Unify and Simplify Security Management http www sonofnights








- Slides: 25

Unify and Simplify: Security Management http: //www. sonofnights. com

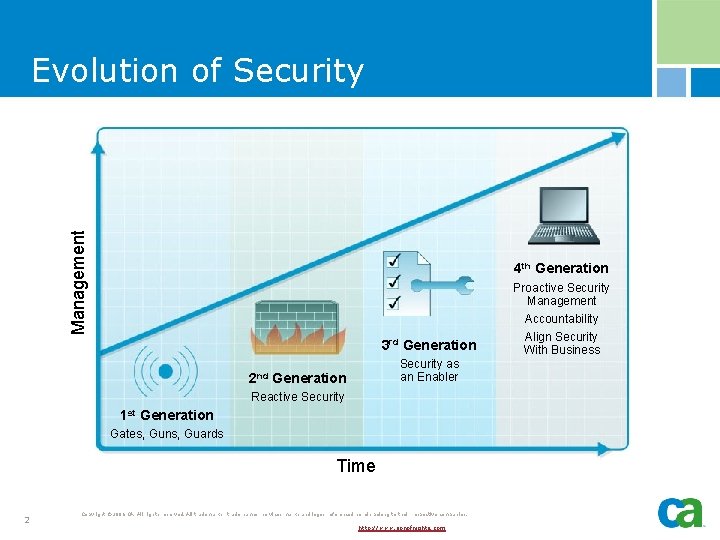
Management Evolution of Security 4 th Generation Proactive Security Management Accountability 3 rd Generation Security as an Enabler 2 nd Generation Reactive Security 1 st Generation Gates, Guns, Guards Time 2 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com Align Security With Business

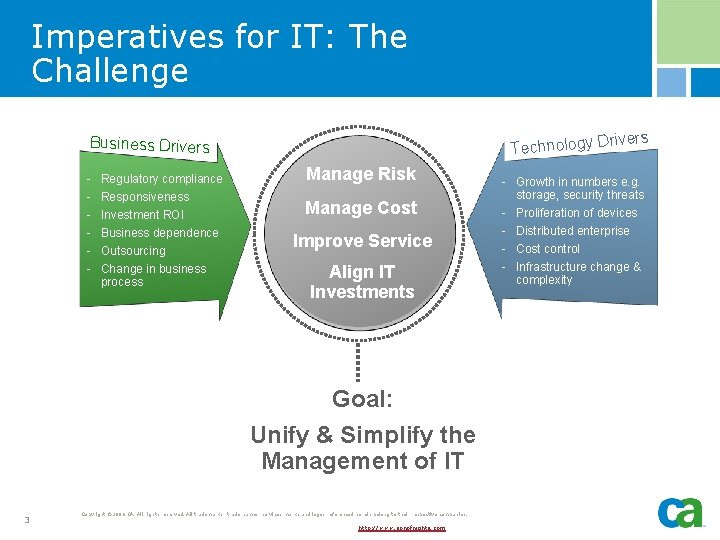
Imperatives for IT: The Challenge rivers Technology D Business Drivers - Regulatory compliance Responsiveness Investment ROI Business dependence Outsourcing Change in business process Manage Risk Manage Cost Improve Service Align IT Investments Goal: Unify & Simplify the Management of IT 3 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com - Growth in numbers e. g. storage, security threats - Proliferation of devices - Distributed enterprise - Cost control - Infrastructure change & complexity

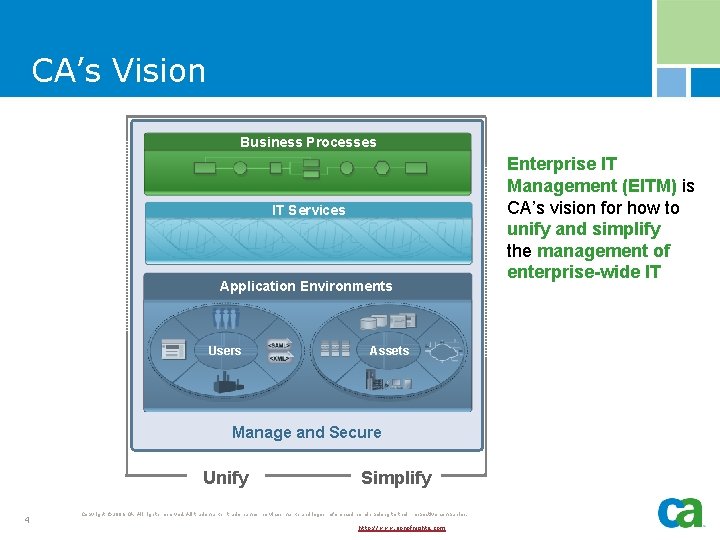
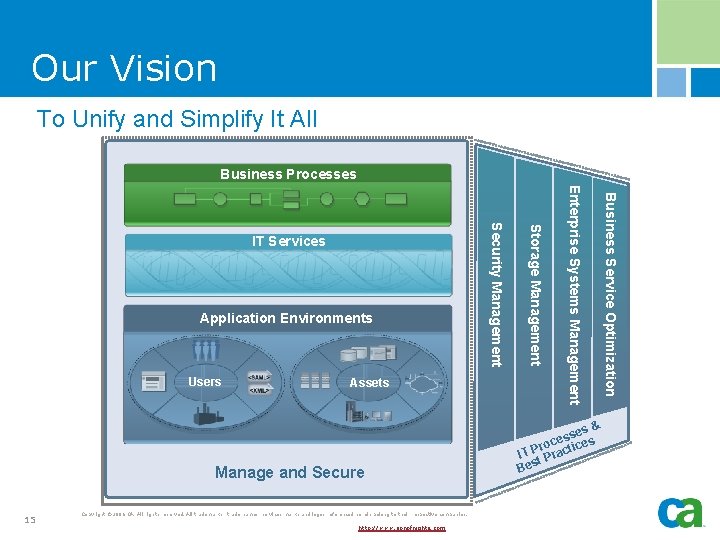
CA’s Vision Business Processes IT Services Application Environments Users Assets Manage and Secure Unify 4 Simplify Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com Enterprise IT Management (EITM) is CA’s vision for how to unify and simplify the management of enterprise-wide IT

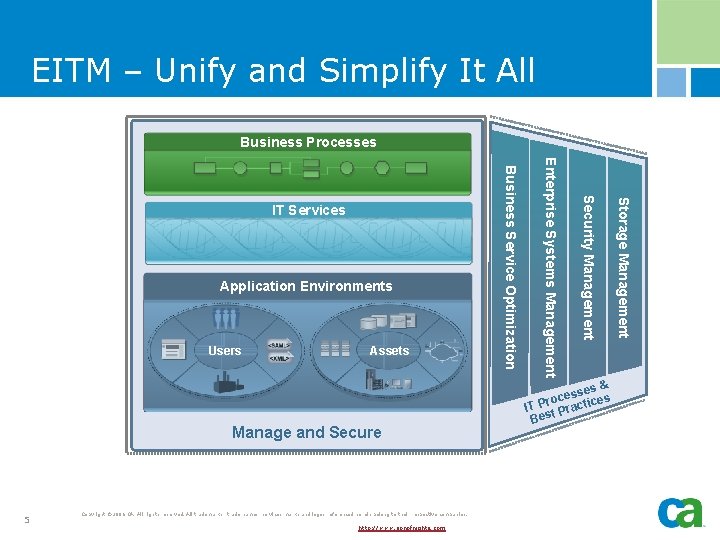
EITM – Unify and Simplify It All Business Processes Manage and Secure 5 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com & ses s s e c e ro IT P t Practic s Be Storage Management Assets Security Management Users Enterprise Systems Management Application Environments Business Service Optimization IT Services

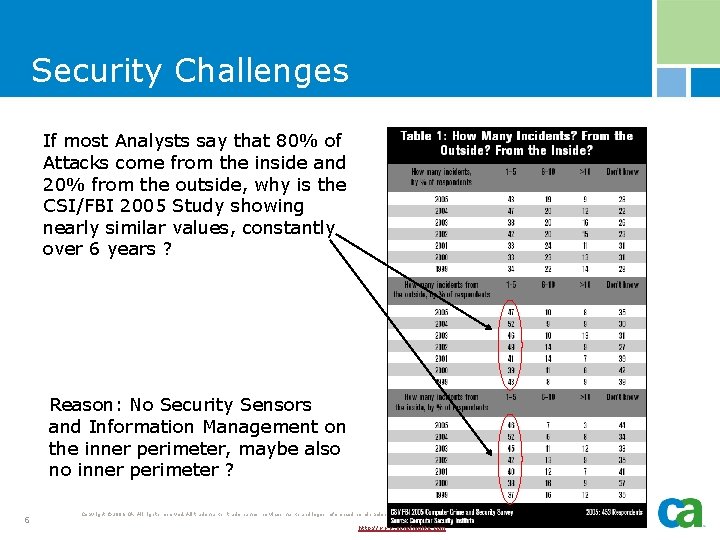
Security Challenges If most Analysts say that 80% of Attacks come from the inside and 20% from the outside, why is the CSI/FBI 2005 Study showing nearly similar values, constantly over 6 years ? Reason: No Security Sensors and Information Management on the inner perimeter, maybe also no inner perimeter ? 6 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

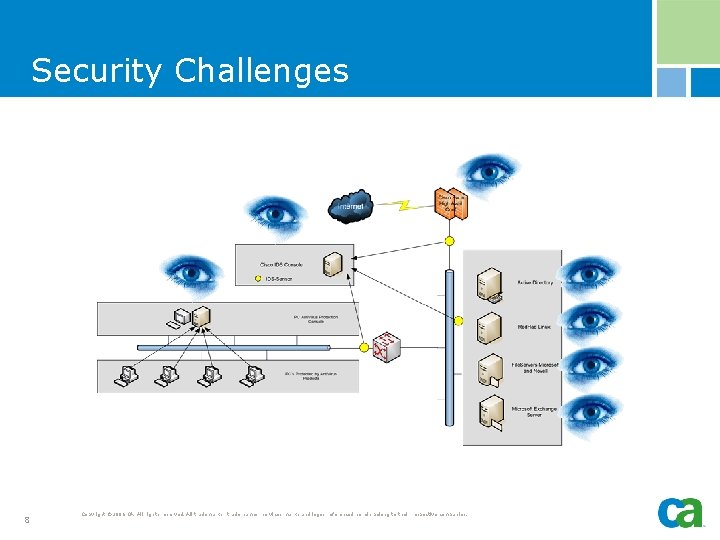
Security Challenges It used to be “simple” - stop attacks § New challenge: - Understanding the impact of security to business § Service Continuity § Efficiently manage identities and their access to assets § Make applications more secure – deep within the application and across the transaction § Enforce business policies § Comply with industry and government regulations Security Needs to be Managed 7 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Security Challenges 8 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

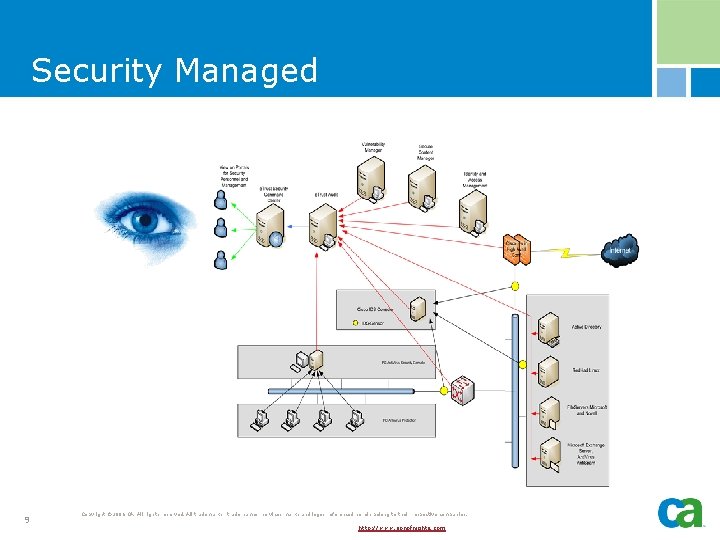
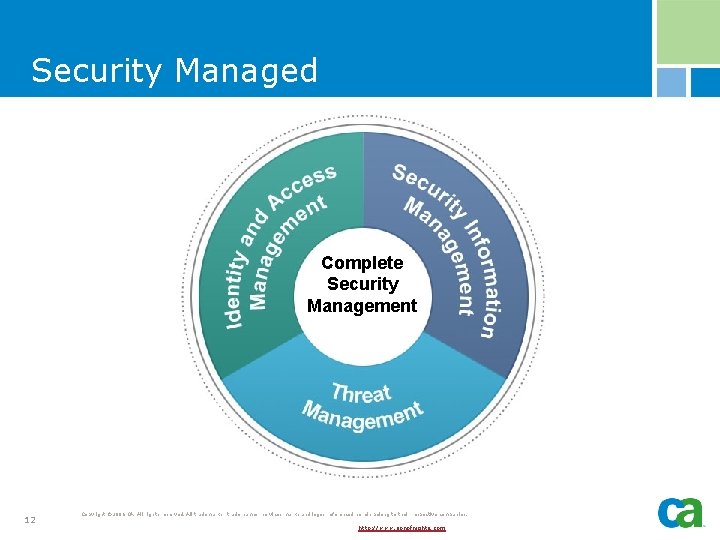
Security Managed 9 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

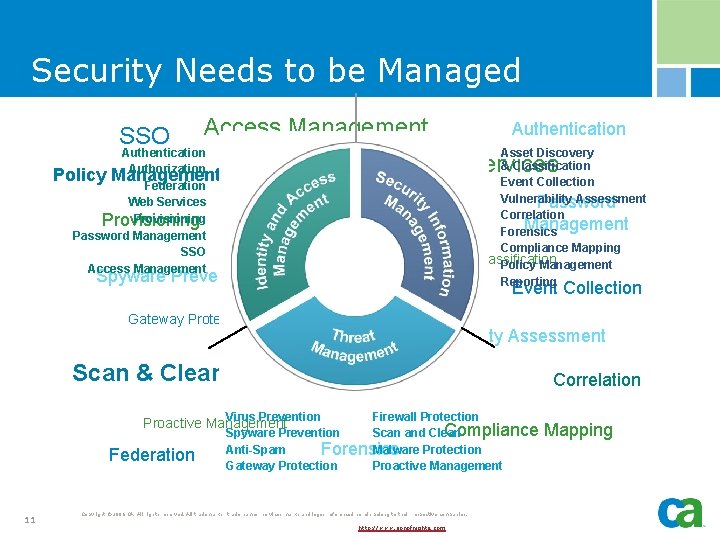
Security Needs to be Managed SSO Access Management Policy Management Provisioning Web Services Reporting Authorization Virus Protection Firewall Protection Vulnerability Assessment Malware Protection Proactive Management 10 Event Collection Anti-Spam Gateway Protection Federation Password Management Asset Discovery & Classification Spyware Prevention Scan & Clean Authentication Forensics Correlation Compliance Mapping Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Security Needs to be Managed SSO Access Management Authentication Authorization Policy Management Federation Web Services Provisioning Password Management SSO Access Management Asset Discovery & Classification Web Services Reporting Event Collection Vulnerability Assessment Password Correlation Management Forensics Protection Compliance Mapping Asset Discovery & Classification Policy Management Reporting Authorization Virus Spyware Prevention Anti-Spam Gateway Protection Scan & Clean Firewall Protection 11 Event Collection Vulnerability Assessment Malware Protection Virus Prevention Firewall Protection Compliance Spyware Prevention Scan and Clean Anti-Spam Malware Protection Forensics Gateway Protection Proactive Management Federation Authentication Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com Correlation Mapping

Security Managed Complete Security Management 12 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

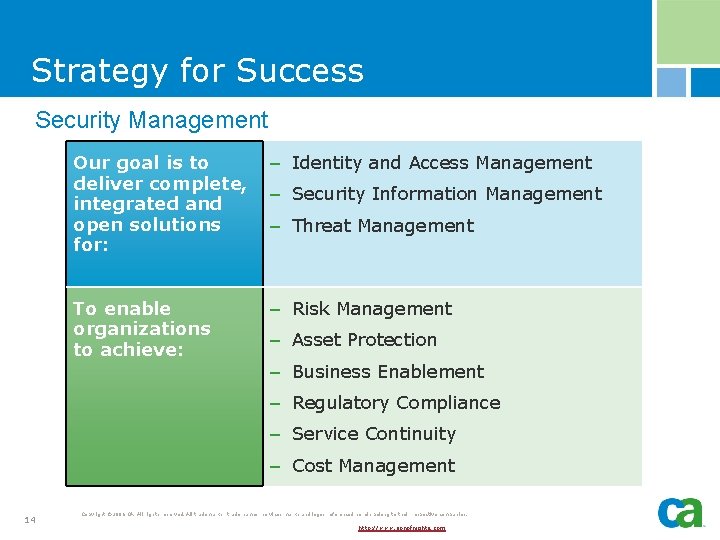
Strategy for Success Security Management § Enables organizations to clearly understand: - Who has access to what within their IT environment? - What is happening in that environment? - What actions need to be taken based on this information? 13 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Strategy for Success Security Management Our goal is to deliver complete, integrated and open solutions for: – Identity and Access Management To enable organizations to achieve: – Risk Management – Security Information Management – Threat Management – Asset Protection – Business Enablement – Regulatory Compliance – Service Continuity – Cost Management 14 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Our Vision To Unify and Simplify It All Business Processes Manage and Secure 15 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com es & s s e roc ices IT P Pract t Bes Business Service Optimization Assets Enterprise Systems Management Users Storage Management Application Environments Security Management IT Services

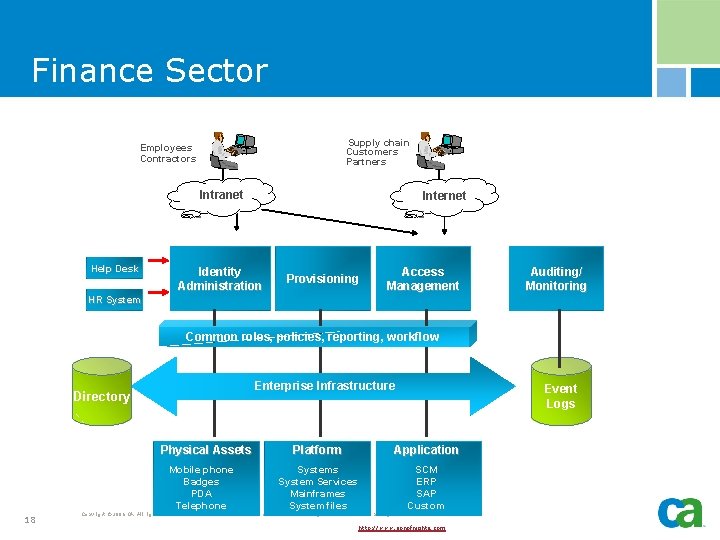
Finance Sector § A key to Basel II conformance is strong, effective internal IT controls, which can yield lower operational risk. § An complete, integrated identity management compliance infrastructure can improve IT controls, and can therefore have significant direct financial benefits. § Specifically, Basel II includes requirements for: - 17 Access rights administration Authentication Network Access Operating System Access Remote Access Logging and data collection Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Finance Sector Supply chain Customers Partners Employees Contractors Intranet Help Desk Internet Identity Administration Provisioning Access Management Auditing/ Monitoring HR System Common roles, policies, reporting, workflow Enterprise Infrastructure Directory Physical Assets Mobile phone Badges PDA Telephone 18 Event Logs Platform Application Systems System Services Mainframes System files SCM ERP SAP Custom Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Finance Sector Platform Components Platform Category Product Compliance Capabilities Identity Management & Provisioning Identity Manager §Delegated admin & self service of user identities §Centralized entitlement management §Approval & notification workflows §Immediate termination of access rights §Identifies and corrects “separation of duties” violations §Role-based allocation of resources Access Management Site. Minder §Authentication management §Centralized control of user access (authorization) §Role-based access control for protected files, and system services §Access control for Super-user privileges §Host intrusion prevention §Control of access to protected mainframe resources §Automated, continuous and unattended security file cleanup §Identifies user accounts (access rights) that are unused Access Control ACF 2, Top. Secret CA-Cleanup Monitoring SCC Audit §Centralized real-time collection and reporting of access control events from network, systems and applications §Asset value based vulnerability analysis and event correlations §Policy based filtering, correlation and alerting §Network, systems, and application level auditing and reporting 19 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Healthcare Sector § Has to protect clients (patients-) data § Conformance to HIPAA or similar Regulations § Specifically, these Regulations include requirements for: - Access rights administration - Authentication - Network Access - Operating System Access - Remote Access - Logging and data collection 20 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

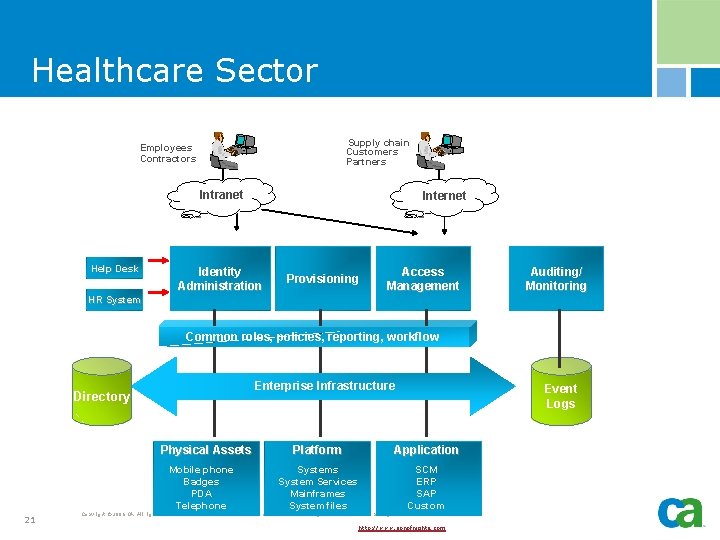
Healthcare Sector Supply chain Customers Partners Employees Contractors Intranet Help Desk Internet Identity Administration Provisioning Access Management Auditing/ Monitoring HR System Common roles, policies, reporting, workflow Enterprise Infrastructure Directory Physical Assets Mobile phone Badges PDA Telephone 21 Event Logs Platform Application Systems System Services Mainframes System files SCM ERP SAP Custom Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

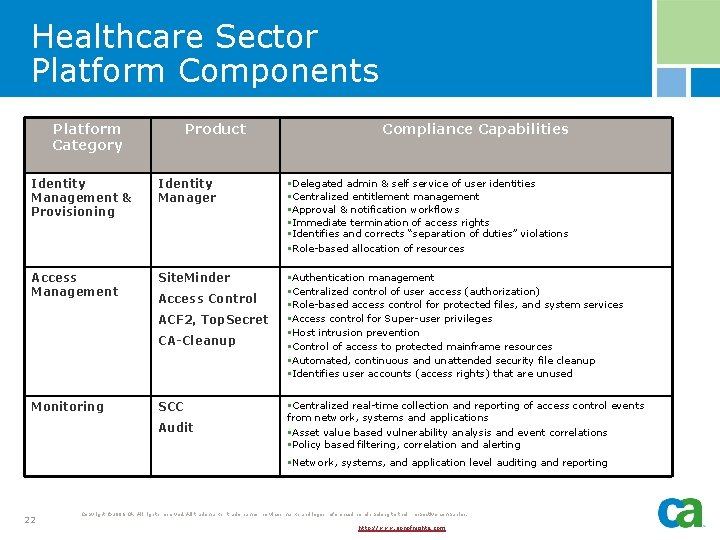
Healthcare Sector Platform Components Platform Category Product Compliance Capabilities Identity Management & Provisioning Identity Manager §Delegated admin & self service of user identities §Centralized entitlement management §Approval & notification workflows §Immediate termination of access rights §Identifies and corrects “separation of duties” violations §Role-based allocation of resources Access Management Site. Minder §Authentication management §Centralized control of user access (authorization) §Role-based access control for protected files, and system services §Access control for Super-user privileges §Host intrusion prevention §Control of access to protected mainframe resources §Automated, continuous and unattended security file cleanup §Identifies user accounts (access rights) that are unused Access Control ACF 2, Top. Secret CA-Cleanup Monitoring SCC Audit §Centralized real-time collection and reporting of access control events from network, systems and applications §Asset value based vulnerability analysis and event correlations §Policy based filtering, correlation and alerting §Network, systems, and application level auditing and reporting 22 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Oil & Gas Sector § Are belonging worldwide to the critical Infrastructure. § An complete, integrated identity management compliance infrastructure is a must in IT controls as they are targets in several ways (physically & digital). § Specifically, this includes requirements for: - 23 Access rights administration Authentication Network Access Operating System Access Remote Access Logging and data collection Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

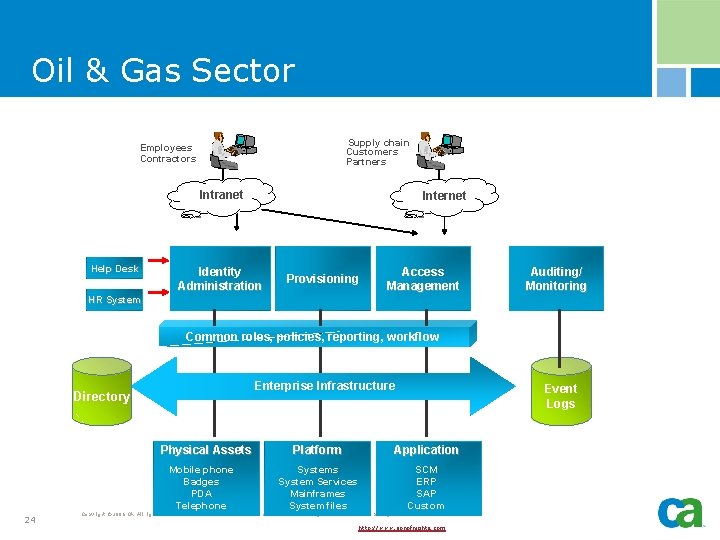
Oil & Gas Sector Supply chain Customers Partners Employees Contractors Intranet Help Desk Internet Identity Administration Provisioning Access Management Auditing/ Monitoring HR System Common roles, policies, reporting, workflow Enterprise Infrastructure Directory Physical Assets Mobile phone Badges PDA Telephone 24 Event Logs Platform Application Systems System Services Mainframes System files SCM ERP SAP Custom Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

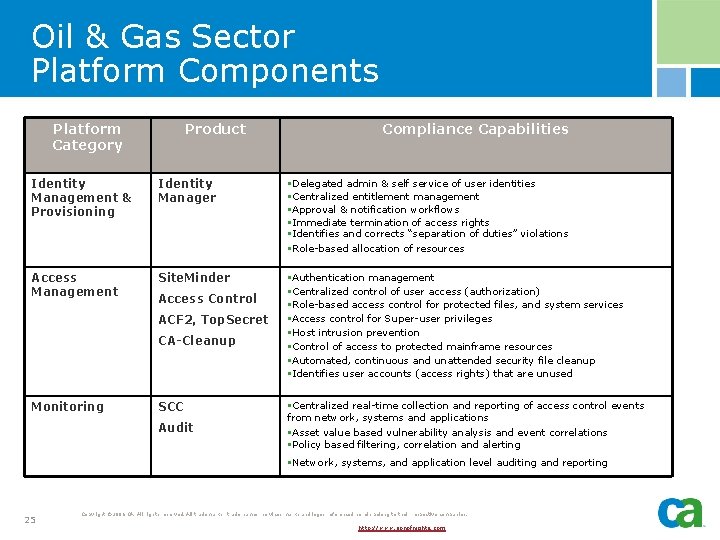
Oil & Gas Sector Platform Components Platform Category Product Compliance Capabilities Identity Management & Provisioning Identity Manager §Delegated admin & self service of user identities §Centralized entitlement management §Approval & notification workflows §Immediate termination of access rights §Identifies and corrects “separation of duties” violations §Role-based allocation of resources Access Management Site. Minder §Authentication management §Centralized control of user access (authorization) §Role-based access control for protected files, and system services §Access control for Super-user privileges §Host intrusion prevention §Control of access to protected mainframe resources §Automated, continuous and unattended security file cleanup §Identifies user accounts (access rights) that are unused Access Control ACF 2, Top. Secret CA-Cleanup Monitoring SCC Audit §Centralized real-time collection and reporting of access control events from network, systems and applications §Asset value based vulnerability analysis and event correlations §Policy based filtering, correlation and alerting §Network, systems, and application level auditing and reporting 25 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com

Telco, Utilities, Transportation § All these sectors can use the Oil & Gas Slides, just exchange the Sector Title. § Utilities are: Power, Water, Gas Distribution Companies or Organisations who deliver Energy to the public and therefore belonging worldwide to the critical infrastructure. § Transportation on high scale also belongs to the critical infrastructure. 26 Copyright © 2006 CA. All rights reserved. All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. http: //www. sonofnights. com