Understanding FISMA ISC2 CAP Certified Authorization Professional Donald


![Definition � “. . [a] model for enabling convenient, on-demand network access to a Definition � “. . [a] model for enabling convenient, on-demand network access to a](https://slidetodoc.com/presentation_image_h2/5bffd779b5e3c9ae232bdbb053dd9da3/image-5.jpg)














- Slides: 33

Understanding FISMA & (ISC)2 CAP Certified Authorization Professional Donald E. Hester CISSP, CISA, CAP, CRISC, MCT, MCITP, MCTS, MCSE Security, Security+, CTT+ 1 www. netcomlearning. com

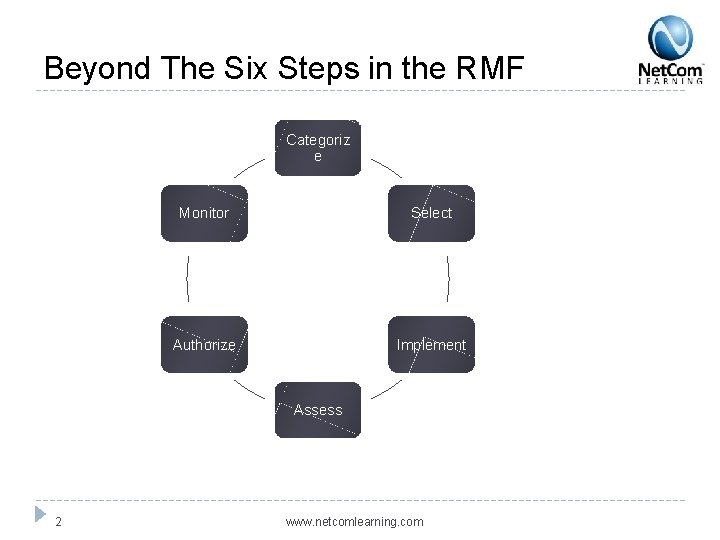
Beyond The Six Steps in the RMF Categoriz e Monitor Select Authorize Implement Assess 2 www. netcomlearning. com

Cloud Computing Federal Cloud Computing Strategy “Cloud First policy” Image: NASA

What is Cloud Computing? � The “Cloud” � Buzz word � Overused cliché � Ill defined � Many different definitions � Marketing term � All hype � The “unknown path” � Service provider “____-as-a-service” � Nebulous 4 www. netcomlearning. com
![Definition a model for enabling convenient ondemand network access to a Definition � “. . [a] model for enabling convenient, on-demand network access to a](https://slidetodoc.com/presentation_image_h2/5bffd779b5e3c9ae232bdbb053dd9da3/image-5.jpg)
Definition � “. . [a] model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e. g. networks, servers, storage, applications, services) that can be provisioned and released with minimal management effort or service provider interactions. ” � NIST �A 5 & Cloud Security Alliance utility model of technology delivery. www. netcomlearning. com

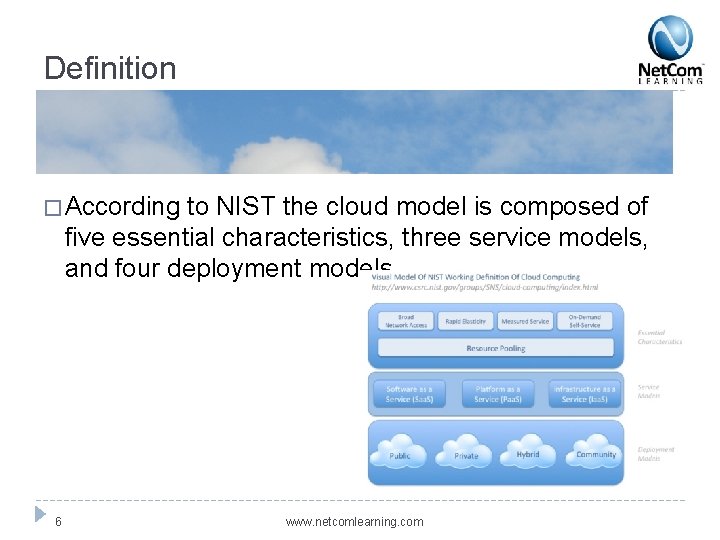
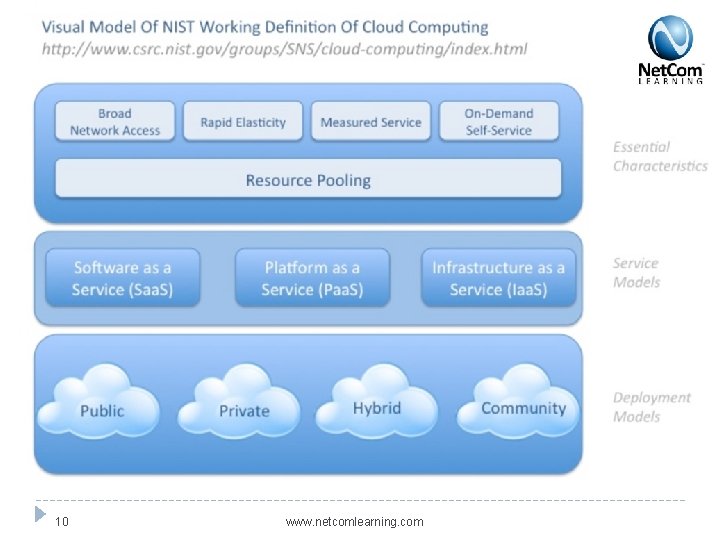
Definition � According to NIST the cloud model is composed of five essential characteristics, three service models, and four deployment models. 6 www. netcomlearning. com

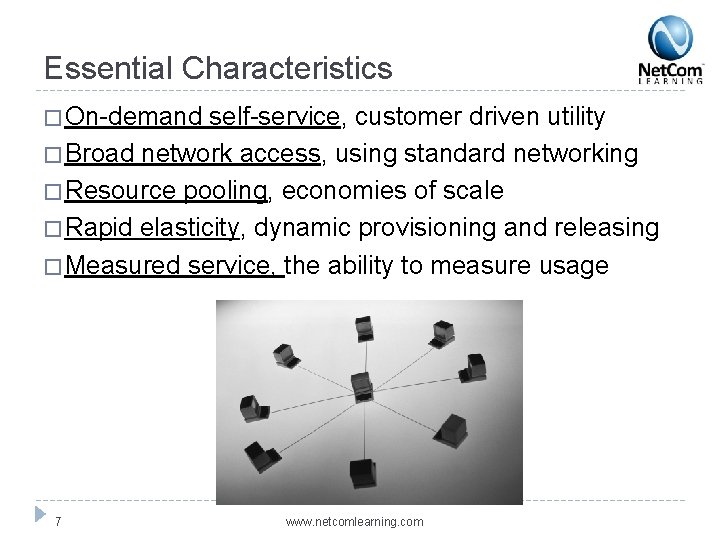
Essential Characteristics � On-demand self-service, customer driven utility � Broad network access, using standard networking � Resource pooling, economies of scale � Rapid elasticity, dynamic provisioning and releasing � Measured service, the ability to measure usage 7 www. netcomlearning. com

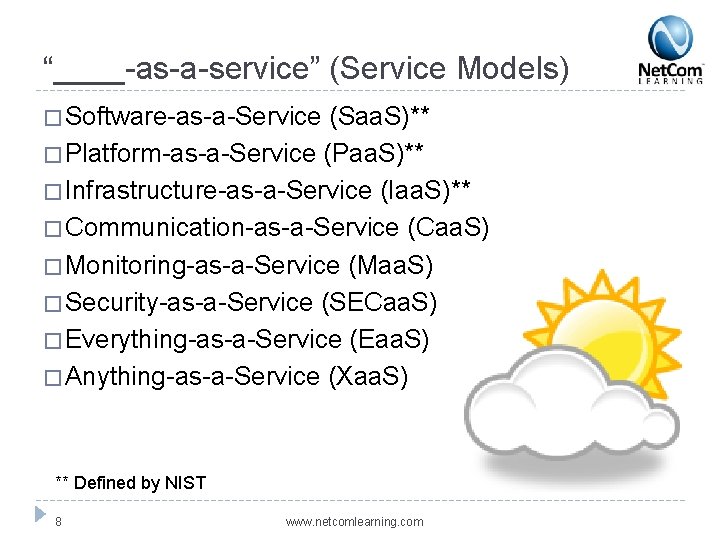
“____-as-a-service” (Service Models) � Software-as-a-Service (Saa. S)** � Platform-as-a-Service (Paa. S)** � Infrastructure-as-a-Service (Iaa. S)** � Communication-as-a-Service (Caa. S) � Monitoring-as-a-Service (Maa. S) � Security-as-a-Service (SECaa. S) � Everything-as-a-Service (Eaa. S) � Anything-as-a-Service (Xaa. S) ** Defined by NIST 8 www. netcomlearning. com

Cloud Flavors (Deployment Models) � Private Cloud � Operated solely for one organization � In-sourcing � Community � Operated � Public Cloud for a group of similar organizations Cloud � Outsourced � Multi-tenant � Hybrid Cloud � Combination 9 of the above www. netcomlearning. com

10 www. netcomlearning. com

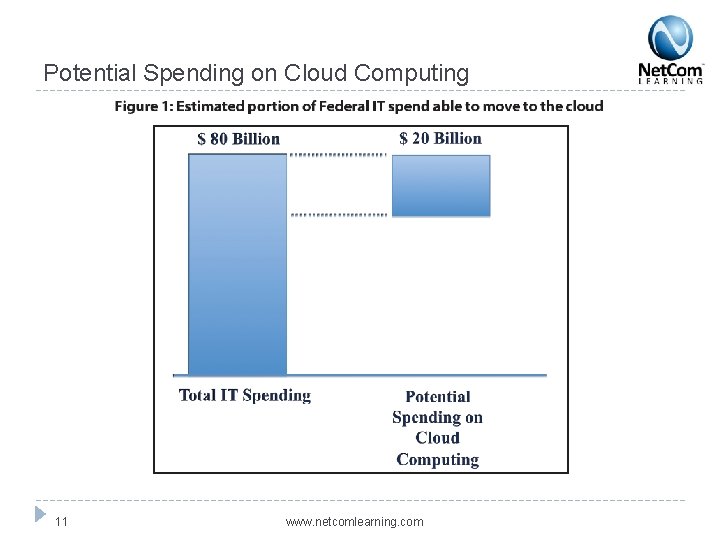
Potential Spending on Cloud Computing 11 www. netcomlearning. com

Reasons Efficiency Agility Innovatio n 12 www. netcomlearning. com

Benefits � Save time and money on provisioning new services � Less time spent on deployment � Move capital investment to operational expenses � Instant test bed � Enables IT systems to be scalable and elastic � Provision computing resources as required, on-demand � No need to own data center infrastructure (for public cloud service) 13 www. netcomlearning. com

Benefits � Energy saving (green) � Increased utilization, less idle time � Cost based on usage � More effective use of capital resources ($) � Better service � Allows IT staff to focus on core competencies � Repurpose IT staff for more customer service � Outsource to esoteric experts � 24/7 service and support � Economies of scale 14 www. netcomlearning. com

Cloud Provider Benefits (NIST SP 800 -144) � They will have specialized staff � The platform will typically be more uniform � They have the ability to scale and add redundancy � Better backup and recovery � May support a greater number of mobile devices � Data may be centralized and not on laptops 15 www. netcomlearning. com

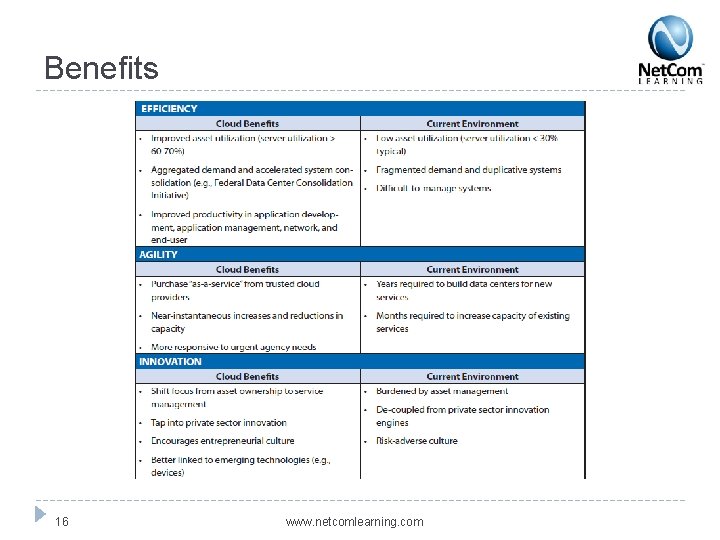
Benefits 16 www. netcomlearning. com

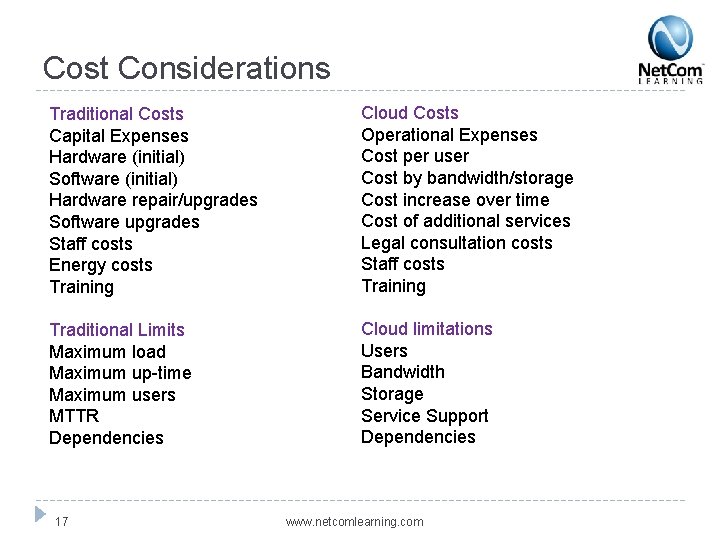
Cost Considerations Traditional Costs Capital Expenses Hardware (initial) Software (initial) Hardware repair/upgrades Software upgrades Staff costs Energy costs Training Cloud Costs Operational Expenses Cost per user Cost by bandwidth/storage Cost increase over time Cost of additional services Legal consultation costs Staff costs Training Traditional Limits Maximum load Maximum up-time Maximum users MTTR Dependencies Cloud limitations Users Bandwidth Storage Service Support Dependencies 17 www. netcomlearning. com

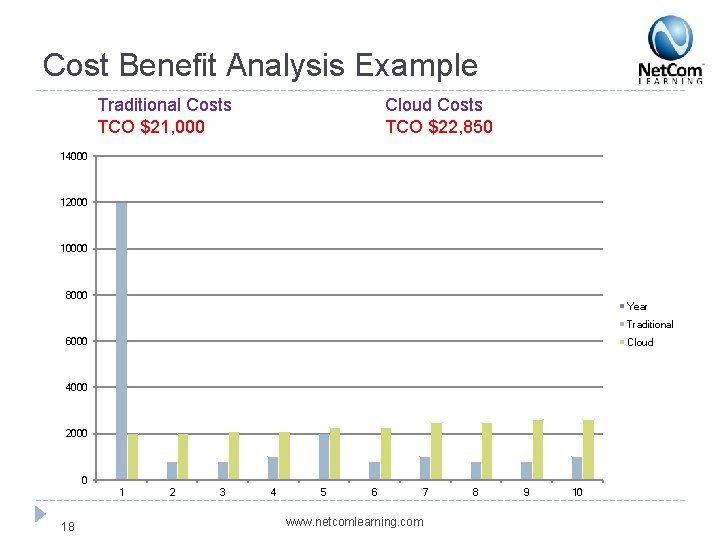
Cost Benefit Analysis Example Traditional Costs TCO $21, 000 Cloud Costs TCO $22, 850 14000 12000 10000 8000 Year Traditional 6000 Cloud 4000 2000 0 1 18 2 3 4 5 6 7 www. netcomlearning. com 8 9 10

Cloud Risks � Where’s My Data? � The Bad Divorce � Trust but Verify � “I thought you knew” � I didn’t think of that � Clarify � Consider � Expectations, Put it in Writing � Compatibility 19 www. netcomlearning. com

Where’s My Data? � In the information age your key asset is information. � Some information requires protection � (Credit Card Data, Student Records, SSN, etc…) � Your information could be anywhere in the world � You may loss access to your data (availability) � ISP failure � Service provider failure � Failure to pay (service provider stops access) 20 www. netcomlearning. com

The Bad Divorce � “Vendor Lock” � All relationships come to an end � Let you down, had a breach, SLA performance etc… � The company fails/gets sold � Introductory pricing or it goes up over time � Transition � How � Lack to new vendor or in-source will you get your data back? of Portability between Paa. S Clouds � Example, something built for Google won’t work for Share. Point or Amazon � Get 21 a prenup – get it in the contract up front www. netcomlearning. com

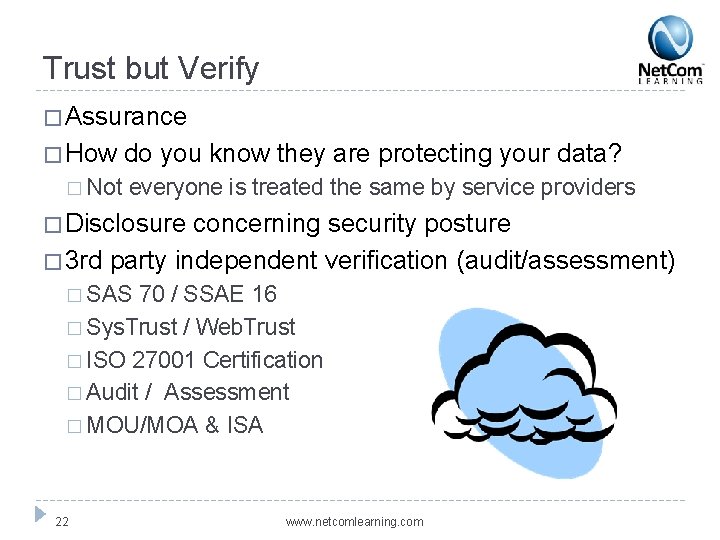
Trust but Verify � Assurance � How � Not do you know they are protecting your data? everyone is treated the same by service providers � Disclosure concerning security posture � 3 rd party independent verification (audit/assessment) � SAS 70 / SSAE 16 � Sys. Trust / Web. Trust � ISO 27001 Certification � Audit / Assessment � MOU/MOA & ISA 22 www. netcomlearning. com

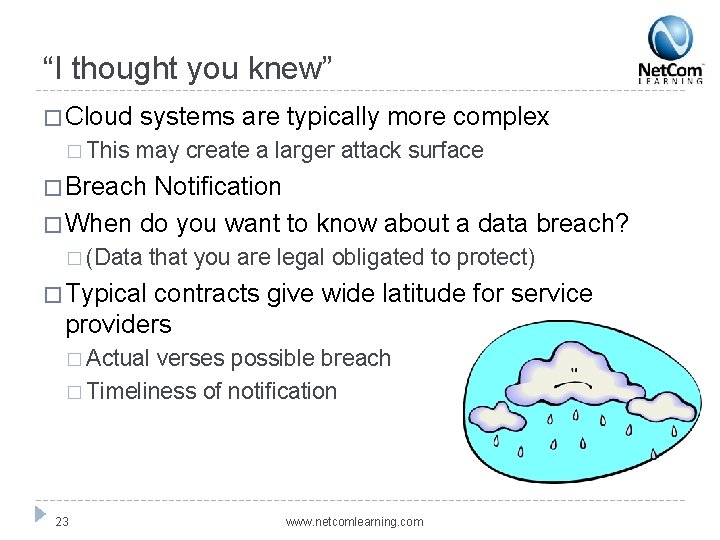
“I thought you knew” � Cloud � This systems are typically more complex may create a larger attack surface � Breach Notification � When do you want to know about a data breach? � (Data that you are legal obligated to protect) � Typical contracts give wide latitude for service providers � Actual verses possible breach � Timeliness of notification 23 www. netcomlearning. com

I didn’t think of that � Dependencies � Infrastructure – Internet � Authentication management (SSO) � Operational budget � Greater dependency on 3 rd parties � Other considerations � Complex legal issues � Multi-tenancy � Transborder data flow � Jurisdiction and Regulation � Support for Forensics 24 www. netcomlearning. com

Clarify � What do they mean by “Cloud” � Establish clear responsibilities and accountability � Your expectations � Cost of compensating controls � What will happen with billing disputes � Will your data be in a multi-tenant environment � What controls will you have 25 www. netcomlearning. com

Consider � The reputation of the service provider � Track record of issues � Large or small, likelihood of change � Vendor ‘supply chain management’ issues � The reliability of the service or technology � Is the technology time tested � Competency of cloud provider � Typically you have no control over upgrades and changes � Training 26 for staff www. netcomlearning. com

Compatibility � When will they upgrade their service? � Will they be ready when you are ready for an upgrade of dependent software � Will you be ready when they are ready to upgrade � Browser-based Risks and Risk Remediation � What software will be required on the client side? � Java � Flash � Active-X � Silverlight � HTML 27 5 www. netcomlearning. com

New attack vectors � Hypervisor complexity � Data leakage (multi-tenant environment) � Man in the Middle � Browser vulnerabilities � Mobile device vulnerabilities 28 www. netcomlearning. com

Service Agreements � Service Level Agreement (SLA) � Some are predefined and non-negotiable � Some are negotiable (typically cost more) � Terms of Service � May cover privacy � Breach notification � Licensing � Acceptable use (What you can and can’t do) � Limitations on liability (Typically in the favor of the service provider) � Modifications of the terms of service (Do you want this? ) � Data ownership 29 www. netcomlearning. com

Traditional risks no matter where you go � Insider threat, � Instead � Access � How of your staff it is their staff control can you control and monitor? � Authentication � Another � Data � Is logon or SSO sanitation your data really deleted? � Others? ? 30 www. netcomlearning. com

What to do? � Careful planning before engagement � Understand the technical aspects of the solution � Make sure it will meet your needs (security and privacy) � Maintain accountability � Define data location restrictions � Ensure laws and regulations are met � Make sure they can support electronic discovery and forensics � Follow 31 NIST and Cloud Security Alliance guidance www. netcomlearning. com

Remember to specify � Personnel (clear backgrounds) � Access control, account resource and management � Availability, including SLA and dependencies � Problem & Incident reporting, notification and resolution � Disclosure agreements � Physical controls � Network boundary protection � Continuity, Backup and Recovery � Assurance levels � Independent audit or assessment 32 www. netcomlearning. com

Resources � Cloud � Security Alliance cloudsecurityalliance. org � ISACA: Cloud Computing Management Audit/Assurance Program, 2010 � NIST SP 800 -144 (draft) � NIST SP 800 -145 � NIST SP 800 -146 (draft) � Federal Cloud Computing Strategy, February 2011 � Above the Clouds managing Risk in the World of Cloud Computing by Mc. Donald (978 -1 -84928 -031 -0) � Cloud Computing, Implementation, Management, and Security by Rittinghouse and Ransome (978 -1 -4398 -0680 -7) 33 www. netcomlearning. com