UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM NET 3 Conference













- Slides: 23

UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM NET 3 Conference & Exhibition 23 July 2003 Information Assessment Test Tool (IATT) for IO/IW Briefing by: Darrell L Quarles Program Director U. S. Army Threat Systems Management Office PEO STRI 256 -876 -9656 ext 268 (DSN: 746) T darrell. quarles@tsmo. redstone. army. mil S M O 23 July 2003 UNCLASSIFIED PM-ITTS

ARMY THREAT SYSTEMS PROGRAM AGENDA Program Background Program Description OTIA Methodology Concept of Operations Capabilities On-Going Development Tool Configuration Summary 23 July 2003 T S M O PM-ITTS

UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM Background This program was developed to supply Information Assurance Analysis to the Intelligence Electronic Warfare Test Directorate (IEWTD) of ATEC/OTC for Operational Testing T S M O 23 July 2003 UNCLASSIFIED PM-ITTS

ARMY THREAT SYSTEMS PROGRAM Program Background (Cont’d) Program was started in FY 01. Task joins the capabilities of two Contractors: Dynetics and General Dynamics (GD) Test Methodology, Threat Definition, and Scenario Development is provided by Dynetics IATT development and IA threat integration by GD T S M O 23 July 2003 PM-ITTS

ARMY THREAT SYSTEMS PROGRAM Program Description This project consists of three tasks to aid in the Information Assurance Assessment: A multi-step Operational Test Information Assurance (OTIA) Assessment Methodology Identification and certification of the IA related DIA validated threat A test tool that can perform penetration testing on the System under Operational test 23 July 2003 PM-ITTS T S M O

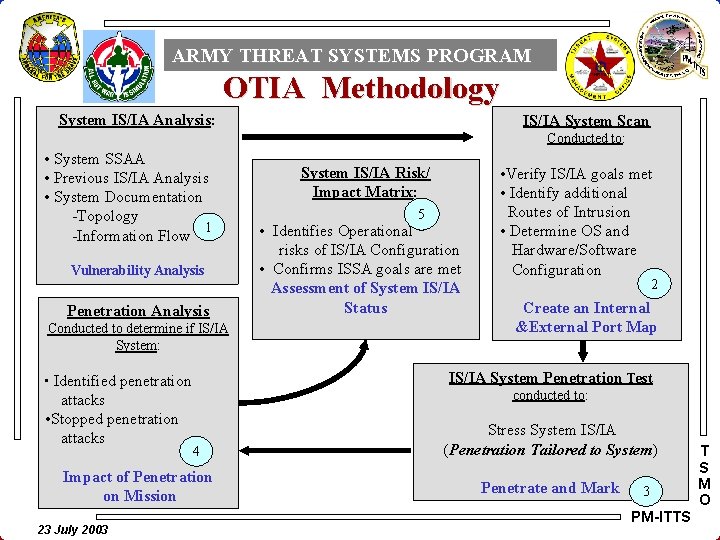
ARMY THREAT SYSTEMS PROGRAM OTIA Methodology System IS/IA Analysis: IS/IA System Scan Conducted to: • System SSAA • Previous IS/IA Analysis • System Documentation -Topology 1 -Information Flow Vulnerability Analysis Penetration Analysis Conducted to determine if IS/IA System: • Identifies Operational risks of IS/IA Configuration • Confirms ISSA goals are met Assessment of System IS/IA Status 2 Create an Internal &External Port Map conducted to: 4 Impact of Penetration on Mission 23 July 2003 5 • Verify IS/IA goals met • Identify additional Routes of Intrusion • Determine OS and Hardware/Software Configuration IS/IA System Penetration Test • Identified penetration attacks • Stopped penetration attacks System IS/IA Risk/ Impact Matrix: Stress System IS/IA (Penetration Tailored to System) Penetrate and Mark 3 PM-ITTS T S M O

UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM IATT Concept of Operations IATT is an easily transportable IA threat launch platform. IATT is to be populated with a DIA validated set of IA Threats that are specific to the target system/test Configuration. IATT is to provide ATEC-OTC and test community the capability to measure the IA health of systems against actual IA threats exercised in realistic scenarios 23 July 2003 UNCLASSIFIED PM-ITTS T S M O

UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM IATT CAPABILITIES Information Gathering - Stealthy and non-stealthy scanning of network assets to find a entry point vulnerability to exploit. Network Monitoring - Passive tools to map the network, steal critical communications. Infiltration - Gain access to a local/remote system by exploiting a vulnerability in COTS software. Password Guessing/Cracking - Guess common passwords / break systems password files. Nefarious Data Manipulation - Intercept/inject mission data transmissions on the network. Denial of Service - Prevent communications through computer service disruption or elimination. 23 July 2003 UNCLASSIFIED PM-ITTS T S M O

UNCLASSIFIED ON-GOING DEVELOPMENTS C 2 IATT/NOVA - Automated scenario execution across multiple IATT units for complex tests. Counter-Counter Measure Development - Provides a more realistic approach of attack scenarios. Automated Decision Aides - Develop capabilities to enhance users decision making process. Wireless IA Capability - Current information attack systems evaluate wired networks against random and intentional threats. The military requires a capability to test military wireless networks against the same types information attack threats. Knowing the susceptibility of military wireless networks to wireless information attack threats increases overall system security. Information assurance on all data links is essential to mission success, force protection, and information dominance. 23 July 2003 UNCLASSIFIED PM-ITTS T S M O

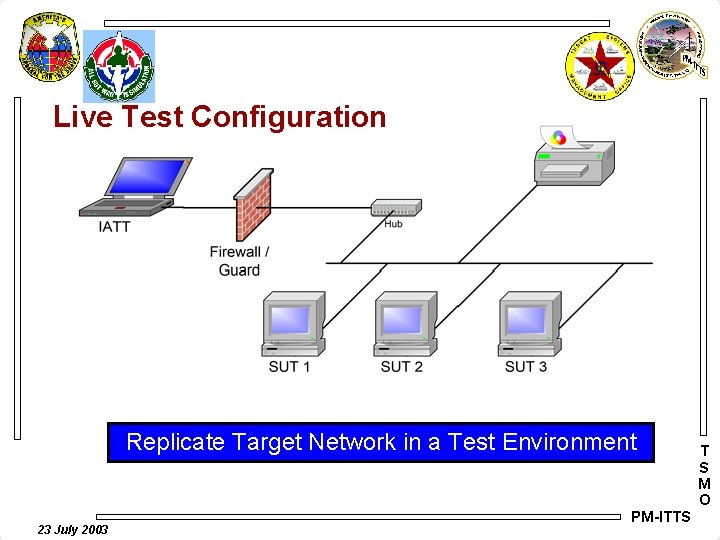
Live Test Configuration Replicate Target Network in a Test Environment 23 July 2003 PM-ITTS T S M O

Mass Scan • Actively scans for hosts on target network • Determines Operating System & Port Information T S M O 23 July 2003 PM-ITTS

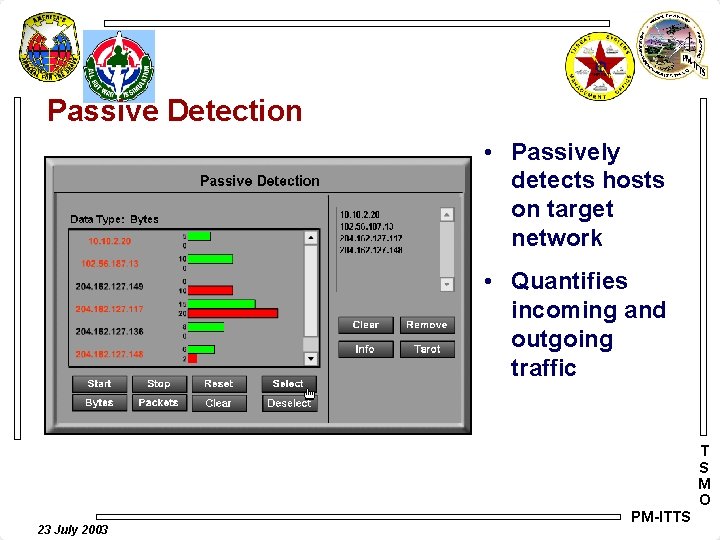
Passive Detection • Passively detects hosts on target network • Quantifies incoming and outgoing traffic T S M O 23 July 2003 PM-ITTS

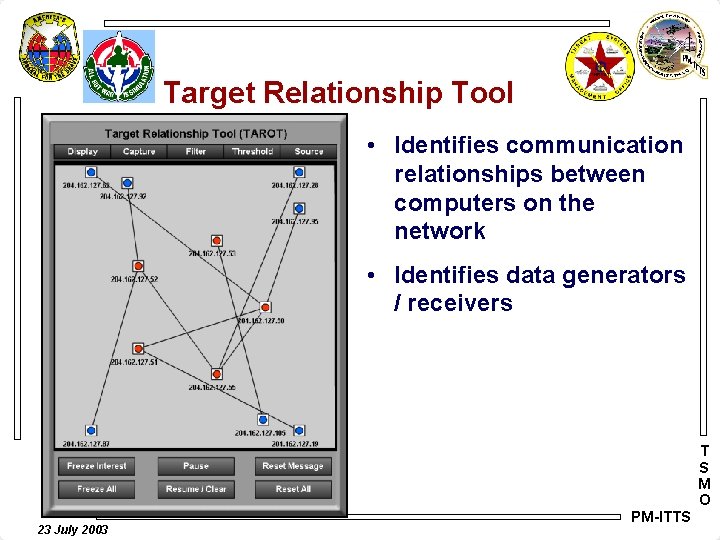
Target Relationship Tool • Identifies communication relationships between computers on the network • Identifies data generators / receivers T S M O 23 July 2003 PM-ITTS

Demonstration Configuration • Singled out target on the network IATT / Illuminate RWS V 6 • The impact of neutralizing the right target is immeasurable Simulated T S M O 23 July 2003 PM-ITTS

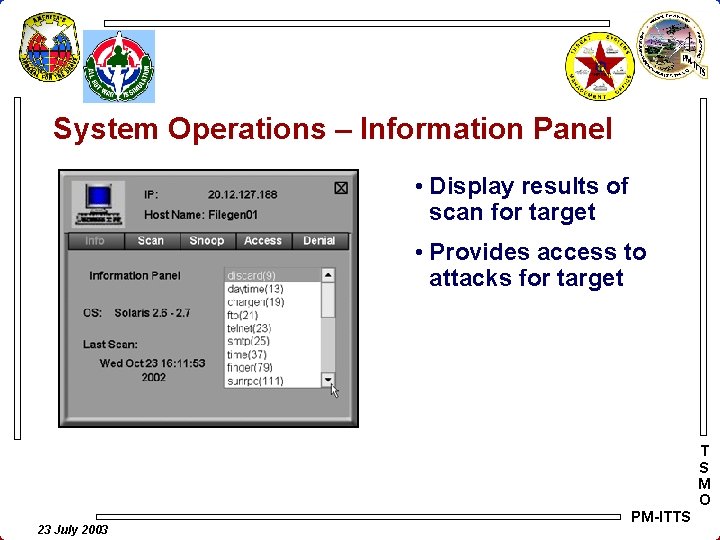
System Operations – Information Panel • Display results of scan for target • Provides access to attacks for target T S M O 23 July 2003 PM-ITTS

System Operations – Snoop • Collects network traffic in multiple protocols, ports, directions. • Collects data to libcap files for review / analysis T S M O 23 July 2003 PM-ITTS

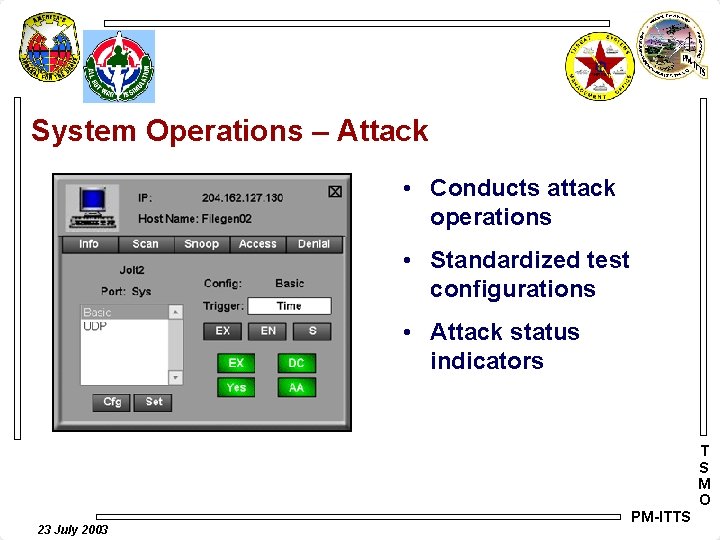
System Operations – Attack • Conducts attack operations • Standardized test configurations • Attack status indicators T S M O 23 July 2003 PM-ITTS

Scan Reports Network Reconnaissance logged for After Action Reviews (AAR) 23 July 2003 PM-ITTS T S M O

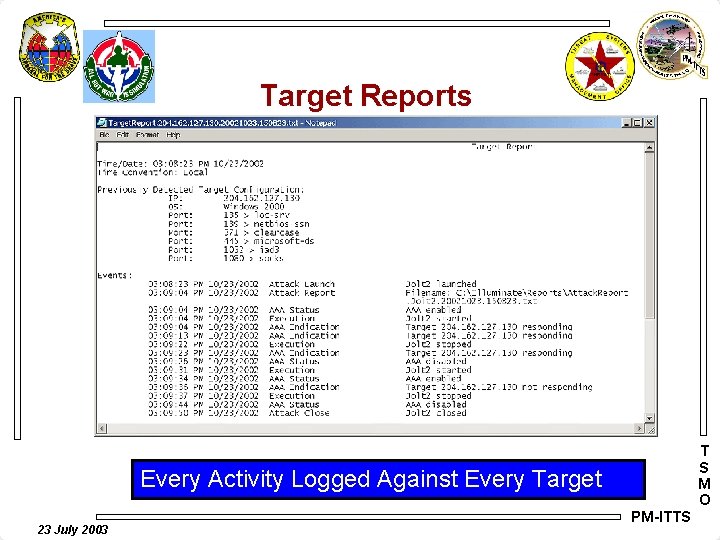
Target Reports T S M O Every Activity Logged Against Every Target 23 July 2003 PM-ITTS

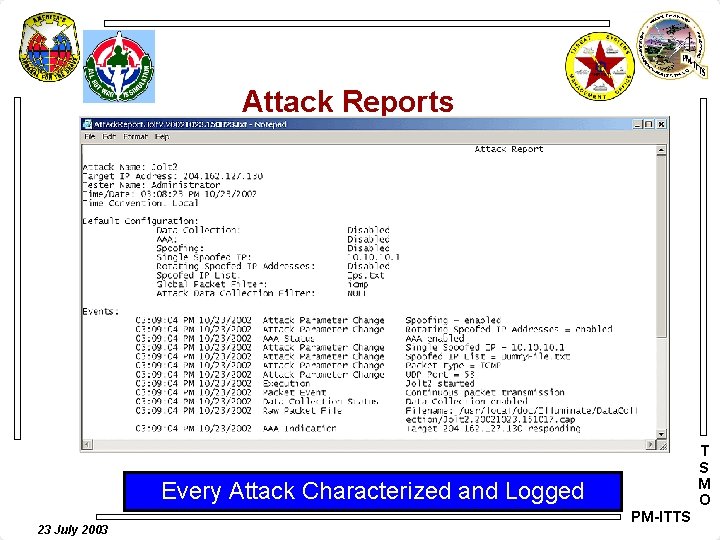
Attack Reports T S M O Every Attack Characterized and Logged 23 July 2003 PM-ITTS

Threat Scenario Requirements Test / Scenario Conductor Threat Execution 23 July 2003 T S M O PM-ITTS

UNCLASSIFIED ARMY THREAT SYSTEMS PROGRAM SUMMARY The methodology and tools being developed is laying the ground work and the essential tools necessary for the T&E community to properly assess the Information Assurance issues associated with our digitized forces. Program foundation success for future development in IA. Program is on schedule. T S M O 23 July 2003 UNCLASSSIFIED PM-ITTS

QUESTIONS? T S M O 23 July 2003 PM-ITTS