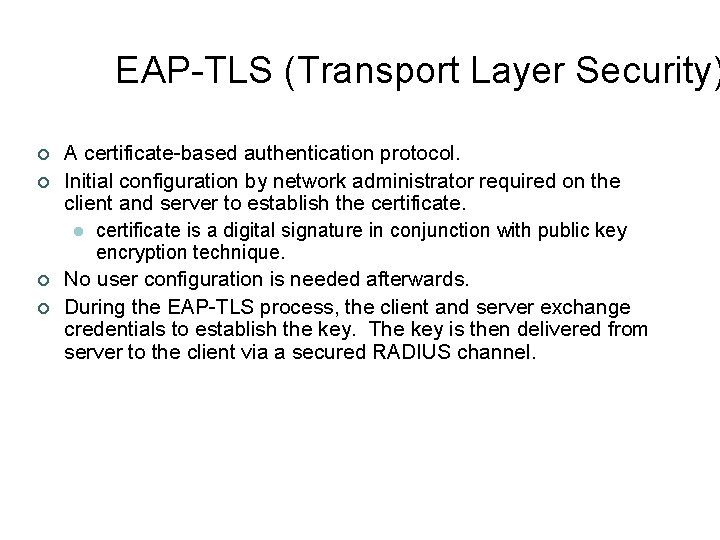
EAP-TLS (Transport Layer Security) ¢ ¢ A certificate-based authentication protocol. Initial configuration by network administrator required on the client and server to establish the certificate. l certificate is a digital signature in conjunction with public key encryption technique. No user configuration is needed afterwards. During the EAP-TLS process, the client and server exchange credentials to establish the key. The key is then delivered from server to the client via a secured RADIUS channel.

Protected EAP (PEAP) ¢ ¢ ¢ A secured password-based authentication method. Only the authentication server needs a certificate. AS sends a public key to the client. The client generate a master encryption key and uses the public key to encrypt the master key to the AS. This master key is used to establish a secure tunnel between AS and the client. Windows XP EAP Configuration

802. 11 i and WPA ¢ ¢ 802. 1 X addresses the issue of authentication, but it does not cover data encryption which is another problem area of 802. 11 i is to provide a complete security solution. l Authentication: 802. 1 X l Key management and distribution: 802. 1 X+ l Improved Encryption over WEP: • Temporal Key Integrity Protocol (TKIP) • AES/CCMP ¢ ¢ Wi. Fi Protected Access (WPA) 1. 0 l Product conformance and interoperability test l 802. 1 X + TKIP [+ MIC] WPA 2. 0 l 802. 1 X + AES/CCMP (including MIC) MIC: message integrity code

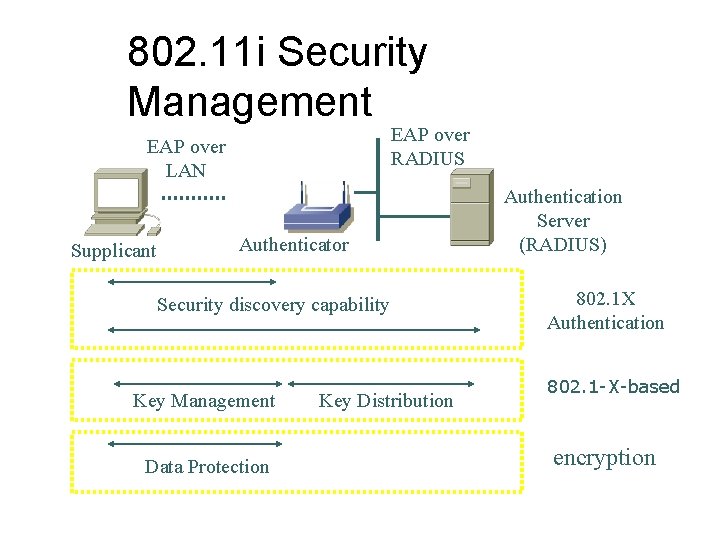
802. 11 i Security Management EAP over RADIUS EAP over LAN Supplicant Authenticator Security discovery capability Key Management Data Protection Key Distribution Authentication Server (RADIUS) 802. 1 X Authentication 802. 1 -X-based encryption

Temporal Key Integrity Protocol (TKIP) ¢ Design objectives: Address known issues of hacker attack and be interoperable with WEP-only device l Made available as firmware or software upgrade to existing WEP devices l It is basically a solution wrapped around WEP. l

TKIP: major improvement over WEP A message integrity code (MIC), called Michael, to defeat forgeries in the frame header. ¢ A 48 -bit IV and IV sequence counter to defeat forgery and replay attacks. ¢ Per packet key mixing with IV to protect weak key attack ¢ A built-in mechanism to change the encryption key regularly ¢

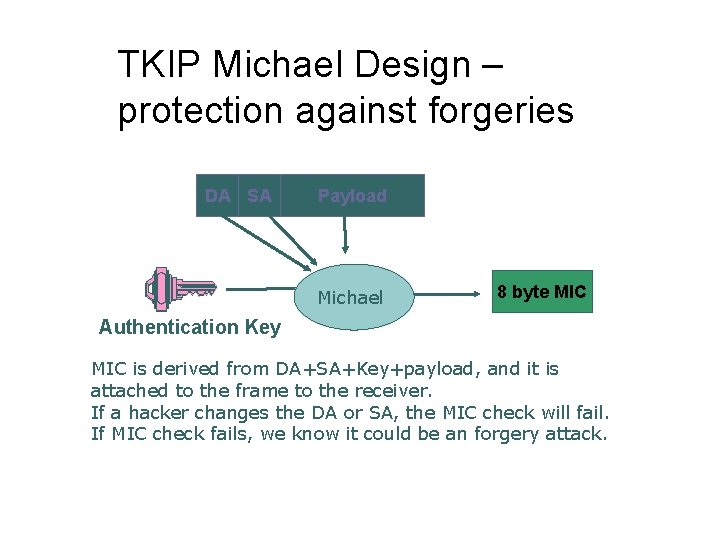
TKIP Michael Design – protection against forgeries DA SA Payload Michael 8 byte MIC Authentication Key MIC is derived from DA+SA+Key+payload, and it is attached to the frame to the receiver. If a hacker changes the DA or SA, the MIC check will fail. If MIC check fails, we know it could be an forgery attack.

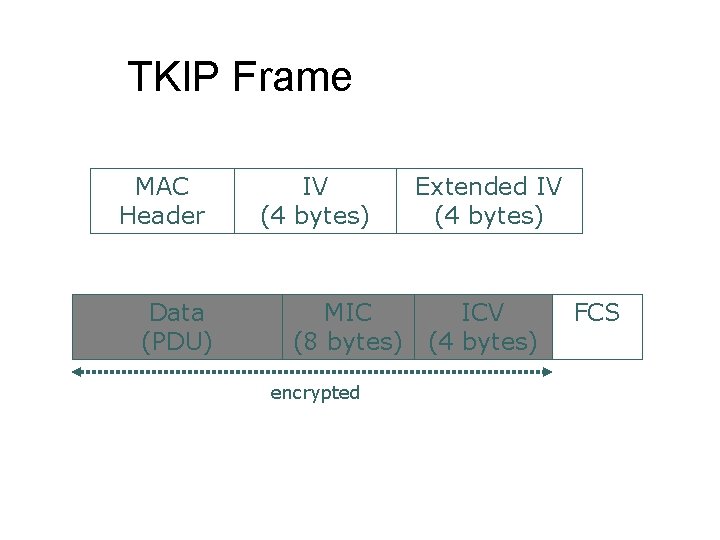
TKIP Frame MAC Header Data (PDU) IV (4 bytes) MIC (8 bytes) encrypted Extended IV (4 bytes) ICV (4 bytes) FCS

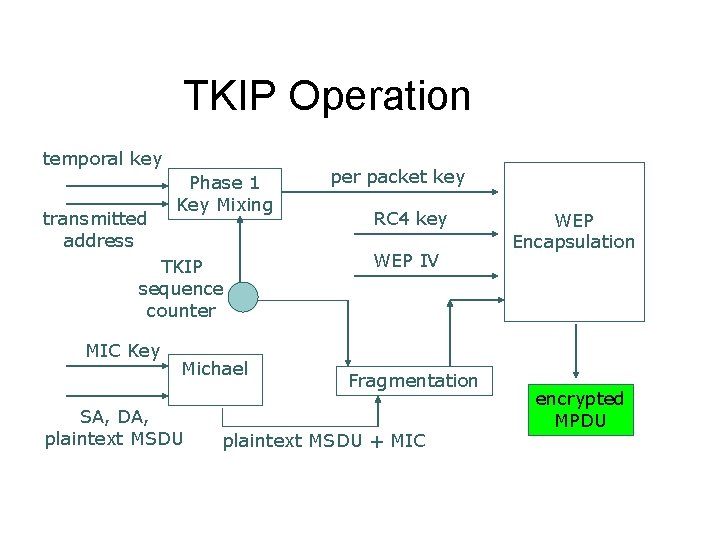
TKIP Operation temporal key transmitted address Phase 1 Key Mixing TKIP sequence counter MIC Key Michael SA, DA, plaintext MSDU per packet key RC 4 key WEP IV Fragmentation plaintext MSDU + MIC WEP Encapsulation encrypted MPDU

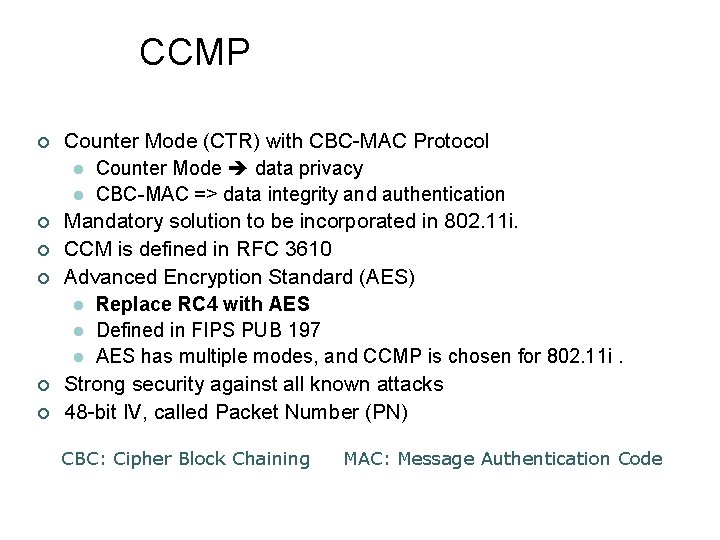
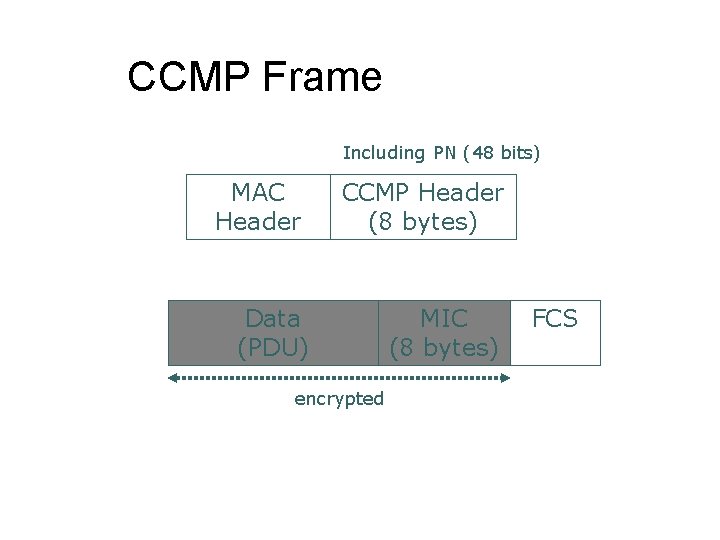
CCMP ¢ ¢ ¢ Counter Mode (CTR) with CBC-MAC Protocol l Counter Mode data privacy l CBC-MAC => data integrity and authentication Mandatory solution to be incorporated in 802. 11 i. CCM is defined in RFC 3610 Advanced Encryption Standard (AES) l Replace RC 4 with AES l Defined in FIPS PUB 197 l AES has multiple modes, and CCMP is chosen for 802. 11 i. Strong security against all known attacks 48 -bit IV, called Packet Number (PN) CBC: Cipher Block Chaining MAC: Message Authentication Code

CCMP Frame Including PN (48 bits) MAC Header CCMP Header (8 bytes) Data (PDU) encrypted MIC (8 bytes) FCS

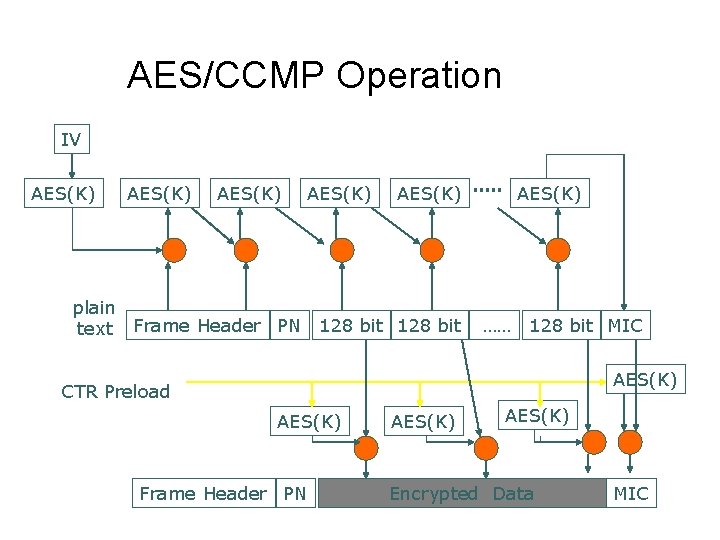
AES/CCMP Overview ¢ ¢ The operation has some similarity to Triple-DES l symmetric key and multiple passes of encryption The MSDU is divided into chains of 128 -bit stream. A recursive algorithm applied to each 128 -bit stream. The result of the first stream is used to encrypt the second stream, etc. It also used MIC against forgery attack.

AES/CCMP Operation IV AES(K) AES(K) plain text Frame Header PN 128 bit AES(K) …… 128 bit MIC AES(K) CTR Preload AES(K) Frame Header PN AES(K) Encrypted Data MIC

Summary ¢ ¢ ¢ Wireless LAN is ready for enterprise environment. l Many attacks l Solutions available to almost all known attacks It is acceptable to use WEP on SOHO networking, but not at the enterprise environment. Current best practice: l 802. 1 X+ + TKIP (WPA 1. 0) + MIC Evolution path (full 802. 11 i) l 802. 1 X+ + AES (WPA 2. 0) Add IP-VPN on WLAN for improved security. There will be new attacks to challenge today’s solutions.