Understanding Operating Systems Fifth Edition Chapter 8 File























- Slides: 42

Understanding Operating Systems Fifth Edition Chapter 8 File Management

The File Manager • File Manager is also called the File management system and is the software responsible for: – Creating, deleting, modifying, controlling access to files • Provides support for libraries of programs to online users, for spooling operation, and for interactive computing Understanding Operating Systems, Fifth Edition 2

Responsibilities of the File Manager • Four tasks – Keep track of where each file is stored – Implement a policy that will: • Determine where and how files are stored • Efficiently use available storage space • Provide efficient file access – Allocate each file when a user has been cleared for access to it, then record its use – File deallocation • File returned to storage • Communicate file availability to others waiting for it Understanding Operating Systems, Fifth Edition 3

Responsibilities of the File Manager (continued) • File Manager’s Policy determines: – File storage location – System and user access files via device-independent commands • Who will have access to which file. This depends on two factors: • Flexibility of access to information (Factor 1) – Shared files – Providing distributed access – Allowing users to browse public directories Understanding Operating Systems, Fifth Edition 4

Responsibilities of the File Manager (continued) • Subsequent protection (Factor 2) – Protect files against system malfunctions – Security checks • Account numbers, passwords, lockwords • File allocation – Activate secondary storage device, load file into memory, update records • File deallocation – Update file tables, rewrite file (if revised), notify waiting processes of file availability Understanding Operating Systems, Fifth Edition 5

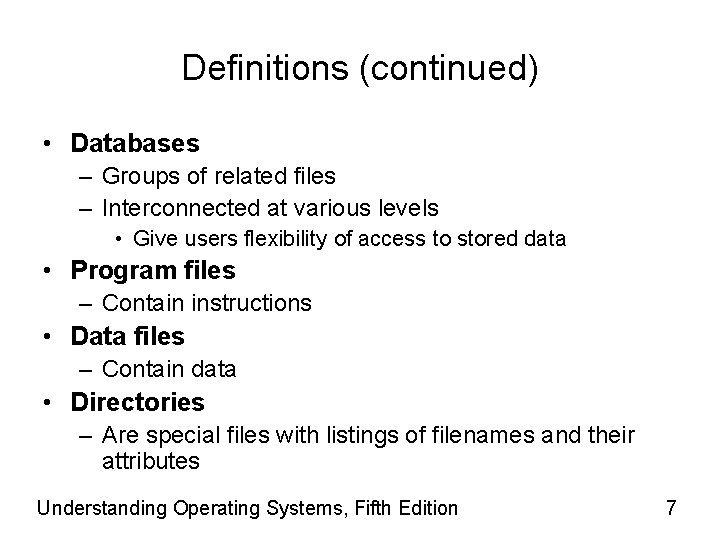
Definitions • Field – Group of related bytes (e. g. last_name, first_name, age) that can be identified by the user with a name, type, and size. • Record – Group of related fields • File – Group of related records that contains information to be used by specific application programs to generate reports. This type of file contains data and is sometimes called a flat file because it has no connections to other files and has no dimensionality. Understanding Operating Systems, Fifth Edition 6

Definitions (continued) • Databases – Groups of related files – Interconnected at various levels • Give users flexibility of access to stored data • Program files – Contain instructions • Data files – Contain data • Directories – Are special files with listings of filenames and their attributes Understanding Operating Systems, Fifth Edition 7

Definitions (continued) Understanding Operating Systems, Fifth Edition 8

Interacting with the File Manager • User interacts with the File Manager with commands that are either: – Embedded in program • OPEN, CLOSE, READ, WRITE, MODIFY – Submitted interactively • CREATE, DELETE, RENAME, COPY • Device independent – Physical location knowledge not needed • Cylinder, surface, sector – Device medium knowledge not needed • Tape, magnetic disk, optical disc, flash storage – Network knowledge not needed Understanding Operating Systems, Fifth Edition 9

Interacting with the File Manager (continued) Understanding Operating Systems, Fifth Edition 10

Interacting with the File Manager (continued) • Each of the logical commands (READ, WRITE etc. ) can be broken into lower-level signals. – Example: READ • Move read/write heads to record cylinder • Wait for rotational delay (sector containing record passes under read/write head) • Activate appropriate read/write head and read record • Transfer record to main memory • Send flag indicating free device for another request • File Manager does all of this and performs error checking and correction – No need for error-checking code in programs Understanding Operating Systems, Fifth Edition 11

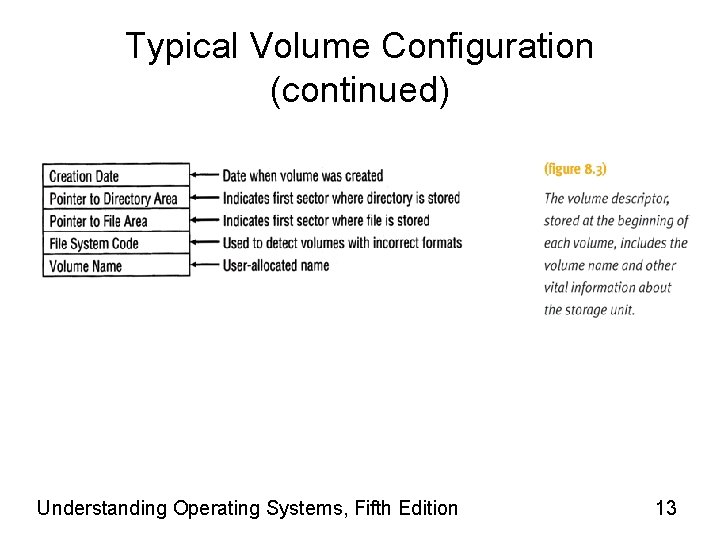
Typical Volume Configuration • Secondary storage unit can be removable (such as CDs, DVDs etc) or non-removable (such as hard disks). Each storage unit is considered a volume. – A multifile volume contains many files – Multivolume files • These are extremely large files spread across several volumes • Each volume is given a name – This is managed by the File manager and it writes this descriptive information in an easily accessible place • Innermost part of CD, beginning of tape, first sector of outermost track Understanding Operating Systems, Fifth Edition 12

Typical Volume Configuration (continued) Understanding Operating Systems, Fifth Edition 13

Typical Volume Configuration (continued) • Master file directory (MFD) • Is stored immediately after volume descriptor • MFD lists: – Names and characteristics of every file in volume • File names (program files, data files, system files) – Any subdirectories • If supported by file manager – The remainder of the volume • Is used for file storage Understanding Operating Systems, Fifth Edition 14

Typical Volume Configuration (continued) • Single directory per volume – Supported by early operating systems • Disadvantages – – – Long search time for individual file Directory space filled before disk storage space filled Users cannot create subdirectories Users cannot safeguard their files Each program needs unique name • Even those serving many users Understanding Operating Systems, Fifth Edition 15

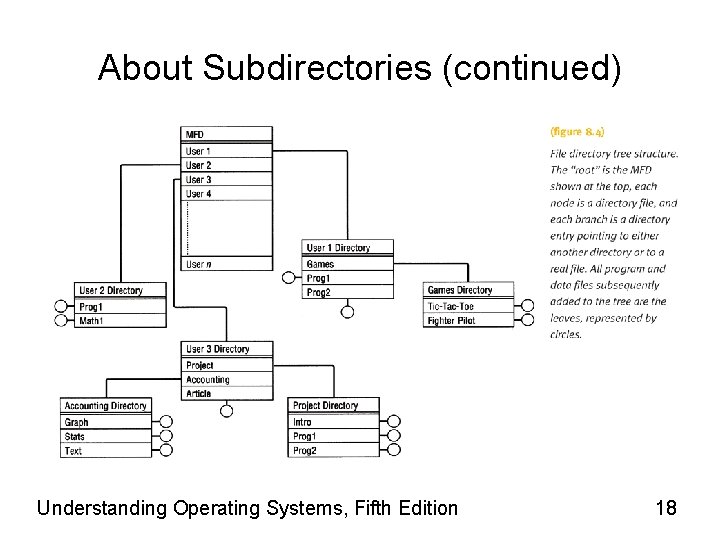
About Subdirectories • Newer File Managers – Create MFD for each volume • Contains file and subdirectory entries – Improvement over single directory scheme • Problems remain: users unable to logically group files by creating their own subdirectories. • Subdirectory – Is created when a user opens an account in the computer system – Is treated as a file • Though flagged in MFD as subdirectory • Has unique properties since its records are filenames pointing to files Understanding Operating Systems, Fifth Edition 16

About Subdirectories (continued) • File managers today – Users create own subdirectories (folders) • Related files grouped together – Implemented as upside-down tree • Efficient system searching of individual directories • May require several directories to reach file Understanding Operating Systems, Fifth Edition 17

About Subdirectories (continued) Understanding Operating Systems, Fifth Edition 18

About Subdirectories (continued) • File descriptor – Filename: ASCII code – File type: organization and usage • System dependent – File size: for convenience – File location • First physical block identification – – Date and time of creation Owner Protection information: access restrictions Record size: fixed size, maximum size Understanding Operating Systems, Fifth Edition 19

File-Naming Conventions • Filename components – Relative filename and extension • Complete filename (absolute filename) – Includes all path information • Relative filename – – Name without path information Appears in directory listings, folders Provides filename differentiation within directory Varies in length • One to many characters • Operating system specific Understanding Operating Systems, Fifth Edition 20

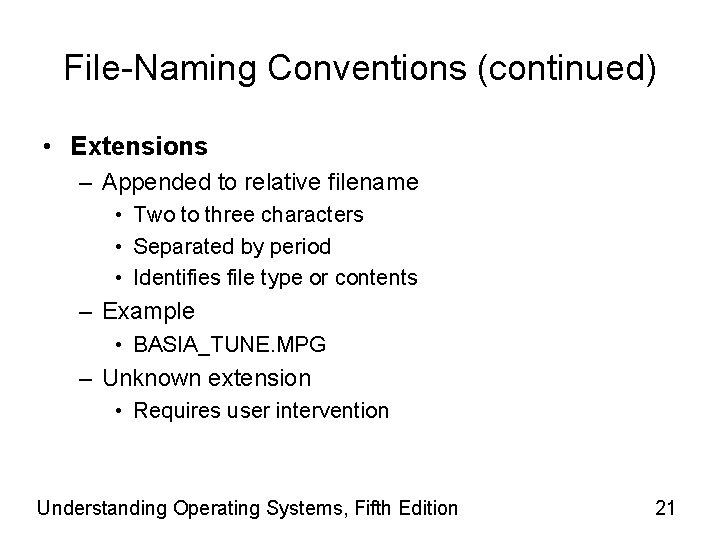
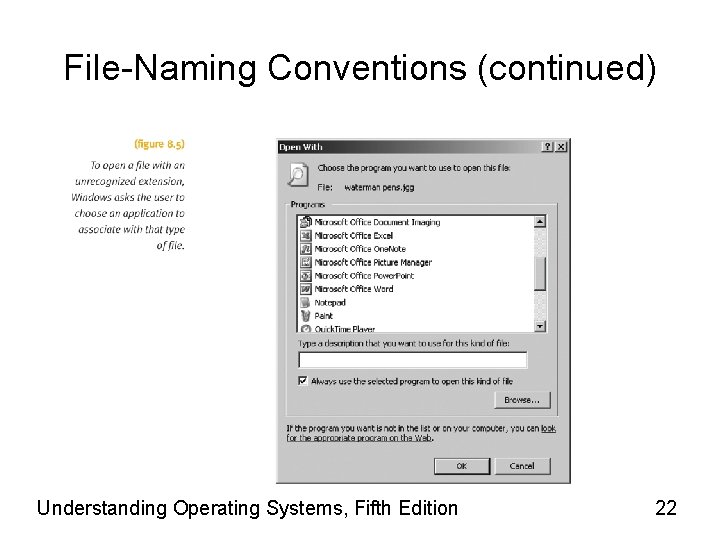
File-Naming Conventions (continued) • Extensions – Appended to relative filename • Two to three characters • Separated by period • Identifies file type or contents – Example • BASIA_TUNE. MPG – Unknown extension • Requires user intervention Understanding Operating Systems, Fifth Edition 21

File-Naming Conventions (continued) Understanding Operating Systems, Fifth Edition 22

File-Naming Conventions (continued) • Operating system specifics – Windows • Drive label and directory name, relative name, and extension – Network with Open VMS Alpha • Node, volume or storage device, directory, subdirectory, relative name and extension, file version number – UNIX/Linux • Forward slash (root), first subdirectory, subsubdirectory, file’s relative name Understanding Operating Systems, Fifth Edition 23

File Organization • Arrangement of records within files • All files composed of records • Modify command – Request to access record within a file Understanding Operating Systems, Fifth Edition 24

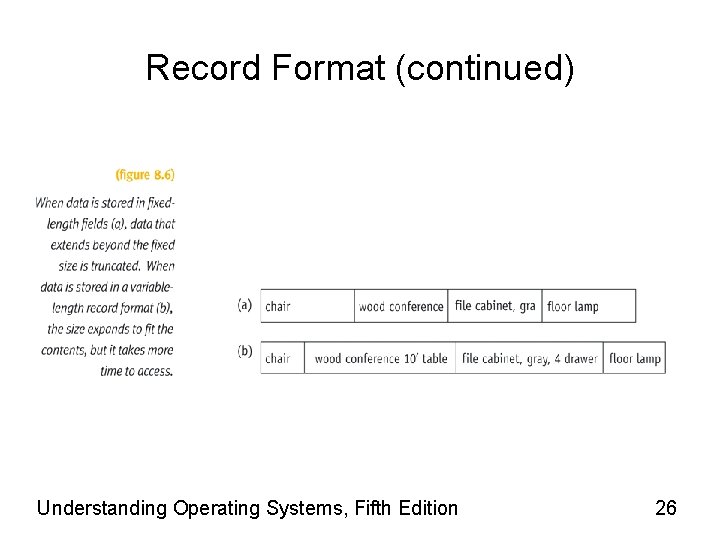
Record Format • Fixed-length records – Easiest to access directly – The record size is critical – Ideal for data files • Variable-length records – – Difficult to access directly No empty storage space and no character truncation File descriptor stores record format Used with files accessed sequentially • Text files, program files – Used with files using index to access records Understanding Operating Systems, Fifth Edition 25

Record Format (continued) Understanding Operating Systems, Fifth Edition 26

UNIX File Management (from Chapter 13) • Three file types – Directories – Ordinary files – Special files • Each enjoys certain privileges • Directories – Are files that maintain the hierarchical structure of file system – Users allowed to read information in directory files – Only system allowed directory file modification Understanding Operating Systems, Fifth Edition 27

UNIX File Management (continued) • Ordinary files – Are those in which users store information – Their protection is based on user requests and are related to the read, write, execute, delete functions performed on a file • Special files – – Device drivers providing I/O hardware interface Appear as entries in directories Part of file system (most in /dev directory) The name of the special file indicates type of device association (e. g. /dev/hd, /dev/lp) Understanding Operating Systems, Fifth Edition 28

UNIX File Management (continued) • Files stored as sequences of bytes – No structure imposed • Text files – Character strings • Lines delimited by line feed or new line character • Binary files – Sequences of binary digits (bits) • Grouped into words as they appear in memory during program execution • Structure of files – Controlled by programs using them and not by UNIX Understanding Operating Systems, Fifth Edition 29

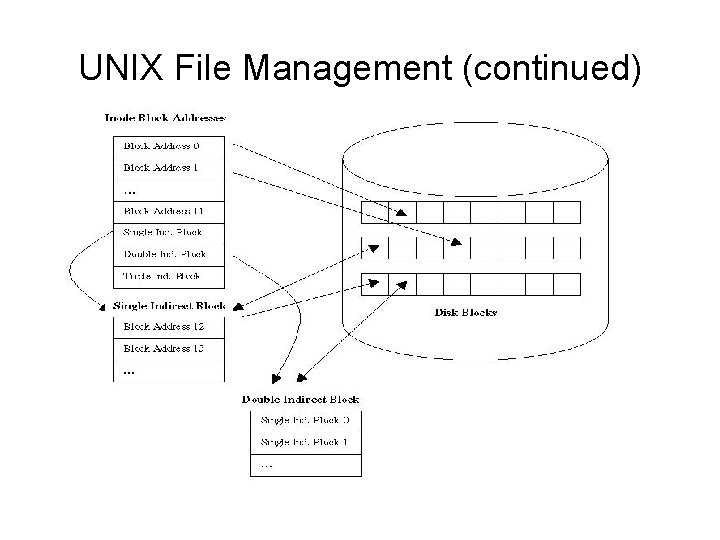
UNIX File Management (continued) • Organizes disk into blocks of 512 bytes each • Divides disk into four basic regions – First region (address 0): reserved for booting – Second region: contains disk size and other regions’ boundaries – Third region includes: list of file definitions called the “i-list”, which is a list of file descriptors (called “i-nodes”), one for each file. The position of an i-node is called an “i-number” and this uniquely identifies a file. – Remaining region: free blocks available for file storage • Files stored in contiguous empty blocks – Simple allocation and no need to compact Understanding Operating Systems, Fifth Edition 30

UNIX File Management (continued) • “i-node” • Each entry in i-list called an “i-node” (or inode) – Contains 13 disk addresses • Contains specific file information – – – Owner’s identification Protection bits, physical address, file size Time of creation, last use, and last update Number of links File type • Directory, ordinary file, or special file Understanding Operating Systems, Fifth Edition 31

UNIX File Management (continued)

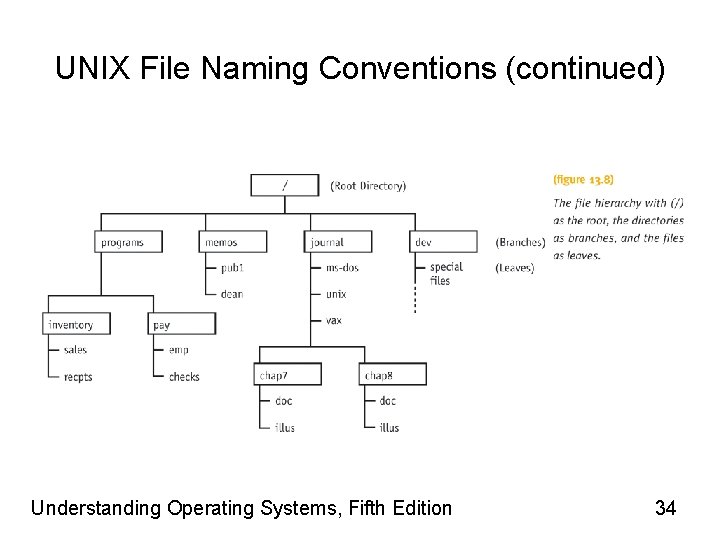
UNIX File Naming Conventions • Case-sensitive filenames • 255 character length • While UNIX does not impose any file naming conventions, system programs such as compilers expect files to have suffixes (“extensions”). - E. g. prog 1. c or prog 1. java • Supports hierarchical tree file structure – Root directory identified by slash (/) – The names of other directories are preceded by the slash (/), which is used as a delimiter E. g. /programs/pay/checks where checks is the actual file (see figure 13. 8) The first slash indicates that this is an absolute path name that starts at the root directory. A relative path name would be pay/checks. Understanding Operating Systems, Fifth Edition 33

UNIX File Naming Conventions (continued) Understanding Operating Systems, Fifth Edition 34

UNIX File Naming Conventions (continued) • Path name rules – If a path name starts with a slash, the path starts at the root directory – Path name can be either: • One name or a list of names separated by slashes • Last name on a list is the name of the file requested – Using two periods (. . ) in path name • Moves you upward in hierarchy (closer to root). This is the only way to go up the hierarchy • All other path names go down tree – Spaces not allowed within path names Understanding Operating Systems, Fifth Edition 35

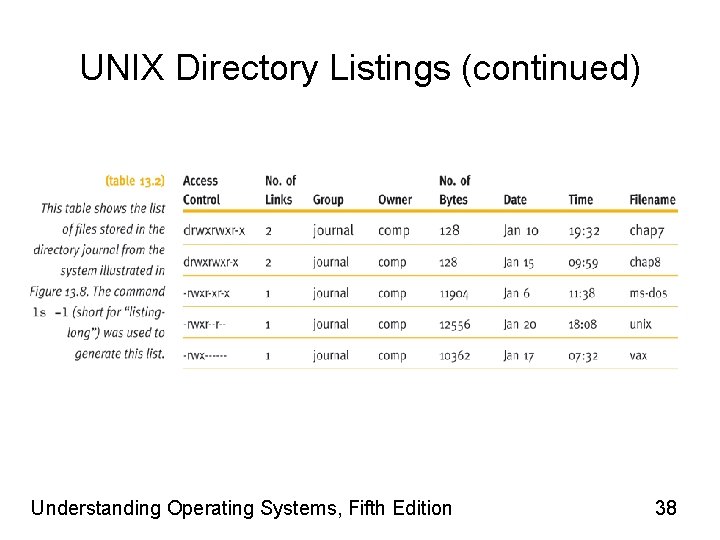
UNIX Directory Listings • Table 13. 2 shows a “long listing” of files in a directory with eight pieces of information for each file • First column – Shows file type and access privileges for each file • First character: nature of file or directory (‘d’ indicates a directory and ‘-’ indicates an ordinary file) • Next three characters: show the access privileges granted to the file owner (‘r’ indicates read, ‘w’ indicates write, and ‘x’ indicates execute) • Next three characters: show the access privileges granted to other members of the user’s group (e. g. students in a class could be a group) • Last three characters: show the access privileges granted to users at large (system-wide) Understanding Operating Systems, Fifth Edition 36

UNIX Directory Listings (continued) • Second column – Indicates number of links (number of aliases) • Referring to same physical file • Aliases (links) – Important UNIX feature: support file sharing • Several users work together on same project – Shared files appear in different directories belonging to different users – Filename: may be different from directory to directory – Eventually number will indicate when file no longer needed: can be deleted Understanding Operating Systems, Fifth Edition 37

UNIX Directory Listings (continued) Understanding Operating Systems, Fifth Edition 38

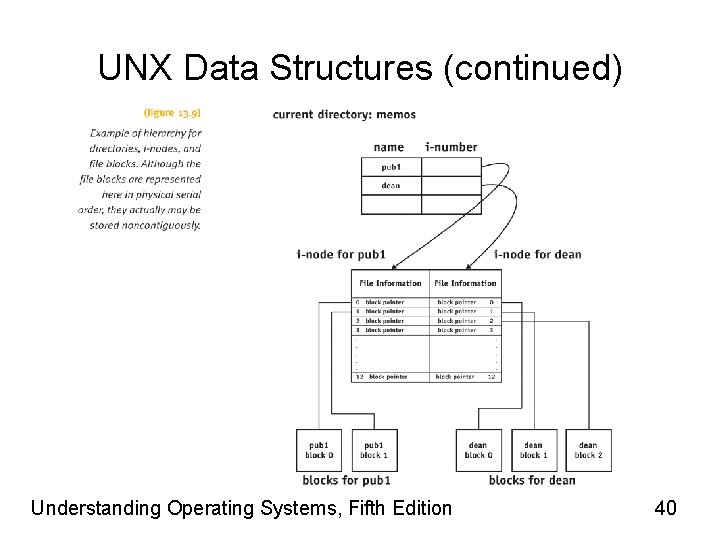
UNIX Data Structures • File descriptors divided into parts – Hierarchical directories • Contain filename and i-number • Pointer to another location: i-node – i-node • Contains rest of information – i-nodes stored in reserved part of device • Where directory resides – i-node has 13 pointers (0– 12) Understanding Operating Systems, Fifth Edition 39

UNX Data Structures (continued) Understanding Operating Systems, Fifth Edition 40

UNIX Data Structures (continued) • When file created – i-node allocated to it – Directory entry with filename and i-node number created Understanding Operating Systems, Fifth Edition 41

UNIX Data Structures (continued) • When file linked – Directory entry created with new name – Original i-node number and link-count field in the inode incremented by one • When shared file deleted – Link-count field in i-node decremented by one – When count reaches zero • Directory entry erased • Deallocate all disk blocks, along with its i-node entry in the disk i-list Understanding Operating Systems, Fifth Edition 42